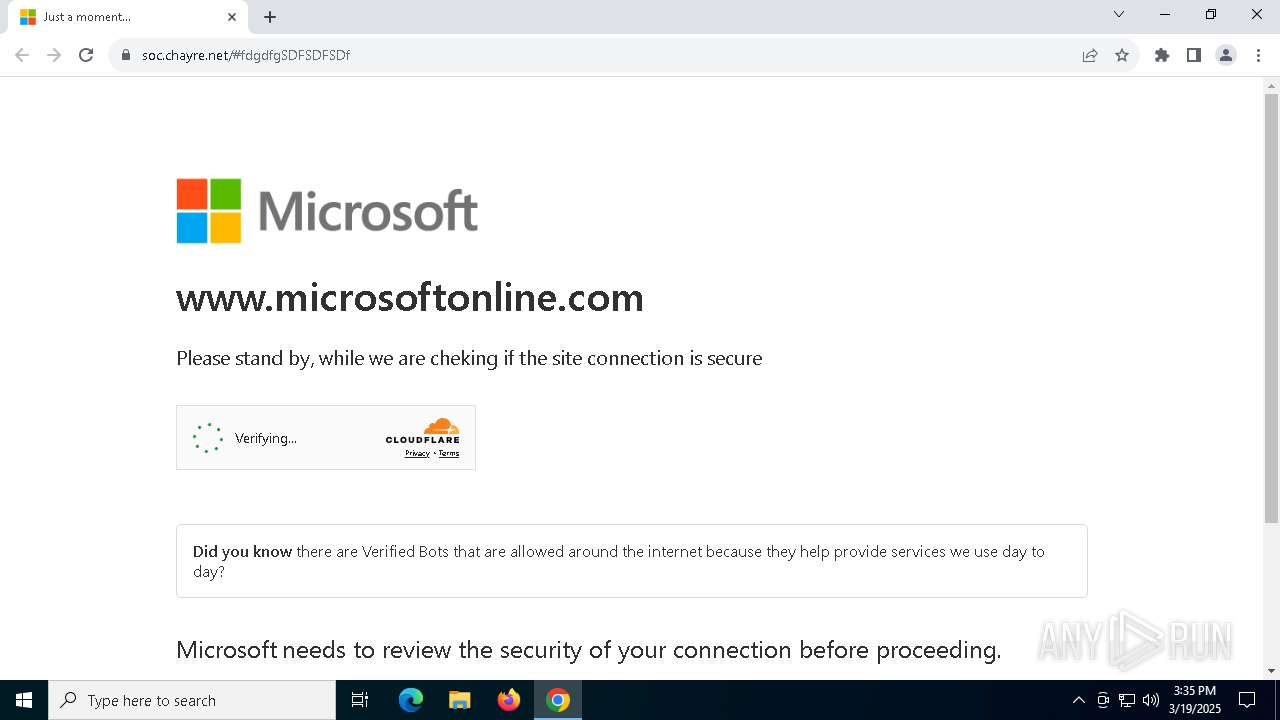
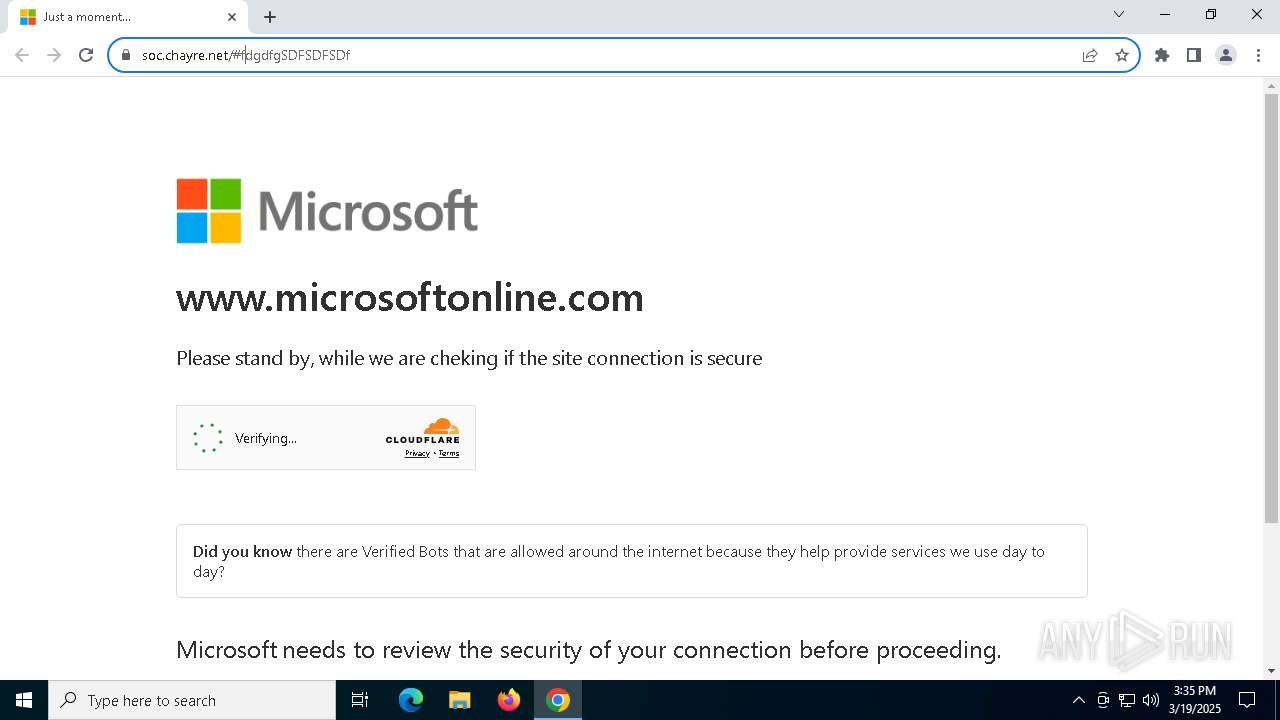
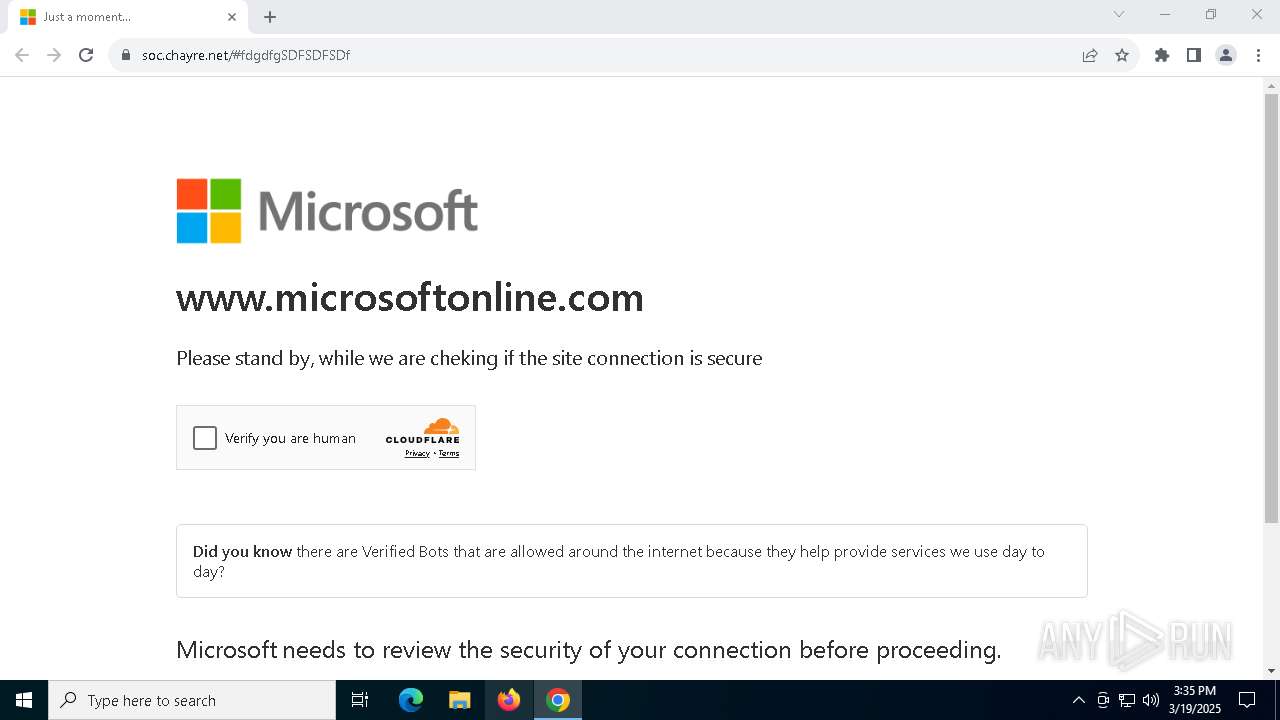
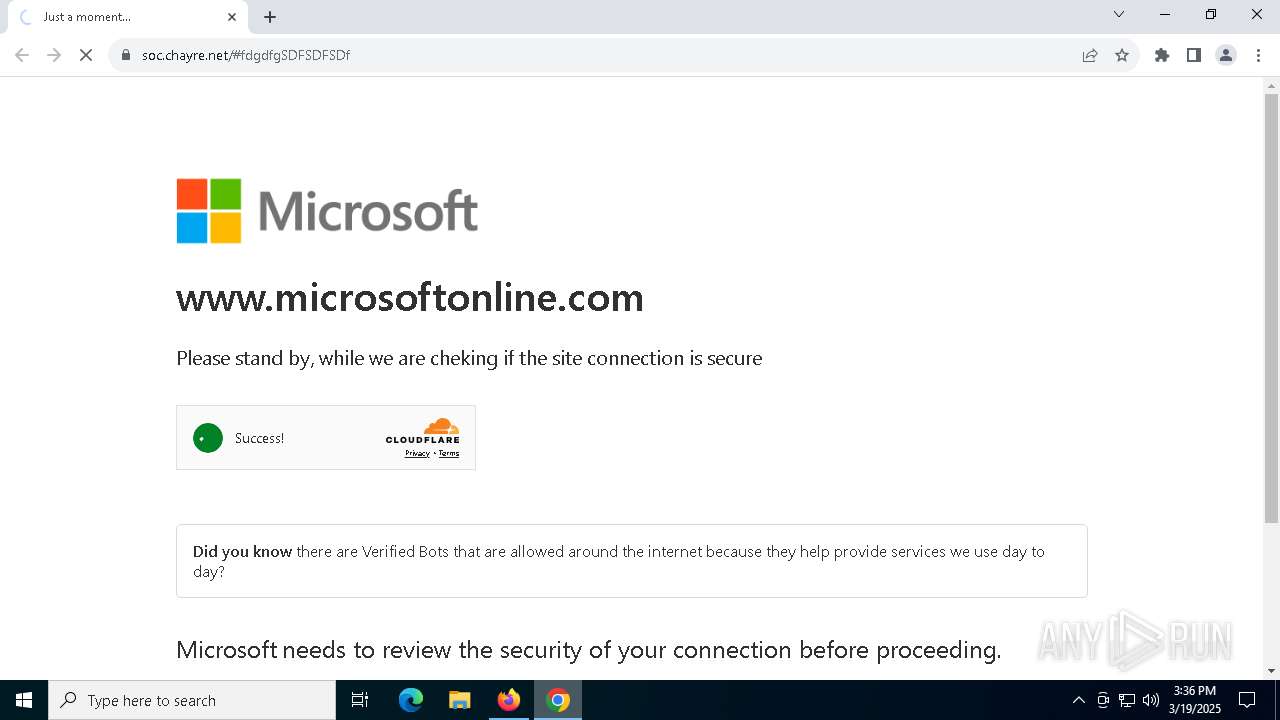
| URL: | soc.chayre.net/#fdgdfgSDFSDFSDf |
| Full analysis: | https://app.any.run/tasks/0ccf8fbb-6b2a-43b7-9374-efc24f8fb4e5 |
| Verdict: | Malicious activity |
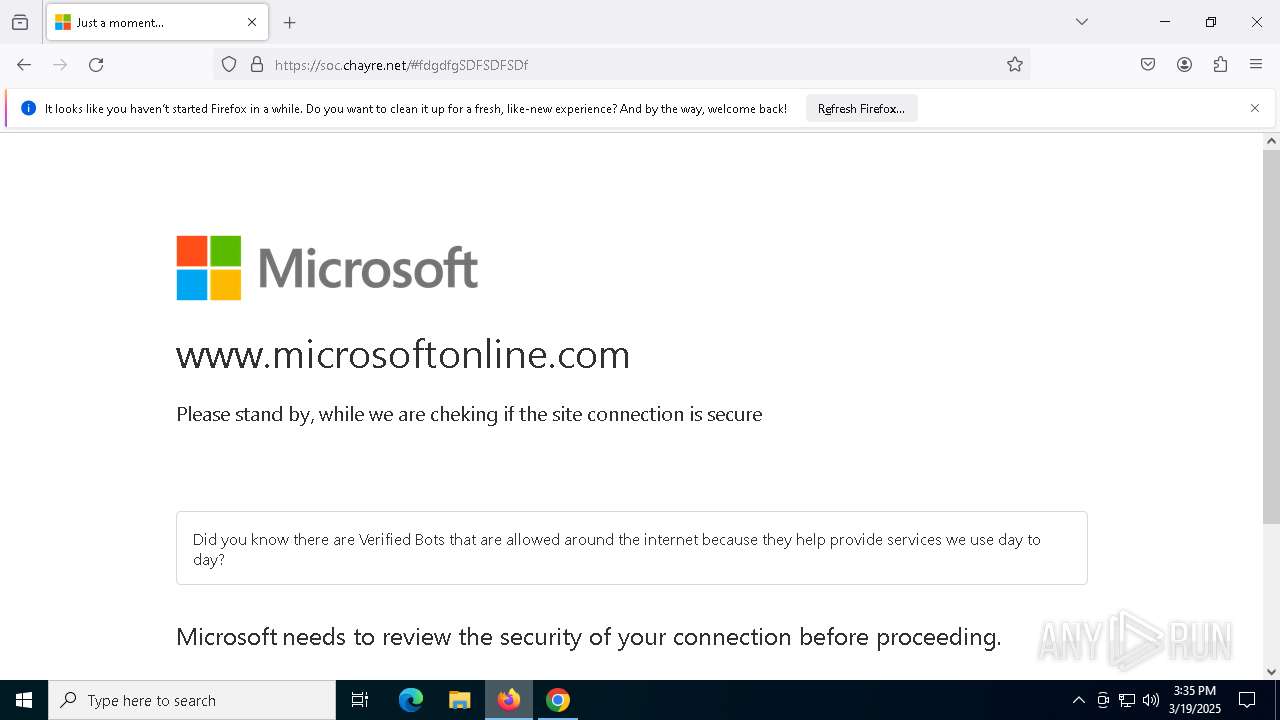
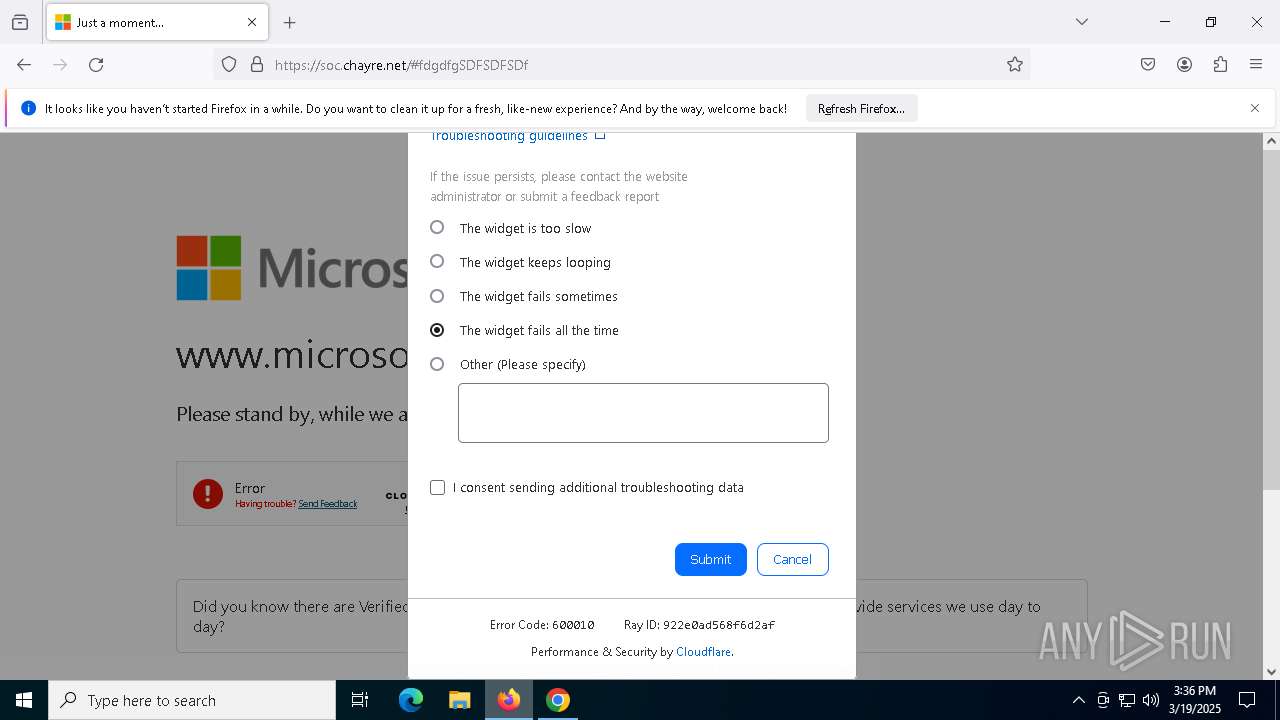
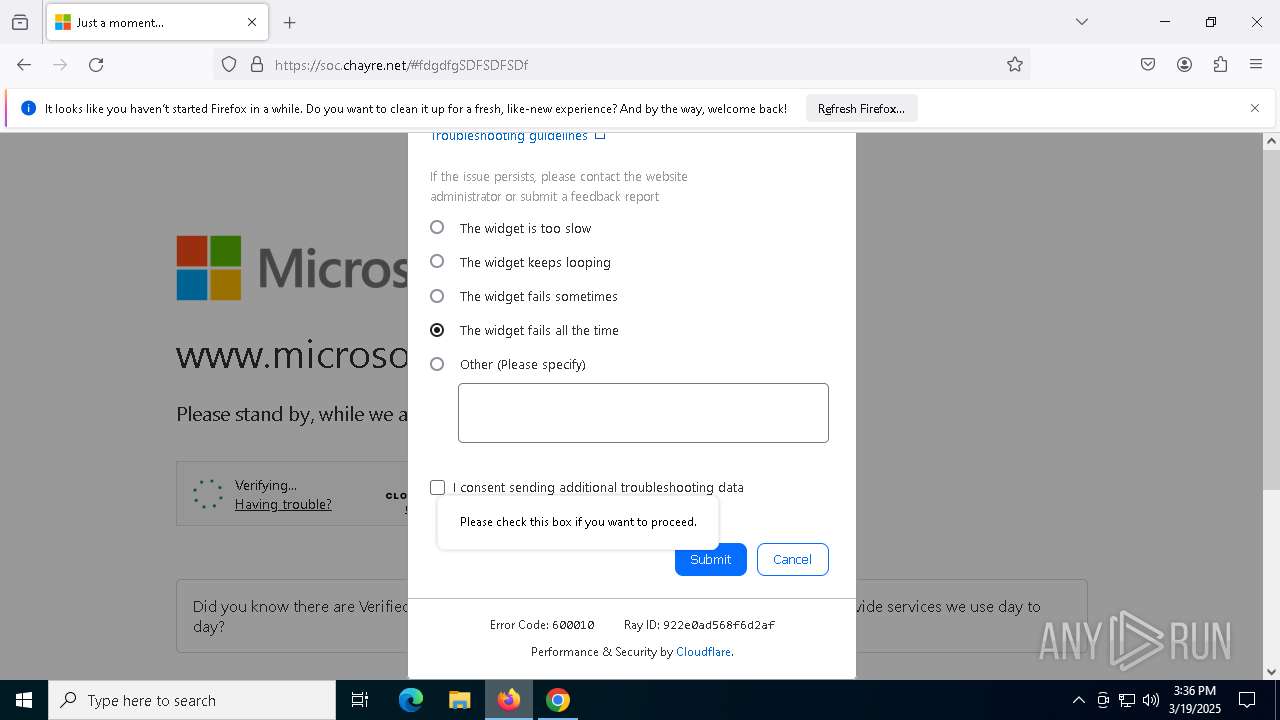
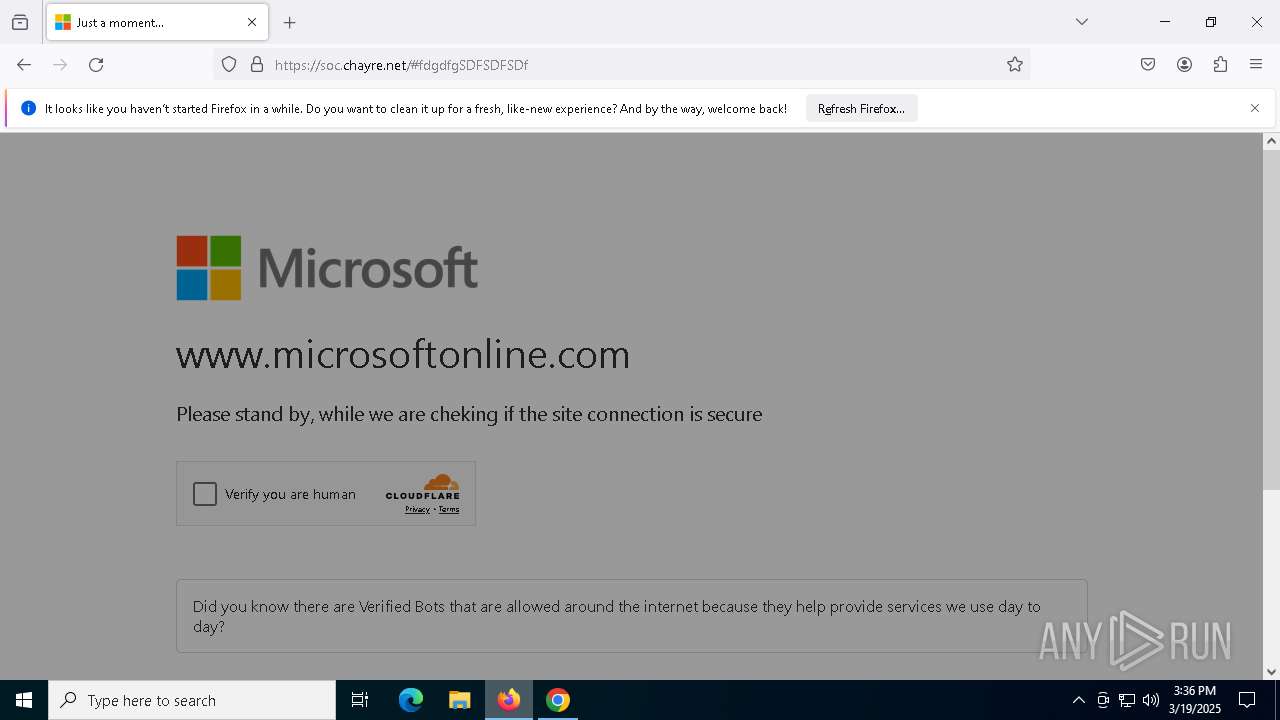
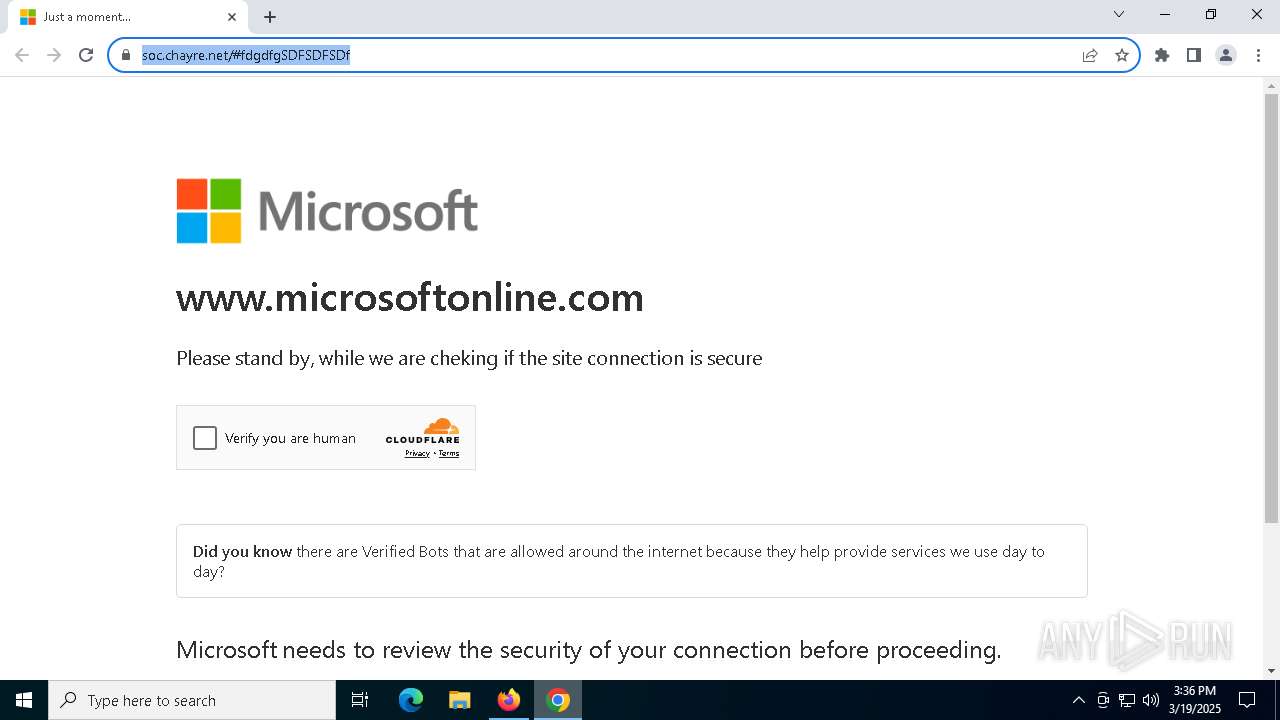
| Threats: | Sneaky 2FA is an Adversary-in-the-Middle (AiTM) phishing kit targeting Microsoft 365 accounts. Distributed as a Phishing-as-a-Service (PhaaS) through a Telegram bot, this malware bypasses two-factor authentication (2FA) to steal credentials and session cookies, posing a significant threat to individuals and organizations. |
| Analysis date: | March 19, 2025, 15:35:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | EAFC50708F079C57172AA095EA586250 |
| SHA1: | 921564FC03E53E57C0DF96E799A56F664030ACFB |
| SHA256: | 3DAFD2E13FCBA0BDE5C242CA2631BF3F5F9D321393CBDCC675D5A782D6B2A76F |
| SSDEEP: | 3:k7XGcLV:H0 |
MALICIOUS
PHISHING has been detected (SURICATA)
- chrome.exe (PID: 7276)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- firefox.exe (PID: 8160)
- firefox.exe (PID: 8136)
- chrome.exe (PID: 5668)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 8668)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 8668)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8668)
Manual execution by a user
- firefox.exe (PID: 8160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
176
Monitored processes
37
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 960 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=856 --field-trial-handle=2032,i,6215889117105868552,8728068116596857182,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1660 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2576 -childID 1 -isForBrowser -prefsHandle 2616 -prefMapHandle 2808 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1472 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {612d5a68-9d14-4163-8e4d-851c9704f333} 8136 "\\.\pipe\gecko-crash-server-pipe.8136" 1d92a4a3f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc8831dc40,0x7ffc8831dc4c,0x7ffc8831dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2188 -parentBuildID 20240213221259 -prefsHandle 2172 -prefMapHandle 2168 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {dc6eb116-877c-4745-ab63-43a94be353ac} 8136 "\\.\pipe\gecko-crash-server-pipe.8136" 1d918981510 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3020 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5380 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1936 -parentBuildID 20240213221259 -prefsHandle 1864 -prefMapHandle 1856 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {9351323f-8fb0-4bfd-9c45-297892add86b} 8136 "\\.\pipe\gecko-crash-server-pipe.8136" 1d9257ef710 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5392 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "soc.chayre.net/#fdgdfgSDFSDFSDf" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 5756 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4344 -childID 2 -isForBrowser -prefsHandle 2252 -prefMapHandle 4328 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1472 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d9fd331a-bde2-4110-b74c-3d2796830d65} 8136 "\\.\pipe\gecko-crash-server-pipe.8136" 1d928e33850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=5464 --field-trial-handle=2032,i,6215889117105868552,8728068116596857182,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
21 119
Read events
21 098
Write events
21
Delete events
0
Modification events
| (PID) Process: | (5668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5668) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (8136) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (8912) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (8912) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (8912) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8668) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
184
Text files
39
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c611.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c611.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c611.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c611.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c620.TMP | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
111
DNS requests
148
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8136 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8136 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
8136 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
8136 | firefox.exe | POST | 200 | 184.24.77.80:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
8136 | firefox.exe | POST | 200 | 184.24.77.80:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
8136 | firefox.exe | POST | 200 | 184.24.77.46:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
7412 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8136 | firefox.exe | POST | 200 | 184.24.77.46:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
8136 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.159:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7276 | chrome.exe | 104.21.96.1:443 | soc.chayre.net | CLOUDFLARENET | — | unknown |
5668 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7276 | chrome.exe | 74.125.143.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
soc.chayre.net |
| unknown |
accounts.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
challenges.cloudflare.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
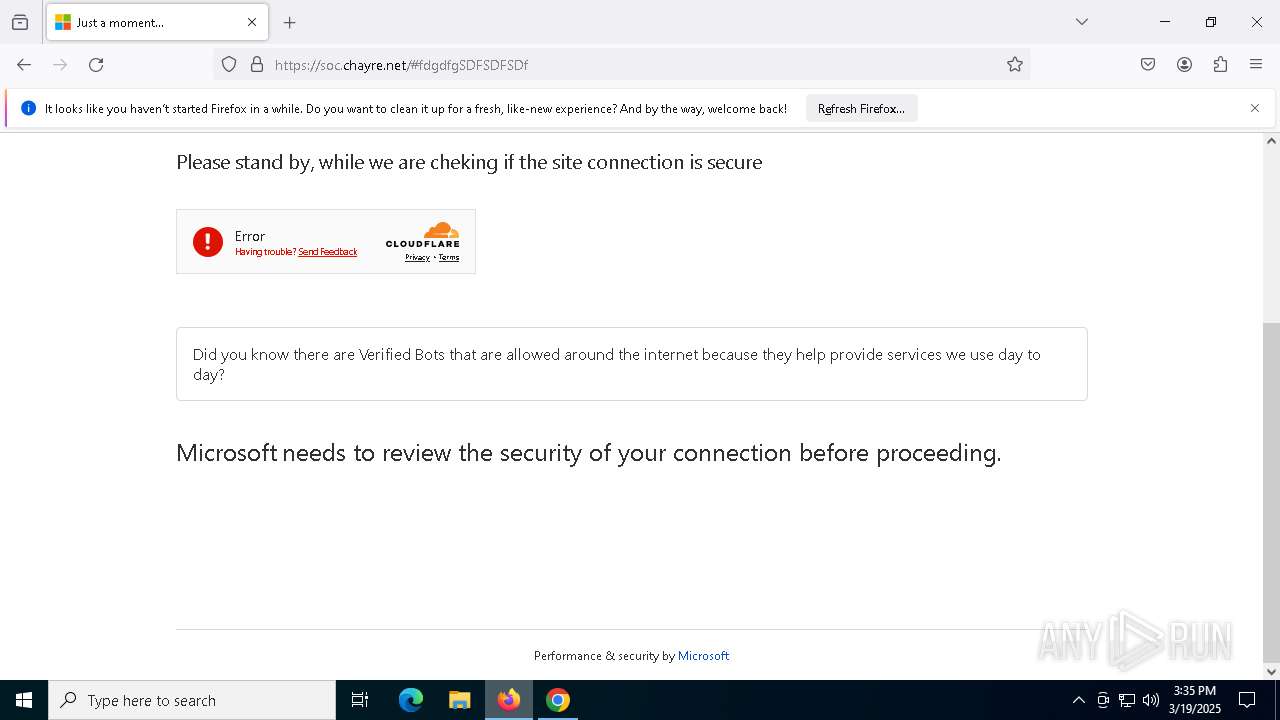
7276 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7276 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
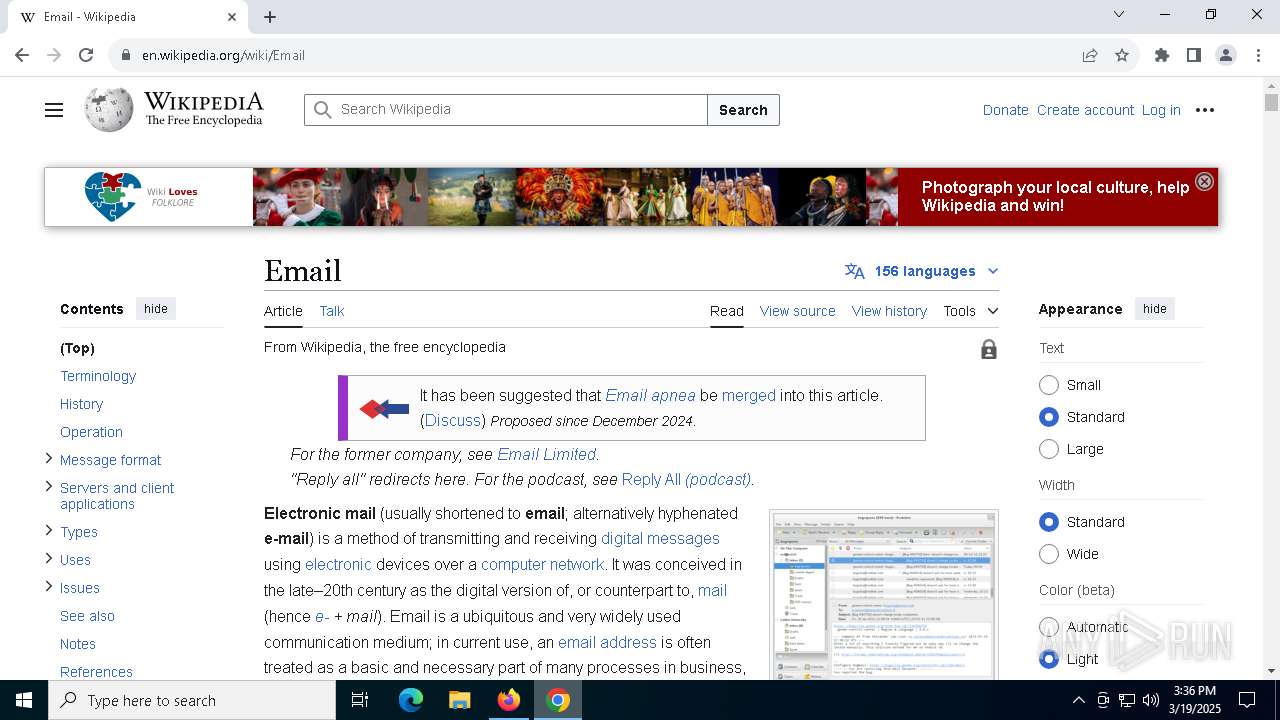
7276 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious redirect to Wikipedia (hrefwiki) |
7276 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious redirect to Wikipedia (hrefwiki) |
7276 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious redirect to Wikipedia (hrefwiki) |
7276 | chrome.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious redirect to Wikipedia (hrefwiki) |
2 ETPRO signatures available at the full report