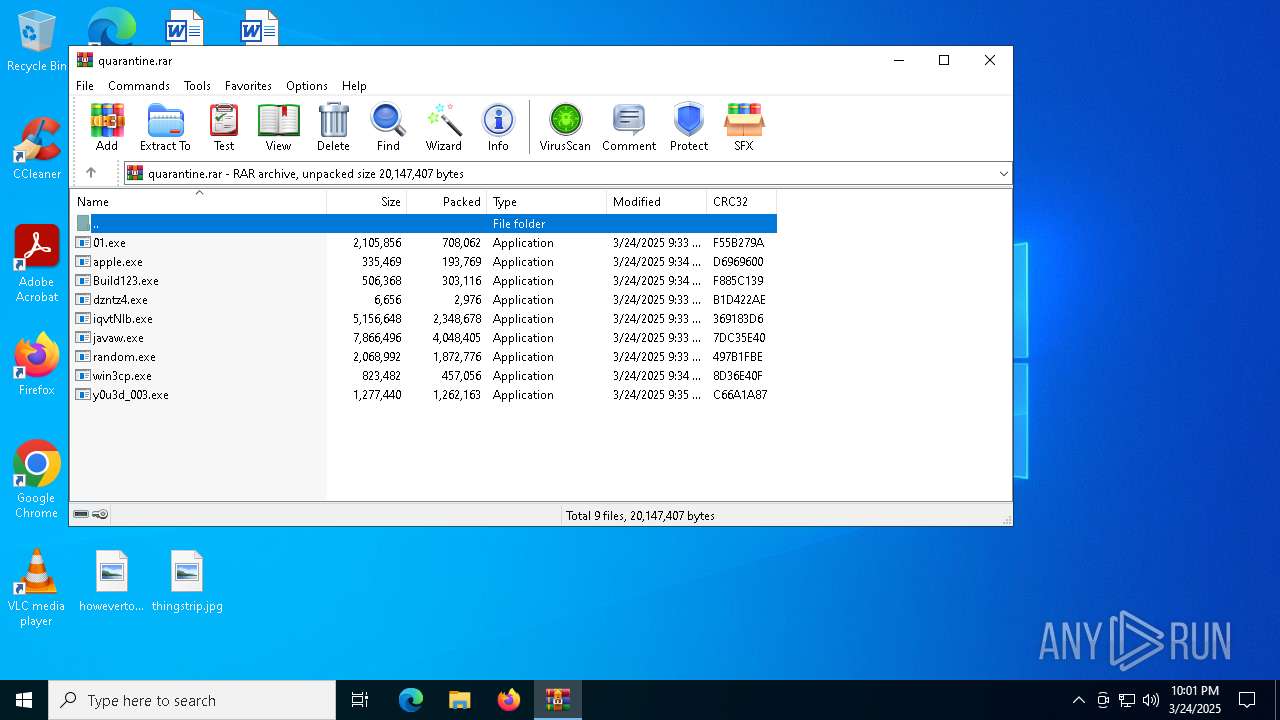
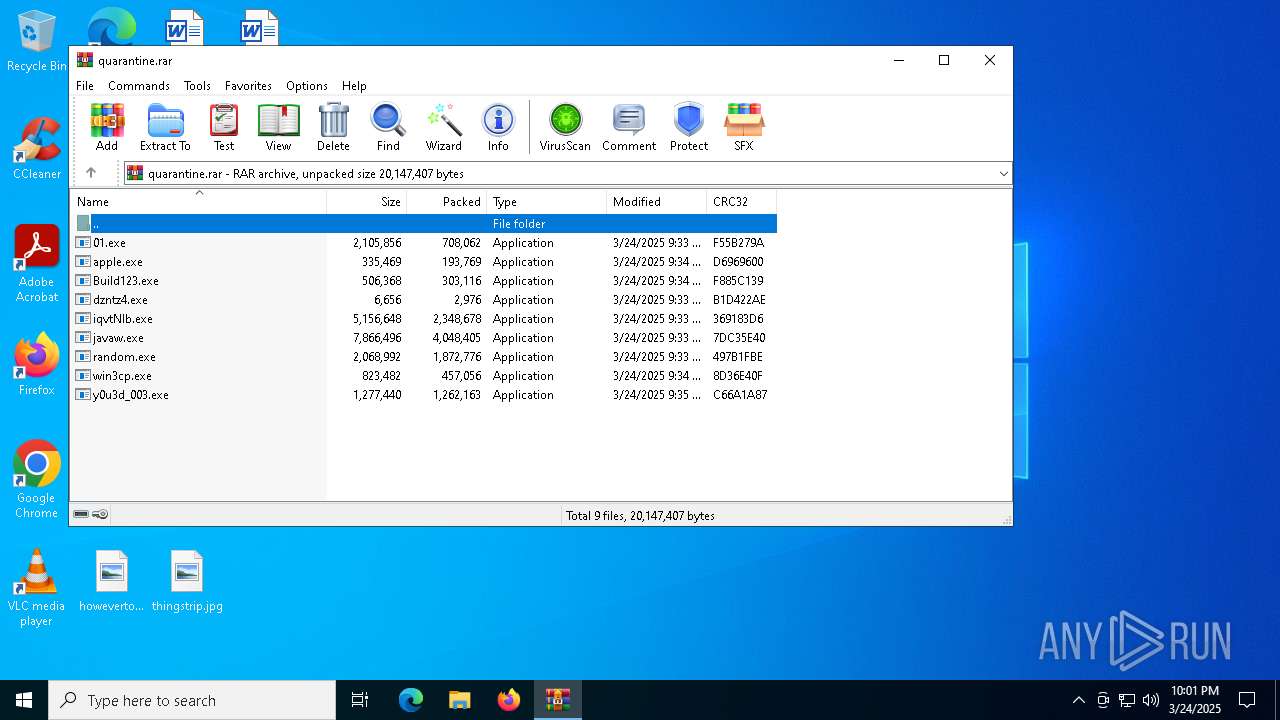
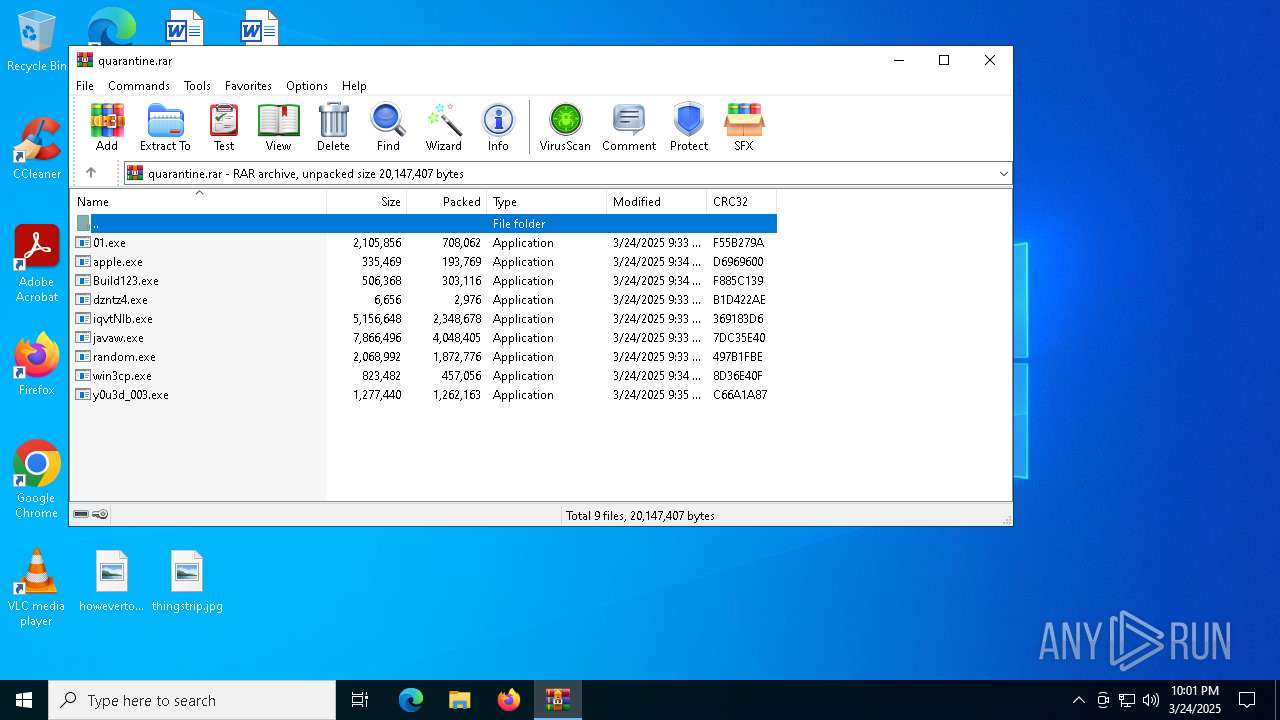
| File name: | quarantine.rar |
| Full analysis: | https://app.any.run/tasks/7bdce5af-139b-4a30-a75c-623250ee20a1 |
| Verdict: | Malicious activity |
| Threats: | DarkVision RAT is a low-cost, modular Remote Access Trojan that gives attackers remote control of infected Windows hosts. Initially observed around 2020 and sold in underground marketplaces, DarkVision has become notable for its full feature set (keylogging, screen capture, file theft, remote command execution and plugin support) and for being distributed via multi-stage loaders in recent campaigns. |
| Analysis date: | March 24, 2025, 22:01:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C2DC35CAB75A8A4F8A37061EA82B6C91 |
| SHA1: | D9292DD2D7292C2DA9083154F99405C3E15705A4 |
| SHA256: | 3A4BF2BAD23AD4C4E276F5AD5F3A6EDF0AA63EEBE3355AD05687913A16A5D823 |
| SSDEEP: | 98304:KCOBUxYdCImp9hh8ou9amfm8h+r7mbinKuxZKY6BjvPlVsbVJsc4mXDreUNEerz3:bPBSJjhHGKbJYIsXWIZtn7Uk |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7572)
GENERIC has been found (auto)
- apple.exe (PID: 7784)
Uses Task Scheduler to run other applications
- 01.exe (PID: 8100)
Starts SC.EXE for service management
- cmd.exe (PID: 8028)
Changes the autorun value in the registry
- svchost.exe (PID: 7300)
Connects to the CnC server
- svchost.exe (PID: 7300)
Actions looks like stealing of personal data
- random.exe (PID: 6540)
DARKVISION has been detected (SURICATA)
- svchost.exe (PID: 7300)
LUMMA mutex has been found
- random.exe (PID: 6540)
Adds path to the Windows Defender exclusion list
- mmc.exe (PID: 6264)
Changes Windows Defender settings
- mmc.exe (PID: 6264)
[YARA] DarkVision RAT is detected
- svchost.exe (PID: 7300)
SUSPICIOUS
Executing commands from a ".bat" file
- 11.exe (PID: 7844)
- 11.exe (PID: 7952)
- svchost.exe (PID: 7300)
Reads security settings of Internet Explorer
- 11.exe (PID: 7844)
- 11.exe (PID: 7952)
- apple.exe (PID: 7784)
Executable content was dropped or overwritten
- apple.exe (PID: 7784)
- 01.exe (PID: 8100)
- svchost.exe (PID: 7300)
- mmc.exe (PID: 6264)
Drops a system driver (possible attempt to evade defenses)
- apple.exe (PID: 7784)
- mmc.exe (PID: 6264)
Starts CMD.EXE for commands execution
- 11.exe (PID: 7952)
- 11.exe (PID: 7844)
- svchost.exe (PID: 7300)
Creates a new Windows service
- sc.exe (PID: 8092)
Uses TASKKILL.EXE to kill process
- 01.exe (PID: 8100)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 8028)
Windows service management via SC.EXE
- sc.exe (PID: 8144)
- sc.exe (PID: 7368)
- sc.exe (PID: 780)
- sc.exe (PID: 3888)
- sc.exe (PID: 1280)
- sc.exe (PID: 1180)
- sc.exe (PID: 1052)
- sc.exe (PID: 7280)
- sc.exe (PID: 7376)
- sc.exe (PID: 6248)
- sc.exe (PID: 7680)
- sc.exe (PID: 7732)
- sc.exe (PID: 6708)
- sc.exe (PID: 7864)
- sc.exe (PID: 7904)
- sc.exe (PID: 8096)
- sc.exe (PID: 8020)
- sc.exe (PID: 640)
- sc.exe (PID: 7244)
Stops a currently running service
- sc.exe (PID: 6108)
- sc.exe (PID: 5056)
- sc.exe (PID: 2236)
- sc.exe (PID: 6768)
- sc.exe (PID: 5392)
- sc.exe (PID: 7412)
- sc.exe (PID: 7528)
- sc.exe (PID: 7324)
- sc.exe (PID: 5868)
- sc.exe (PID: 7796)
- sc.exe (PID: 7700)
- sc.exe (PID: 7772)
- sc.exe (PID: 7944)
- sc.exe (PID: 7896)
- sc.exe (PID: 8048)
- sc.exe (PID: 5668)
- sc.exe (PID: 3268)
- sc.exe (PID: 6184)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 8028)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 8028)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8028)
Starts SC.EXE for service management
- cmd.exe (PID: 8028)
Starts a Microsoft application from unusual location
- y0u3d_003.exe (PID: 1676)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7184)
- schtasks.exe (PID: 5864)
- schtasks.exe (PID: 1348)
- schtasks.exe (PID: 4880)
Potential Corporate Privacy Violation
- svchost.exe (PID: 7300)
Checks for external IP
- svchost.exe (PID: 2196)
- busdrv.exe (PID: 7364)
- busdrv.exe (PID: 6768)
- busdrv.exe (PID: 5392)
- svchost.exe (PID: 2172)
Connects to the server without a host name
- svchost.exe (PID: 7300)
- mmc.exe (PID: 6264)
The process executes via Task Scheduler
- busdrv.exe (PID: 6768)
- PLUGScheduler.exe (PID: 4128)
- busdrv.exe (PID: 5392)
Reads the BIOS version
- random.exe (PID: 6540)
Searches for installed software
- random.exe (PID: 6540)
Starts POWERSHELL.EXE for commands execution
- mmc.exe (PID: 6264)
Script adds exclusion path to Windows Defender
- mmc.exe (PID: 6264)
Creates or modifies Windows services
- mmc.exe (PID: 6264)
Executes application which crashes
- dzntz4.exe (PID: 2140)
INFO
Reads the computer name
- apple.exe (PID: 7784)
- 11.exe (PID: 7952)
- 11.exe (PID: 7844)
- y0u3d_003.exe (PID: 1676)
- dzntz4.exe (PID: 2140)
- busdrv.exe (PID: 7364)
- busdrv.exe (PID: 6768)
- random.exe (PID: 6540)
- tzutil.exe (PID: 7316)
- w32tm.exe (PID: 2564)
Manual execution by a user
- apple.exe (PID: 7736)
- apple.exe (PID: 7784)
- 01.exe (PID: 8100)
- y0u3d_003.exe (PID: 1676)
- busdrv.exe (PID: 7364)
- dzntz4.exe (PID: 2140)
- random.exe (PID: 6540)
Create files in a temporary directory
- 11.exe (PID: 7952)
- apple.exe (PID: 7784)
- 11.exe (PID: 7844)
- svchost.exe (PID: 7300)
- w32tm.exe (PID: 2564)
Checks supported languages
- 11.exe (PID: 7952)
- apple.exe (PID: 7784)
- 01.exe (PID: 8100)
- 11.exe (PID: 7844)
- busdrv.exe (PID: 7364)
- dzntz4.exe (PID: 2140)
- busdrv.exe (PID: 6768)
- y0u3d_003.exe (PID: 1676)
- random.exe (PID: 6540)
- w32tm.exe (PID: 2564)
- tzutil.exe (PID: 7316)
- PLUGScheduler.exe (PID: 4128)
- busdrv.exe (PID: 5392)
Process checks computer location settings
- apple.exe (PID: 7784)
- 11.exe (PID: 7952)
- 11.exe (PID: 7844)
Autorun file from Task Scheduler
- 01.exe (PID: 8100)
Creates files in the program directory
- y0u3d_003.exe (PID: 1676)
- svchost.exe (PID: 7300)
- powershell.exe (PID: 664)
Checks proxy server information
- busdrv.exe (PID: 7364)
- busdrv.exe (PID: 6768)
- busdrv.exe (PID: 5392)
The sample compiled with english language support
- svchost.exe (PID: 7300)
Reads the machine GUID from the registry
- dzntz4.exe (PID: 2140)
- random.exe (PID: 6540)
- w32tm.exe (PID: 2564)
Reads the software policy settings
- random.exe (PID: 6540)
Creates files or folders in the user directory
- WerFault.exe (PID: 5640)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 664)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 664)
Reads security settings of Internet Explorer
- svchost.exe (PID: 7300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 4048405 |
| UncompressedSize: | 7866496 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | javaw.exe |
Total processes
345
Monitored processes
97
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | timeout /t 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | sc delete "MsSecCore" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | powershell Add-MpPreference -ExclusionPath C:\ | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | mmc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | sc delete "WinDefend" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | sc delete "wscsvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | sc delete "Sense" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | sc delete "WdNisSvc" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | schtasks /Delete /TN "Microsoft\Windows\Windows Defender\Windows Defender Verification" /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | reg delete "HKLM\System\CurrentControlset\Services\SecurityHealthService" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | "C:\Users\admin\Desktop\y0u3d_003.exe" | C:\Users\admin\Desktop\y0u3d_003.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ProQuota Exit code: 0 Version: 10.0.22621.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 095
Read events
22 072
Write events
23
Delete events
0
Modification events
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\quarantine.rar | |||
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7572) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7300) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | {57F06FF0-B2D5-45F3-BFEE-970F76E38EFD} |
Value: C:\ProgramData\{A332F586-BC6E-46FF-BB3B-A67E49F41010}\aitstatic.exe {1CF6DD21-C538-4D1C-883F-AD3AF450FA11} | |||
| (PID) Process: | (7300) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\{C4D0194B-9AE4-494F-9114-56C8BEACC6F4} |
| Operation: | write | Name: | {C4D0194B-9AE4-494F-9114-56C8BEACC6F4} |
Value: 0000000001000000010000000100000000000000000000000000000068007400740070003A002F002F003100300037002E003100370034002E003100390032002E003100370039002F0064006100740061002F00300030003300000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B00340032003500460037003800340045002D0039003200310041002D0034004300430030002D0041004500380037002D003000360041003300420030003300390033004100300045007D000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000074007A007500740069006C002E00650078006500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000020000000100000002000000000000000000000000000000680074007400700073003A002F002F0067007200610062006900660079002E006C0069006E006B002F005A0041005400460051004F000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B00340032003500460037003800340045002D0039003200310041002D0034004300430030002D0041004500380037002D003000360041003300420030003300390033004100300045007D00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007300650074002E0062006100740000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000010000000200000000000000000000000000000068007400740070003A002F002F003100300037002E003100370034002E003100390032002E003100370039002F0063006C00650061006E00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000007B00340032003500460037003800340045002D0039003200310041002D0034004300430030002D0041004500380037002D003000360041003300420030003300390033004100300045007D000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000077003300320074006D002E00650078006500000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
6
Suspicious files
47
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5640 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_dzntz4.exe_aee15124ce96fc9c65fc7ea7e14fe4c9f4fdb420_6a7c928b_49a175b8-f11b-4403-9c5c-54227a0b41c9\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5640 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\dzntz4.exe.2140.dmp | — | |
MD5:— | SHA256:— | |||
| 7784 | apple.exe | C:\Users\admin\AppData\Local\Temp\11.exe | executable | |
MD5:89CCC29850F1881F860E9FD846865CAD | SHA256:E163DCA9890DD778CE4C413E6C5A10340AEBBCDFFC1CC4FBD42F54942B302DD1 | |||
| 7784 | apple.exe | C:\Users\admin\AppData\Local\Temp\ssisd.sys | executable | |
MD5:B69F744F56196978A2F9493F7DCB6765 | SHA256:38907D224AC0DF6DDB5EB115998CC0BE9FFDAE237F9B61C39DDAEDA812D5160D | |||
| 5640 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERECE2.tmp.dmp | binary | |
MD5:F4FBF936F5DAD5FE8E12399C1AB63F35 | SHA256:96B4405A6C5ED54C66F109C3335A13641CA44D945383E6B1FA9FB8518E407BD1 | |||
| 7952 | 11.exe | C:\Users\admin\AppData\Local\Temp\D563.tmp\D564.tmp\D565.bat | text | |
MD5:E5DDB7A24424818E3B38821CC50EE6FD | SHA256:4734305286027757086EF56B9033319EC92C3756E3CA41D7BF22C631D392E1EA | |||
| 7844 | 11.exe | C:\Users\admin\AppData\Local\Temp\D449.tmp\D44A.tmp\D44B.bat | text | |
MD5:E5DDB7A24424818E3B38821CC50EE6FD | SHA256:4734305286027757086EF56B9033319EC92C3756E3CA41D7BF22C631D392E1EA | |||
| 7300 | svchost.exe | C:\Users\admin\AppData\Local\Temp\{425F784E-921A-4CC0-AE87-06A3B0393A0E}\w32tm.exe | executable | |
MD5:15BDC4BD67925EF33B926843B3B8154B | SHA256:4F0B2C61BCCFD9AA3DB301EE4E15607DF41DED533757DE34C986A0FF25B6246D | |||
| 664 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2ipadteo.yma.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7300 | svchost.exe | C:\Users\admin\AppData\Local\Temp\{425F784E-921A-4CC0-AE87-06A3B0393A0E}\set.bat | image | |
MD5:77D9AB6E61CF9928494530BE8ED5D80D | SHA256:0324BA4D164702B4020EC6BF79CFBFA93E9A635234085E96888854B173735CBC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
314
TCP/UDP connections
57
DNS requests
13
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7300 | svchost.exe | GET | 200 | 107.174.192.179:80 | http://107.174.192.179/data/003 | unknown | — | — | unknown |
7364 | busdrv.exe | GET | 200 | 208.95.112.1:80 | http://208.95.112.1:80/json/ | unknown | — | — | unknown |
2432 | RUXIMICS.exe | GET | 200 | 2.16.168.200:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6768 | busdrv.exe | GET | 200 | 208.95.112.1:80 | http://208.95.112.1:80/json/ | unknown | — | — | unknown |
7300 | svchost.exe | GET | 200 | 107.174.192.179:80 | http://107.174.192.179/clean | unknown | — | — | unknown |
— | — | HEAD | 206 | 46.8.206.115:443 | https://devbuilds.s.kaspersky-labs.com/devbuilds/KVRT/latest/full/KVRT.exe | unknown | — | — | unknown |
6264 | mmc.exe | HEAD | 206 | 104.168.28.10:80 | http://104.168.28.10/003/01/d1 | unknown | — | — | malicious |
6264 | mmc.exe | GET | 206 | 104.168.28.10:80 | http://104.168.28.10/003/01/d1 | unknown | — | — | malicious |
6264 | mmc.exe | GET | 206 | 104.168.28.10:80 | http://104.168.28.10/003/01/d1 | unknown | — | — | malicious |
6264 | mmc.exe | GET | 206 | 104.168.28.10:80 | http://104.168.28.10/003/01/d1 | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2432 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2432 | RUXIMICS.exe | 2.16.168.200:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
7300 | svchost.exe | 107.174.192.179:80 | — | AS-COLOCROSSING | US | unknown |
7364 | busdrv.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
6768 | busdrv.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
7300 | svchost.exe | 104.26.9.202:443 | grabify.link | CLOUDFLARENET | US | whitelisted |
7300 | svchost.exe | 82.29.67.160:443 | — | Virgin Media Limited | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ip-api.com |
| whitelisted |
grabify.link |
| whitelisted |
fluffycqomfort.world |
| unknown |
devbuilds.s.kaspersky-labs.com |
| unknown |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
7364 | busdrv.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7300 | svchost.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7300 | svchost.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
6768 | busdrv.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
7300 | svchost.exe | Potentially Bad Traffic | ET INFO Observed IP Tracking Domain (grabify .link in TLS SNI) |
7300 | svchost.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkVision Check-in |
7300 | svchost.exe | A Network Trojan was detected | ET MALWARE Win32/DarkVision RAT CnC Checkin M1 |
— | — | A Network Trojan was detected | ET MALWARE Win32/DarkVision RAT CnC Checkin M1 |