| File name: | file |
| Full analysis: | https://app.any.run/tasks/8ae9d853-6e91-4ced-8e17-d4f97d41475e |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | August 24, 2023, 17:21:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | E35CAB492708456C94AD9EE0BEB35544 |
| SHA1: | C48364BC381F70F0AA936700C024D6EB034107CF |
| SHA256: | 3BF5525F7E9536DA0A0CF982FAD11DC70C315868DE1F3FE90C3BD38C0595BF20 |
| SSDEEP: | 196608:gjF5UGBB3FYugDKNVXNtxey54nnIUtA7z0/:4UGBB3gKNhNbH40o |
MALICIOUS
Connects to the CnC server
- file.exe (PID: 3204)
- oneetx.exe (PID: 1716)
- explorer.exe (PID: 1924)
PRIVATELOADER was detected
- file.exe (PID: 3204)
Actions looks like stealing of personal data
- file.exe (PID: 3204)
- CCleaner64.exe (PID: 2436)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- powershell.exe (PID: 2912)
- powershell.exe (PID: 3452)
- powershell.exe (PID: 3460)
- powershell.exe (PID: 2232)
Application was dropped or rewritten from another process
- HLLgzlfa7ECf06BWaX9ocvvk.exe (PID: 1432)
- toolspub2.exe (PID: 2960)
- a2644a17.exe (PID: 3536)
- toolspub2.exe (PID: 3384)
- newplayer.exe (PID: 2788)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 2884)
- oneetx.exe (PID: 1716)
- latestX.exe (PID: 3904)
- updater.exe (PID: 2344)
- QpSq06pGq1Fw2kZC6AaJvcX8.exe (PID: 2260)
- oneetx.exe (PID: 2312)
- updater.exe (PID: 2660)
Changes the autorun value in the registry
- oneetx.exe (PID: 1716)
Uses Task Scheduler to run other applications
- oneetx.exe (PID: 1716)
- explorer.exe (PID: 1924)
Creates a writable file the system directory
- svchost.exe (PID: 876)
- file.exe (PID: 3204)
- powershell.exe (PID: 2912)
Steals credentials from Web Browsers
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
ARKEI was detected
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Loads dropped or rewritten executable
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
AMADEY was detected
- oneetx.exe (PID: 1716)
KELIHOS was detected
- oneetx.exe (PID: 1716)
Steals credentials
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Application was injected by another process
- explorer.exe (PID: 1924)
- svchost.exe (PID: 1052)
- spoolsv.exe (PID: 872)
- CCleaner64.exe (PID: 2436)
- lsass.exe (PID: 504)
- svchost.exe (PID: 876)
- conhost.exe (PID: 4004)
- conhost.exe (PID: 2468)
- svchost.exe (PID: 1184)
- wmpnetwk.exe (PID: 1720)
- lsm.exe (PID: 512)
- msiexec.exe (PID: 2724)
- dllhost.exe (PID: 676)
- svchost.exe (PID: 332)
- svchost.exe (PID: 608)
- winlogon.exe (PID: 444)
- svchost.exe (PID: 684)
- IMEDICTUPDATE.EXE (PID: 1240)
- svchost.exe (PID: 1656)
- svchost.exe (PID: 1208)
- taskeng.exe (PID: 980)
- svchost.exe (PID: 772)
- svchost.exe (PID: 816)
- services.exe (PID: 488)
- svchost.exe (PID: 844)
- taskeng.exe (PID: 3044)
- conhost.exe (PID: 2288)
- conhost.exe (PID: 732)
- conhost.exe (PID: 2684)
- conhost.exe (PID: 4052)
- conhost.exe (PID: 3220)
- conhost.exe (PID: 1336)
- conhost.exe (PID: 2392)
- conhost.exe (PID: 2588)
- conhost.exe (PID: 464)
- conhost.exe (PID: 3048)
- conhost.exe (PID: 1480)
- conhost.exe (PID: 4088)
- svchost.exe (PID: 2508)
- WerFault.exe (PID: 300)
- dwm.exe (PID: 1828)
Runs injected code in another process
- a2644a17.exe (PID: 3536)
- dialer.exe (PID: 3644)
- dialer.exe (PID: 1676)
Adds path to the Windows Defender exclusion list
- explorer.exe (PID: 1924)
Modifies hosts file to block updates
- QpSq06pGq1Fw2kZC6AaJvcX8.exe (PID: 2260)
Uses Task Scheduler to autorun other applications
- powershell.exe (PID: 2520)
- powershell.exe (PID: 3452)
- powershell.exe (PID: 2456)
- powershell.exe (PID: 2232)
AMADEY detected by memory dumps
- oneetx.exe (PID: 1716)
SMOKE was detected
- explorer.exe (PID: 1924)
MINER was detected
- svchost.exe (PID: 332)
SUSPICIOUS
Connects to the server without a host name
- file.exe (PID: 3204)
- oneetx.exe (PID: 1716)
Reads the Internet Settings
- file.exe (PID: 3204)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- HLLgzlfa7ECf06BWaX9ocvvk.exe (PID: 1432)
- newplayer.exe (PID: 2788)
- oneetx.exe (PID: 1716)
- powershell.exe (PID: 1392)
- powershell.exe (PID: 3976)
Checks for external IP
- file.exe (PID: 3204)
Reads security settings of Internet Explorer
- file.exe (PID: 3204)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Checks Windows Trust Settings
- file.exe (PID: 3204)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Reads settings of System Certificates
- file.exe (PID: 3204)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Process requests binary or script from the Internet
- file.exe (PID: 3204)
- oneetx.exe (PID: 1716)
Executable content was dropped or overwritten
- file.exe (PID: 3204)
- HLLgzlfa7ECf06BWaX9ocvvk.exe (PID: 1432)
- newplayer.exe (PID: 2788)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- oneetx.exe (PID: 1716)
- QpSq06pGq1Fw2kZC6AaJvcX8.exe (PID: 2260)
- explorer.exe (PID: 1924)
- updater.exe (PID: 2344)
- updater.exe (PID: 2660)
Application launched itself
- toolspub2.exe (PID: 2960)
- cmd.exe (PID: 2544)
- explorer.exe (PID: 1924)
Starts itself from another location
- newplayer.exe (PID: 2788)
Starts CMD.EXE for commands execution
- oneetx.exe (PID: 1716)
- explorer.exe (PID: 1924)
- cmd.exe (PID: 2544)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2544)
Reads browser cookies
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Connects to unusual port
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- dialer.exe (PID: 3288)
- explorer.exe (PID: 4088)
Executes as Windows Service
- raserver.exe (PID: 2828)
Searches for installed software
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Starts POWERSHELL.EXE for commands execution
- explorer.exe (PID: 1924)
Script adds exclusion path to Windows Defender
- explorer.exe (PID: 1924)
Starts SC.EXE for service management
- cmd.exe (PID: 3924)
- cmd.exe (PID: 2588)
- cmd.exe (PID: 3684)
- cmd.exe (PID: 2672)
Uses powercfg.exe to modify the power settings
- cmd.exe (PID: 2392)
- cmd.exe (PID: 2944)
- cmd.exe (PID: 2880)
- cmd.exe (PID: 1916)
Adds/modifies Windows certificates
- services.exe (PID: 488)
The process executes via Task Scheduler
- updater.exe (PID: 2344)
- oneetx.exe (PID: 2312)
- updater.exe (PID: 2660)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 2344)
- updater.exe (PID: 2660)
Unusual connection from system programs
- powershell.exe (PID: 2912)
The Powershell connects to the Internet
- powershell.exe (PID: 2912)
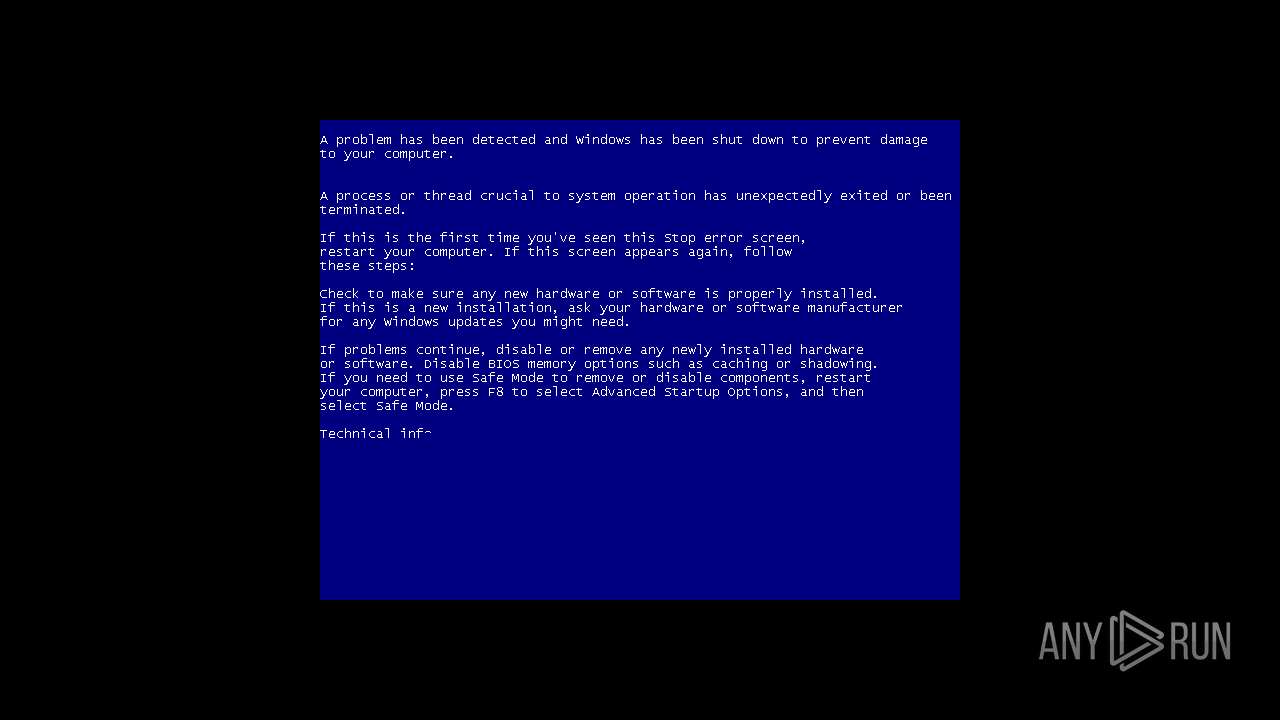
Executes application which crashes
- svchost.exe (PID: 2508)
The process creates files with name similar to system file names
- WerFault.exe (PID: 300)
INFO
Creates files in the program directory
- svchost.exe (PID: 876)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- QpSq06pGq1Fw2kZC6AaJvcX8.exe (PID: 2260)
- updater.exe (PID: 2344)
Process checks computer location settings
- file.exe (PID: 3204)
Checks supported languages
- file.exe (PID: 3204)
- HLLgzlfa7ECf06BWaX9ocvvk.exe (PID: 1432)
- QpSq06pGq1Fw2kZC6AaJvcX8.exe (PID: 2260)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- a2644a17.exe (PID: 3536)
- toolspub2.exe (PID: 2960)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 2884)
- newplayer.exe (PID: 2788)
- toolspub2.exe (PID: 3384)
- oneetx.exe (PID: 1716)
- latestX.exe (PID: 3904)
- oneetx.exe (PID: 2312)
- updater.exe (PID: 2344)
- updater.exe (PID: 2660)
Reads the machine GUID from the registry
- file.exe (PID: 3204)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- newplayer.exe (PID: 2788)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 2884)
- oneetx.exe (PID: 1716)
Checks proxy server information
- file.exe (PID: 3204)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- oneetx.exe (PID: 1716)
Creates files or folders in the user directory
- dllhost.exe (PID: 676)
- file.exe (PID: 3204)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- oneetx.exe (PID: 1716)
- explorer.exe (PID: 1924)
Reads the computer name
- HLLgzlfa7ECf06BWaX9ocvvk.exe (PID: 1432)
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
- newplayer.exe (PID: 2788)
- oneetx.exe (PID: 1716)
- 31839b57a4f11171d6abc8bbc4451ee4.exe (PID: 2884)
- file.exe (PID: 3204)
Create files in a temporary directory
- HLLgzlfa7ECf06BWaX9ocvvk.exe (PID: 1432)
- newplayer.exe (PID: 2788)
- oneetx.exe (PID: 1716)
- QpSq06pGq1Fw2kZC6AaJvcX8.exe (PID: 2260)
Reads product name
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Reads Environment values
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Reads CPU info
- hCqwkDJJE7ppEx2IzTHfJRzd.exe (PID: 680)
Manual execution by a user
- powershell.exe (PID: 1392)
- dialer.exe (PID: 3644)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 3924)
- powershell.exe (PID: 2520)
- schtasks.exe (PID: 2256)
Reads the Internet Settings
- explorer.exe (PID: 1924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(1716) oneetx.exe
C2 (1)http://45.9.74.80
Version3.83
Options
Drop directory207aa4515d
Drop nameoneetx.exe
Strings (116)SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Startup
Rem
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
rundll32
/Delete /TN "
Programs
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
%USERPROFILE%
\App
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
&og=
cred.dll|clip.dll|
d1
e1
e0
Main
http://
https://
exe
dll
cmd
ps1
<c>
<d>
Plugins/
+++
#
|
&unit=
=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
rb
wb
Content-Type: multipart/form-data; boundary=----
------
Content-Disposition: form-data; name="data"; filename="
"
Content-Type: application/octet-stream
------
--
?scr=1
.jpg
Content-Type: application/x-www-form-urlencoded
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
ComputerName
abcdefghijklmnopqrstuvwxyz0123456789-_
-unicode-
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\BasicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
2019
2022
2016
CurrentBuild
&&
echo Y|CACLS "
" /P "
:N"
CACLS "
" /P "
:R" /E
:F" /E
&&Exit
..\
\
:::
rundll32.exe
/k
"taskkill /f /im "
" && timeout 1 && del
&& Exit"
" && ren
&&
Powershell.exe
-executionpolicy remotesigned -File "
"
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| ProductVersion: | 1.0.1.6 |
|---|---|
| ProductName: | DarkLab |
| OriginalFileName: | DarkLab.exe |
| LegalCopyright: | Copyright (C) 2023 DarkLab |
| InternalName: | DarkLab.exe |
| FileVersion: | 1.0.1.6 |
| FileDescription: | DarkLab |
| CompanyName: | DarkLab |
| CharacterSet: | Unicode |
| LanguageCode: | German |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT |
| FileFlags: | Patched, Private build |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.1.6 |
| FileVersionNumber: | 1.0.1.6 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x778b7b |
| UninitializedDataSize: | - |
| InitializedDataSize: | 489472 |
| CodeSize: | 3209728 |
| LinkerVersion: | 14.29 |
| PEType: | PE32+ |
| ImageFileCharacteristics: | No relocs, Executable, Large address aware |
| TimeStamp: | 2023:08:24 09:01:48+00:00 |
| MachineType: | AMD AMD64 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_AMD64 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 24-Aug-2023 09:01:48 |
| Detected languages: |
|
| CompanyName: | DarkLab |
| FileDescription: | DarkLab |
| FileVersion: | 1.0.1.6 |
| InternalName: | DarkLab.exe |
| LegalCopyright: | Copyright (C) 2023 DarkLab |
| OriginalFilename: | DarkLab.exe |
| ProductName: | DarkLab |
| ProductVersion: | 1.0.1.6 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_AMD64 |
| Number of sections: | 9 |
| Time date stamp: | 24-Aug-2023 09:01:48 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00F0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0030F905 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.rdata | 0x00311000 | 0x0003C176 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.data | 0x0034E000 | 0x00012490 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.pdata | 0x00361000 | 0x000157C8 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
_RDATA | 0x00377000 | 0x000000FC | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.text0 | 0x00378000 | 0x003ED35E | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.text1 | 0x00766000 | 0x00000C28 | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.133922 |
.text2 | 0x00767000 | 0x00780ED8 | 0x00781000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_NOT_PAGED, IMAGE_SCN_MEM_READ | 7.82438 |
.rsrc | 0x00EE8000 | 0x00010DA8 | 0x00010E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.61851 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.89623 | 392 | UNKNOWN | English - United States | RT_MANIFEST |
107 | 1.98048 | 20 | UNKNOWN | Russian - Russia | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
148
Monitored processes
129
Malicious processes
22
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\Windows\system32\WerFault.exe -u -p 2760 -s 16 | C:\Windows\System32\WerFault.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 356 | CACLS "oneetx.exe" /P "admin:N" | C:\Windows\SysWOW64\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 444 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 464 | \??\C:\Windows\system32\conhost.exe "-420669810-59555211800987024563541757-1877059622-338748490-951672118-53257570" | C:\Windows\System32\conhost.exe | csrss.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 488 | C:\Windows\system32\services.exe | C:\Windows\System32\services.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 504 | C:\Windows\system32\lsass.exe | C:\Windows\System32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Exit code: 0 Version: 6.1.7601.23915 (win7sp1_ldr.170913-0600) Modules
| |||||||||||||||
| 512 | C:\Windows\system32\lsm.exe | C:\Windows\System32\lsm.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Session Manager Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 608 | C:\Windows\system32\svchost.exe -k DcomLaunch | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | sc stop UsoSvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
71 978
Read events
71 603
Write events
349
Delete events
26
Modification events
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{01979c6a-42fa-414c-b8aa-eee2c8202018}.check.100 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A00000000020000000000106600000001000020000000C4B1A467741734F3821BFCAAE610C2C2C81049CFA634A473AD86B580DBADDFB4000000000E8000000002000020000000C1F736FD4202246DC32D75F1C4293A0CB97E28E07C19256F19A5980840F3F9A5B00000003C566115544BF2EA09A65DFFFF9D38423FBA9B473395EDD59BC11E4754ADB46175988D82CCA22CDF675BD8D394B777E893B29CE8DA031ED0604E6D63576A331D5C2D9746B62D7088A1893172D010B2367B4342A5A704675DFFBD756CF454EFF77D486FF8AF0808163C4DDF5213D8CB2E9A6F4B275ABE38818982110D78669D465F91CC8D8CF0B61066D6618DB1C944FDDFAA9223CBA538DB6BB9A1CCB6A6450C4B35EF15E80DFE1578668A8C46A0FA4D400000004124FE3232A0A0CC9F187D77848FE12C018FC81529264685E637C4A08C272C05C4B50DF68918485586392BD9C6978FEBB51B77C814837675FA3A156450929549 | |||
| (PID) Process: | (332) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {00E51A5A-6FF0-414A-B358-C7EB6484BAF5} |
Value: 525400363EFF | |||
| (PID) Process: | (1924) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A00000000020000000000106600000001000020000000DE596CC00FA0CE6036B57F3745DF211B8CEDC7563B5C7C90E189DFBFE4E216FC000000000E800000000200002000000034A09CAFA8980668BD48169E708CCFDA06F4ADAD9A6D0FF324841FD89016AF6F3000000097B2B3329B62DD4C9AB1E283BD9359B999E8411B9FC15AF795BFA67D05007F5CE28F7E84193A17AFEBE2A486810ADC32400000007E5B4D515AE7EE2B367ED77D5D9A272891BC7B3019A3AA7BC4BF2CA5315073E7F321A33013E44AD95CE9A5E9CA3FF01D3584C54FECFB9C1227BA4AE46F87EAF7 | |||
| (PID) Process: | (3204) file.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{65EBFF6D-3B2F-49E5-9E63-ECD2F89ABC07}User |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3204) file.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3204) file.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{65EBFF6D-3B2F-49E5-9E63-ECD2F89ABC07}Machine |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3204) file.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{65EBFF6D-3B2F-49E5-9E63-ECD2F89ABC07}Machine\SOFTWARE |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3204) file.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{65EBFF6D-3B2F-49E5-9E63-ECD2F89ABC07}Machine\SOFTWARE\Policies |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3204) file.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{65EBFF6D-3B2F-49E5-9E63-ECD2F89ABC07}Machine\SOFTWARE\Policies\Microsoft |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3204) file.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{65EBFF6D-3B2F-49E5-9E63-ECD2F89ABC07}Machine\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
25
Suspicious files
49
Text files
17
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 676 | dllhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat | — | |
MD5:— | SHA256:— | |||
| 3204 | file.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\HQYU0XHJ\tmvwr[1].bmp | — | |
MD5:— | SHA256:— | |||
| 3204 | file.exe | C:\Users\admin\Pictures\Minor Policy\QpSq06pGq1Fw2kZC6AaJvcX8.exe | — | |
MD5:— | SHA256:— | |||
| 3204 | file.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:CDFD60E717A44C2349B553E011958B85 | SHA256:0EE08DA4DA3E4133E1809099FC646468E7156644C9A772F704B80E338015211F | |||
| 3204 | file.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\26RFQ5FQ.txt | text | |
MD5:8E52AEE30AACE8405313C8A246EB259F | SHA256:2F42C8518445F6FE34C0CD1B41E7F87D156136390D3004543F68FEE42C860D18 | |||
| 876 | svchost.exe | C:\ProgramData\ntuser.pol | binary | |
MD5:76671BB4551FD5C17A70C0887A244756 | SHA256:9407AEBA273CBE186E10D7B2E5F3739456271446B82012D6B0410F7BA0A2B956 | |||
| 3204 | file.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\3KPNZUF8.txt | text | |
MD5:05E63056E2947964B41F435DA8DE9813 | SHA256:622F2A07ABFF086AA25552F005F06268B6FD4D658202FC9D08C049316EB47664 | |||
| 3204 | file.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\RQU3256D.txt | text | |
MD5:7A1AE004864DF2F7A13821D9ED2C2091 | SHA256:31A83D72405E5E447D54B6B61BD6E62462B1AB394DC1631BB7BB76D081FAB40E | |||
| 3204 | file.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\JOYHNSIG.txt | text | |
MD5:4DDA4A059F533253F03356C1CF44B448 | SHA256:EABA09107E2117A79C9976B51200E20D2D3533A1C8353AAD81D35955B021F88F | |||
| 676 | dllhost.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\V01.log | binary | |
MD5:907D48D22152F2DE93361A3FD7CE015C | SHA256:A4952D2335FC3944038B9763990D0CC5B5BC714EC2C7B2F72456A7C0A199EA62 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
47
DNS requests
14
Threats
44
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3204 | file.exe | HEAD | 404 | 45.9.74.80:80 | http://45.9.74.80/loa.exe | SC | — | — | malicious |
3204 | file.exe | HEAD | 200 | 45.9.74.80:80 | http://45.9.74.80/super.exe | SC | — | — | malicious |
3204 | file.exe | GET | 200 | 45.15.156.229:80 | http://45.15.156.229/api/tracemap.php | RU | text | 15 b | malicious |
2912 | powershell.exe | GET | 304 | 8.238.34.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c5b7611f4098ea60 | US | — | — | whitelisted |
3204 | file.exe | GET | 404 | 94.156.35.76:80 | http://230809204625331.nes.dtf99.top/f/fikim0809331.exe | CY | text | 17 b | suspicious |
1716 | oneetx.exe | GET | 200 | 79.137.192.18:80 | http://79.137.192.18/latestX.exe | RU | executable | 5.60 Mb | malicious |
1716 | oneetx.exe | POST | 200 | 45.9.74.80:80 | http://45.9.74.80/0bjdn2Z/index.php | SC | text | 3 b | malicious |
3204 | file.exe | POST | 200 | 45.15.156.229:80 | http://45.15.156.229/api/firegate.php | RU | text | 108 b | malicious |
3204 | file.exe | POST | 200 | 45.15.156.229:80 | http://45.15.156.229/api/firegate.php | RU | text | 1.04 Kb | malicious |
1924 | explorer.exe | POST | — | 95.86.21.52:80 | http://taibi.at/tmp/ | MK | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3204 | file.exe | 45.15.156.229:80 | — | Galaxy LLC | RU | malicious |
1208 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3204 | file.exe | 104.26.8.59:443 | api.myip.com | CLOUDFLARENET | US | suspicious |
332 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3204 | file.exe | 87.240.132.67:80 | vk.com | VKontakte Ltd | RU | suspicious |
3204 | file.exe | 87.240.132.67:443 | vk.com | VKontakte Ltd | RU | suspicious |
3204 | file.exe | 94.156.35.76:80 | 230809204625331.nes.dtf99.top | Belcloud LTD | CY | suspicious |
3204 | file.exe | 45.9.74.80:80 | — | Delta Ltd | SC | malicious |
3204 | file.exe | 34.117.59.81:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
1716 | oneetx.exe | 45.9.74.80:80 | — | Delta Ltd | SC | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.myip.com |
| suspicious |
ipinfo.io |
| shared |
vk.com |
| whitelisted |
230809204625331.nes.dtf99.top |
| suspicious |
sun6-23.userapi.com |
| unknown |
sun6-22.userapi.com |
| unknown |
teredo.ipv6.microsoft.com |
| whitelisted |
t.me |
| whitelisted |
taibi.at |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3204 | file.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
3204 | file.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET) |
3204 | file.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
332 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3204 | file.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3204 | file.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3204 | file.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
3204 | file.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3204 | file.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
3204 | file.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
9 ETPRO signatures available at the full report