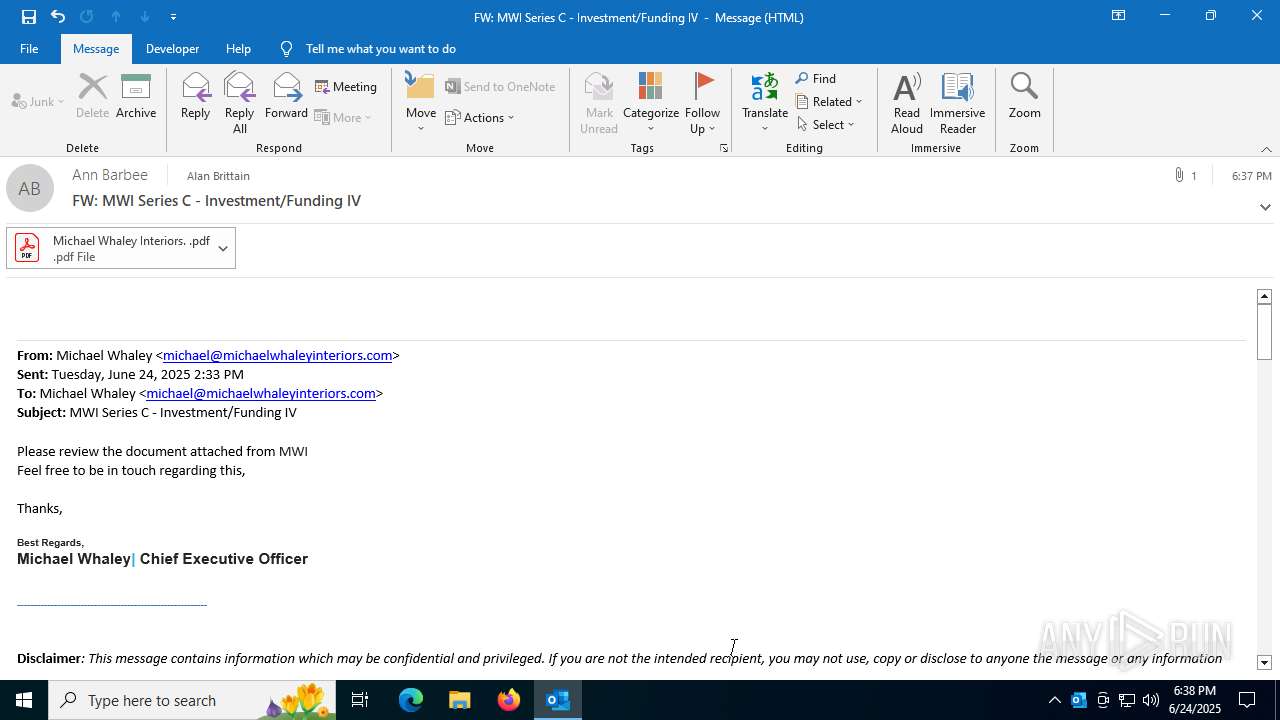
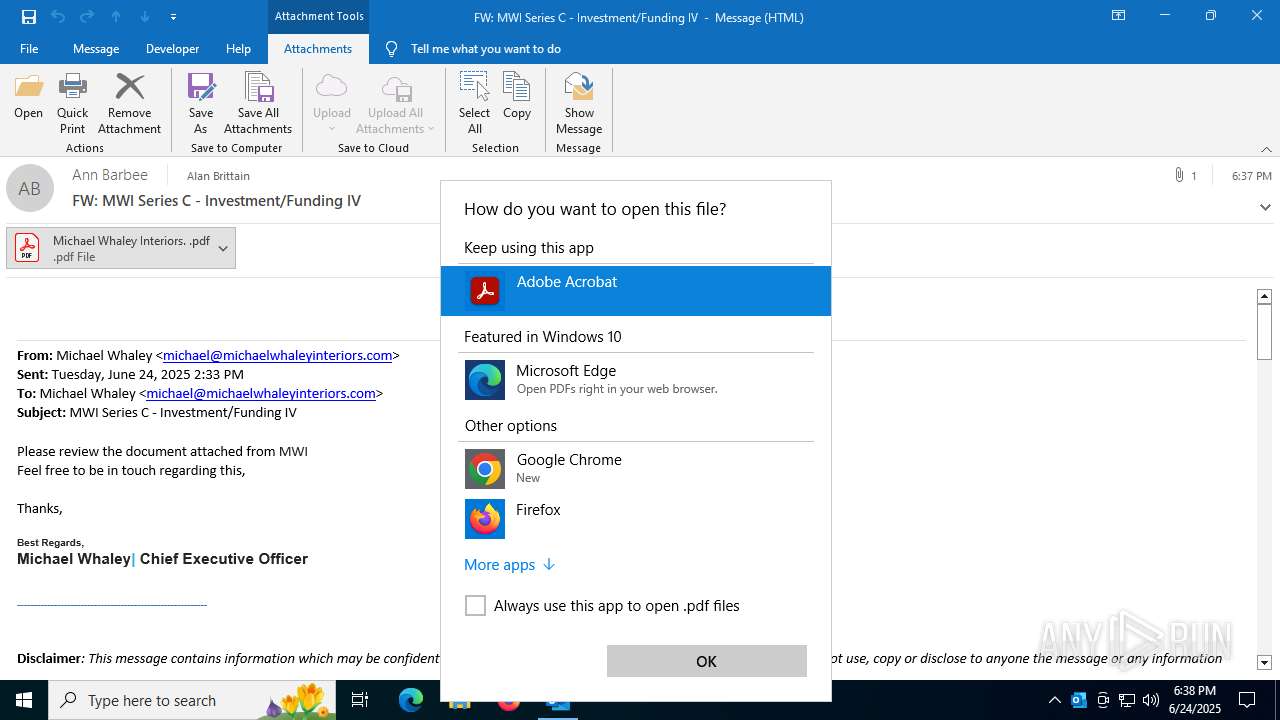
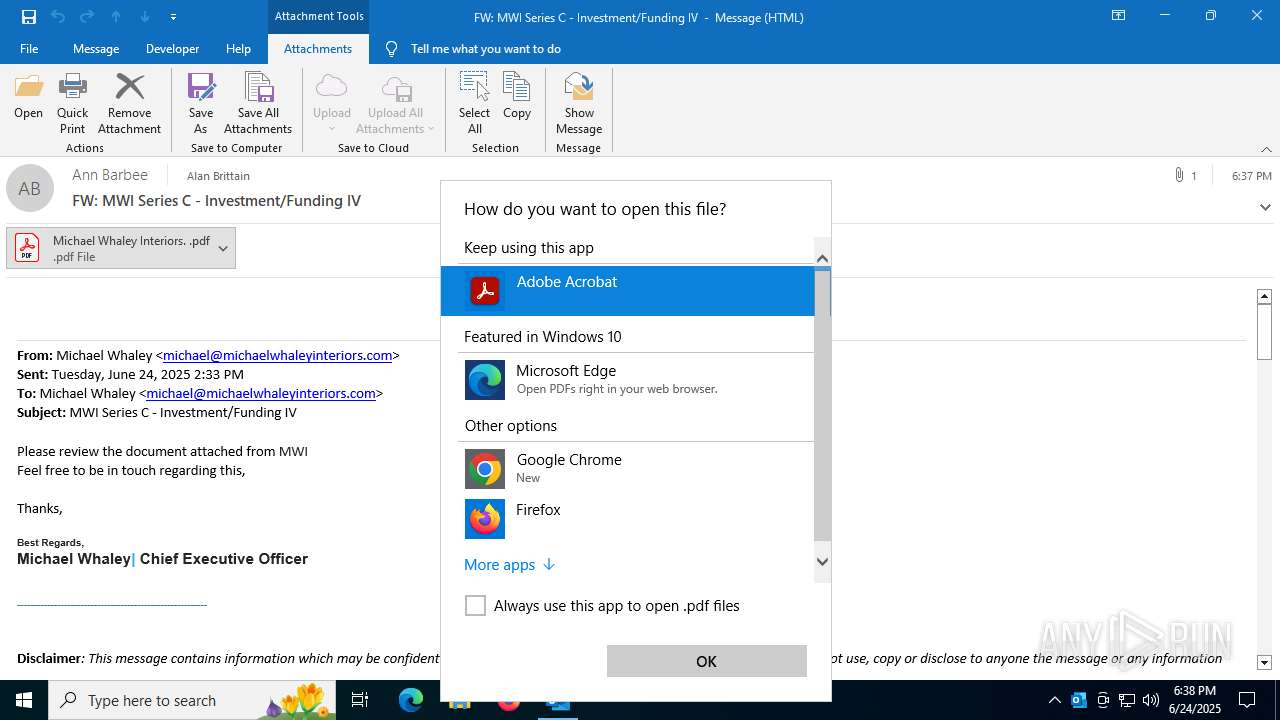
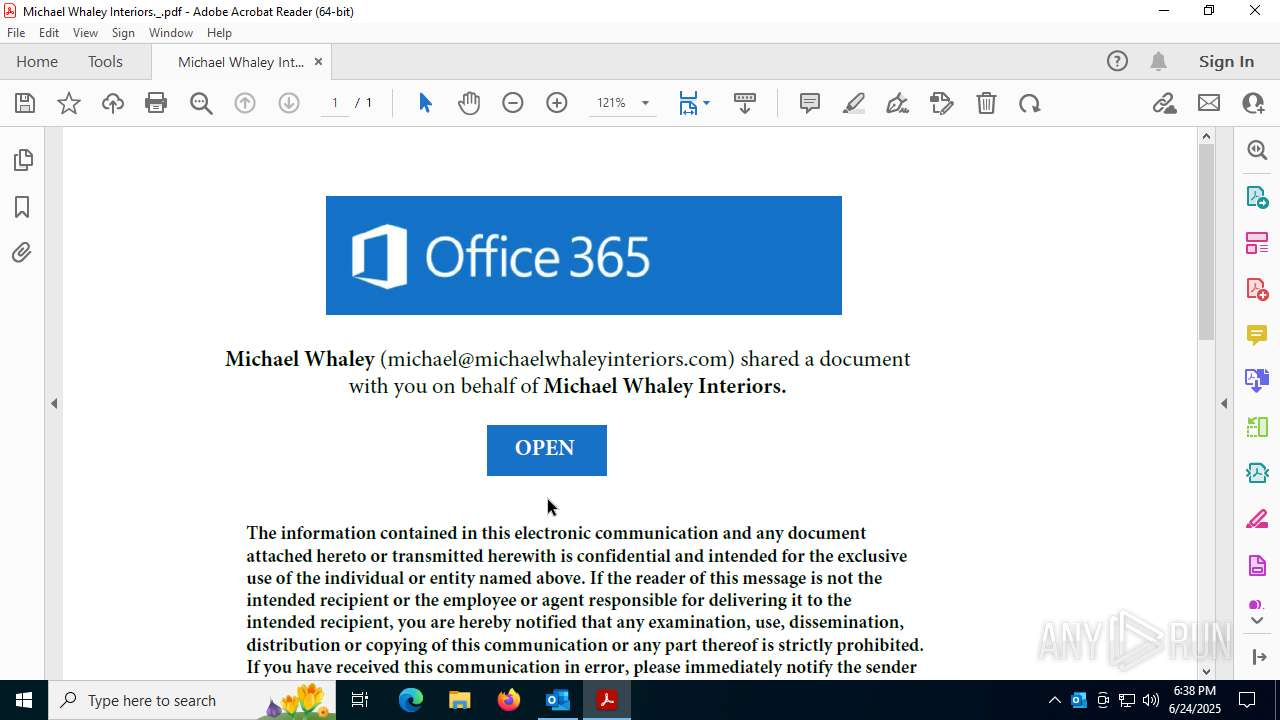
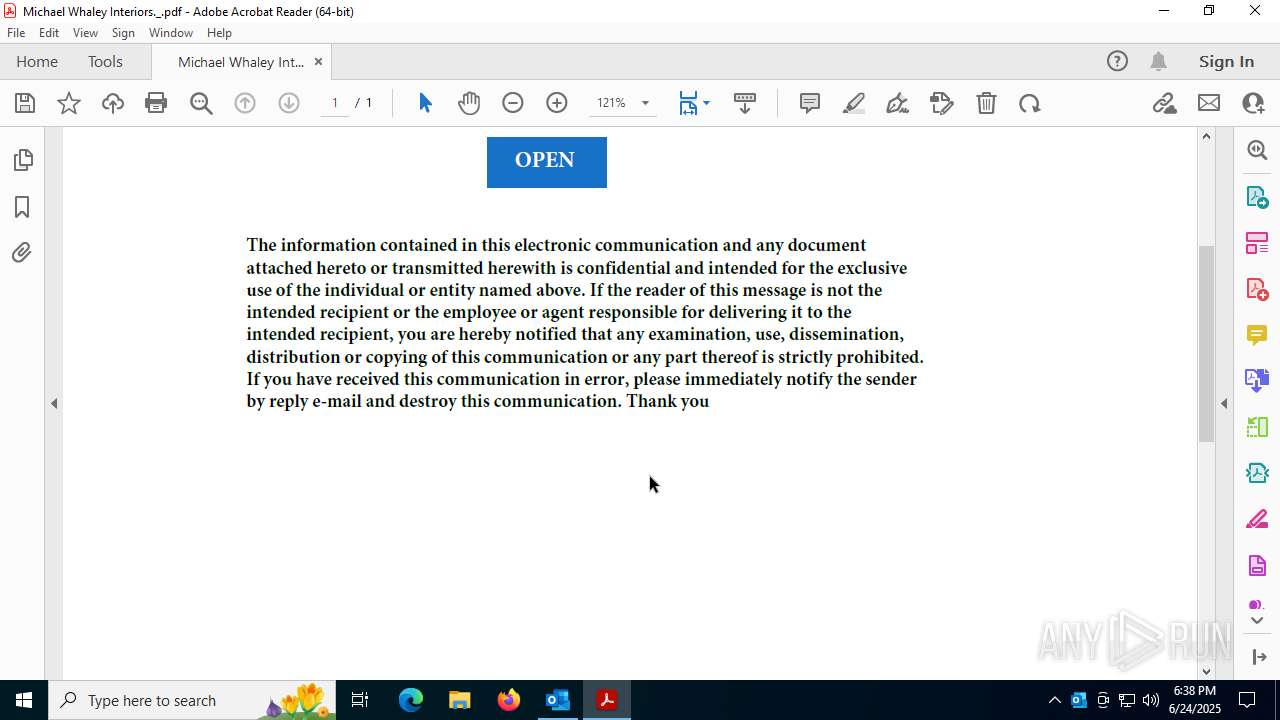
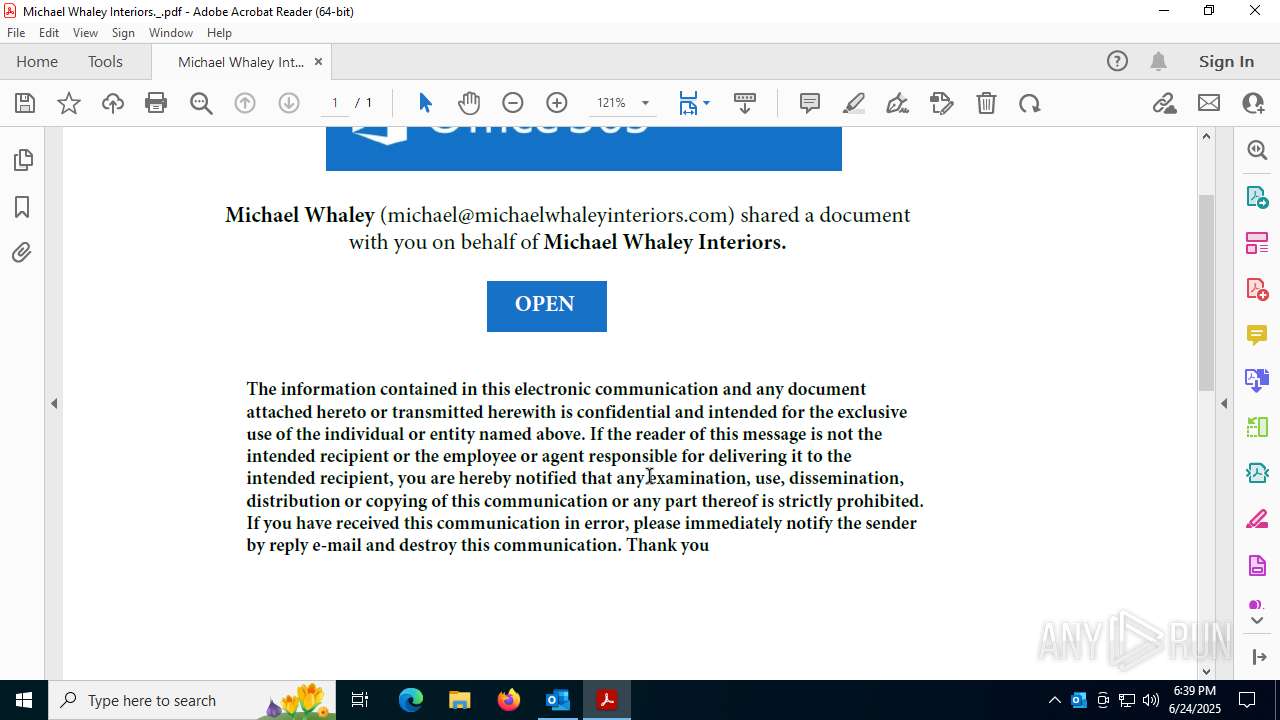
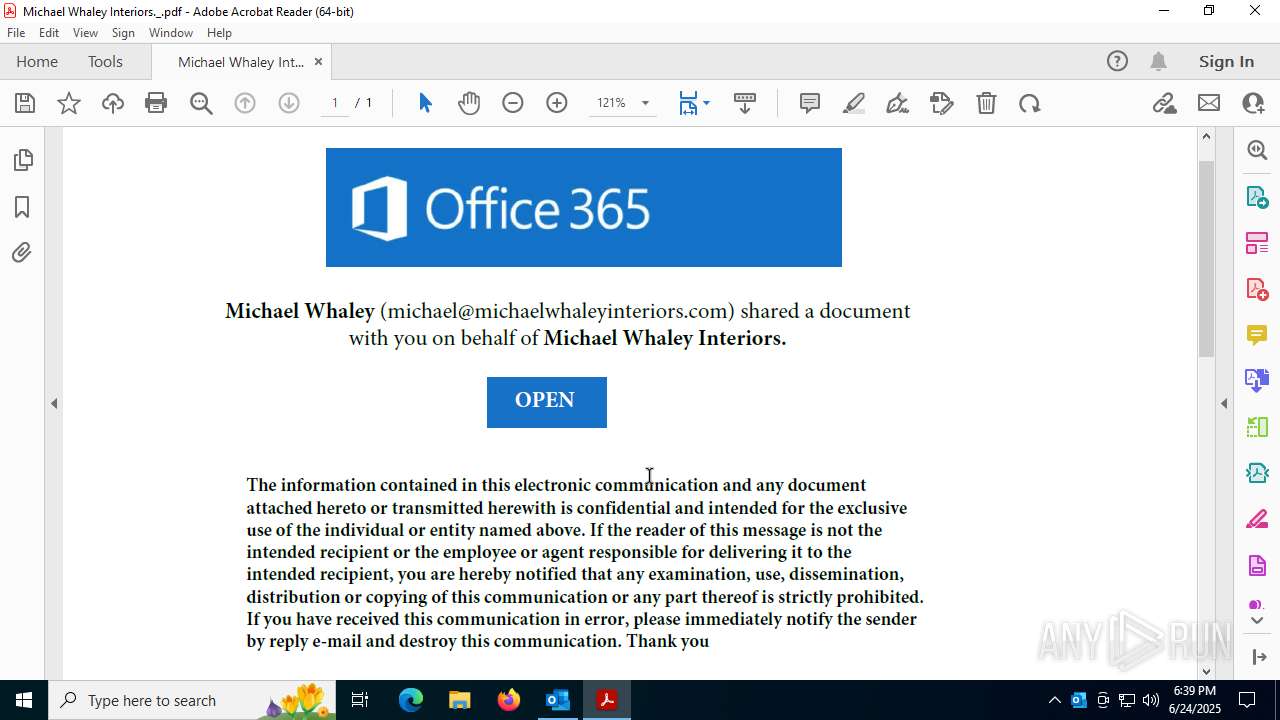
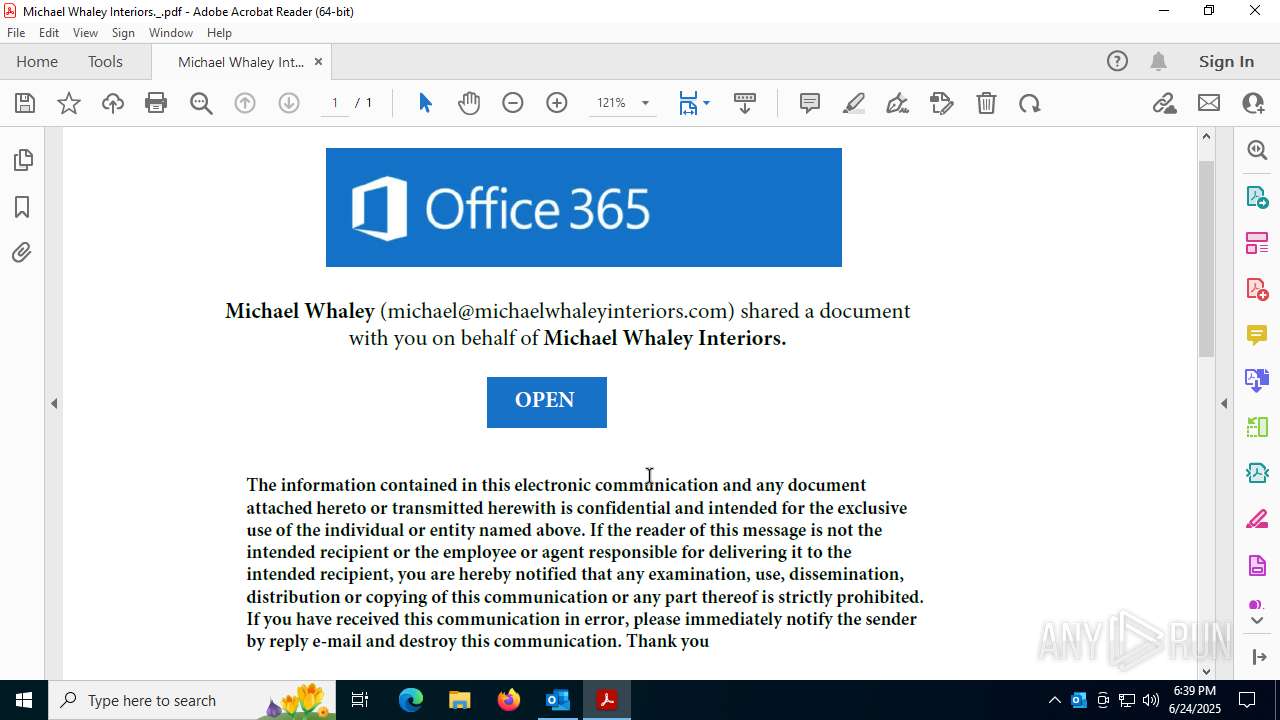
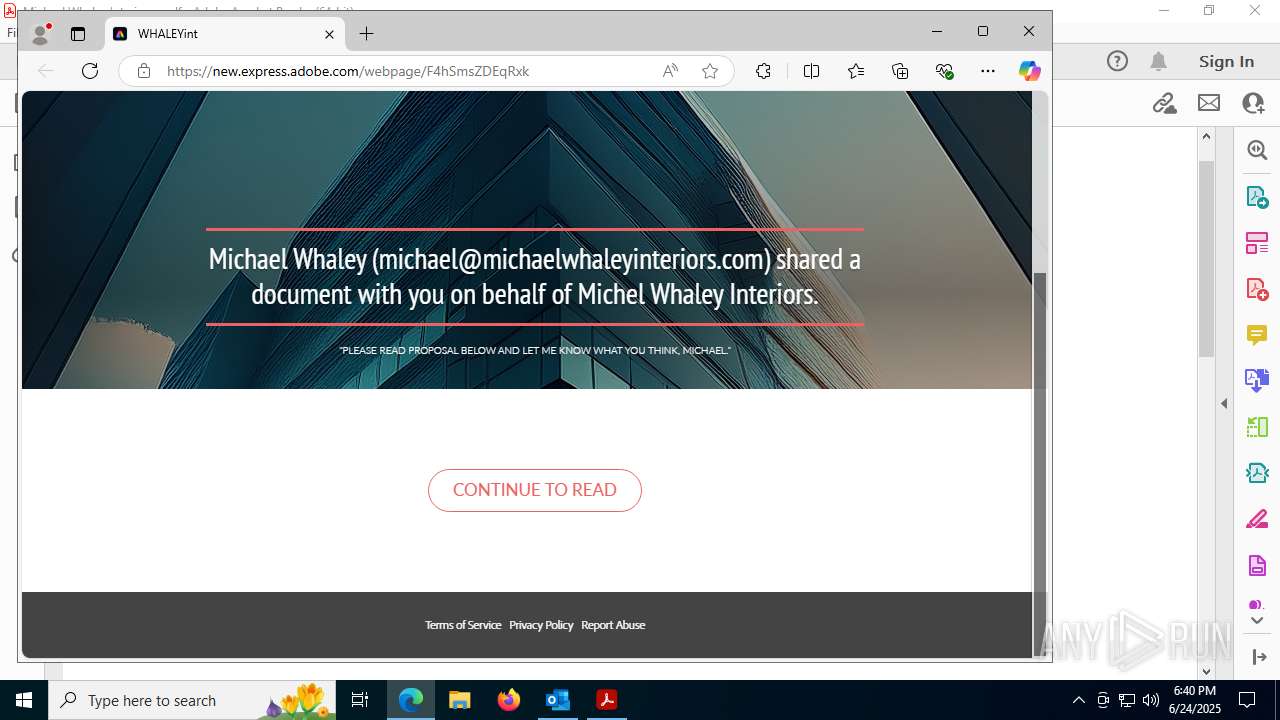
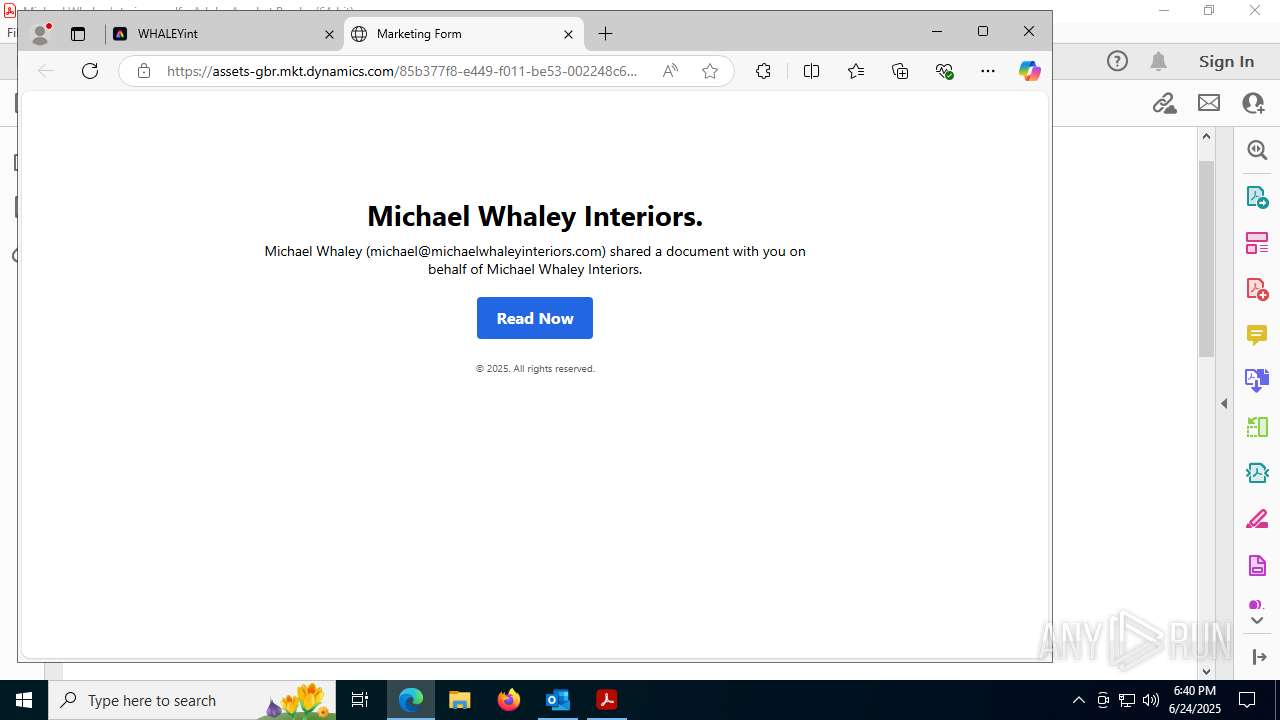
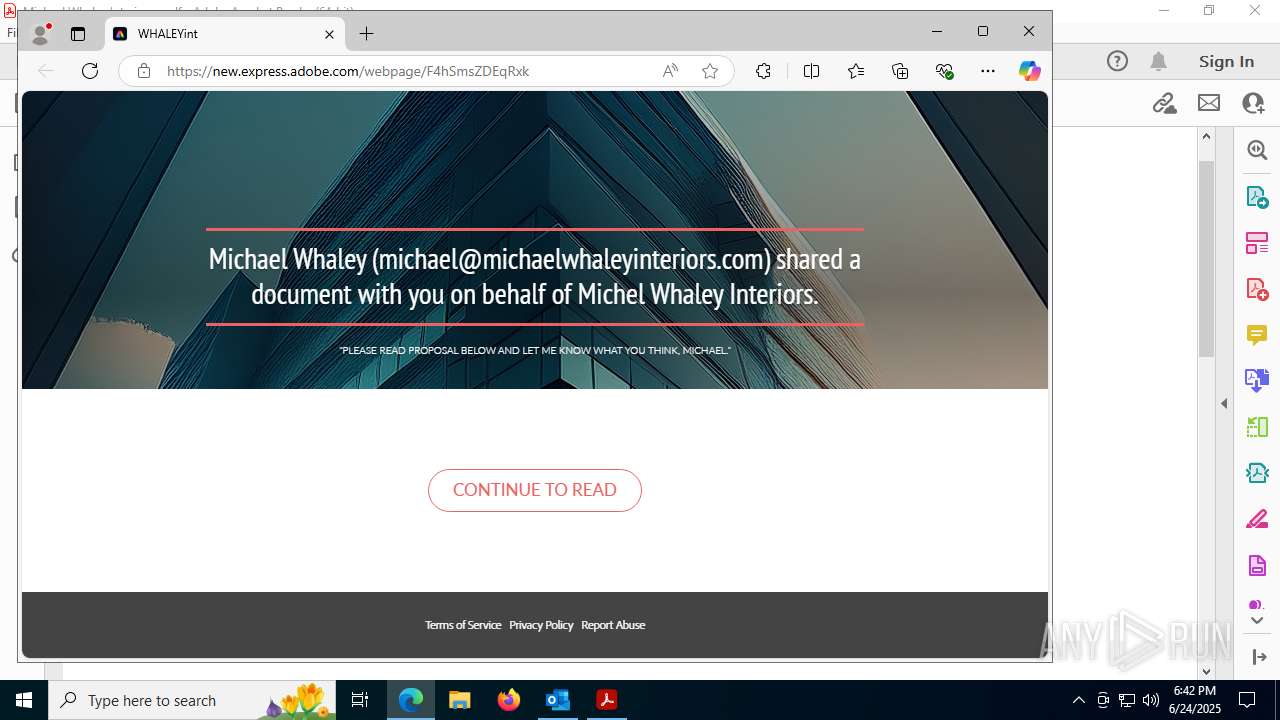
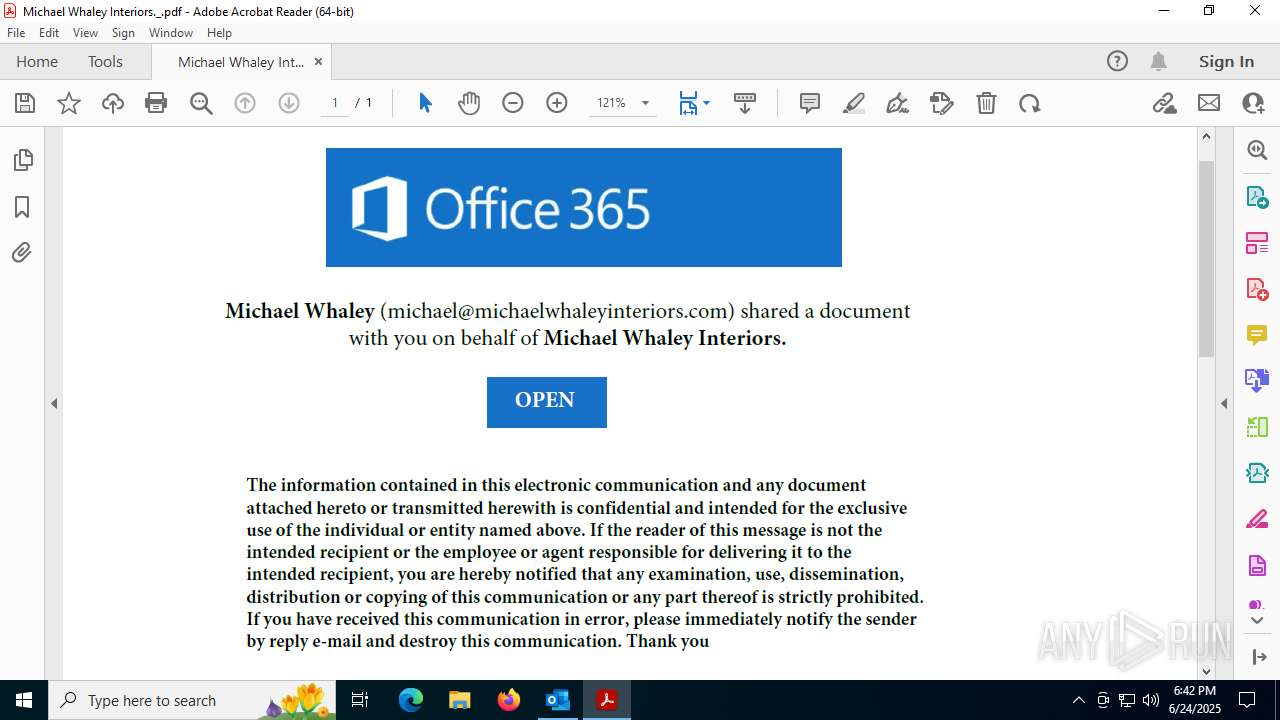
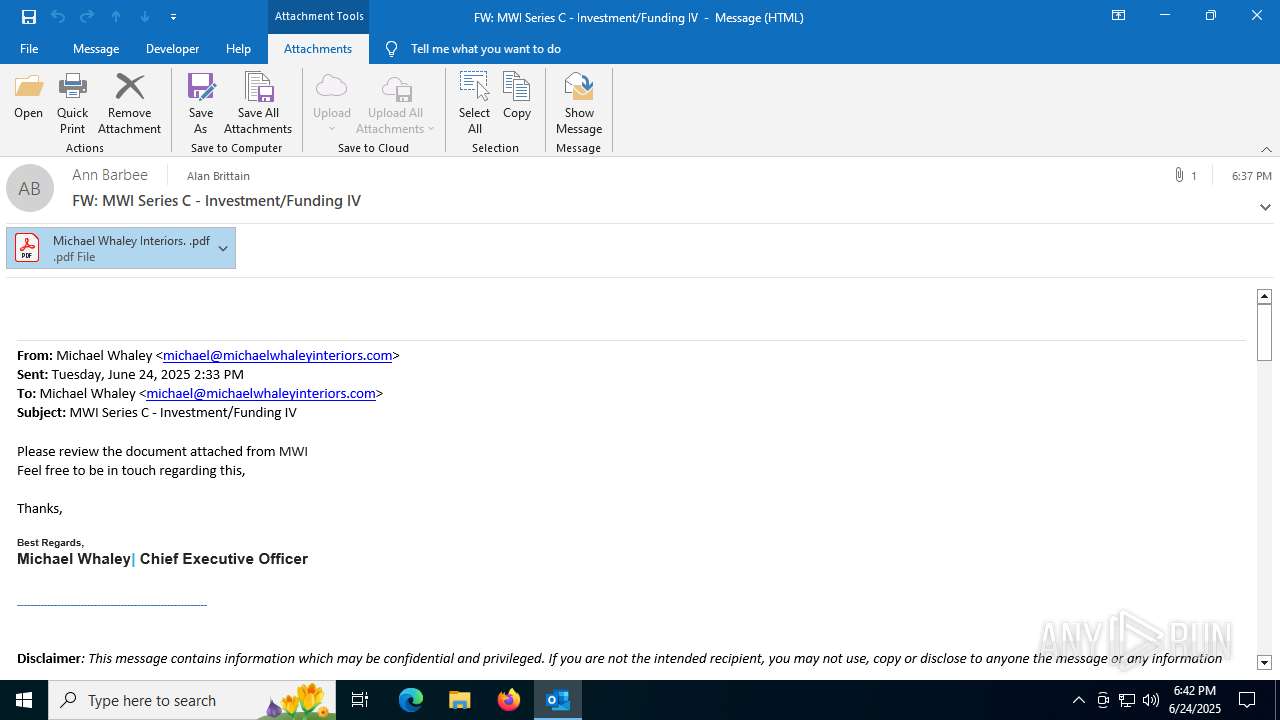
| File name: | FW MWI Series C - InvestmentFunding IV.msg |
| Full analysis: | https://app.any.run/tasks/57eb45e0-fcaa-4d1b-b9b9-574f95b8ade3 |
| Verdict: | Malicious activity |
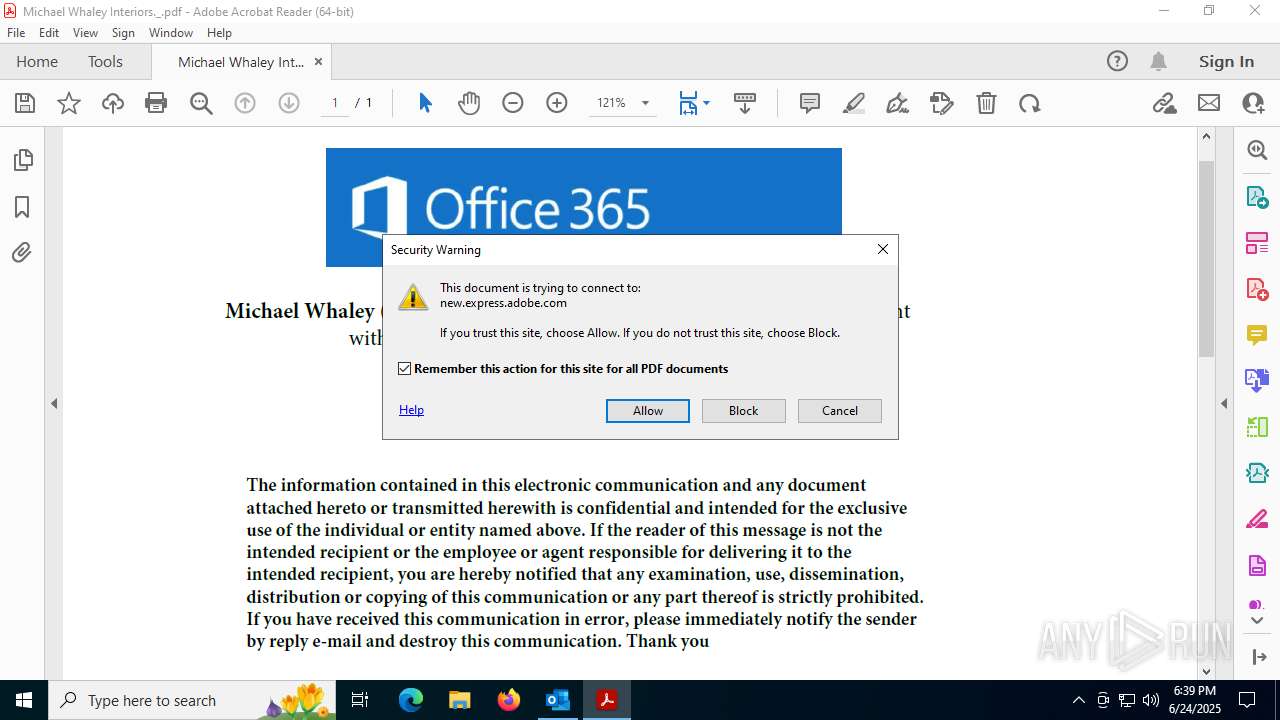
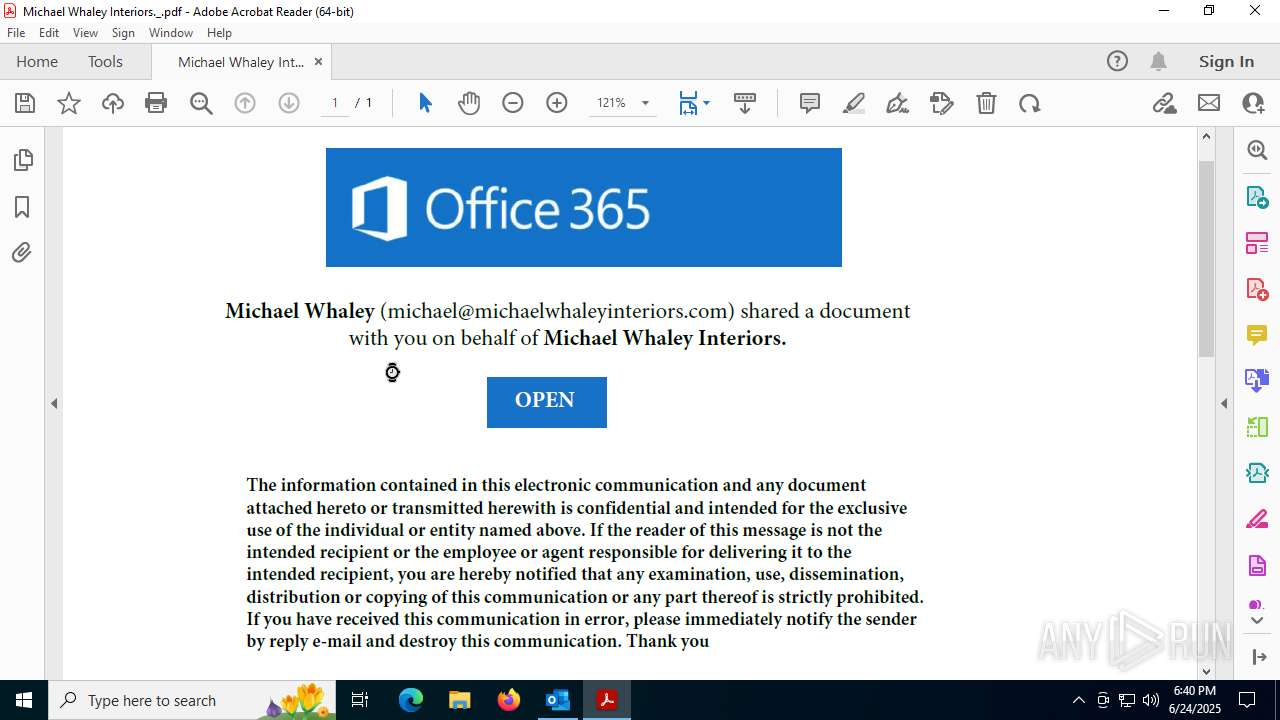
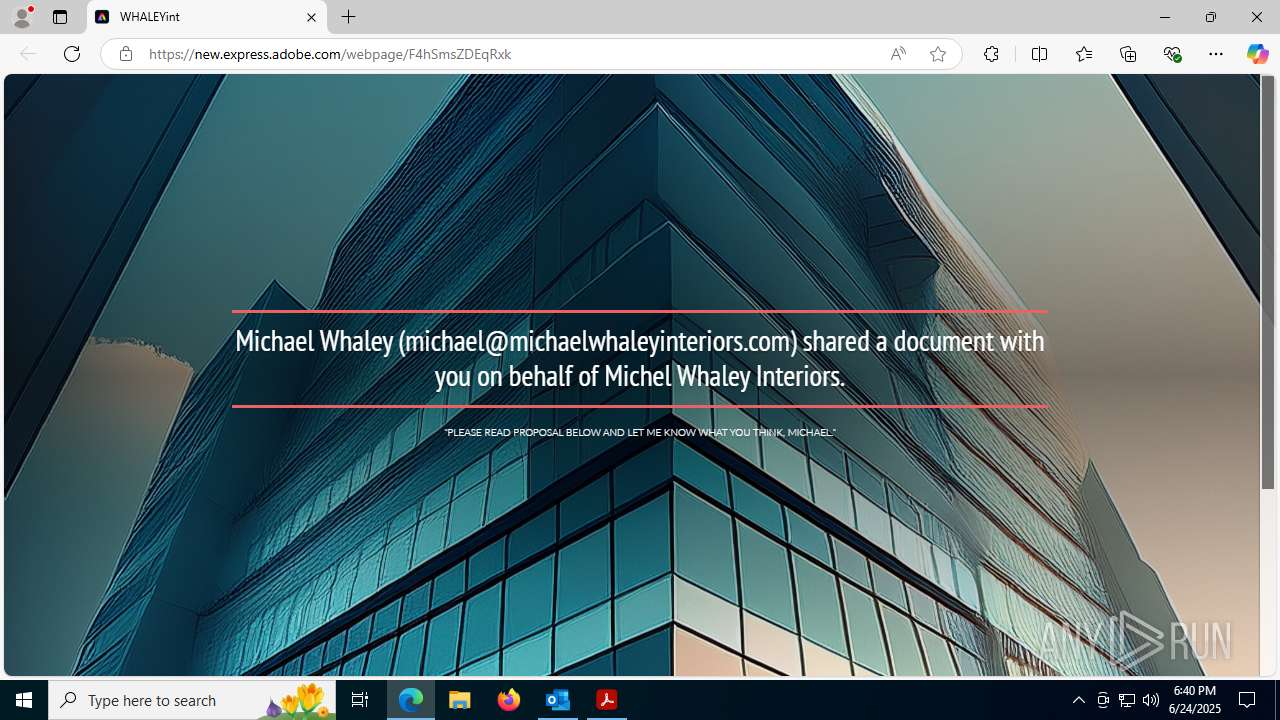
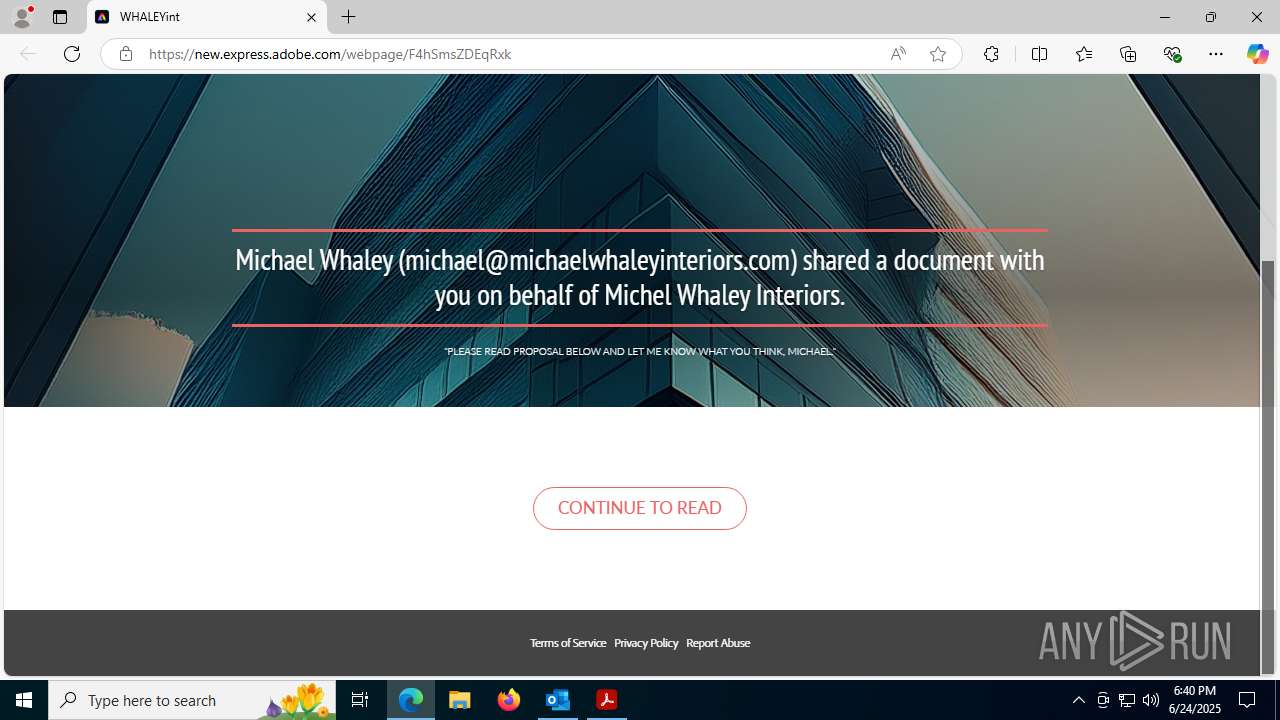
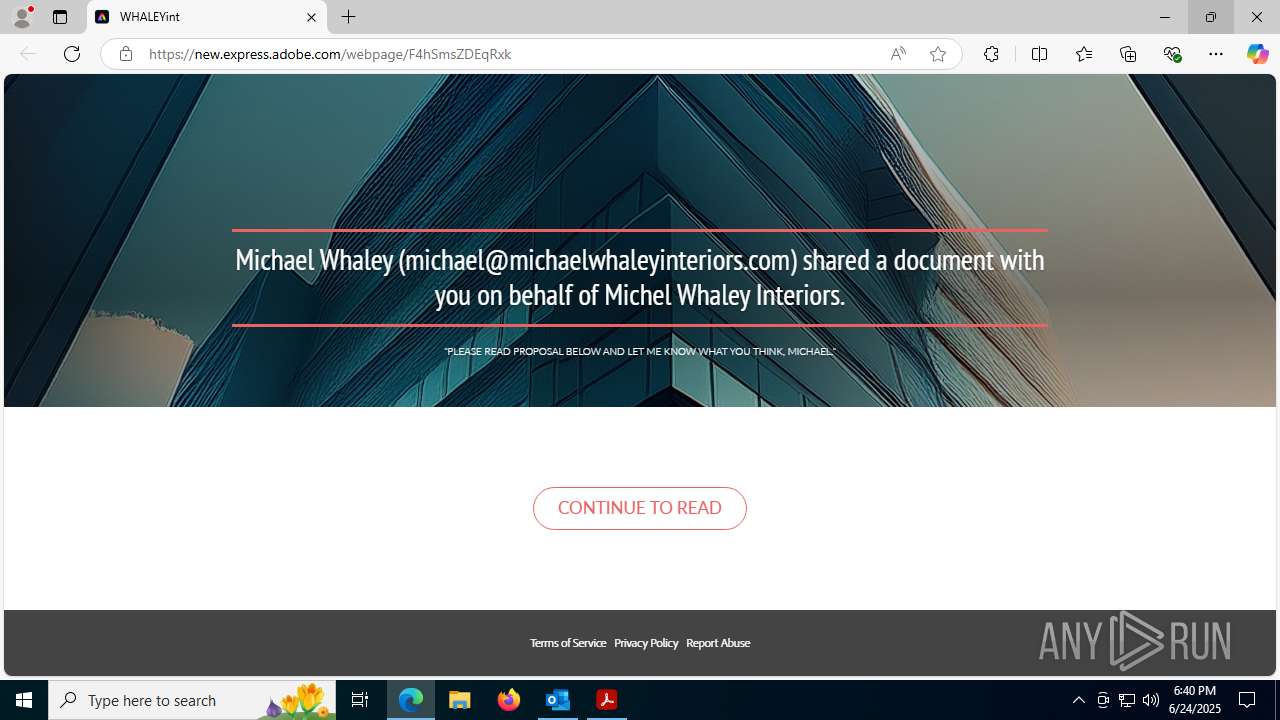
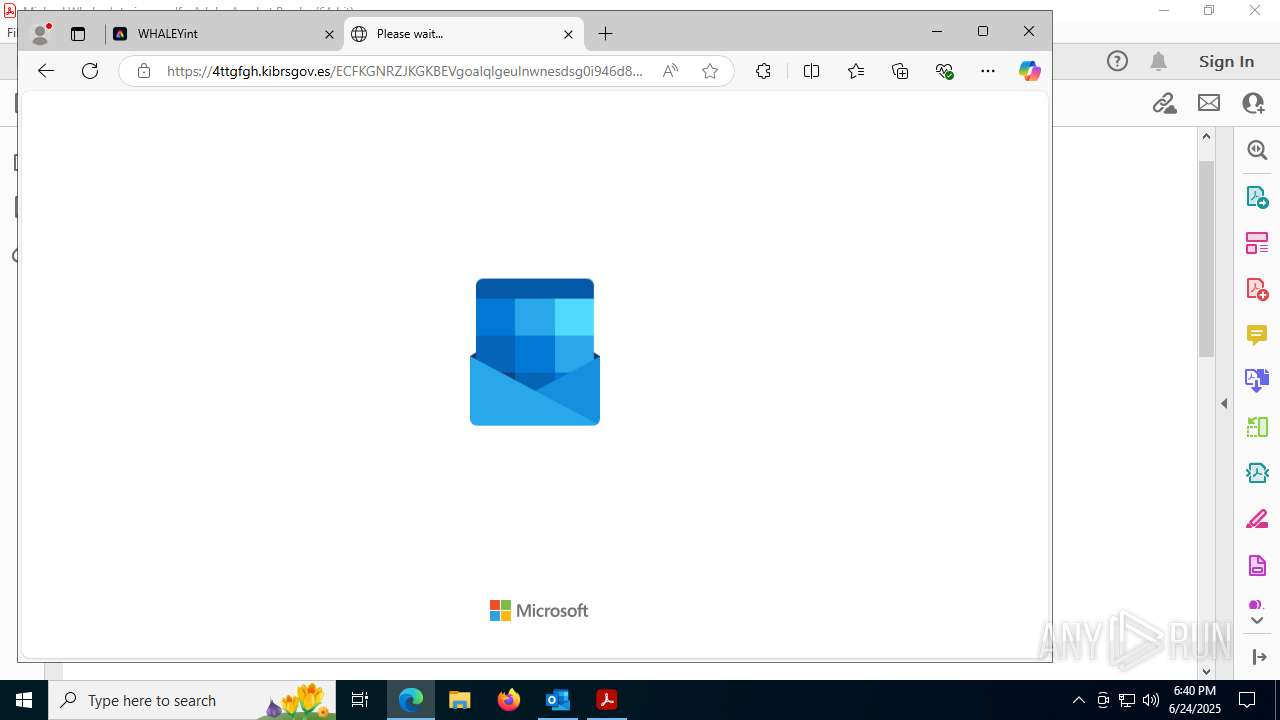
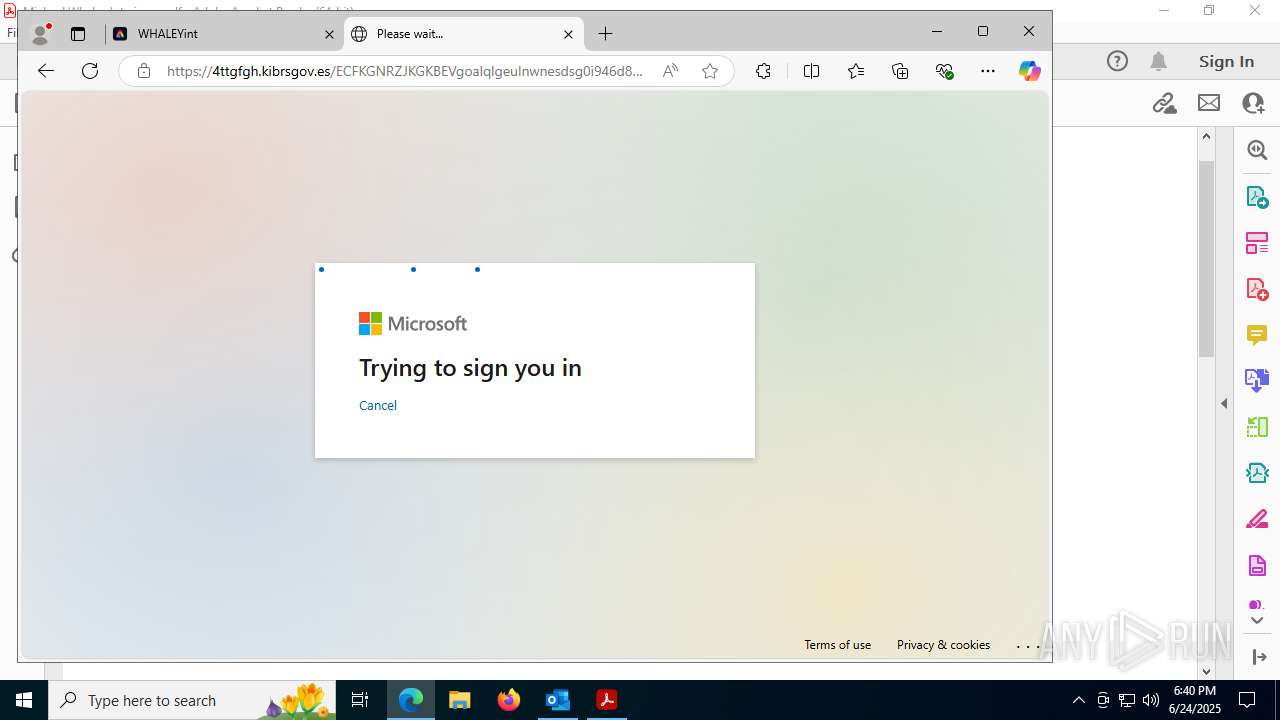
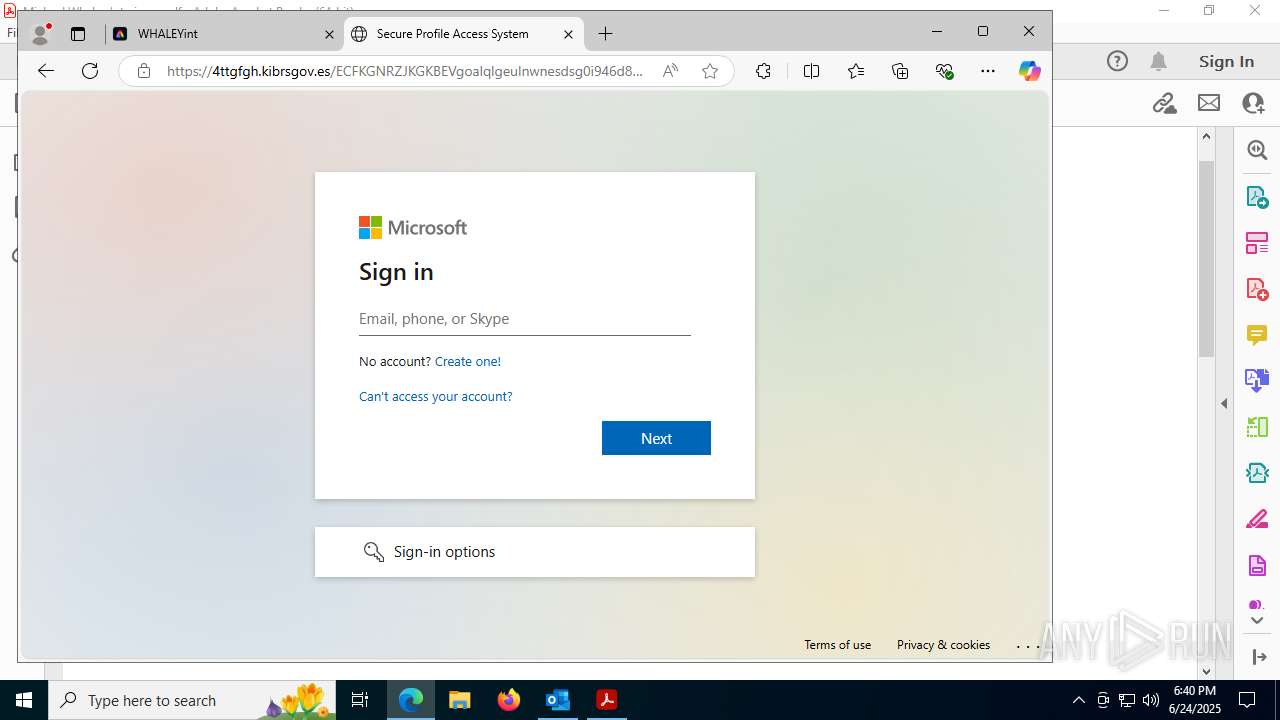
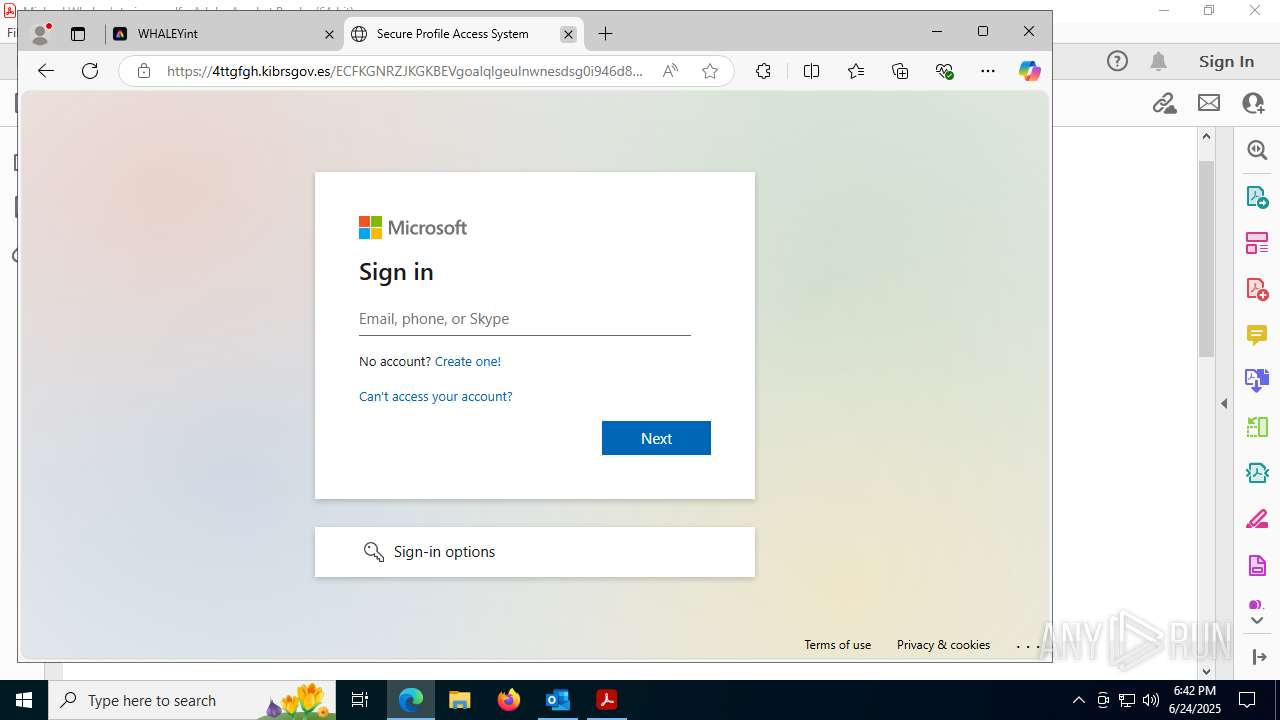
| Threats: | Sneaky 2FA is an Adversary-in-the-Middle (AiTM) phishing kit targeting Microsoft 365 accounts. Distributed as a Phishing-as-a-Service (PhaaS) through a Telegram bot, this malware bypasses two-factor authentication (2FA) to steal credentials and session cookies, posing a significant threat to individuals and organizations. |
| Analysis date: | June 24, 2025, 18:38:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | B2994C093C9B265C7B9995E78FDD3DBD |
| SHA1: | 5E53081429E6783F3C885444E796419FC9DA68B4 |
| SHA256: | 3CC2914D1D1497BA1051F6A8E65B5644C334A8E5DA03672280D957FDCF10C1D1 |
| SSDEEP: | 1536:fV1Rscv3/HSL3gEVyYpNZWhvWaWhWU5WhdWkb1FlwZvwQNVa4nauP+3WeRrh460Q:fV1RscP/H0G1PC5pNVa/kihBIgCpU5/ |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 7600)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- AcroCEF.exe (PID: 7260)
INFO
Application launched itself
- msedge.exe (PID: 8144)
- Acrobat.exe (PID: 6224)
- AcroCEF.exe (PID: 1336)
- msedge.exe (PID: 5340)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 620)
- Acrobat.exe (PID: 6472)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 620)
Checks supported languages
- identity_helper.exe (PID: 6980)
- identity_helper.exe (PID: 7136)
Reads the computer name
- identity_helper.exe (PID: 6980)
- identity_helper.exe (PID: 7136)
Reads Environment values
- identity_helper.exe (PID: 6980)
- identity_helper.exe (PID: 7136)
Checks proxy server information
- slui.exe (PID: 8012)
Reads the software policy settings
- slui.exe (PID: 8012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
203
Monitored processes
56
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7400,i,11867381253629121288,13967102175720730828,262144 --variations-seed-version --mojo-platform-channel-handle=6200 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 420 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2284 --field-trial-handle=1636,i,12548405726221333061,11064328814794912095,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 424 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=5264,i,8526632107749359368,8646391721117469322,262144 --variations-seed-version --mojo-platform-channel-handle=5248 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 620 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --string-annotations --gpu-preferences=UAAAAAAAAADoAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=1344,i,11867381253629121288,13967102175720730828,262144 --variations-seed-version --mojo-platform-channel-handle=6676 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1336 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\FW MWI Series C - InvestmentFunding IV.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1544 --field-trial-handle=1636,i,12548405726221333061,11064328814794912095,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1984 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2352,i,8526632107749359368,8646391721117469322,262144 --variations-seed-version --mojo-platform-channel-handle=2348 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x294,0x298,0x29c,0x28c,0x2a4,0x7ffc3cf2f208,0x7ffc3cf2f214,0x7ffc3cf2f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
35 435
Read events
34 752
Write events
595
Delete events
88
Modification events
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsData |
| Operation: | write | Name: | SessionId |
Value: 48F7FD1D-AA86-40C8-B758-3FB1FFC5B2AD | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\1732 |
| Operation: | write | Name: | 0 |
Value: 0B0E101DFDF74886AAC840B7583FB1FFC5B2AD230046C09CA9BBF3A6F9ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511C40DD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (1732) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
347
Text files
111
Unknown types
81
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1732 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 1732 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\IW113ZNH\Michael Whaley Interiors._ (002).pdf | ||
MD5:BB6A4DB307E361F7D90C44AD8554B857 | SHA256:E4E9446E62551A9FE686BAF34EA632EFD3A195FC08784CD75262F60F9222007A | |||
| 1732 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:CB65D48A8124AE38E9247C5E65DC42EF | SHA256:875CE3CCB76F699E4558EF25BE552A37E20686C591E1150B5F7B0161EEF988F8 | |||
| 1732 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\DD3D7ABE.dat | image | |
MD5:C3B8663217640285F88EDF7CD6438EC8 | SHA256:9B09964FB03C62CE2F3166AAD0BAD2FAEFD089416EAD8D3B46C7FE068C72F210 | |||
| 1732 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:62BACEE40537F1B0F3F8297F9C0A0574 | SHA256:61CB04375A54CC1E6F0DDD3D6D54FDC5929336F670A097D81DF688135005CCCD | |||
| 1732 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:9569432C3E3BF0C9E9EF41711710CC6B | SHA256:1811A4DA4DBE73237F3C6DC8A80C30CDE528F01C28A99BFEC2CE5E0367B49A39 | |||
| 1732 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 1336 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old~RF178c90.TMP | text | |
MD5:D012E5B4EB91B61F6E8AE2F8EC3C623E | SHA256:1BDA750084F20306722008016420E1912BA608CA8EFB9C661F7E7EFCF5E89673 | |||
| 6472 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\NGLClient_AcrobatReader123.1.20093.6 2025-06-24 18-39-00-671.log | text | |
MD5:460C6041966002D8384A18C895A65EB0 | SHA256:C83EC6E8FB3EC62481289C033238C1D9B08DB8076EAAD304099FD7A7F594F1B9 | |||
| 1732 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:EAB306BEAA18DF39981D8916E3DDC506 | SHA256:AD54849C320DA886EB40A232294075130710F85BC7DC46286E7CDDFFCEDF5CDF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
137
DNS requests
150
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.192:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
436 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1732 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
7860 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7600 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:3Wj8OycXG09DUXfI-lphsm8mLqJaUDK9EwJenrxYiTs&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6496 | svchost.exe | HEAD | 200 | 208.89.74.31:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1751024772&P2=404&P3=2&P4=E7DFoZsO3uhYuRYzRWh4eLyV787ScnguJqJ1PiE3gbVVFfjhq3MjAMPP5BJhrIUjqTxKgc50cDEpAIMO6L7rDw%3d%3d | unknown | — | — | whitelisted |
6496 | svchost.exe | GET | 206 | 208.89.74.31:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751024771&P2=404&P3=2&P4=Kl9s2HBbC0ccZn5xiFP7jDUEpClz%2f2OIXwSY%2fHhEV3FgtBNF%2fAU7qhsaYbw8aqz2xcAac6qGWklTIXYP%2fbilNg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7152 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1732 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1732 | OUTLOOK.EXE | 2.16.10.163:443 | omex.cdn.office.net | Akamai International B.V. | AT | whitelisted |
1732 | OUTLOOK.EXE | 52.111.236.4:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.192:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to sentry .io |
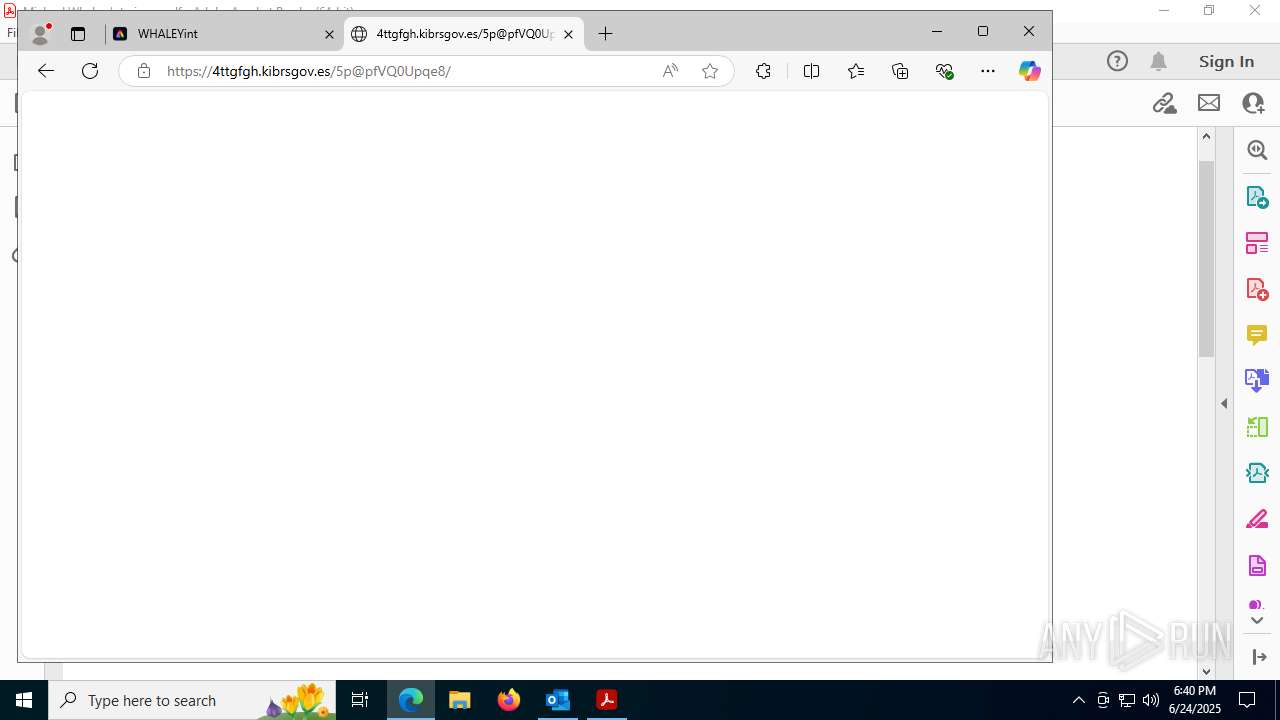
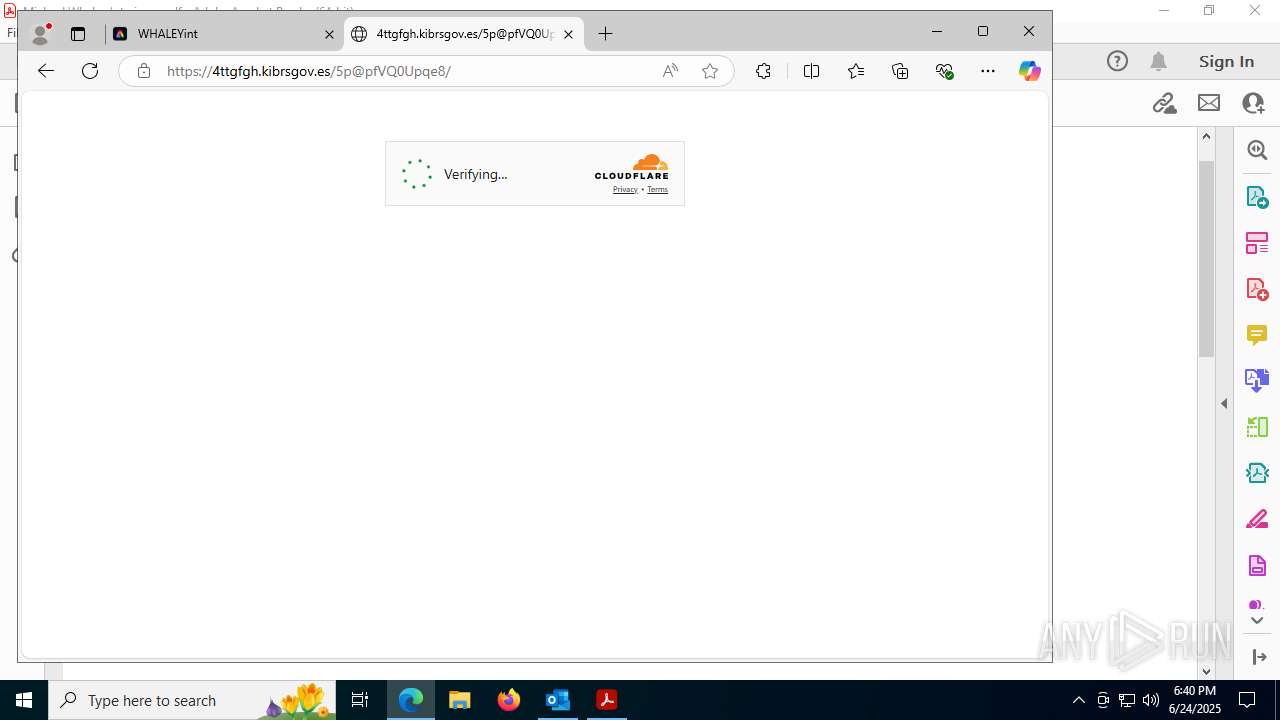
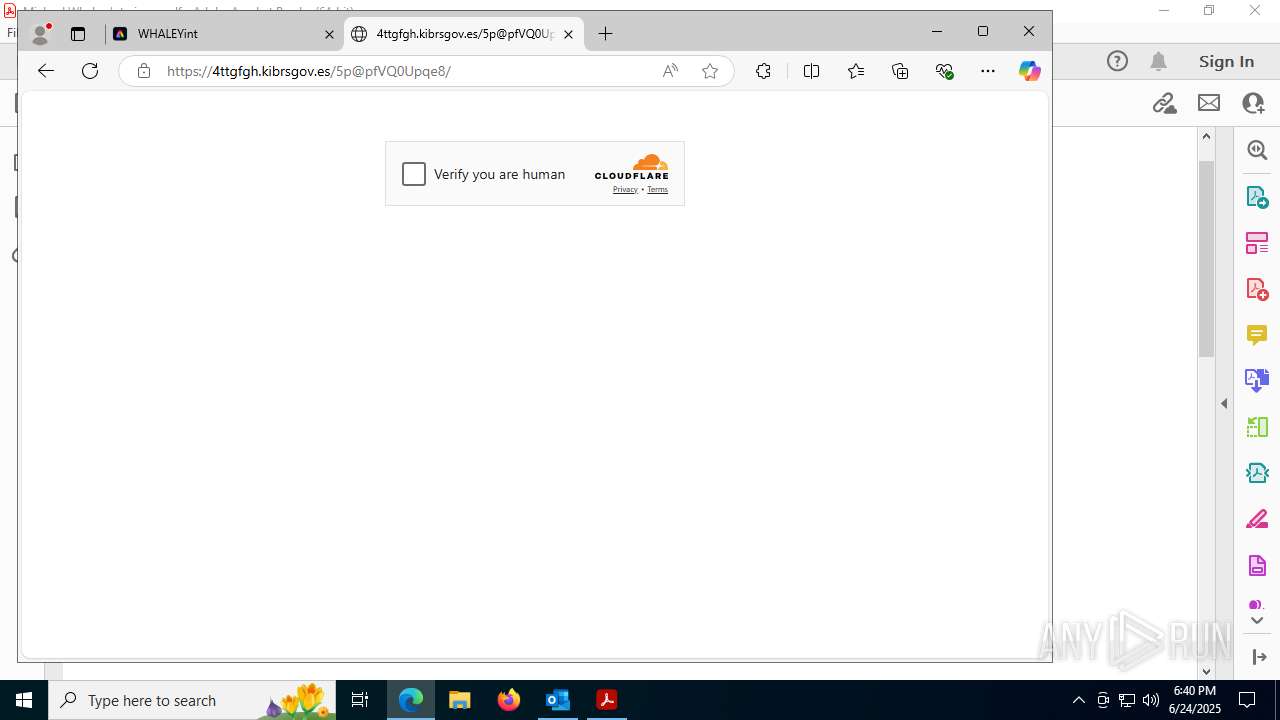
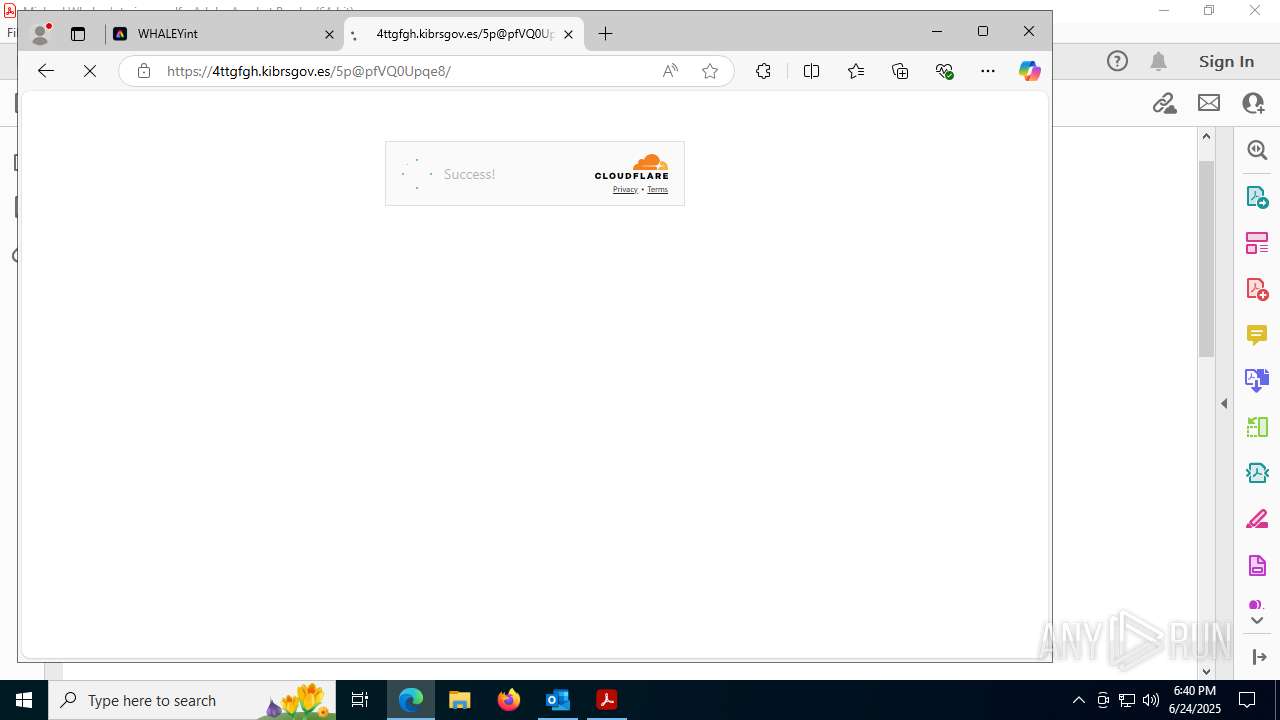
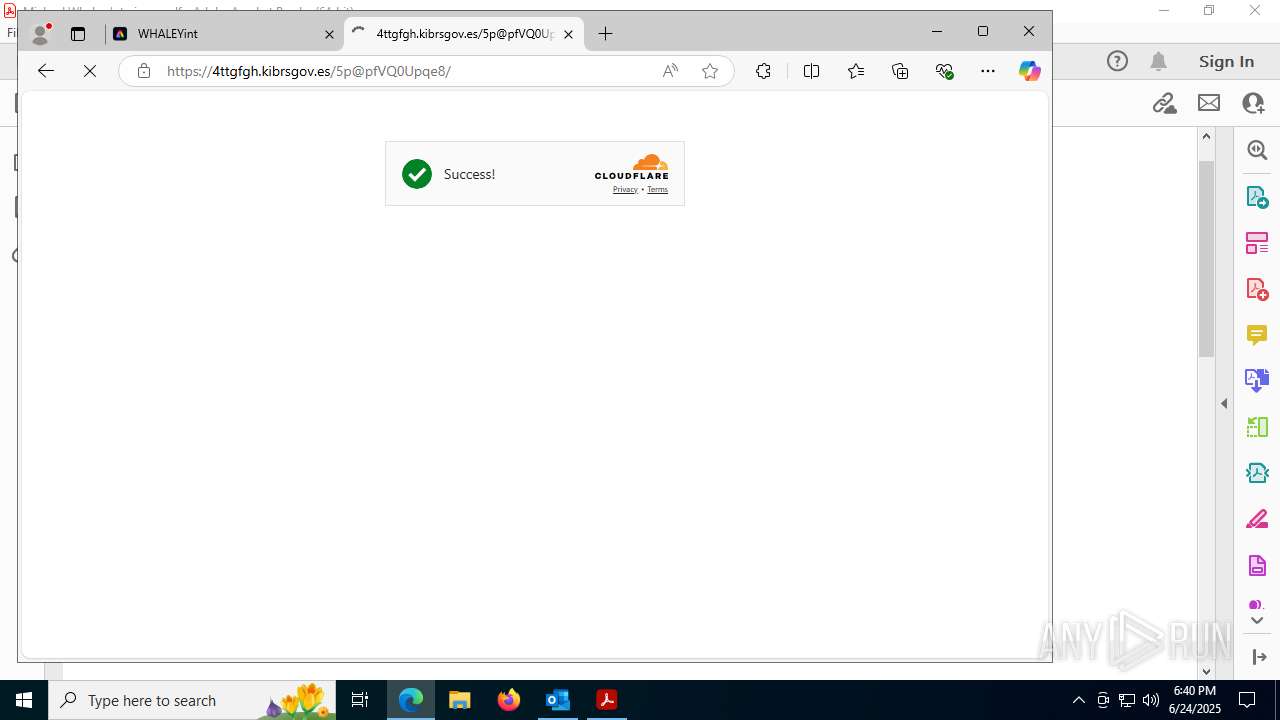
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7600 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain (eeacukybnpjg .es) |
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7600 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |