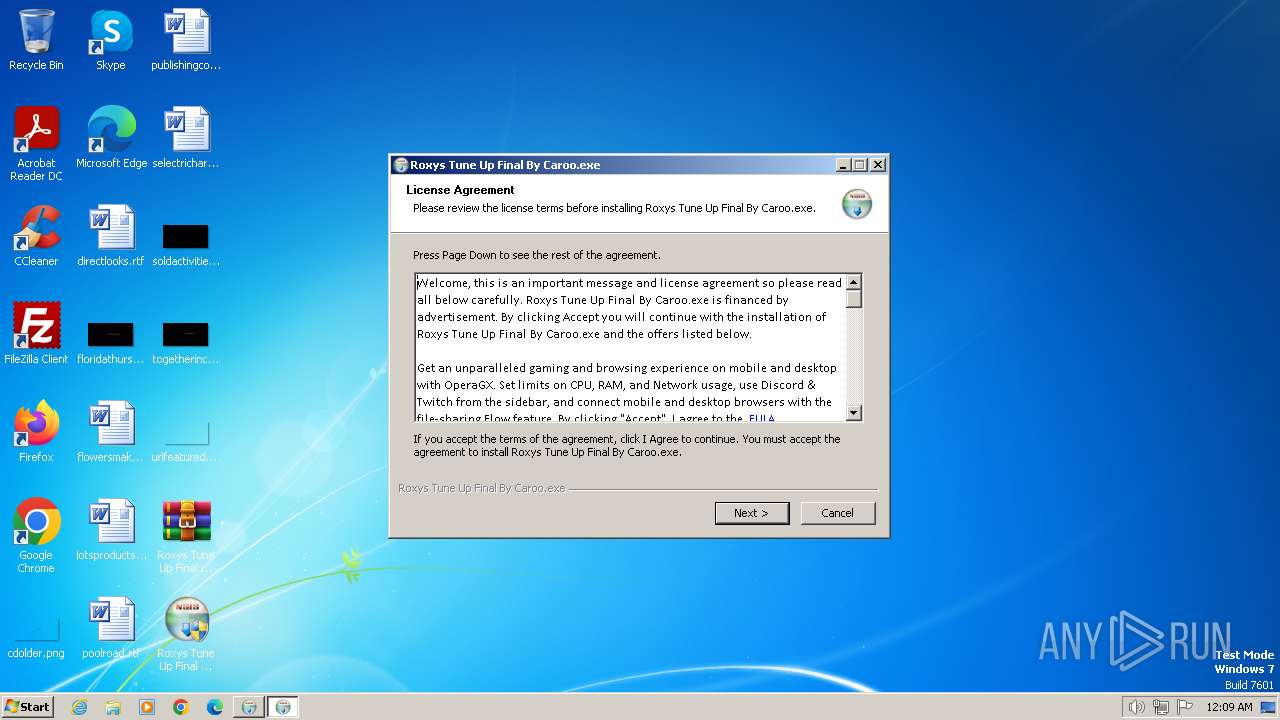
| File name: | Roxys Tune Up Final By Caroo.zip |
| Full analysis: | https://app.any.run/tasks/7637a363-87f7-477b-9202-be4dfd6560bc |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | February 16, 2024, 00:08:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | B544746428B3A29863225C2B7F0F96BE |
| SHA1: | D3E29319D1BE4BACC09586D7850E6306CBC41113 |
| SHA256: | 3CA5B8D552162E24287913AEED328077BF1E12E5D1491EAB303A1E28F6FFE6AA |
| SSDEEP: | 98304:Rw6S5TQC73REIxBfQtdOESn18u2KK8/PqIo/zM0aGX/TK6sj83vDAlJH8QAWDCGI:oEaXLF6KkNh1hjD5nXGCuhQsSsxI0U8w |
MALICIOUS
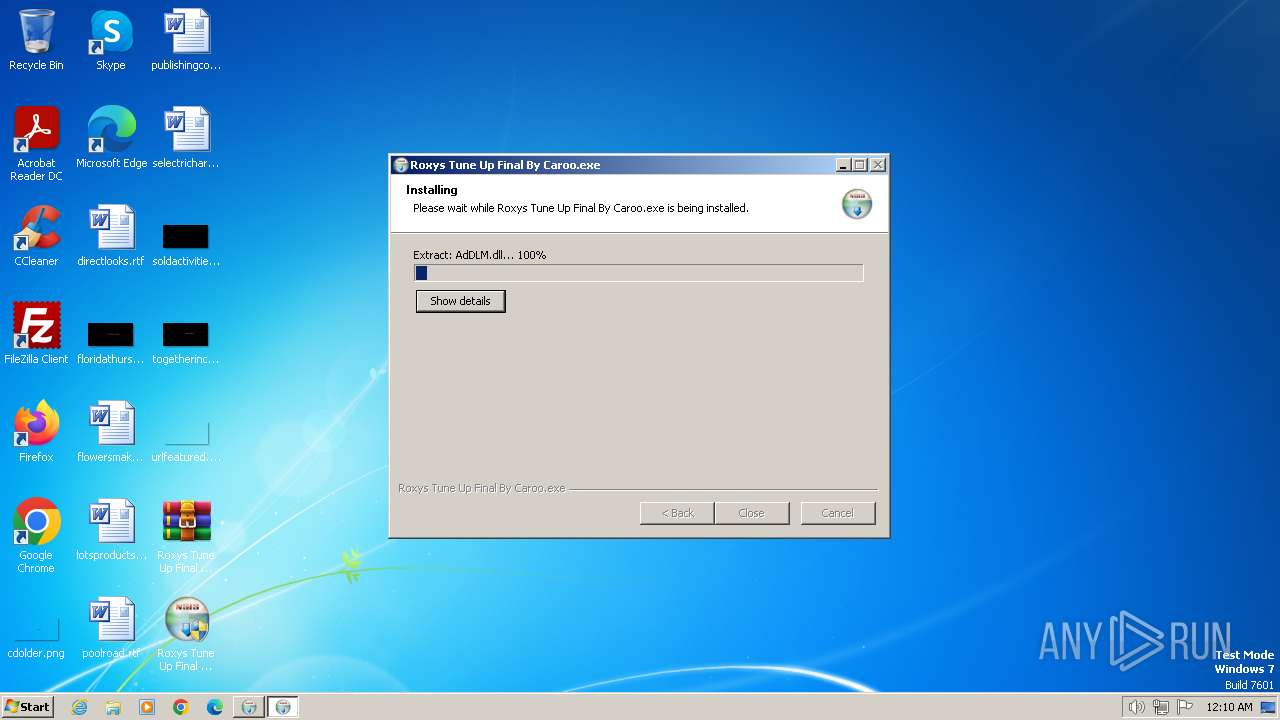
Drops the executable file immediately after the start
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
- set_2.exe (PID: 3256)
- set_2.tmp (PID: 3132)
- set_3.exe (PID: 2416)
- cmd.exe (PID: 584)
Changes the autorun value in the registry
- set_3.exe (PID: 2416)
Lu0bot is detected
- fghnmuro.exe (PID: 3456)
LU0BOT has been detected (YARA)
- fghnmuro.exe (PID: 3456)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
Executable content was dropped or overwritten
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
- set_2.exe (PID: 3256)
- set_2.tmp (PID: 3132)
- set_3.exe (PID: 2416)
- cmd.exe (PID: 584)
The process creates files with name similar to system file names
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
Reads the Internet Settings
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
Reads security settings of Internet Explorer
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
Checks Windows Trust Settings
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
Reads settings of System Certificates
- set_1.exe (PID: 3508)
- go.exe (PID: 2672)
Reads the Windows owner or organization settings
- set_1.exe (PID: 3508)
- set_2.tmp (PID: 3132)
Probably fake Windows Update file has been dropped
- set_1.exe (PID: 3508)
Adds/modifies Windows certificates
- set_1.exe (PID: 3508)
Process drops legitimate windows executable
- set_3.exe (PID: 2416)
- go.exe (PID: 2672)
Starts a Microsoft application from unusual location
- set_3.exe (PID: 2416)
Starts CMD.EXE for commands execution
- set_3.exe (PID: 2416)
Executing commands from a ".bat" file
- set_3.exe (PID: 2416)
The executable file from the user directory is run by the CMD process
- fghnmuro.exe (PID: 3456)
Uses REG/REGEDIT.EXE to modify registry
- fghnmuro.exe (PID: 3456)
Process requests binary or script from the Internet
- go.exe (PID: 2672)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3784)
- Roxys Tune Up Final By Caroo.exe (PID: 3228)
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3784)
Reads the computer name
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
- set_2.tmp (PID: 3132)
- fghnmuro.exe (PID: 3456)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3784)
Checks supported languages
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
- set_2.exe (PID: 3256)
- set_2.tmp (PID: 3132)
- set_3.exe (PID: 2416)
- fghnmuro.exe (PID: 3456)
Checks proxy server information
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
Create files in a temporary directory
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
- set_2.exe (PID: 3256)
- set_3.exe (PID: 2416)
Reads the machine GUID from the registry
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
- fghnmuro.exe (PID: 3456)
Creates files or folders in the user directory
- Roxys Tune Up Final By Caroo.exe (PID: 4008)
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
- set_2.tmp (PID: 3132)
Reads the software policy settings
- go.exe (PID: 2672)
- set_1.exe (PID: 3508)
Reads Environment values
- set_1.exe (PID: 3508)
Creates a software uninstall entry
- set_2.tmp (PID: 3132)
Reads CPU info
- fghnmuro.exe (PID: 3456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lu0Bot
(PID) Process(3456) fghnmuro.exe
С2 (2)aoa.aent78.sbs
otl.dwt51.shop
Strings (5428)bec296d7
*.aoa.aent78.sbs
a15a30
*.otl.dwt51.shop
require
mainModule
require
crypto
path
sep
dgram
child_process
env
kkqQK
toLowerCase
toLowerCase
env
object
ignore
LtGvd
cmd.exe
sMmIQ
kXvGa
stdio
tMclg
detached
windowsHide
env
env
env
env
slice
bTZxp
yZSge
LtGvd
error
unshift
unshift
unshift
unshift
NQuND
shift
spawn
unref
1|0|4|2|3
aes-128-cbc
0|2|4|9|7|1|3|5|8|6|10
cxMkW
pjWZu
DICsf
pGXIs
undefined
network service
system
dwm-
umfd-
4|0|5|1|2|3
recv
MPgki
XqUDi
JVNmK
zfOnl
gFBGP
yRVKu
PfxvL
function
vlJwB
object
pipe
error
close
data
tDEib
VFEfw
XxwCi
LxuNH
kusvC
split
createDecipheriv
hseCH
slice
slice
readFileSync
prs
parse
toString
concat
update
slice
final
ZTqma
kYLhx
stdio
pfaAU
detached
windowsHide
env
env
env
env
slice
shift
spawn
timeout
ktmr
GQACy
cRUYZ
Gexcv
nWyxV
GvVll
split
vfgbj
QlYdH
length
length
slice
createDecipheriv
aes-128-cbc
slice
concat
update
slice
cNlWp
final
slice
toString
readUInt16BE
Zguja
readUInt16BE
kill
timeout
once
UdtNy
wsNlv
lDaxa
lDaxa
readFileSync
toString
trim
error
once
exit
cRUYZ
rATUx
xQysc
out
outbuf
toString
outbuf
err
errbuf
toString
errbuf
Zguja
FlPEc
code
BnrJX
FlPEc
signal
once
tydwx
JsmSC
YqfrZ
RIxZu
ABtuw
Bdpva
yInad
yInad
ktmr
YAyca
GPmyS
SJwRN
LXWId
split
tkstp
Oijou
CWYjd
log
FVyzW
ktmr
ktmr
error
YAyca
zfOnl
Owqzr
lRqKX
error
error
error
FlPEc
code
Yatfa
FlPEc
signal
outbuf
concat
outbuf
errbuf
concat
errbuf
returnbuffer
OaEuJ
qEqSu
qEqSu
out
outbuf
toString
outbuf
err
errbuf
toString
errbuf
GQACy
nostr
out
usr
toLowerCase
JSOAq
YCGlr
FZiBp
OnAlj
local service
OnAlj
substr
length
WgbBY
indexOf
IxbMn
indexOf
kFMDn
isc
stdout
ulxyl
KzJCu
yRVKu
outbuf
outbuf
push
kTkBT
ppid
length
tree
stderr
ulxyl
eVNTF
eVNTF
Quad
outerr
outerr
push
5|4|0|1|2|6|3
WAZNm
split
push
eedYo
pid
name
ppid
nUpFq
length
dSgEB
ppid
1|2|5|0|4|3
\.\
6|0|2|3|4|5|1
LIgQM
KaaYb
OzoOi
emFnJ
fAkmu
commandline
executablepath
path
parentprocessid
ppid
processid
pid
name
Console
Services
GnTMX
zahzt
wmic
process
processid,parentprocessid,name,executablepath,commandline
/format:csv
release
aEkDs
indexOf
aEkDs
indexOf
6.0
kYzTg
bZKcg
rjDJx
pGaOT
get
xuody
PKLZr
8|7|3|10|1|9|6|4|11|0|5|12|2
DdpNv
aes-128-cbc
EQmZJ
DdpNv
ZNykT
LIgQM
LHzbp
VvWvI
length
VvWvI
split
join
split
length
length
shift
FbZXd
indexOf
Node,
dofpm
CcFPJ
CcFPJ
split
shift
KGmKJ
length
dofpm
bPCGD
bPCGD
split
YYZXb
length
length
IEKzi
OUqBU
JRwSK
split
AGrFq
substr
substr
mailw
indexOf
split
join
sSSmm
indexOf
hkejH
split
hkejH
join
AGrFq
length
MLMQy
substr
MLMQy
substr
WYSgm
length
substr
WYSgm
length
KGmKJ
length
QYBMU
UjeCI
fAkmu
toLowerCase
Iqmmu
args
length
xFian
YIaAc
length
YIqbS
ZqIDL
zXMJw
dXxEn
FNpWy
FNpWy
lFeRh
split
aSqbE
concat
from
alloc
YQQsa
length
concat
alloc
concat
update
final
randomBytes
createCipheriv
TfmZJ
slice
writeUInt16BE
aSqbE
ycoNF
VsjRt
pid
Node
pid
QYBMU
DeBug
tIjpV
file
pid
session
path
DrzmM
sDGUq
VOZPV
BljbF
BljbF
pid
tvZrb
split
ppid
ppid
session
push
pid
push
path
path
length
path
name
push
args
args
env
dofpm
toLowerCase
toLowerCase
env
readFileSync
orUvy
aOcxU
wAWEM
bZKcg
ppid
length
tree
writeFileSync
VvWvI
4|1|5|7|2|3|0|8|6
windir
systemroot
appdata
username
\networkservice\
gxDqW
system
local service
dwm-
umfd-
oLhYY
isc
nQZeX
Odhqr
tmp
DYbGi
temp
aup
DYbGi
allusersprofile
apd
dbhey
YWYOS
usr
PthEC
BDTdo
tmp
isc
isc
uDtMm
tmp
toLowerCase
indexOf
toLowerCase
isc
isc
CSZgU
tmp
toLowerCase
indexOf
JZRGd
isc
isc
aup
apd
isc
isc
usr
isc
isc
uDtMm
fEIKp
VPbWP
ZxrvQ
PJnFv
eYtIG
PJnFv
BAtEm
lfrmb
OWALX
usr
toLowerCase
BAtEm
network service
YYFNJ
rwUhe
lXUIV
VGezj
substr
AEGLd
length
uDtMm
indexOf
tdNgZ
JMEVl
indexOf
ItSne
QEuXz
QEuXz
JWWok
split
BkDsm
BkDsm
apd
\Microsoft\Windows\Start Menu\Programs\Startup\
OlcaD
LTmxs
uYdLv
.lnk
LTmxs
aup
LiqkS
LTmxs
LiqkS
XXOoM
FXPWu
dQQqq
chNfo
.exe
CYqnl
yJTvk
chNfo
yJTvk
chNfo
MhxdK
zRMjE
MvRHK
DYbGi
sfmHq
tmp
mkdirSync
isc
sha256
createHash
pTrXD
update
digest
8|0|2|5|3|6|7|4|9|1
u
computername
LfMEK
split
userdomain
concat
CnbzX
username
Ctldi
push
lJrQw
Tjamo
Tjamo
AoTnt
dfPcw
TdXlT
prototype
slice
call
floor
eVhEZ
pop
ELHkP
fromCharCode
EveLs
ZwxmU
IdmBH
0|2|9|1|3|7|8|5|4|6
hex
Microsoft Root
Washington1
Undefined
9|0|1|5|15|2|8|13|12|4|3|10|14|6|7|11
string
false
mMjiq
eWOCF
ZCRCK
XBuqs
aQcer
gubLS
win32
linux
darwin
openbsd
freebsd
intel
core(tm)2
amd
i3
i7
ryzen
threadrip
kvm
qemu
md5
DESKTOP
PLNvG
nLutb
art-pc
work
amazing-av
bea-chi
shadow-
JTAPJCC
azure-
janusz-
compalexey
dillon
anna-
gary-pc
mars-pc
host1
administrator
admin
frank
george
shadow
straznj
john doe
cape
goatuser
azure
janusz
stark
a.monaldo
peter wilson
Unknown
Intel Undefined
Intel Celeron
Intel i3
Intel Pentium
Intel i5
Intel Core(TM)2
Intel i7
Intel i9
AMD EPYC
AMD Ryzen
AMD Threadripper
AMD Undefined
CPU KVM/QEMU
uOyYL
TlIxm
Duo
sVMrk
Quad
dxyrt
NOHID
my_pc_
AMAZING-AVOCADO
cape-pc
DESKTOP-JTAPJCC
Host1
NOUID
user
john
lisa
STRAZNJICA.GRUBUTT
harry johnson
joe smith
alexeyzolotov
UNKNOWNUID
TczCR
alloc
floor
sFtkG
writeUInt8
VdDqG
round
kOVrL
ujsQv
XyTeK
yTwow
WlkMX
WlkMX
KOjRt
RYbVh
yTwow
tgmNF
eWOCF
lQTZv
Pkamt
AXQAl
SMsOq
MxffE
zMYIb
FmSLS
bJLNg
yTwow
lhEVa
lhEVa
JmzUv
gDAud
lKxqQ
lKxqQ
env
sfxname
length
basename
toLowerCase
FvSgy
EGLEn
aQcer
nexyZ
push
iXjUI
vnMtQ
vnMtQ
pid
name
ppid
XyTeK
length
KKQIq
ppid
WrcMe
WrcMe
isc
oDwWu
writeUInt8
length
split
min
RfNmo
min
VPxiM
min
VPxiM
writeUInt8
VdDqG
IvuYz
CJHpC
writeUInt16BE
VdDqG
join
round
KOjRt
writeUInt8
ixJYF
ceil
VLXEb
BJaaT
FmSLS
xjNJk
LEwSy
XcWiW
LEwSy
Izzpi
freebsd
unknown
BJaaT
xjNJk
XcWiW
Izzpi
yIEYk
sFtkG
sFtkG
IvuYz
CJHpC
tJyHd
EjvXb
writeUInt8
length
toLowerCase
indexOf
fGMis
indexOf
celeron
XyTeK
indexOf
pentium
XyTeK
indexOf
oBPjY
XyTeK
indexOf
qDNRf
indexOf
amd
indexOf
atom
XyTeK
indexOf
fWACv
etIfn
indexOf
i5
etIfn
indexOf
udxZM
QioCy
indexOf
i9
QioCy
indexOf
xeon
indexOf
epyc
indexOf
EiOvA
QioCy
indexOf
BVObA
indexOf
TxDpH
indexOf
iyTeE
ceil
KOjRt
VLXEb
writeUInt8
ixJYF
dmvmZ
CJHpC
createHash
NuyJp
update
digest
slice
toString
ALsuD
copy
length
split
toLowerCase
BnZfZ
length
KKgWI
ajXgh
Nvniv
hnyHa
pid
SFcee
indexOf
my_pc_
KKgWI
eMkOG
QibNf
gIyhj
cGzaM
indexOf
KlmXX
cGzaM
indexOf
GIubH
indexOf
latCD
sNwln
cape-pc
sNwln
hGpBW
uQnLf
indexOf
qiuvY
UEvdp
indexOf
DnuGh
TnLkS
snStM
TnLkS
IwkLi
UEvdp
indexOf
UJDaJ
AbINF
ZAixD
ESJDi
mhUvr
ArwxU
writeUInt8
JOaJe
createHash
md5
update
digest
slice
toString
ALsuD
copy
length
split
toLowerCase
gLiWK
qipwj
eHDTB
qipwj
user
UTfDf
john
XFVSl
AYurx
lisa
XFVSl
FXUxs
PApRT
LqPub
UEvdp
indexOf
hybJa
QZxjk
harry johnson
xoQjT
joe smith
qQrpG
tadOh
GEMBV
kOyhb
xQCTj
Sqnyt
tAdIM
usMtr
tAdIM
zwklL
tAdIM
FUmYe
alexeyzolotov
tAdIM
grMRI
writeUInt8
JOaJe
createHash
NuyJp
update
digest
slice
toString
hex
copy
FaQPJ
tMQVB
rLxQk
pvAGe
umEoI
qeBHR
WhsSH
Pbqxt
Intel Atom
IXHhL
Intel Xeon
JuDMM
IrmFS
WZrEP
mEctU
xpfRS
ysbFO
ysbFO
iEhoo
WTVJp
kfJLZ
vpqoA
euvmM
split
eaCUc
\Fonts\micross.ttf
length
length
toString
ALsuD
indexOf
from
yFfMr
toString
ALsuD
from
nTkkM
toString
ALsuD
raejC
indexOf
readFileSync
ysbFO
EJrRd
sVMrk
LvPDy
vUmrW
floor
IYEfI
ujsQv
pop
vkIIF
dxyrt
TJwHr
JaJQn
JaJQn
ZveNe
rnrYN
meqhC
ajXgh
nONOO
art-pc
gIyhj
gxRrL
GIubH
latCD
kPiJG
gELzm
qiuvY
janusz-
CompAlexey
IwkLi
UJDaJ
gary-pc
ESJDi
lNbyP
UNKNOWNHID
CTpyR
CTpyR
NYqdQ
gLiWK
admin
JIGlA
wVtSt
frank
czChl
FXUxs
LqPub
NxaIj
ZsBZi
YmjTL
tadOh
GEMBV
goatuser
Sqnyt
usMtr
stark
FUmYe
TichM
peter wilson
KjZkY
CTpyR
GIBEN
Fjarx
Fjarx
YiLAo
split
pmFXb
OWDHi
length
split
YUyGo
length
FmSLS
gjaQA
isArray
length
toString
hex
9|7|6|5|10|11|4|2|0|13|3|8|15|1|14|12
string
false
OqewN
split
length
split
jpVzK
KRDje
length
isArray
length
TURKe
fKSJf
76|18|171|20|93|94|40|70|12|53|144|123|167|88|67|112|172|100|163|22|15|148|57|108|135|37|89|125|21|121|178|61|92|181|183|65|10|164|5|27|69|157|98|1|78|187|131|68|71|59|134|73|3|127|140|117|173|104|9|118|175|86|43|84|72|11|16|66|7|79|41|110|159|39|153|122|30|2|119|176|19|147|44|33|136|6|25|13|190|48|...
e32aca
win32
10.0
804a
DESKTOP
frank
b445bf
lisa
10.0.19041
2a4494
10.0.15063
2970
8e776c
10.0.22621
8920
0cbc66
10.0.19044
6.1.7601
NOHID
john
10.0.19045
6d05
6cfdbc
b38e56
6.1.
STRAZNJICA.GRUBUTT
4f81e3
b75705
janusz-
janusz
Xeon
061613
user
stark
b1a8
7db39b
10.0.18362
NOUID
9a50
351468
mars-pc
administrator
Host1
b71c
admin
709b
52acd9
0fdc
cc1a
18275d
f5faf7
6e64
7aed
851c
b0f8e1
7c1a
cd4ec1
1cce9e
10.0.17763
3322
bca236
c589
a65640
5bc06f
e717
646a8b
86438b
10.0.18363
7f8794
3635
24889e
18126e
5803c5
72f6c0
1e75
5fd4c0
10.0.22000
a98d
efba14
930d8a
167bfe
azure-
95deb5
d04f74
2bf408
cb0013
AMD EPYC
10.0.10240
7e73
70b4
d580
32b1d5
c350
db9a51
64ca98
953225
9d5196
48fdf5
6adf97
CompAlexey
badfad
1285
abcf10
b3c775
10.0.16299
570a90
4b9de2
dillon
peter wilson
KVM/QEMU
bc54f4
aff8
9f72
bd9ff1
10.0.19042
fb6ab4
10.0.17134
DESKTOP-JTAPJCC
ed6464
george
a739
75c891
55d8
AMAZING-AVOCADO
harry johnson
3219
9db1e4
93a77b
275dec
16a7c1
39549c
100
anna-
97a9d3
101
2cd67e
3e45fc
103
6.3.9600
72e748
104
106
471915
107
86131a
108
109
10.0.19043
110
11d4d6
2253
e8c630
3f9b99
112
c8b63d
114
f4cb33
115
8818
40c7c9
ee7e47
116
8fdf0b
117
EPYC
shadow-
shadow
joe smith
119
25cd40
59a422
32b5
121
122
123
10.0.10586
124
4f5cec
125
7bf5
2cb5a5
f3f0c6
033bd9
cc9adb
130
13b4
ab86a1
dc599a
56d4
d33e1f
9ec750
e06b
6a29b3
133
a888
2001f7
134
bea-chi
john doe
135
cd4ee8
7fa24d
56aee3
4b418f
74529b
835669
137
436f
138
a6f2
5b2e9c
a592e8
0b6631
f1dd
141
a4757d
142
41c07c
143
4ed984
2652ee
144
145
146
147
2088
148
2be941
149
150
6bd1
bb2e4c
151
d0062c
e8b9
fca565
153
379a7d
155
156
157
e379b3
72c1f0
158
159
160
dd15
6e6551
161
c037
b4a2c8
162
2988b8
164
50ab44
9639a3
165
9ca5a0
166
299243
d1457b
167
3151
00181a
a8776a
e94c92
9ab4de
129654
168
c23200
169
10.0.
b624
03fea1
4b33b6
4085c6
171
172
35ae2e
d8716f
173
my_pc_
7b7cd2
175
176
177
b5a0
73a080
52c9
bf0760
9114
9a8599
181
990d1b
582a34
183
184
3a83fe
d38e35
185
f6b8ae
186
#56d4#
62efb9
b7e24d
189
190
191
9b6b46
4d42bf
e2c5
iuWdE
split
win32
lNCyL
wXfbo
APGCS
10.0.19045
qkFFT
qkFFT
qkFFT
juVxf
qkFFT
nkHtm
unqfu
gAofR
indexOf
IiUiW
10.0.18363
qkFFT
SQoXG
qkFFT
indexOf
Smcvn
indexOf
XTlhF
qkFFT
win32
jtqFc
qkFFT
6.1.7601
Rnqwk
WyCPh
indexOf
xBcMn
nkHtm
qkFFT
qkFFT
pXhMv
GCxmg
tcHFx
pXhMv
nkHtm
unqfu
wyWJh
FLbUR
VgboZ
FMAEP
fADAG
xjsIC
ZWpkn
tlxbi
win32
unqfu
soXWL
WyCPh
indexOf
10.0
indexOf
Smcvn
ZWpkn
sapyT
fnPxU
sapyT
JvjLb
sapyT
TyeMN
sapyT
nkHtm
bRITs
sapyT
3635
sapyT
88dba0
XrgwJ
21232f
ZATKI
nkHtm
ZATKI
ZfNJO
jygMg
WyCPh
indexOf
TsgxQ
indexOf
ouqss
nkHtm
unqfu
CjJgN
jygMg
gCBVX
cIqJl
MyBjC
hDlTR
yTZJN
hDlTR
wwDZk
cUTgp
OyFPs
cUTgp
nkHtm
unqfu
NhjMb
jVVzl
indexOf
UXKZi
bFYVI
indexOf
qlAoI
erGjt
nkHtm
unqfu
NDmui
bFYVI
indexOf
6.1
rpqHr
rpqHr
unqfu
indexOf
Xeon
LRolJ
ymdWo
bLnEI
ymdWo
nkHtm
HqErI
FfocQ
indexOf
CkUvg
indexOf
YxFWI
CcjtC
nkHtm
mrmjZ
indexOf
a.monaldo
6.1.7601
CcjtC
indexOf
jkPda
CcjtC
nkHtm
HqErI
mrmjZ
IUQbB
6.1.7601
UMaBH
UMaBH
GwYcz
bFYVI
indexOf
Smcvn
indexOf
admin
XMJbf
nkHtm
xWgpt
XmsWF
XMJbf
XMJbf
BCXQE
uVUGf
851c
eChvH
VwzPk
YcIqy
nkHtm
OcqMI
XmsWF
ehdNN
indexOf
jkPda
qOKZY
indexOf
Host1
indexOf
uRePG
ylhlb
win32
fexIB
lOQMD
indexOf
6.1.
indexOf
gary-pc
tzCmT
indexOf
mlTLL
ErfCS
nkHtm
ErfCS
10.0.19045
ugJkX
MIeAp
MIeAp
vqVcB
MIeAp
nkHtm
riGMk
MIeAp
pbmin
pbmin
10.0.17134
hDDNL
xCYUI
GOxQg
2088
tzCmT
indexOf
Smcvn
tzCmT
indexOf
uXnuy
nkHtm
riGMk
XmsWF
GOxQg
HCmTQ
WhpIC
QxnlY
ozzaM
nkHtm
QAHug
ozzaM
ZfNJO
tzCmT
indexOf
tQzqD
indexOf
RXGKU
nkHtm
riGMk
TRYRi
riGMk
indexOf
jkPda
tzCmT
indexOf
ZRojL
EoQKe
indexOf
user
jcKDa
nkHtm
UkEPD
gCBVX
gAdSS
MRDGp
oUGLz
oUGLz
c39efd
ayFsh
nkHtm
mWrCU
TRYRi
nceAf
nceAf
xCYUI
amFIj
NeuWw
RWzBZ
NeuWw
NeuWw
NeuWw
nkHtm
oBglk
ScbEz
dgXEv
ZfNJO
tBkvI
tBkvI
VgboZ
tBkvI
oKQFj
ysSfZ
EoQKe
indexOf
NOHID
EoQKe
indexOf
HVBOu
ysSfZ
zjJGH
xuOuU
nkHtm
xuOuU
gCBVX
xuOuU
eaQCk
eaQCk
fKvEi
nkHtm
VnNFw
fYTss
NhwFn
fYTss
zKPBa
fYTss
88dba0
fYTss
grYxf
EoQKe
indexOf
RXGKU
fYTss
win32
VibwL
ZfNJO
VibwL
VibwL
VibwL
Jowwd
f94649
VibwL
nkHtm
10.0.19045
VibwL
AXjWw
hwBcC
PuziB
AENsa
AENsa
747890
AENsa
win32
oBglk
AENsa
ZfNJO
AENsa
keYMX
keYMX
keYMX
WUxTX
keYMX
Rnqwk
LUlYJ
indexOf
xBcMn
erSHC
win32
ScbEz
erSHC
erSHC
JawyL
GzNWe
gjdNY
ZkDHR
Smwvd
Smwvd
YcIqy
Smwvd
nkHtm
fnPxU
kQdTB
czqec
kQdTB
8726e3
kQdTB
WatdR
zHyxZ
win32
oBglk
ScbEz
WKZIW
boawF
boawF
mxzsc
LUlYJ
indexOf
HVBOu
boawF
nkHtm
FubTt
xqZie
XymKD
bRITs
vQJvn
cuqcM
cuqcM
indexOf
DESKTOP
cuqcM
nkHtm
cuqcM
10.0.22621
SRQeF
SRQeF
zrZmA
jlhrZ
vWhEY
723943
vWhEY
nkHtm
ScbEz
oBglk
indexOf
jkPda
QjZYM
ZfNJO
QjZYM
QjZYM
iFJzX
MdEpr
611a3e
LUlYJ
indexOf
RXGKU
qVLnm
nkHtm
sSHkB
eSrQz
vwHXt
ZfNJO
YWnLW
YWnLW
YWnLW
zDDUW
indexOf
jkPda
YWnLW
iturq
OluiC
GihSv
nkHtm
YWYEX
fnPxU
YWYEX
tzfpb
KhTZJ
mcfGu
XdYLo
XdYLo
FwpBs
XdYLo
win32
sHbMr
KAlwD
XdYLo
ZfNJO
uODGk
uODGk
uODGk
krEhy
LUlYJ
indexOf
HVBOu
win32
sHbMr
fPdKA
e1e853
uODGk
6.1.7601
uODGk
win32
sHbMr
fPdKA
uODGk
611a3e
uODGk
ZfNJO
uODGk
uODGk
uODGk
sHbMr
indexOf
jkPda
LUlYJ
indexOf
TsgxQ
MJDeI
indexOf
RXGKU
uODGk
nkHtm
uODGk
MuJJz
HfbaD
HfbaD
gNPFi
HfbaD
nkHtm
fITrR
WIsqM
uUXYD
indexOf
6.1.
indexOf
goatuser
eQnrZ
nkHtm
ZfNJO
eQnrZ
lQtad
FVQXp
ClrNR
mxzsc
uUXYD
indexOf
HVBOu
gNANr
nkHtm
CdmFd
VRqvW
poIFQ
ZfNJO
poIFQ
poIFQ
poIFQ
YNKhx
ctFRO
IbslQ
wrqgR
wFxXs
bot 115 W7 Xeon H 24889e U 18126e
IbslQ
nkHtm
CdmFd
VRqvW
gOUcs
10.0.15063
zdBsP
zdBsP
MrhVz
tKHgV
nkHtm
gCBVX
jtwqr
MjDlU
gzzEi
dYsAa
nkHtm
qpUne
xqZie
KWeWi
bRITs
KWeWi
indexOf
Smcvn
CIFJn
LWMlk
nkHtm
ADiHS
LWMlk
ZfNJO
rZvwS
rZvwS
psaFv
KWJYR
KWJYR
KWJYR
KWJYR
nkHtm
lBCcc
fnPxU
EwbMb
EwbMb
AnhQJ
AnhQJ
jFnlE
VKjje
win32
fYTxo
BlSHy
XJeEK
BlSHy
BlSHy
CZERj
gtWnu
mZKof
gtWnu
nkHtm
gtWnu
IFKOC
fnPxU
IFKOC
NxUvi
jBzfQ
gLUhC
nNriy
d6a5b0
gLUhC
nkHtm
vmBBM
imkrL
indexOf
lYekj
indexOf
azure
gLUhC
ZfNJO
tQgzE
ERcbZ
indexOf
jkPda
nkHtm
Suqkp
fnPxU
qBxvO
indexOf
Smcvn
Suqkp
wLZlR
jXOBZ
nkHtm
ERcbZ
PMZtQ
jXOBZ
ZfNJO
jXOBZ
OgkYi
OgkYi
mUqWj
RWzBZ
idKor
eQorn
zfXNF
eQorn
nkHtm
gIHaJ
UNoEf
gIHaJ
5bc06f
GFWJZ
win32
ERcbZ
vSgeb
IVFDe
indexOf
IiUiW
UHHUV
RvOWy
LNidU
indexOf
jkPda
iCqFT
indexOf
FetbN
piCal
jtAId
bRITs
IVFDe
indexOf
TsgxQ
tddlA
a888
BoDmm
tddlA
ByPlb
dcymA
kgqEr
indexOf
RXGKU
dcymA
nkHtm
EMfpg
fnPxU
mAeoX
mAeoX
QnxYe
ZinZL
KwjoK
win32
NCzfn
indexOf
IiUiW
HQrvI
XVwsk
HTNuP
indexOf
Smcvn
XVwsk
77bd
736b19
XVwsk
win32
fnPxU
MXHuo
OtmRj
MXHuo
OJFsf
BSXvv
nkHtm
aQXSJ
ZfNJO
aQXSJ
RPhzz
bykor
indexOf
ouqss
aQXSJ
nkHtm
zVagG
GCxmg
zVagG
zVagG
VZRKX
VZRKX
d76211
VZRKX
nkHtm
VZRKX
fYTxo
HdaqX
HdaqX
Oplgt
LalOC
WhQwy
nkHtm
LalOC
ZfNJO
LalOC
VwEjt
tdlzG
092f16
kfZxp
tdlzG
nkHtm
iCqFT
vSgeb
tdlzG
6.1.7601
tdlzG
46502a
WZPwl
indexOf
RXGKU
TaMTh
nkHtm
ZvBmc
vSgeb
TaMTh
ZfNJO
TaMTh
TaMTh
WZPwl
indexOf
RXGKU
TaMTh
gvqzo
5a1d
RMxeI
glcBl
hKUrv
win32
ZvBmc
ObecO
CJZWB
indexOf
uzAZV
CJZWB
indexOf
alexeyzolotov
nkHtm
ZvBmc
FIQOa
CJZWB
indexOf
IiUiW
hKUrv
RDUoz
EyEAF
CYZNR
indexOf
admin
nkHtm
CYZNR
indexOf
IiUiW
RBWjm
jhIrV
jhIrV
rajKo
jhIrV
ezioy
jhIrV
FTFmR
jhIrV
nkHtm
HmsPK
fpxAh
cyQLW
EgYzd
cyQLW
nkHtm
wBUry
FIQOa
CYZNR
indexOf
IiUiW
LcgIo
UAewr
EyEAF
CYZNR
indexOf
HVBOu
lUpKy
win32
indexOf
DESKTOP-JTAPJCC
lUpKy
nkHtm
MZHNy
GYgmC
rdiEF
GCxmg
rdiEF
2a4494
win32
bRITs
bUwQY
bUwQY
cGOuD
czqec
mOMvF
DIkWP
MMTdn
591acb
nkHtm
oinuS
NvknN
MMTdn
6.3.9600
MMTdn
TQvaB
TQvaB
04159b
TQvaB
isArray
dnlgi
length
TQvaB
nkHtm
LyxBn
MuJJz
ykJcH
ykJcH
wskOu
bOTCQ
0bd650
bOTCQ
8215e4
hFLba
nkHtm
xKYvQ
NvknN
indexOf
JLrFX
HHGkH
indexOf
jqdXz
hFLba
nkHtm
HHGkH
indexOf
IiUiW
xKYvQ
indexOf
Xltfk
tGhhz
tGhhz
5d0c
WlHkf
WlHkf
bRITs
HHGkH
indexOf
Smcvn
haSWC
oegBy
haSWC
nkHtm
MuJJz
VjIlm
tvfmt
gNPFi
ChQil
ChQil
Cjvqi
nkHtm
txbYO
10.0.17763
txbYO
sOnIz
BpgeK
BpgeK
YSVcA
BpgeK
GSgmi
nkHtm
vlYaR
ahRiB
ZfNJO
BpgeK
BpgeK
BpgeK
gtvFH
OIVJe
ZjdQT
nkHtm
iEmad
VzNZI
yZrHz
yZrHz
yZrHz
OMwcH
cYtoJ
OMwcH
nkHtm
AwoeN
indexOf
KPJuf
nkHtm
10.0.19044
TkzIh
iuIkH
VkIir
nkHtm
HHGkH
indexOf
IiUiW
VkIir
aHAYo
indexOf
uPZdN
aHAYo
win32
lLkdj
ZMeht
ZfNJO
CDljM
bMitM
bMitM
bMitM
xXJpC
bMitM
d60869
XvGOZ
emVnw
tOVFw
nkHtm
YhgWl
ZMeht
tOVFw
NWHFq
ueKPd
ZfNJO
ueKPd
jtAId
IrIeQ
BjpJJ
indexOf
TsgxQ
indexOf
uXnuy
IrIeQ
nkHtm
qmAFL
indexOf
SOquw
indexOf
IOYRT
qCMLL
nkHtm
hwIYv
OLyxa
RRWkk
gCBVX
dEdoP
dEdoP
NQdtn
NQdtn
NQdtn
nkHtm
nuABq
YsMTZ
NQdtn
ZfNJO
NQdtn
NQdtn
NQdtn
bdQNX
cdWgK
fMuRT
CjxKq
fMuRT
KQdkV
CuEdJ
nkHtm
VWuTN
nuABq
indexOf
Xltfk
tONvX
nkHtm
TAsTF
VWuTN
HCmTQ
dosok
TfQYu
dosok
nkHtm
TAsTF
VWuTN
275dec
sZfKL
QxnlY
vaJXh
nkHtm
vaJXh
gCBVX
xhMKm
DXMwy
5a1d
ipCbt
ipCbt
ipCbt
nkHtm
VWuTN
ZfNJO
ipCbt
geMrn
geMrn
KOOXt
nIinV
fZnAa
nIinV
nkHtm
TAsTF
gCTwJ
QcdgR
indexOf
IiUiW
nIinV
6f2958
indexOf
john
nkHtm
FeoKL
nIinV
ZfNJO
nIinV
amXaA
indexOf
jkPda
indexOf
TsgxQ
QcdgR
indexOf
uXnuy
FgBua
whNtx
win32
HYTRx
HYTRx
indexOf
TQBPu
JGKmV
vsXbF
lsWNV
iqeht
nkHtm
EQbFI
AlHKK
iqeht
fnPxU
iqeht
iqeht
oJbah
102
nkHtm
MuJJz
lmNNk
iqeht
46e6f8
AxuVf
iqeht
nkHtm
JsfTu
iqeht
iqeht
gEfJq
NzuGs
gEfJq
CAzyP
win32
QbVWG
QcdgR
indexOf
UXKZi
zPUkK
indexOf
DESKTOP
KGlqb
indexOf
admin
105
iQIGV
win32
npuIk
xkxhB
iQIGV
gCBVX
mrTZC
eebAM
eebAM
eebAM
SPpJP
win32
GFRea
10.0.19045
Yupjr
OAquw
rmcle
MrtxG
OAquw
nkHtm
xMcIc
OAquw
ZfNJO
AcCmT
AcCmT
ghEay
EGrbG
EGrbG
EGrbG
EGrbG
hRxCU
AqCgX
EGrbG
win32
MlPrz
GFRea
indexOf
DESKTOP
KGlqb
indexOf
HVBOu
EGrbG
KpUse
xCYUI
MlPrz
indexOf
jkPda
qIwHH
nkHtm
MlPrz
KpUse
GfTcQ
iOjRI
gCBVX
TfcGe
TfcGe
TfcGe
Noodl
YikCg
zcjzI
zfNjJ
woeko
nkHtm
GFRea
ZfNJO
woeko
tfJAC
PEZTl
indexOf
RXGKU
111
tatnB
nkHtm
hwGmG
GFRea
tatnB
fnPxU
tatnB
agTvj
tatnB
qQBoT
2293
qQBoT
ptJdW
qQBoT
EZOGH
UUeas
indexOf
TsgxQ
UUeas
indexOf
uXnuy
inKZp
kRUJo
nkHtm
indexOf
uzAZV
UUeas
indexOf
alexeyzolotov
113
tPEmd
win32
YRhkt
JsfTu
WWPgC
dSSaH
oMXcJ
7b7bc2
oXbui
oMXcJ
nkHtm
hwGmG
dUHnp
bRITs
SuGgf
IKWrD
uJVvR
SuGgf
nkHtm
nUmTY
fZLRn
AwoeN
rEyCd
RLetr
RLetr
RLetr
xQTzO
RLetr
lKwSj
UUZzj
TlfMM
BzkmM
PmlYt
nkHtm
QptxL
pUhXE
PmlYt
ZfNJO
PmlYt
PmlYt
bwqni
YJEAK
709b
GjTFP
oWvtw
AZwZN
oWvtw
nkHtm
UmqyW
indexOf
IiUiW
QptxL
indexOf
WOddi
UrdRn
indexOf
jkPda
indexOf
eZkuq
UmqyW
indexOf
VBUsV
118
oWvtw
nkHtm
UrdRn
AYeKf
zvdyX
indexOf
Smcvn
indexOf
ootvh
QfxdP
win32
ZfNJO
TgCQA
TgCQA
OqWzw
fFjjA
vqsNU
120
fFjjA
nkHtm
QfxCY
10.0.19045
QfxCY
kGKPO
xSNbQ
xSNbQ
pODJU
djHtW
9f9d51
OzsoA
pODJU
win32
ZDTbZ
ZfNJO
ohxGB
indexOf
art-pc
brcql
indexOf
RXGKU
xSlBE
zJPzw
win32
DMgCX
ZDTbZ
fYGtO
10.0.14393
lubHV
lubHV
lubHV
brcql
indexOf
Smcvn
brcql
indexOf
HVBOu
LPqgo
lubHV
nkHtm
UuQkS
UTneV
CKXlV
6.1.7601
TRoRt
jOIgf
sXvPz
3151
brcql
indexOf
TsgxQ
brcql
indexOf
uXnuy
hqIwE
nkHtm
uwQUE
DSOiN
dEuRa
bRITs
pYgJA
pYgJA
pYgJA
QztwS
GsPAo
HoyHJ
QztwS
nkHtm
eyavi
DSOiN
nefTR
GfTcQ
LXZUF
indexOf
IOYRT
126
nefTR
nkHtm
RHAGE
QMwNE
ZfNJO
QMwNE
QMwNE
QMwNE
QMwNE
MVaFh
WDfsy
BJbUC
AZpri
SPGiL
127
AZpri
nkHtm
AueDi
fnPxU
AueDi
tcHFx
128
AueDi
nkHtm
TEKyl
ofRkq
AueDi
bRITs
RLPPX
FPhVR
jdXho
gCZRP
129
nkHtm
jdXho
MuJJz
jdXho
Pqywh
uHgTZ
gZOLh
qAfWT
uHgTZ
win32
uHgTZ
fpxAh
uHgTZ
Yzpbt
Yzpbt
Resmm
QCpdb
Kdogz
hZeKK
SlzPM
131
zDbIF
win32
TEKyl
njPDR
ZfNJO
njPDR
njPDR
tfEFv
DjvdL
viWNS
sJiwF
OegNk
132
XVkMu
win32
LPbRz
klJjI
bRITs
klJjI
hxtPG
hxtPG
hxtPG
WYGis
hxtPG
UNaKx
AkVEQ
cvXXU
nkHtm
NHqxh
OhWeV
AkVEQ
ZfNJO
HvIHk
OBDoZ
OBDoZ
FyFHL
OBDoZ
rbCtd
hqtbd
indexOf
RXGKU
uKowb
CRXRc
win32
NHqxh
LuKxN
indexOf
bfELS
LuKxN
indexOf
sNryV
NJNKQ
CRXRc
nkHtm
CRXRc
ZfNJO
CRXRc
eSUgQ
eSUgQ
RWzBZ
qoQqW
OgDbg
qoQqW
bac5dd
xOjWv
GUYUY
zHRhM
xOjWv
2b22
xOjWv
mMTvu
BYDjd
EYOoO
136
nkHtm
NHqxh
ZRDHY
10.0.19044
pEDJV
3635
psMGk
psMGk
zafMs
LuKxN
indexOf
admin
Knola
psMGk
win32
GfTcQ
DxCNB
DxCNB
DxCNB
bmdEg
DxCNB
DxCNB
OphTt
CblNr
win32
vqFxg
ZfNJO
vqFxg
BDBgi
LknAG
VaRSv
nIvzG
bBjWC
CRCpJ
bBjWC
mmMVR
JkJNf
139
tYyDR
nkHtm
VaRSv
nIvzG
tYyDR
6.1.7600
qbrfy
qbrfy
qbrfy
UDpEM
xxAkG
140
mREWS
nkHtm
fYTxo
WFdSx
indexOf
Smcvn
mREWS
mMBei
hsEmC
LSAuo
fxUJB
hsEmC
nkHtm
hsEmC
xqZie
hYPTB
MFJrb
wcNXd
62327b
wcNXd
EeGVj
xtaCd
nkHtm
VaRSv
BZxCV
ihkzb
ZfNJO
ihkzb
ihkzb
ihkzb
yvyvG
OlXqc
tRhVa
OlXqc
nkHtm
VaRSv
zvPQg
oJLBJ
ZfNJO
oJLBJ
oJLBJ
bLwIx
bLwIx
ZDGaP
rxCJO
jjQzQ
ecZTY
wVPHs
nkHtm
SAjFA
indexOf
TsgxQ
WFdSx
indexOf
uRePG
wVPHs
qUqDA
10.0.18362
iWQBC
ZfNJO
llYrx
iWQBC
nkHtm
FDQJg
qaRbf
indexOf
jkPda
iWQBC
10.0.19044
iWQBC
pGuRy
Xlpuy
YboEi
indexOf
TsgxQ
YboEi
indexOf
HVBOu
tYbvr
dZjRC
win32
ATzbb
fnPxU
ATzbb
ATzbb
xghJT
xghJT
a30c
ukHih
6eb45e
EtvNo
TOcSf
nkHtm
Rhzqu
qaRbf
VExOl
GDbVT
GDbVT
ZfNJO
GDbVT
xCYUI
kzgLm
QlcWr
VRnEt
nkHtm
HHlMB
xaYqX
64ccb5
BbEno
EATci
gCBVX
HHlMB
indexOf
Xeon
QzgmY
BbEno
nkHtm
CQhOl
AwoeN
CQhOl
CQhOl
hPxJZ
CQhOl
win32
HHlMB
yumBq
ZfNJO
YLsAA
tVDUA
tVDUA
tVDUA
OUAgF
tVDUA
d864df
plXAh
dMXhg
NyCkc
potKV
nkHtm
HHlMB
bTeQS
d61484
potKV
BGefy
152
potKV
nkHtm
UyhxR
amhbO
potKV
ZfNJO
zYjuO
zYjuO
wEasK
zYjuO
qVMZC
zYjuO
f2886f
OOnDh
zYjuO
win32
gVLoY
Tgymz
AarUZ
6.1.7601
AarUZ
krEhy
indexOf
admin
154
AarUZ
nkHtm
UJJIE
ZfNJO
fZNZO
JJSCS
FyFHL
VcmlK
ixLAM
YboEi
indexOf
RXGKU
DRjWR
VcmlK
nkHtm
BUZkQ
VcmlK
ZfNJO
VcmlK
zBMdH
zBMdH
zBMdH
fXgaW
XPIjd
nkHtm
XPIjd
gCBVX
qPaPN
qPaPN
qPaPN
MjDlU
kKtMO
qPaPN
nkHtm
BUZkQ
tEZZI
6.1.7601
qPaPN
qPaPN
BUZkQ
indexOf
jkPda
mjpJN
XtOSN
mjpJN
yzgxU
foJoc
mjpJN
nkHtm
Dovst
fnPxU
kRFvS
QnxYe
McXrS
nkHtm
BUZkQ
SUKMc
ZfNJO
PEZTl
indexOf
RXGKU
VWdCB
win32
BUZkQ
tEZZI
ZfNJO
gZDOH
bneoz
JBrgI
YboEi
indexOf
administrator
Gdbbl
gZDOH
nkHtm
gZDOH
fnPxU
gZDOH
gZDOH
Ckwio
GTCyC
GTCyC
vGBKs
BxXyp
nkHtm
tKluI
xZbcw
MuJJz
eSJzE
26112
vdbSr
slRdz
vdbSr
163
nkHtm
lNHCN
indexOf
TQBPu
97a9d3
TAjyn
YXgps
win32
TfkHc
tEZZI
YboEi
indexOf
10.0
YXgps
YXgps
YXgps
ThfRI
indexOf
jkPda
zUxLT
10.0.15063
TvGBk
tojkc
CbPyl
zUxLT
win32
INVfb
bWTch
zUxLT
ZfNJO
PXSHm
uhYUg
uhYUg
uhYUg
uhYUg
LQKel
uhYUg
QfoHE
uhYUg
nkHtm
uhYUg
10.0.17763
wyeHy
iPegS
iPegS
ZKLiQ
iPegS
bEVpk
fbZIv
iPegS
win32
iPegS
iPegS
iPegS
RcfYt
indexOf
NOHID
indexOf
uXnuy
cPPaR
GCxmg
vTzua
CKXlV
vTzua
UYBLj
cOcgT
nCPxw
cOcgT
AJoTE
cOcgT
OUSDl
cOcgT
XGBnX
BgBOz
eBUCu
BgBOz
f7e0fe
IJbxK
nkHtm
BgBOz
LrqVW
769fc7
TSXWe
PDadH
nkHtm
DaLyS
goawL
indexOf
xlrTu
jugTq
EDTXw
EDTXw
EDTXw
RWanf
IUKbW
vyXpQ
MAehl
CxmJh
170
nkHtm
gCBVX
MAehl
Mxnyy
AwDEZ
AwDEZ
AwDEZ
qrjBi
BlEMP
AwDEZ
nkHtm
HCmTQ
RiQeg
275dec
QxnlY
BNKxt
win32
INVfb
DaLyS
neKoW
bRITs
bf7e
neKoW
ADfWB
YLvFl
pejSM
tVnKg
win32
INVfb
DaLyS
indexOf
UXKZi
YJdle
indexOf
mSHmA
indexOf
RXGKU
174
YLvFl
nkHtm
YLvFl
fnPxU
TITCN
7e0c8b
XuzoS
pdWyc
BtDzw
XuzoS
nkHtm
YaLhE
Xrrkk
indexOf
UXKZi
indexOf
work
indexOf
HVBOu
cToVE
zPTng
nkHtm
icgKs
zPTng
zPTng
AwoeN
qedVd
xCYUI
kzgLm
Xrrkk
indexOf
Smcvn
keEKD
indexOf
uXnuy
FBGxo
qedVd
nkHtm
uUIkd
icgKs
ZfNJO
vvXDX
vvXDX
vvXDX
TPuXl
FWVlC
alBUY
mfRui
178
win32
uUIkd
icgKs
YdAJT
6.1.7601
YdAJT
iWcXT
keEKD
indexOf
NOHID
lVuDK
indexOf
uXnuy
dwnKF
179
nkHtm
uUIkd
iWcXT
gCBVX
iWcXT
sKWRg
sKWRg
sKWRg
KGpfy
KGpfy
qXoBM
Fukmj
nhsSB
180
Fukmj
nkHtm
ySfPL
ZxGVr
bRITs
ZxGVr
rrGqb
GkTib
GkTib
RwBSt
jXlkM
GkTib
win32
uUIkd
JcbXn
mZCmv
indexOf
KVM/QEMU
GkTib
GkTib
182
GkTib
nkHtm
gCBVX
GkTib
GkTib
rTVnh
lEbyl
TJPck
JsvJe
HOfZa
nkHtm
mZCmv
eRbWb
uyeqv
indexOf
Xltfk
HOfZa
URmbe
HOfZa
nkHtm
GdaWd
fnPxU
ipGuV
jpuFd
hQqHg
UPpVc
wajDD
DiUBo
UPpVc
nkHtm
ZfNJO
USQOj
USQOj
omdBF
XJpdU
FbBQv
VhEzT
win32
eRbWb
jSrah
ZfNJO
jSrah
Qxjjl
gCqrp
BLFjb
foZTX
BWfaS
foZTX
187
SKzqk
win32
uyeqv
eRbWb
lVuDK
indexOf
IiUiW
RktEk
soOge
PXdcT
indexOf
Smcvn
ujnSb
RWzBZ
ujnSb
bac5dd
188
ujnSb
nkHtm
ujnSb
gCBVX
ujnSb
DcFhQ
UAtDS
UAtDS
IHQPD
UAtDS
b6f4a2
Onguy
nkHtm
UAtDS
6.1.7601
UAtDS
UAtDS
uoBZF
indexOf
Xeon
zFckG
NyKqM
win32
uoBZF
wMQDm
rbjKh
indexOf
DESKTOP
TIzKm
jtAId
TIzKm
uLBXS
XCNWh
MhnZw
nkHtm
wMQDm
XCNWh
10.0.14393
oCqeq
rWigB
rWigB
pyKjF
xrpcj
xXJpC
xrpcj
192
xrpcj
win32
gkufx
nUFlH
6.1.7601
xrpcj
EMfZD
BMypU
afERo
0ae8
ipXxx
CDgXS
ipXxx
aROpl
193
nkHtm
gCBVX
syMKD
syMKD
syMKD
syMKD
vxDUi
12a5b6
bAJPU
aqlKQ
4|3|2|1|0|5
aes-128-cbc
UI32BE
UI8
GUID
UI32LE
UI16LE
HEX
FTIME
DTSTP
WSVFD
rgJwm
UI32LE
alloc
writeUInt32LE
EwDqj
alloc
writeUInt32BE
UI16LE
alloc
writeUInt16LE
UI16BE
alloc
writeUInt16BE
eNvTU
alloc
writeUInt8
HEX
from
hex
QvATL
split
fxwcJ
wpBQO
fxwcJ
wcbWm
ysdJp
fxwcJ
wcbWm
ysdJp
jNpYk
HEX
jNpYk
cNabS
concat
isBca
MSxwZ
yyutS
LQvgN
smHDZ
floor
rnbgY
floor
IQhzX
ojFHY
UI32LE
rEoGL
wpBQO
concat
UOHIM
hTGhk
AVGaJ
smHDZ
getFullYear
hTGhk
zWfyW
OWKhd
getMonth
LIAVr
getDate
wcbWm
NrfPR
JjUlS
getHours
MxLxi
hQzMw
getMinutes
plBQo
floor
AlYSd
getSeconds
rEoGL
UI16LE
concat
STR16
alloc
length
xAThT
length
writeUInt16LE
charCodeAt
XyVzc
undefined
JzOnI
xOxgX
xlqrt
split
writeFileSync
prs
concat
update
final
createCipheriv
VpISK
slice
slice
randomBytes
from
stringify
push
EIvuy
DVHEp
DVHEp
outerr
outerr
push
0|4|1|2|5|3
\.\
vGDQf
split
uDGjZ
indexOf
split
join
rbQJv
substr
ScTxG
length
substr
ggwGK
length
rbQJv
substr
substr
uDGjZ
indexOf
\.\
split
mGKCa
join
zMlfG
length
ozGgv
substr
4|1|3|7|5|0|2|6
test
Duo
UI16LE
STR16
base64
object
WcmSA
oVgAc
xlMeh
hUqfz
TtjdC
gorwm
max
min
UI32LE
GUID
00021401-0000-0000-c000-000000000046
FTIME
QKpRN
UI8
20d04fe0-3aea-1069-a2d8-08002b30309d
SthdS
4|0|2|1|3
TgUrJ
LxzCC
DTSTP
mXmyp
ZPrOt
xSoTF
mPMuH
bdEpQ
amcrT
axChN
kjkWn
rEmBL
length
siIRm
NggCV
name
name
length
name
file
file
length
file
workdir
workdir
length
workdir
args
args
length
args
icon
icon
length
icon
now
workdir
dnPFI
shOCg
shOCg
mkdirSync
workdir
NEaXh
workdir
workdir
indexOf
dnPFI
workdir
file
dnPFI
oVgAc
XAdEg
nQVBd
split
qDFlg
resolve
pf1
resolve
pf2
pf1
pf2
resolve
argv
resolve
argv
file
file
file
indexOf
TDHin
cBofC
EwJBp
EwJBp
xBtpC
xBtpC
file
undefined
code
undefined
signal
EwJBp
VJiHW
VJiHW
file
log
NdjsX
writeFileSync
trim
exit
split
flg
flg
flg
flg
flg
UwwMu
name
flg
usfpX
file
flg
usfpX
workdir
flg
usfpX
args
flg
PJhhg
icon
flg
att
att
file
wtzsy
fRnup
fRnup
att
lnQGN
BucVH
fyTDx
fyTDx
att
log
shcm
show
KcGEF
shcm
EVQuz
show
vYYHv
jacUS
show
shcm
DFnHg
ClfUh
AZMEO
aoPXM
DFnHg
flg
BhbLy
DFnHg
att
BhbLy
kePNv
ftc
ftc
BhbLy
FTIME
fta
fta
BhbLy
kePNv
ftw
ftw
YBBPa
DFnHg
fsz
fsz
YBBPa
UI32LE
icidx
icidx
UI32LE
shcm
cyjOx
oKYOX
hky
hky
cyjOx
oKYOX
Qepfl
UI32LE
MzGgO
DFnHg
concat
CIWWa
jLvNU
flg
sWNnG
sWNnG
MzGgO
oKYOX
MzGgO
oKYOX
nbPAK
UI8
qblvw
PHZVD
ClfUh
oxkDy
length
cgswK
substr
HaeId
lLJXP
SthdS
TMnmT
split
qblvw
PHZVD
PHZVD
push
from
fgmaq
push
alloc
UI16LE
writeFileSync
pf2
readFileSync
NoJOc
length
xnQVO
CXxfc
btlyA
length
from
file
cgswK
length
UI16LE
fgmaq
length
PHZVD
Gknkx
PHZVD
Gknkx
UI32LE
DTSTP
ftw
ftw
Cpsjn
oKYOX
push
Cpsjn
PHZVD
Cpsjn
PHZVD
FBlXD
oKYOX
wFxgW
oKYOX
jnQuz
DFnHg
XwlmL
VWHAd
ftc
ftc
RPgKv
VWHAd
fta
fta
length
XPevI
oKYOX
fgmaq
fgmaq
length
XPevI
oKYOX
XPevI
tRAjI
oKYOX
XPevI
UI16LE
concat
writeUInt16LE
length
push
concat
writeUInt16LE
length
push
args
trim
xqreb
oKYOX
length
tRAjI
XPevI
oKYOX
log
concat
length
writeUInt16LE
DfEqC
length
RdAUa
flg
HWksk
EemSh
EemSh
statSync
name
oKYOX
length
tRAjI
CIWWa
RdAUa
flg
HWksk
ZPrOt
gZBOW
CBgoM
file
qoxsh
jTQRe
file
wlgWP
oKYOX
length
UunEE
tRAjI
dfpPg
flg
MhmKI
xSoTF
LTEYW
workdir
length
UunEE
UI16LE
length
PiIEd
STR16
parse
lDsFA
from
env
LU0
SXOKw
toString
flg
SoHGZ
SaIyx
kpbUJ
prs
prs
exit
args
trim
oKYOX
length
XIKBJ
tRAjI
bpmvL
flg
NZxPi
GaRdF
icon
oKYOX
length
tRAjI
writeFileSync
readFileSync
length
XIKBJ
UI32LE
concat
concat
wUbJv
cIFaG
ojNaP
writeFileSync
iENJA
VCmqV
VCmqV
JWSDO
iUdjW
STR16
.exe
\Microsoft\Windows\Start Menu\Programs\Startup\
.lnk
oRVbx
Uiofe
BpHSZ
XVooN
xBBsB
wPnfX
aup
xBBsB
xBBsB
tmp
RSjwg
JeVKN
JeVKN
xBBsB
JeVKN
rZiIl
Wlnum
GlnmJ
FpvMP
GlnmJ
bgoNz
apd
punaQ
bgoNz
UwnFo
qCLlr
IvwQb
pQMIn
name
UI16LE
length
uNrWR
jjmiH
mkdirSync
C:\
tmpbuild
_i_
.txt
undefined
prsv
DpcGi
nEIVz
XfEVo
iUMAn
BDxjK
ouvlv
DRUKn
QxXsN
vDdzY
log
Txlrv
pf1
pf2
LPRSs
DpcGi
XHslJ
mkdirSync
ZsjwW
existsSync
resolve
argv
resolve
argv
lIbhS
GLcPP
nEIVz
x64
statSync
pf1
lIbhS
zDYwW
SNsDE
statSync
0|2|3|4|1
split
file
HidmS
file
kHuni
file
srTmE
file
file
indexOf
qkCSo
mOKZf
qkCSo
zJqFA
size
size
lIbhS
SYDaM
SYDaM
close
writeFileSync
pf1
readFileSync
oTPlw
gDZdq
statSync
pf1
length
model
model
trim
speed
speed
size
size
lIbhS
CNlmA
BDxjK
srTmE
srTmE
EgvGW
chAxx
chAxx
chAxx
chAxx
LbTXo
rpcsrv
UvqVW
LU0TO
zpTNE
ShxWQ
readFileSync
toString
trim
statSync
pf2
mfxrz
mfxrz
ktmr
fZgVx
ktmr
ktmr
error
kBheY
error
error
sZghq
QLDsL
code
QLDsL
signal
outbuf
concat
outbuf
errbuf
concat
errbuf
returnbuffer
out
outbuf
toString
outbuf
err
errbuf
toString
errbuf
nostr
out
statSync
size
size
exxXf
YKhpq
writeFileSync
pf2
readFileSync
mkdirSync
lIbhS
qkAyl
qkAyl
mkdirSync
statSync
pf2
size
size
basename
pf1
basename
pf2
argv
LvDbh
join
pf1
pf2
resolve
pf1
resolve
pf2
resolve
argv
resolve
argv
fmMNz
\Fonts\micross.ttf
rkQpR
hex
Washington1
Microsoft Root
BPuxn
oduEF
yRRIj
ddLmv
ddLmv
createHash
sha256
update
digest
readFileSync
length
saLkj
length
toString
SmMXc
from
lvPng
toString
hex
indexOf
from
JXnSF
toString
hex
szhIc
indexOf
zKsPB
2|6|4|3|0|5|1
ELmOM
eqsSg
length
tbfXg
HwjAL
vwhyv
att
XhOMK
split
push
path
path
length
path
name
XBBUT
pUxYO
ppid
ppid
push
pid
session
push
args
args
createHash
sha256
shDgE
JFXAi
bVmvA
msiexec.exe
oTUMY
lBfDY
nZOSP
sQrLc
createHash
rtLnS
TuDry
Tgezg
kill
pid
HKEwD
kNkDP
ppid
ppid
NxKcz
kNkDP
ppid
ppid
ppid
ppid
length
length
Wfbkm
hglsz
bVmvA
IBwpw
createHash
sha256
update
elmEh
digest
slice
SDDWI
rtLnS
OBcUf
vBIaI
QmKXc
kUVpg
LLoUM
LJEHP
nkKBH
length
KYCkU
toLowerCase
indexOf
OBcUf
tiJVt
inFLn
oTUMY
env
sfxname
length
basename
toLowerCase
outbuf
outbuf
push
AbyyV
OFRbP
auMgK
chdir
path
path
toLowerCase
name
name
toLowerCase
kNkDP
pid
nkKBH
indexOf
KYCkU
indexOf
push
OBcUf
length
qazxf
qazxf
jCJeW
wHMSk
EaLLg
ppid
ppid
EaLLg
ppid
WqbWD
createHash
UrMIj
update
UtaVT
digest
slice
KGPAZ
KGPAZ
sguSk
length
log
psls
fdHMR
msiexec.exe
kfSnJ
aes-128-cbc
tYWXq
VKBFx
VKBFx
5|4|1|2|3|0
split
createCipheriv
NSEYR
slice
slice
concat
update
final
writeFileSync
prs
randomBytes
from
stringify
cXTGP
length
LNGiD
toLowerCase
indexOf
oZMKF
0|1|4|2|3
aes-128-cbc
gScex
QxwUv
QxwUv
VyTVs
split
readFileSync
prs
createDecipheriv
qwosx
slice
slice
parse
toString
concat
update
slice
final
randomBytes
dKJsd
dKJsd
tDsRB
Ezxgl
dKjiP
tSfgB
hxbcC
TvsBP
YFkCw
DUAJf
XJaGE
tmWLp
EIMfG
bVQbz
FEOfk
oBIqw
FZAoF
oBIqw
wCHHb
oBIqw
aes-128-cbc
gttk
.exe
LU0TO
WYVan
Ralsb
XqkEJ
C:\
eANUA
rpcsrv
tmpbuild
_i_
.txt
VCnFp
hwv
wfr
sfre
atct
argv
indexOf
.exe
argv
nzNxk
msuLd
argv
HnPoL
KzxWW
argv
KzxWW
joefO
DilHh
WYVan
jYqTr
pslo
KzxWW
DilHh
lNmbC
gtNHO
readdirSync
xBNWA
9|7|2|5|0|4|3|8|1|10|6
split
readUInt16BE
readUInt16BE
createDecipheriv
UZdqB
slice
lHhxk
length
slice
concat
update
slice
lHhxk
final
pwKIR
BRQwx
length
slice
toString
indexOf
rpcsrv
DilHh
FjGos
FjGos
log
KmgoI
ANaud
lHhxk
lHhxk
lHhxk
lHhxk
lHhxk
lHhxk
xQvHT
uOItO
xBNWA
ckZae
HGzZB
LU0TO
URLLT
kprsq
LqhCy
FadAG
QMfdJ
readFileSync
toString
trim
uerepl
uncaughtException
removeAllListeners
log
ihMOQ
stack
log
stack
IMvXu
BxNte
log
qoOhF
log
WwVSb
isc
log
rZnnz
log
MydMZ
KdXrO
0|3|1|2|4
aes-128-cbc
qwnCX
add
HKCU\Software\SPoloCleaner
Installed
REG_DWORD
windir
systemroot
temp
username
\networkservice\
network service
system
local service
dwm-
umfd-
UI16LE
STR16
prsf
sbchn
THSCe
FTBeK
jAzmK
xGAof
mGySZ
IVMKW
KzlWX
yHmXW
gwyND
LFHsV
ogFJp
Rzony
JVCAp
prsi
a15a30
14f1a0
ifLQT
reg.exe
s1b
bxsTZ
SypZk
LU0
cwnqi
log
FWpws
srQIp
now
prs
pslo
vSxlN
tRzcR
dlIuN
srQIp
att
now
ata
cta
prs
SlaiI
aLgIt
KaTVM
qJjTF
OoZtC
RIyzB
KaTVM
UbYYR
GxIrC
dzZyx
tTSBd
tTSBd
VLdMD
uzXib
pslo
XAakU
split
readFileSync
prs
concat
update
slice
final
parse
toString
createDecipheriv
KdRtL
slice
slice
OEqwP
reg.exe
dpnXU
lYyMx
lkVml
tbMTF
dzZyx
rdfxn
zwtaq
fill
IevFU
log
log
Unpacking installer archive ...
rvBYn
IGTWi
IGTWi
mUyaE
IevFU
WgCAz
iyVPh
ozctd
DTZcZ
DAIjd
prs
prs
exit
iyVPh
POXEB
eLHwd
eLHwd
MXiQU
gAotX
pslo
sfEBf
hdFzX
argv
qfWzD
IevFU
argv
slice
PPorS
dzZyx
xCQiM
SsRNG
readdirSync
C:\
resolve
resolve
dirname
resolve
qfWzD
zxOgI
zxOgI
sep
basename
wyaJS
PSxXr
sep
basename
ozctd
RZsdy
RZsdy
isc
LAmJU
luShU
LAmJU
EwoCc
tmp
LAmJU
tvcAY
aup
LAmJU
allusersprofile
apd
wGVqg
appdata
usr
ZPXBf
lQmko
tmp
isc
isc
dzZyx
tmp
toLowerCase
indexOf
toLowerCase
isc
isc
QMSsb
tmp
toLowerCase
indexOf
YqNOJ
isc
isc
aup
apd
isc
isc
usr
isc
isc
usr
toLowerCase
gGsBy
VLdMD
GCwLo
JbFRE
substr
SiDuO
length
indexOf
EtJfS
dzZyx
indexOf
PdbvW
isc
mkdirSync
ffJfX
PEWre
PEWre
writeFileSync
readFileSync
esbSL
ogFJp
writeFileSync
readFileSync
rLecw
iWicR
ppid
ppid
audCK
ppid
gMwwm
bOSrL
HFFgA
HFFgA
chdir
iyVPh
bOSrL
lbNMh
lbNMh
ZPXBf
icon
ohzDK
NQzDV
length
eWfeJ
gsXxX
prsi
log
nRXsI
IevFU
mniYC
QXeGk
prs
gMwwm
prs
log
HBwmJ
prsi
eGeHR
331db0
OTepM
Uficc
pgsSR
KBUsm
Ccndk
DDlRV
DDlRV
uvYkc
add
HKCU\Software\SPoloCleaner
lkVml
tbMTF
prsi
log
nRXsI
log
QbMFU
ozYpA
ndQqT
parse
ZeXoo
from
env
LU0
base64
toString
zawXq
close
env
LU0
mXtUN
s1e
bOSrL
LJsvs
LJsvs
workdir
workdir
workdir
indexOf
vSxlN
workdir
s1e
s1e
vrsav
lNIsH
1|2|3|5|4|0
aes-128-cbc
Unknown
USERNAME
USER
PROCESSOR_ARCHITECTURE
string
SgQDJ
x64
kICJf
platform
arch
release
uptime
totalmem
freemem
JbnZb
hostname
OMWnR
FwGzr
IGbxq
cwd
tmpdir
versions
node
OMWnR
nLltz
PROCESSOR_ARCHITEW6432
cswEL
indexOf
TyGFd
cswEL
lYeDj
indexOf
larPP
SmAKR
SmAKR
dbjtu
jCiil
split
from
stringify
randomBytes
createCipheriv
uLJKZ
slice
slice
writeFileSync
prs
concat
update
final
cpus
length
larPP
RhNSW
CIxLy
statSync
pf1
length
model
model
trim
speed
speed
YmQUd
length
XEeIa
length
substr
XEeIa
length
substr
length
substr
XEeIa
length
substr
XEeIa
length
substr
lfIDF
czreg
sha256
createHash
dprUu
JCMrd
statSync
createHash
fxzJz
update
BHaoD
digest
slice
AAUFD
8|12|6|7|4|2|11|1|10|0|3|5|9
split
TiwUg
length
createCipheriv
aes-128-cbc
slice
concat
alloc
concat
from
alloc
writeUInt16BE
FVTRz
EVLWc
concat
update
final
randomBytes
ABLCC
aes-128-cbc
slDDn
ziRbr
YZvFf
YZvFf
writeFileSync
pf1
readFileSync
2|1|5|8|10|4|7|6|0|9|3
split
cnFly
readUInt16BE
slice
JwuLK
length
UGvev
length
concat
update
slice
KQhoj
final
createDecipheriv
KRLre
slice
slice
toString
readUInt16BE
now
random
4|1|0|2|3|5
recv
nfPzt
split
log
LYezV
SEXMw
tkstp
jxfoM
Console
Services
3|4|0|2|1
UI16LE
UI8
zICsd
MfCCd
Xlrec
BpTuF
hquzb
VjBtI
gttk
pgCfF
test
XXOsa
bClCf
createSocket
udp4
error
message
tUcif
ZViHQ
rIlAm
log
JoItq
dfWEi
PriKT
writeFileSync
trim
RmaNB
Firgy
now
JVSNi
JVSNi
exit
oJyBY
gEWIj
doKDt
ykLwH
ykLwH
ykLwH
length
argv
split
join
stringify
JoItq
length
tUcif
Ttvrw
xXGSY
log
szqgF
HCZoK
EmumW
EmumW
writeFileSync
trim
exit
writeFileSync
readFileSync
HCZoK
cRHVO
mvZLa
OKZRu
aEwsy
zxmIB
RMhNj
tkstp
rcCxd
zICsd
eLNIm
pid
session
path
ldBRF
DNFaR
eXDaP
xZhWs
twViR
iGasD
kqfSg
tEDgB
vzpnn
close
jSFWu
split
push
from
GtMhk
push
alloc
Cvwsz
UI8
Cvwsz
JVATt
Cvwsz
tqfZD
send
length
hex
NqpUv
hhCar
length
from
fvCLz
HbhkD
uAiws
uAiws
QPoMl
fromCharCode
OLaFa
QQRNo
YcUbs
createDecipheriv
concat
update
final
toString
0|6|4|3|1|2|5
UI16LE
STR16
ZWCcN
iwYJs
UPlnM
iBBDo
IpzDD
AlwKc
afzux
UqPSi
AmlYK
ZWCcN
log
AQgAM
stack
log
stack
CaHAd
jysIw
mMylK
log
GjWlt
zbNAi
length
JAZXx
split
push
path
path
length
path
name
push
args
args
push
pid
session
nmrdV
yCmDA
ppid
ppid
XVLFB
EFxkU
pOcbv
SCOFy
HUtjq
KnluE
file
wgpAB
length
Apayo
VXvzA
CuWWs
bxXRN
DDwaQ
length
from
hex
createDecipheriv
concat
update
final
toString
log
USER
USERNAME
string
PROCESSOR_ARCHITEW6432
PROCESSOR_ARCHITECTURE
x64
qcxpw
cmd.exe
ZLnEZ
PNWeO
nTbGl
yuJxn
LkHfQ
uncaughtException
base64
ini
isc
from
from
vxWTd
DJtxC
DJtxC
0|5|21|14|1|13|20|18|24|15|6|27|7|3|12|16|9|23|28|11|2|8|30|25|29|4|22|26|31|17|10|19
split
release
GBVSF
string
OLthj
indexOf
wHfyl
cuEhw
DvIbm
length
platform
uGJgq
GBVSF
joLTl
indexOf
versions
node
NvtBt
length
substr
bkNFL
NmkVy
cwd
uptime
Unknown
tmpdir
HHGKT
length
substr
freemem
totalmem
arch
HHGKT
length
substr
cpus
HHGKT
length
substr
hostname
bkNFL
xkTgq
length
length
model
model
trim
speed
speed
QPDWG
length
substr
alloc
alloc
sxaap
GkOOI
GkOOI
fill
unshift
unshift
unshift
unshift
FLVzC
allocUnsafe
allocUnsafe
sxaap
ZCGaW
ZCGaW
createDecipheriv
concat
update
final
toString
versions
node
indexOf
uerepl
dbtuQ
yQmVY
yQmVY
uerepl
DeyRL
removeAllListeners
iybkN
Cftmd
ygmAS
ZetLy
yMAkG
BLURs
mqOiF
vTLOu
ggiBC
randomBytes
aQgfL
aQgfL
zuOeS
jpiXj
fIsOv
fIsOv
qodaS
qhyOp
JvywP
log
tLWRV
stack
log
stack
statSync
pf1
length
DvIbm
length
length
exit
from
SNIXJ
log
rdTie
sgsau
log
mjnHL
isc
sgsau
xdQZQ
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:02:16 00:00:38 |
| ZipCRC: | 0xf1a751b0 |
| ZipCompressedSize: | 11463792 |
| ZipUncompressedSize: | 11463792 |
| ZipFileName: | Roxys Tune Up Final By Caroo.zip |
Total processes
68
Monitored processes
15
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | cmd.exe /d /c bymrtpvf.bat 2630160793 | C:\Windows\System32\cmd.exe | set_3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1316 | reg.exe add HKCU\Software\SPoloCleaner /v Installed /t REG_DWORD /d 1 | C:\Windows\System32\reg.exe | — | fghnmuro.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1336 | "C:\Windows\system32\msiexec.exe" /i "C:\Users\admin\AppData\Roaming\AW Manager\Windows Manager 1.0.0\install\97FDF62\Windows Manager - Postback Johan.msi" /qn CAMPAIGN=2479 AI_SETUPEXEPATH=C:\Users\admin\AppData\Local\Temp\nsxD156.tmp\set_1.exe SETUPEXEDIR=C:\Users\admin\AppData\Local\Temp\nsxD156.tmp\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1708040578 /qn CAMPAIGN=""2479"" " CAMPAIGN="2479" | C:\Windows\System32\msiexec.exe | — | set_1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2192 | "schtasks" /Create /TN "DPUpdateTask" /SC HOURLY /TR "C:\Users\admin\AppData\Local\DP\DPUpdate.exe" | C:\Windows\System32\schtasks.exe | — | set_2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2416 | "C:\Users\admin\AppData\Local\Temp\nsxD156.tmp\set_3.exe" | C:\Users\admin\AppData\Local\Temp\nsxD156.tmp\set_3.exe | go.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.22621.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | "schtasks" /Query /TN "DPUpdateTask" | C:\Windows\System32\schtasks.exe | — | set_2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Users\admin\AppData\Local\Temp\nsa7FCB.tmp\go.exe" | C:\Users\admin\AppData\Local\Temp\nsa7FCB.tmp\go.exe | Roxys Tune Up Final By Caroo.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3132 | "C:\Users\admin\AppData\Local\Temp\is-TO7EL.tmp\set_2.tmp" /SL5="$1C0192,6358074,832512,C:\Users\admin\AppData\Local\Temp\nsxD156.tmp\set_2.exe" /SP- /VERYSILENT /SUPPRESSMSGBOXES /PID=2964 /CLICKID=2479 /SOURCEID=2479 | C:\Users\admin\AppData\Local\Temp\is-TO7EL.tmp\set_2.tmp | set_2.exe | ||||||||||||
User: admin Company: DP, Ltd. Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3228 | "C:\Users\admin\Desktop\Roxys Tune Up Final By Caroo.exe" | C:\Users\admin\Desktop\Roxys Tune Up Final By Caroo.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3256 | "C:\Users\admin\AppData\Local\Temp\nsxD156.tmp\set_2.exe" /SP- /VERYSILENT /SUPPRESSMSGBOXES /PID=2964 /CLICKID=2479 /SOURCEID=2479 | C:\Users\admin\AppData\Local\Temp\nsxD156.tmp\set_2.exe | go.exe | ||||||||||||
User: admin Company: DP, Ltd. Integrity Level: HIGH Description: DP Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
22 113
Read events
21 909
Write events
170
Delete events
34
Modification events
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Roxys Tune Up Final By Caroo.zip | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3288) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
30
Suspicious files
7
Text files
17
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3784 | WinRAR.exe | C:\Users\admin\Desktop\Roxys Tune Up Final By Caroo.exe | executable | |
MD5:2F79C3D276C51FC3416B1E920D6EA77E | SHA256:B16BEAB3FE4215128FA3D2EC7088ACAF9780EA6DC30C14393DFB3B946F92379F | |||
| 4008 | Roxys Tune Up Final By Caroo.exe | C:\Users\admin\AppData\Local\Temp\nsa7FCB.tmp\nsDialogs.dll | executable | |
MD5:1D8F01A83DDD259BC339902C1D33C8F1 | SHA256:4B7D17DA290F41EBE244827CC295CE7E580DA2F7E9F7CC3EFC1ABC6898E3C9ED | |||
| 4008 | Roxys Tune Up Final By Caroo.exe | C:\Users\admin\AppData\Local\Temp\nsa7FCB.tmp\saved | text | |
MD5:252217817D6C7C1CBC6835348BA2A54C | SHA256:CAB69F3CE8046407E871C77D5F73D8DC3794AAD3172C1B403D96480295FE0DF1 | |||
| 4008 | Roxys Tune Up Final By Caroo.exe | C:\Users\admin\AppData\Local\Temp\nsa7FCB.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 4008 | Roxys Tune Up Final By Caroo.exe | C:\Users\admin\AppData\Local\Temp\nsa7FCB.tmp\System.dll | executable | |
MD5:4ADD245D4BA34B04F213409BFE504C07 | SHA256:9111099EFE9D5C9B391DC132B2FAF0A3851A760D4106D5368E30AC744EB42706 | |||
| 3288 | WinRAR.exe | C:\Users\admin\Desktop\Roxys Tune Up Final By Caroo.zip | compressed | |
MD5:E93F3D24832AB98936DBF764987C66B6 | SHA256:F320341F802E264A34EEAA6E077B4B4512D8B03F30812DE3608F7766F1E0085A | |||
| 4008 | Roxys Tune Up Final By Caroo.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\run[1].htm | text | |
MD5:252217817D6C7C1CBC6835348BA2A54C | SHA256:CAB69F3CE8046407E871C77D5F73D8DC3794AAD3172C1B403D96480295FE0DF1 | |||
| 4008 | Roxys Tune Up Final By Caroo.exe | C:\Users\admin\AppData\Local\Temp\nsa7FCB.tmp\INetC.dll | executable | |
MD5:40D7ECA32B2F4D29DB98715DD45BFAC5 | SHA256:85E03805F90F72257DD41BFDAA186237218BBB0EC410AD3B6576A88EA11DCCB9 | |||
| 4008 | Roxys Tune Up Final By Caroo.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\Roxys_Tune_Up_Final_By_Caroo.exe_[1].exe | executable | |
MD5:24B364A8D7F27BFF9FACC62FE1360FDB | SHA256:CB1488DC3C9D5C30BB1421A0242A545A00C1109A68D38AF381111EF64320F27E | |||
| 2672 | go.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
22
DNS requests
17
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4008 | Roxys Tune Up Final By Caroo.exe | GET | 200 | 188.114.96.3:80 | http://placehouse.xyz/pe/build.php?pe=n&sub=&source=3812&s1=48711627&title=Um94eXMgVHVuZSBVcCBGaW5hbCBCeSBDYXJvby5leGU%3D&ti=1708042194 | unknown | executable | 333 Kb | unknown |
2672 | go.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
2672 | go.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2672 | go.exe | GET | 200 | 188.114.96.3:80 | http://humorscience.website/asik.php?fz=&d=nsis&msg=&r=offer_exists&rk=no&o=1662&a=2479&dn=420&spot=1&t=1708042203 | unknown | text | 2 b | unknown |
4008 | Roxys Tune Up Final By Caroo.exe | GET | 200 | 188.114.97.3:80 | http://wastetop.website/run.php?pe=n&p=3812&t=48711627&title=Um94eXMgVHVuZSBVcCBGaW5hbCBCeSBDYXJvby5leGU=&sub=&ps=65cea5adeebb8 | unknown | text | 135 b | unknown |
2672 | go.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?89bd818bf8781628 | unknown | — | — | unknown |
2672 | go.exe | GET | 302 | 188.114.96.3:80 | http://humorscience.website/asiko.php?spot=2&a=2479&on=244&o=331 | unknown | text | 2 b | unknown |
2804 | msiexec.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
2804 | msiexec.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | binary | 1.37 Kb | unknown |
2672 | go.exe | GET | 200 | 159.223.29.40:80 | http://kapetownlink.com/installer.exe | unknown | executable | 4.51 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4008 | Roxys Tune Up Final By Caroo.exe | 188.114.97.3:80 | wastetop.website | CLOUDFLARENET | NL | unknown |
4008 | Roxys Tune Up Final By Caroo.exe | 188.114.96.3:80 | wastetop.website | CLOUDFLARENET | NL | unknown |
2672 | go.exe | 188.114.96.3:443 | wastetop.website | CLOUDFLARENET | NL | unknown |
2672 | go.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2672 | go.exe | 216.58.212.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2672 | go.exe | 188.114.96.3:80 | wastetop.website | CLOUDFLARENET | NL | unknown |
2672 | go.exe | 159.223.29.40:80 | kapetownlink.com | DIGITALOCEAN-ASN | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wastetop.website |
| unknown |
placehouse.xyz |
| unknown |
humorscience.website |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
kapetownlink.com |
| malicious |
collect.installeranalytics.com |
| unknown |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4008 | Roxys Tune Up Final By Caroo.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
4008 | Roxys Tune Up Final By Caroo.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
4008 | Roxys Tune Up Final By Caroo.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
4008 | Roxys Tune Up Final By Caroo.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4008 | Roxys Tune Up Final By Caroo.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2672 | go.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2672 | go.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2672 | go.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2672 | go.exe | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
2672 | go.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
5 ETPRO signatures available at the full report