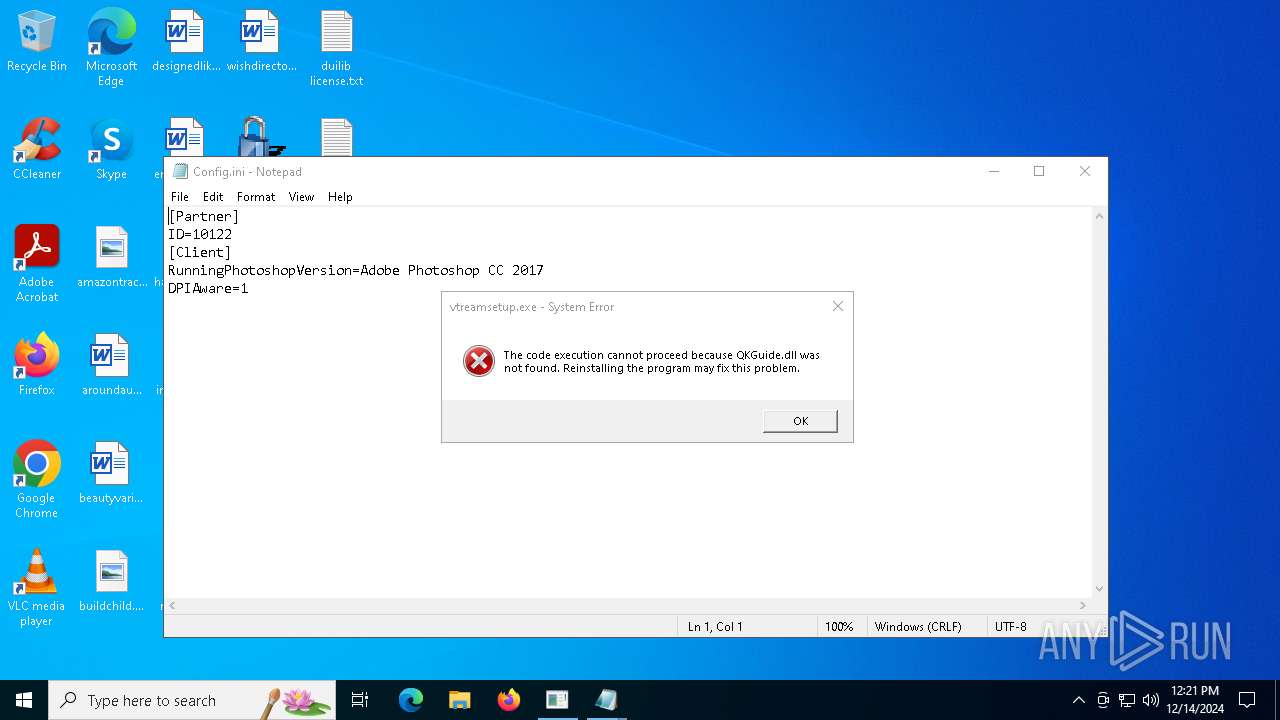
| File name: | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9 |
| Full analysis: | https://app.any.run/tasks/3676db02-c2d7-4ad2-9825-b3d935441982 |
| Verdict: | Malicious activity |
| Threats: | Gh0st RAT is a malware with advanced trojan functionality that enables attackers to establish full control over the victim’s system. The spying capabilities of Gh0st RAT made it a go-to tool for numerous criminal groups in high-profile attacks against government and corporate organizations. The most common vector of attack involving this malware begins with spam and phishing emails. |
| Analysis date: | December 14, 2024, 12:20:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 6A3D6CA7819AB95ADD89A52BCF5C38B1 |
| SHA1: | 606BF1706687D2896D401FE13A0AE60898D4D780 |
| SHA256: | 3D05A3574CC1A041E721BA95F25DE138517D65E2B4CB60854013D56B086728A9 |
| SSDEEP: | 24576:cBissSh156qCDN8NezCDUomnfDhMYIVP:cBissSRDfNezCQomfF2V |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Changes settings for real-time protection
- powershell.exe (PID: 6892)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 7040)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 7124)
Adds path to the Windows Defender exclusion list
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
GH0ST has been detected (SURICATA)
- vtreamsetup.exe (PID: 5888)
SUSPICIOUS
Script disables Windows Defender's real-time protection
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Script disables Windows Defender's behavior monitoring
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Reads security settings of Internet Explorer
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Starts POWERSHELL.EXE for commands execution
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Script adds exclusion path to Windows Defender
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3532)
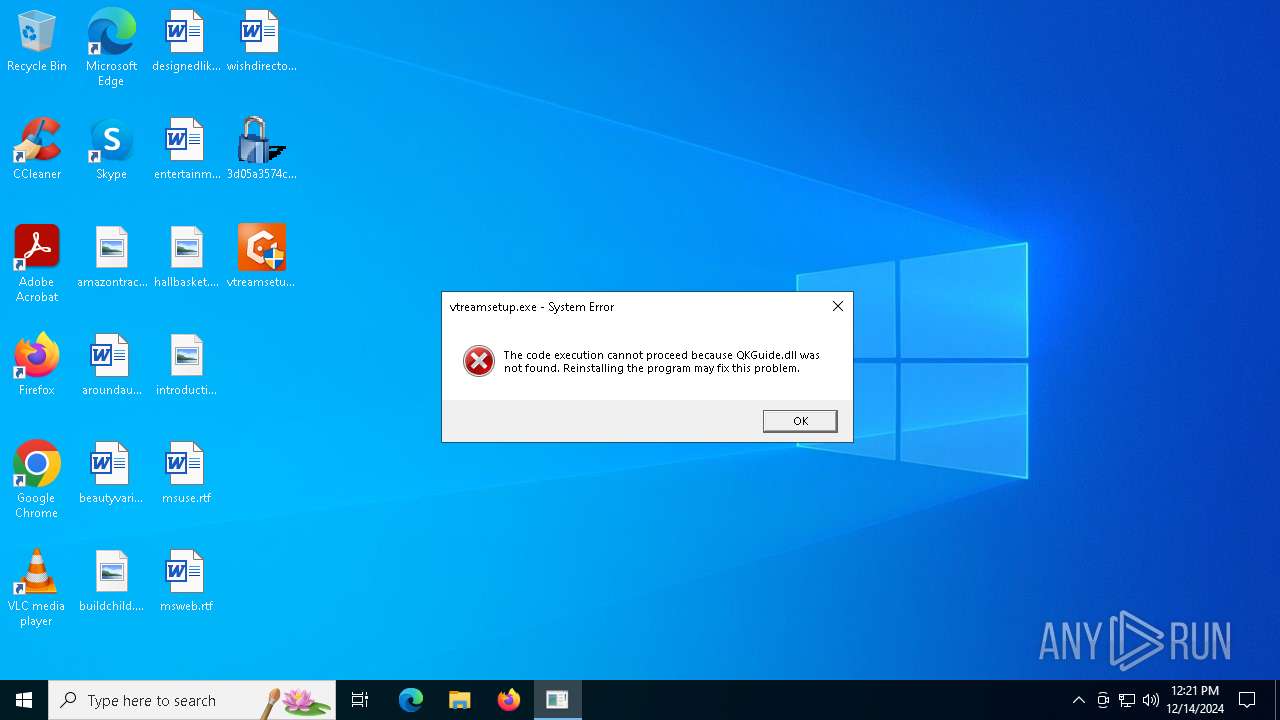
- vtreamsetup.exe (PID: 5156)
- vtreamsetup.exe (PID: 5888)
Executable content was dropped or overwritten
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Process drops legitimate windows executable
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
The process drops C-runtime libraries
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Contacting a server suspected of hosting an CnC
- vtreamsetup.exe (PID: 5888)
Connects to unusual port
- vtreamsetup.exe (PID: 5888)
INFO
Checks supported languages
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
- vtreamsetup.exe (PID: 5888)
Reads the computer name
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
- vtreamsetup.exe (PID: 5888)
The process uses the downloaded file
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
- powershell.exe (PID: 7100)
- powershell.exe (PID: 6864)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 6936)
- powershell.exe (PID: 6980)
- powershell.exe (PID: 7124)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 6892)
- OpenWith.exe (PID: 4596)
Process checks computer location settings
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
The sample compiled with english language support
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
The sample compiled with chinese language support
- 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe (PID: 6480)
Reads CPU info
- vtreamsetup.exe (PID: 5888)
Reads the machine GUID from the registry
- vtreamsetup.exe (PID: 5888)
Sends debugging messages
- vtreamsetup.exe (PID: 5888)
- Acrobat.exe (PID: 6160)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 7100)
- powershell.exe (PID: 7124)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 6892)
- powershell.exe (PID: 6980)
- powershell.exe (PID: 6936)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7100)
- powershell.exe (PID: 6892)
- powershell.exe (PID: 6864)
- powershell.exe (PID: 7124)
- powershell.exe (PID: 3532)
- powershell.exe (PID: 7040)
- powershell.exe (PID: 6936)
- powershell.exe (PID: 6980)
Reads security settings of Internet Explorer
- notepad.exe (PID: 2292)
- OpenWith.exe (PID: 4596)
- notepad.exe (PID: 3612)
- notepad.exe (PID: 848)
- notepad.exe (PID: 6336)
- notepad.exe (PID: 1876)
- notepad.exe (PID: 5556)
- notepad.exe (PID: 6252)
Manual execution by a user
- vtreamsetup.exe (PID: 6072)
- vtreamsetup.exe (PID: 5568)
- notepad.exe (PID: 2292)
- notepad.exe (PID: 3612)
- notepad.exe (PID: 1876)
- notepad.exe (PID: 6336)
- notepad.exe (PID: 848)
- OpenWith.exe (PID: 4596)
- notepad.exe (PID: 5556)
- notepad.exe (PID: 6252)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4596)
Application launched itself
- Acrobat.exe (PID: 5540)
- AcroCEF.exe (PID: 6940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:23 12:19:21+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 581632 |
| InitializedDataSize: | 647168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x32fd6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
165
Monitored processes
40
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\duilib license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2852 --field-trial-handle=1632,i,1336541389437937504,7792286121434922758,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1876 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\mysql connector.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2292 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\directui license.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2548 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2308 --field-trial-handle=1632,i,1336541389437937504,7792286121434922758,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3532 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-MpPreference -ExclusionPath 'C:\Users\Public\stdio' -Force | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\duilib license troy.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3640 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2192 --field-trial-handle=1632,i,1336541389437937504,7792286121434922758,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 4596 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\task.dat | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
59 126
Read events
59 024
Write events
100
Delete events
2
Modification events
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (5540) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\DLLInjection |
| Operation: | write | Name: | bBlockDLLInjection |
Value: 0 | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | sProductGUID |
Value: 4143524F5F5245534944554500 | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | delete value | Name: | ProductInfoCache |
Value: | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AdobeViewer |
| Operation: | write | Name: | EULAAcceptedForBrowser |
Value: 1 | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVEntitlement |
| Operation: | write | Name: | bSynchronizeOPL |
Value: 0 | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | uLastAppLaunchTimeStamp |
Value: | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iNumAcrobatLaunches |
Value: 7 | |||
| (PID) Process: | (6160) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\HomeWelcomeFirstMile |
| Operation: | write | Name: | iCardCountShown |
Value: 3 | |||
Executable files
45
Suspicious files
122
Text files
49
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\Downloads\vst4ySmvG3wizb.dat | — | |
MD5:— | SHA256:— | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\alibabacloud-oss-cpp-sdk.dll | executable | |
MD5:0AAEB781E651BE69F6D643A72B15C6CB | SHA256:E9359D5C42B6767D63525AE73EB194A88C3E68111CEE4EC1A2BDBB8ECF530BB9 | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:79EE4A2FCBE24E9A65106DE834CCDA4A | SHA256:9F7BDA59FAAFC8A455F98397A63A7F7D114EFC4E8A41808C791256EBF33C7613 | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:95C5B49AF7F2C7D3CD0BC14B1E9EFACB | SHA256:FF9B51AFF7FBEC8D7FE5CC478B12492A59B38B068DC2B518324173BB3179A0E1 | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-core-timezone-l1-1-0.dll | executable | |
MD5:C9A55DE62E53D747C5A7FDDEDEF874F9 | SHA256:B5C725BBB475B5C06CC6CB2A2C3C70008F229659F88FBA25CCD5D5C698D06A4B | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-crt-environment-l1-1-0.dll | executable | |
MD5:39325E5F023EB564C87D30F7E06DFF23 | SHA256:56D8B7EE7619579A3C648EB130C9354BA1BA5B33A07A4F350370EE7B3653749A | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-core-synch-l1-2-0.dll | executable | |
MD5:6E704280D632C2F8F2CADEFCAE25AD85 | SHA256:758A2F9EF6908B51745DB50D89610FE1DE921D93B2DBEA919BFDBA813D5D8893 | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-crt-convert-l1-1-0.dll | executable | |
MD5:9DDEA3CC96E0FDD3443CC60D649931B3 | SHA256:B7C3EBC36C84630A52D23D1C0E79D61012DFA44CDEBDF039AF31EC9E322845A5 | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-crt-filesystem-l1-1-0.dll | executable | |
MD5:228C6BBE1BCE84315E4927392A3BAEE5 | SHA256:AC0CEC8644340125507DD0BC9A90B1853A2D194EB60A049237FB5E752D349065 | |||
| 6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | C:\Users\Public\stdio\api-ms-win-crt-heap-l1-1-0.dll | executable | |
MD5:1776A2B85378B27825CF5E5A3A132D9A | SHA256:675B1B82DD485CC8C8A099272DB9241D0D2A7F45424901F35231B79186EC47EE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
29
DNS requests
14
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | GET | 200 | 27.124.47.7:80 | http://download.linuxroot.site/download/3190.dat | unknown | — | — | unknown |
6092 | svchost.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.177:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6092 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | OPTIONS | 204 | 3.233.129.217:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=MY&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | — | — | unknown |
— | — | GET | 200 | 23.218.208.137:443 | https://geo2.adobe.com/ | unknown | text | 50 b | whitelisted |
— | — | GET | 200 | 184.30.20.134:443 | https://armmf.adobe.com/onboarding/smskillreader.txt | unknown | text | 120 b | whitelisted |
— | — | GET | 200 | 23.48.23.149:443 | https://acroipm2.adobe.com/23/rdr_64x/ENU/win/nooem/none/consumer/message.zip | unknown | compressed | 141 Kb | whitelisted |
— | — | GET | 200 | 52.6.155.20:443 | https://p13n.adobe.io/psdk/v2/content?surfaceId=ACROBAT_READER_MASTER_SURFACEID&surfaceId=DC_READER_LAUNCH_CARD&surfaceId=DC_Reader_RHP_Banner&surfaceId=DC_Reader_RHP_Retention&surfaceId=Edit_InApp_Aug2020&surfaceId=DC_FirstMile_Right_Sec_Surface&surfaceId=DC_Reader_Upsell_Cards&surfaceId=DC_FirstMile_Home_View_Surface&surfaceId=DC_Reader_RHP_Intent_Banner&surfaceId=DC_Reader_Disc_LHP_Banner&surfaceId=DC_Reader_Edit_LHP_Banner&surfaceId=DC_Reader_Convert_LHP_Banner&surfaceId=DC_Reader_Sign_LHP_Banner&surfaceId=DC_Reader_More_LHP_Banner&surfaceId=DC_Reader_Disc_LHP_Retention&adcProductLanguage=en-us&adcVersion=23.1.20093&adcProductType=SingleClientMini&adcOSType=WIN&adcCountryCode=MY&adcXAPIClientID=api_reader_desktop_win_23.1.20093&encodingScheme=BASE_64 | unknown | binary | 187 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6092 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.155:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6480 | 3d05a3574cc1a041e721ba95f25de138517d65e2b4cb60854013d56b086728a9.exe | 27.124.47.7:80 | download.linuxroot.site | BGPNET Global ASN | SG | unknown |
4712 | MoUsoCoreWorker.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6092 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6092 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
download.linuxroot.site |
| unknown |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.baiodu.com |
| unknown |
hehua.cookielive.top |
| malicious |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
5888 | vtreamsetup.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Gh0stRAT TCP Packet |
Process | Message |
|---|---|
vtreamsetup.exe | vtreamsetup.exe |