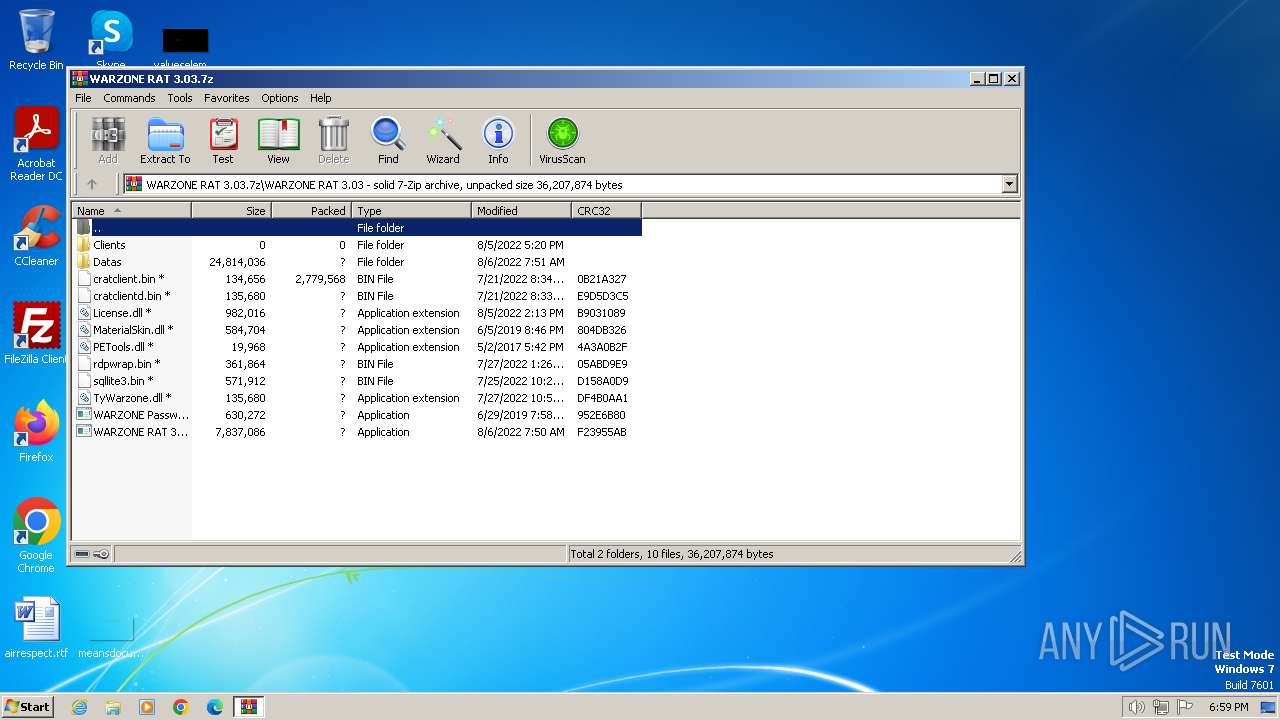
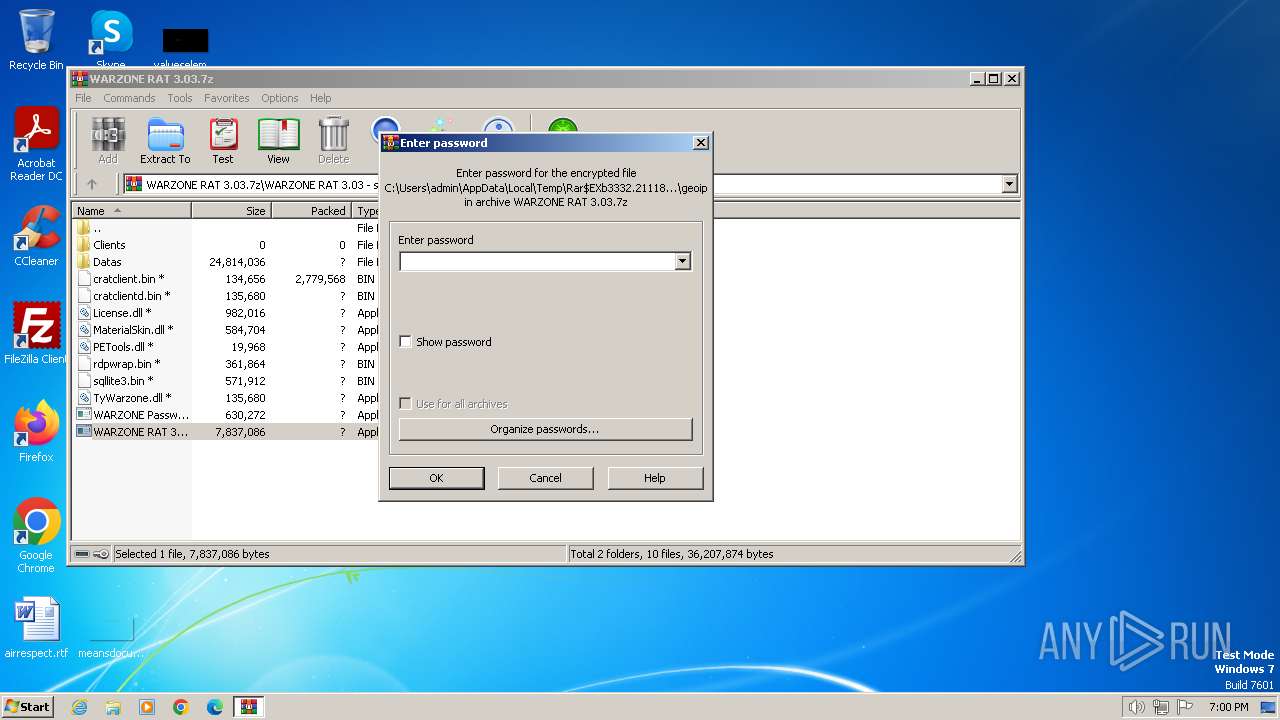
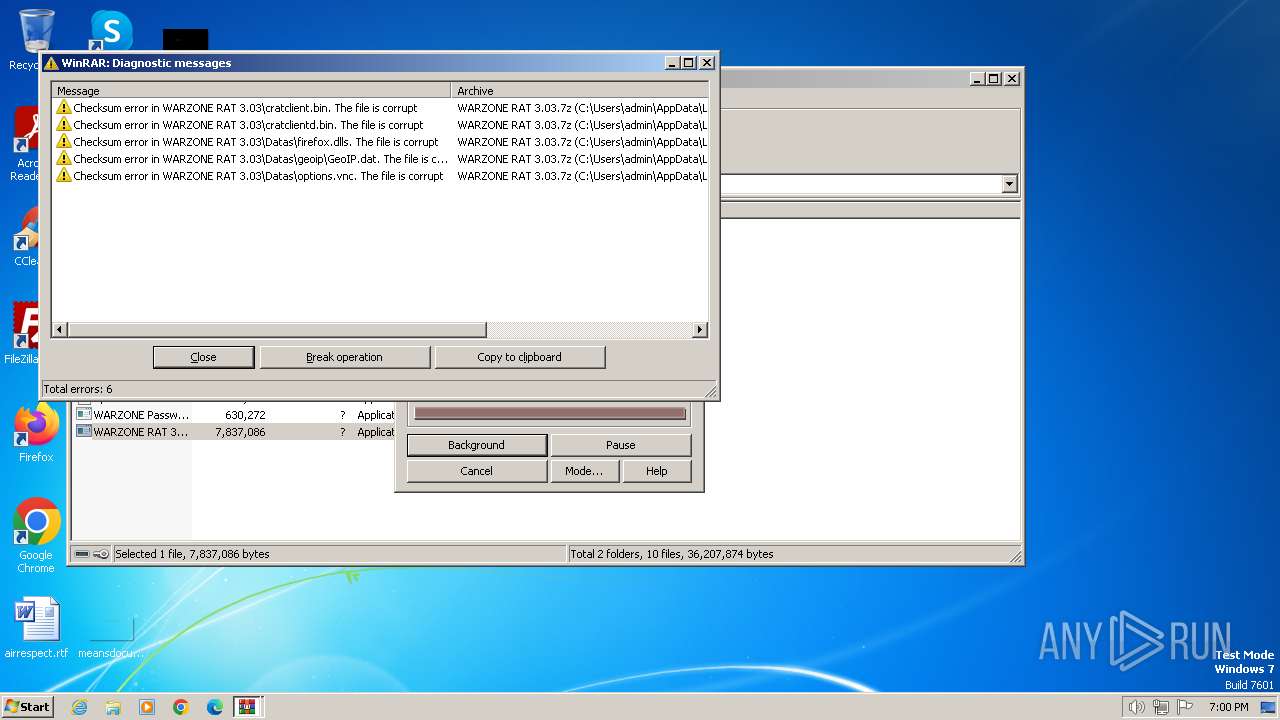
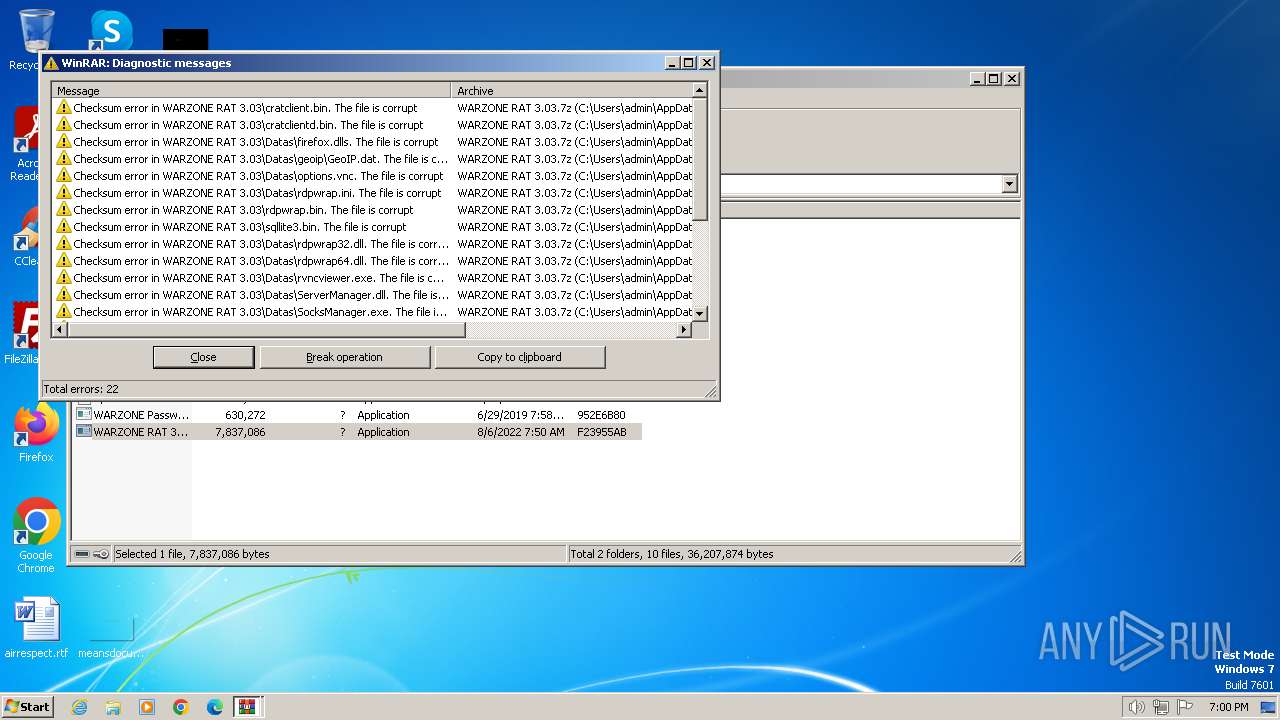
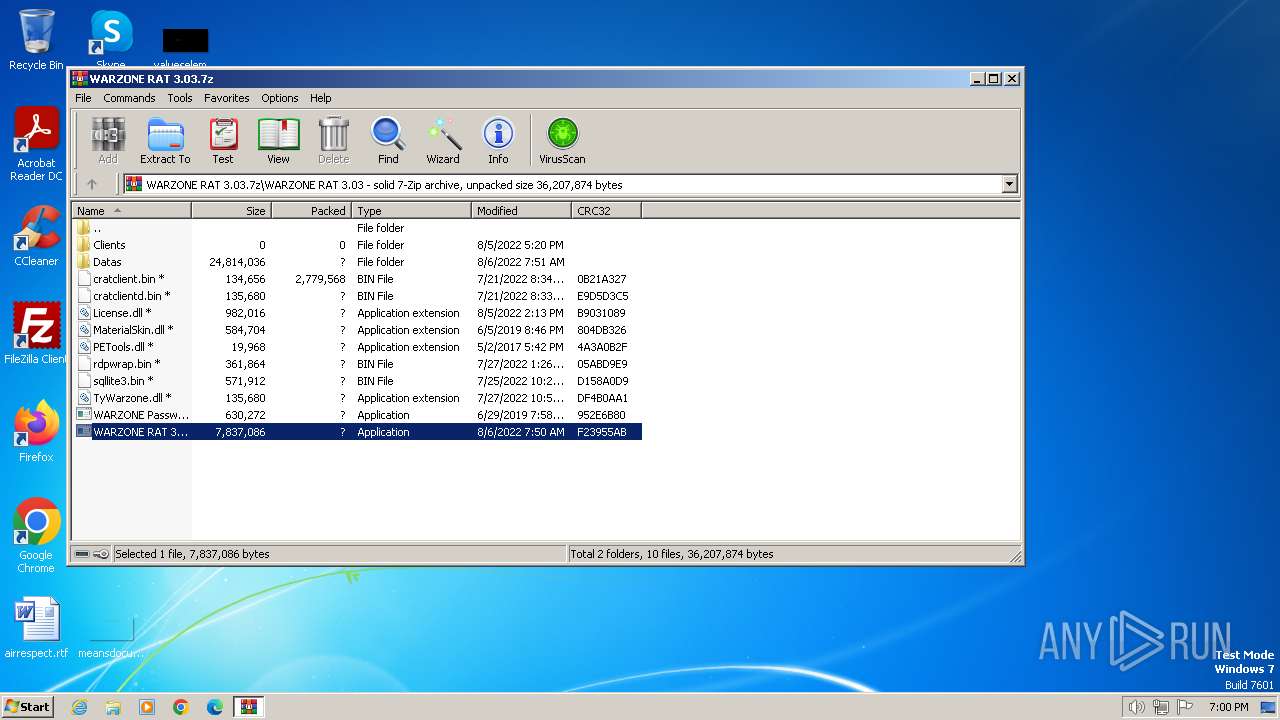
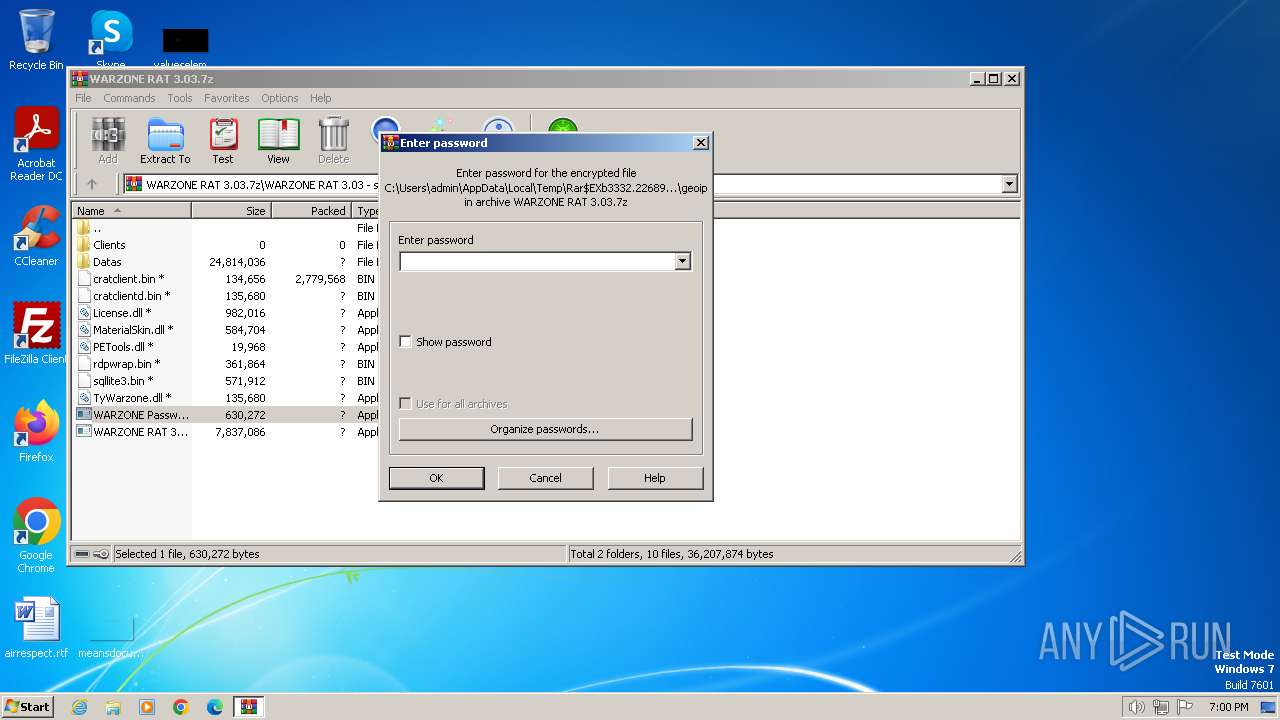
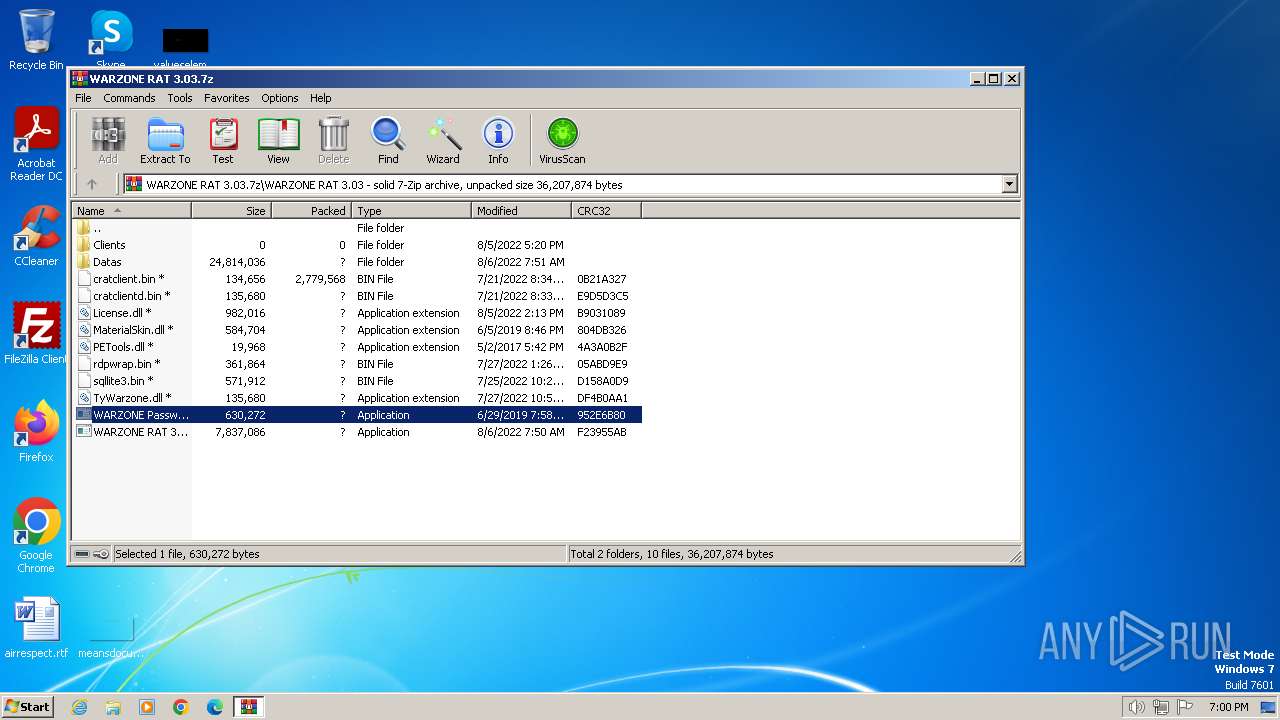
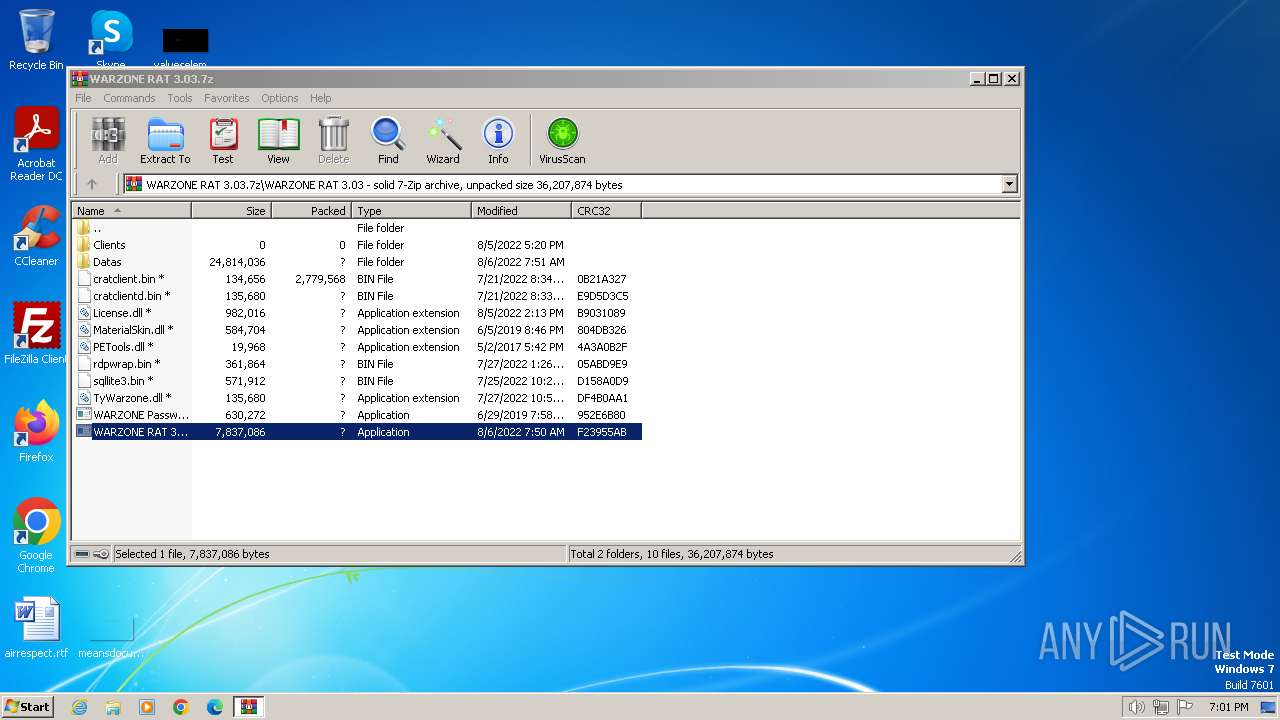
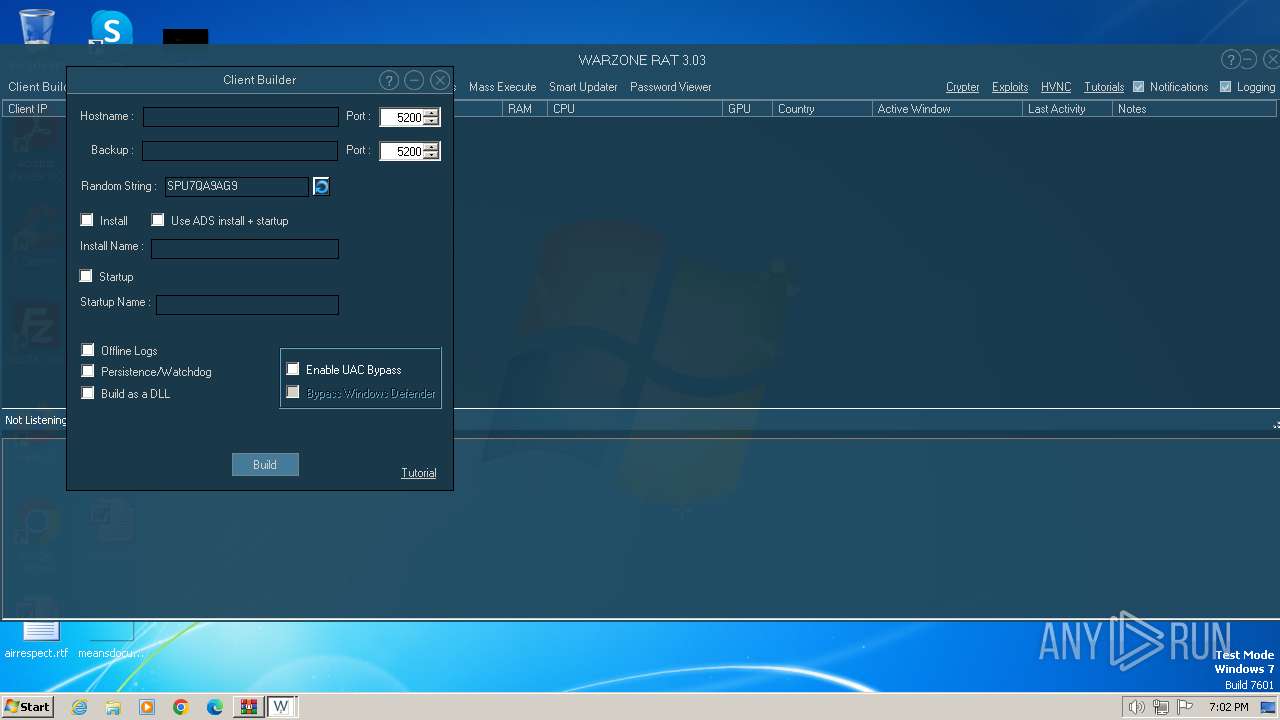
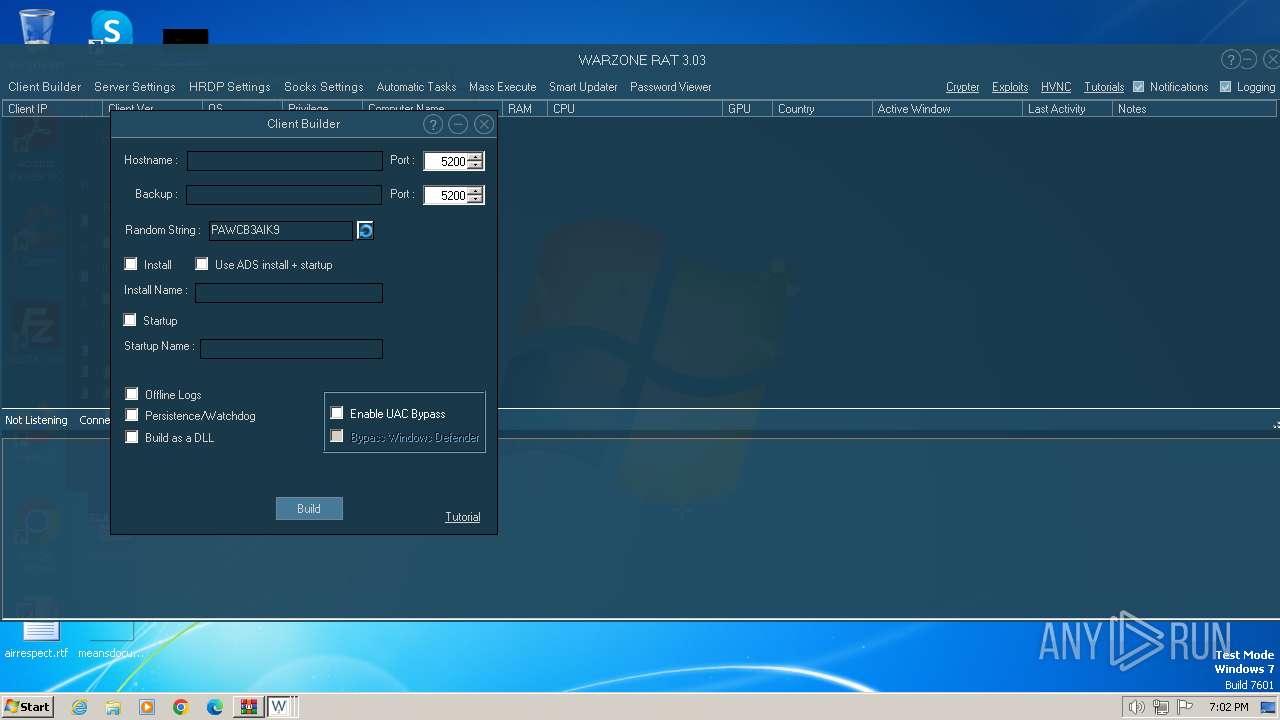
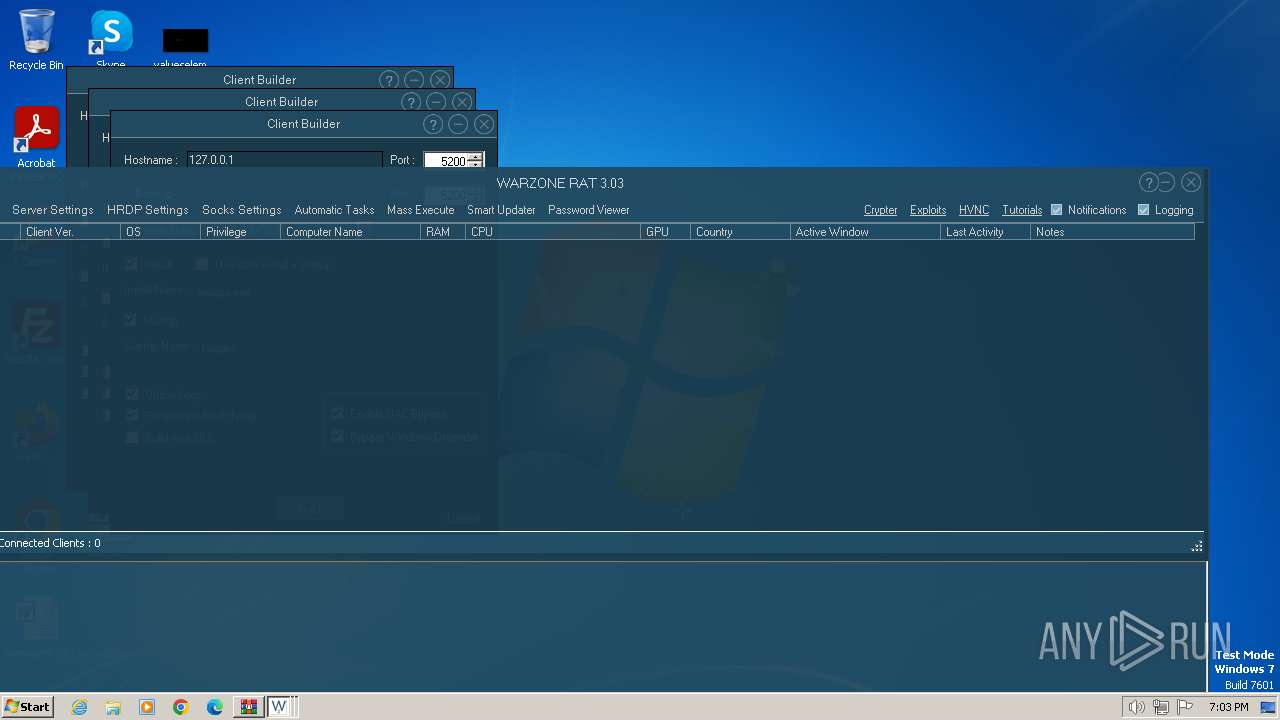
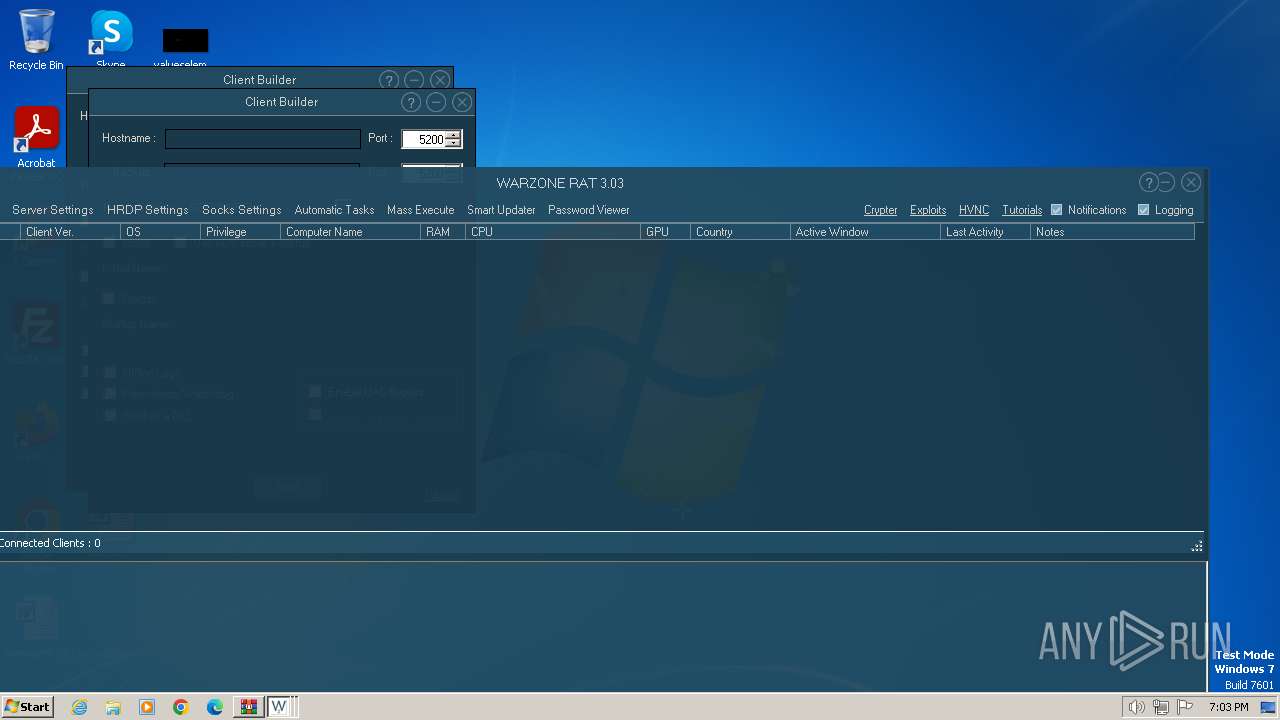
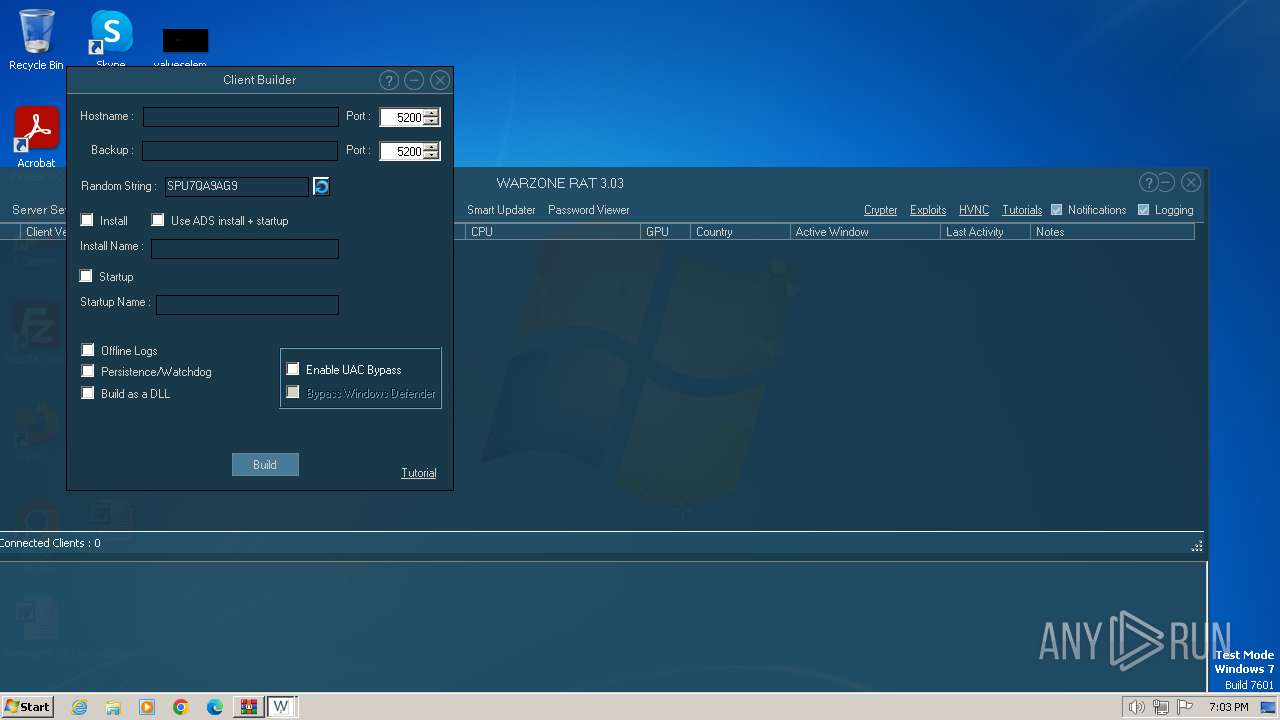
| File name: | WARZONE RAT 3.03.7z |
| Full analysis: | https://app.any.run/tasks/7e279dd7-2f03-47db-a7d1-019b7f2c3c75 |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | July 15, 2024, 17:59:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | BAA48B7B4F818EAC1961077A5A8DEC7B |
| SHA1: | DFB920F433043FC37C52C41BEEF84A7C3F5FEA51 |
| SHA256: | 3ACCE18FA1327B1E89C47997FE1DA62A86A1211D893F5128B4C59FA44D57B335 |
| SSDEEP: | 98304:TTzw3lMQ5RT71rIomca39H6/EvF/kUprELTFdDWAvQOzUhP2b8W8SPq4rLXsDj/s:QEo0sohXE+q+Oa3AgN/Xh9IQ/KgSj |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3332)
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- test.exe (PID: 2832)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 348)
WARZONE has been detected (YARA)
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- images.exe (PID: 3712)
Avemaria is detected
- test.exe (PID: 2832)
- images.exe (PID: 3924)
Changes the autorun value in the registry
- test.exe (PID: 2832)
Runs injected code in another process
- images.exe (PID: 3924)
- images.exe (PID: 3712)
The process bypass UAC
- Dism.exe (PID: 3784)
- Dism.exe (PID: 2776)
Application was injected by another process
- explorer.exe (PID: 1296)
Adds path to the Windows Defender exclusion list
- images.exe (PID: 3712)
SUSPICIOUS
The process drops Mozilla's DLL files
- WinRAR.exe (PID: 3332)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3332)
There is functionality for taking screenshot (YARA)
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
Reads the BIOS version
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- WARZONE RAT 3.03 Cracked.exe (PID: 3988)
Executable content was dropped or overwritten
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- cmd.exe (PID: 3328)
- test.exe (PID: 2832)
- dllhost.exe (PID: 3832)
- cmd.exe (PID: 348)
Reads the Internet Settings
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 348)
- powershell.exe (PID: 2672)
The process checks if it is being run in the virtual environment
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
Starts CMD.EXE for commands execution
- test.exe (PID: 2832)
- images.exe (PID: 3924)
Starts itself from another location
- test.exe (PID: 2832)
Script adds exclusion path to Windows Defender
- images.exe (PID: 3712)
Starts POWERSHELL.EXE for commands execution
- images.exe (PID: 3712)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2672)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3332)
Reads the machine GUID from the registry
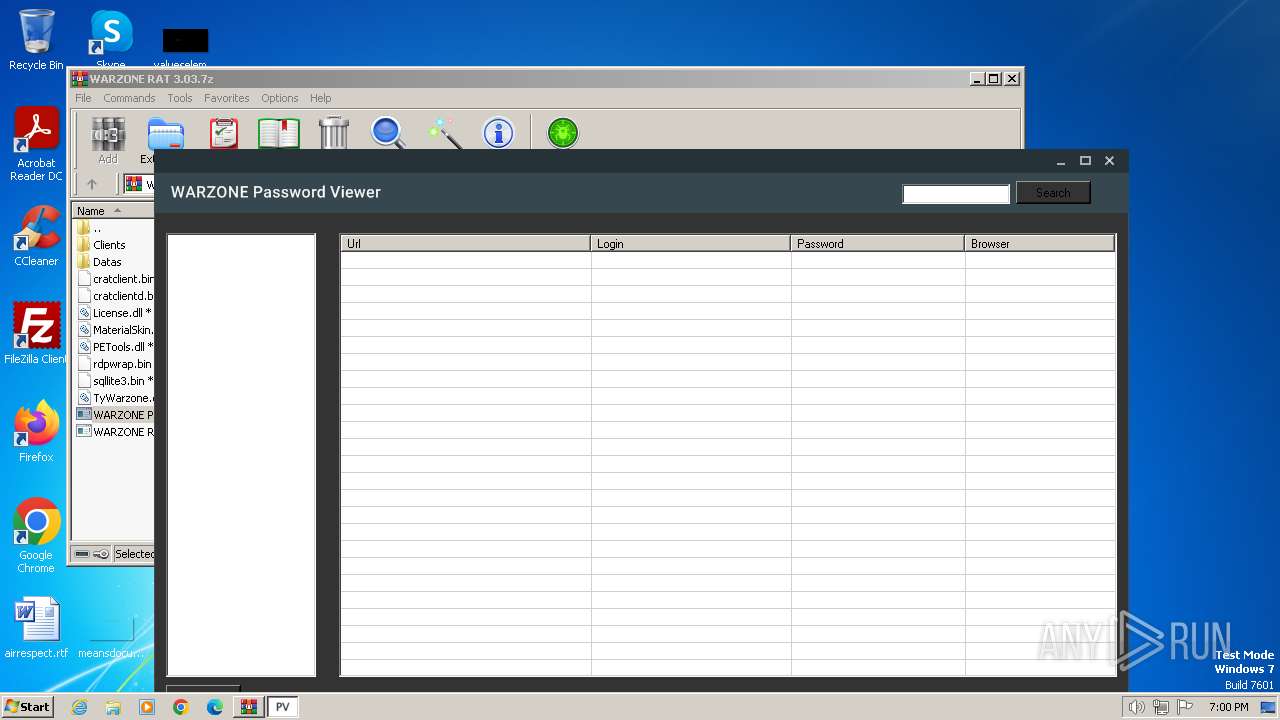
- WARZONE Password Viewer 1.0.exe (PID: 3128)
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
Checks supported languages
- WARZONE Password Viewer 1.0.exe (PID: 3128)
- wmpnscfg.exe (PID: 3556)
- WARZONE RAT 3.03 Cracked.exe (PID: 3988)
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- test.exe (PID: 2832)
- images.exe (PID: 3924)
- images.exe (PID: 3888)
- images.exe (PID: 3712)
- images.exe (PID: 1916)
- images.exe (PID: 3764)
- test.exe (PID: 2452)
Reads the computer name
- WARZONE Password Viewer 1.0.exe (PID: 3128)
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- wmpnscfg.exe (PID: 3556)
- test.exe (PID: 2832)
- WARZONE RAT 3.03 Cracked.exe (PID: 3988)
- images.exe (PID: 3924)
- images.exe (PID: 3888)
- images.exe (PID: 3764)
- images.exe (PID: 1916)
- test.exe (PID: 2452)
- images.exe (PID: 3712)
Manual execution by a user
- wmpnscfg.exe (PID: 3556)
- test.exe (PID: 2832)
- images.exe (PID: 3764)
- images.exe (PID: 1916)
- test.exe (PID: 2452)
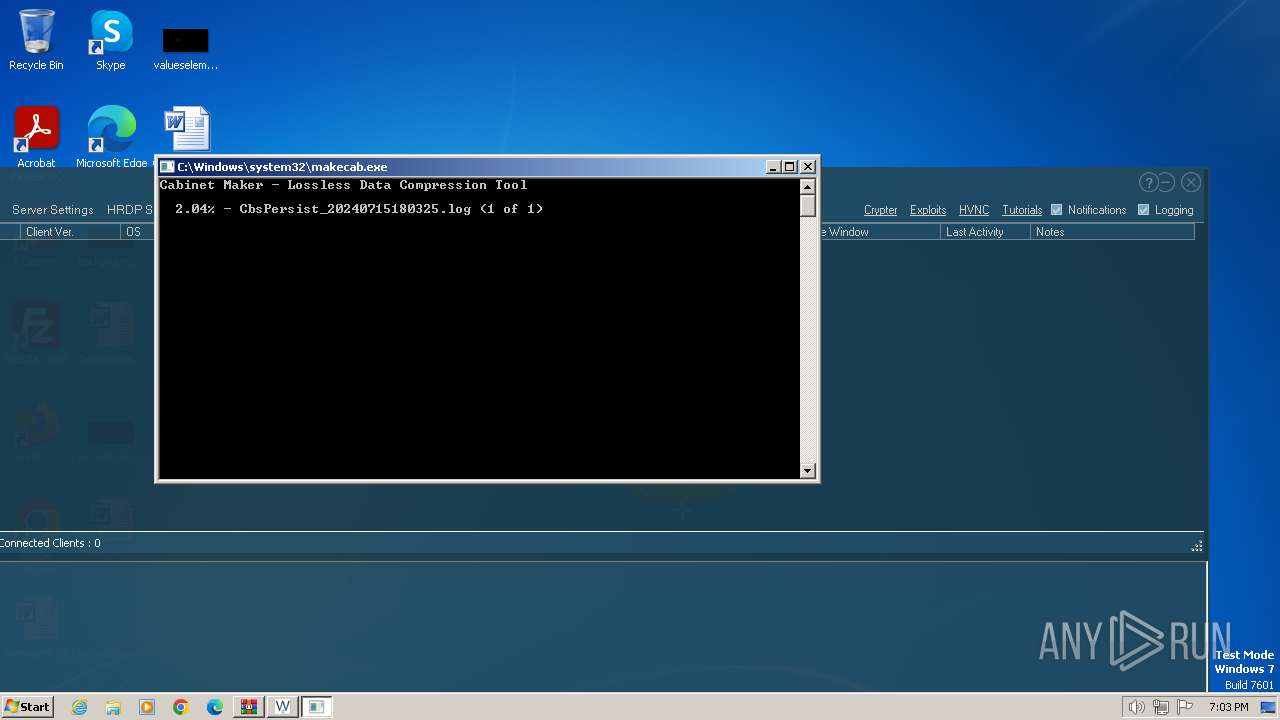
Create files in a temporary directory
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
- makecab.exe (PID: 3836)
- makecab.exe (PID: 2780)
Reads Windows Product ID
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
Themida protector has been detected
- WARZONE RAT 3.03 Cracked.exe (PID: 2420)
Reads security settings of Internet Explorer
- explorer.exe (PID: 1296)
Drops the executable file immediately after the start
- dllhost.exe (PID: 3832)
Checks transactions between databases Windows and Oracle
- cmd.exe (PID: 348)
- cmd.exe (PID: 3328)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2672)
Creates files in the program directory
- images.exe (PID: 3712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
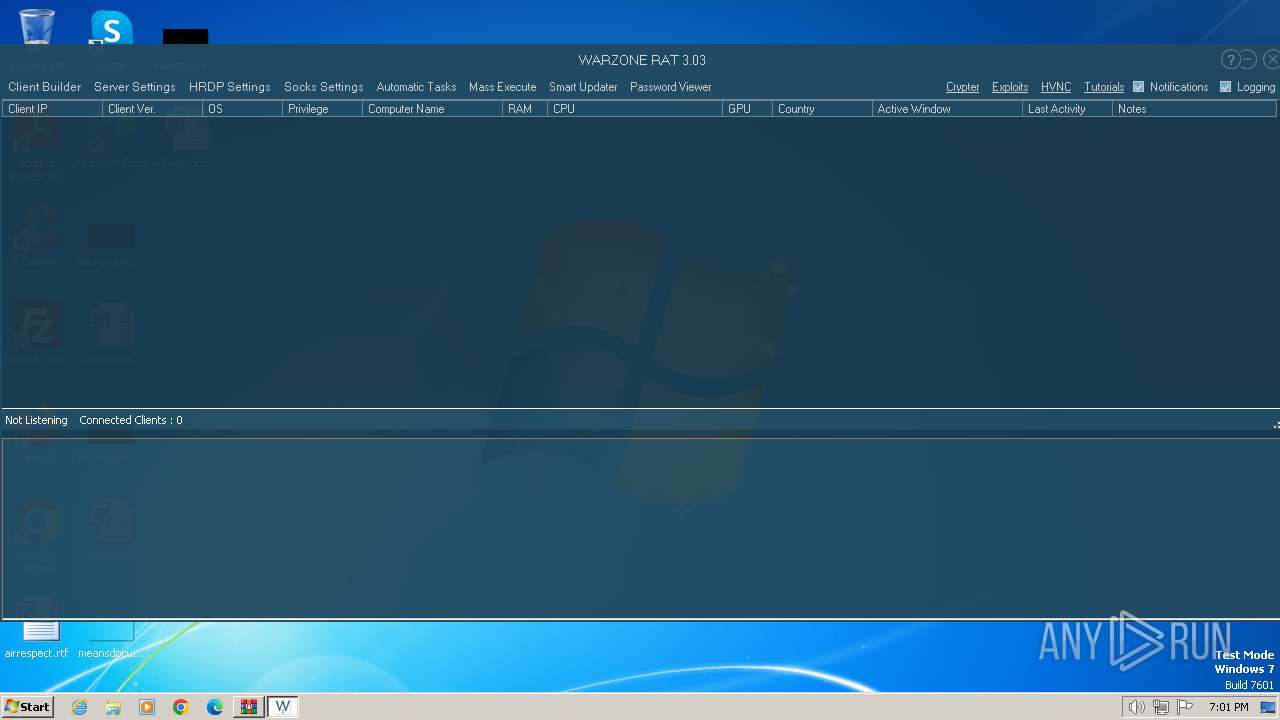
WarZone
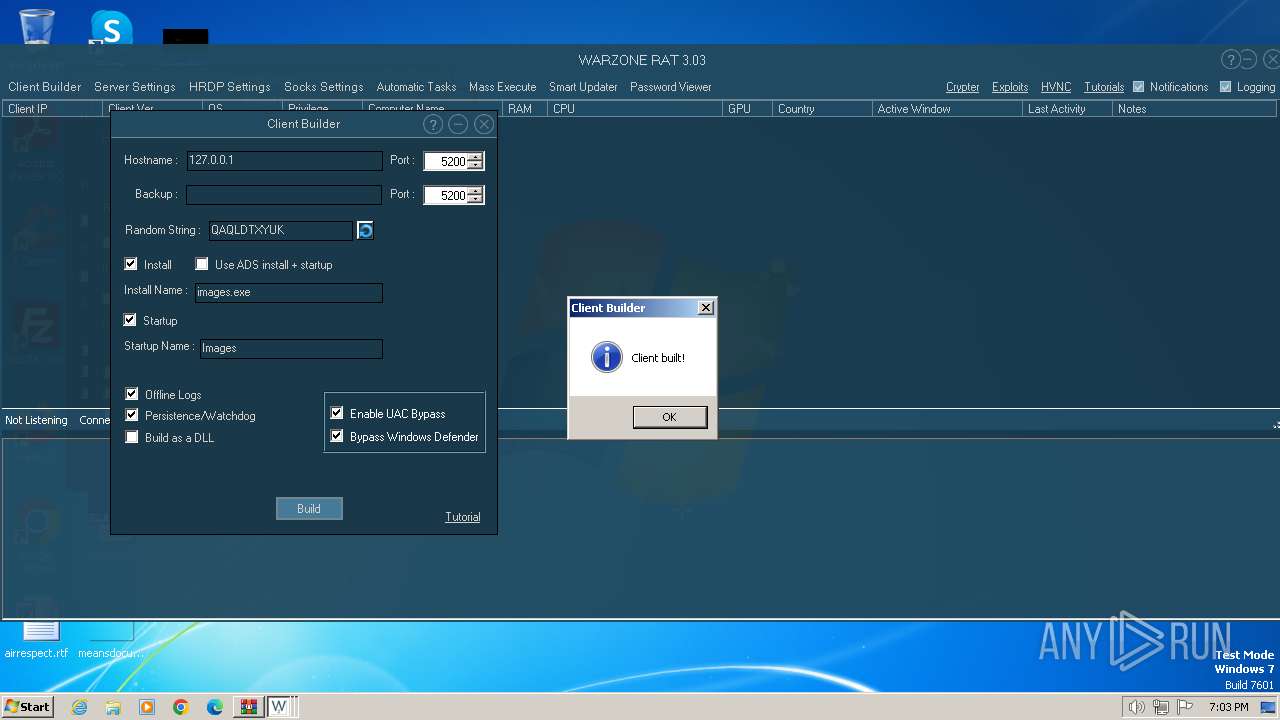
(PID) Process(3712) images.exe
C2 (1)127.0.0.1:5200
Options
Install FlagTrue
Startup FlagFalse
Startup nameimages.exeQAQLDTXYUK
Reverse Proxy local portNone
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
77
Monitored processes
25
Malicious processes
10
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 348 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | images.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1296 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1804 | "C:\Windows\system32\pkgmgr.exe" /n:%temp%\ellocnak.xml | C:\Windows\System32\PkgMgr.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Package Manager Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1916 | "C:\Users\admin\Documents\images.exe" | C:\Users\admin\Documents\images.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2396 | "C:\Windows\system32\pkgmgr.exe" /n:%temp%\ellocnak.xml | C:\Windows\System32\PkgMgr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Package Manager Exit code: 3221226540 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.24240\WARZONE RAT 3.03\WARZONE RAT 3.03 Cracked.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.24240\WARZONE RAT 3.03\WARZONE RAT 3.03 Cracked.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2452 | "C:\Users\admin\Desktop\test.exe" | C:\Users\admin\Desktop\test.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2672 | powershell Add-MpPreference -ExclusionPath C:\ | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | images.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2776 | "C:\Windows\system32\dism.exe" /online /norestart /apply-unattend:"C:\Users\admin\AppData\Local\Temp\ellocnak.xml" | C:\Windows\System32\Dism.exe | — | PkgMgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Image Servicing Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2780 | "C:\Windows\system32\makecab.exe" C:\Windows\Logs\CBS\CbsPersist_20240715180325.log C:\Windows\Logs\CBS\CbsPersist_20240715180325.cab | C:\Windows\System32\makecab.exe | — | PkgMgr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
22 735
Read events
22 509
Write events
221
Delete events
5
Modification events
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WARZONE RAT 3.03.7z | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3332) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
54
Suspicious files
26
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\Datas\firefox.dlls | executable | |
MD5:A26861558315278D5960FE1BF58B1950 | SHA256:B52720863EC78E0F7BFF98E6C809FDF50AB2D0EA361E95EB5341E870AAFB0354 | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\cratclient.bin | executable | |
MD5:AEDB2E69D91D2C8AFF792E5C0B2396A0 | SHA256:E76B0D04117DAA58544D87B69427AAA6A78D90461470A2A55C80616842180451 | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\cratclientd.bin | executable | |
MD5:F6DBE80A1B68A734C92375FBBCF4BE88 | SHA256:D364FE03510F34C22E8B5D25784BA80DECAE568BD939DB66E4CD8B90538D60BE | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\Datas\options.vnc | ini | |
MD5:6243B2004273137CB880196F4472268B | SHA256:11C79026B86D78DF113DD84848065175BC39EFADD48DF4C9768CA685E8FAFFC4 | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\Datas\geoip\GeoIP.dat | binary | |
MD5:42368516B6BD3C337AA64A012FBA8C3D | SHA256:57B31E52D36571CF8D52BA6ECAB8D0DC8C6705B5ED94D9F7F98B01F40863E5A0 | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\sqllite3.bin | binary | |
MD5:3FF5EB1505911A17716FE10A9CA96CB4 | SHA256:467B77FB1D8559AB4A6D9C2DE21575E81E39D07E617F1AA2E5F47FA86F80D92C | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\Datas\rvncviewer.exe | executable | |
MD5:27561E722C736AB5A77110790402999B | SHA256:5E49A7FEC8C9F81B191E5FA69BDB1A627814631813FEDFC4136C71E55CD57C0F | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\License.dll | executable | |
MD5:CB63D02B2189EEEF93F7ABDD88450095 | SHA256:8E680C2074E5E701174F801125CB438C55A4A65649B4C7307E10DE61879CBE65 | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\Datas\rdpwrap.ini | binary | |
MD5:4D18179C3E64E912A2ECD80A8AED4AA7 | SHA256:2DE7C3DB2E91021BAE6E16D67677EA9EF123809EED237F804D4F7B3C0315BA5C | |||
| 3332 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb3332.22689\WARZONE RAT 3.03\TyWarzone.dll | executable | |
MD5:8972FBD74954FB223BD1F8000AFEFBED | SHA256:20B6D6C9E4C611BEB2394539B90CE3B904B28D296B08DA9D07D19A0FFC2971A1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
15
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 217.20.57.34:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1060 | svchost.exe | 217.20.57.34:80 | ctldl.windowsupdate.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
microsoft.com |
| whitelisted |