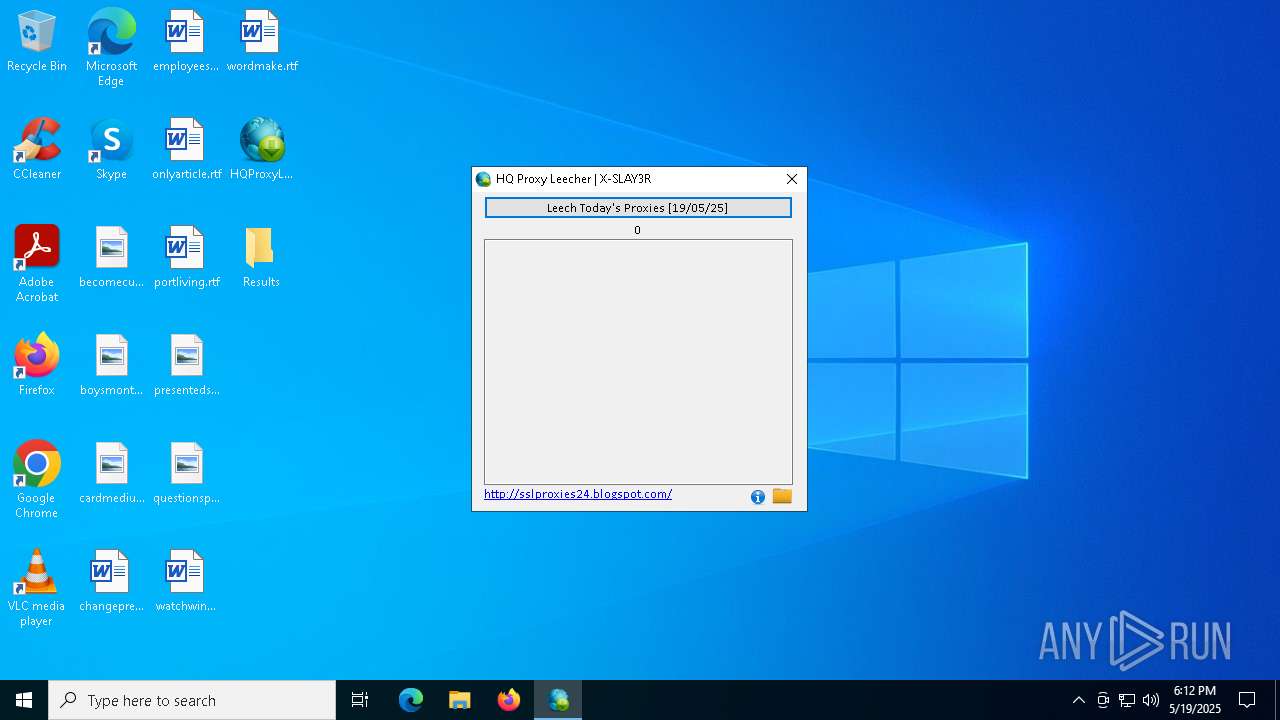
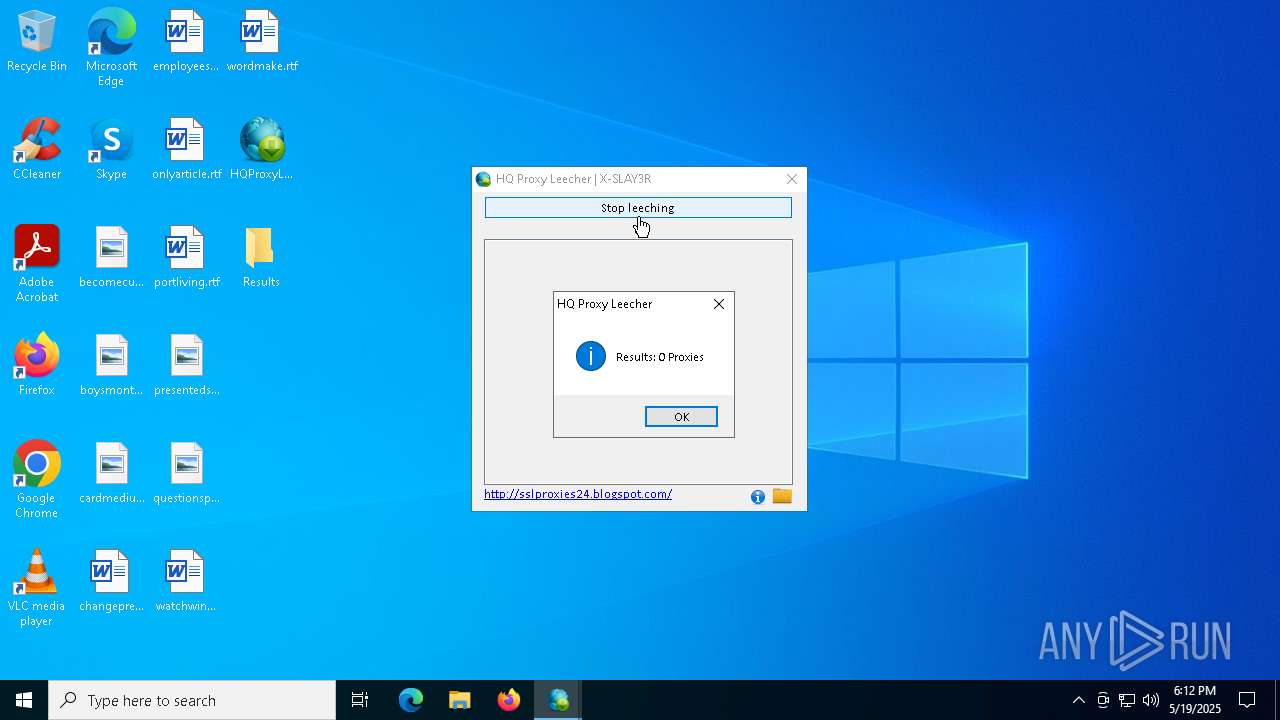
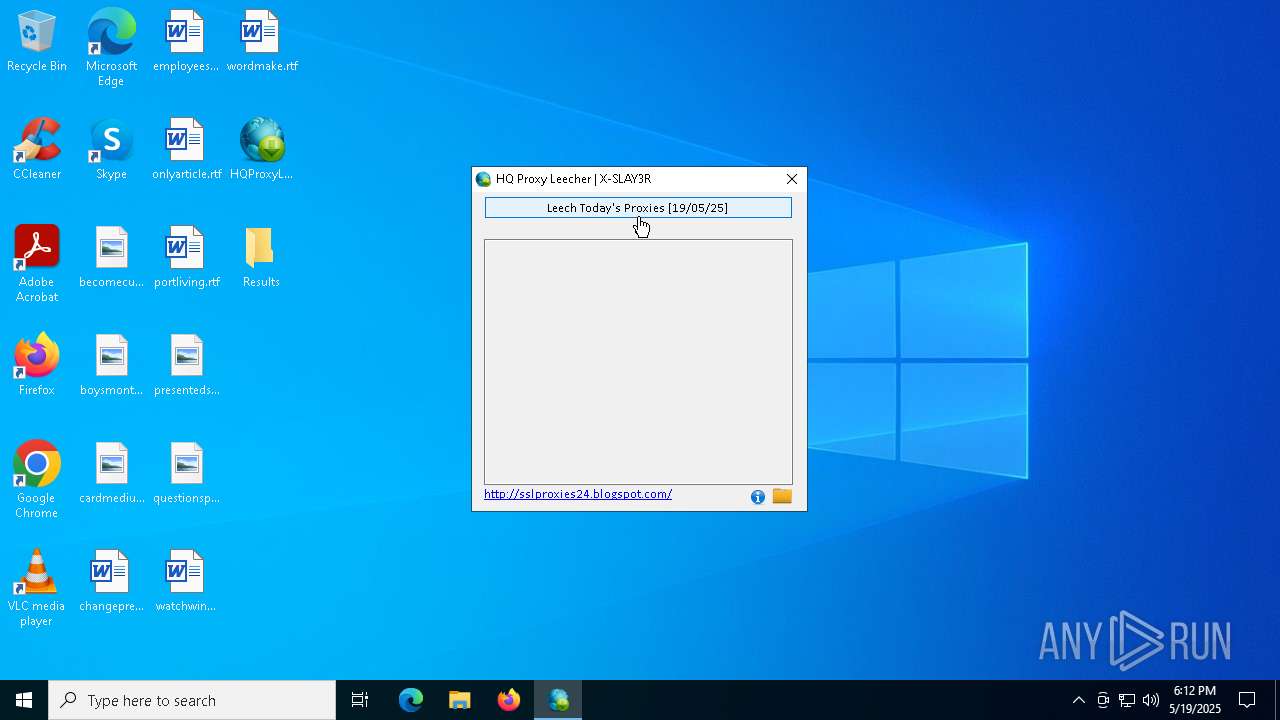
| File name: | HQProxyLeecher.exe |
| Full analysis: | https://app.any.run/tasks/0d942178-ceb7-41b6-8c66-a9a6c622c923 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 19, 2025, 18:11:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 6E9E65685E1C491D9720DF0A4D7D2A62 |
| SHA1: | 4A99C09E7F072DB0087D67689FD7D1135BEAEC45 |
| SHA256: | 3AA57CD00E4A4096942C3B108934E697D2E3A485B0204F973FCA5D80EE38F449 |
| SSDEEP: | 98304:OrNMECxyXubAe80/mIkGCpljvWw7qTeFpghH5m00zDQAvj1Tr+rjcTcBmZhP1FtS:OUcld2hj |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- fsdfsdfsdf.tmp (PID: 7824)
AMADEY has been detected (SURICATA)
- nudwee.exe (PID: 7872)
Connects to the CnC server
- nudwee.exe (PID: 7872)
Actions looks like stealing of personal data
- erezrzerze.exe (PID: 7652)
Runs injected code in another process
- regsvr32.exe (PID: 7952)
AMADEY has been detected (YARA)
- nudwee.exe (PID: 7872)
Application was injected by another process
- explorer.exe (PID: 5492)
SUSPICIOUS
Reads the date of Windows installation
- HQProxyLeecher.exe (PID: 7568)
Process drops legitimate windows executable
- HQProxyLeecher.exe (PID: 7568)
- fsdfsdfsdf.tmp (PID: 7708)
- fsdfsdfsdf.tmp (PID: 7824)
- explorer.exe (PID: 5492)
Executable content was dropped or overwritten
- HQProxyLeecher.exe (PID: 7568)
- fsdfsdfsdf.tmp (PID: 7708)
- fsdfsdfsdf.exe (PID: 7632)
- fsdfsdfsdf.exe (PID: 7796)
- cxwcwxs.exe (PID: 7668)
- fsdfsdfsdf.tmp (PID: 7824)
- explorer.exe (PID: 5492)
Reads security settings of Internet Explorer
- HQProxyLeecher.exe (PID: 7568)
- cxwcwxs.exe (PID: 7668)
- fsdfsdfsdf.tmp (PID: 7708)
- nudwee.exe (PID: 7872)
- Launcher.exe (PID: 7688)
- erezrzerze.exe (PID: 7652)
Reads the Windows owner or organization settings
- fsdfsdfsdf.tmp (PID: 7708)
- fsdfsdfsdf.tmp (PID: 7824)
Starts itself from another location
- cxwcwxs.exe (PID: 7668)
Reads Internet Explorer settings
- Launcher.exe (PID: 7688)
Starts POWERSHELL.EXE for commands execution
- regsvr32.exe (PID: 7952)
- regsvr32.exe (PID: 1272)
- regsvr32.exe (PID: 7480)
Connects to the server without a host name
- nudwee.exe (PID: 7872)
- erezrzerze.exe (PID: 7652)
- D762.tmp.exe (PID: 4200)
- explorer.exe (PID: 5492)
Contacting a server suspected of hosting an CnC
- nudwee.exe (PID: 7872)
The process hide an interactive prompt from the user
- regsvr32.exe (PID: 7952)
The process bypasses the loading of PowerShell profile settings
- regsvr32.exe (PID: 7952)
Potential Corporate Privacy Violation
- erezrzerze.exe (PID: 7652)
- D762.tmp.exe (PID: 4200)
There is functionality for taking screenshot (YARA)
- nudwee.exe (PID: 7872)
There is functionality for enable RDP (YARA)
- nudwee.exe (PID: 7872)
The process executes via Task Scheduler
- nudwee.exe (PID: 3884)
- regsvr32.exe (PID: 1272)
- regsvr32.exe (PID: 7480)
- nudwee.exe (PID: 7228)
Executes application which crashes
- D762.tmp.exe (PID: 4200)
Starts a Microsoft application from unusual location
- D762.tmp.exe (PID: 4200)
INFO
The sample compiled with english language support
- HQProxyLeecher.exe (PID: 7568)
- fsdfsdfsdf.tmp (PID: 7708)
- fsdfsdfsdf.tmp (PID: 7824)
- explorer.exe (PID: 5492)
Reads the computer name
- HQProxyLeecher.exe (PID: 7568)
- vxcvxcvcx.exe (PID: 7612)
- fsdfsdfsdf.tmp (PID: 7708)
- Launcher.exe (PID: 7688)
- fsdfsdfsdf.tmp (PID: 7824)
- cxwcwxs.exe (PID: 7668)
- nudwee.exe (PID: 7872)
- erezrzerze.exe (PID: 7652)
- identity_helper.exe (PID: 2284)
Checks supported languages
- HQProxyLeecher.exe (PID: 7568)
- vxcvxcvcx.exe (PID: 7612)
- fsdfsdfsdf.exe (PID: 7632)
- erezrzerze.exe (PID: 7652)
- Launcher.exe (PID: 7688)
- fsdfsdfsdf.tmp (PID: 7708)
- fsdfsdfsdf.exe (PID: 7796)
- fsdfsdfsdf.tmp (PID: 7824)
- nudwee.exe (PID: 7872)
- cxwcwxs.exe (PID: 7668)
- identity_helper.exe (PID: 2284)
- nudwee.exe (PID: 3884)
- D762.tmp.exe (PID: 4200)
Create files in a temporary directory
- fsdfsdfsdf.tmp (PID: 7708)
- fsdfsdfsdf.exe (PID: 7632)
- fsdfsdfsdf.exe (PID: 7796)
- fsdfsdfsdf.tmp (PID: 7824)
- cxwcwxs.exe (PID: 7668)
- erezrzerze.exe (PID: 7652)
- explorer.exe (PID: 5492)
Process checks computer location settings
- HQProxyLeecher.exe (PID: 7568)
- cxwcwxs.exe (PID: 7668)
- fsdfsdfsdf.tmp (PID: 7708)
Creates files or folders in the user directory
- HQProxyLeecher.exe (PID: 7568)
- fsdfsdfsdf.tmp (PID: 7824)
- erezrzerze.exe (PID: 7652)
Reads the machine GUID from the registry
- Launcher.exe (PID: 7688)
Disables trace logs
- Launcher.exe (PID: 7688)
Reads Environment values
- Launcher.exe (PID: 7688)
- identity_helper.exe (PID: 2284)
Checks proxy server information
- nudwee.exe (PID: 7872)
- Launcher.exe (PID: 7688)
- erezrzerze.exe (PID: 7652)
- explorer.exe (PID: 5492)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7972)
- powershell.exe (PID: 5072)
- powershell.exe (PID: 1388)
Application based on Rust
- erezrzerze.exe (PID: 7652)
Confuser has been detected (YARA)
- Launcher.exe (PID: 7688)
Creates files in the program directory
- erezrzerze.exe (PID: 7652)
Manual execution by a user
- msedge.exe (PID: 7012)
Application launched itself
- msedge.exe (PID: 6640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(7872) nudwee.exe
C2185.156.72.8
URLhttp://185.156.72.8/rob75u9v/index.php
Version5.34
Options
Drop directory56e51a1e3a
Drop namenudwee.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
nudwee.exe
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
185.156.72.8
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
/rob75u9v/index.php
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
56e51a1e3a
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (46.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (41) |
| .exe | | | Win32 Executable (generic) (6.6) |
| .exe | | | Generic Win/DOS Executable (2.9) |
| .exe | | | DOS Executable Generic (2.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:17 17:10:46+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 122880 |
| InitializedDataSize: | 6600704 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5e6c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.1.1 |
| ProductVersionNumber: | 3.1.1.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Opwcv |
| FileVersion: | 6.0.0.0 |
| InternalName: | Opwcv.exe |
| LegalCopyright: | (C) 2026 |
| OriginalFileName: | Opwcv.exe |
| ProductName: | Opwcv |
| ProductVersion: | 3.1.1.1 |
Total processes
203
Monitored processes
75
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6676 --field-trial-handle=2392,i,15784883992151682363,13664499303884639500,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=33 --mojo-platform-channel-handle=7064 --field-trial-handle=2392,i,15784883992151682363,13664499303884639500,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6456 --field-trial-handle=2392,i,15784883992151682363,13664499303884639500,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 968 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3876 --field-trial-handle=2392,i,15784883992151682363,13664499303884639500,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5200 --field-trial-handle=2392,i,15784883992151682363,13664499303884639500,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1272 | "C:\WINDOWS\system32\regsvr32.EXE" /s /i:INSTALL "C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\2XamlDiagnostics_3.pfx" | C:\Windows\System32\regsvr32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | C:\WINDOWS\system32\WerFault.exe -u -p 4200 -s 1316 | C:\Windows\System32\WerFault.exe | — | D762.tmp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "powershell" -Command "if (Get-ScheduledTask | Where-Object { $_.Actions.Execute -eq 'regsvr32' -and $_.Actions.Arguments -eq '/s /i:INSTALL \"%APPDATA%\Microsoft\SystemCertificates\2XamlDiagnostics_3.pfx\"' }) { exit 0 } else { exit 1 }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4400 --field-trial-handle=2392,i,15784883992151682363,13664499303884639500,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
38 297
Read events
38 231
Write events
62
Delete events
4
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 75742B6800000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000030308 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000030308 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000004034E |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000004034E |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000A0288 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000020258 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000020258 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010015000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000011000000000000006200650063006F006D0065006300750070002E0070006E0067003E00200020000000110000000000000062006F00790073006D006F006E00740068002E006A00700067003E00200020000000120000000000000063006100720064006D0065006400690075006D002E0070006E0067003E0020002000000012000000000000006300680061006E006700650070007200650076002E007200740066003E00200020000000170000000000000065006D0070006C006F0079006500650073006C006F006E0064006F006E002E007200740066003E0020002000000013000000000000006F006E006C007900610072007400690063006C0065002E007200740066003E00200020000000120000000000000070006F00720074006C006900760069006E0067002E007200740066003E002000200000001400000000000000700072006500730065006E00740065006400730075006E002E006A00700067003E0020002000000015000000000000007100750065007300740069006F006E00730070006F00730074002E006A00700067003E00200020000000140000000000000077006100740063006800770069006E0064006F00770073002E007200740066003E00200020000000100000000000000077006F00720064006D0061006B0065002E007200740066003E00200020000000160000000000000048005100500072006F00780079004C006500650063006800650072002E006500780065003E002000200000000B0000000000000052006500730075006C00740073003E005C0020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001500000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000040400000803F130000004040000000401400 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
Executable files
25
Suspicious files
160
Text files
56
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7568 | HQProxyLeecher.exe | C:\Users\admin\AppData\Roaming\Launcher.exe | executable | |
MD5:A160657E3486492BA76934962550AA24 | SHA256:E3259748D2CD8E80B5A53F37C45CE2225D54F0291CF88ACC36BE8B50DACE614F | |||
| 7568 | HQProxyLeecher.exe | C:\Users\admin\AppData\Roaming\vxcvxcvcx.exe | executable | |
MD5:3E06E418F438F814525C2BAD5BB80028 | SHA256:A73CFF305EDDEA87953AAC19C8EB192357E67898E630836082B9087D173AC2BC | |||
| 7824 | fsdfsdfsdf.tmp | C:\Users\admin\AppData\Local\Temp\is-H1034.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 7568 | HQProxyLeecher.exe | C:\Users\admin\AppData\Roaming\fsdfsdfsdf.exe | executable | |
MD5:4E8144068DAF97AE616160FDCC26F34F | SHA256:0C181B7D7E866BE58430F2B4EA0B8822BD1C1A5C64E63815AE9B8531134F42B4 | |||
| 7632 | fsdfsdfsdf.exe | C:\Users\admin\AppData\Local\Temp\is-8B6A6.tmp\fsdfsdfsdf.tmp | executable | |
MD5:FFD4DF78AA9788CA6A3DC61077AD50ED | SHA256:5F620B954086C437DAA38012076FE6C453F28F6FD2A1459018C26CB7BDCF20E6 | |||
| 7568 | HQProxyLeecher.exe | C:\Users\admin\AppData\Roaming\erezrzerze.exe | executable | |
MD5:4F17FF0609C453A1D2DE788D8F9744C3 | SHA256:FBCBE26A6C1A6FC8B451D3AEC8A91384A15124C8CA9931363BDD9ED174631B11 | |||
| 7568 | HQProxyLeecher.exe | C:\Users\admin\AppData\Roaming\cxwcwxs.exe | executable | |
MD5:B672FBD389B94BF5449CEAFE32346037 | SHA256:2106190991EFC4291F4211DD54DDB7444E7BF51503842A1380A4A1D902D888B6 | |||
| 7824 | fsdfsdfsdf.tmp | C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\is-R5SBR.tmp | executable | |
MD5:E1C166179121741D0D0E7E3EB37483D7 | SHA256:042EDF9FA6AE5D48C84E66361312ADA77B419BE6D4DD0B1AA2CF538550B23AB6 | |||
| 7708 | fsdfsdfsdf.tmp | C:\Users\admin\AppData\Local\Temp\is-HDNRH.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 7708 | fsdfsdfsdf.tmp | C:\Users\admin\AppData\Local\Temp\is-HDNRH.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
145
DNS requests
118
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7688 | Launcher.exe | GET | 200 | 103.224.182.251:80 | http://www.sslproxies24.top/ | unknown | — | — | whitelisted |
7872 | nudwee.exe | POST | 200 | 185.156.72.8:80 | http://185.156.72.8/rob75u9v/index.php | unknown | — | — | malicious |
7872 | nudwee.exe | POST | 200 | 185.156.72.8:80 | http://185.156.72.8/rob75u9v/index.php | unknown | — | — | malicious |
7652 | erezrzerze.exe | POST | 200 | 185.156.72.8:80 | http://185.156.72.8/zpaxpjz/get.php | unknown | — | — | malicious |
7652 | erezrzerze.exe | POST | 200 | 185.156.72.8:80 | http://185.156.72.8/zpaxpjz/get.php | unknown | — | — | malicious |
5680 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7652 | erezrzerze.exe | POST | 200 | 185.156.72.8:80 | http://185.156.72.8/zpaxpjz/get.php | unknown | — | — | malicious |
7652 | erezrzerze.exe | POST | 200 | 185.156.72.8:80 | http://185.156.72.8/zpaxpjz/get.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
2104 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7872 | nudwee.exe | 185.156.72.8:80 | — | Tov Vaiz Partner | RU | malicious |
7688 | Launcher.exe | 103.224.182.251:80 | www.sslproxies24.top | Trellian Pty. Limited | AU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
www.sslproxies24.top |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
7872 | nudwee.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7688 | Launcher.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
7688 | Launcher.exe | Potentially Bad Traffic | ET HUNTING Request to .TOP Domain with Minimal Headers |
7872 | nudwee.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7872 | nudwee.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7652 | erezrzerze.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
7652 | erezrzerze.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Sending Screenshot in Archive via POST Request |
7652 | erezrzerze.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
7652 | erezrzerze.exe | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |