| download: | /bbf2.zip |
| Full analysis: | https://app.any.run/tasks/71cadfb9-c669-4ba5-90de-f3febc9bb446 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | February 17, 2024, 01:42:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B9AE47E689E028C4DC52650F63A7B741 |
| SHA1: | 76C54BCF4AC2D471336FD057B24B6A663BEAF87B |
| SHA256: | 3A6E5838A03790664F3653D6EEDAE016D0EB6E2006EF6E870281D18A697FA9D8 |
| SSDEEP: | 98304:V8W3RTTrbwmGgrVdoaiPA8Eqfz6fZzGdyssYTbpd5vF5+PJlIdcXcnBYwIy/FnJW:A1vhD+6E |
MALICIOUS
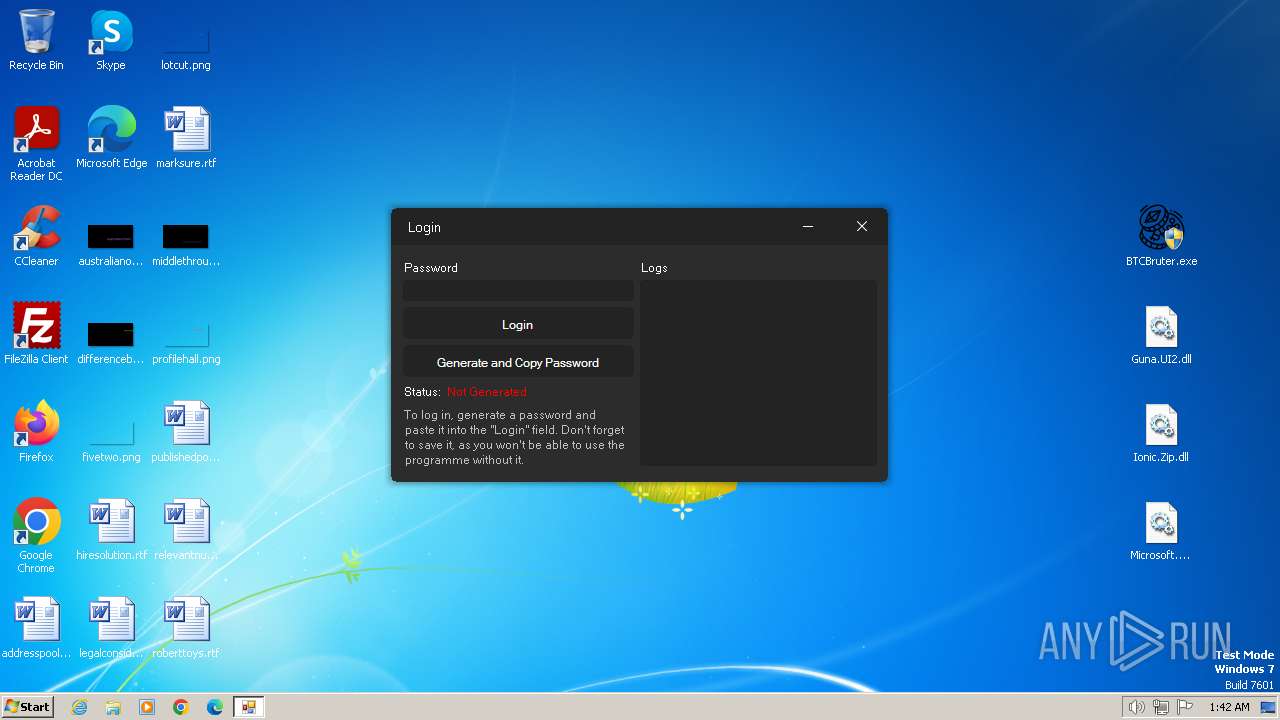
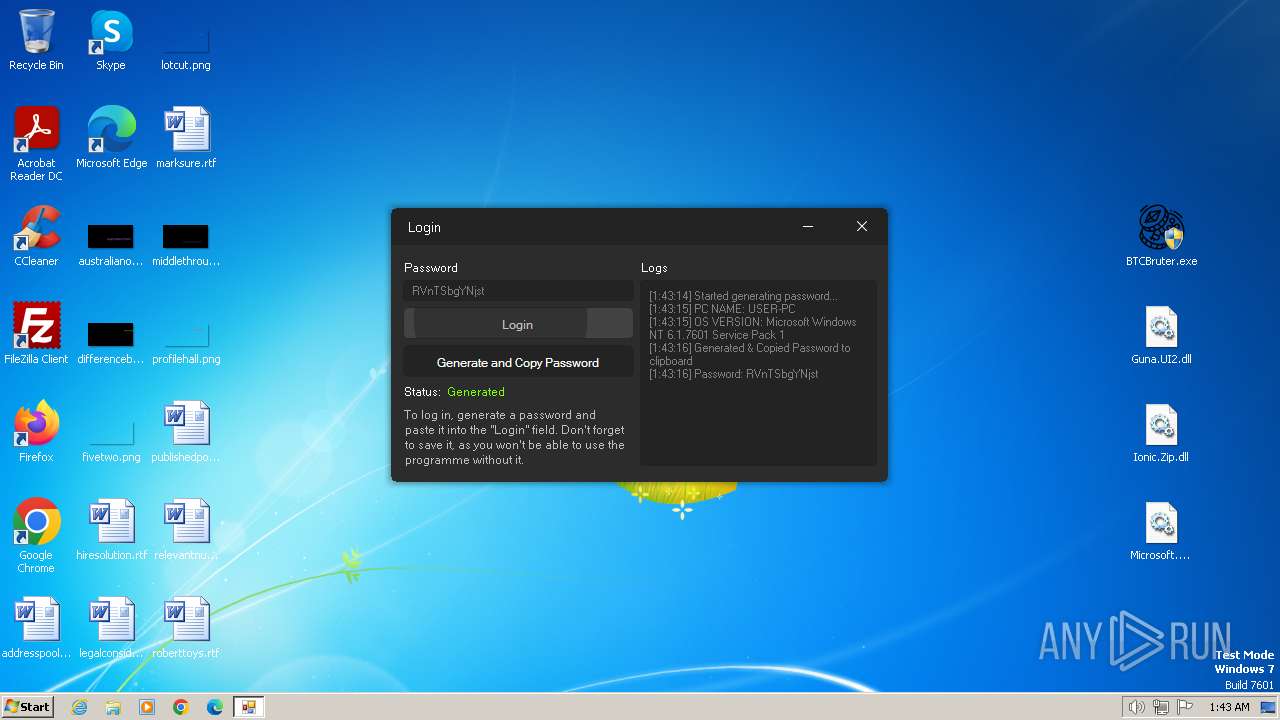
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1384)
- csc.exe (PID: 2672)
- BTCBruter.exe (PID: 2636)
Adds extension to the Windows Defender exclusion list
- BTCBruter.exe (PID: 2636)
Starts Visual C# compiler
- BTCBruter.exe (PID: 2636)
Connects to the CnC server
- PING.EXE (PID: 2168)
LUMMA has been detected (SURICATA)
- PING.EXE (PID: 2168)
SUSPICIOUS
Script adds exclusion extension to Windows Defender
- BTCBruter.exe (PID: 2636)
Reads the Internet Settings
- powershell.exe (PID: 2580)
- BTCBruter.exe (PID: 2636)
- PING.EXE (PID: 2168)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 2580)
Starts POWERSHELL.EXE for commands execution
- BTCBruter.exe (PID: 2636)
Uses .NET C# to load dll
- BTCBruter.exe (PID: 2636)
Executable content was dropped or overwritten
- csc.exe (PID: 2672)
- BTCBruter.exe (PID: 2636)
Reads security settings of Internet Explorer
- BTCBruter.exe (PID: 2636)
Reads settings of System Certificates
- PING.EXE (PID: 2168)
Adds/modifies Windows certificates
- PING.EXE (PID: 2168)
INFO
Checks supported languages
- BTCBruter.exe (PID: 2636)
- csc.exe (PID: 2672)
- cvtres.exe (PID: 1496)
- Update.exe (PID: 3164)
Reads the computer name
- BTCBruter.exe (PID: 2636)
- Update.exe (PID: 3164)
Reads the machine GUID from the registry
- BTCBruter.exe (PID: 2636)
- csc.exe (PID: 2672)
- cvtres.exe (PID: 1496)
- Update.exe (PID: 3164)
Manual execution by a user
- BTCBruter.exe (PID: 2036)
- BTCBruter.exe (PID: 2636)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1384)
Create files in a temporary directory
- BTCBruter.exe (PID: 2636)
- csc.exe (PID: 2672)
- cvtres.exe (PID: 1496)
- PING.EXE (PID: 2168)
Reads the software policy settings
- PING.EXE (PID: 2168)
Checks proxy server information
- PING.EXE (PID: 2168)
Reads security settings of Internet Explorer
- PING.EXE (PID: 2168)
Creates files or folders in the user directory
- PING.EXE (PID: 2168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:09:09 06:24:44 |
| ZipCRC: | 0x33606bc8 |
| ZipCompressedSize: | 1003763 |
| ZipUncompressedSize: | 4003208 |
| ZipFileName: | Guna.UI2.dll |
Total processes
51
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1384 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\bbf2.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1496 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES8BFF.tmp" "c:\Users\admin\AppData\Local\Temp\vphzpxy4\CSC34CFA6A4C8034EF4A129809FD8A9DECA.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\Desktop\BTCBruter.exe" | C:\Users\admin\Desktop\BTCBruter.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: LoginPage Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2168 | "C:\Windows\SYSWOW64\ping.exe" | C:\Windows\System32\PING.EXE | Update.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2580 | "powershell.exe" -command Add-MpPreference -ExclusionExtension '.exe' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | BTCBruter.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2636 | "C:\Users\admin\Desktop\BTCBruter.exe" | C:\Users\admin\Desktop\BTCBruter.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: LoginPage Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2672 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\vphzpxy4\vphzpxy4.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | BTCBruter.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 3164 | "C:\Users\admin\AppData\Local\Temp\Update.exe" | C:\Users\admin\AppData\Local\Temp\Update.exe | — | BTCBruter.exe | |||||||||||
User: admin Company: aMaeAwAP Integrity Level: HIGH Description: OkizoYiIot oauJAlIQeJU AoEFIb EbeFUBevo ODaSeTIyAB ARoGUGu OVAyOaeW ivavAkoEa. Exit code: 0 Version: 8.26.171.74 Modules
| |||||||||||||||
| 3724 | "C:\Windows\SYSWOW64\calc.exe" | C:\Windows\System32\calc.exe | — | Update.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Calculator Exit code: 4294967295 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 925
Read events
15 837
Write events
77
Delete events
11
Modification events
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\bbf2.zip | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
9
Suspicious files
12
Text files
8
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.15560\Guna.UI2.dll | executable | |
MD5:846A7E5993282E220B26B82E7A39A40A | SHA256:5613682635617CD43720807448F69B10090932E8571A358B92361D2A2C7A4597 | |||
| 2168 | PING.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2636 | BTCBruter.exe | C:\Users\admin\AppData\Local\Temp\Update.zip | compressed | |
MD5:3CC7B76FC56B164408B835569B6F1B76 | SHA256:9C682F6376CC2B8818C1F759763B0AA294F6D2BC66038E4FA56C41317B2E9CFE | |||
| 2580 | powershell.exe | C:\Users\admin\AppData\Local\Temp\rlpnq50g.saa.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2580 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.15560\Ionic.Zip.dll | executable | |
MD5:6DED8FCBF5F1D9E422B327CA51625E24 | SHA256:3B3E541682E48F3FD2872F85A06278DA2F3E7877EE956DA89B90D732A1EAA0BD | |||
| 2636 | BTCBruter.exe | C:\Users\admin\AppData\Local\Temp\vphzpxy4\vphzpxy4.cmdline | text | |
MD5:71521579DE802DE1AFDCA70C640C6BE3 | SHA256:3E97FA5A10500529BAD525BB25FBFEC69F28A4EAF7020FA3B28D64FE1FBA4292 | |||
| 1384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1384.15560\BTCBruter.exe | executable | |
MD5:4B3B43353F794CFC488C1FAC504AB9F3 | SHA256:4264B83B4F4349664BFD3CF276C5E8308DFAA914652A415788106597A64408D0 | |||
| 2672 | csc.exe | C:\Users\admin\AppData\Local\Temp\vphzpxy4\vphzpxy4.exe | executable | |
MD5:8926F00B78184A46DD864486C92648B6 | SHA256:522FEFCBA10FF06F9E2FC5AA947E2DECDACE48C67E4DE4F1998645109145F992 | |||
| 2580 | powershell.exe | C:\Users\admin\AppData\Local\Temp\c2feaqkq.gu5.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
10
DNS requests
12
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2168 | PING.EXE | POST | 200 | 104.21.13.74:80 | http://zamesblack.fun/api | unknown | html | 4.62 Kb | unknown |
2168 | PING.EXE | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?51ee1f964119b966 | unknown | — | — | unknown |
2168 | PING.EXE | POST | 302 | 104.21.13.74:80 | http://zamesblack.fun/api | unknown | — | — | unknown |
2168 | PING.EXE | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d123ac630b302fcd | unknown | compressed | 65.2 Kb | unknown |
2168 | PING.EXE | GET | 200 | 2.19.105.18:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2168 | PING.EXE | GET | 200 | 23.192.153.142:80 | http://x2.c.lencr.org/ | unknown | binary | 299 b | unknown |
2168 | PING.EXE | GET | 302 | 104.21.13.74:80 | http://zamesblack.fun/api | unknown | — | — | unknown |
2168 | PING.EXE | GET | 302 | 104.21.13.74:80 | http://zamesblack.fun/api | unknown | — | — | unknown |
2168 | PING.EXE | GET | 302 | 104.21.13.74:80 | http://zamesblack.fun/api | unknown | — | — | unknown |
2168 | PING.EXE | GET | 302 | 104.21.13.74:80 | http://zamesblack.fun/api | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2168 | PING.EXE | 104.21.13.74:80 | zamesblack.fun | CLOUDFLARENET | — | unknown |
2168 | PING.EXE | 104.21.13.74:443 | zamesblack.fun | CLOUDFLARENET | — | unknown |
2168 | PING.EXE | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2168 | PING.EXE | 2.19.105.18:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2168 | PING.EXE | 23.192.153.142:80 | x2.c.lencr.org | AKAMAI-AS | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
alosevera.fun |
| unknown |
bluepablo.fun |
| unknown |
howlcars.fun |
| unknown |
comperssw.fun |
| unknown |
duhodown.fun |
| unknown |
kowersize.fun |
| unknown |
mouseoiet.fun |
| unknown |
plengreg.fun |
| unknown |
zamesblack.fun |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | PING.EXE | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
2168 | PING.EXE | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Win32/Lumma Stealer Check-In |
2168 | PING.EXE | Malware Command and Control Activity Detected | ET MALWARE [ANY.RUN] Win32/Lumma Stealer Check-In |