| File name: | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer |
| Full analysis: | https://app.any.run/tasks/0eeb04fb-348b-403e-a573-b3dcff604740 |
| Verdict: | Malicious activity |
| Threats: | Fog is a ransomware strain that locks and steals sensitive information both on Windows and Linux endpoints. The medial ransom demand is $220,000. The medial payment is $100,000. First spotted in the spring of 2024, it was used to attack educational organizations in the USA, later expanding on other sectors and countries. Main distribution method — compromised VPN credentials. |
| Analysis date: | March 29, 2025, 10:59:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | C909AB654B9474ACEB2ADDB87739B06C |
| SHA1: | E41E9864195F4B0A1718CA374C85F2A000D5232A |
| SHA256: | 3D2CBEF9BE0C48C61A18F0E1DC78501DDABFD7A7663B21C4FCC9C39D48708E91 |
| SSDEEP: | 6144:6/69TBjKU/SFgBLe2UD6w5PatVcFMu/pg9iTcwm:kCKrFALeRDX54VcFR6sT |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 1056)
- net.exe (PID: 7052)
FOG has been detected (YARA)
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
RANSOMWARE has been detected
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
SUSPICIOUS
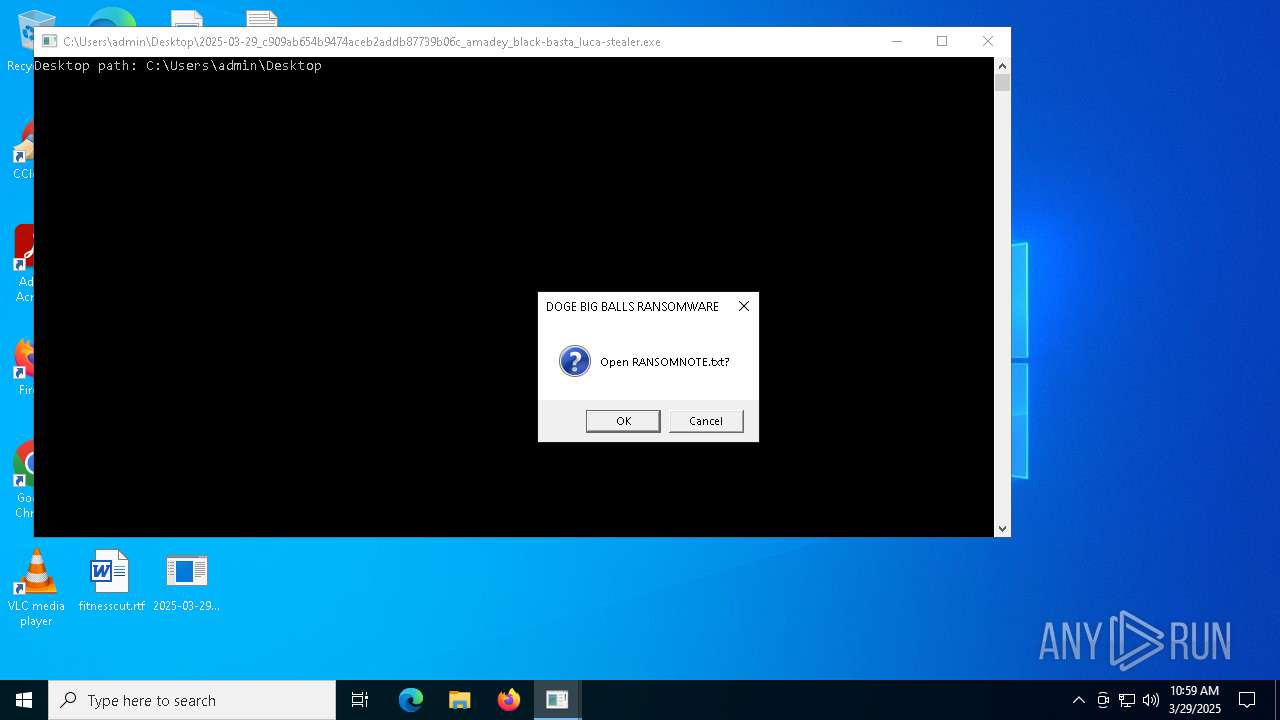
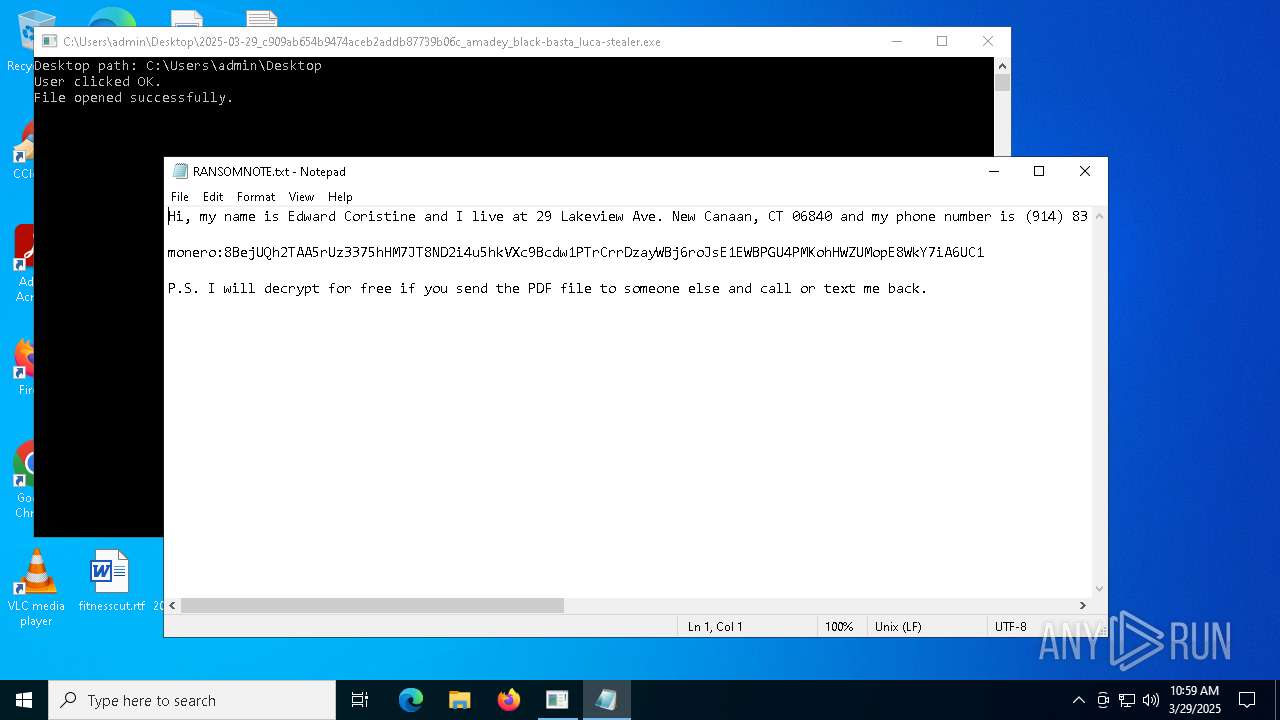
Start notepad (likely ransomware note)
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Starts CMD.EXE for commands execution
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Starts NET.EXE to manage network resources
- cmd.exe (PID: 7508)
- net.exe (PID: 7524)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 8032)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 7576)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 4228)
- cmd.exe (PID: 6700)
Get information on the list of running processes
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
- cmd.exe (PID: 2692)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 8084)
Lists all scheduled tasks in specific format
- schtasks.exe (PID: 1532)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- cmd.exe (PID: 6712)
Creates file in the systems drive root
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Reads security settings of Internet Explorer
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
INFO
Checks supported languages
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 8100)
Reads the machine GUID from the registry
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Creates files or folders in the user directory
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Reads the software policy settings
- slui.exe (PID: 5200)
Checks proxy server information
- slui.exe (PID: 5200)
Process checks computer location settings
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Reads the computer name
- 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe (PID: 7336)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:03:27 12:47:03+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 296448 |
| InitializedDataSize: | 165376 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3513b |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
160
Monitored processes
36
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | netsh firewall show state | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | cmd.exe /c net start | C:\Windows\SysWOW64\cmd.exe | — | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | schtasks /query /fo LIST /v | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | tasklist /SVC | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | DRIVERQUERY | C:\Windows\SysWOW64\driverquery.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Queries the drivers on a system Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | netsh firewall show config | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | cmd.exe /c tasklist /SVC | C:\Windows\SysWOW64\cmd.exe | — | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4228 | cmd.exe /c netsh firewall show state | C:\Windows\SysWOW64\cmd.exe | — | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5200 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5380 | cmd.exe /c schtasks /query /fo LIST /v | C:\Windows\SysWOW64\cmd.exe | — | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 183
Read events
11 180
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7336) 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
| (PID) Process: | (7856) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31170713 | |||
| (PID) Process: | (7856) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
Executable files
0
Suspicious files
2
Text files
2 295
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\Desktop\RANSOMNOTE.txt | text | |
MD5:711990EE3616FF54FEADD91B636DF0E3 | SHA256:75EDCDF92240CBD9DCCDC69E83230B17F2402EB21157A24E7F6E1E97BE1D7FE6 | |||
| 7856 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:F6EC08852F2B037E9A90DD7E5EF51691 | SHA256:82CFA8608DFAB931D2667A17547E247B2ED6FAE759F8417F4F20F55BC8EE4884 | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\Desktop\DbgLog.sys | text | |
MD5:05FD2E4B38DBD2DD9F8F73A6408DDB38 | SHA256:744FF59B62E8A67B39EA5F8E44523FFBB9FE0D816997D20D86E0A21EE74F4A5D | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\Browser\WCChromeExtn\readme.txt | text | |
MD5:B2DE8D453DD3BC4C37AE219A73506A3A | SHA256:4478FFF2DF7DB69E1AFEF769DB2796B2CC9AABF83B6E9D4929858487A2FDF532 | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\locales\readme.txt | text | |
MD5:B2DE8D453DD3BC4C37AE219A73506A3A | SHA256:4478FFF2DF7DB69E1AFEF769DB2796B2CC9AABF83B6E9D4929858487A2FDF532 | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\readme.txt | text | |
MD5:B2DE8D453DD3BC4C37AE219A73506A3A | SHA256:4478FFF2DF7DB69E1AFEF769DB2796B2CC9AABF83B6E9D4929858487A2FDF532 | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\DocSettings\Redaction\CAN\readme.txt | text | |
MD5:B2DE8D453DD3BC4C37AE219A73506A3A | SHA256:4478FFF2DF7DB69E1AFEF769DB2796B2CC9AABF83B6E9D4929858487A2FDF532 | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\bootTel.dat.flocked | binary | |
MD5:5C95D04D8A6FEF2C823E9538BD0A1B38 | SHA256:FDD46368879C37E8002FE3CD17BF800A066B3D5A870DCE8B8D69D19C4513D485 | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\readme.txt | text | |
MD5:B2DE8D453DD3BC4C37AE219A73506A3A | SHA256:4478FFF2DF7DB69E1AFEF769DB2796B2CC9AABF83B6E9D4929858487A2FDF532 | |||
| 7336 | 2025-03-29_c909ab654b9474aceb2addb87739b06c_amadey_black-basta_luca-stealer.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\locales\readme.txt | text | |
MD5:B2DE8D453DD3BC4C37AE219A73506A3A | SHA256:4478FFF2DF7DB69E1AFEF769DB2796B2CC9AABF83B6E9D4929858487A2FDF532 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
40
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4112 | SIHClient.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
4112 | SIHClient.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 13.95.31.18:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
4112 | SIHClient.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
4112 | SIHClient.exe | GET | 200 | 23.222.10.99:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4112 | SIHClient.exe | GET | 200 | 23.222.10.99:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 4.245.163.56:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4112 | SIHClient.exe | GET | 200 | 23.222.10.99:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
4112 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4112 | SIHClient.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4112 | SIHClient.exe | 23.222.10.99:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
4112 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5972 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |