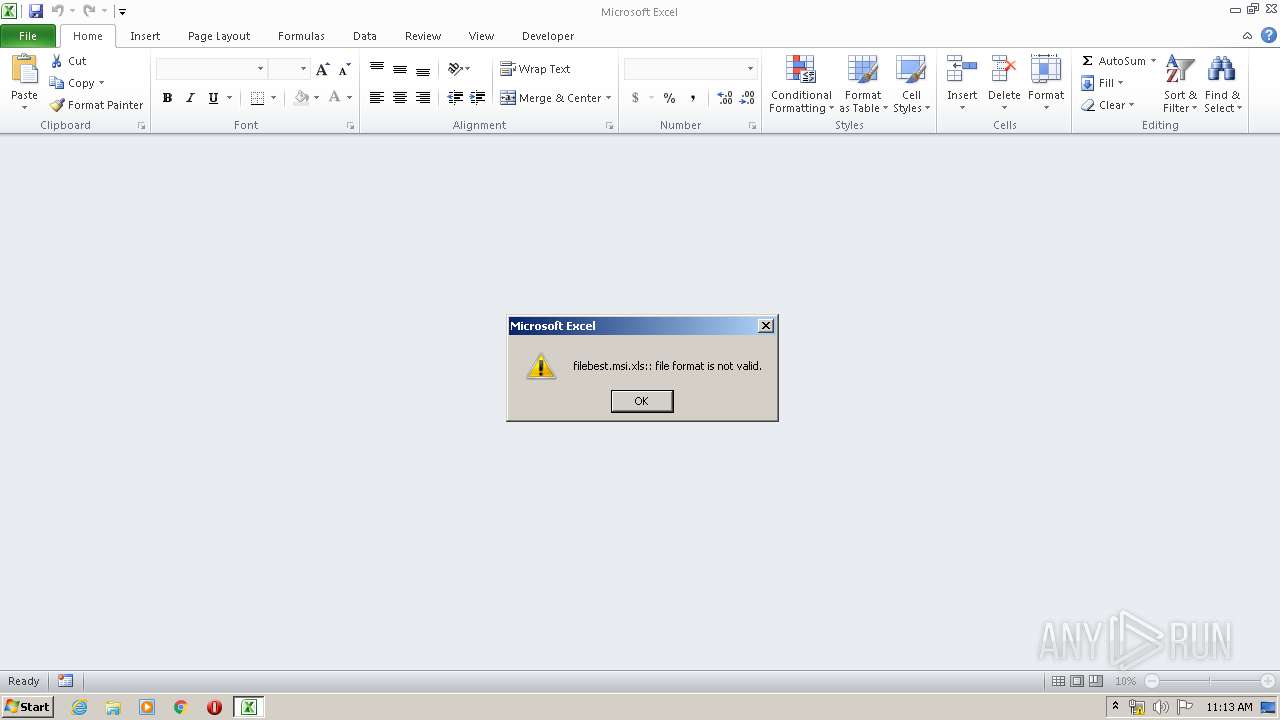
| File name: | filebest.msi |
| Full analysis: | https://app.any.run/tasks/7254d0cb-cc6c-45a6-a35f-f2e39b290165 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | May 30, 2020, 10:13:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Code page: 1252, Last Printed: Fri Sep 21 10:56:09 2012, Create Time/Date: Fri Sep 21 10:56:09 2012, Name of Creating Application: Windows Installer, Title: Exe to msi converter free, Author: www.exetomsi.com, Template: ;0, Last Saved By: devuser, Revision Number: {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E}, Last Saved Time/Date: Tue May 21 12:56:44 2013, Number of Pages: 100, Number of Words: 0, Security: 0 |
| MD5: | B99E0ABDC6AB2AABB9523D5D2B0BA92D |
| SHA1: | 83C428FDF452C2EAE45E4802EBD8E297D47C4F77 |
| SHA256: | 3C9DC2CB717D4CEC7A2D0C0868ABC49DF469162002698B52B95EB94791F430D5 |
| SSDEEP: | 12288:9EouuQtqB5urTIoYWBQk1E+VF9mOx9si:9E8QtqBorTlYWBhE+V3mO |
MALICIOUS
HAWKEYE was detected
- MSI9BB8.tmp (PID: 1428)
Changes the autorun value in the registry
- MSI9BB8.tmp (PID: 1428)
Actions looks like stealing of personal data
- vbc.exe (PID: 444)
- vbc.exe (PID: 968)
Changes settings of System certificates
- MSI9BB8.tmp (PID: 1428)
SUSPICIOUS
Creates files in the user directory
- MSI9BB8.tmp (PID: 1428)
Executable content was dropped or overwritten
- MSI9BB8.tmp (PID: 1428)
Checks for external IP
- MSI9BB8.tmp (PID: 1428)
Executes scripts
- MSI9BB8.tmp (PID: 1428)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 968)
Adds / modifies Windows certificates
- MSI9BB8.tmp (PID: 1428)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1396)
Application was dropped or rewritten from another process
- MSI9BB8.tmp (PID: 1428)
Manual execution by user
- explorer.exe (PID: 3592)
- msiexec.exe (PID: 2340)
Reads settings of System Certificates
- MSI9BB8.tmp (PID: 1428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| LastPrinted: | 2012:09:21 09:56:09 |
| CreateDate: | 2012:09:21 09:56:09 |
| Software: | Windows Installer |
| Title: | Exe to msi converter free |
| Subject: | - |
| Author: | www.exetomsi.com |
| Keywords: | - |
| Comments: | - |
| Template: | ;0 |
| LastModifiedBy: | devuser |
| RevisionNumber: | {C35CF0AA-9B3F-4903-9F05-EBF606D58D3E} |
| ModifyDate: | 2013:05:21 11:56:44 |
| Pages: | 100 |
| Words: | - |
| Security: | None |
Total processes
48
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | MSI9BB8.tmp | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 968 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | MSI9BB8.tmp | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1428 | "C:\Windows\Installer\MSI9BB8.tmp" | C:\Windows\Installer\MSI9BB8.tmp | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Phulli Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2340 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\filebest.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3592 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 782
Read events
529
Write events
1 245
Delete events
8
Modification events
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | >v4 |
Value: 3E76340074050000010000000000000000000000 | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1396) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1396 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR9A3E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1396 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF1840F87F00122E9A.TMP | — | |
MD5:— | SHA256:— | |||
| 968 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holderwb.txt | — | |
MD5:— | SHA256:— | |||
| 1428 | MSI9BB8.tmp | C:\Users\admin\AppData\Roaming\pidloc.txt | text | |
MD5:— | SHA256:— | |||
| 1428 | MSI9BB8.tmp | C:\Users\admin\AppData\Roaming\WindowsUpdate.exe | executable | |
MD5:— | SHA256:— | |||
| 1428 | MSI9BB8.tmp | C:\Users\admin\AppData\Roaming\pid.txt | text | |
MD5:0663A4DDCEACB40B095EDA264A85F15C | SHA256:DA4BB298D82E8B0C1CDE703B60549806E385DF057824E9C9B032167C945B0FA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
4
DNS requests
2
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1428 | MSI9BB8.tmp | GET | 301 | 104.16.154.36:80 | http://whatismyipaddress.com/ | US | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1428 | MSI9BB8.tmp | 104.16.154.36:80 | whatismyipaddress.com | Cloudflare Inc | US | shared |
1428 | MSI9BB8.tmp | 66.102.1.108:587 | smtp.gmail.com | Google Inc. | US | whitelisted |
1428 | MSI9BB8.tmp | 104.16.154.36:443 | whatismyipaddress.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
whatismyipaddress.com |
| shared |
smtp.gmail.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1428 | MSI9BB8.tmp | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
1428 | MSI9BB8.tmp | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
1428 | MSI9BB8.tmp | A Network Trojan was detected | SPYWARE [PTsecurity] HawkEye / Predator Pain (IP Chck) |
1428 | MSI9BB8.tmp | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2 ETPRO signatures available at the full report