| File name: | Netflix Checker by xRisky (2).rar |
| Full analysis: | https://app.any.run/tasks/cf3703de-4a29-49c4-9294-6d1422065c00 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | January 14, 2025, 03:45:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 6EF6235945F75DAE71D61D0E79684287 |
| SHA1: | 6D91CA22FFD8271794704C1ABA52DEDE7D2ACBA0 |
| SHA256: | 3BC539105A485A56FBC7BE1031E9A6F668F33AD06A52B0A984FB45702225DFB3 |
| SSDEEP: | 12288:EBlPfernA556A/ov7hBGA6QsnzE2A2d6/y3:EBlPfInA556A/oGN7zE2A2U/y3 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1544)
Adds extension to the Windows Defender exclusion list
- conhost.exe (PID: 836)
- cmd.exe (PID: 5256)
- conhost.exe (PID: 6884)
- cmd.exe (PID: 6796)
- conhost.exe (PID: 3060)
- cmd.exe (PID: 5240)
Execute application with conhost.exe as parent process
- cmd.exe (PID: 5256)
- cmd.exe (PID: 6464)
- cmd.exe (PID: 6796)
- sihost64.exe (PID: 2600)
- cmd.exe (PID: 1760)
- cmd.exe (PID: 6088)
- explorer.exe (PID: 6420)
- cmd.exe (PID: 5240)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 5256)
- cmd.exe (PID: 6796)
- cmd.exe (PID: 5240)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 1760)
- cmd.exe (PID: 6464)
MINER has been detected (SURICATA)
- explorer.exe (PID: 6420)
- svchost.exe (PID: 2192)
Connects to the CnC server
- explorer.exe (PID: 6420)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5256)
- cmd.exe (PID: 6796)
- cmd.exe (PID: 5240)
Starts CMD.EXE for commands execution
- conhost.exe (PID: 836)
- conhost.exe (PID: 6884)
- conhost.exe (PID: 3060)
Manipulates environment variables
- powershell.exe (PID: 6352)
- powershell.exe (PID: 6928)
- powershell.exe (PID: 3128)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 5256)
- cmd.exe (PID: 6796)
- cmd.exe (PID: 5240)
Script adds exclusion extension to Windows Defender
- cmd.exe (PID: 5256)
- cmd.exe (PID: 6796)
- cmd.exe (PID: 5240)
Executable content was dropped or overwritten
- conhost.exe (PID: 6884)
- conhost.exe (PID: 836)
Drops a system driver (possible attempt to evade defenses)
- conhost.exe (PID: 6884)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2192)
- explorer.exe (PID: 6420)
Crypto Currency Mining Activity Detected
- explorer.exe (PID: 6420)
Connects to unusual port
- explorer.exe (PID: 6420)
INFO
Manual execution by a user
- NetflixChecker by xRisky.exe (PID: 2676)
- NetflixChecker by xRisky.exe (PID: 3288)
- NetflixChecker by xRisky.exe (PID: 420)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1544)
The process uses the downloaded file
- WinRAR.exe (PID: 1544)
- conhost.exe (PID: 836)
- conhost.exe (PID: 6884)
- conhost.exe (PID: 3060)
- conhost.exe (PID: 4528)
Reads security settings of Internet Explorer
- conhost.exe (PID: 836)
- conhost.exe (PID: 3060)
Checks supported languages
- NetflixChecker by xRisky.exe (PID: 420)
- NetflixChecker by xRisky.exe (PID: 3288)
- services64.exe (PID: 7160)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6352)
- powershell.exe (PID: 5876)
- powershell.exe (PID: 1556)
- powershell.exe (PID: 6928)
- powershell.exe (PID: 1076)
- powershell.exe (PID: 3128)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6352)
- powershell.exe (PID: 5876)
- powershell.exe (PID: 1556)
- powershell.exe (PID: 6928)
- powershell.exe (PID: 3128)
- powershell.exe (PID: 1076)
The sample compiled with japanese language support
- conhost.exe (PID: 6884)
Disables trace logs
- conhost.exe (PID: 6884)
Reads the software policy settings
- conhost.exe (PID: 6884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | - |
| UncompressedSize: | - |
| OperatingSystem: | Win32 |
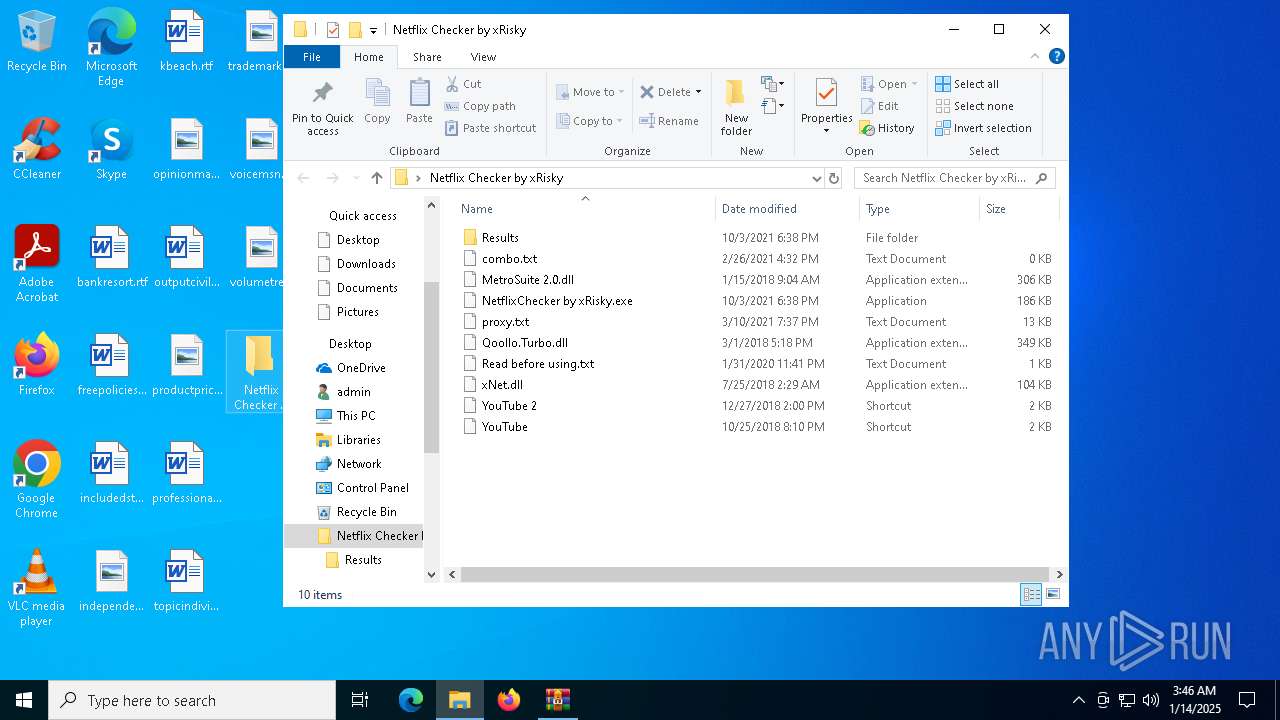
| ArchivedFileName: | Netflix Checker by xRisky/combo.txt |
Total processes
163
Monitored processes
33
Malicious processes
13
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Users\admin\Desktop\Netflix Checker by xRisky\NetflixChecker by xRisky.exe" | C:\Users\admin\Desktop\Netflix Checker by xRisky\NetflixChecker by xRisky.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 836 | "C:\WINDOWS\System32\\conhost.exe" "C:\Users\admin\Desktop\Netflix Checker by xRisky\NetflixChecker by xRisky.exe" | C:\Windows\System32\conhost.exe | NetflixChecker by xRisky.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | powershell -Command "Add-MpPreference -ExclusionExtension @('exe','dll') -Force" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1544 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Netflix Checker by xRisky (2).rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1556 | powershell -Command "Add-MpPreference -ExclusionExtension @('exe','dll') -Force" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "cmd" /c schtasks /create /f /sc onlogon /rl highest /tn "services64" /tr "C:\WINDOWS\system32\services64.exe" | C:\Windows\System32\cmd.exe | conhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | "C:\WINDOWS\system32\Microsoft\Libs\sihost64.exe" | C:\Windows\System32\Microsoft\Libs\sihost64.exe | — | conhost.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 2676 | "C:\Users\admin\Desktop\Netflix Checker by xRisky\NetflixChecker by xRisky.exe" | C:\Users\admin\Desktop\Netflix Checker by xRisky\NetflixChecker by xRisky.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3060 | "C:\WINDOWS\System32\\conhost.exe" "C:\WINDOWS\system32\services64.exe" | C:\Windows\System32\conhost.exe | — | services64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 991
Read events
35 969
Write events
22
Delete events
0
Modification events
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Netflix Checker by xRisky (2).rar | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1544) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6884) conhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\conhost_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6884) conhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\conhost_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
7
Suspicious files
4
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1544.18582\Netflix Checker by xRisky\proxy.txt | text | |
MD5:BB41BD619C663B5260BC226D3B8D3132 | SHA256:C7DF599C7A8425D81645F366AA2B28A14972B50675C7E0B7C01CA54436827A33 | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1544.18582\Netflix Checker by xRisky\Results\10 مارس (20;36;55)\Invalid.txt | text | |
MD5:1FB218BE6B10D33A41EF2139211B937A | SHA256:90B5A68375867C2E5A0F93B440F8BA3D28CB18B690E18C4B7FB5C4784147FB75 | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1544.18582\Netflix Checker by xRisky\YouTube.lnk | binary | |
MD5:C7056A1F92245EEC9E5CA71F406C4811 | SHA256:BDE117478E44D3AA7D55122CF450F10B5AF74CFB4CE82AE4FC6FB7DD414C2469 | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1544.18582\Netflix Checker by xRisky\MetroSuite 2.0.dll | executable | |
MD5:0D30A398CEC0FF006B6EA2B52D11E744 | SHA256:8604BF2A1FE2E94DC1EA1FBD0CF54E77303493B93994DF48479DC683580AA654 | |||
| 1544 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1544.18582\Netflix Checker by xRisky\NetflixChecker by xRisky.exe | executable | |
MD5:F14F5C96F54F8997E7D54973720385BC | SHA256:DBA4ADBE50CF3AB0EFBF35BC5B9930B50B92162CA29EEC77A59DA66A6AB4CD57 | |||
| 1556 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cy32pvon.ykt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1556 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2z1pqsf2.axz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 836 | conhost.exe | C:\Windows\System32\services64.exe | executable | |
MD5:F14F5C96F54F8997E7D54973720385BC | SHA256:DBA4ADBE50CF3AB0EFBF35BC5B9930B50B92162CA29EEC77A59DA66A6AB4CD57 | |||
| 5876 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ecr32zky.3uc.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6928 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1jzfg5k5.p1k.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
51
DNS requests
25
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6296 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6236 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6236 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2736 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 2.16.164.72:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2192 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY Observed DNS Query to Coin Mining Domain (nanopool .org) |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
6420 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
1 ETPRO signatures available at the full report