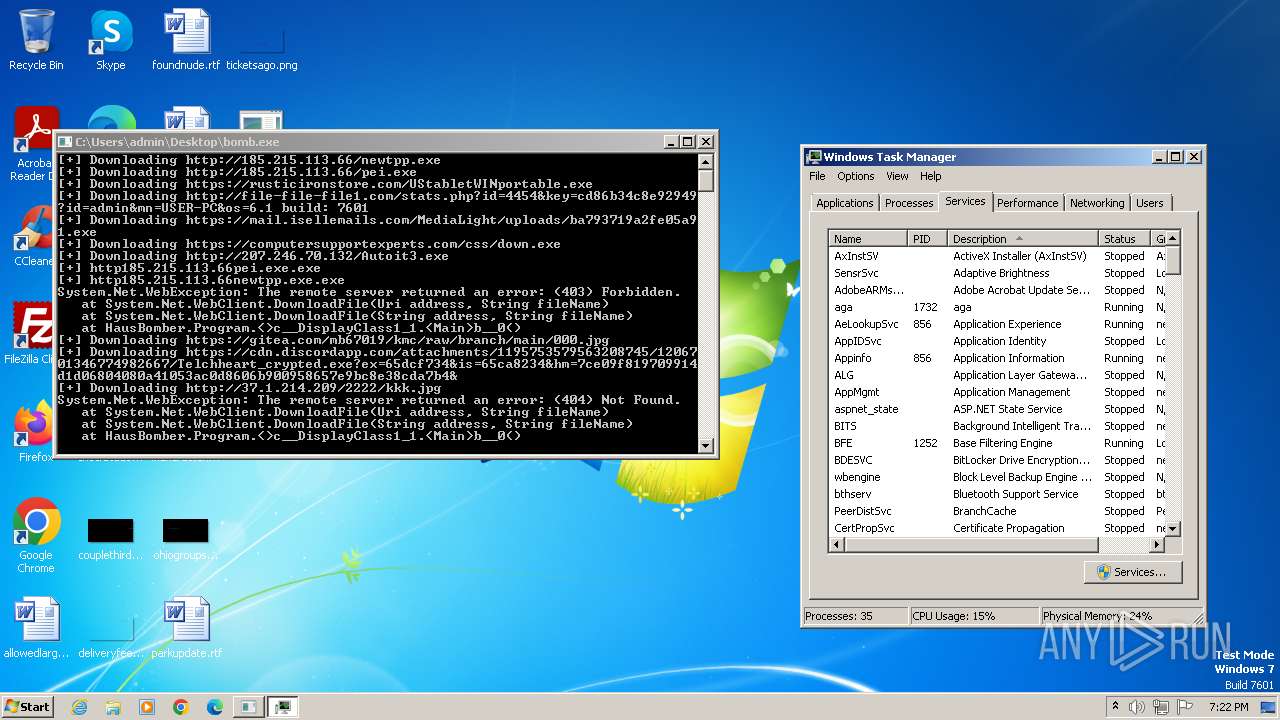
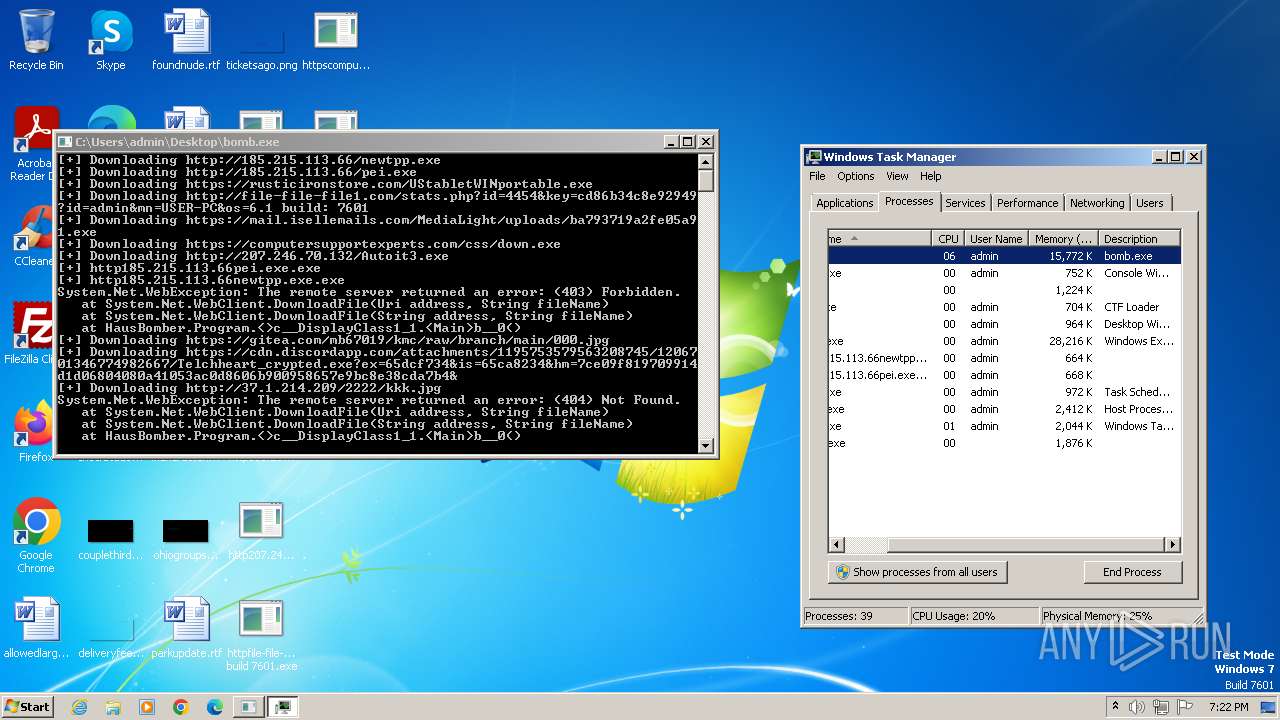
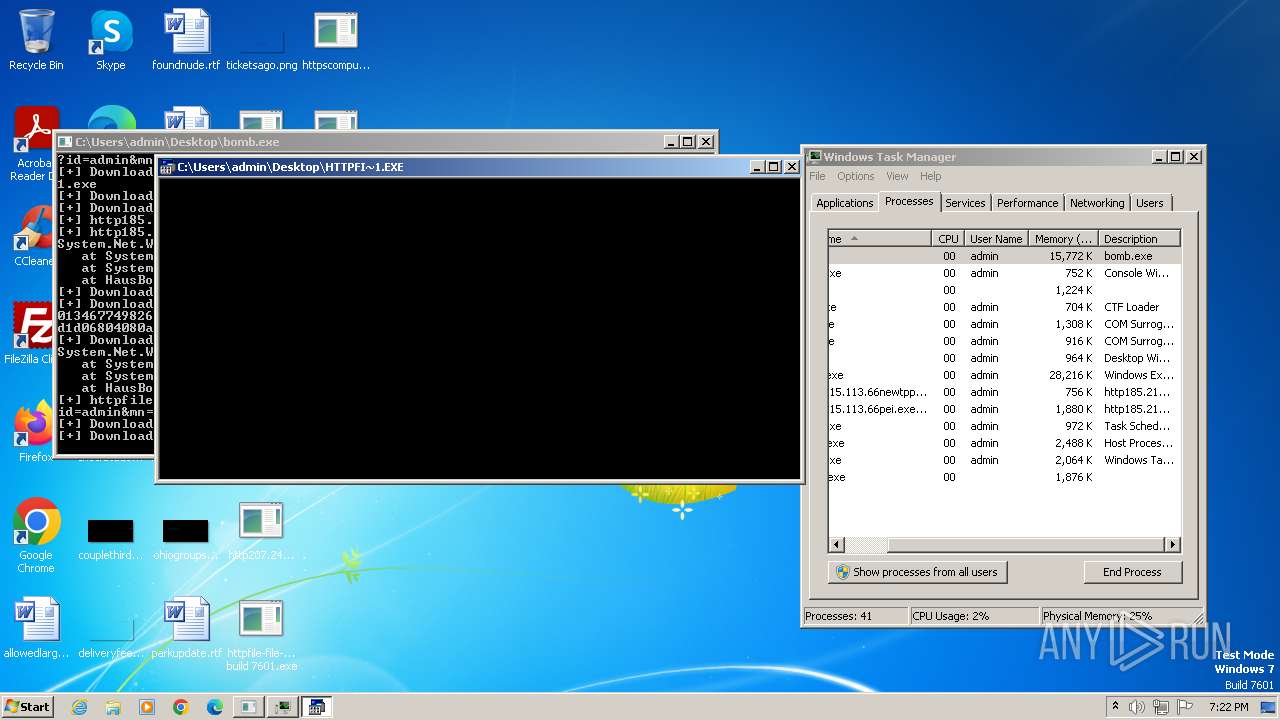
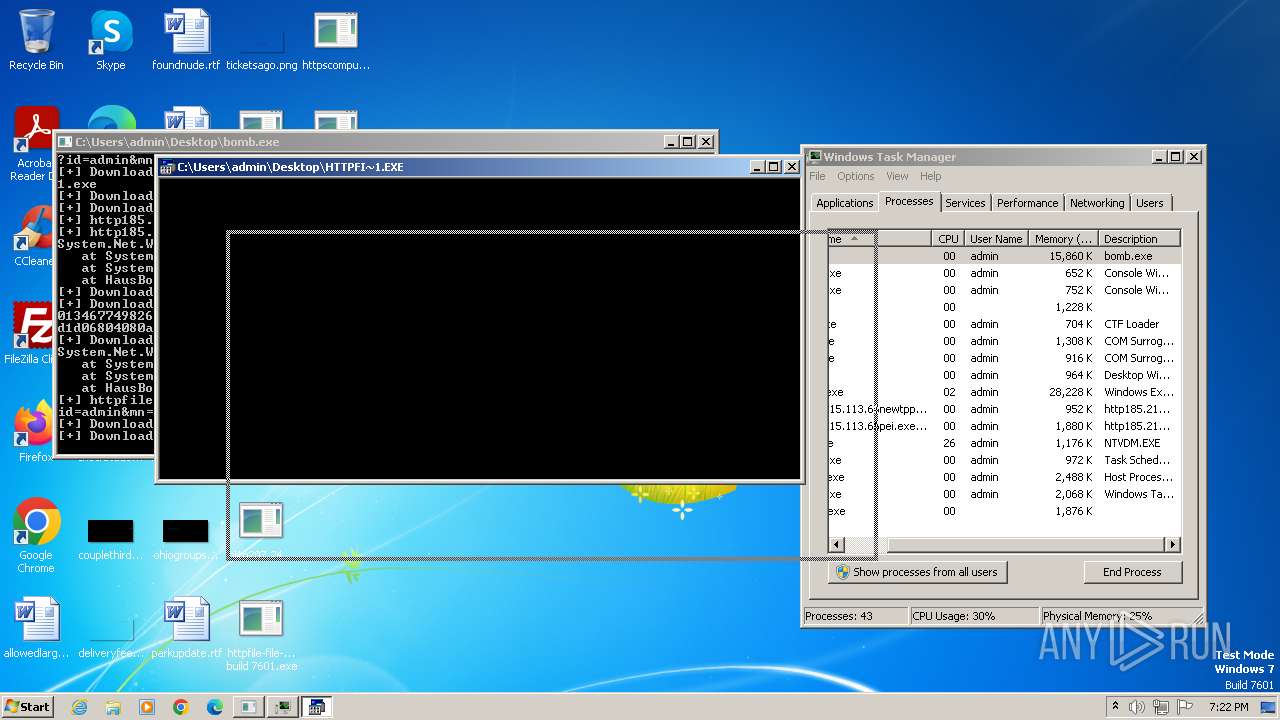
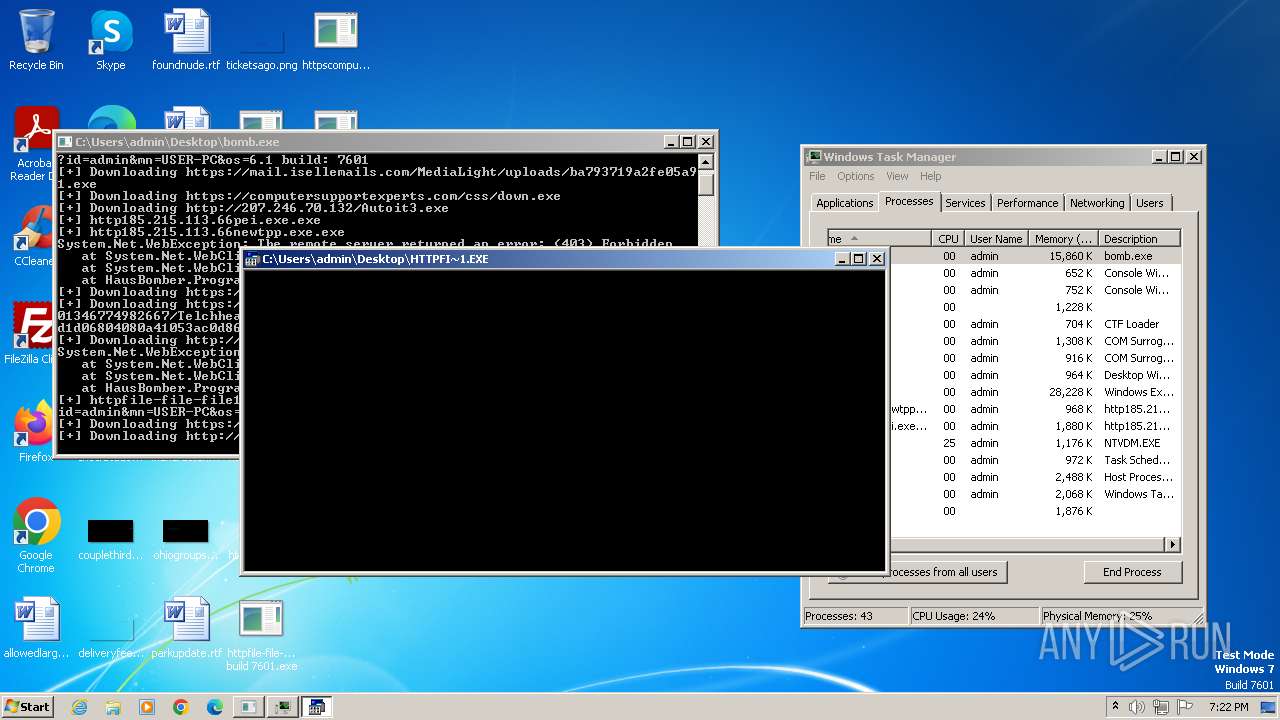
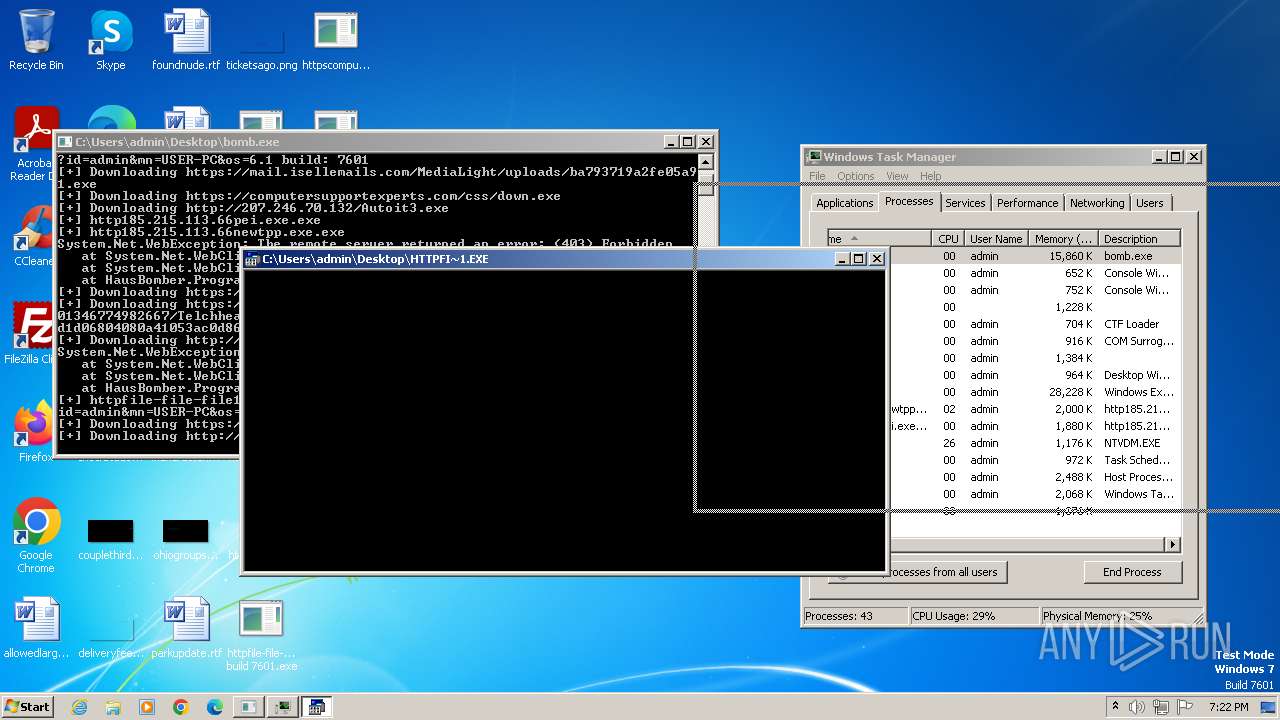
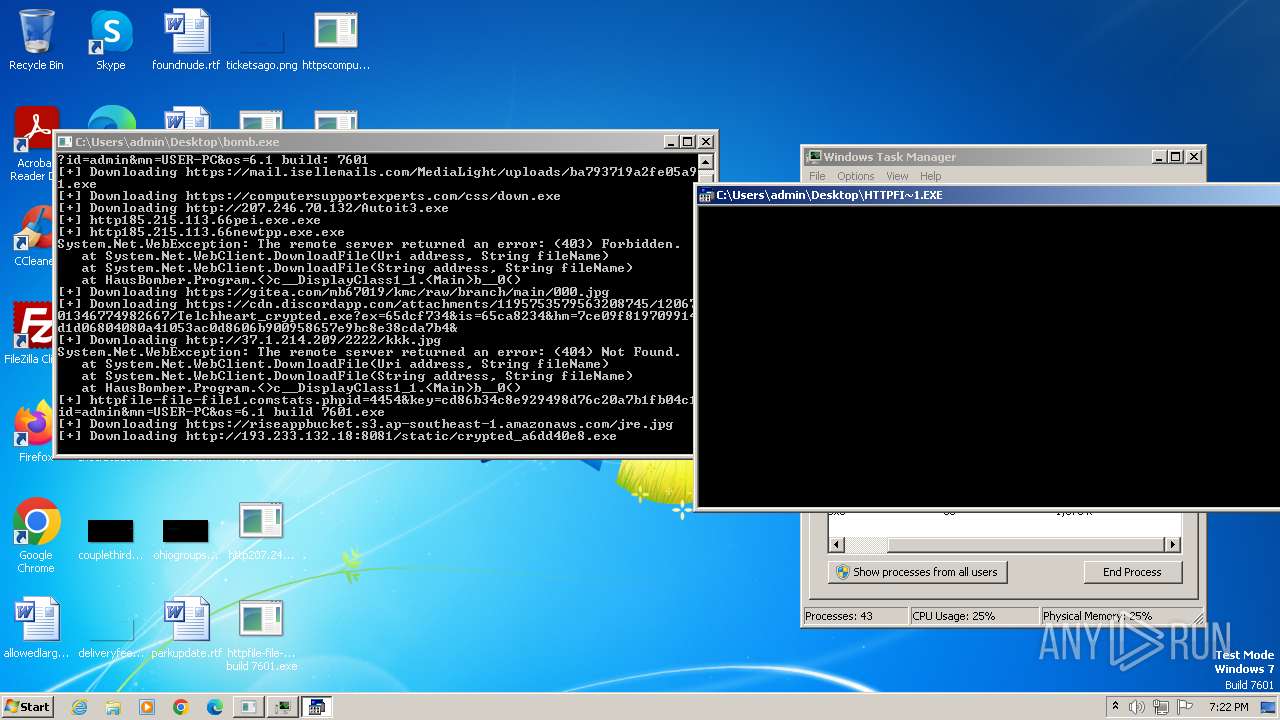
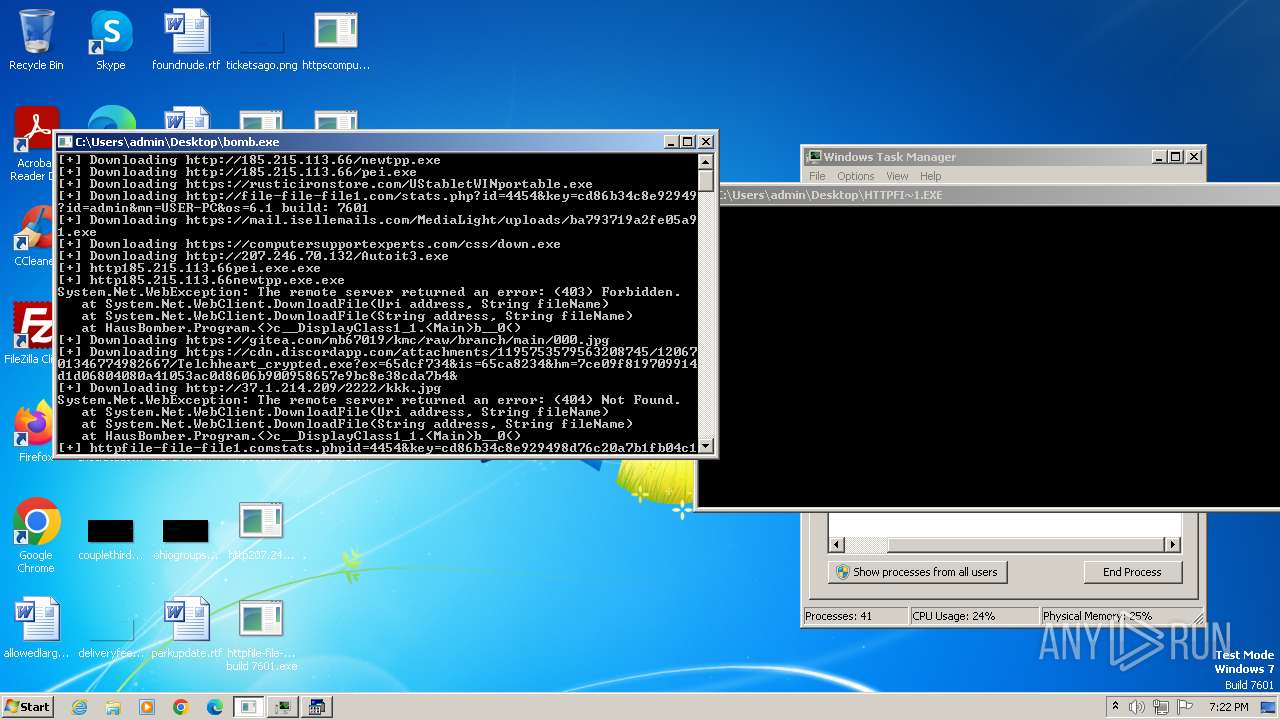
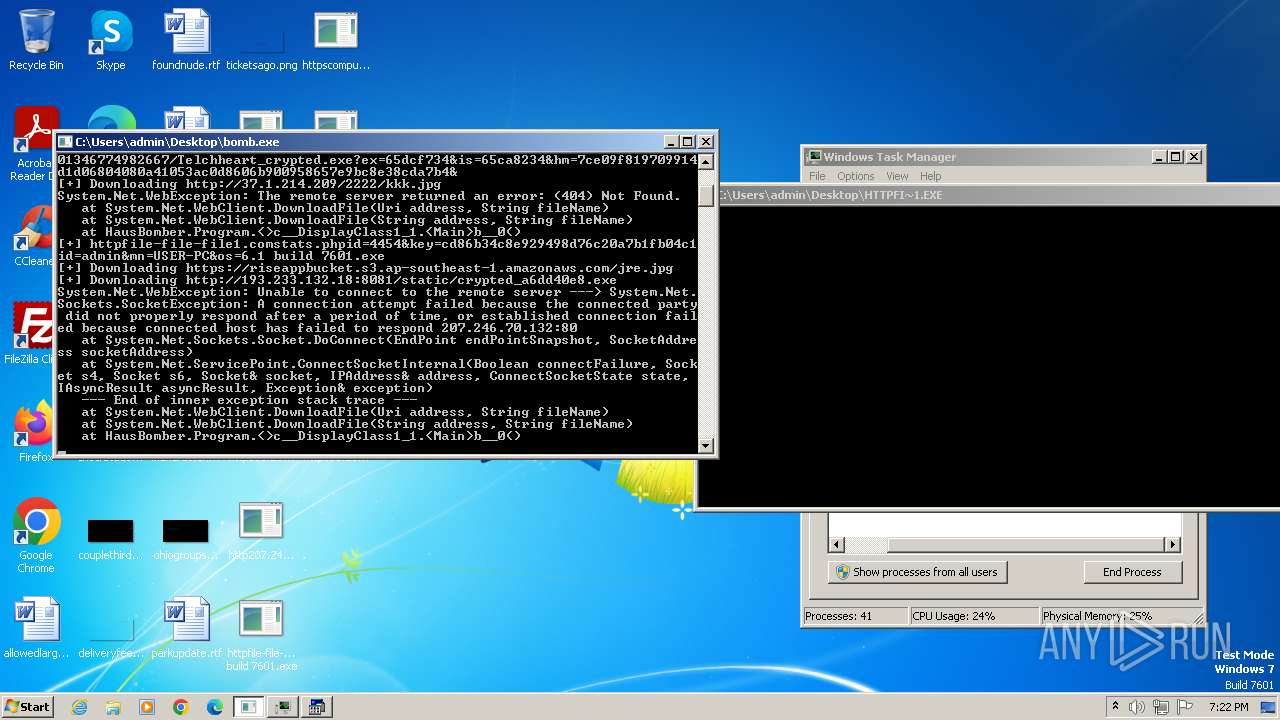
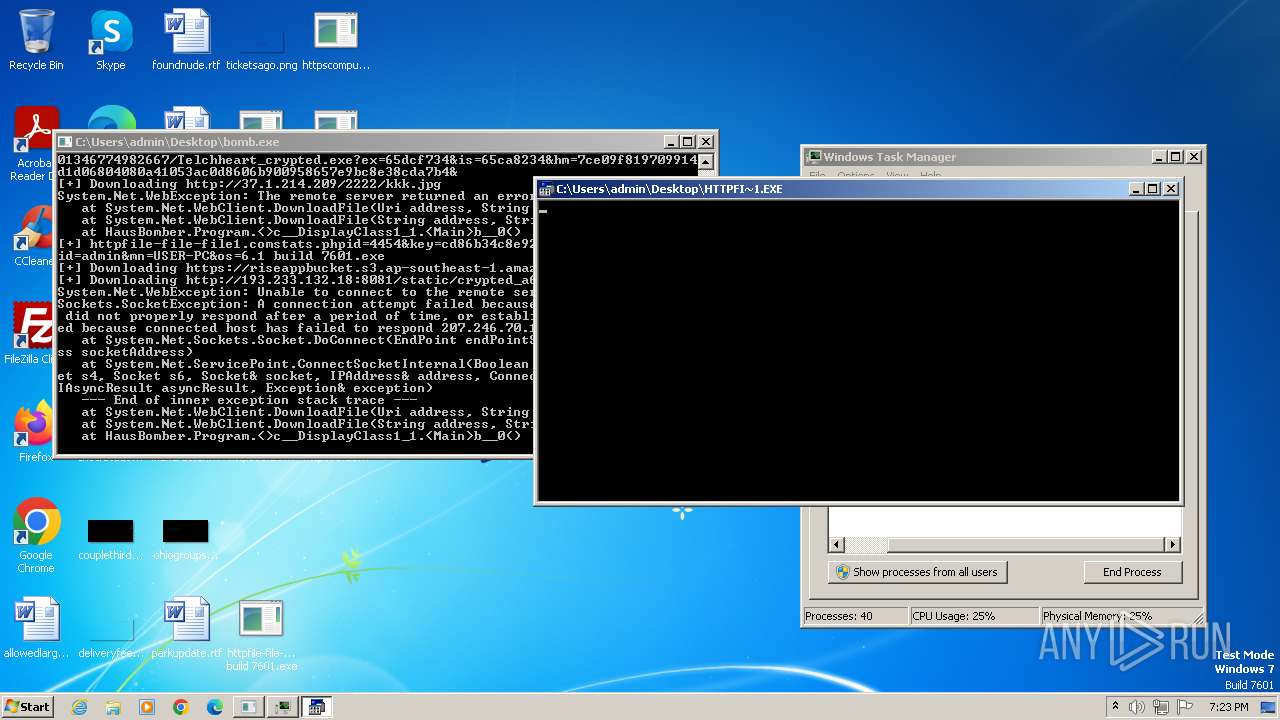
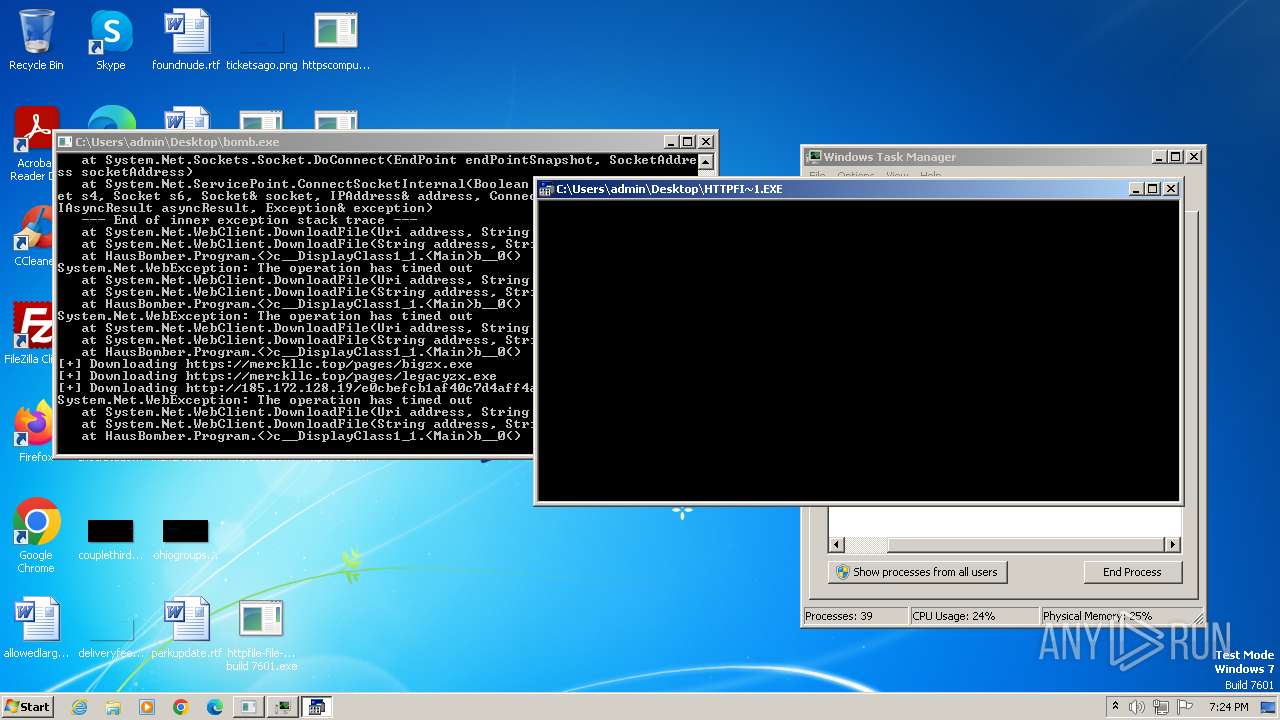
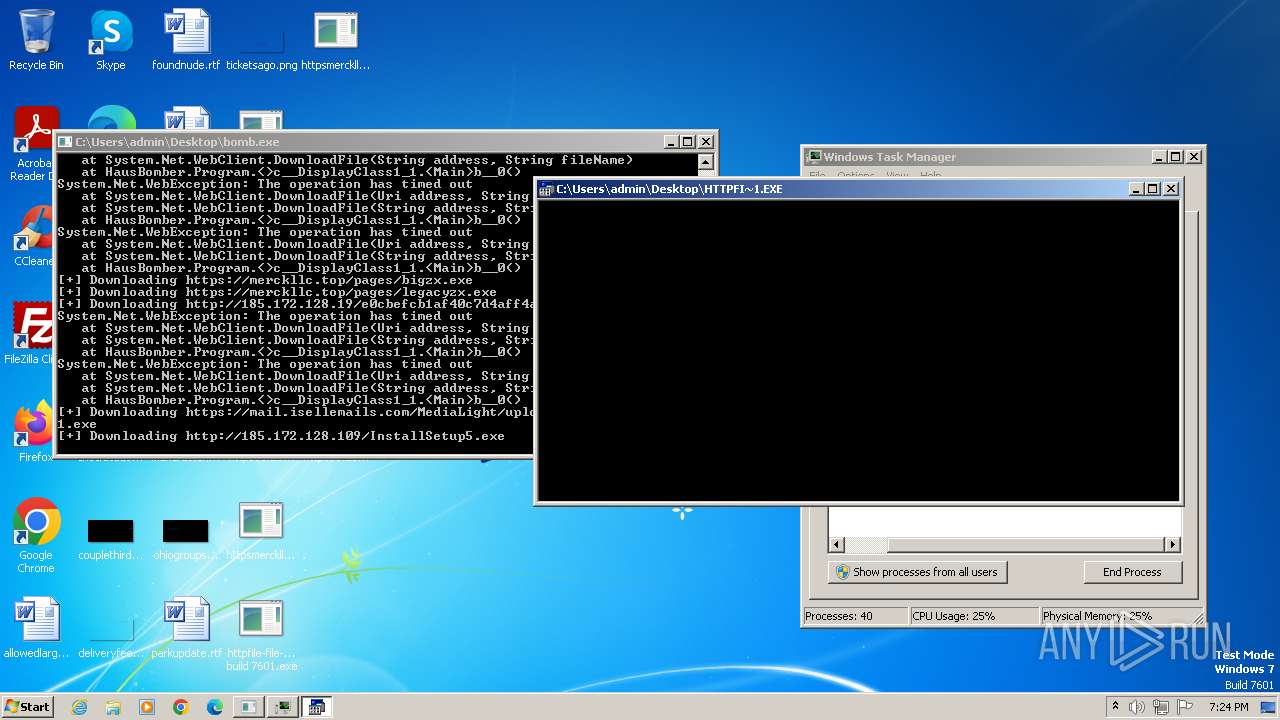
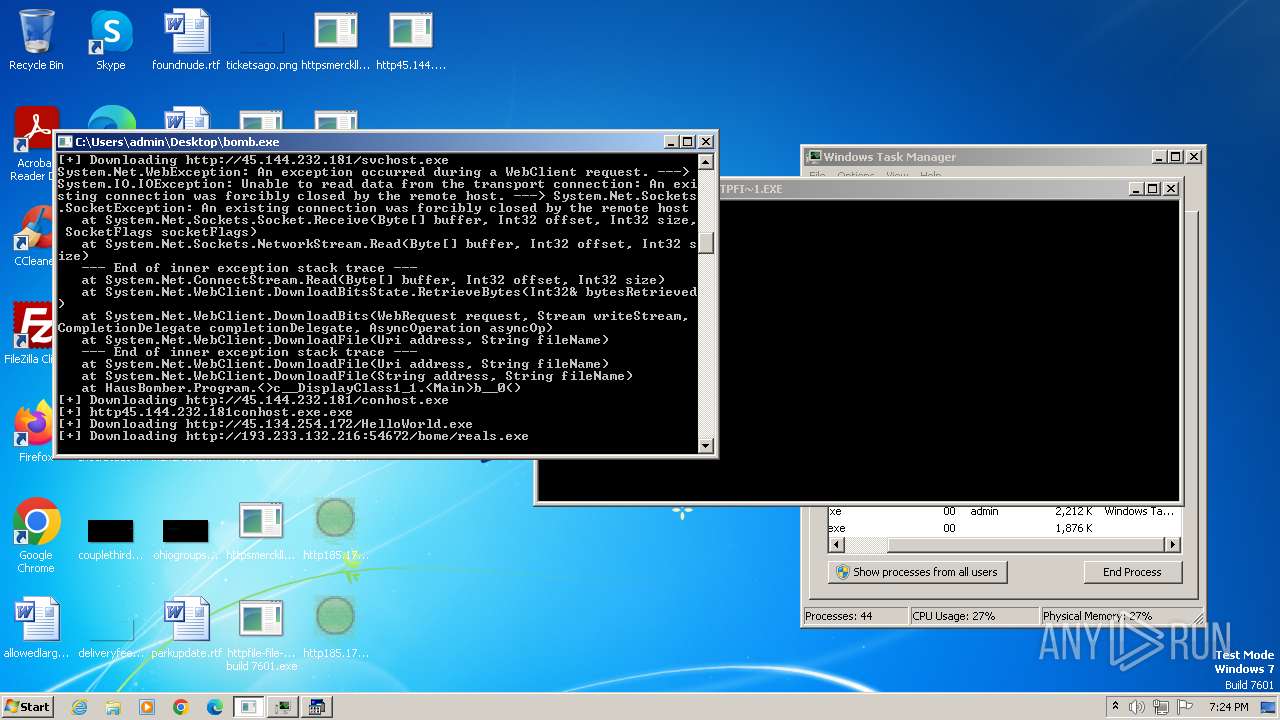
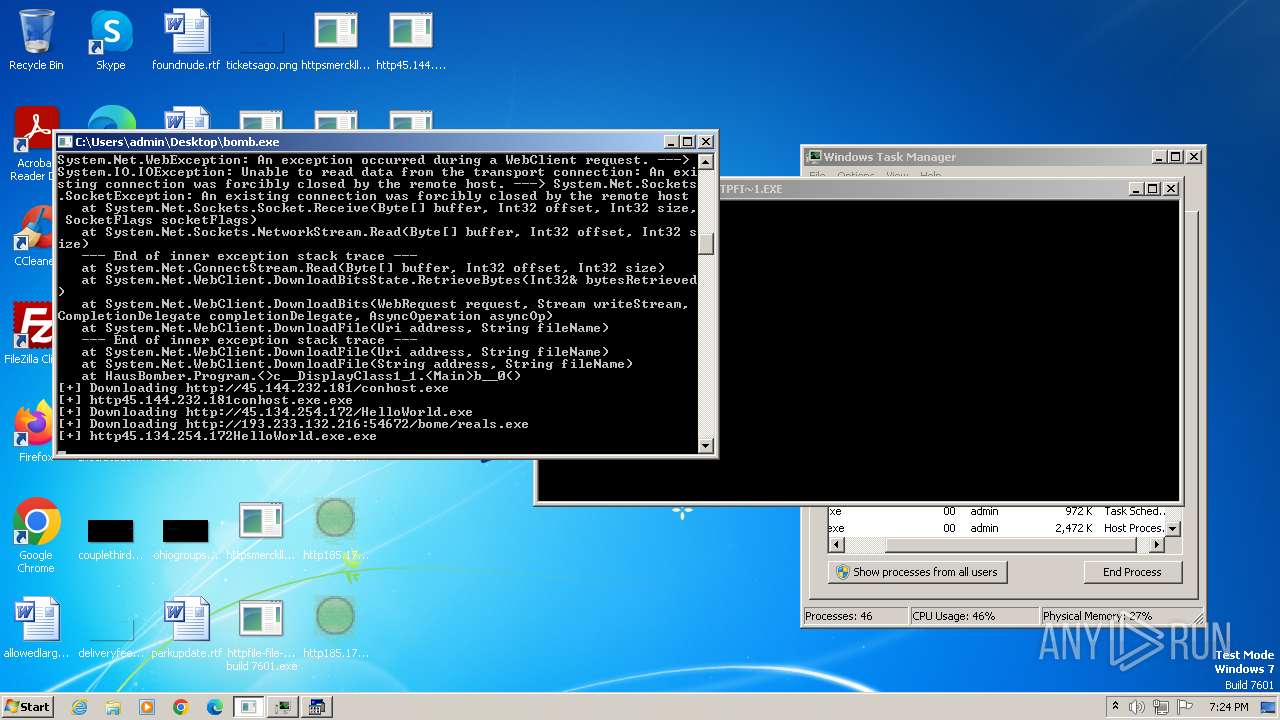
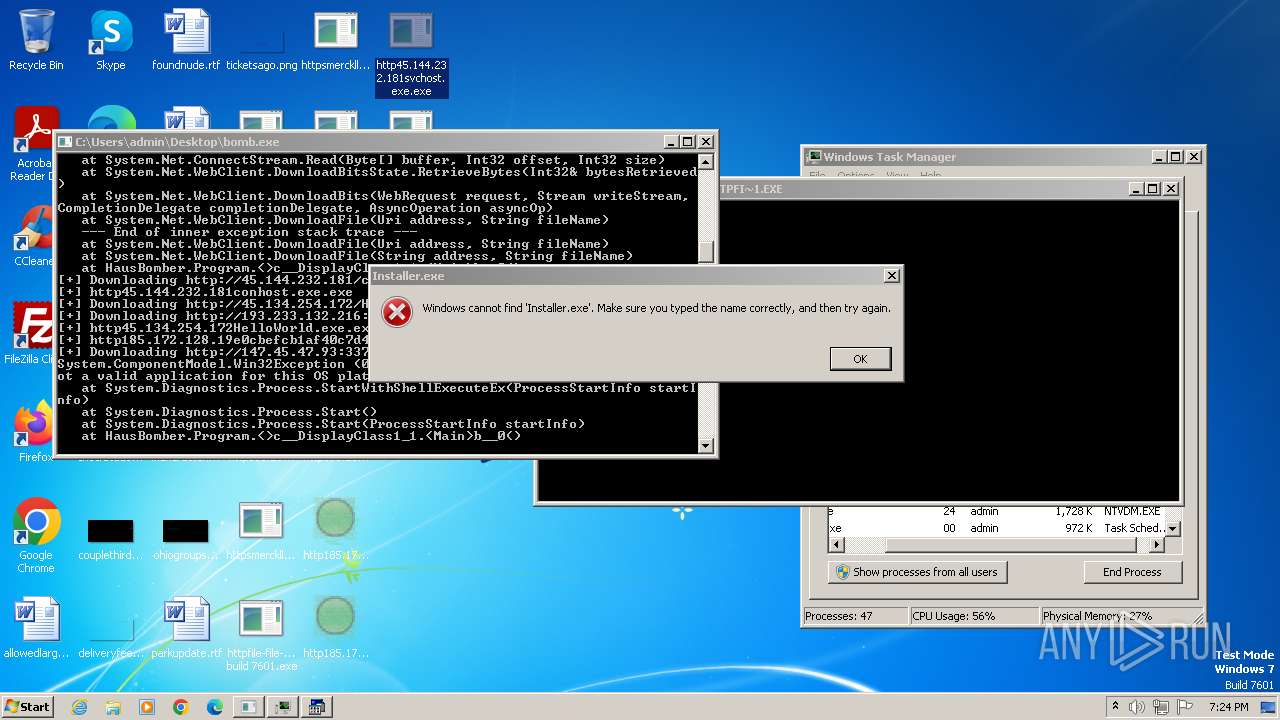
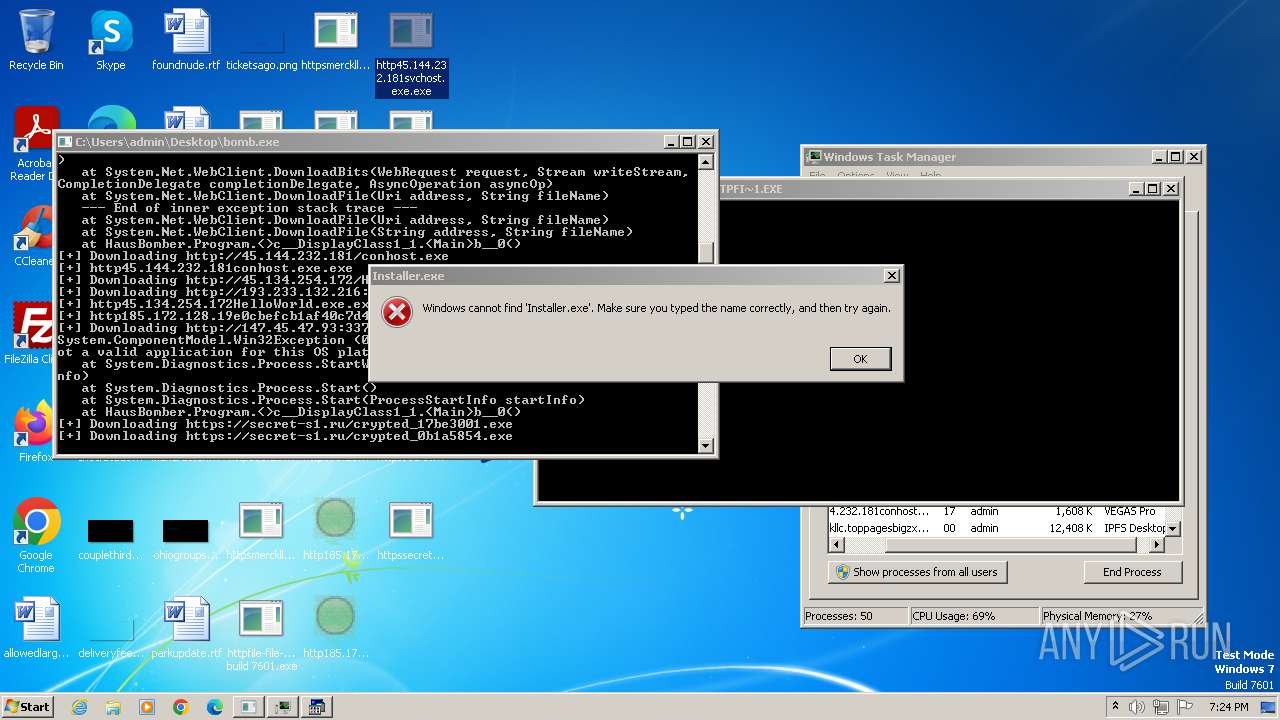
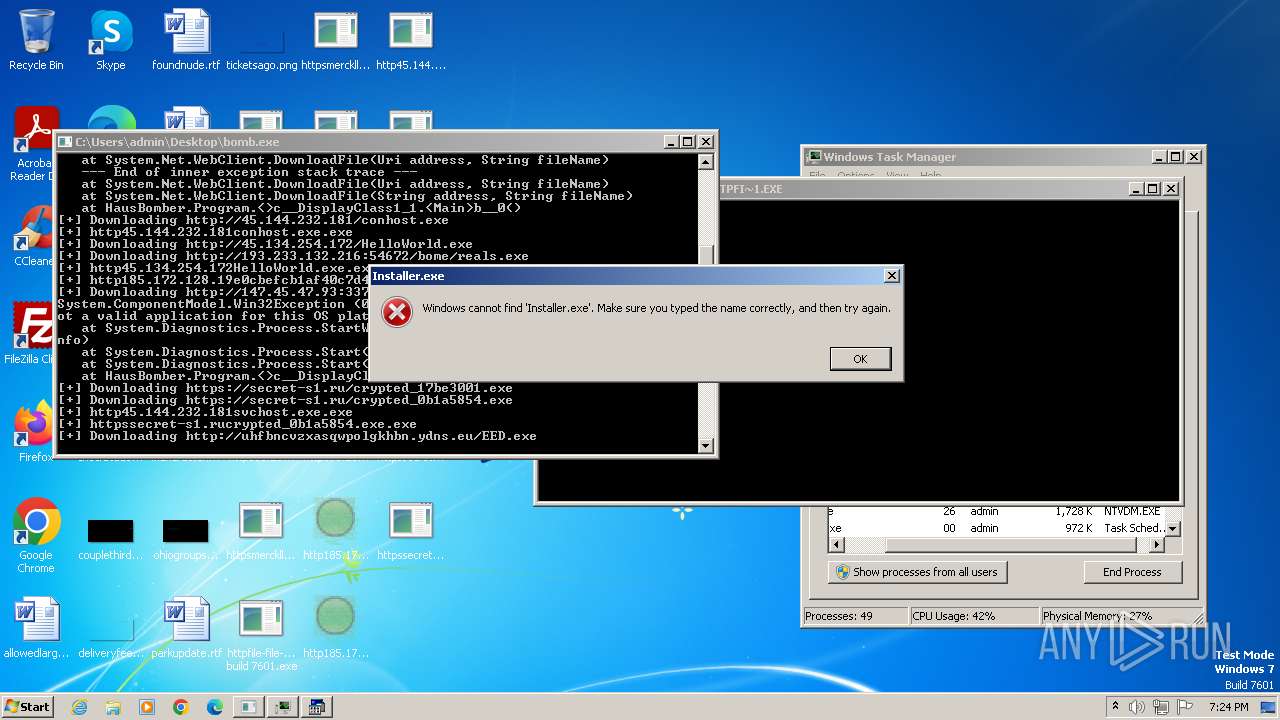
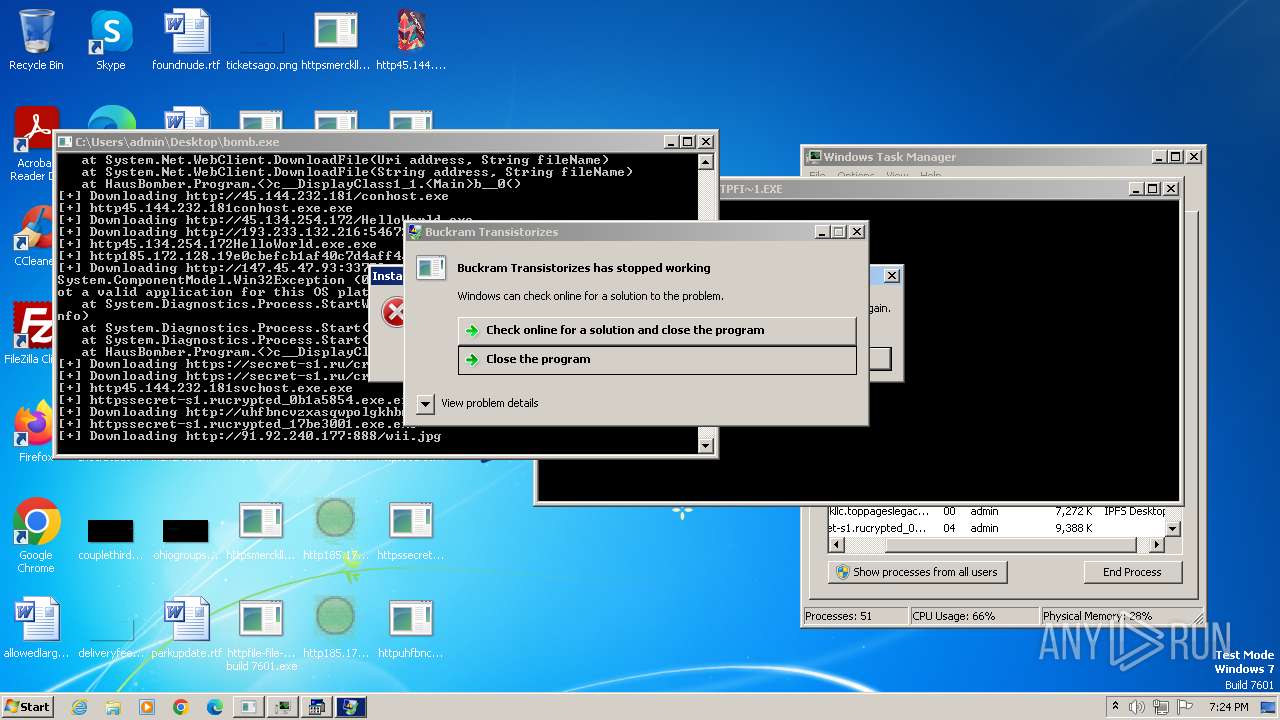
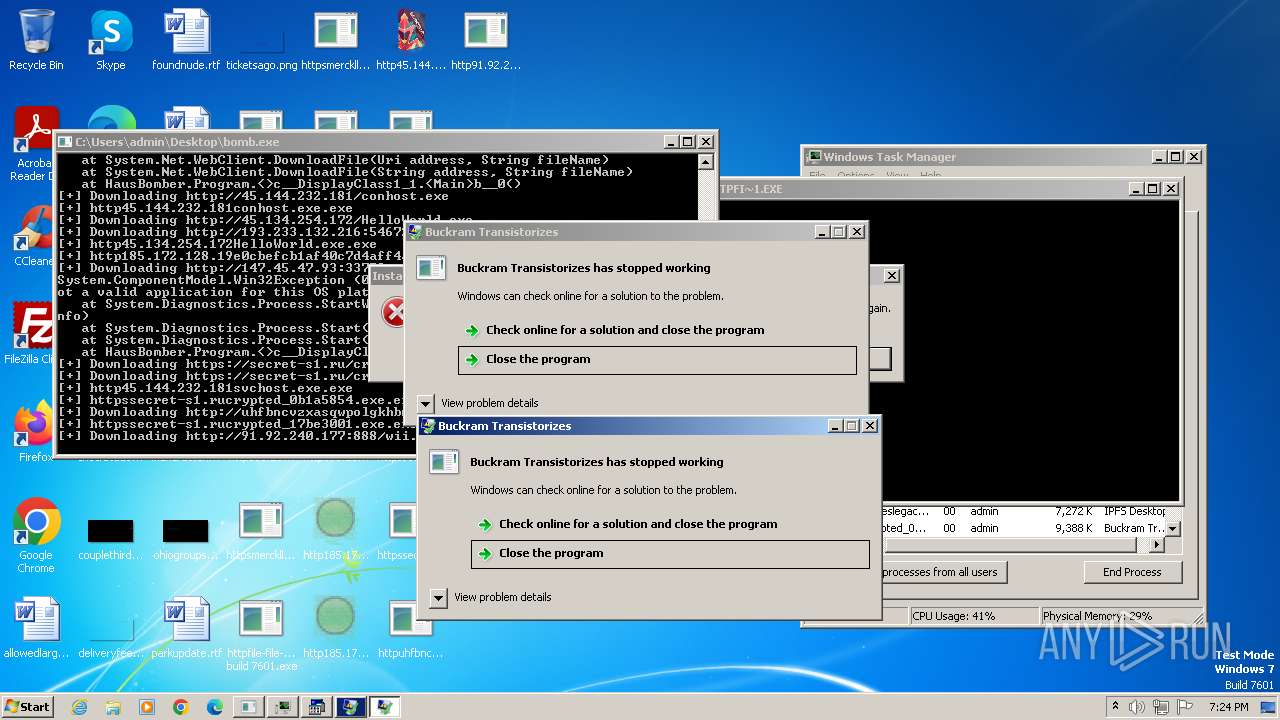
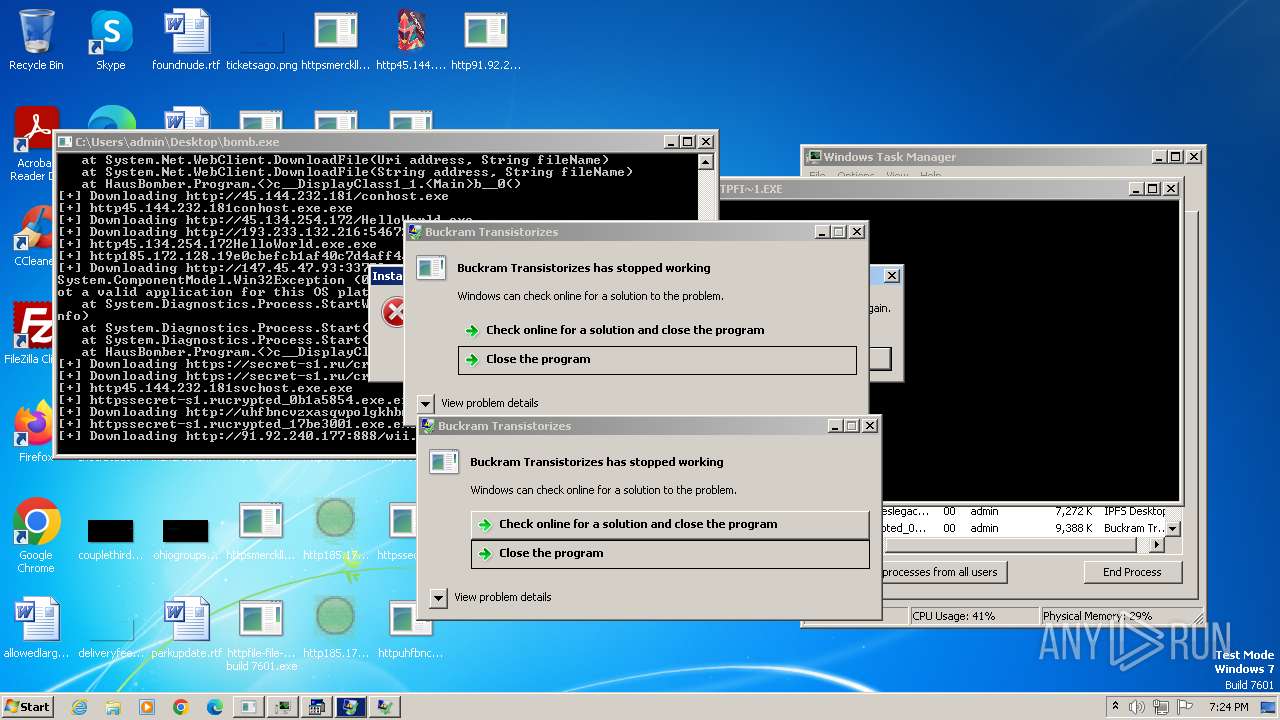
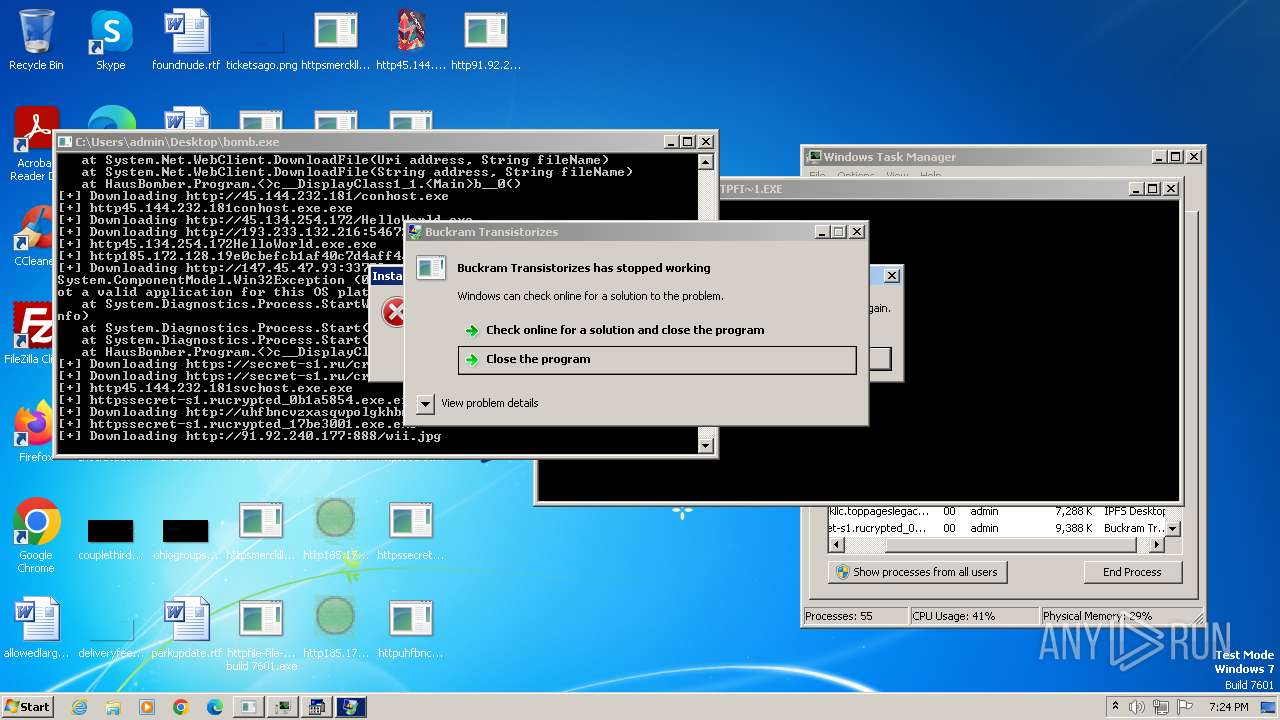
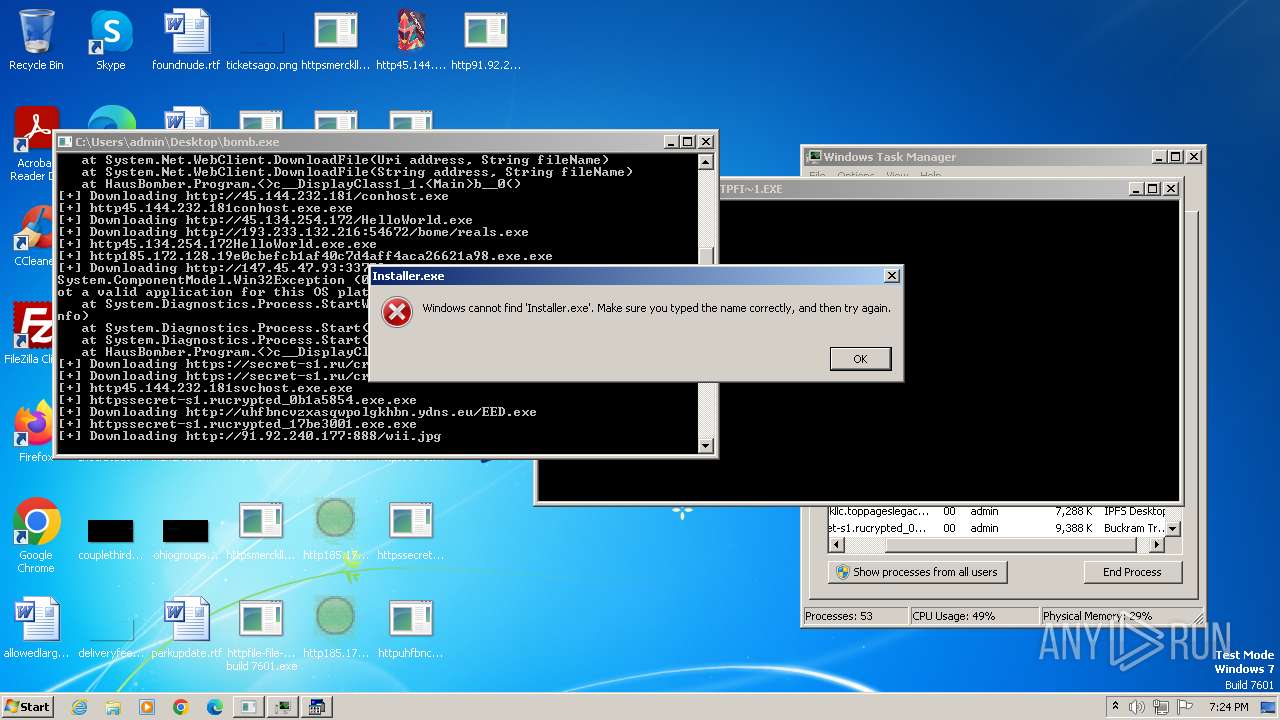
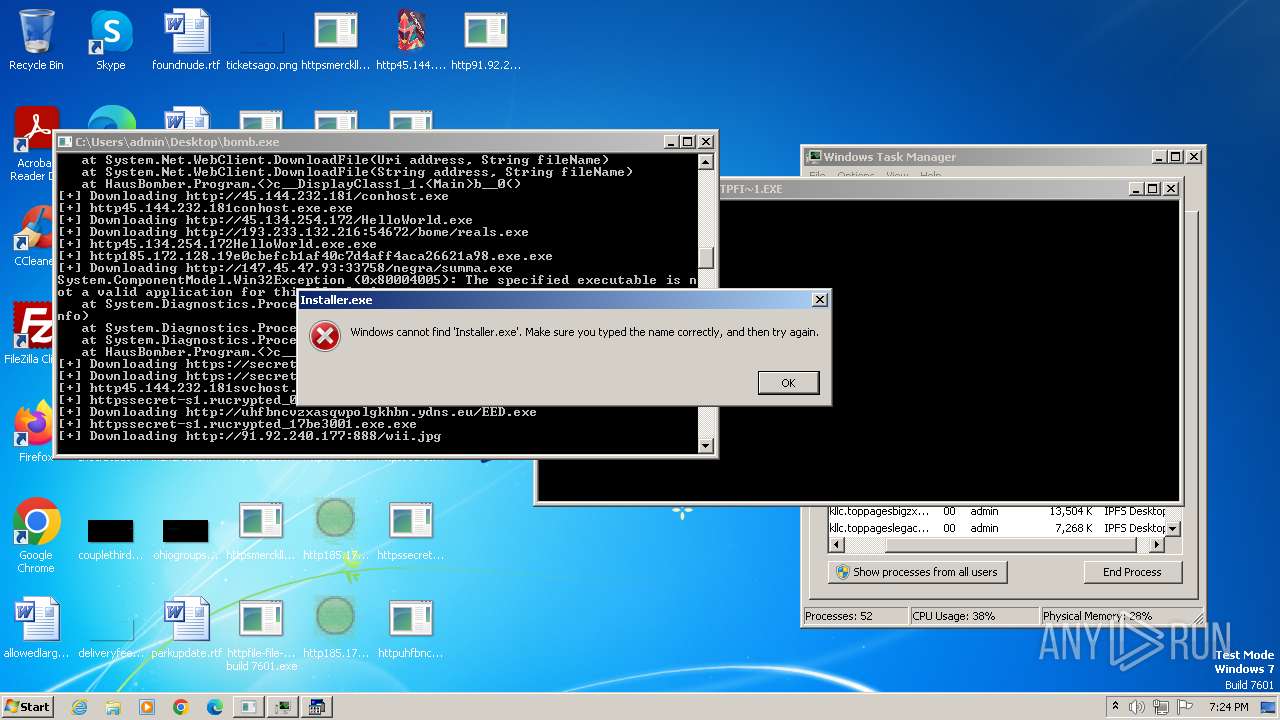
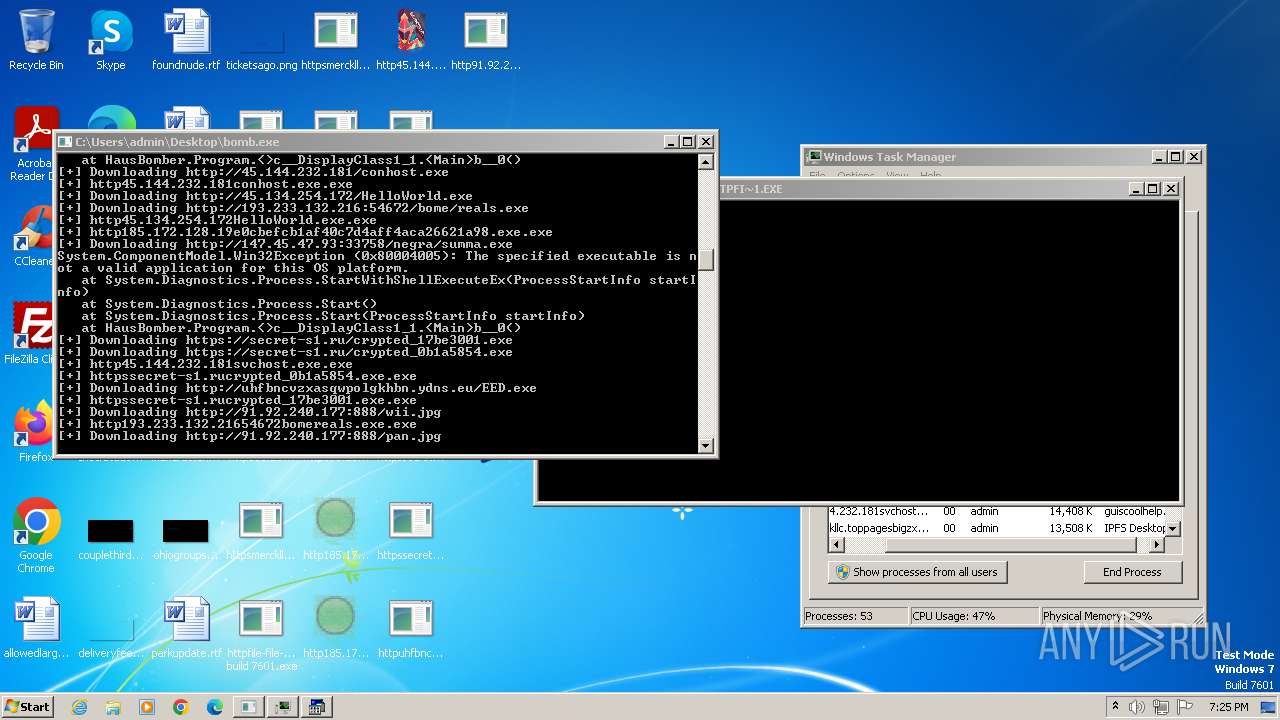
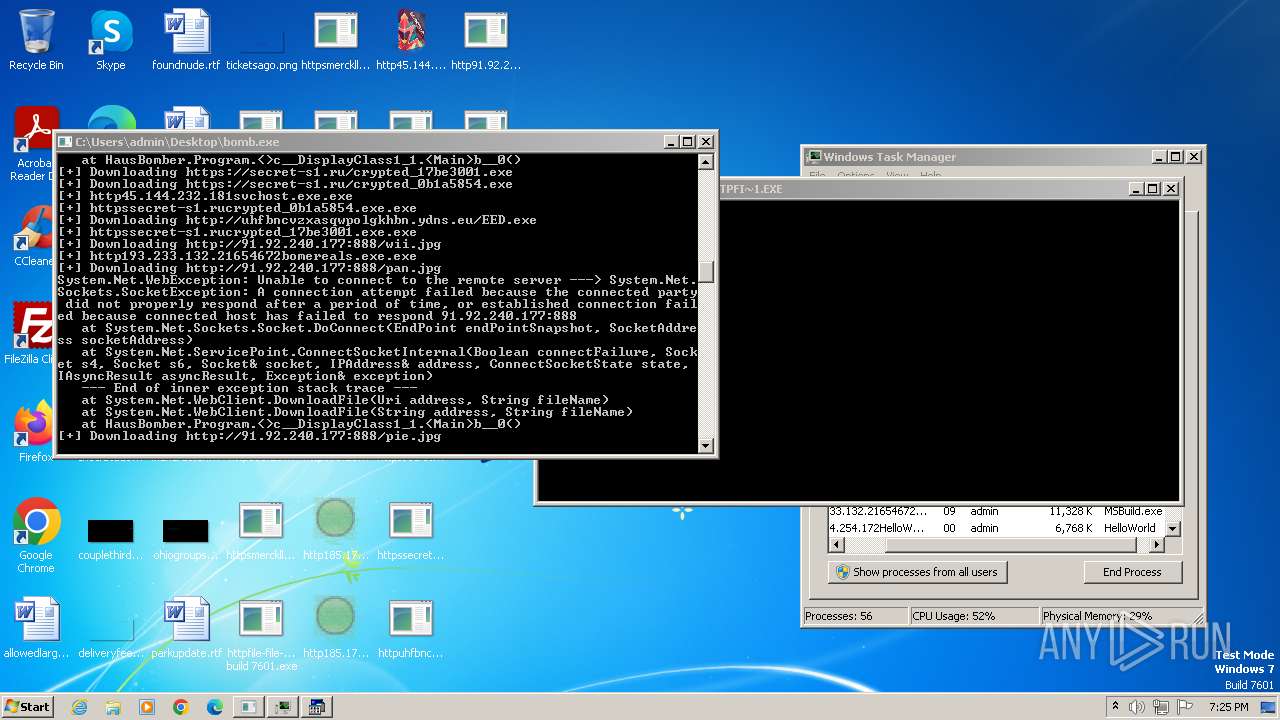
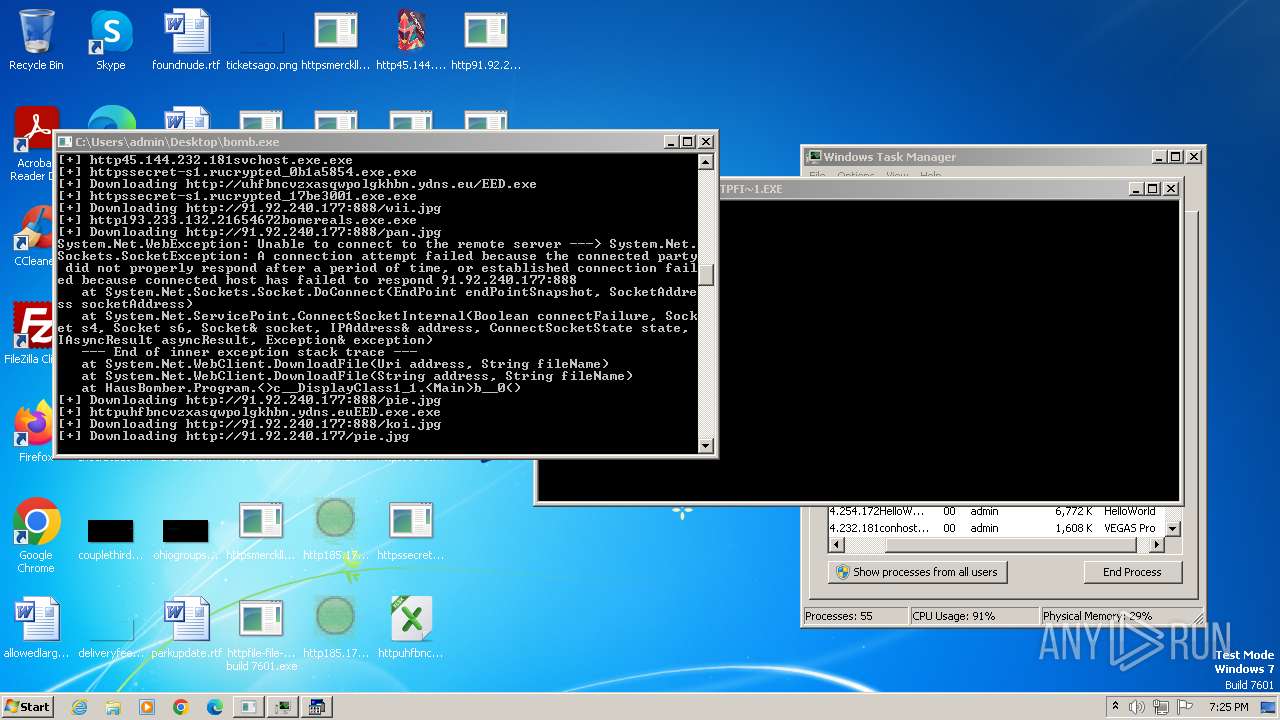
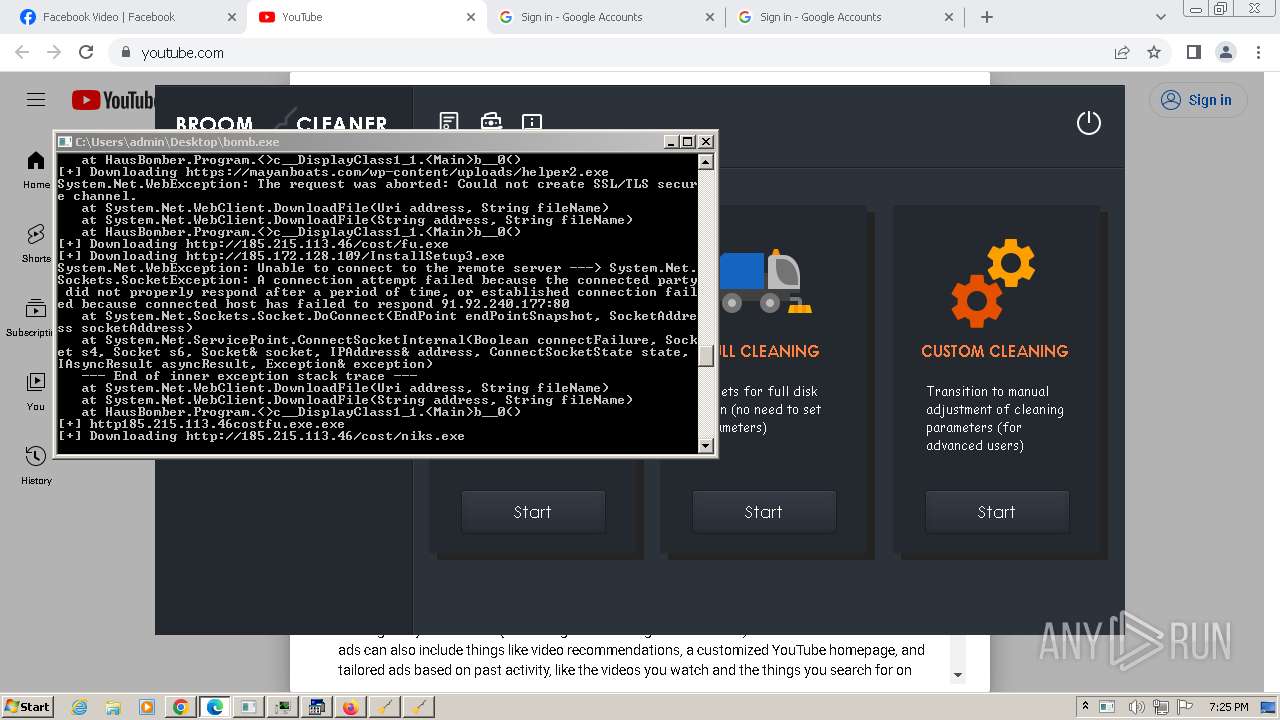
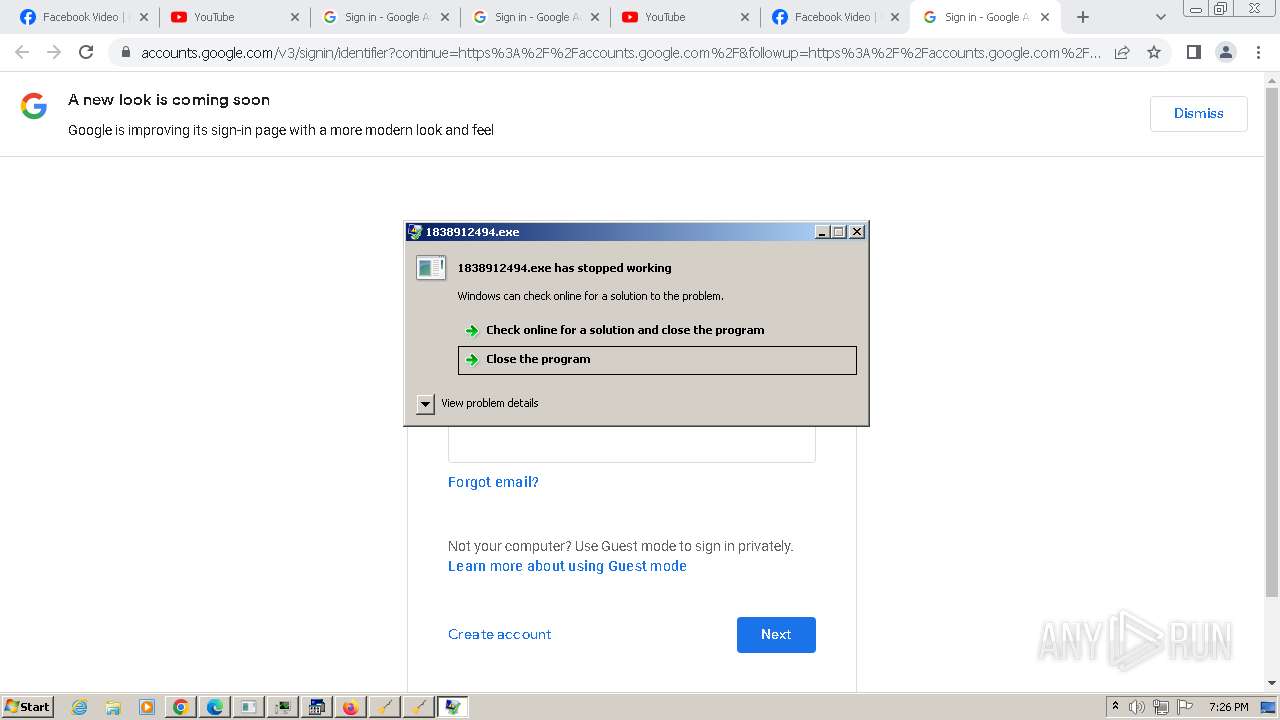
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/99f8cef9-7e0e-4542-b65f-73be2df4e84b |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 20, 2024, 19:21:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 55DBA6E7AA4E8CC73415F4E3F9F6BDAE |
| SHA1: | 87C9F29D58F57A5E025061D389BE2655EE879D5D |
| SHA256: | 3CEA805F1396DF15BDBCD4317388A046A41A6079DBA04576A58BA7B2C812338A |
| SSDEEP: | 192:HLmmmmlmtYz0wZick7pDMj4GbCrMz+MCZLa7HhdSbwxz1OLU87glpp/bI6J4yfm4:pmi7k7pMiLLaLhM6OLU870NJqoI |
MALICIOUS
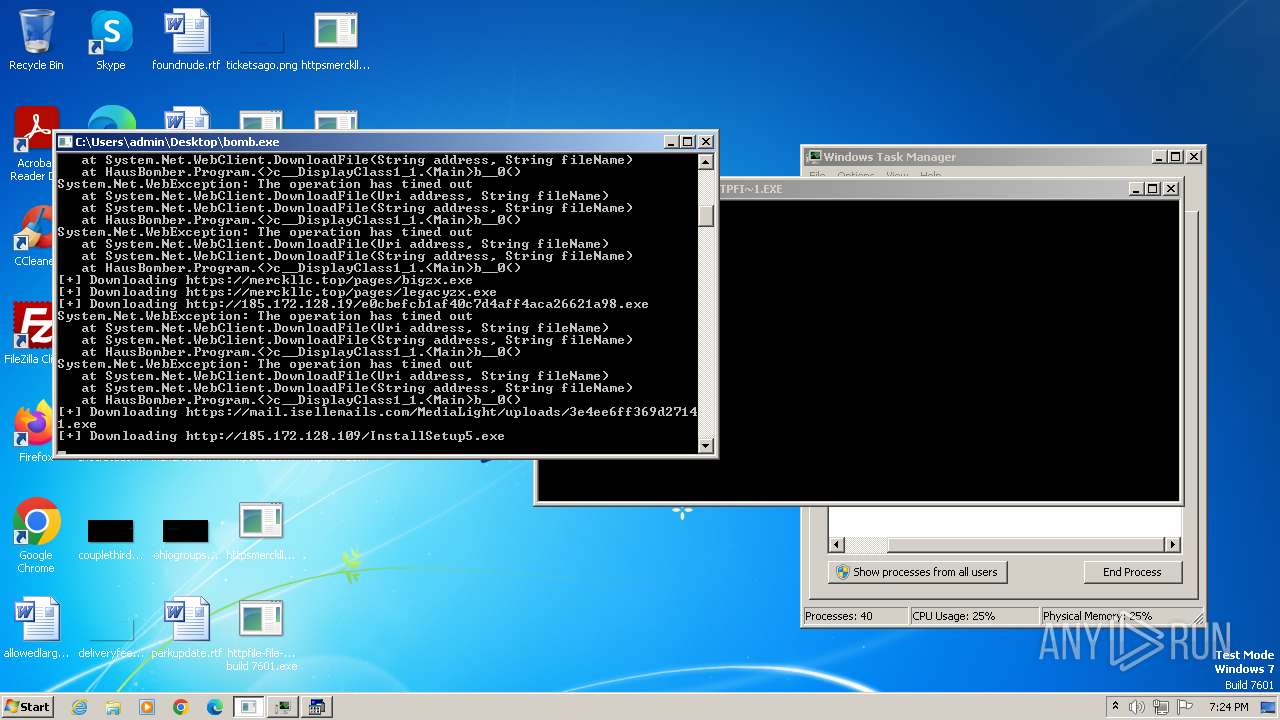
Drops the executable file immediately after the start
- bomb.exe (PID: 4052)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- http185.215.113.66pei.exe.exe (PID: 3964)
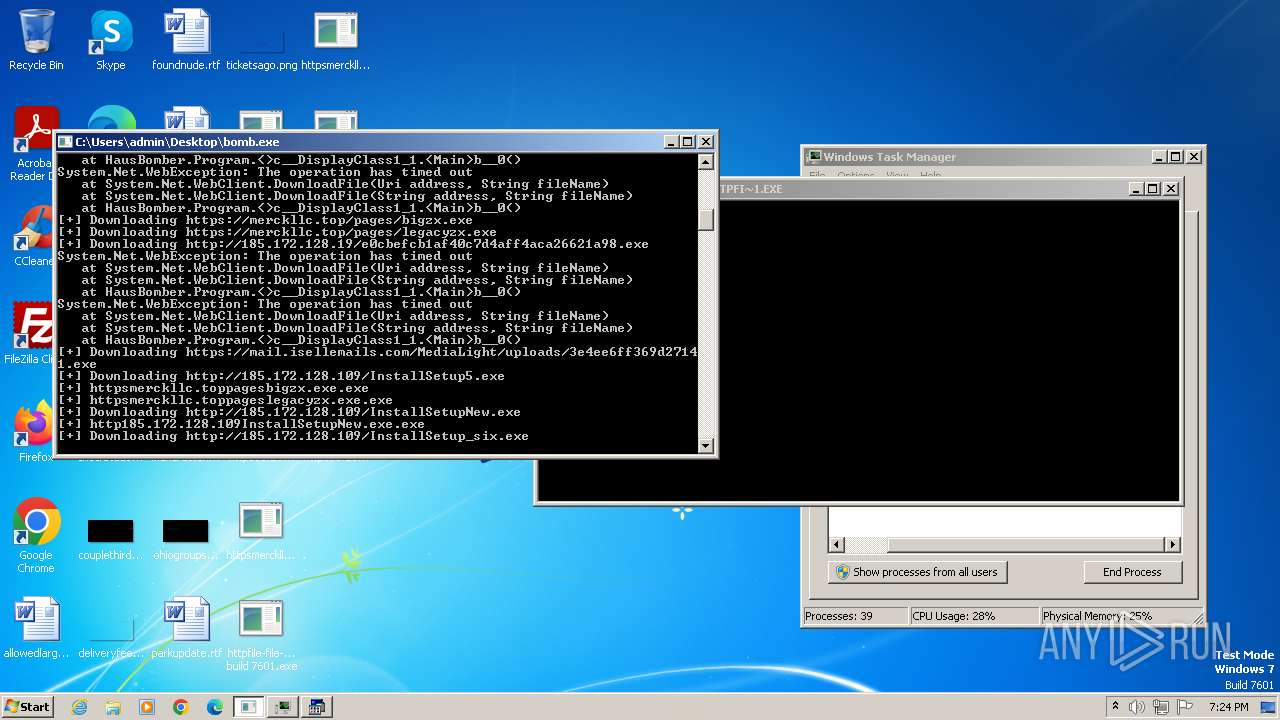
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
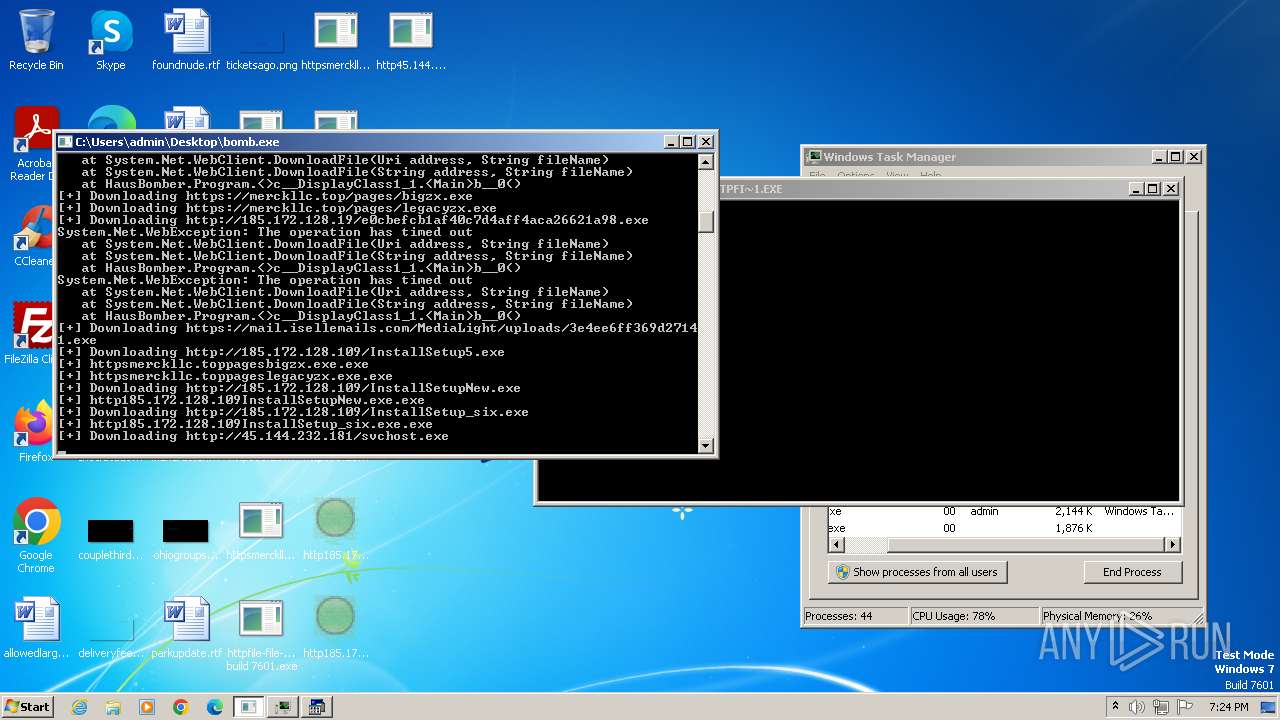
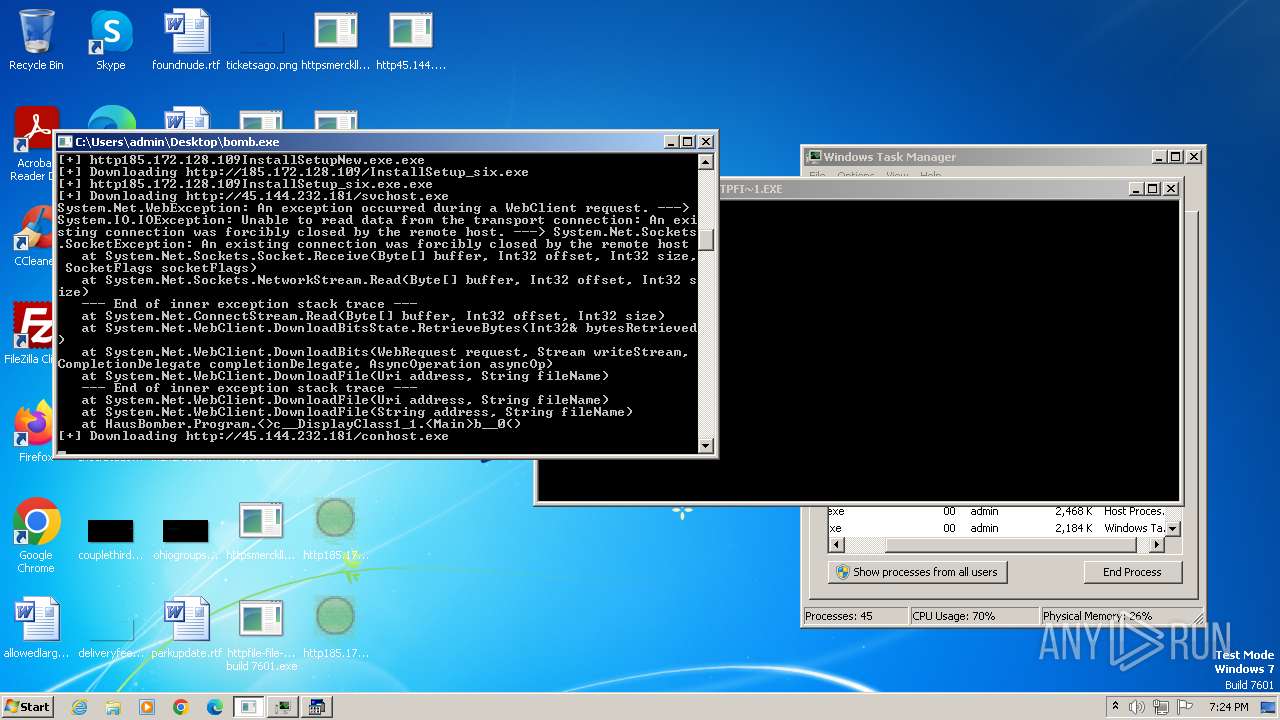
- http45.144.232.181conhost.exe.exe (PID: 3632)
- 468210291.exe (PID: 2960)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- FhrxRWmBqPUtAWZ2i1os.exe (PID: 5992)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
Changes the autorun value in the registry
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- 468210291.exe (PID: 2960)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Connects to the CnC server
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- u30c.0.exe (PID: 2028)
- u354.0.exe (PID: 1408)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- 468210291.exe (PID: 2960)
- nsh2F58.tmp (PID: 6832)
Changes Security Center notification settings
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- 468210291.exe (PID: 2960)
PHORPIEX has been detected (SURICATA)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- bomb.exe (PID: 4052)
- 468210291.exe (PID: 2960)
Actions looks like stealing of personal data
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- RegSvcs.exe (PID: 4560)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 7620)
- RegSvcs.exe (PID: 6960)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Steals credentials from Web Browsers
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- RegSvcs.exe (PID: 4560)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 7620)
- RegSvcs.exe (PID: 8008)
KELIHOS has been detected (SURICATA)
- bomb.exe (PID: 4052)
STEALC has been detected (SURICATA)
- u354.0.exe (PID: 1408)
- u30c.0.exe (PID: 2028)
- nsh2F58.tmp (PID: 6832)
NANOCORE has been detected (SURICATA)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
NANOCORE has been detected (YARA)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
Uses Task Scheduler to autorun other applications
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
RISEPRO has been detected (SURICATA)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
Steals credentials
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
AGENTTESLA has been detected (YARA)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- RegSvcs.exe (PID: 4560)
- RegSvcs.exe (PID: 8008)
Create files in the Startup directory
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
RISEPRO has been detected (YARA)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
SUSPICIOUS
Reads settings of System Certificates
- bomb.exe (PID: 4052)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- RegSvcs.exe (PID: 4560)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 7620)
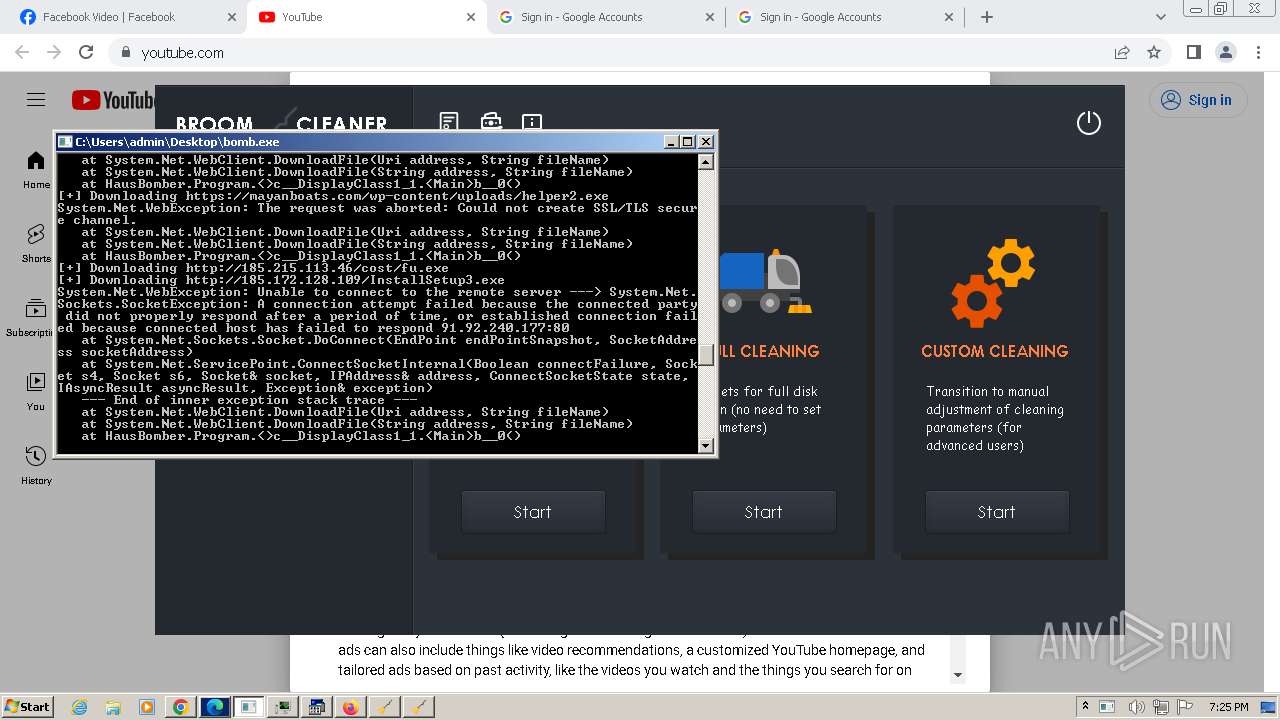
Process requests binary or script from the Internet
- bomb.exe (PID: 4052)
- http185.215.113.66pei.exe.exe (PID: 3964)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
Reads the Internet Settings
- http185.215.113.66pei.exe.exe (PID: 3964)
- bomb.exe (PID: 4052)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- u30c.0.exe (PID: 2028)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- u354.0.exe (PID: 1408)
- http45.134.254.172HelloWorld.exe.exe (PID: 3420)
- http45.144.232.181conhost.exe.exe (PID: 3632)
- cmd.exe (PID: 3700)
- 468210291.exe (PID: 2960)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- CuNfylgNalAX7EHVWHu8.exe (PID: 1796)
- RegSvcs.exe (PID: 4560)
- hCbz_rkhHD8grJmG1Wxk.exe (PID: 6420)
- http185.215.113.46costfu.exe.exe (PID: 5532)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- nsh2F58.tmp (PID: 6832)
Connects to the server without a host name
- bomb.exe (PID: 4052)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- nsh2F58.tmp (PID: 6832)
Executable content was dropped or overwritten
- bomb.exe (PID: 4052)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- http185.215.113.66pei.exe.exe (PID: 3964)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- http45.144.232.181conhost.exe.exe (PID: 3632)
- 468210291.exe (PID: 2960)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- FhrxRWmBqPUtAWZ2i1os.exe (PID: 5992)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
Reads security settings of Internet Explorer
- bomb.exe (PID: 4052)
- http185.215.113.66pei.exe.exe (PID: 3964)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- u30c.0.exe (PID: 2028)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- u354.0.exe (PID: 1408)
- http45.144.232.181conhost.exe.exe (PID: 3632)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- CuNfylgNalAX7EHVWHu8.exe (PID: 1796)
- hCbz_rkhHD8grJmG1Wxk.exe (PID: 6420)
- http185.215.113.46costfu.exe.exe (PID: 5532)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- nsh2F58.tmp (PID: 6832)
Application launched itself
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2404)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 2376)
The process creates files with name similar to system file names
- bomb.exe (PID: 4052)
Connects to unusual port
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- bomb.exe (PID: 4052)
- http45.134.254.172HelloWorld.exe.exe (PID: 3420)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- 468210291.exe (PID: 2960)
Accesses Microsoft Outlook profiles
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- RegSvcs.exe (PID: 4560)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 7620)
Windows Defender mutex has been found
- u30c.0.exe (PID: 2028)
- u354.0.exe (PID: 1408)
- nsh2F58.tmp (PID: 6832)
Connects to SMTP port
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- RegSvcs.exe (PID: 4560)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 7620)
Starts CMD.EXE for commands execution
- http45.144.232.181conhost.exe.exe (PID: 3632)
- u30c.1.exe (PID: 1344)
- u354.1.exe (PID: 996)
- BroomSetup.exe (PID: 7364)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3700)
Drops 7-zip archiver for unpacking
- http45.144.232.181conhost.exe.exe (PID: 3632)
Executing commands from a ".bat" file
- http45.144.232.181conhost.exe.exe (PID: 3632)
- u30c.1.exe (PID: 1344)
- u354.1.exe (PID: 996)
- BroomSetup.exe (PID: 7364)
Process drops legitimate windows executable
- bomb.exe (PID: 4052)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Reads the BIOS version
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- FhrxRWmBqPUtAWZ2i1os.exe (PID: 5992)
- NwdWg5ByPM0EfEapgjWT.exe (PID: 2928)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- http185.215.113.46costniks.exe.exe (PID: 8044)
Starts a Microsoft application from unusual location
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Starts itself from another location
- 468210291.exe (PID: 2960)
Checks for external IP
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
Reads browser cookies
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Adds/modifies Windows certificates
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
Searches for installed software
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Starts application with an unusual extension
- cmd.exe (PID: 7540)
- cmd.exe (PID: 7448)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- cmd.exe (PID: 1932)
Checks Windows Trust Settings
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
INFO
Manual execution by a user
- taskmgr.exe (PID: 2752)
Reads the computer name
- bomb.exe (PID: 4052)
- http185.215.113.66pei.exe.exe (PID: 3964)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2404)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 2376)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- u30c.0.exe (PID: 2028)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- u354.0.exe (PID: 1408)
- http45.134.254.172HelloWorld.exe.exe (PID: 3420)
- http45.144.232.181conhost.exe.exe (PID: 3632)
- http185.172.128.19e0cbefcb1af40c7d4aff4aca26621a98.exe.exe (PID: 3924)
- u30c.1.exe (PID: 1344)
- u354.1.exe (PID: 996)
- http45.144.232.181svchost.exe.exe (PID: 2628)
- httpssecret-s1.rucrypted_17be3001.exe.exe (PID: 3844)
- httpssecret-s1.rucrypted_0b1a5854.exe.exe (PID: 4048)
- 468210291.exe (PID: 2960)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- 230629444.exe (PID: 1852)
- CuNfylgNalAX7EHVWHu8.exe (PID: 1796)
- RegSvcs.exe (PID: 4560)
- FhrxRWmBqPUtAWZ2i1os.exe (PID: 5992)
- NwdWg5ByPM0EfEapgjWT.exe (PID: 2928)
- hCbz_rkhHD8grJmG1Wxk.exe (PID: 6420)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- http185.215.113.46costfu.exe.exe (PID: 5532)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- BroomSetup.exe (PID: 7364)
- http185.215.113.46costniks.exe.exe (PID: 8044)
- nsh2F58.tmp (PID: 6832)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 7620)
Reads Environment values
- bomb.exe (PID: 4052)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- http45.134.254.172HelloWorld.exe.exe (PID: 3420)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- RegSvcs.exe (PID: 4560)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 7620)
Reads the software policy settings
- bomb.exe (PID: 4052)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- RegSvcs.exe (PID: 4560)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 7620)
Checks supported languages
- bomb.exe (PID: 4052)
- http185.215.113.66pei.exe.exe (PID: 3964)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- 1111224825.exe (PID: 3984)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2404)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 2376)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- u30c.0.exe (PID: 2028)
- u354.0.exe (PID: 1408)
- http45.144.232.181conhost.exe.exe (PID: 3632)
- http45.134.254.172HelloWorld.exe.exe (PID: 3420)
- http185.172.128.19e0cbefcb1af40c7d4aff4aca26621a98.exe.exe (PID: 3924)
- mode.com (PID: 2356)
- u30c.1.exe (PID: 1344)
- u354.1.exe (PID: 996)
- httpssecret-s1.rucrypted_17be3001.exe.exe (PID: 3844)
- httpssecret-s1.rucrypted_0b1a5854.exe.exe (PID: 4048)
- 468210291.exe (PID: 2960)
- http45.144.232.181svchost.exe.exe (PID: 2628)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- 1217027251.exe (PID: 4000)
- httpuhfbncvzxasqwpolgkhbn.ydns.euEED.exe.exe (PID: 1836)
- CuNfylgNalAX7EHVWHu8.exe (PID: 1796)
- RegSvcs.exe (PID: 4560)
- 2120817444.exe (PID: 5632)
- FhrxRWmBqPUtAWZ2i1os.exe (PID: 5992)
- NwdWg5ByPM0EfEapgjWT.exe (PID: 2928)
- hCbz_rkhHD8grJmG1Wxk.exe (PID: 6420)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- chcp.com (PID: 7488)
- chcp.com (PID: 7564)
- http185.215.113.46costfu.exe.exe (PID: 5532)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- BroomSetup.exe (PID: 7364)
- 1838912494.exe (PID: 5804)
- nsh2F58.tmp (PID: 6832)
- http185.215.113.46costniks.exe.exe (PID: 8044)
- chcp.com (PID: 1336)
- httpsmail.isellemails.comMediaLightuploadsb3edefeeca7bf5e33.exe.exe (PID: 6988)
- RegSvcs.exe (PID: 8008)
- httpsmail.isellemails.comMediaLightuploads83c276d11d7b72505.exe.exe (PID: 2104)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 7620)
- httpsmail.isellemails.comMediaLightuploads1c4633665c468d043.exe.exe (PID: 6636)
Reads the machine GUID from the registry
- bomb.exe (PID: 4052)
- http185.215.113.66pei.exe.exe (PID: 3964)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2404)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 2376)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- httpsmerckllc.toppageslegacyzx.exe.exe (PID: 920)
- u30c.0.exe (PID: 2028)
- u354.0.exe (PID: 1408)
- http45.134.254.172HelloWorld.exe.exe (PID: 3420)
- http185.172.128.19e0cbefcb1af40c7d4aff4aca26621a98.exe.exe (PID: 3924)
- http45.144.232.181svchost.exe.exe (PID: 2628)
- httpssecret-s1.rucrypted_0b1a5854.exe.exe (PID: 4048)
- httpssecret-s1.rucrypted_17be3001.exe.exe (PID: 3844)
- 230629444.exe (PID: 1852)
- 468210291.exe (PID: 2960)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- RegSvcs.exe (PID: 4560)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- nsh2F58.tmp (PID: 6832)
- RegSvcs.exe (PID: 6960)
- RegSvcs.exe (PID: 8008)
- RegSvcs.exe (PID: 7620)
Checks proxy server information
- http185.215.113.66pei.exe.exe (PID: 3964)
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- u30c.0.exe (PID: 2028)
- u354.0.exe (PID: 1408)
- 468210291.exe (PID: 2960)
- 230629444.exe (PID: 1852)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- nsh2F58.tmp (PID: 6832)
Creates files or folders in the user directory
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- http185.215.113.66pei.exe.exe (PID: 3964)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- u30c.1.exe (PID: 1344)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
Create files in a temporary directory
- http185.215.113.66newtpp.exe.exe (PID: 2892)
- http185.215.113.66pei.exe.exe (PID: 3964)
- http185.172.128.109InstallSetup_six.exe.exe (PID: 4072)
- bomb.exe (PID: 4052)
- http185.172.128.109InstallSetupNew.exe.exe (PID: 3900)
- http45.144.232.181conhost.exe.exe (PID: 3632)
- 468210291.exe (PID: 2960)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
- httpuhfbncvzxasqwpolgkhbn.ydns.euEED.exe.exe (PID: 1836)
- FhrxRWmBqPUtAWZ2i1os.exe (PID: 5992)
- Sm9IoqrusX_sqXySlHUL.exe (PID: 7148)
- qJ5_pcw3gR_qjNC4lAml.exe (PID: 7336)
- http185.172.128.109InstallSetup3.exe.exe (PID: 292)
- httpsmail.isellemails.comMediaLightuploadsb3edefeeca7bf5e33.exe.exe (PID: 6988)
- httpsmail.isellemails.comMediaLightuploads83c276d11d7b72505.exe.exe (PID: 2104)
- httpsmail.isellemails.comMediaLightuploads1c4633665c468d043.exe.exe (PID: 6636)
Process checks whether UAC notifications are on
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
Reads product name
- httpsmerckllc.toppagesbigzx.exe.exe (PID: 2480)
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Reads CPU info
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
Reads mouse settings
- httpuhfbncvzxasqwpolgkhbn.ydns.euEED.exe.exe (PID: 1836)
- CuNfylgNalAX7EHVWHu8.exe (PID: 1796)
- hCbz_rkhHD8grJmG1Wxk.exe (PID: 6420)
- http185.215.113.46costfu.exe.exe (PID: 5532)
- httpsmail.isellemails.comMediaLightuploadsb3edefeeca7bf5e33.exe.exe (PID: 6988)
- httpsmail.isellemails.comMediaLightuploads83c276d11d7b72505.exe.exe (PID: 2104)
- httpsmail.isellemails.comMediaLightuploads1c4633665c468d043.exe.exe (PID: 6636)
Application launched itself
- msedge.exe (PID: 3036)
- msedge.exe (PID: 2568)
- msedge.exe (PID: 124)
- msedge.exe (PID: 2584)
- msedge.exe (PID: 3440)
- msedge.exe (PID: 752)
- msedge.exe (PID: 3636)
- chrome.exe (PID: 3868)
- chrome.exe (PID: 2656)
- firefox.exe (PID: 1832)
- firefox.exe (PID: 3272)
- firefox.exe (PID: 3604)
- chrome.exe (PID: 3896)
- firefox.exe (PID: 4208)
- chrome.exe (PID: 6768)
- msedge.exe (PID: 2380)
- msedge.exe (PID: 2916)
- msedge.exe (PID: 4520)
- msedge.exe (PID: 3436)
- msedge.exe (PID: 4884)
- msedge.exe (PID: 3200)
- chrome.exe (PID: 1168)
- firefox.exe (PID: 7448)
- firefox.exe (PID: 6424)
- firefox.exe (PID: 7824)
- chrome.exe (PID: 7348)
- chrome.exe (PID: 7472)
Creates files in the program directory
- http193.233.132.21654672bomereals.exe.exe (PID: 2096)
The process uses the downloaded file
- chrome.exe (PID: 5576)
- chrome.exe (PID: 1044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Nanocore
(PID) Process(2480) httpsmerckllc.toppagesbigzx.exe.exe
KeyboardLoggingTrue
BuildTime2024-02-12 21:33:34.835016
Version1.2.2.0
Mutexfbf9faaf-f2bf-43ae-91ec-07031d9e9f20
DefaultGroupNEW JOY
PrimaryConnectionHosttzitziklishop3.ddns.net
BackupConnectionHosttzitziklishop3.ddns.net
ConnectionPort1663
RunOnStartupTrue
RequestElevationFalse
BypassUserAccountControlTrue
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
AgentTesla
(PID) Process(920) httpsmerckllc.toppageslegacyzx.exe.exe
Protocolsmtp
Hostcp8nl.hyperhost.ua
Port587
Usernamelegacylog@fibraunollc.top
Password7213575aceACE@#$
(PID) Process(4560) RegSvcs.exe
Protocolsmtp
Hostmail.awelleh3.top
Port587
Usernameservereric33@awelleh3.top
Password54x%ex3wbV$1
(PID) Process(8008) RegSvcs.exe
Protocolsmtp
Hostmail.worlorderbillions.top
Port587
Usernamesimonsky@worlorderbillions.top
Passwordc_V]g4Z*O.;%
RisePro
(PID) Process(2096) http193.233.132.21654672bomereals.exe.exe
C2193.233.132.62
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2048:07:19 19:03:26+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9728 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x457a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
284
Monitored processes
212
Malicious processes
33
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument https://accounts.google.com/ | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | CuNfylgNalAX7EHVWHu8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 292 | "C:\Users\admin\Desktop\http185.172.128.109InstallSetup3.exe.exe" | C:\Users\admin\Desktop\http185.172.128.109InstallSetup3.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" https://accounts.google.com | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | CuNfylgNalAX7EHVWHu8.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 920 | "C:\Users\admin\Desktop\httpsmerckllc.toppageslegacyzx.exe.exe" | C:\Users\admin\Desktop\httpsmerckllc.toppageslegacyzx.exe.exe | httpsmerckllc.toppageslegacyzx.exe.exe | ||||||||||||
User: admin Company: Protocol Labs, Inc. Integrity Level: MEDIUM Description: IPFS Desktop Exit code: 0 Version: 0.30.1.0 Modules
AgentTesla(PID) Process(920) httpsmerckllc.toppageslegacyzx.exe.exe Protocolsmtp Hostcp8nl.hyperhost.ua Port587 Usernamelegacylog@fibraunollc.top Password7213575aceACE@#$ | |||||||||||||||
| 996 | "C:\Users\admin\AppData\Local\Temp\u354.1.exe" | C:\Users\admin\AppData\Local\Temp\u354.1.exe | — | http185.172.128.109InstallSetup_six.exe.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Broom Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3736 --field-trial-handle=1268,i,1501165745835462627,1469687842698894239,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://accounts.google.com | C:\Program Files\Google\Chrome\Application\chrome.exe | — | http185.215.113.46costfu.exe.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --mojo-platform-channel-handle=7960 --field-trial-handle=1400,i,1008537502837809087,10194851078824679173,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1336 | chcp 1251 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1344 | "C:\Users\admin\AppData\Local\Temp\u30c.1.exe" | C:\Users\admin\AppData\Local\Temp\u30c.1.exe | — | http185.172.128.109InstallSetupNew.exe.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Broom Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
129 029
Read events
127 968
Write events
917
Delete events
144
Modification events
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (4052) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
59
Suspicious files
609
Text files
273
Unknown types
440
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | bomb.exe | C:\Users\admin\Desktop\http185.215.113.66pei.exe.exe | executable | |
MD5:62B97CF4C0ABAFEDA36E3FC101A5A022 | SHA256:E172537ADCEE1FCDC8F16C23E43A5AC82C56A0347FA0197C08BE979438A534AB | |||
| 4052 | bomb.exe | C:\Users\admin\Desktop\httpsmerckllc.toppagesbigzx.exe.exe | executable | |
MD5:47FF001C25D1C4F807DBFE0428F3A370 | SHA256:307E36DBFA77C7FE9D4ED5CB61D36A4FADA75E7A2DB52DB3E1DF80D222F768D0 | |||
| 1888 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsC1C.tmp | text | |
MD5:8CF6DDB5AA59B49F34B967CD46F013B6 | SHA256:EE06792197C3E025B84860A72460EAF628C66637685F8C52C5A08A9CC35D376C | |||
| 3964 | http185.215.113.66pei.exe.exe | C:\Users\admin\AppData\Local\Temp\1857813056.exe | executable | |
MD5:91C9157C58C8E8C87D721819A6D0C054 | SHA256:A7D157612744986D6CFE057A5A544A23212111B96750F6E276CDB9B18BD5C5BE | |||
| 2892 | http185.215.113.66newtpp.exe.exe | C:\Users\admin\winxsdrvcsa.exe | executable | |
MD5:BB3D7BD66C92454429A8C78BF64F977B | SHA256:94A66EEA65EDD08CA19BF6DB266058E81714312B6A51892298B461FFD8B90161 | |||
| 2892 | http185.215.113.66newtpp.exe.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\1[1] | binary | |
MD5:BB1927E141203BCAD01B9A072297D1E5 | SHA256:0CBC8D95D04EB29ACE06CF127237E4B0EC0BABBF69DAB7FCBC6EA5BC0D5064F7 | |||
| 2892 | http185.215.113.66newtpp.exe.exe | C:\Users\admin\tbnds.dat | binary | |
MD5:9E14DF9996202F3DE5854EDDCD3E36C8 | SHA256:CAFE78A8271B6E494EEC13AD31DD982221F3627EB9BABE324583AAA1B5BB4E7A | |||
| 2480 | httpsmerckllc.toppagesbigzx.exe.exe | C:\Users\admin\AppData\Roaming\90059C37-1320-41A4-B58D-2B75A9850D2F\TCP Monitor\tcpmon.exe | executable | |
MD5:47FF001C25D1C4F807DBFE0428F3A370 | SHA256:307E36DBFA77C7FE9D4ED5CB61D36A4FADA75E7A2DB52DB3E1DF80D222F768D0 | |||
| 2892 | http185.215.113.66newtpp.exe.exe | C:\Users\admin\AppData\Local\Temp\1584415341.exe | binary | |
MD5:BB1927E141203BCAD01B9A072297D1E5 | SHA256:0CBC8D95D04EB29ACE06CF127237E4B0EC0BABBF69DAB7FCBC6EA5BC0D5064F7 | |||
| 4052 | bomb.exe | C:\Users\admin\Desktop\http185.172.128.109InstallSetupNew.exe.exe | executable | |
MD5:516A9BBD226DDA41E84928755B1DFF4D | SHA256:53D117E063610D5FB756D1BC7C9BD4C293D35E8609FF242E2476CC62036B4768 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
104
TCP/UDP connections
574
DNS requests
360
Threats
368
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pei.exe | unknown | executable | 9.50 Kb | unknown |
4052 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/newtpp.exe | unknown | executable | 79.5 Kb | unknown |
3964 | http185.215.113.66pei.exe.exe | GET | — | 185.215.113.66:80 | http://twizt.net/newtpp.exe | unknown | — | — | unknown |
4052 | bomb.exe | GET | — | 37.1.214.209:80 | http://37.1.214.209/2222/kkk.jpg | unknown | — | — | unknown |
4052 | bomb.exe | GET | — | 193.233.132.18:8081 | http://193.233.132.18:8081/static/crypted_a6dd40e8.exe | unknown | — | — | unknown |
3964 | http185.215.113.66pei.exe.exe | GET | 206 | 185.215.113.66:80 | http://twizt.net/newtpp.exe | unknown | binary | 26.6 Kb | unknown |
2892 | http185.215.113.66newtpp.exe.exe | GET | — | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
2892 | http185.215.113.66newtpp.exe.exe | GET | — | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
3964 | http185.215.113.66pei.exe.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/peinstall.php | unknown | binary | 26.6 Kb | unknown |
3900 | http185.172.128.109InstallSetupNew.exe.exe | GET | 200 | 185.172.128.90:80 | http://185.172.128.90/cpa/ping.php?substr=0&s=ab&sub=0 | unknown | binary | 1 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4052 | bomb.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
4052 | bomb.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
4052 | bomb.exe | 207.246.70.132:80 | — | AS-CHOOPA | US | malicious |
4052 | bomb.exe | 104.21.37.191:443 | rusticironstore.com | CLOUDFLARENET | — | unknown |
4052 | bomb.exe | 137.103.255.230:443 | mail.isellemails.com | ATLANTICBB-JOHNSTOWN | US | unknown |
4052 | bomb.exe | 37.1.214.209:80 | — | HVC-AS | US | unknown |
4052 | bomb.exe | 162.159.134.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
file-file-file1.com |
| unknown |
rusticironstore.com |
| malicious |
mail.isellemails.com |
| unknown |
computersupportexperts.com |
| unknown |
gitea.com |
| unknown |
cdn.discordapp.com |
| shared |
twizt.net |
| unknown |
riseappbucket.s3.ap-southeast-1.amazonaws.com |
| unknown |
www.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4052 | bomb.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 22 |
4052 | bomb.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
4052 | bomb.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
4052 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4052 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4052 | bomb.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
4052 | bomb.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4052 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
4052 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Self-Hosted Git Service Domain in DNS Lookup (gitea .com) |
17 ETPRO signatures available at the full report
Process | Message |
|---|---|
http193.233.132.21654672bomereals.exe.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
http193.233.132.21654672bomereals.exe.exe | gert4634 |
http193.233.132.21654672bomereals.exe.exe | eger 43 634 |
FhrxRWmBqPUtAWZ2i1os.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
NwdWg5ByPM0EfEapgjWT.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
Sm9IoqrusX_sqXySlHUL.exe | erert46456 |
Sm9IoqrusX_sqXySlHUL.exe | reyerreyerreyerreyerreyerreyerreyerreyerreyer |
http193.233.132.21654672bomereals.exe.exe | ret34634734g dfyh y rtdyrtyrty |
qJ5_pcw3gR_qjNC4lAml.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
qJ5_pcw3gR_qjNC4lAml.exe | DevBug OPS |