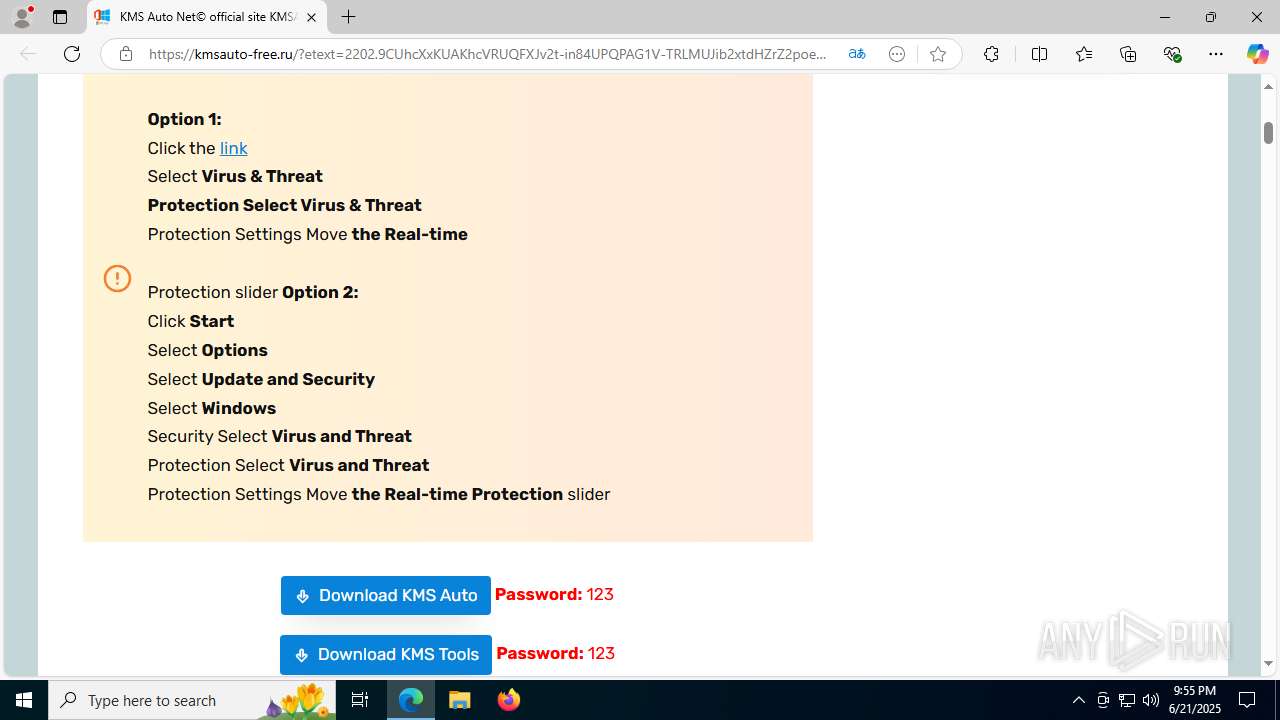
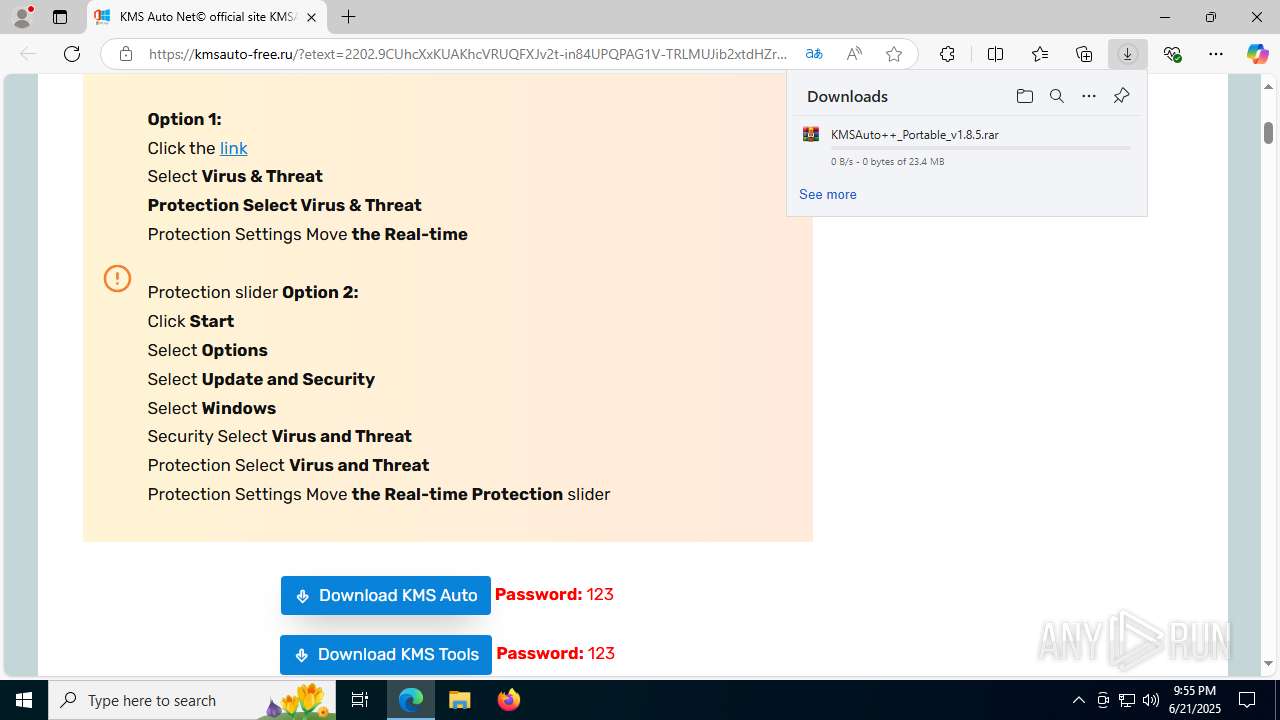
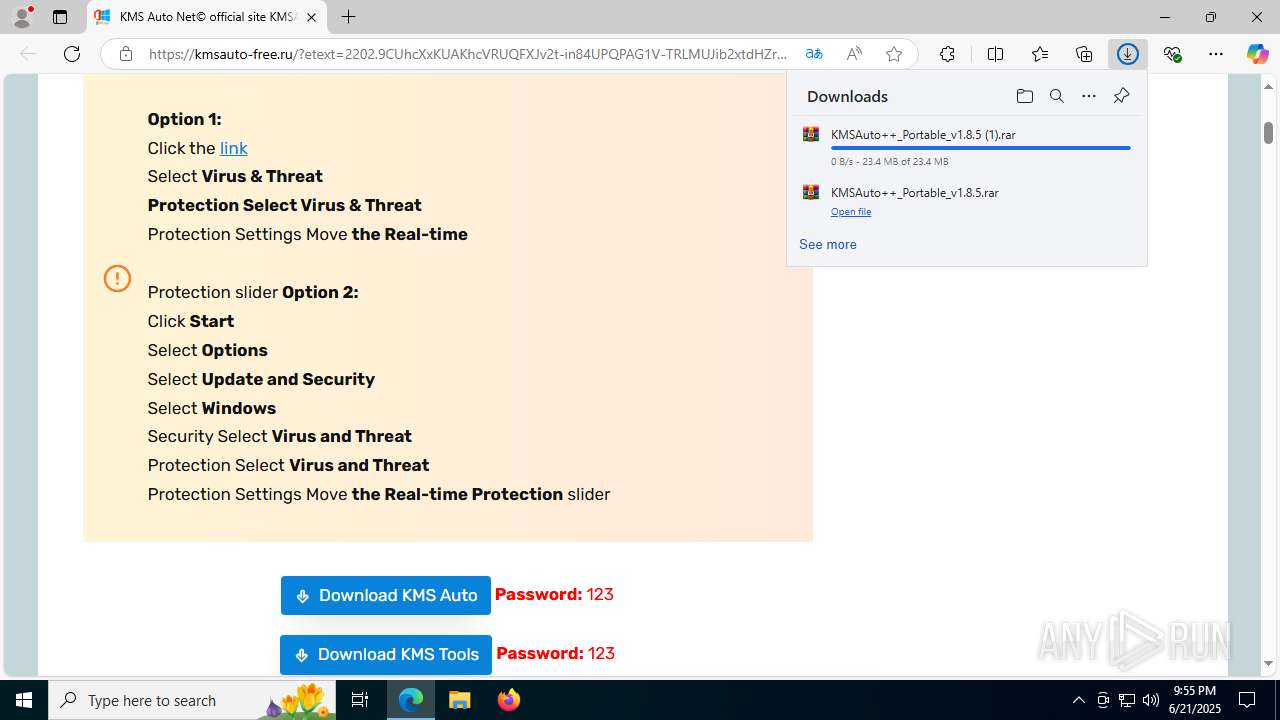
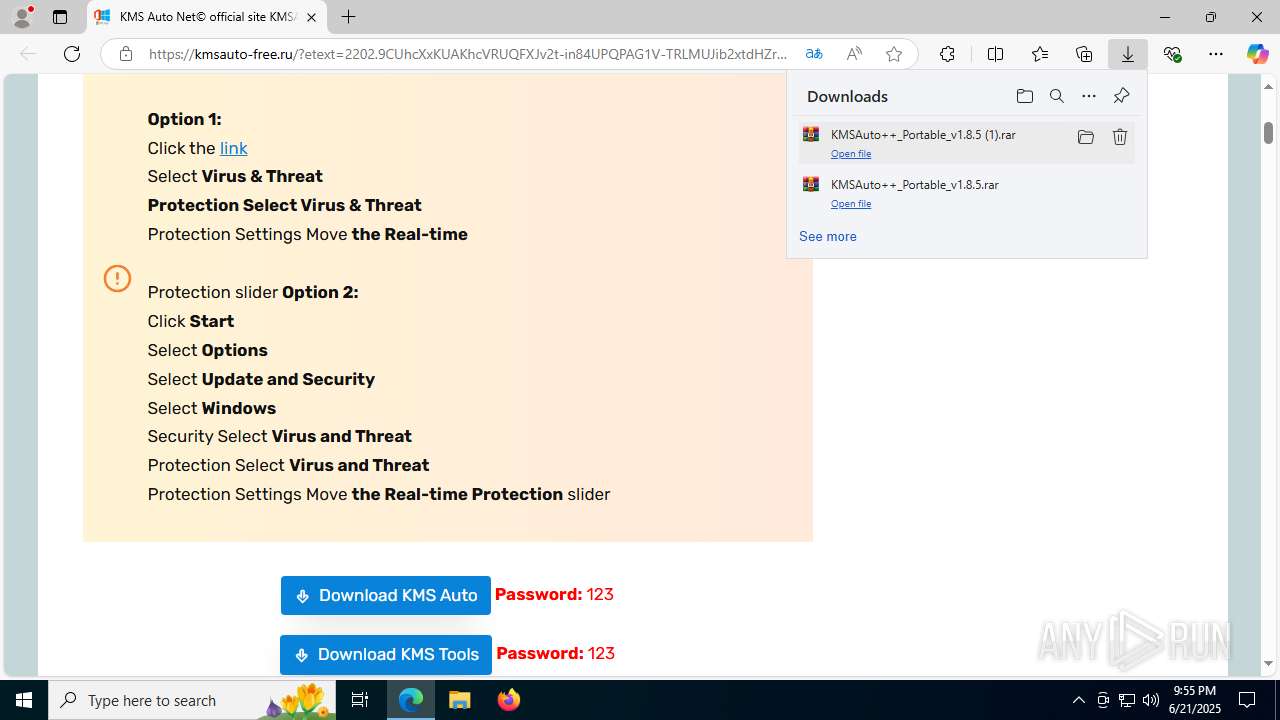
| URL: | https://yabs.yandex.ru/count/WfCejI_zOoVX2Lai0YqK09DbaRw7b904pDum0RrvDmZ8Xe2t0W8wzFbSxkpPVkVETttjVFsErnlkS4ai8OsmMf6kjP7I4ZM9YCCEcBAPuy1yMS21qaVGj4DaeWw3ZkC8tQmVJRAYdAVeR2qC6Q8_UTfw6c8YnYckW2Pq0U4A40lWLg1LLe2s0grk0TeAjBW5Q2lG8Yj0Mq4KOm7Q2gAk5A2j86gn06q5KLOAq5OGfLY0jeAeAWLeAuWg5w2bO1yNeALWTrA0jW8Vv9olYJy3EW3XQa4efwi47h94EgsfGpNiEvhZKNjgHvrHfnE_eSzeVUFFQNxdq_o9GvrGgIq13jRh_JsnRH5IX77AZVU3mISeyTx8fChDlXKpDFZ1oFbymsJZNHxQx3uGS0CuW0tS6-t74s_KtP8mhOQzUMSNfzMmnQ0BuFK2S3a8CJA5rxRbyP26owJPQY_mwF9YrNaR3iC7qcf82E2hWYWh0MmTqEfWNr8asSGXYP9aYnQs9iegc89e2H9dOGSTrkGHfh2riCTa5KDkwbWQnWppTMBO88W3Q0HDC5qfbSxDG27DObDlUTZaBW-RUxED-yCsM-4Fzb6g_dT6bE-T4ULp0H3uz-QKA5-xv8BysIKN9DCiy-K8ioppvGXpN1Rr24MdpSmYXLVe1i32Yj7x05XOCNhhe_Pyq5a6VDdZUPlCdkoNV3bb-J7jmGXiHKQs-MyEoLtRwBUqhkkIahksqMkztbtNI1MVzLxtupcoGobuY3ps8vgPAvLAvOmO2Jpj61t3KeJoStZKmEj2MHOT4_nII0jCY4UzZYrpCWYall33kk6GAbRp0UkL3tFW_VOj3xOs9gLreDq9yMy5LvAWvEzWhRSeg8MLljUy1m00~2?etext=2202.9CUhcXxKUAKhcVRUQFXJv2t-in84UPQPAG1V-TRLMUJib2xtdHZrZ2poemJsb2hs.a92c099e16eb8861724c34f8156c2ebc9cc110ad&from=yandex.ru%3Bsearch%26%23x2F%3B%3Bweb%3B%3B0%3B&q=windows+cracks&baobab_event_id=mc6s1m4p9z |
| Full analysis: | https://app.any.run/tasks/1048a12f-1f6b-42c1-a1bd-7dad20055c4c |
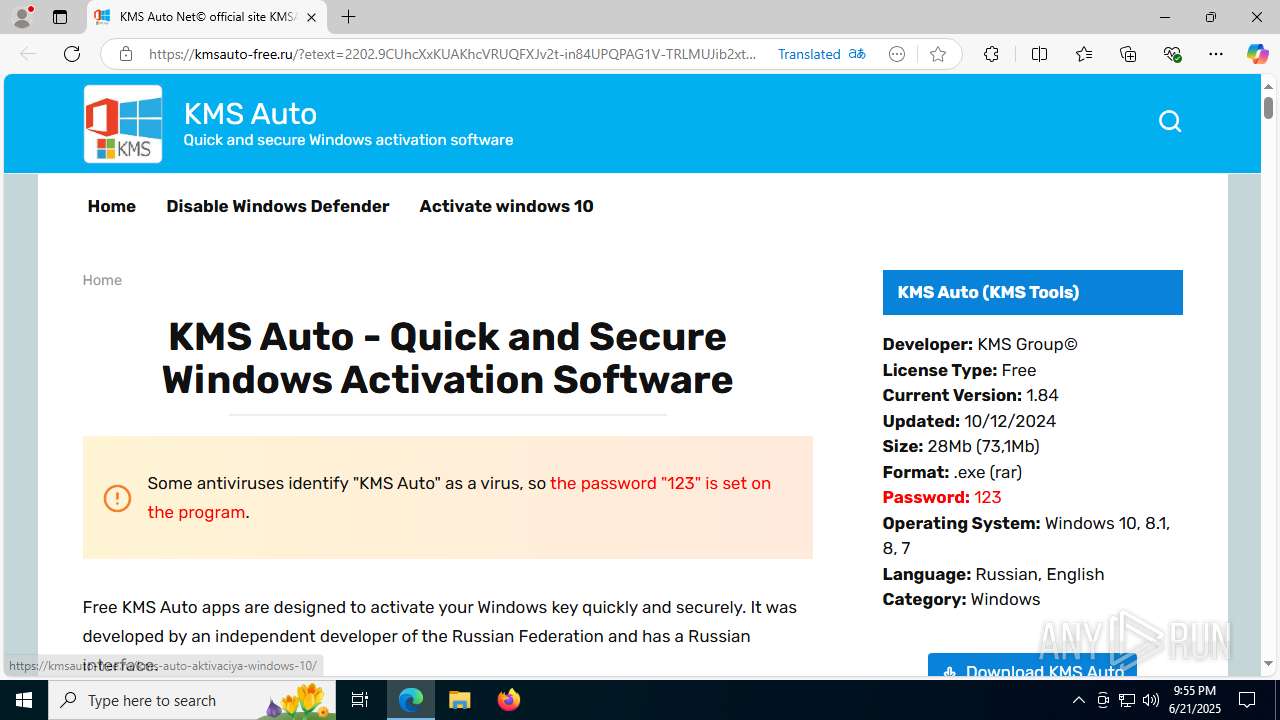
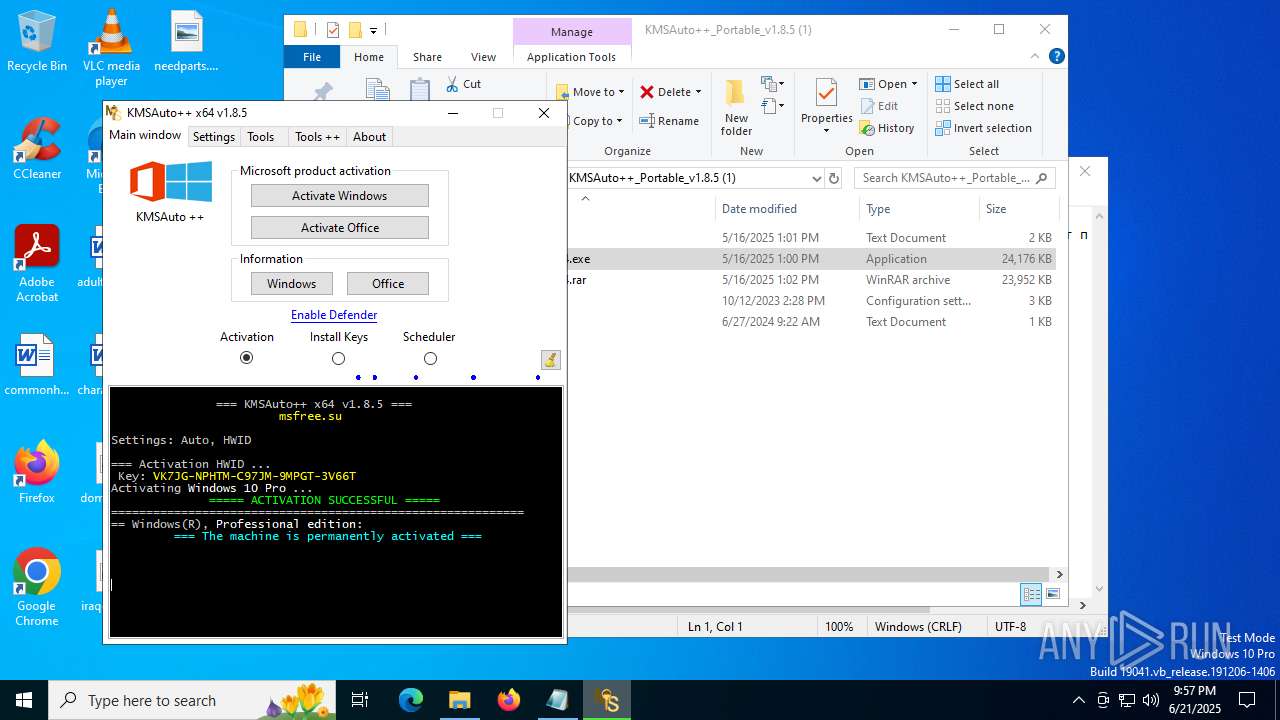
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | June 21, 2025, 21:55:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0D9256FAD3E69B5ECACA11D2FD8832FD |
| SHA1: | A21B0E1305BA568FA29592694EDAA392E6FDA959 |
| SHA256: | 3B5BA5C13BC408307F7897BDF521230EE0BF9A410248BD81867CF35B1DD59522 |
| SSDEEP: | 24:2FogkBR7+42KPrEl1+UYXi30B6n09nIzRvHgrqgK6vSXzRw:SkX7+FfY/qgatKqgKXzW |
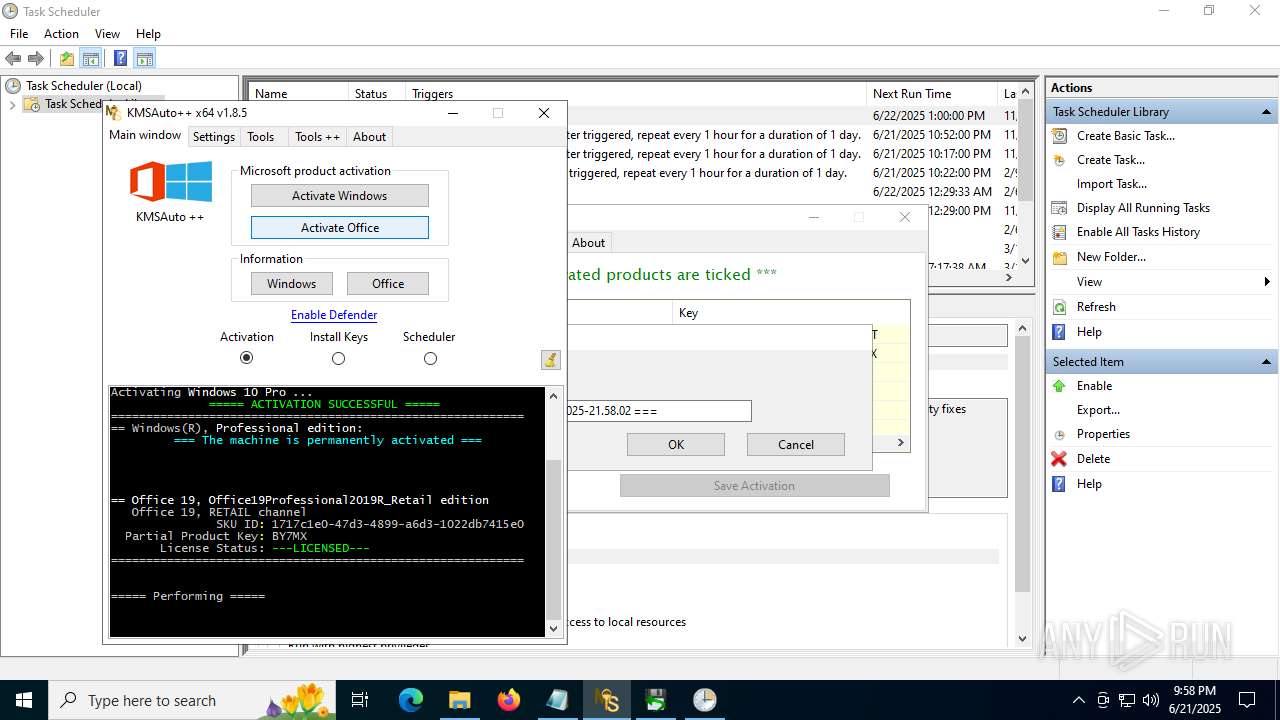
MALICIOUS
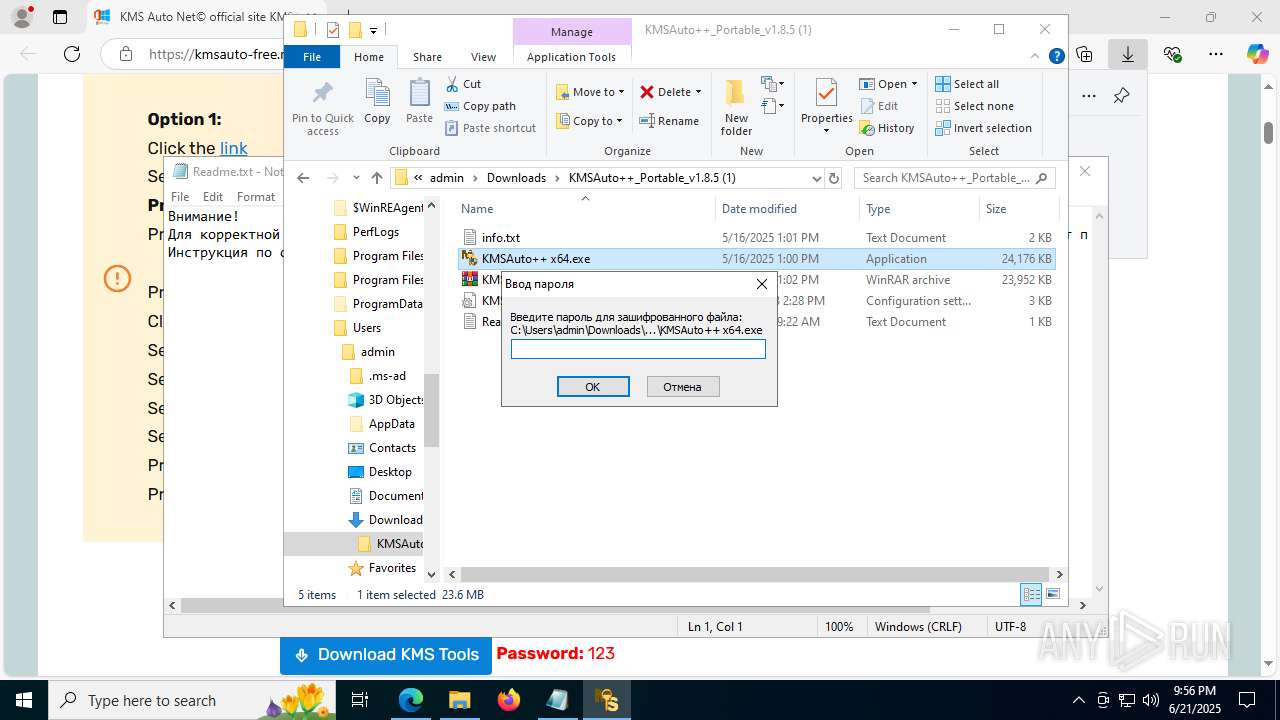
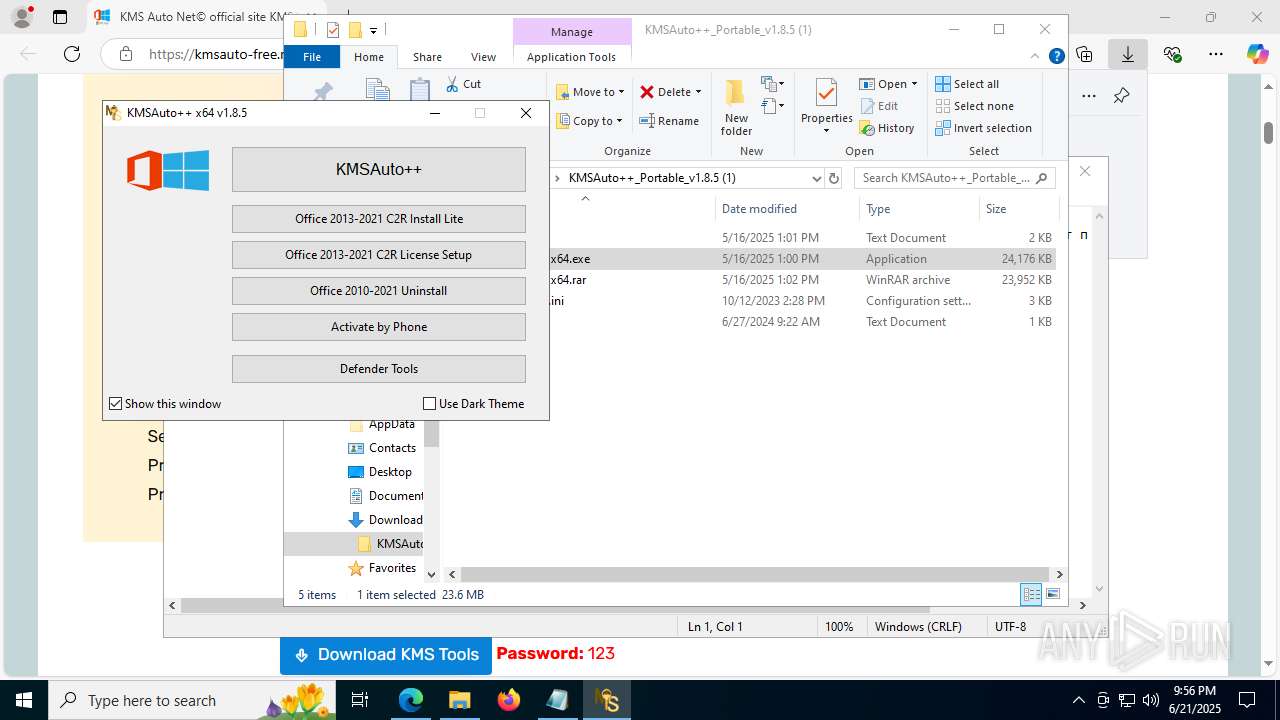
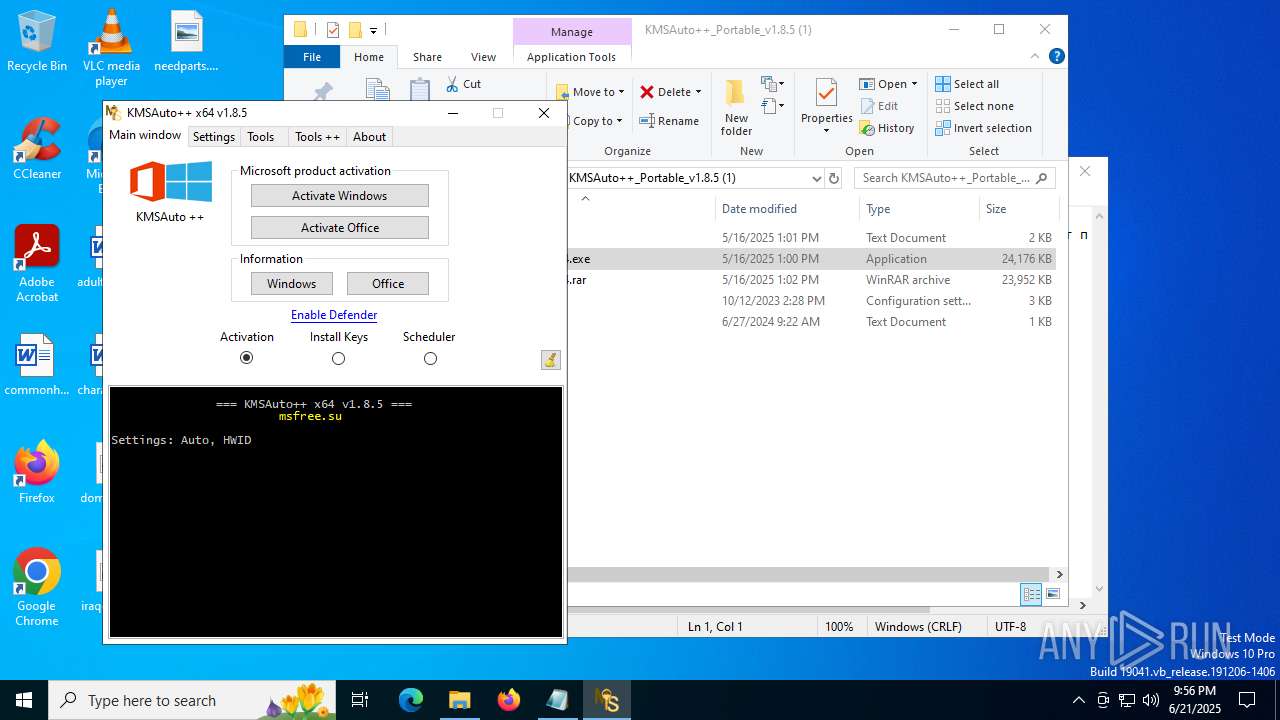
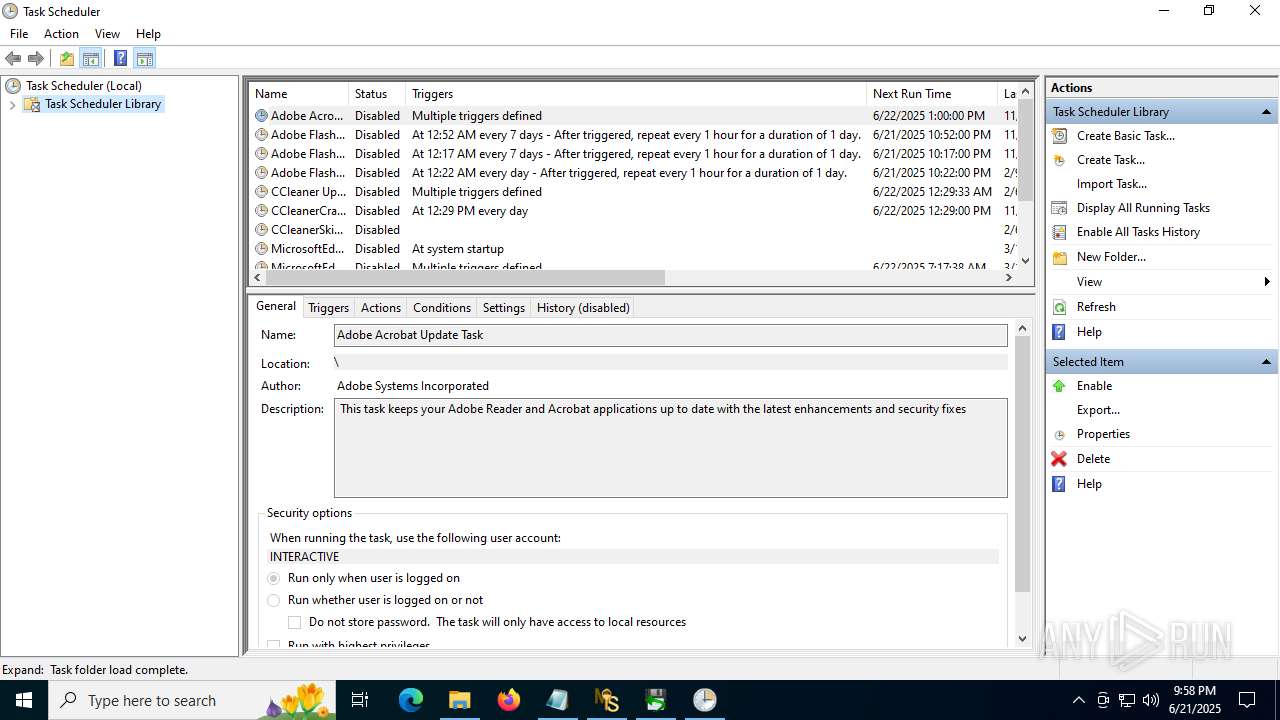
Executing a file with an untrusted certificate
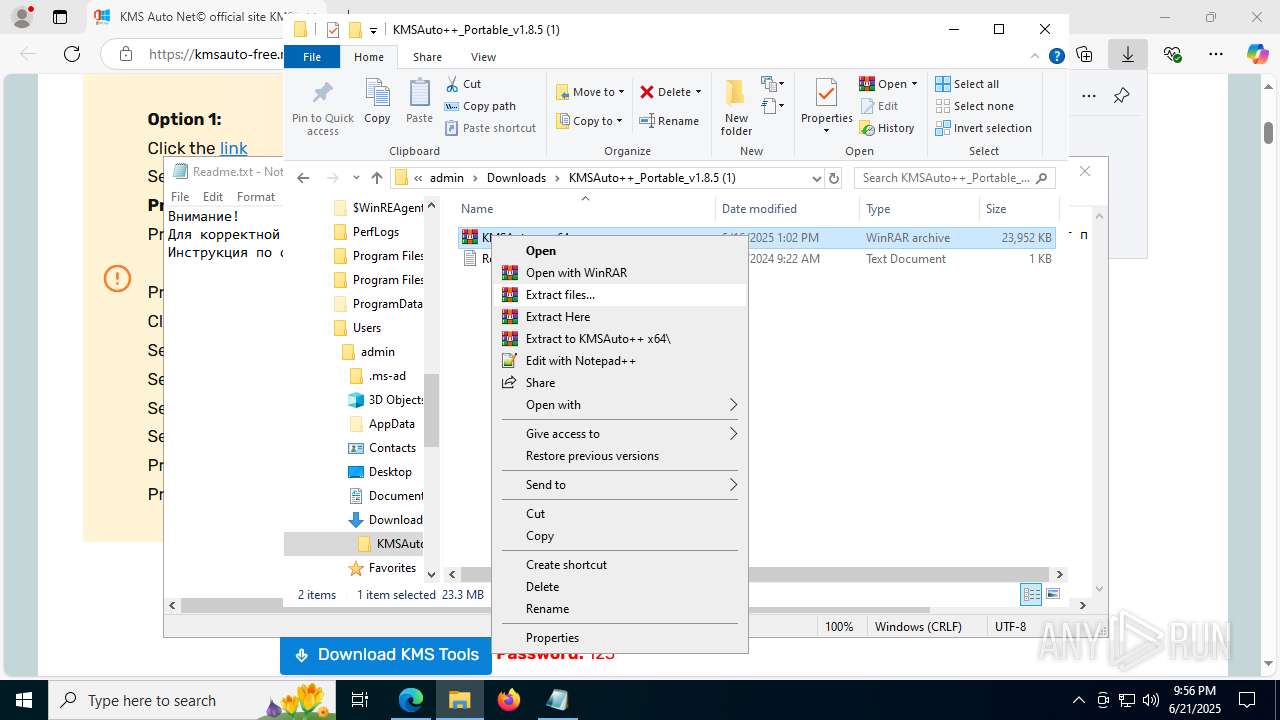
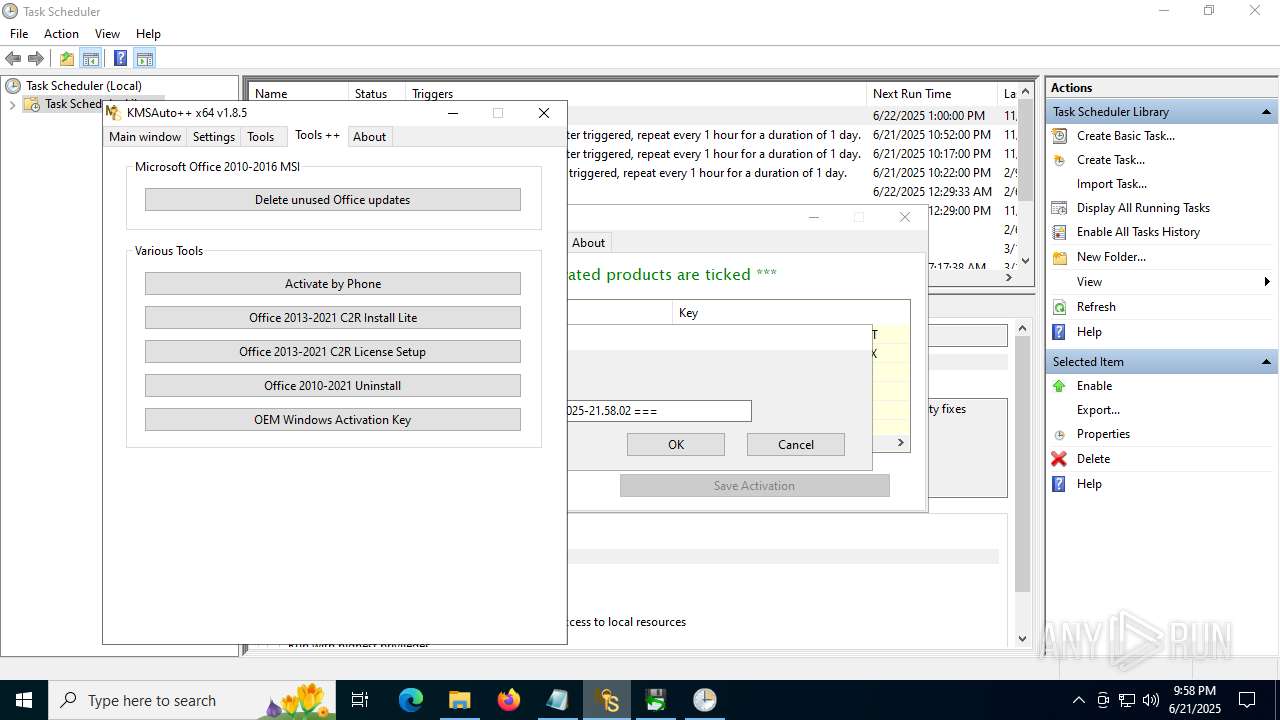
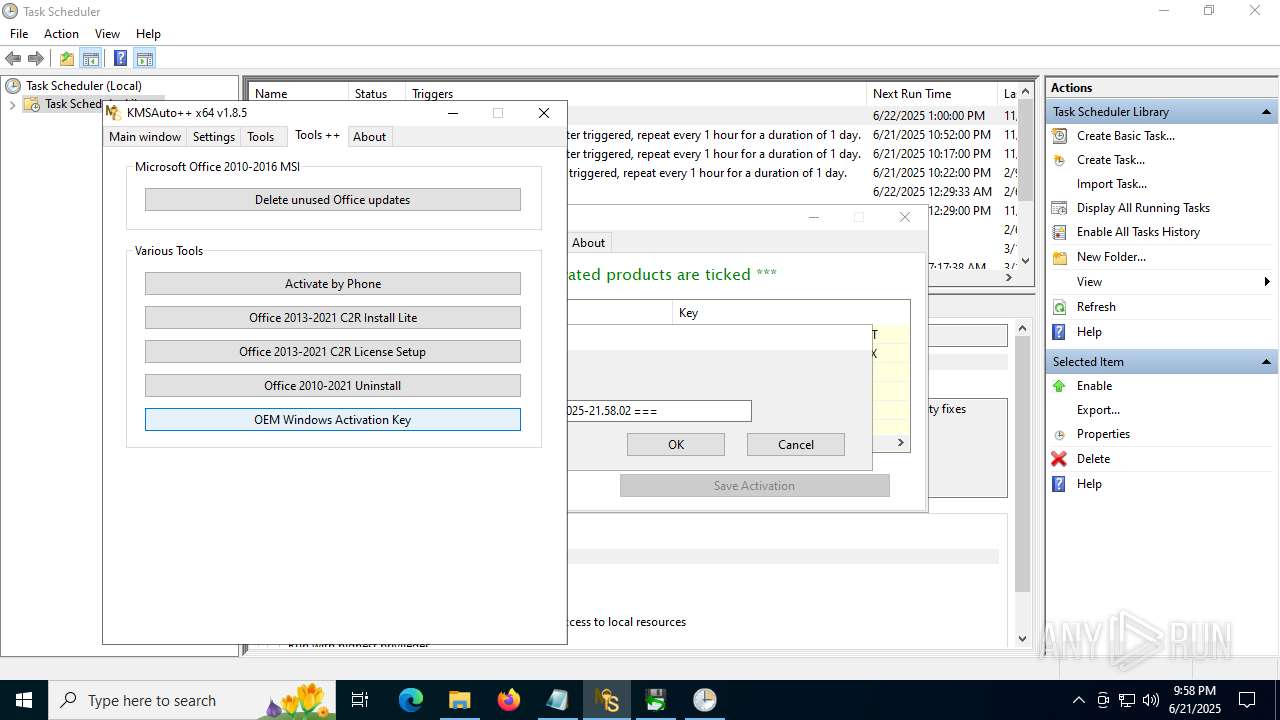
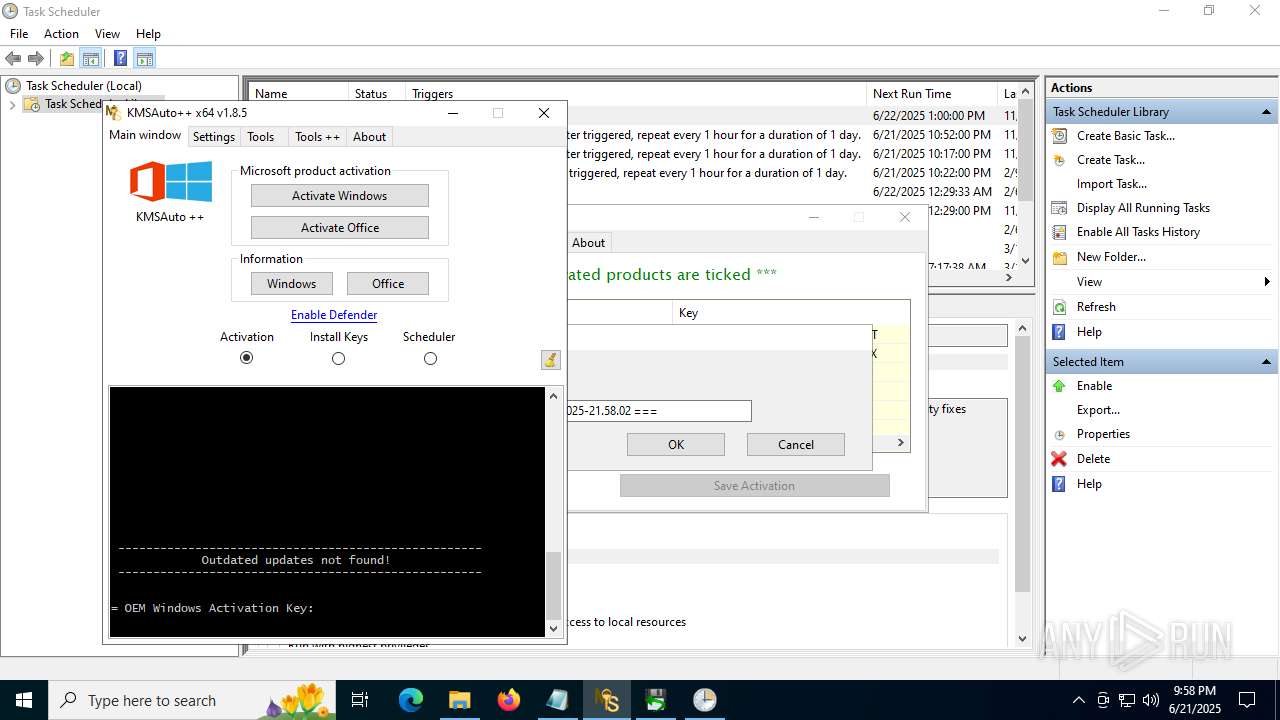
- KMSAuto++.exe (PID: 7020)
- KMSAuto++ x64.exe (PID: 7060)
- signtool.exe (PID: 3748)
- updater.exe (PID: 3832)
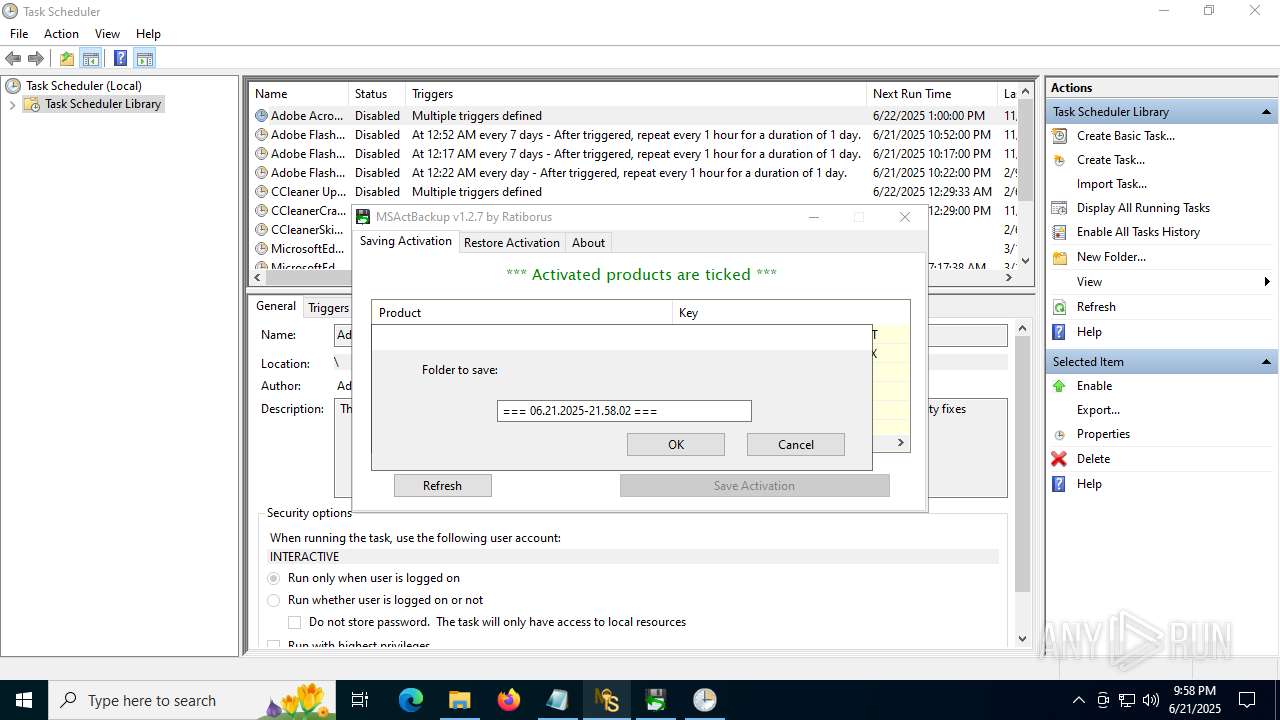
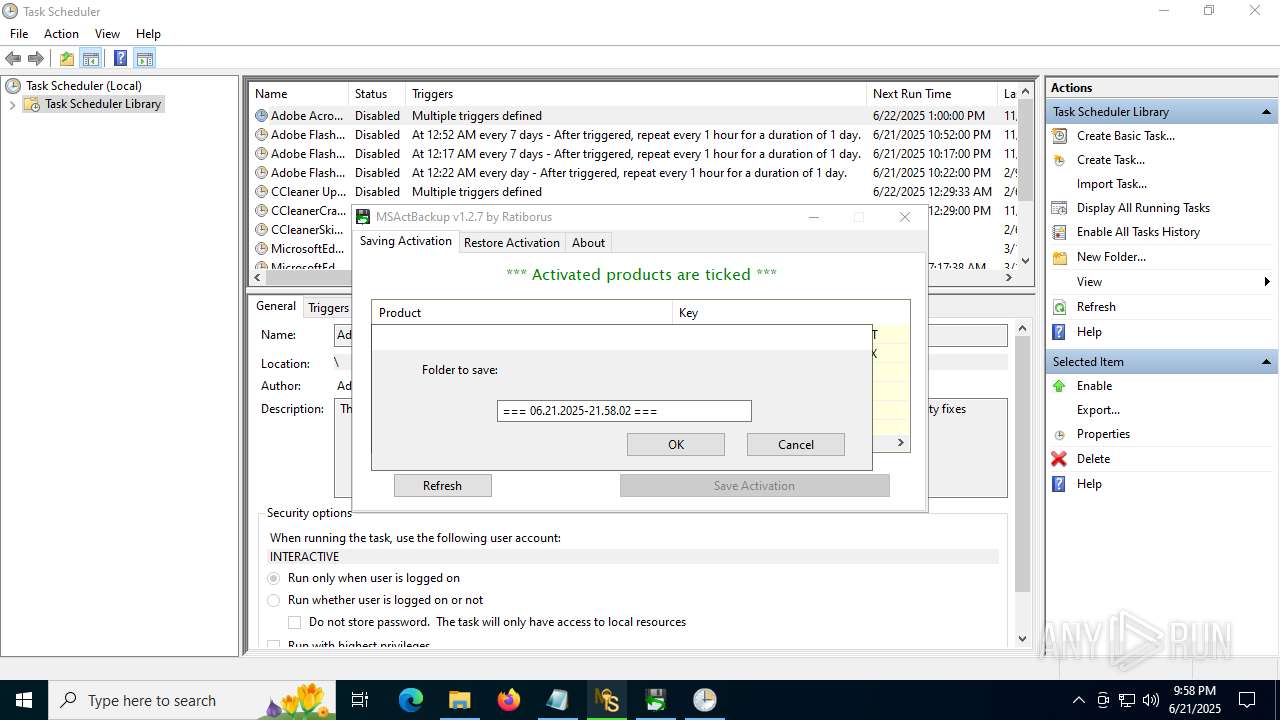
- MSActBackup.exe (PID: 6636)
- pdk.dll (PID: 7476)
- Defender Tools.exe (PID: 6296)
- Defender Tools.exe (PID: 7324)
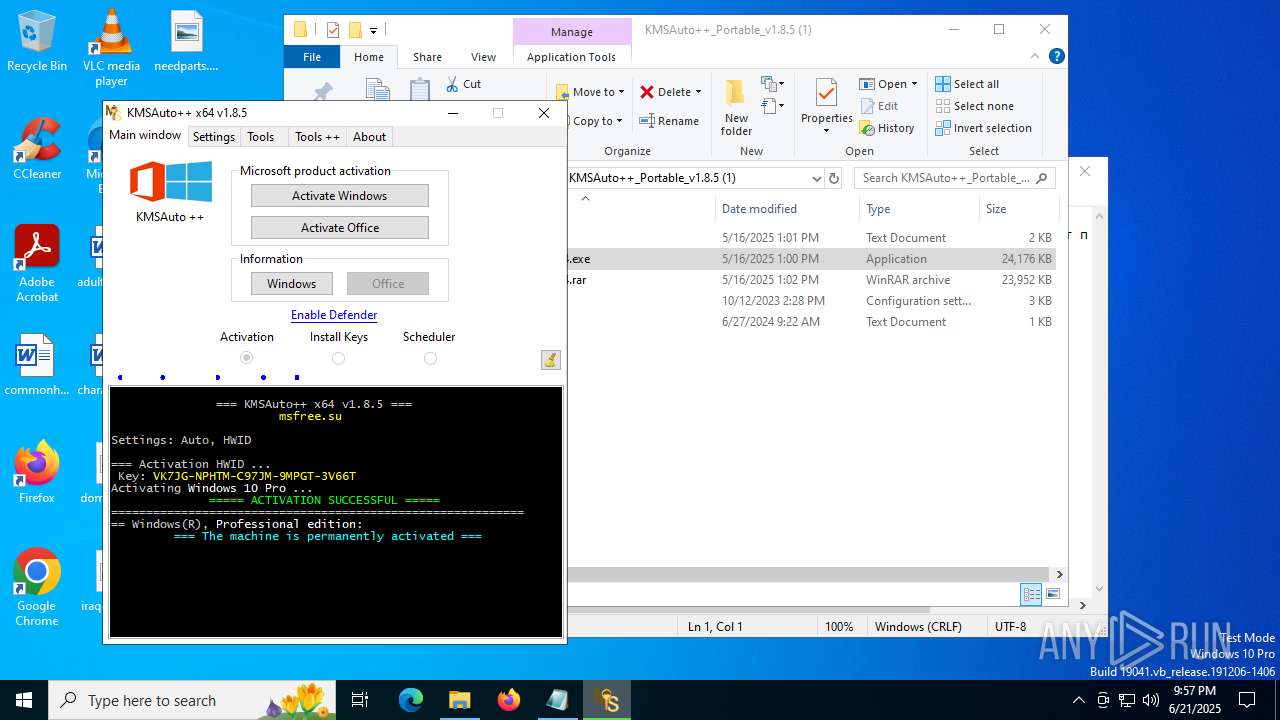
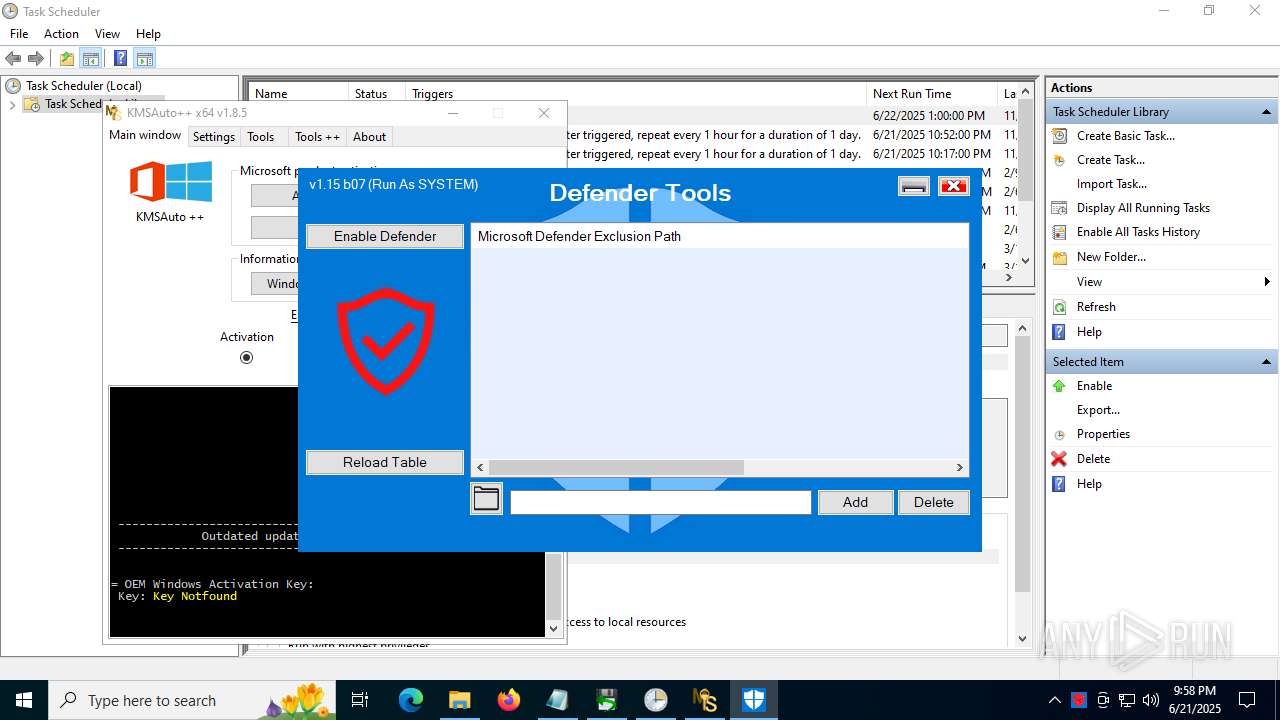
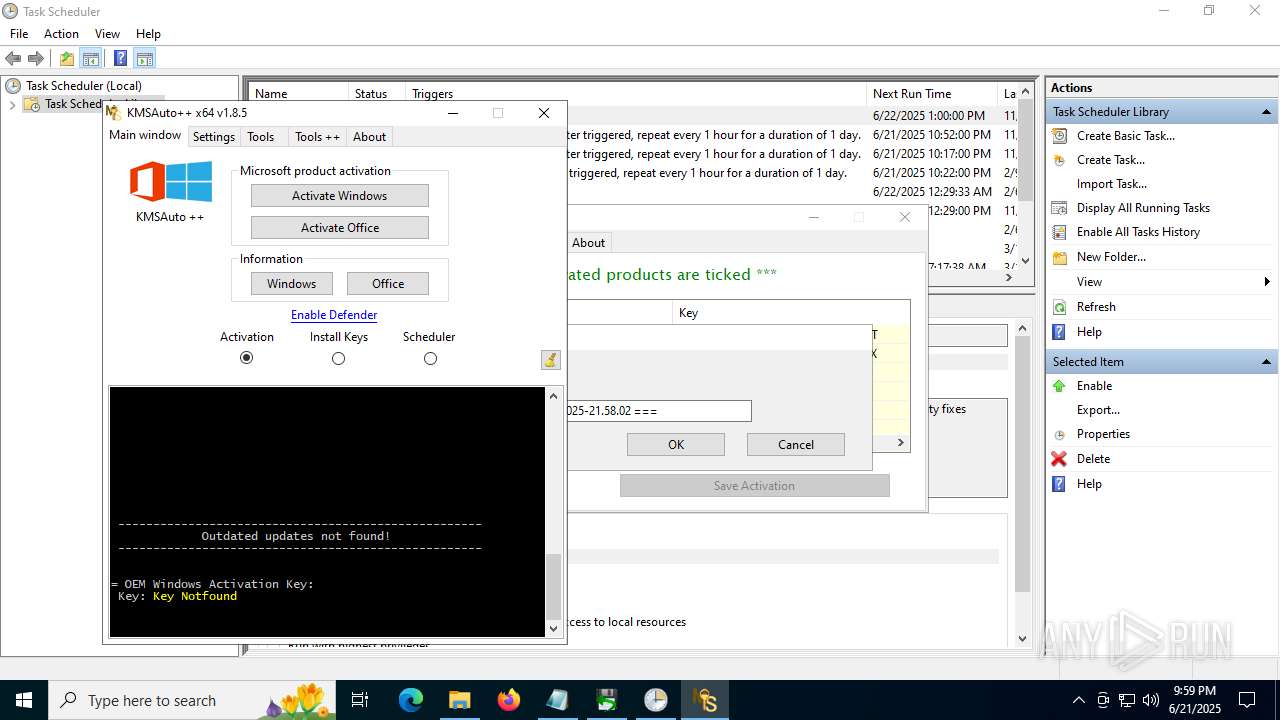
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 7656)
- cmd.exe (PID: 8028)
- cmd.exe (PID: 7528)
- cmd.exe (PID: 8184)
- cmd.exe (PID: 5944)
Adds extension to the Windows Defender exclusion list
- KMSAuto++.exe (PID: 7020)
- updater.exe (PID: 3832)
Changes Windows Defender settings
- KMSAuto++.exe (PID: 7020)
- updater.exe (PID: 3832)
Uninstalls Malicious Software Removal Tool (MRT)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 6956)
Vulnerable driver has been detected
- updater.exe (PID: 3832)
Starts NET.EXE for service management
- cmd.exe (PID: 7240)
- net.exe (PID: 6612)
- net.exe (PID: 5652)
- net.exe (PID: 2120)
- net.exe (PID: 236)
- net.exe (PID: 7324)
- net.exe (PID: 5744)
- net.exe (PID: 8136)
- net.exe (PID: 7352)
- net.exe (PID: 948)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2200)
Opens a text file (SCRIPT)
- cscript.exe (PID: 4036)
XMRIG has been detected (YARA)
- explorer.exe (PID: 3640)
Changes the autorun value in the registry
- reg.exe (PID: 4156)
SUSPICIOUS
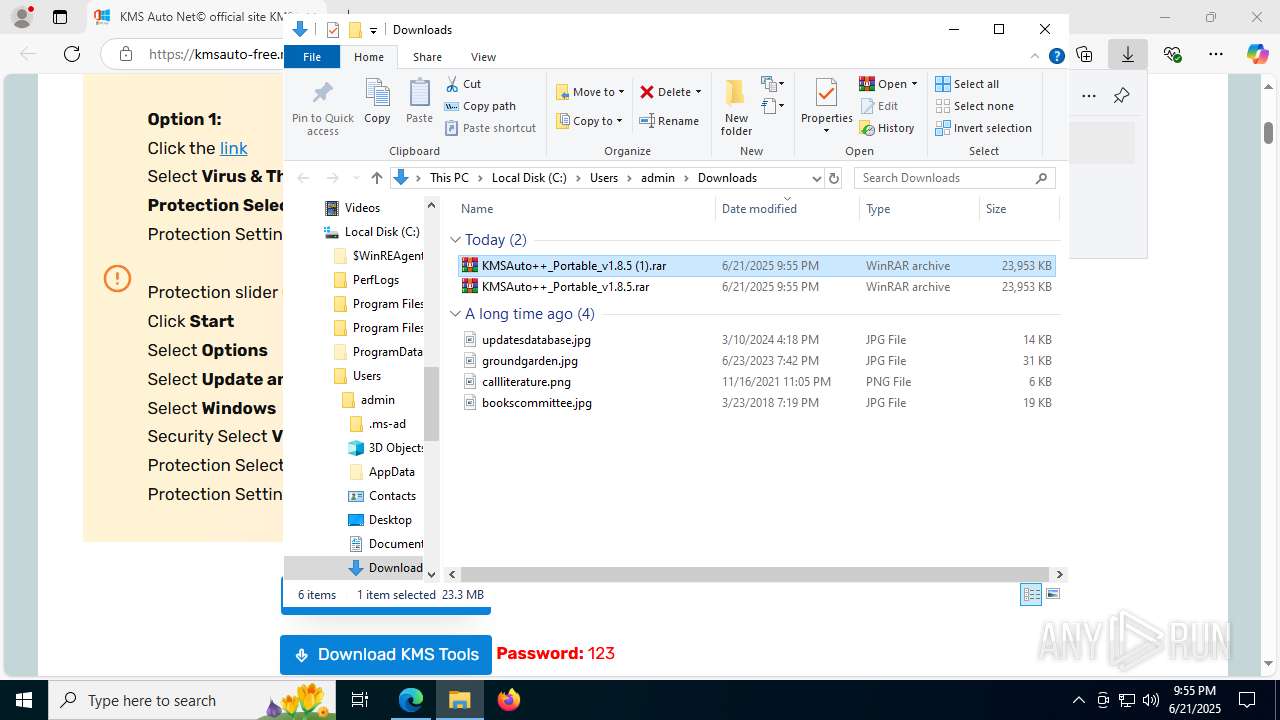
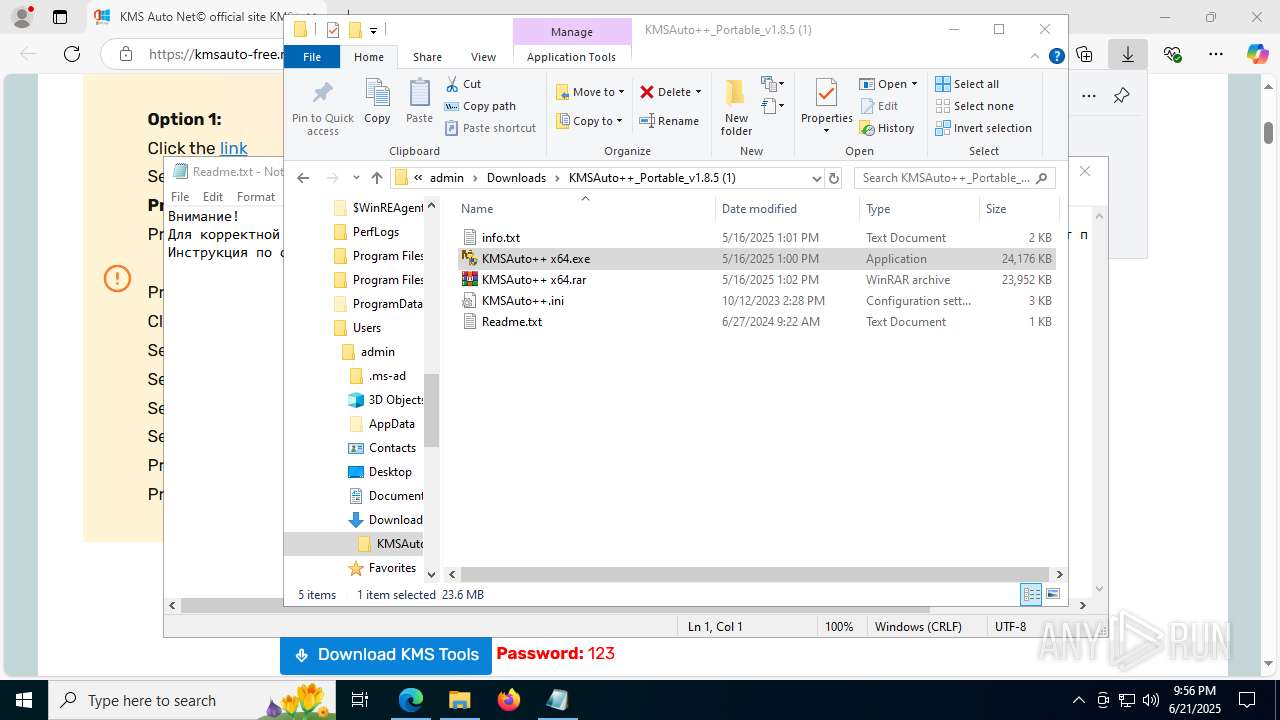
Executable content was dropped or overwritten
- KMSAuto++ x64.exe (PID: 4156)
- KMSAuto++ x64.exe (PID: 7060)
- KMSAuto++.exe (PID: 7020)
- updater.exe (PID: 3832)
- Dism.exe (PID: 5720)
- MSActBackup.exe (PID: 6636)
- pdk.dat (PID: 6352)
- Defender Tools.exe (PID: 6296)
- Defender Tools.exe (PID: 7324)
Reads security settings of Internet Explorer
- KMSAuto++ x64.exe (PID: 4156)
- signtool.exe (PID: 3748)
- KMSAuto++ x64.exe (PID: 7060)
Reads the date of Windows installation
- KMSAuto++ x64.exe (PID: 4156)
- KMSAuto++ x64.exe (PID: 7060)
Starts CMD.EXE for commands execution
- KMSAuto++ x64.exe (PID: 7060)
- cmd.exe (PID: 7240)
- KMSAuto++.exe (PID: 7020)
- updater.exe (PID: 3832)
- MSActBackup.exe (PID: 6636)
- cmd.exe (PID: 4888)
- Defender Tools.exe (PID: 7324)
- loader.exe (PID: 2716)
Found strings related to reading or modifying Windows Defender settings
- KMSAuto++ x64.exe (PID: 7060)
- Defender Tools.exe (PID: 7324)
Process drops legitimate windows executable
- KMSAuto++ x64.exe (PID: 7060)
- msedge.exe (PID: 1868)
- msedge.exe (PID: 7264)
Starts a Microsoft application from unusual location
- signtool.exe (PID: 3748)
- DismHost.exe (PID: 3196)
Starts SC.EXE for service management
- KMSAuto++ x64.exe (PID: 7060)
- cmd.exe (PID: 2464)
- cmd.exe (PID: 6424)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 1128)
- cmd.exe (PID: 7804)
- cmd.exe (PID: 3964)
- KMSAuto++.exe (PID: 7020)
- cmd.exe (PID: 7240)
- updater.exe (PID: 3832)
- Defender Tools.exe (PID: 7324)
- cmd.exe (PID: 6652)
Windows service management via SC.EXE
- sc.exe (PID: 8104)
- sc.exe (PID: 3488)
- sc.exe (PID: 6148)
- sc.exe (PID: 2072)
- sc.exe (PID: 1352)
- sc.exe (PID: 2620)
- sc.exe (PID: 7364)
- sc.exe (PID: 7076)
- sc.exe (PID: 5244)
- sc.exe (PID: 8160)
- sc.exe (PID: 856)
- sc.exe (PID: 1984)
- sc.exe (PID: 3936)
- sc.exe (PID: 3572)
- sc.exe (PID: 7304)
- sc.exe (PID: 3108)
- sc.exe (PID: 7300)
- sc.exe (PID: 7096)
- sc.exe (PID: 5080)
- sc.exe (PID: 3972)
- sc.exe (PID: 5008)
- sc.exe (PID: 7352)
- sc.exe (PID: 1688)
- sc.exe (PID: 2664)
- sc.exe (PID: 7356)
- sc.exe (PID: 4892)
- sc.exe (PID: 6112)
- sc.exe (PID: 2220)
- sc.exe (PID: 6772)
- sc.exe (PID: 3668)
- sc.exe (PID: 2276)
- sc.exe (PID: 6688)
- sc.exe (PID: 7636)
- sc.exe (PID: 3800)
- sc.exe (PID: 2168)
- sc.exe (PID: 5528)
- sc.exe (PID: 7996)
- sc.exe (PID: 1296)
- sc.exe (PID: 7272)
- sc.exe (PID: 7640)
- sc.exe (PID: 7848)
- sc.exe (PID: 3972)
- sc.exe (PID: 984)
- sc.exe (PID: 4868)
- sc.exe (PID: 3844)
- sc.exe (PID: 7176)
- sc.exe (PID: 4460)
- sc.exe (PID: 4456)
- sc.exe (PID: 5444)
- sc.exe (PID: 8020)
- sc.exe (PID: 532)
- sc.exe (PID: 8008)
- sc.exe (PID: 7368)
- sc.exe (PID: 6176)
- sc.exe (PID: 7336)
- sc.exe (PID: 6392)
- sc.exe (PID: 4500)
- sc.exe (PID: 5340)
- sc.exe (PID: 4816)
- sc.exe (PID: 5012)
- sc.exe (PID: 7932)
- sc.exe (PID: 6612)
- sc.exe (PID: 6012)
- sc.exe (PID: 3132)
- sc.exe (PID: 728)
- sc.exe (PID: 6360)
- sc.exe (PID: 2632)
- sc.exe (PID: 8000)
- sc.exe (PID: 5372)
- sc.exe (PID: 2072)
- sc.exe (PID: 2588)
- sc.exe (PID: 4500)
- sc.exe (PID: 7028)
- sc.exe (PID: 3100)
- sc.exe (PID: 5028)
- sc.exe (PID: 7040)
- sc.exe (PID: 7484)
- sc.exe (PID: 7052)
- sc.exe (PID: 2596)
- sc.exe (PID: 5804)
- sc.exe (PID: 3564)
- sc.exe (PID: 6368)
- sc.exe (PID: 2952)
- sc.exe (PID: 7224)
- sc.exe (PID: 6652)
- sc.exe (PID: 4892)
- sc.exe (PID: 7836)
- sc.exe (PID: 7300)
- sc.exe (PID: 2520)
- sc.exe (PID: 6308)
- sc.exe (PID: 4380)
- sc.exe (PID: 4664)
- sc.exe (PID: 7096)
- sc.exe (PID: 7340)
Adds/modifies Windows certificates
- signtool.exe (PID: 3748)
Uses WMIC.EXE
- KMSAuto++ x64.exe (PID: 7060)
The process executes VB scripts
- cmd.exe (PID: 7464)
- cmd.exe (PID: 6336)
- cmd.exe (PID: 7240)
- cmd.exe (PID: 4828)
- cmd.exe (PID: 1728)
- cmd.exe (PID: 1128)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 7868)
- cscript.exe (PID: 4860)
- cscript.exe (PID: 4036)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 480)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7868)
- cscript.exe (PID: 4860)
- cscript.exe (PID: 4036)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 480)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 7868)
- cscript.exe (PID: 4860)
- cscript.exe (PID: 4036)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 480)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 7868)
- cscript.exe (PID: 4860)
- cscript.exe (PID: 4036)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 480)
- cscript.exe (PID: 7640)
Script adds exclusion path to Windows Defender
- KMSAuto++.exe (PID: 7020)
- updater.exe (PID: 3832)
Starts POWERSHELL.EXE for commands execution
- KMSAuto++.exe (PID: 7020)
- cmd.exe (PID: 5372)
- updater.exe (PID: 3832)
- cmd.exe (PID: 6788)
- cmd.exe (PID: 7240)
- cmd.exe (PID: 6100)
- cmd.exe (PID: 5772)
Manipulates environment variables
- powershell.exe (PID: 5620)
- powershell.exe (PID: 6584)
Script adds exclusion extension to Windows Defender
- KMSAuto++.exe (PID: 7020)
- updater.exe (PID: 3832)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 4860)
- cscript.exe (PID: 7868)
- cscript.exe (PID: 4036)
- cscript.exe (PID: 1816)
- cscript.exe (PID: 480)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7048)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 3800)
- cmd.exe (PID: 4088)
- cmd.exe (PID: 7240)
- cmd.exe (PID: 6652)
Executing commands from ".cmd" file
- KMSAuto++ x64.exe (PID: 7060)
- loader.exe (PID: 2716)
Application launched itself
- cmd.exe (PID: 7240)
- ClipUp.exe (PID: 5944)
- cmd.exe (PID: 4888)
Stops a currently running service
- sc.exe (PID: 3048)
- sc.exe (PID: 7460)
- sc.exe (PID: 6348)
- sc.exe (PID: 3672)
- sc.exe (PID: 7500)
- sc.exe (PID: 5716)
- sc.exe (PID: 4052)
- sc.exe (PID: 7092)
- sc.exe (PID: 6612)
- sc.exe (PID: 7272)
- sc.exe (PID: 432)
Process uninstalls Windows update
- wusa.exe (PID: 1800)
- wusa.exe (PID: 3788)
Creates a new Windows service
- sc.exe (PID: 4760)
Uses powercfg.exe to modify the power settings
- KMSAuto++.exe (PID: 7020)
- updater.exe (PID: 3832)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7240)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7240)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7240)
- cmd.exe (PID: 5716)
- KMSAuto++ x64.exe (PID: 7060)
Executes as Windows Service
- updater.exe (PID: 3832)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 236)
Drops a system driver (possible attempt to evade defenses)
- updater.exe (PID: 3832)
Connects to unusual port
- explorer.exe (PID: 3640)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2200)
The process creates files with name similar to system file names
- Dism.exe (PID: 5720)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 4036)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7240)
- KMSAuto++ x64.exe (PID: 7060)
- cmd.exe (PID: 6652)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4312)
Detected use of alternative data streams (AltDS)
- msdt.exe (PID: 6620)
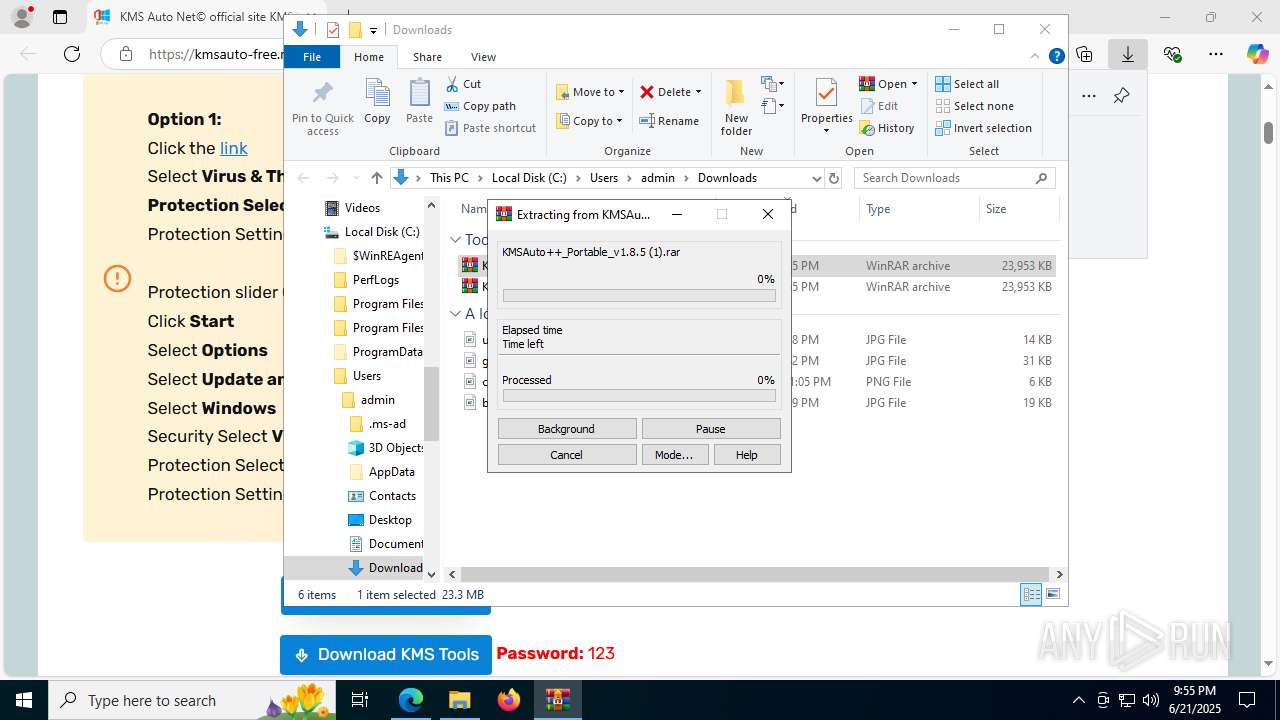
Drops 7-zip archiver for unpacking
- MSActBackup.exe (PID: 6636)
Starts application with an unusual extension
- cmd.exe (PID: 5184)
- cmd.exe (PID: 3572)
- cmd.exe (PID: 3844)
- cmd.exe (PID: 1380)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- cscript.exe (PID: 7640)
Accesses operating system name via WMI (SCRIPT)
- cscript.exe (PID: 7640)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1380)
Executing commands from a ".bat" file
- Defender Tools.exe (PID: 7324)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 6228)
- WMIC.exe (PID: 6364)
- WMIC.exe (PID: 3624)
- WMIC.exe (PID: 7572)
- WMIC.exe (PID: 4836)
- WMIC.exe (PID: 4216)
- cscript.exe (PID: 7868)
- cscript.exe (PID: 4860)
- WMIC.exe (PID: 5564)
- WMIC.exe (PID: 4088)
- WMIC.exe (PID: 1044)
- cscript.exe (PID: 4036)
- WMIC.exe (PID: 532)
- WMIC.exe (PID: 6876)
- WMIC.exe (PID: 432)
- WMIC.exe (PID: 1352)
- WMIC.exe (PID: 7256)
- cscript.exe (PID: 1816)
- WMIC.exe (PID: 4048)
- WMIC.exe (PID: 7048)
- WMIC.exe (PID: 7804)
- WMIC.exe (PID: 7384)
- WMIC.exe (PID: 2228)
- msdt.exe (PID: 316)
- cscript.exe (PID: 480)
- msdt.exe (PID: 6620)
- sdiagnhost.exe (PID: 6012)
- cscript.exe (PID: 7640)
- mmc.exe (PID: 7380)
- WMIC.exe (PID: 7240)
- WMIC.exe (PID: 5028)
- WMIC.exe (PID: 1964)
- WMIC.exe (PID: 2072)
- WMIC.exe (PID: 7880)
- WMIC.exe (PID: 6788)
- WMIC.exe (PID: 1752)
- WMIC.exe (PID: 7664)
Application launched itself
- msedge.exe (PID: 2760)
- msedge.exe (PID: 8100)
Reads the computer name
- identity_helper.exe (PID: 7644)
- KMSAuto++ x64.exe (PID: 4156)
- KMSAuto++ x64.exe (PID: 7060)
- identity_helper.exe (PID: 7748)
- DismHost.exe (PID: 3196)
- MSActBackup.exe (PID: 6636)
- Defender Tools.exe (PID: 6296)
- pdk.dll (PID: 7476)
- Defender Tools.exe (PID: 7324)
- oinstrun.exe (PID: 5744)
- loader.exe (PID: 2716)
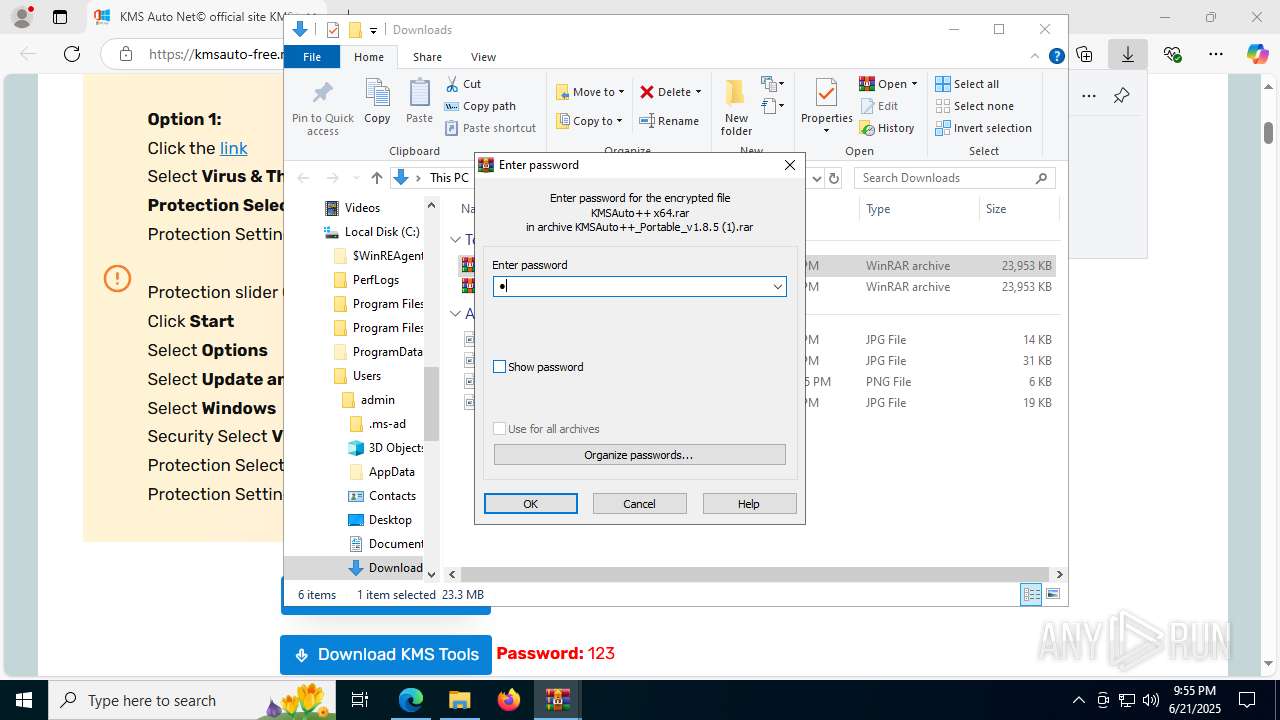
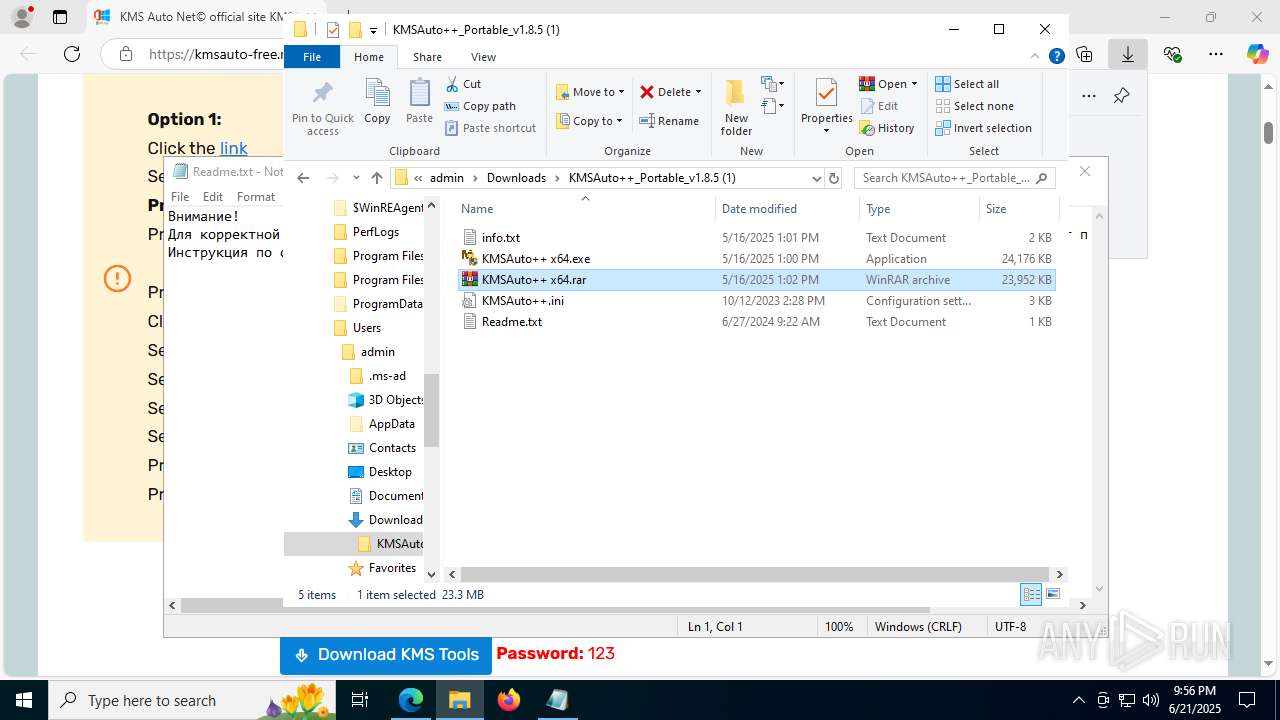
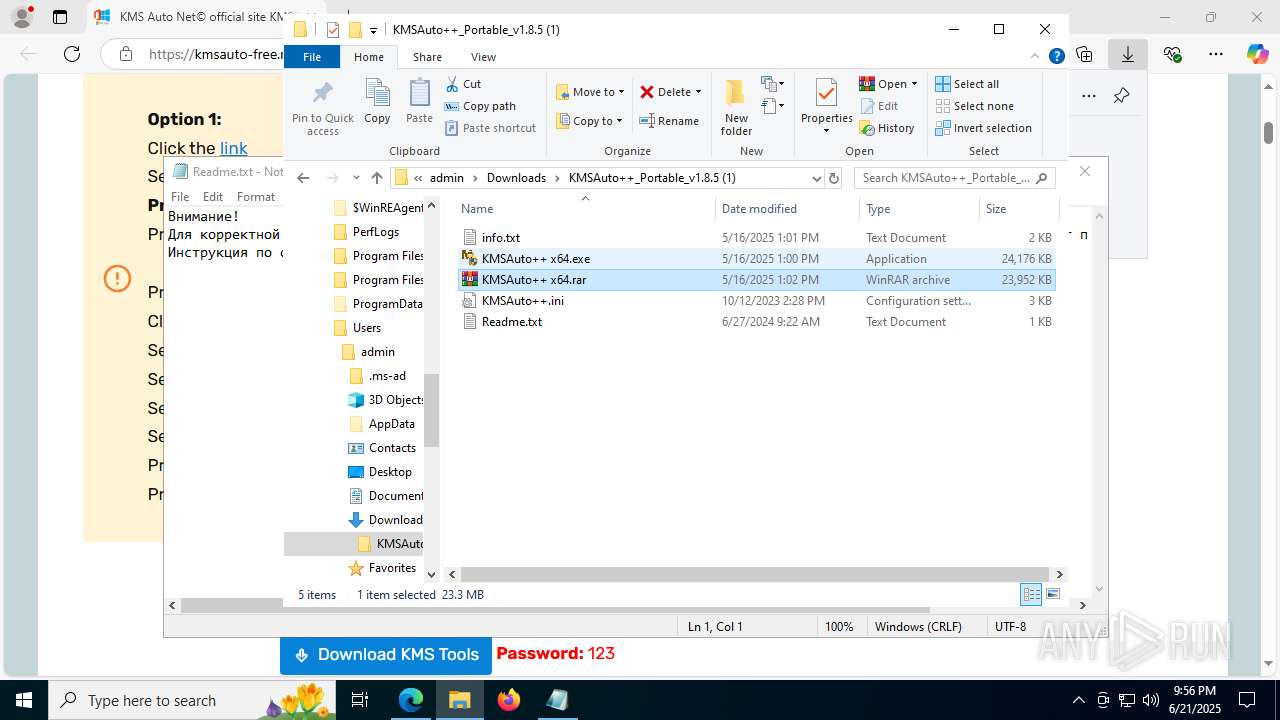
Manual execution by a user
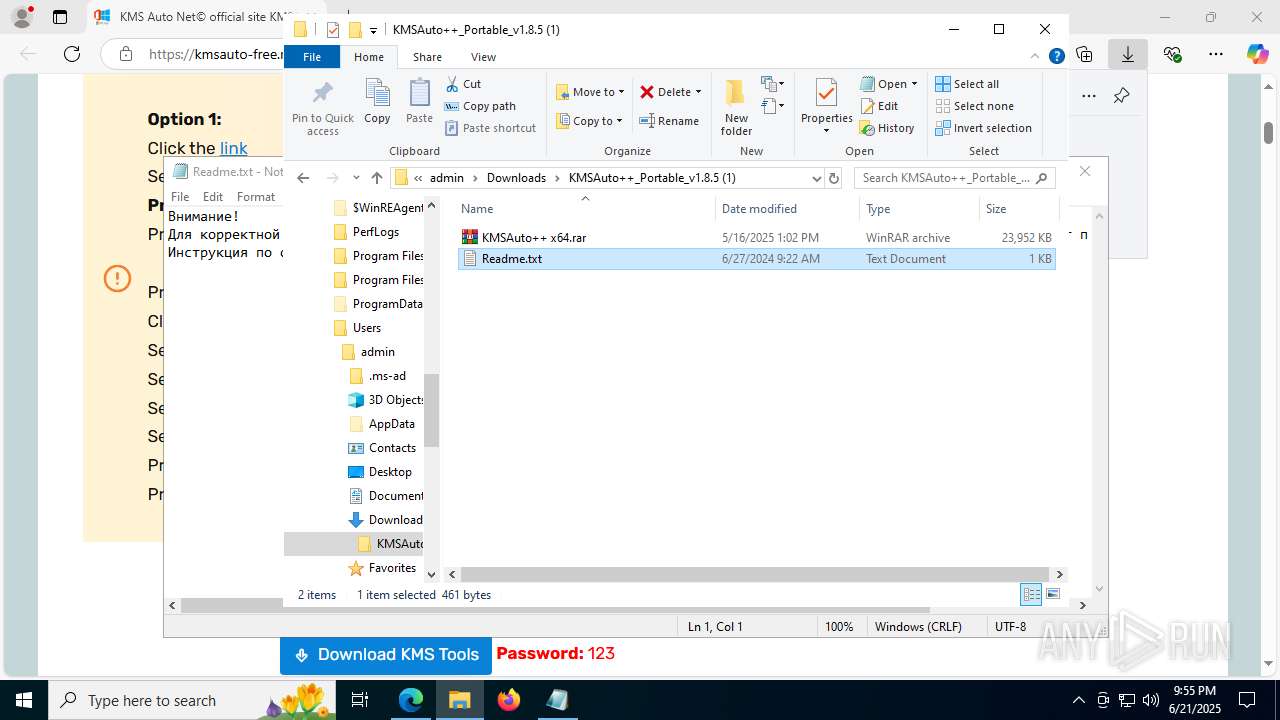
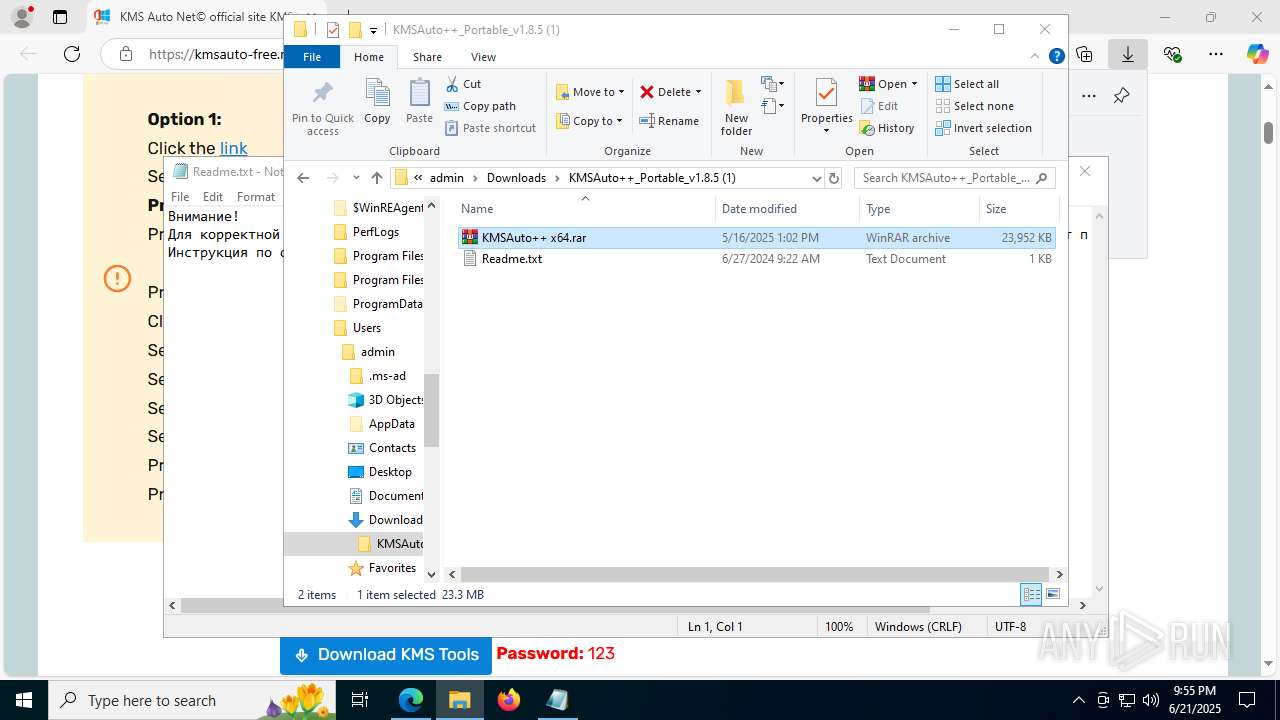
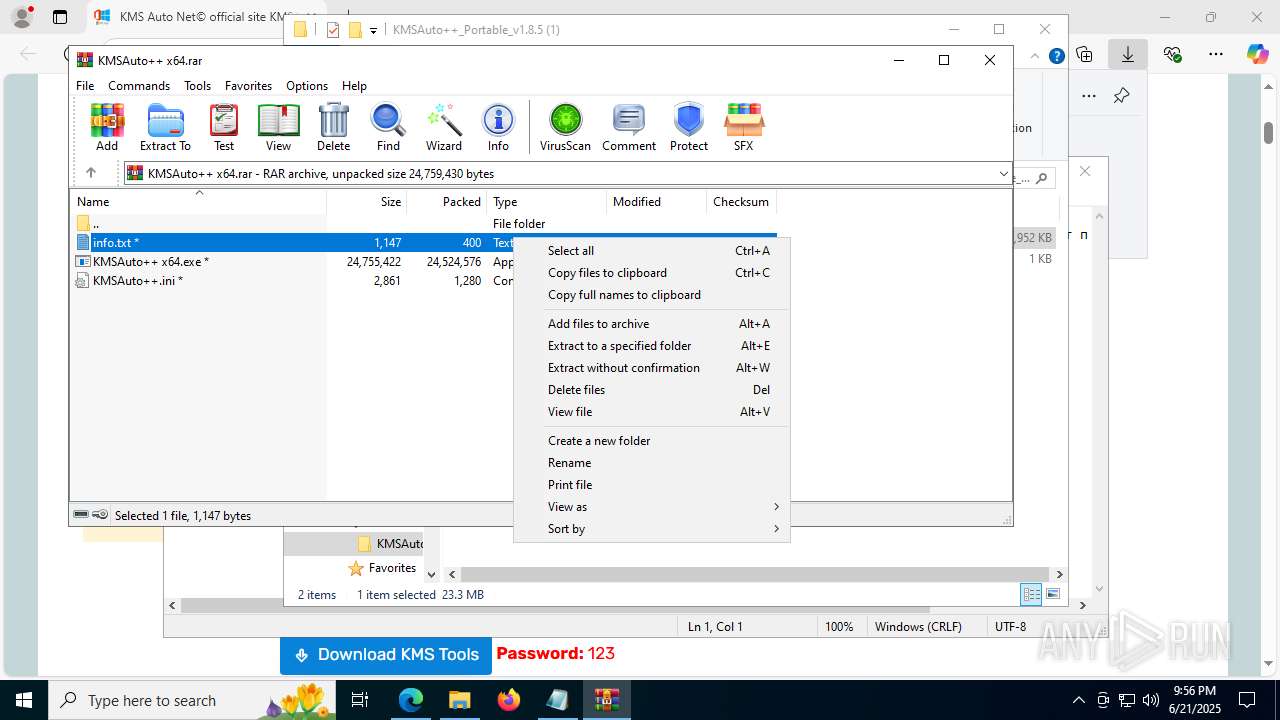
- WinRAR.exe (PID: 7432)
- notepad.exe (PID: 6228)
- WinRAR.exe (PID: 3956)
- WinRAR.exe (PID: 7716)
- KMSAuto++ x64.exe (PID: 7868)
- KMSAuto++ x64.exe (PID: 4156)
Reads Environment values
- identity_helper.exe (PID: 7644)
- KMSAuto++ x64.exe (PID: 7060)
- identity_helper.exe (PID: 7748)
- DismHost.exe (PID: 3196)
- MSActBackup.exe (PID: 6636)
- pdk.dll (PID: 7476)
Checks supported languages
- identity_helper.exe (PID: 7644)
- KMSAuto++ x64.exe (PID: 4156)
- KMSAuto++.exe (PID: 7020)
- KMSAuto++ x64.exe (PID: 7060)
- signtool.exe (PID: 3748)
- identity_helper.exe (PID: 7748)
- updater.exe (PID: 3832)
- DismHost.exe (PID: 3196)
- MSActBackup.exe (PID: 6636)
- bin.dat (PID: 5988)
- pdk.dll (PID: 7476)
- pdk.dat (PID: 6352)
- Defender Tools.exe (PID: 6296)
- Defender Tools.exe (PID: 7324)
- oinstrun.exe (PID: 5744)
- loader.exe (PID: 2716)
- chcp.com (PID: 3960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3956)
- msedge.exe (PID: 1868)
- msedge.exe (PID: 7588)
- msedge.exe (PID: 7264)
Create files in a temporary directory
- KMSAuto++ x64.exe (PID: 4156)
- KMSAuto++ x64.exe (PID: 7060)
- Dism.exe (PID: 5720)
- ClipUp.exe (PID: 7968)
- msdt.exe (PID: 316)
- msdt.exe (PID: 6620)
- sdiagnhost.exe (PID: 6012)
- MSActBackup.exe (PID: 6636)
- bin.dat (PID: 5988)
- pdk.dat (PID: 6352)
- Defender Tools.exe (PID: 6296)
- Defender Tools.exe (PID: 7324)
The sample compiled with english language support
- KMSAuto++ x64.exe (PID: 4156)
- KMSAuto++ x64.exe (PID: 7060)
- KMSAuto++.exe (PID: 7020)
- Dism.exe (PID: 5720)
- msedge.exe (PID: 1868)
- pdk.dat (PID: 6352)
- MSActBackup.exe (PID: 6636)
- msedge.exe (PID: 7588)
- msedge.exe (PID: 7264)
Process checks computer location settings
- KMSAuto++ x64.exe (PID: 4156)
- KMSAuto++ x64.exe (PID: 7060)
Reads product name
- KMSAuto++ x64.exe (PID: 7060)
- MSActBackup.exe (PID: 6636)
- pdk.dll (PID: 7476)
Reads the software policy settings
- signtool.exe (PID: 3748)
- msdt.exe (PID: 316)
- sdiagnhost.exe (PID: 6012)
- msdt.exe (PID: 6620)
Reads the machine GUID from the registry
- signtool.exe (PID: 3748)
UPX packer has been detected
- KMSAuto++ x64.exe (PID: 7060)
- explorer.exe (PID: 3640)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5620)
- powershell.exe (PID: 6584)
Checks operating system version
- cmd.exe (PID: 7240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5620)
- powershell.exe (PID: 6584)
Creates files in the program directory
- KMSAuto++.exe (PID: 7020)
- ClipUp.exe (PID: 7968)
- cmd.exe (PID: 7240)
The sample compiled with japanese language support
- updater.exe (PID: 3832)
Reads Microsoft Office registry keys
- KMSAuto++ x64.exe (PID: 7060)
- pdk.dll (PID: 7476)
Checks proxy server information
- sdiagnhost.exe (PID: 6012)
Creates files or folders in the user directory
- sdiagnhost.exe (PID: 6012)
- msdt.exe (PID: 6620)
Uses string split method (POWERSHELL)
- sdiagnhost.exe (PID: 6012)
NirSoft software is detected
- pdk.dll (PID: 7476)
Reads Windows Product ID
- pdk.dll (PID: 7476)
Launching a file from a Registry key
- reg.exe (PID: 4156)
Changes the display of characters in the console
- cmd.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
839
Monitored processes
683
Malicious processes
24
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\WINDOWS\system32\cmd.exe /c "wmic Path Win32_OperatingSystem Get OperatingSystemSKU /format:LIST" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | net start LicenseManager /y | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 316 | reg query HKLM\SYSTEM\CurrentControlSet\Services\wlidsvc /v Start | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 316 | findstr /i "0x800410 0x800440" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 316 | "C:\WINDOWS\system32\msdt.exe" /cab "C:\Users\admin\AppData\Local\Temp\o15-ctrremove.diagcab" | C:\Windows\System32\msdt.exe | — | KMSAuto++ x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Diagnostics Troubleshooting Wizard Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 424 | "C:\WINDOWS\Sysnative\reg.exe" query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender" /v DisableAntiSpyware | C:\Windows\System32\reg.exe | — | Defender Tools.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 432 | C:\WINDOWS\system32\sc.exe stop dosvc | C:\Windows\System32\sc.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Exit code: 1062 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
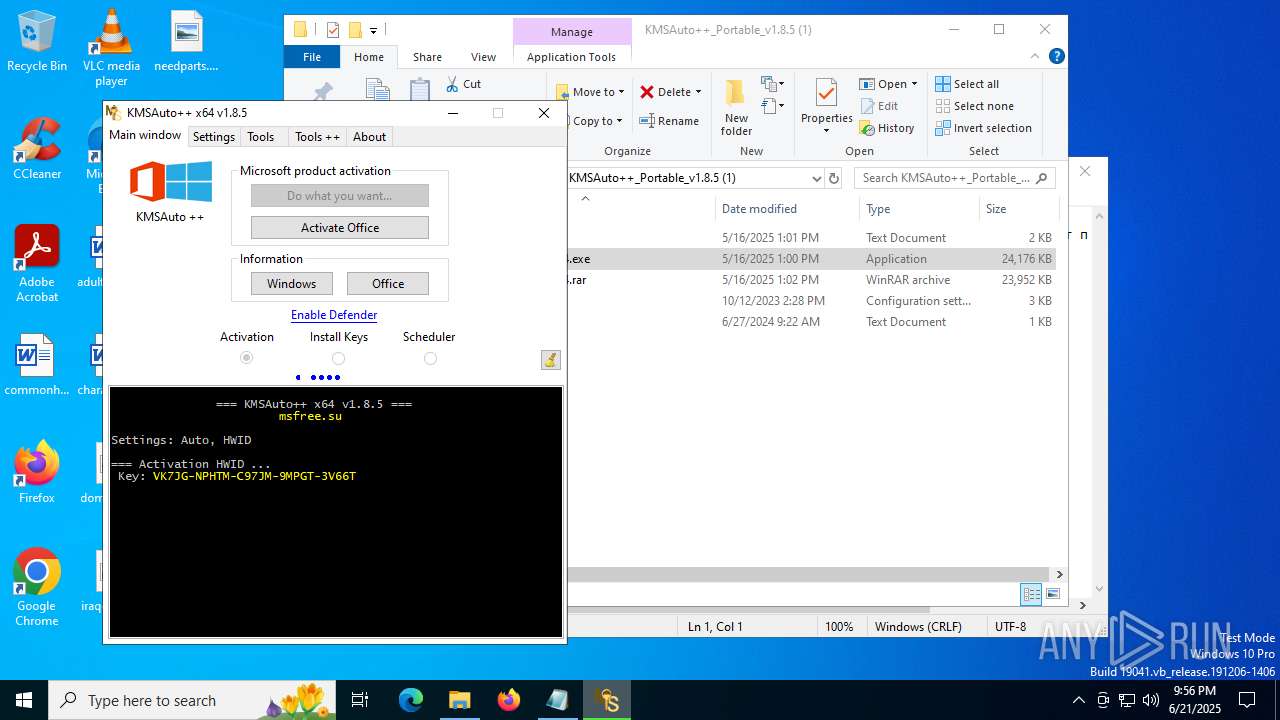
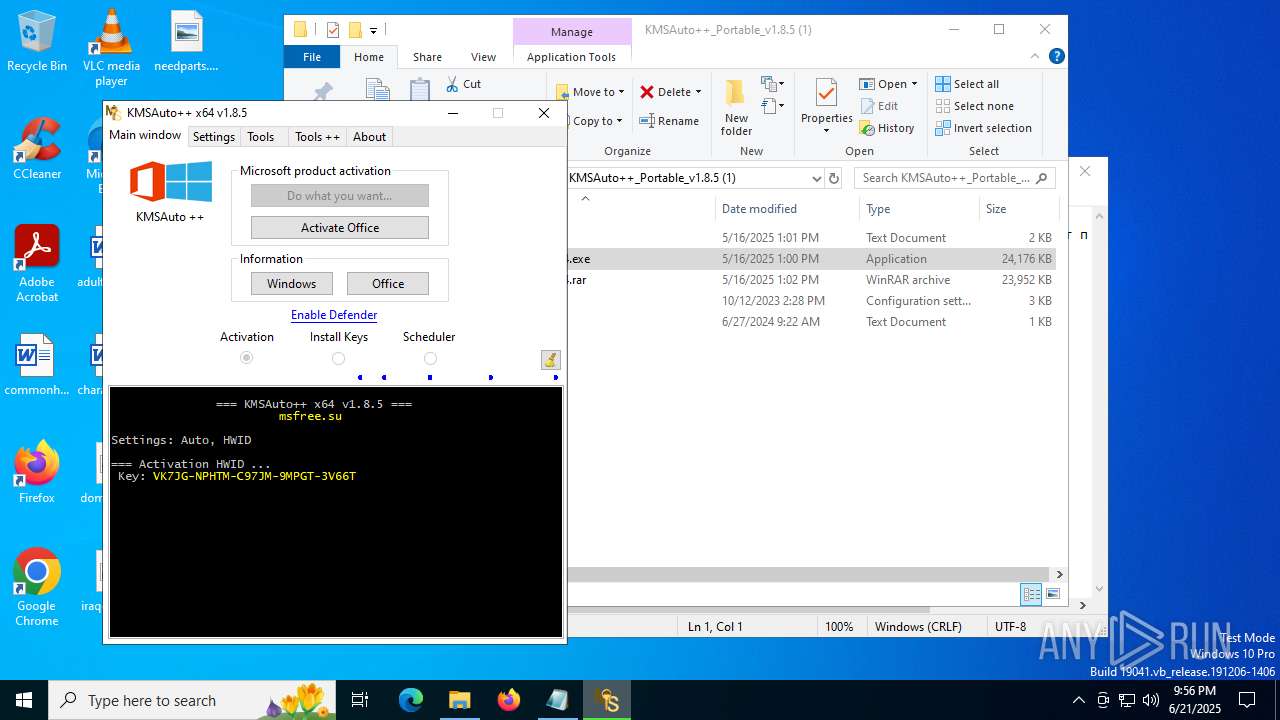
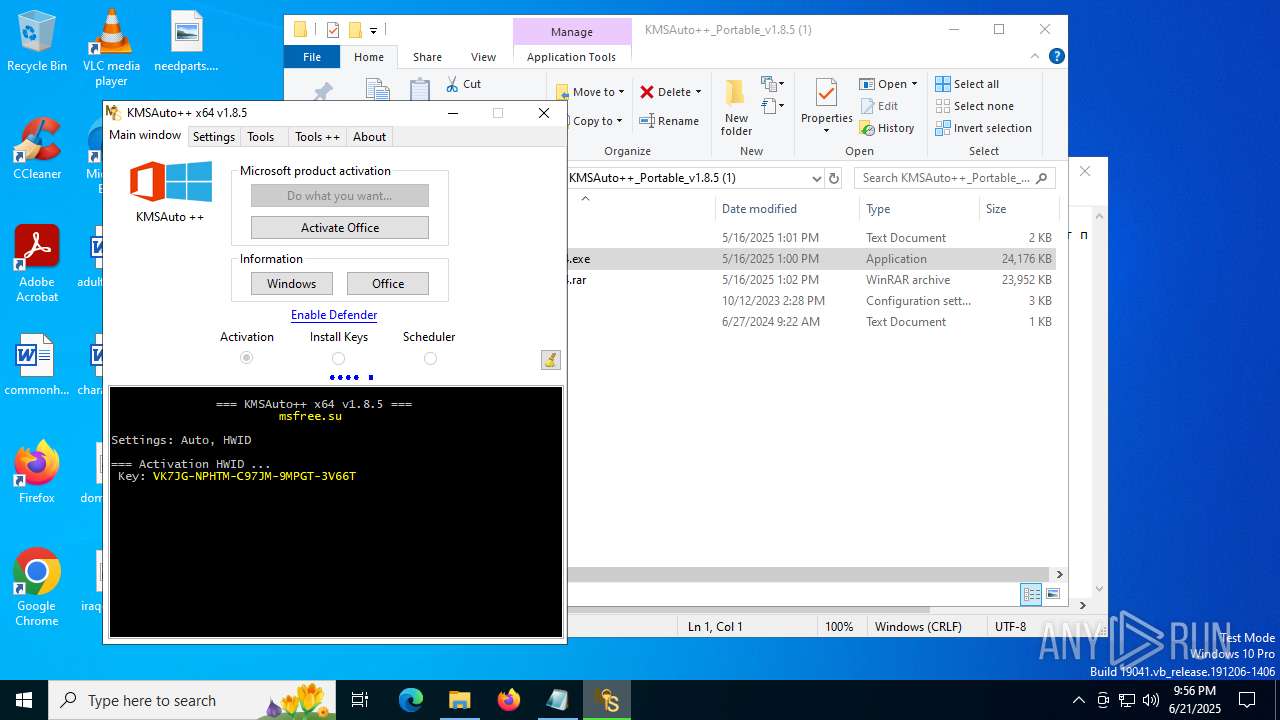
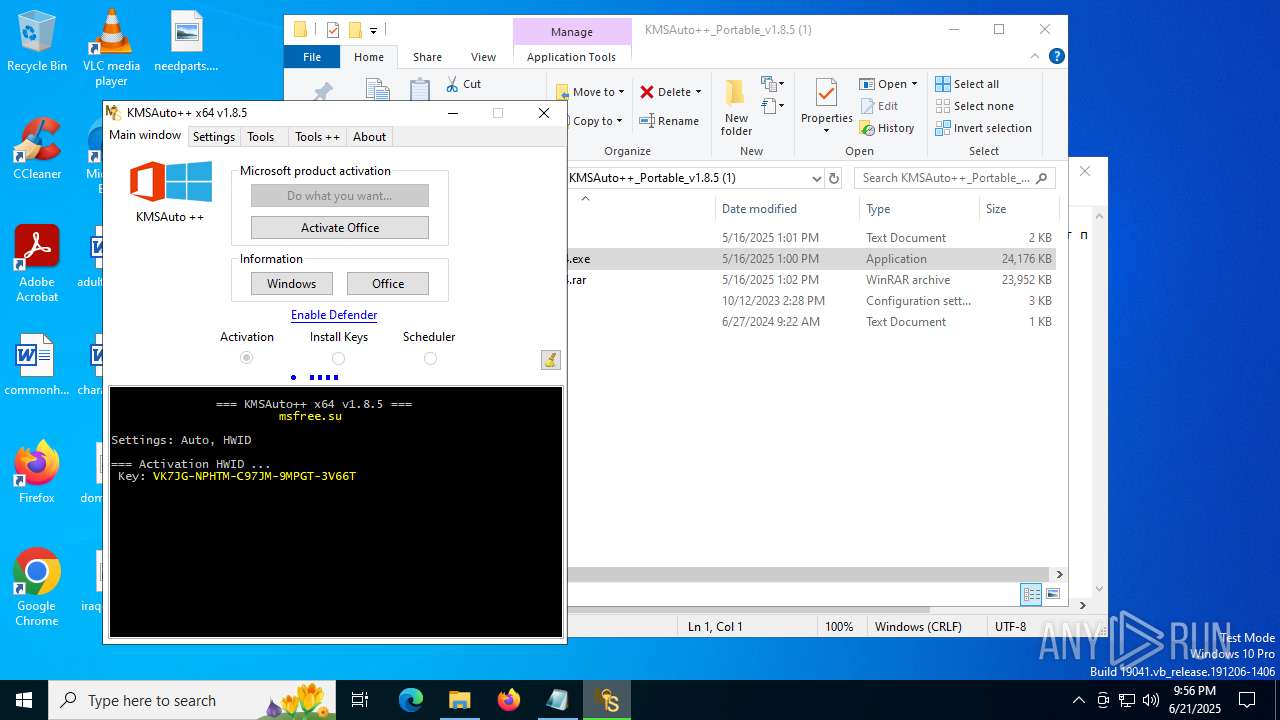
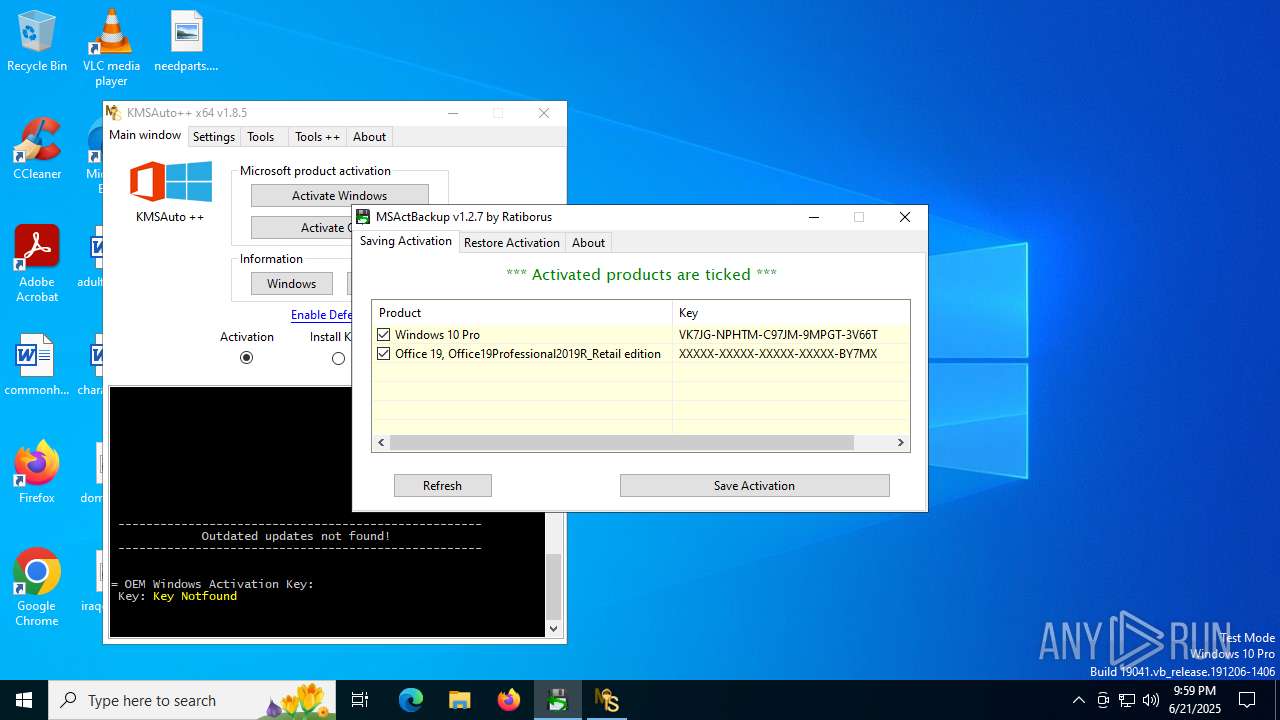
| 432 | wmic path SoftwareLicensingService where __CLASS='SoftwareLicensingService' call InstallProductKey ProductKey="VK7JG-NPHTM-C97JM-9MPGT-3V66T" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
84 196
Read events
84 103
Write events
86
Delete events
7
Modification events
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D95D8C51B2962F00 | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590702 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FDF8EFAD-B6ED-437A-810E-4AD73BB90D0C} | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590702 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7DE88523-2964-454C-B9C2-EDC9893D9A0B} | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590702 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CBDADDFE-26D9-4A90-AD36-56D64053E7EC} | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (2760) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
85
Suspicious files
465
Text files
348
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF176a91.TMP | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF176a91.TMP | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF176aa1.TMP | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF176ac0.TMP | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF176a91.TMP | — | |
MD5:— | SHA256:— | |||
| 2760 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
122
DNS requests
99
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6748 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:UUSRX5fUswrI9vlQ5-2NVIKXjCrbDPoT-IFSf04KDp0&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.25.50.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8164 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4648 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751018023&P2=404&P3=2&P4=Qa6B8JfUN9OofafXsE2bQCNpP7HUFO1Bj02OodteAhVx1leLSTZjE2Bbu3E4jx7UVwl%2b0U6u88%2bX3jxcUc8GPQ%3d%3d | unknown | — | — | whitelisted |
8164 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4648 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751018023&P2=404&P3=2&P4=Qa6B8JfUN9OofafXsE2bQCNpP7HUFO1Bj02OodteAhVx1leLSTZjE2Bbu3E4jx7UVwl%2b0U6u88%2bX3jxcUc8GPQ%3d%3d | unknown | — | — | whitelisted |
4648 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1751018023&P2=404&P3=2&P4=Qa6B8JfUN9OofafXsE2bQCNpP7HUFO1Bj02OodteAhVx1leLSTZjE2Bbu3E4jx7UVwl%2b0U6u88%2bX3jxcUc8GPQ%3d%3d | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3956 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6748 | msedge.exe | 93.158.134.91:443 | yabs.yandex.ru | YANDEX LLC | RU | whitelisted |
6748 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6748 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6748 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6748 | msedge.exe | 2.16.241.220:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
yabs.yandex.ru |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
kmsauto-free.ru |
| unknown |
www.bing.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potential Corporate Privacy Violation | ET INFO Observed DNS Query to Coin Mining Domain (nanopool .org) |
Process | Message |
|---|---|
Dism.exe | PID=5720 TID=7384 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5720 TID=7384 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=5720 TID=7384 Loading Provider from location C:\WINDOWS\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5720 TID=7384 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=5720 TID=7384 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=5720 TID=7384 Connecting to the provider located at C:\WINDOWS\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=3196 TID=3588 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=3196 TID=3588 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=3196 TID=3588 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=5720 TID=7384 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |