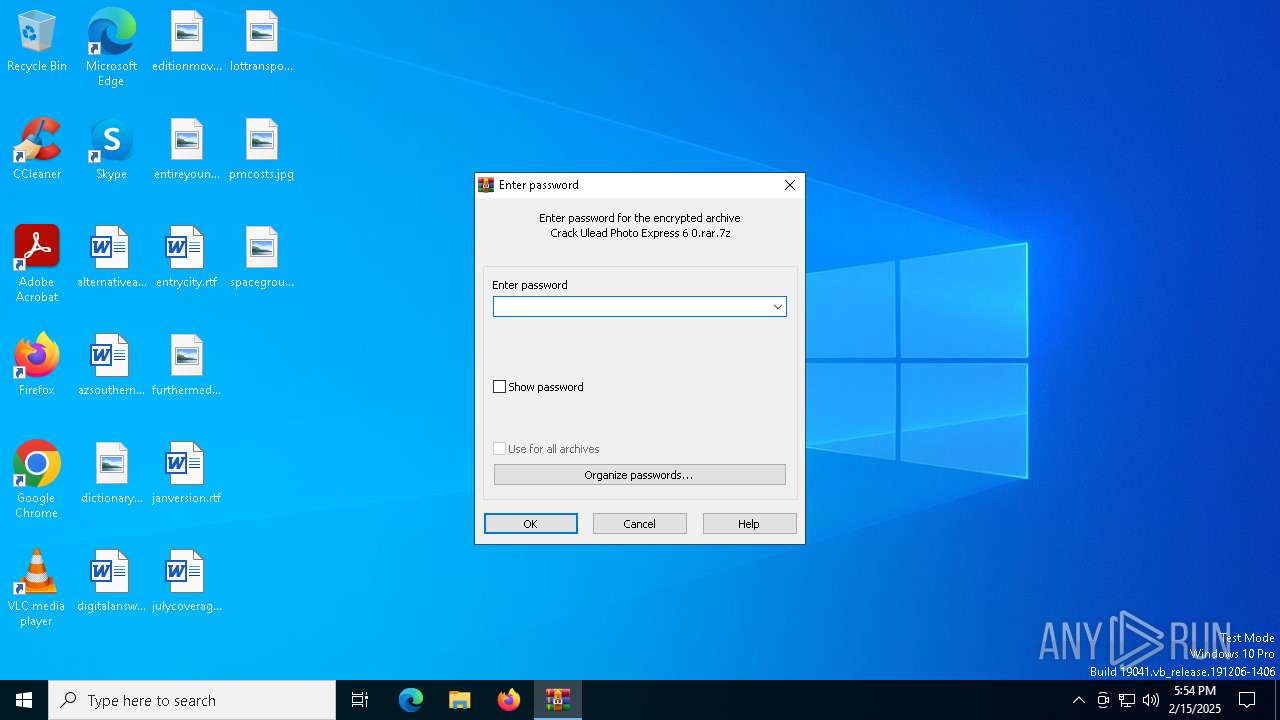
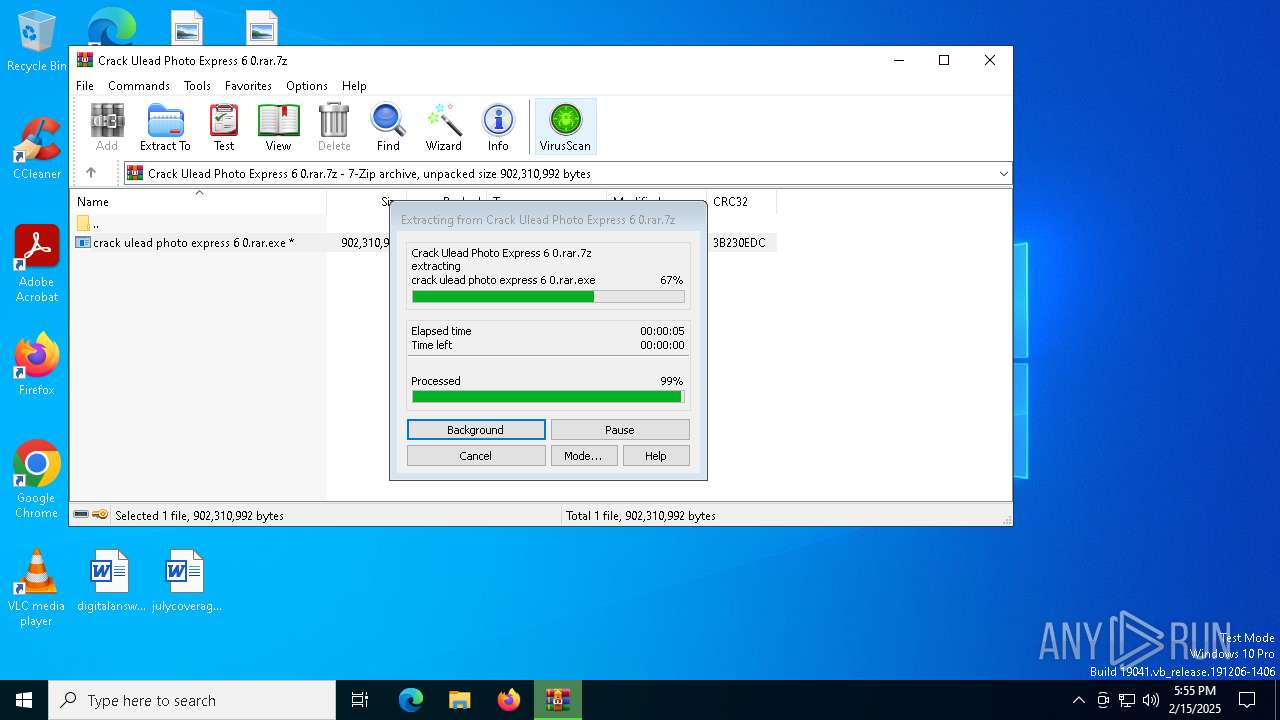
| File name: | Crack Ulead Photo Express 6 0.rar.7z |
| Full analysis: | https://app.any.run/tasks/ec9e2dd3-698d-4f1e-86a0-36ec685f110d |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | February 15, 2025, 17:54:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3286D33D0E0DBBC0C409C55B1691165D |
| SHA1: | 7A56352491D85F7AA1DC3E72C7042300ACFA6646 |
| SHA256: | 3BF72B2F0DC069944B93F20C5E86230CC6B4CC5B403A9F6610F8B70CA50C419A |
| SSDEEP: | 196608:agkme5SEDsH0/ZH20ClVvDItsHMTIA8QIBmDO:agkme5FQU/ZWuoMUAowO |
MALICIOUS
LUMMA has been detected (SURICATA)
- Arabic.com (PID: 3772)
- svchost.exe (PID: 2192)
Actions looks like stealing of personal data
- Arabic.com (PID: 3772)
LUMMA mutex has been found
- Arabic.com (PID: 3772)
AutoIt loader has been detected (YARA)
- Arabic.com (PID: 3772)
Connects to the CnC server
- svchost.exe (PID: 2192)
Steals credentials from Web Browsers
- Arabic.com (PID: 3772)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5592)
- crack ulead photo express 6 0.rar.exe (PID: 4140)
Starts CMD.EXE for commands execution
- crack ulead photo express 6 0.rar.exe (PID: 4140)
- cmd.exe (PID: 3532)
Executing commands from a ".bat" file
- crack ulead photo express 6 0.rar.exe (PID: 4140)
Get information on the list of running processes
- cmd.exe (PID: 3532)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3532)
The executable file from the user directory is run by the CMD process
- Arabic.com (PID: 3772)
Starts application with an unusual extension
- cmd.exe (PID: 3532)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- Arabic.com (PID: 3772)
Searches for installed software
- Arabic.com (PID: 3772)
There is functionality for taking screenshot (YARA)
- Arabic.com (PID: 3772)
Starts the AutoIt3 executable file
- cmd.exe (PID: 3532)
Application launched itself
- cmd.exe (PID: 3532)
INFO
Manual execution by a user
- WinRAR.exe (PID: 5592)
Checks supported languages
- crack ulead photo express 6 0.rar.exe (PID: 4140)
- expand.exe (PID: 5748)
- Arabic.com (PID: 3772)
- extrac32.exe (PID: 5252)
Reads the computer name
- crack ulead photo express 6 0.rar.exe (PID: 4140)
- Arabic.com (PID: 3772)
- extrac32.exe (PID: 5252)
Create files in a temporary directory
- expand.exe (PID: 5748)
- crack ulead photo express 6 0.rar.exe (PID: 4140)
- extrac32.exe (PID: 5252)
Process checks computer location settings
- crack ulead photo express 6 0.rar.exe (PID: 4140)
Reads mouse settings
- Arabic.com (PID: 3772)
Reads the software policy settings
- Arabic.com (PID: 3772)
Creates a new folder
- cmd.exe (PID: 5628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
140
Monitored processes
19
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | cmd /c copy /b ..\Namibia.xls + ..\Alan.xls + ..\Limitations.xls + ..\Computer.xls + ..\Men.xls + ..\Bryan.xls + ..\Certificates.xls + ..\Watts.xls H | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3532 | "C:\WINDOWS\system32\cmd.exe" /c expand Valves.xls Valves.xls.bat & Valves.xls.bat | C:\Windows\SysWOW64\cmd.exe | — | crack ulead photo express 6 0.rar.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3772 | Arabic.com H | C:\Users\admin\AppData\Local\Temp\210993\Arabic.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 3816 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3992 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4140 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb5592.45700\crack ulead photo express 6 0.rar.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb5592.45700\crack ulead photo express 6 0.rar.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4548 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4592 | findstr /V "pupils" Controls | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4624 | cmd /c copy /b 210993\Arabic.com + Approval + Cholesterol + Plenty + Reaches + Benefit + Zope + Dale + Cp + Sensors + Oldest + Imagination 210993\Arabic.com | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 477
Read events
4 460
Write events
17
Delete events
0
Modification events
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000001603050000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F0000000000000000000000000000000000000000000060305000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (6484) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000C20206000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (5592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
0
Suspicious files
22
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb5592.45700\crack ulead photo express 6 0.rar.exe | — | |
MD5:— | SHA256:— | |||
| 4140 | crack ulead photo express 6 0.rar.exe | C:\Users\admin\AppData\Local\Temp\Computer.xls | binary | |
MD5:30400E574D4AB9712C19770FE995EF1F | SHA256:E1861FADEC05BF22DA8BAB0436990ACC35D68847D78BF140E7A0E7AF3F46D9A5 | |||
| 5252 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Cp | binary | |
MD5:2B8A576A5176797713F708962E4EF4F9 | SHA256:AC786EF1EE2EF00887B46AEEB308F118DA017F776E4A93D0593BE0A0F0D385D4 | |||
| 4140 | crack ulead photo express 6 0.rar.exe | C:\Users\admin\AppData\Local\Temp\Valves.xls | text | |
MD5:8A88D483165EB766EABBD6D51B2D87A7 | SHA256:8F476CF288A133A273B4246C79F2C3B10DA444E4A428E8597BF39B67EB08360C | |||
| 4140 | crack ulead photo express 6 0.rar.exe | C:\Users\admin\AppData\Local\Temp\Alan.xls | binary | |
MD5:509D882D25965E8A823B670EB2A76238 | SHA256:33376E37C471F169356BA7F9555560DCC4F063B3F5A8E76369D9B94E1047BA6E | |||
| 4140 | crack ulead photo express 6 0.rar.exe | C:\Users\admin\AppData\Local\Temp\Ii.xls | compressed | |
MD5:7FE41A83AB6AD006DB9A1C28B8CA3EC1 | SHA256:F698159AB0BE5B50284D3FDBB903A2E77C814E9EDFAAE7BDA18AE34513A946F2 | |||
| 5252 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Approval | binary | |
MD5:91983E305A84719726F0ECAAF00FC4A3 | SHA256:44040CDE9FAA895796644B346B67E9F39D113B97D464143537EC9669CAD24264 | |||
| 5252 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Controls | binary | |
MD5:C72236CAEEA8855E0B2BABF7E5F55BA7 | SHA256:0C0C627756CD24BE429B5893E813A341D4941F966D657B974546E4CFBF7D4AC9 | |||
| 4140 | crack ulead photo express 6 0.rar.exe | C:\Users\admin\AppData\Local\Temp\Certificates.xls | binary | |
MD5:6D2DE9590B607EC4D0F9B6FCDFB06E13 | SHA256:9A54E926AF101DDD5F34D4C48AFA21217983AF7BE75D88296B5D300ABF4A257F | |||
| 5252 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Dale | binary | |
MD5:F24BC2C05B161A38723BE86EDC26CB60 | SHA256:D5395389454DDEE5BD5D8F44A07094FDFBA44206D5D7A3481BABD5E4F453AF3B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
24
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6176 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7036 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 92.123.104.12:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3508 | svchost.exe | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3508 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (shiningrstars .help) |
3772 | Arabic.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (shiningrstars .help in TLS SNI) |
3772 | Arabic.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (shiningrstars .help in TLS SNI) |
3772 | Arabic.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (shiningrstars .help in TLS SNI) |
3772 | Arabic.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (shiningrstars .help in TLS SNI) |
3772 | Arabic.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (shiningrstars .help in TLS SNI) |
3772 | Arabic.com | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (shiningrstars .help in TLS SNI) |
2192 | svchost.exe | Misc activity | ET FILE_SHARING Anonymous File Sharing Domain in DNS Lookup (qu .ax) |
3772 | Arabic.com | Misc activity | ET FILE_SHARING Observed Anonymous File Sharing Service Domain (qu .ax) in TLS SNI |