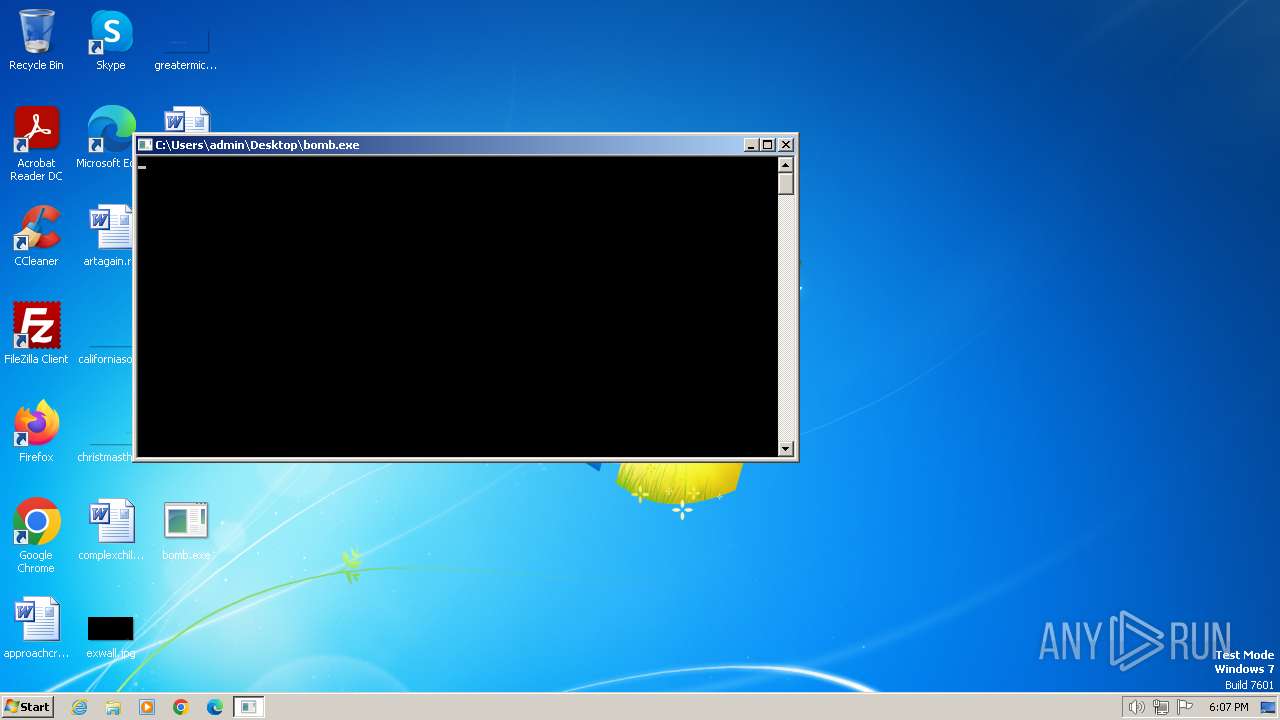
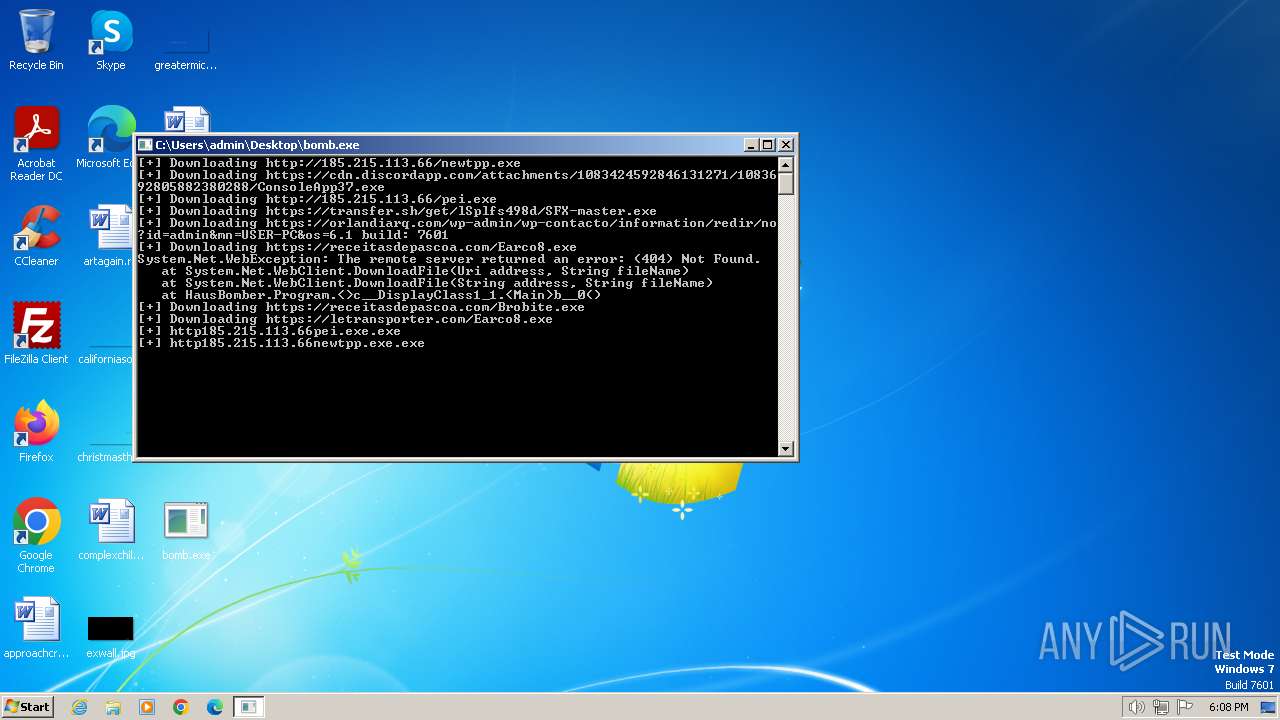
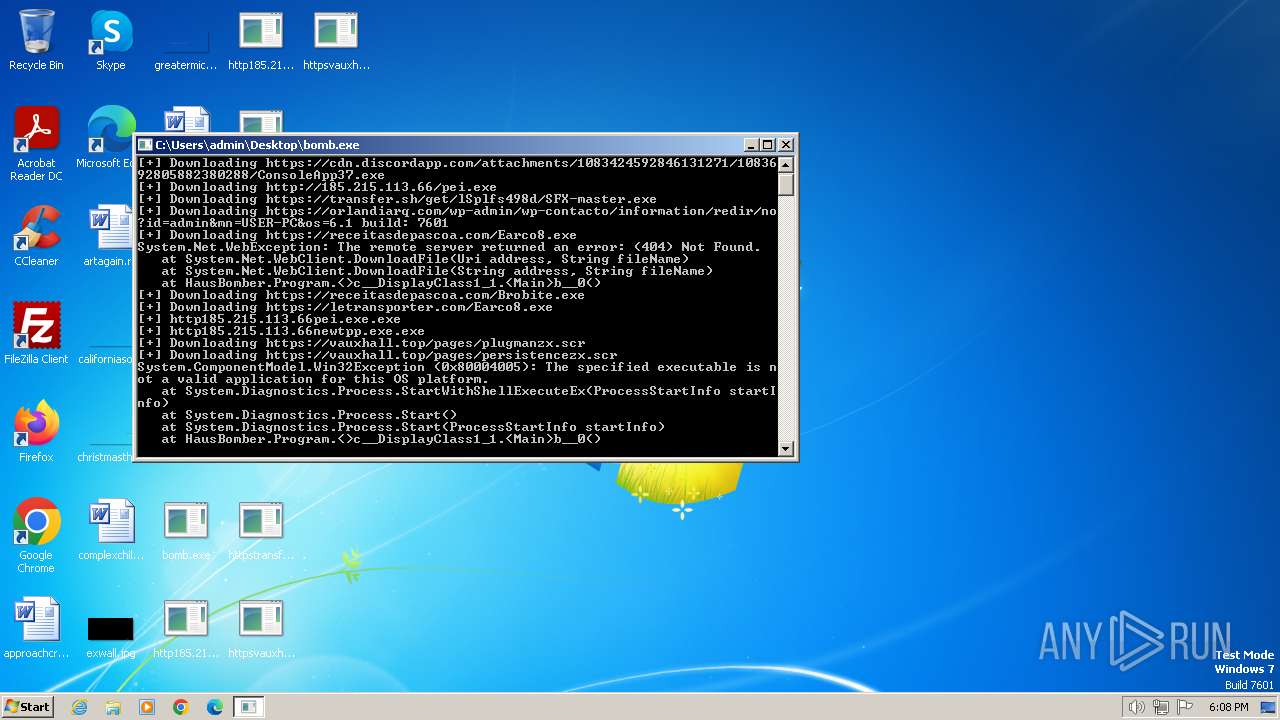
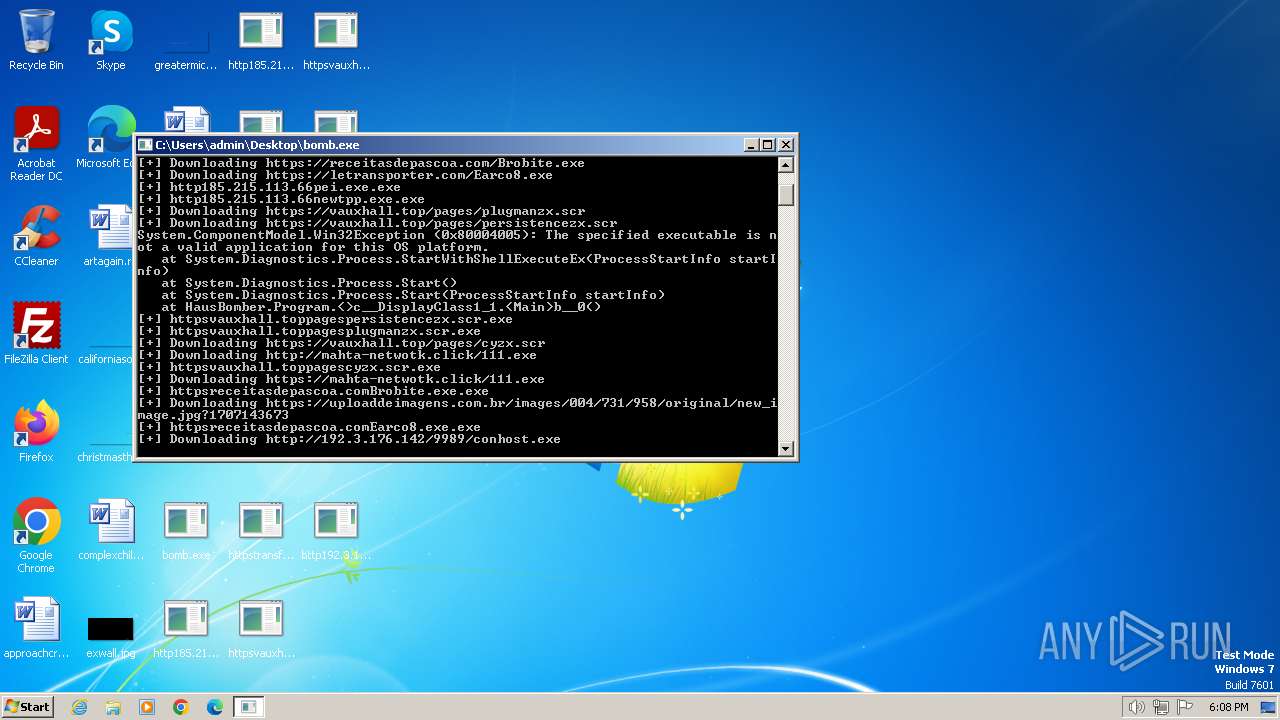
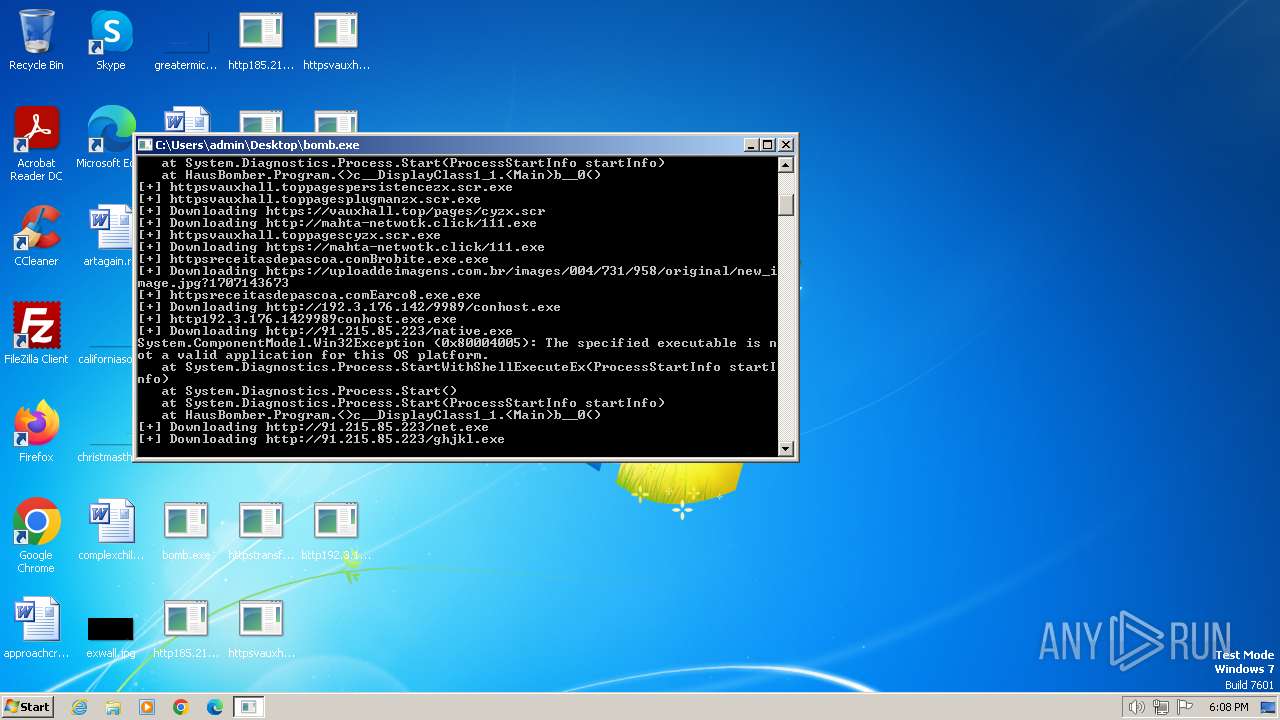
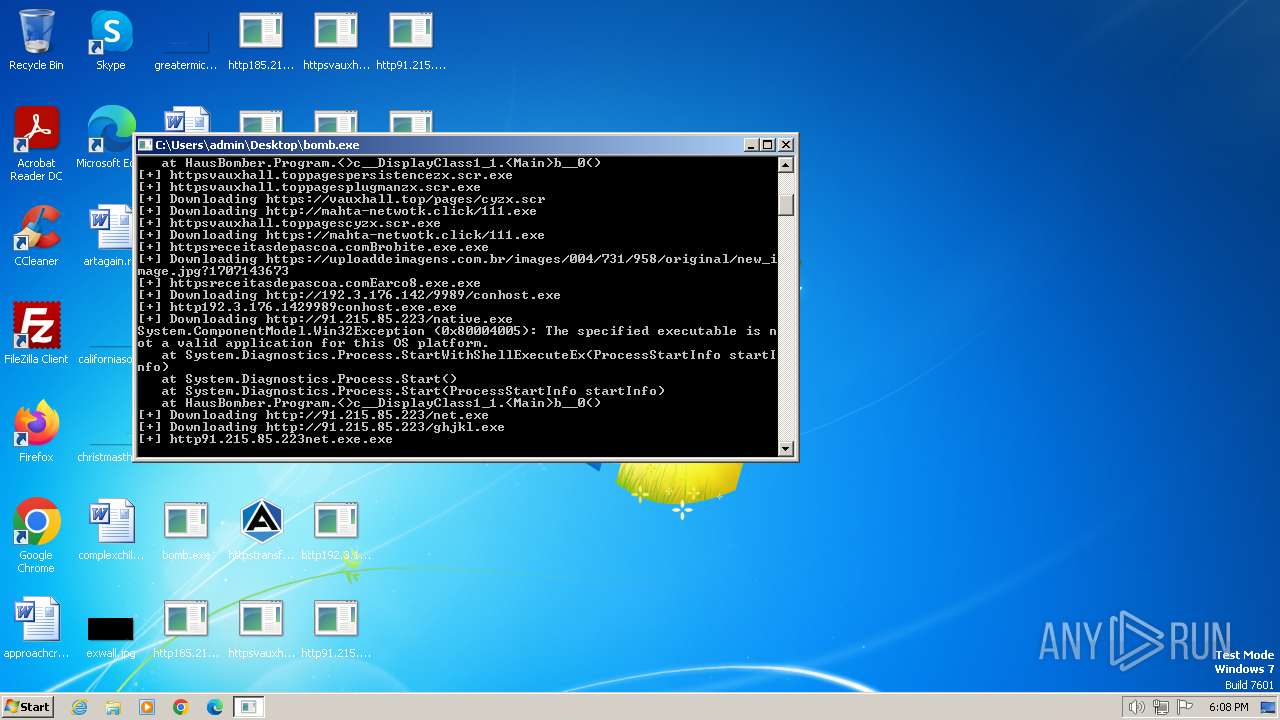
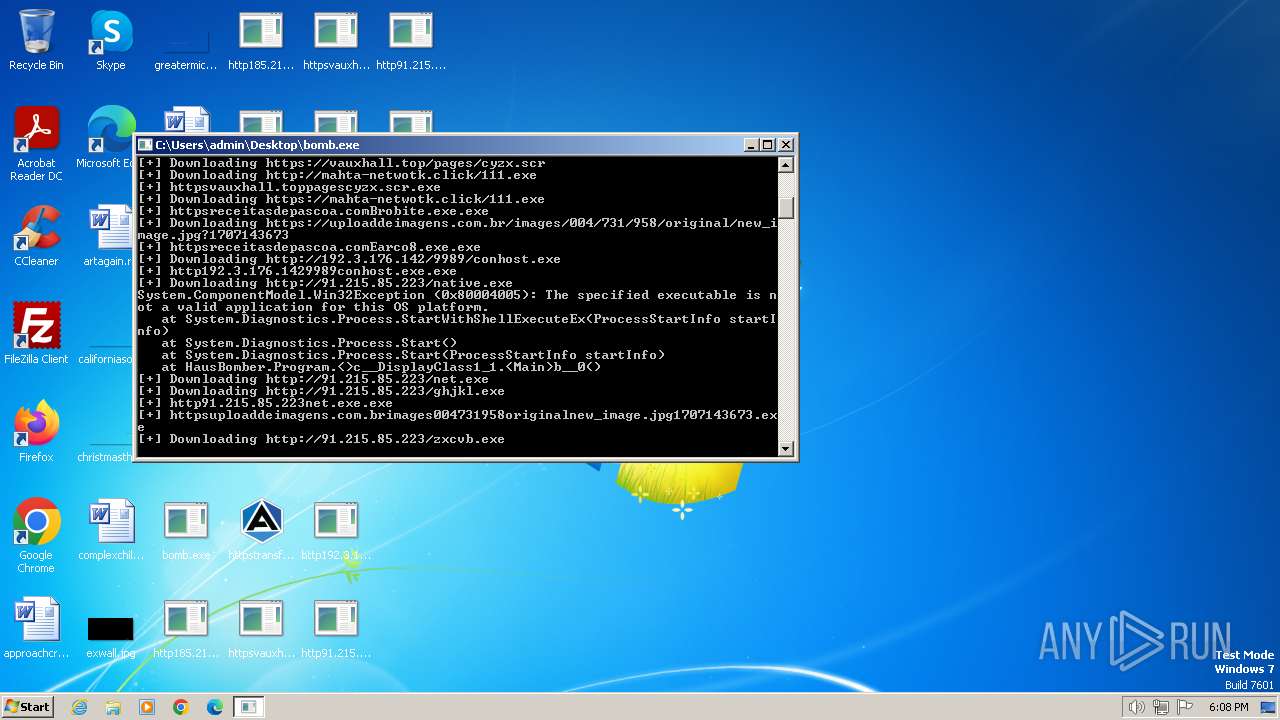
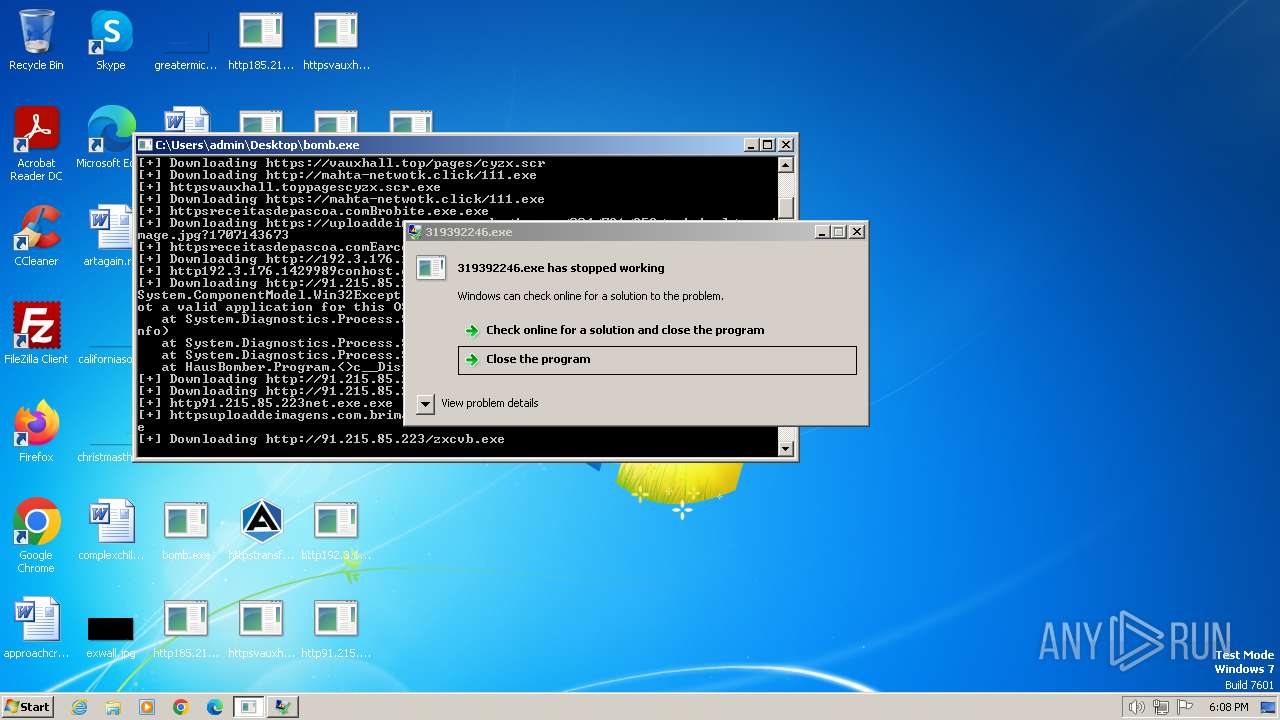
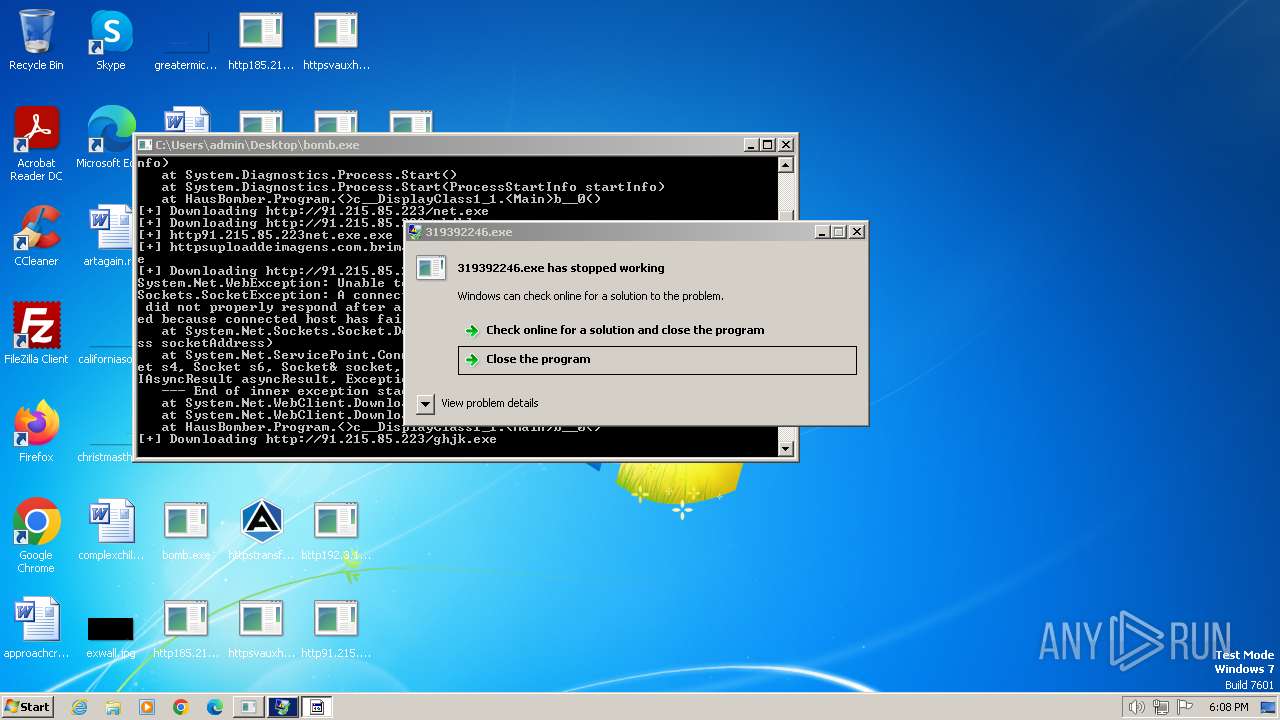
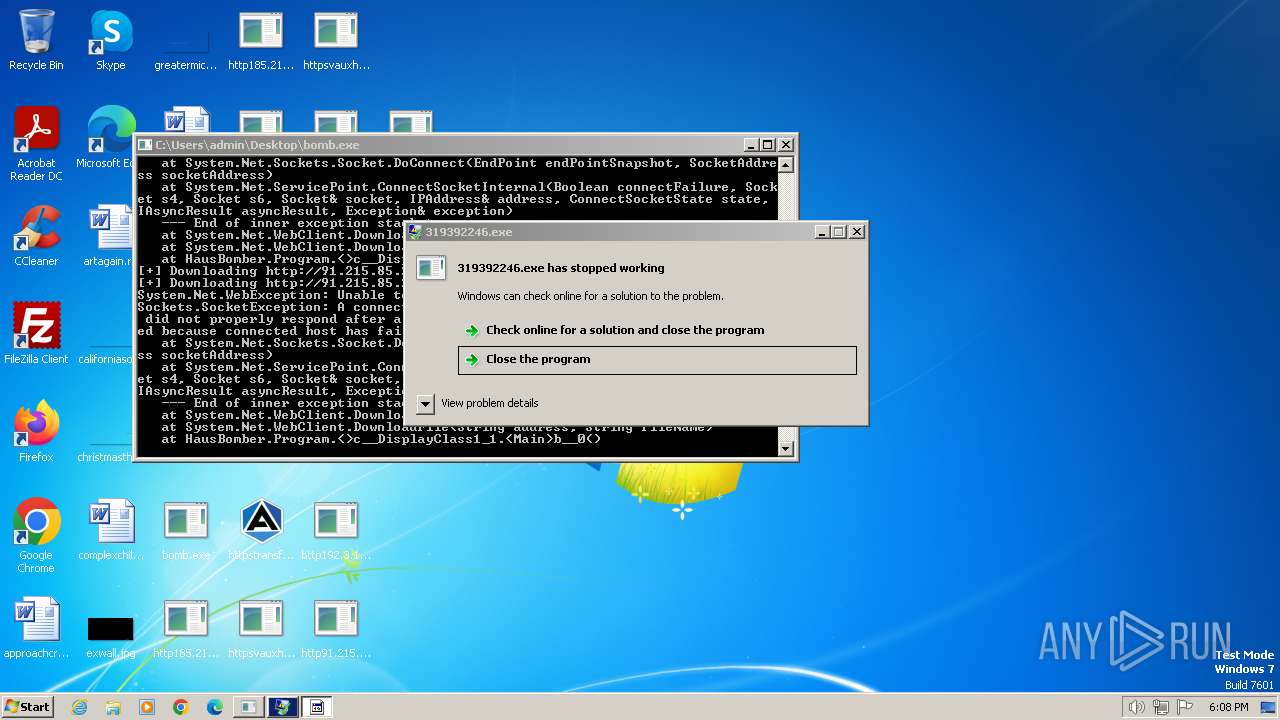
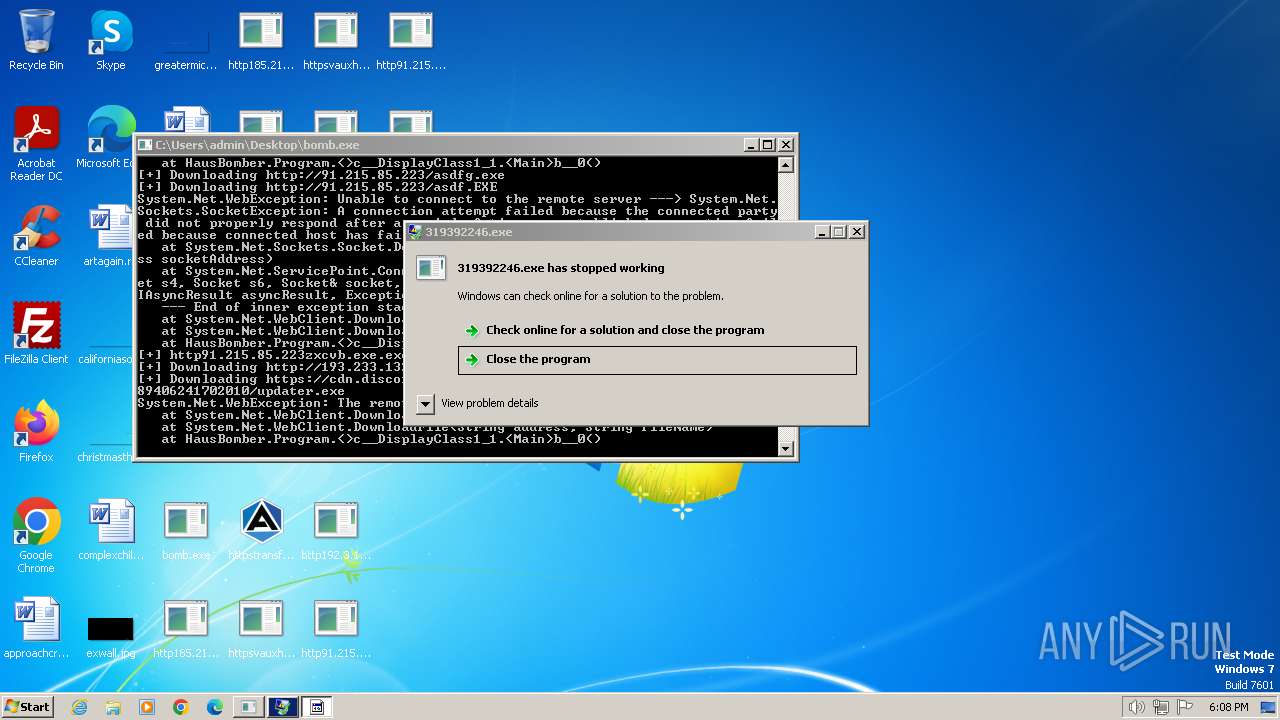
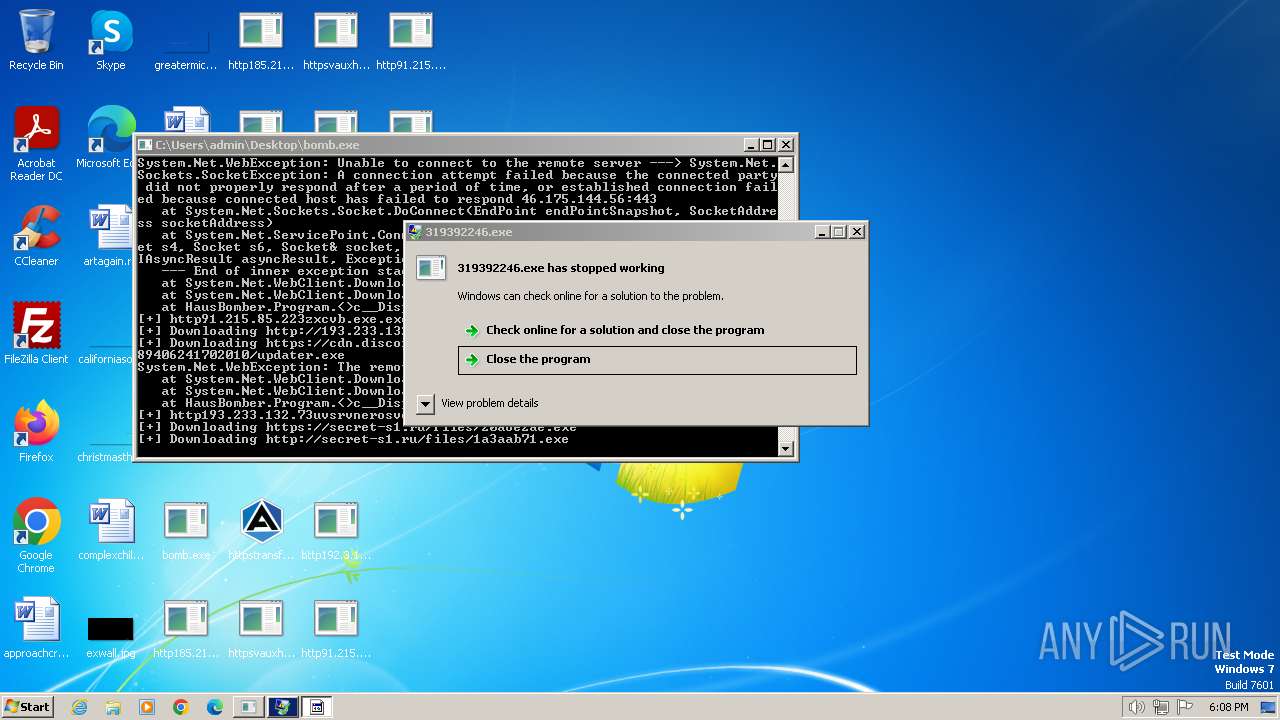
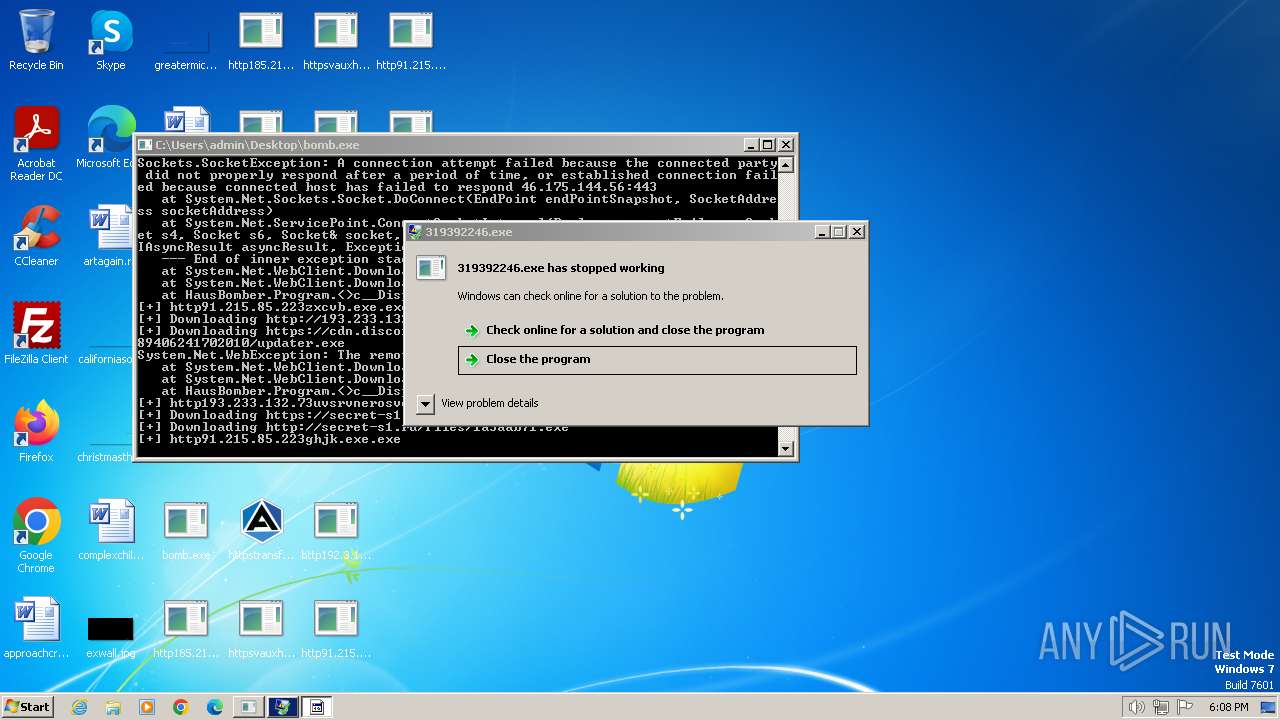
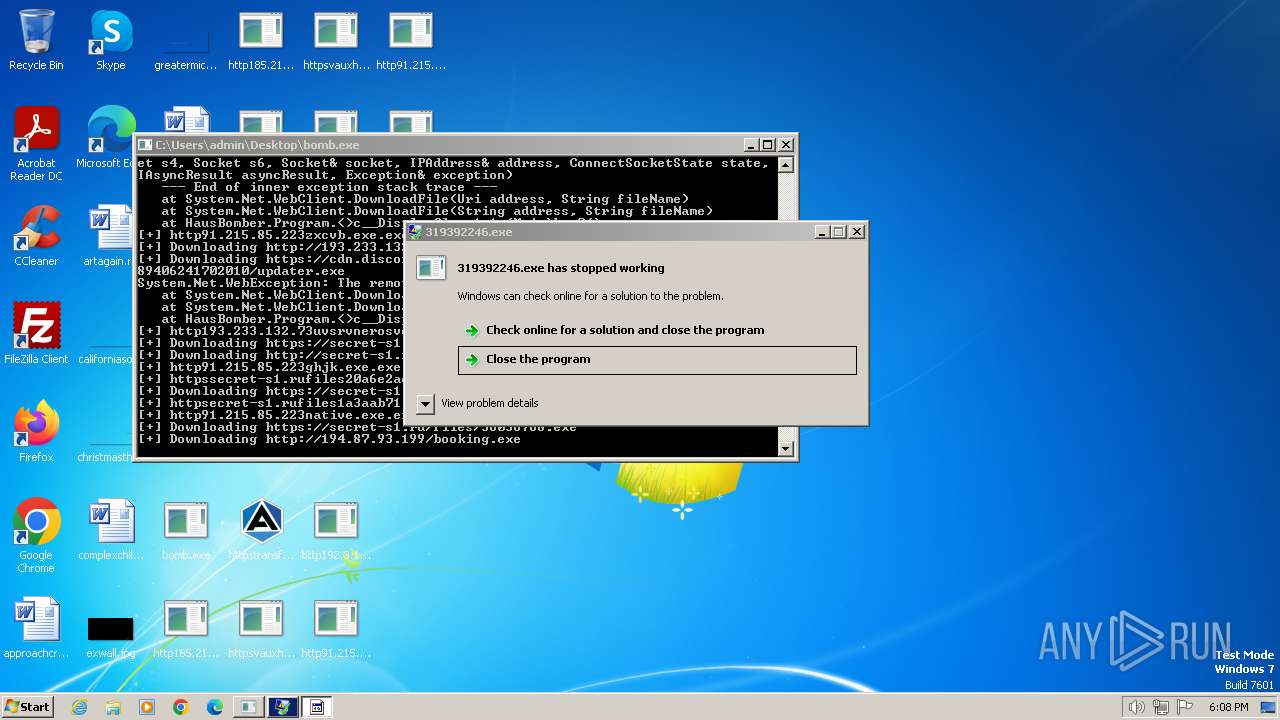
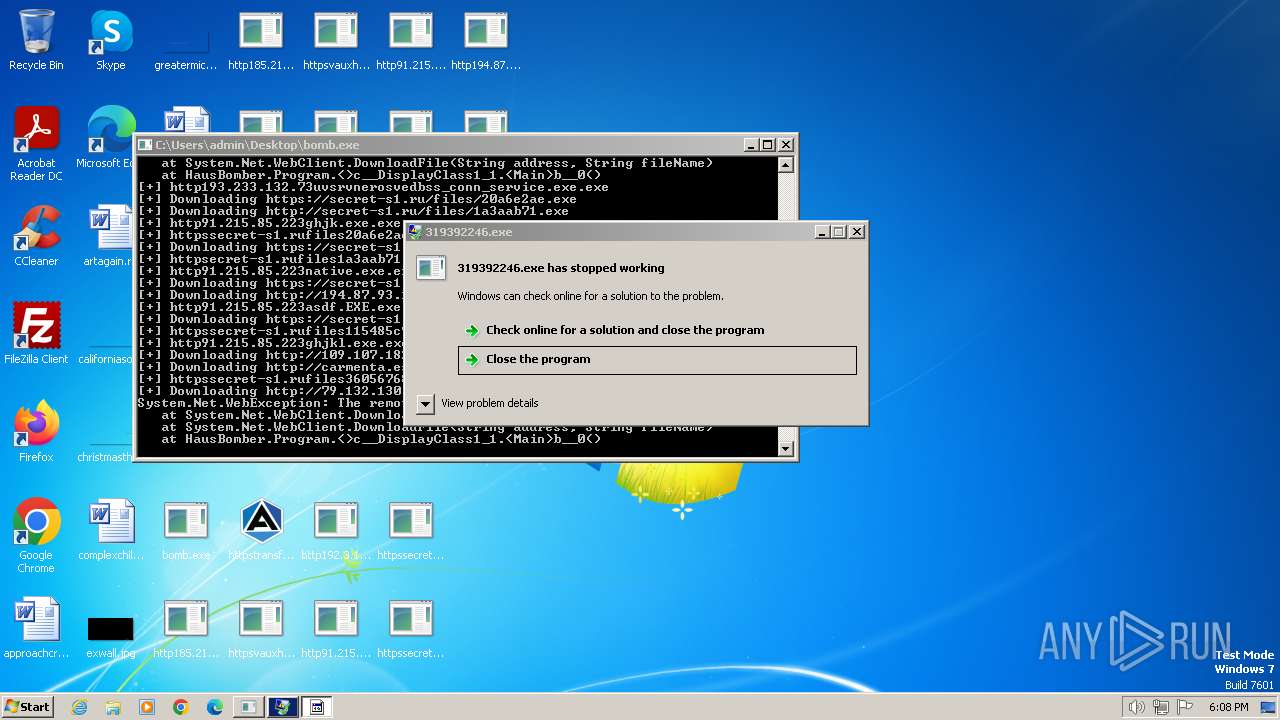
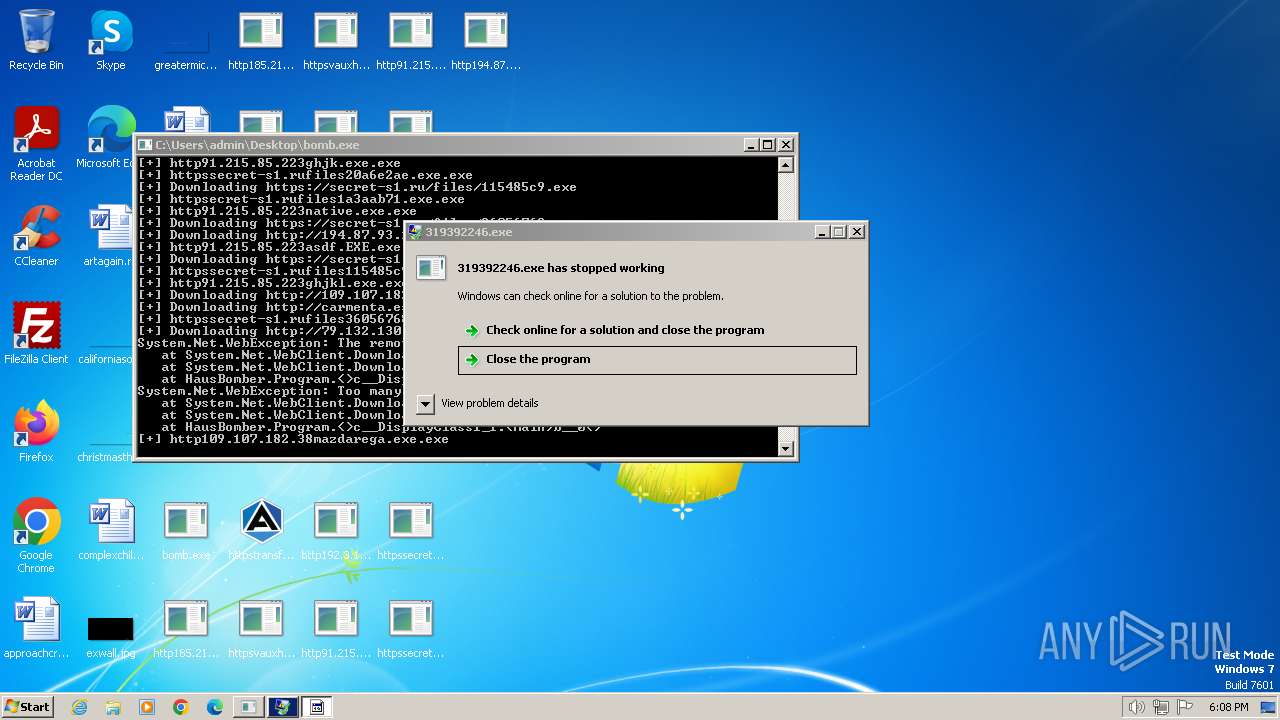
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/71c4b0fa-5ddb-4957-bc06-6fe2309216b0 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | February 07, 2024, 18:07:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 55DBA6E7AA4E8CC73415F4E3F9F6BDAE |
| SHA1: | 87C9F29D58F57A5E025061D389BE2655EE879D5D |
| SHA256: | 3CEA805F1396DF15BDBCD4317388A046A41A6079DBA04576A58BA7B2C812338A |
| SSDEEP: | 192:HLmmmmlmtYz0wZick7pDMj4GbCrMz+MCZLa7HhdSbwxz1OLU87glpp/bI6J4yfm4:pmi7k7pMiLLaLhM6OLU870NJqoI |
MALICIOUS
Drops the executable file immediately after the start
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- http91.215.85.223net.exe.exe (PID: 2860)
- BBLb.exe (PID: 2096)
- 2918823158.exe (PID: 3396)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- http194.87.93.199booking.exe.exe (PID: 2876)
- cs2.exe (PID: 3140)
Steals credentials from Web Browsers
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
Actions looks like stealing of personal data
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
PHORPIEX has been detected (SURICATA)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- bomb.exe (PID: 1504)
REDLINE has been detected (SURICATA)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
Connects to the CnC server
- http185.215.113.66newtpp.exe.exe (PID: 2528)
Run PowerShell with an invisible window
- powershell.exe (PID: 3760)
Bypass execution policy to execute commands
- powershell.exe (PID: 3760)
Create files in the Startup directory
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3832)
AGENTTESLA has been detected (YARA)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
SUSPICIOUS
Reads settings of System Certificates
- bomb.exe (PID: 1504)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
Reads the Internet Settings
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- http91.215.85.223net.exe.exe (PID: 2860)
- BBLb.exe (PID: 2908)
- http192.3.176.1429989conhost.exe.exe (PID: 3300)
- powershell.exe (PID: 3760)
- 2918823158.exe (PID: 3396)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- http194.87.93.199booking.exe.exe (PID: 2876)
- wscript.exe (PID: 3832)
Executable content was dropped or overwritten
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- http91.215.85.223net.exe.exe (PID: 2860)
- BBLb.exe (PID: 2096)
- 2918823158.exe (PID: 3396)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- http194.87.93.199booking.exe.exe (PID: 2876)
- cs2.exe (PID: 3140)
Process requests binary or script from the Internet
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
Connects to the server without a host name
- bomb.exe (PID: 1504)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- 2918823158.exe (PID: 3396)
Application launched itself
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3356)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 3580)
- http91.215.85.223net.exe.exe (PID: 2860)
- BBLb.exe (PID: 4004)
- BBLb.exe (PID: 2728)
- http91.215.85.223ghjk.exe.exe (PID: 3904)
- http91.215.85.223zxcvb.exe.exe (PID: 3584)
- http91.215.85.223native.exe.exe (PID: 2420)
- http91.215.85.223asdf.EXE.exe (PID: 1496)
- http91.215.85.223ghjkl.exe.exe (PID: 568)
- http91.215.85.223asdfg.exe.exe (PID: 2868)
- AttributeString.exe (PID: 3136)
- MSBuild.exe (PID: 3560)
The process creates files with name similar to system file names
- bomb.exe (PID: 1504)
Accesses Microsoft Outlook profiles
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
Searches for installed software
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
Reads browser cookies
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
Connects to SMTP port
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
Connects to unusual port
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- http193.233.132.73uvsrvnerosvedbss_conn_service.exe.exe (PID: 3636)
Starts CMD.EXE for commands execution
- BBLb.exe (PID: 2908)
- wscript.exe (PID: 3832)
The executable file from the user directory is run by the CMD process
- BBLb.exe (PID: 2728)
- cs2.exe (PID: 3140)
The process checks if it is being run in the virtual environment
- dialer.exe (PID: 1560)
The process executes via Task Scheduler
- powershell.exe (PID: 3760)
- AttributeString.exe (PID: 3136)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3760)
Reads the BIOS version
- http109.107.182.38mazdarega.exe.exe (PID: 552)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3832)
Executing commands from a ".bat" file
- wscript.exe (PID: 3832)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1432)
INFO
Create files in a temporary directory
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
- http91.215.85.223net.exe.exe (PID: 2860)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
Reads Environment values
- bomb.exe (PID: 1504)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- cs2.exe (PID: 3140)
Reads the computer name
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 3580)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3356)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- http192.3.176.1429989conhost.exe.exe (PID: 3300)
- http91.215.85.223net.exe.exe (PID: 2860)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- BBLb.exe (PID: 4004)
- BBLb.exe (PID: 2908)
- BBLb.exe (PID: 2728)
- BBLb.exe (PID: 2096)
- http91.215.85.223zxcvb.exe.exe (PID: 3584)
- http91.215.85.223ghjk.exe.exe (PID: 3904)
- httpssecret-s1.rufiles20a6e2ae.exe.exe (PID: 3092)
- http91.215.85.223asdf.EXE.exe (PID: 1496)
- 2918823158.exe (PID: 3396)
- httpsecret-s1.rufiles1a3aab71.exe.exe (PID: 3940)
- http91.215.85.223native.exe.exe (PID: 2420)
- qemu-ga.exe (PID: 3848)
- httpssecret-s1.rufiles115485c9.exe.exe (PID: 1592)
- http91.215.85.223ghjkl.exe.exe (PID: 568)
- httpssecret-s1.rufiles36056768.exe.exe (PID: 2000)
- http194.87.93.199booking.exe.exe (PID: 2876)
- http91.215.85.223asdfg.exe.exe (PID: 2868)
- cs2.exe (PID: 3140)
- AttributeString.exe (PID: 3136)
- http193.233.132.73uvsrvnerosvedbss_conn_service.exe.exe (PID: 3636)
- MSBuild.exe (PID: 3560)
- AttributeString.exe (PID: 3952)
- MSBuild.exe (PID: 2564)
Checks supported languages
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 3580)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3356)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsreceitasdepascoa.comBrobite.exe.exe (PID: 3824)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- 251399556.exe (PID: 3740)
- http192.3.176.1429989conhost.exe.exe (PID: 3300)
- http91.215.85.223net.exe.exe (PID: 2860)
- BBLb.exe (PID: 4004)
- http91.215.85.223net.exe.exe (PID: 3996)
- BBLb.exe (PID: 2908)
- 319392246.exe (PID: 3516)
- BBLb.exe (PID: 2728)
- BBLb.exe (PID: 2096)
- 1640625667.exe (PID: 1728)
- http91.215.85.223zxcvb.exe.exe (PID: 3584)
- http91.215.85.223zxcvb.exe.exe (PID: 3728)
- http91.215.85.223ghjk.exe.exe (PID: 3904)
- http91.215.85.223ghjk.exe.exe (PID: 3436)
- 2918823158.exe (PID: 3396)
- httpssecret-s1.rufiles20a6e2ae.exe.exe (PID: 3092)
- RegAsm.exe (PID: 2044)
- httpsecret-s1.rufiles1a3aab71.exe.exe (PID: 3940)
- http193.233.132.73uvsrvnerosvedbss_conn_service.exe.exe (PID: 3636)
- http91.215.85.223asdf.EXE.exe (PID: 1496)
- http91.215.85.223native.exe.exe (PID: 2644)
- http91.215.85.223native.exe.exe (PID: 2420)
- RegAsm.exe (PID: 2648)
- qemu-ga.exe (PID: 3848)
- http91.215.85.223ghjkl.exe.exe (PID: 568)
- RegAsm.exe (PID: 2660)
- http91.215.85.223ghjkl.exe.exe (PID: 712)
- RegAsm.exe (PID: 2384)
- httpssecret-s1.rufiles115485c9.exe.exe (PID: 1592)
- httpssecret-s1.rufiles36056768.exe.exe (PID: 2000)
- http91.215.85.223asdfg.exe.exe (PID: 2868)
- http91.215.85.223asdfg.exe.exe (PID: 3268)
- http109.107.182.38mazdarega.exe.exe (PID: 552)
- http194.87.93.199booking.exe.exe (PID: 2876)
- AttributeString.exe (PID: 3136)
- cs2.exe (PID: 3140)
- MSBuild.exe (PID: 3560)
- MSBuild.exe (PID: 2564)
- AttributeString.exe (PID: 3952)
- http91.215.85.223asdf.EXE.exe (PID: 1976)
Reads the machine GUID from the registry
- bomb.exe (PID: 1504)
- http185.215.113.66pei.exe.exe (PID: 3136)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 3580)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3356)
- httpsvauxhall.toppagespersistencezx.scr.exe (PID: 2612)
- httpsvauxhall.toppagesplugmanzx.scr.exe (PID: 3320)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- http192.3.176.1429989conhost.exe.exe (PID: 3300)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- http91.215.85.223net.exe.exe (PID: 2860)
- BBLb.exe (PID: 2908)
- BBLb.exe (PID: 4004)
- BBLb.exe (PID: 2728)
- BBLb.exe (PID: 2096)
- http91.215.85.223zxcvb.exe.exe (PID: 3584)
- http91.215.85.223ghjk.exe.exe (PID: 3904)
- 2918823158.exe (PID: 3396)
- http91.215.85.223native.exe.exe (PID: 2420)
- http91.215.85.223asdf.EXE.exe (PID: 1496)
- http91.215.85.223ghjkl.exe.exe (PID: 568)
- http91.215.85.223asdfg.exe.exe (PID: 2868)
- cs2.exe (PID: 3140)
- AttributeString.exe (PID: 3136)
- http193.233.132.73uvsrvnerosvedbss_conn_service.exe.exe (PID: 3636)
- MSBuild.exe (PID: 3560)
- AttributeString.exe (PID: 3952)
Checks proxy server information
- http185.215.113.66pei.exe.exe (PID: 3136)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- 2918823158.exe (PID: 3396)
Creates files or folders in the user directory
- http185.215.113.66pei.exe.exe (PID: 3136)
- http185.215.113.66newtpp.exe.exe (PID: 2528)
- BBLb.exe (PID: 2096)
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- http194.87.93.199booking.exe.exe (PID: 2876)
Reads product name
- httpsreceitasdepascoa.comEarco8.exe.exe (PID: 2916)
- cs2.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2048:07:19 21:03:26+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9728 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x457a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
129
Monitored processes
58
Malicious processes
13
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | "C:\Users\admin\Desktop\http109.107.182.38mazdarega.exe.exe" | C:\Users\admin\Desktop\http109.107.182.38mazdarega.exe.exe | bomb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: HeidiSQL 12.6.0.6783 32 Bit Exit code: 0 Version: 12.6.0.6783 Modules
| |||||||||||||||
| 568 | "C:\Users\admin\Desktop\http91.215.85.223ghjkl.exe.exe" | C:\Users\admin\Desktop\http91.215.85.223ghjkl.exe.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 712 | C:\Users\admin\Desktop\http91.215.85.223ghjkl.exe.exe | C:\Users\admin\Desktop\http91.215.85.223ghjkl.exe.exe | http91.215.85.223ghjkl.exe.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1112 | "C:\Windows\System32\cmd.exe" /k START "" "C:\Users\admin\AppData\Local\Temp\BBLb.exe" & EXIT | C:\Windows\System32\cmd.exe | BBLb.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1432 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\cs2\mUIe5kBMcLtyyRfVNE6smXkJvw6d4pdtgx5QPUAHzK9h0eXdEXMeamhYXU.bat" " | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1496 | "C:\Users\admin\Desktop\http91.215.85.223asdf.EXE.exe" | C:\Users\admin\Desktop\http91.215.85.223asdf.EXE.exe | — | bomb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1504 | "C:\Users\admin\Desktop\bomb.exe" | C:\Users\admin\Desktop\bomb.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1560 | "C:\Windows\system32\dialer.exe" | C:\Windows\System32\dialer.exe | http91.215.85.223net.exe.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Phone Dialer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\Desktop\httpssecret-s1.rufiles115485c9.exe.exe" | C:\Users\admin\Desktop\httpssecret-s1.rufiles115485c9.exe.exe | — | bomb.exe | |||||||||||
User: admin Company: AppGenius Integrity Level: MEDIUM Description: Huzzah Rigidly Software Exit code: 0 Version: 1.0.0.3 Modules
| |||||||||||||||
| 1728 | C:\Users\admin\AppData\Local\Temp\1640625667.exe | C:\Users\admin\AppData\Local\Temp\1640625667.exe | — | http185.215.113.66newtpp.exe.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
25 480
Read events
25 234
Write events
246
Delete events
0
Modification events
| (PID) Process: | (1504) bomb.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1504) bomb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1504) bomb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1504) bomb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1504) bomb.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3136) http185.215.113.66pei.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3136) http185.215.113.66pei.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3136) http185.215.113.66pei.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3136) http185.215.113.66pei.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3136) http185.215.113.66pei.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
19
Suspicious files
18
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1504 | bomb.exe | C:\Users\admin\Desktop\http185.215.113.66pei.exe.exe | executable | |
MD5:62B97CF4C0ABAFEDA36E3FC101A5A022 | SHA256:E172537ADCEE1FCDC8F16C23E43A5AC82C56A0347FA0197C08BE979438A534AB | |||
| 1504 | bomb.exe | C:\Users\admin\AppData\Local\Temp\Cab5F5B.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 1504 | bomb.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2792 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs893A.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 3136 | http185.215.113.66pei.exe.exe | C:\Users\admin\AppData\Local\Temp\251399556.exe | executable | |
MD5:BB3D7BD66C92454429A8C78BF64F977B | SHA256:94A66EEA65EDD08CA19BF6DB266058E81714312B6A51892298B461FFD8B90161 | |||
| 1504 | bomb.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:9621BFE5AF7F55BB1EC6651848DE3578 | SHA256:4C40830173D3B513D77285F648EA98CD9CFE71C4CA2C11A6376C4A9780847C15 | |||
| 1504 | bomb.exe | C:\Users\admin\Desktop\httpsvauxhall.toppagespersistencezx.scr.exe | executable | |
MD5:D3F42BBFCE4403373A10572E542E1063 | SHA256:FAE750F4A45D13BC3549BD6448957EB66AC39992BDE13DBEAD9B054A71001A65 | |||
| 1504 | bomb.exe | C:\Users\admin\AppData\Local\Temp\Tar5F5C.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 1504 | bomb.exe | C:\Users\admin\Desktop\httpsvauxhall.toppagesplugmanzx.scr.exe | executable | |
MD5:7A6FECBFE4387BC416938FB3D053DC2E | SHA256:4668272288037C99F4A25B5620E2DC1294A62FA8A490918AE851226F3F5EF579 | |||
| 3548 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs6AF4.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
61
DNS requests
20
Threats
90
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1504 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pei.exe | unknown | executable | 9.50 Kb | unknown |
3136 | http185.215.113.66pei.exe.exe | GET | 200 | 185.215.113.84:80 | http://twizt.net/newtpp.exe | unknown | executable | 79.5 Kb | unknown |
1504 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/newtpp.exe | unknown | executable | 79.5 Kb | unknown |
1504 | bomb.exe | GET | 200 | 173.222.108.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ab4180b5d892811c | unknown | compressed | 65.2 Kb | unknown |
1504 | bomb.exe | GET | 200 | 91.215.85.223:80 | http://91.215.85.223/net.exe | unknown | executable | 2.13 Mb | unknown |
1504 | bomb.exe | GET | 200 | 192.3.176.142:80 | http://192.3.176.142/9989/conhost.exe | unknown | executable | 896 Kb | unknown |
2528 | http185.215.113.66newtpp.exe.exe | GET | — | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
1504 | bomb.exe | GET | 200 | 91.215.85.223:80 | http://91.215.85.223/native.exe | unknown | executable | 2.13 Mb | unknown |
3136 | http185.215.113.66pei.exe.exe | GET | 200 | 185.215.113.84:80 | http://twizt.net/peinstall.php | unknown | executable | 79.5 Kb | unknown |
1504 | bomb.exe | GET | — | 91.215.85.223:80 | http://91.215.85.223/zxcvb.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1504 | bomb.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
1504 | bomb.exe | 185.215.113.66:80 | — | 1337team Limited | SC | unknown |
1504 | bomb.exe | 162.159.133.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
1504 | bomb.exe | 144.76.136.153:443 | transfer.sh | Hetzner Online GmbH | DE | unknown |
1504 | bomb.exe | 154.7.253.53:443 | receitasdepascoa.com | TIER-NET | US | unknown |
1504 | bomb.exe | 173.222.108.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
1504 | bomb.exe | 176.97.69.6:443 | letransporter.com | M247 Ltd | AU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
cdn.discordapp.com |
| shared |
orlandiarq.com |
| unknown |
receitasdepascoa.com |
| unknown |
transfer.sh |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
letransporter.com |
| unknown |
vauxhall.top |
| unknown |
twizt.net |
| unknown |
mahta-netwotk.click |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY Observed DNS Query to File Transfer Service Domain (transfer .sh) |
1080 | svchost.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed (transfer .sh in DNS Lookup) |
1504 | bomb.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1504 | bomb.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed (transfer .sh in TLS SNI) |
1504 | bomb.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 22 |
1504 | bomb.exe | Potential Corporate Privacy Violation | ET POLICY Observed File Transfer Service SSL/TLS Certificate (transfer .sh) |
1504 | bomb.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1504 | bomb.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1504 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
10 ETPRO signatures available at the full report
Process | Message |
|---|---|
http109.107.182.38mazdarega.exe.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|