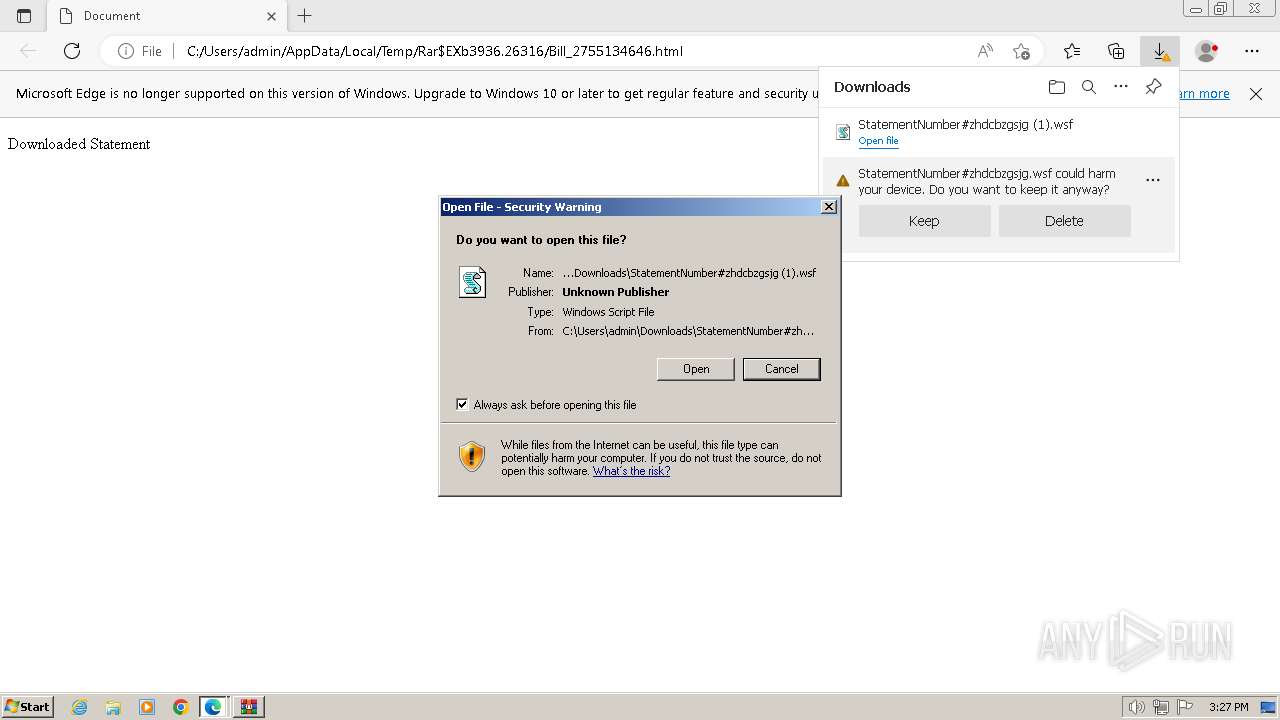
| File name: | Bill_2755134646.html (1).zip |
| Full analysis: | https://app.any.run/tasks/0954edab-541a-4bd8-8cf0-e498ceaba65b |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 16, 2024, 15:26:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 8EB23E80AF0747DA1A19ED95421A6EC4 |
| SHA1: | 1D5FA68D1CB13DC146ED8626462978FB79884ADF |
| SHA256: | 39D5E3C50B28CCFEFE68C2EB1A178CC7000F557C9C377327E5A642E4CC1BF70F |
| SSDEEP: | 384:2QwhpU1z8GrjnR+rsTXisneExiUTulFzN9mv:v1z8G/crsTSsbxiGWg |
MALICIOUS
Probably downloads file via BitsAdmin
- powershell.exe (PID: 3416)
Unusual connection from system programs
- wscript.exe (PID: 3020)
Bypass execution policy to execute commands
- powershell.exe (PID: 3200)
- powershell.exe (PID: 2560)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 2820)
- cmd.exe (PID: 2724)
Creates a new scheduled task (SCRIPT)
- powershell.exe (PID: 1864)
ASYNCRAT has been detected (MUTEX)
- aspnet_compiler.exe (PID: 1092)
- aspnet_compiler.exe (PID: 3192)
Actions looks like stealing of personal data
- aspnet_compiler.exe (PID: 1092)
ASYNCRAT has been detected (SURICATA)
- aspnet_compiler.exe (PID: 1092)
ASYNCRAT has been detected (YARA)
- aspnet_compiler.exe (PID: 1092)
Extracts files to directory (POWERSHELL)
- wscript.exe (PID: 3020)
SUSPICIOUS
The process executes JS scripts
- cmd.exe (PID: 3708)
- cmd.exe (PID: 864)
Likely accesses (executes) a file from the Public directory
- wscript.exe (PID: 1196)
- wscript.exe (PID: 3904)
- powershell.exe (PID: 3416)
- cmd.exe (PID: 2820)
- cmd.exe (PID: 864)
- wscript.exe (PID: 4008)
- cmd.exe (PID: 2724)
- powershell.exe (PID: 1864)
- powershell.exe (PID: 3200)
- powershell.exe (PID: 2560)
- cmd.exe (PID: 3708)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 3020)
- cmd.exe (PID: 2820)
- cmd.exe (PID: 2724)
- cmd.exe (PID: 864)
Reads the Internet Settings
- wscript.exe (PID: 3020)
- powershell.exe (PID: 3416)
- wscript.exe (PID: 1196)
- wscript.exe (PID: 3904)
- wscript.exe (PID: 4008)
- aspnet_compiler.exe (PID: 1092)
- cmd.exe (PID: 3708)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3020)
Executing commands from a ".bat" file
- wscript.exe (PID: 1196)
- wscript.exe (PID: 3904)
- wscript.exe (PID: 4008)
- wscript.exe (PID: 3020)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1196)
- wscript.exe (PID: 3904)
- wscript.exe (PID: 4008)
- wscript.exe (PID: 3020)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3904)
- wscript.exe (PID: 1196)
- wscript.exe (PID: 4008)
- wscript.exe (PID: 3020)
The process executes Powershell scripts
- cmd.exe (PID: 2820)
- cmd.exe (PID: 2724)
Extracts substring from string (POWERSHELL)
- powershell.exe (PID: 3200)
- powershell.exe (PID: 2560)
Gets context to manipulate scheduled tasks (SCRIPT)
- powershell.exe (PID: 1864)
Creates a scheduled task using COM
- powershell.exe (PID: 1864)
Converts data to Integer (POWERSHELL)
- powershell.exe (PID: 3200)
- powershell.exe (PID: 2560)
Reads settings of System Certificates
- aspnet_compiler.exe (PID: 1092)
Gets a folder of registered tasks (SCRIPT)
- powershell.exe (PID: 1864)
Connects to unusual port
- aspnet_compiler.exe (PID: 1092)
INFO
The process uses the downloaded file
- msedge.exe (PID: 2740)
- msedge.exe (PID: 3276)
Application launched itself
- msedge.exe (PID: 3276)
Checks proxy server information
- wscript.exe (PID: 3020)
Encodes string to ASCII (POWERSHELL)
- powershell.exe (PID: 3200)
- powershell.exe (PID: 2560)
Reads the machine GUID from the registry
- aspnet_compiler.exe (PID: 1092)
- aspnet_compiler.exe (PID: 3192)
Reads the software policy settings
- aspnet_compiler.exe (PID: 1092)
Reads the computer name
- aspnet_compiler.exe (PID: 3192)
- aspnet_compiler.exe (PID: 1092)
Reads Environment values
- aspnet_compiler.exe (PID: 1092)
Checks supported languages
- aspnet_compiler.exe (PID: 1092)
- aspnet_compiler.exe (PID: 3192)
Create files in a temporary directory
- aspnet_compiler.exe (PID: 1092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(1092) aspnet_compiler.exe
C2 (1)hassan.webhop.net
Ports (1)5055
BotnetNew
VersionAWS | 3Losh
Options
AutoRunfalse
MutexAsyncMutex_alosh
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureDBW+nY08DS9GPYky3emWfG3X2UfcshlDvMGAnJmP7DurO1GljnVBIlbwq7kvt5fr0vxhkjRqf3v7vQ/yFEoec50URlUcrxGhe2D0mBuHtq7p/hVazL7ZgQy115iH4S7XU0xKF7ma1mH/ClIqqfqs7CMNt+GWuCpTOCxHw2et3mDMEKfL4jg2BRvsrjAhMbBsUpgCJFHdVi2fp6O3D7N3qzyybqu66Tz6Tacmk3YhyMsEBs9LziKqfPIktuW5LBdNls/KkH6W+/2kNC6rliYQkV8f3jQdhT7jcmLBIFB2fYK/...
Keys
AES3ba19f5745707765622685da09069cc136aa4bab50332d61ed039d571eac5931
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:03:12 05:53:58 |
| ZipCRC: | 0x7b81fa60 |
| ZipCompressedSize: | 9869 |
| ZipUncompressedSize: | 34410 |
| ZipFileName: | Bill_2755134646.html |
Total processes
78
Monitored processes
35
Malicious processes
14
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4364 --field-trial-handle=1352,i,14259957167152711850,793287415789943488,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 128 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --mojo-platform-channel-handle=3868 --field-trial-handle=1352,i,14259957167152711850,793287415789943488,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1656 --field-trial-handle=1352,i,14259957167152711850,793287415789943488,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 864 | C:\Windows\system32\cmd.exe /c ""C:\Users\Public\node.bat" C:\Users\Public\" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 948 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4240 --field-trial-handle=1352,i,14259957167152711850,793287415789943488,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1092 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_compiler.exe Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
AsyncRat(PID) Process(1092) aspnet_compiler.exe C2 (1)hassan.webhop.net Ports (1)5055 BotnetNew VersionAWS | 3Losh Options AutoRunfalse MutexAsyncMutex_alosh InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva... Server_SignatureDBW+nY08DS9GPYky3emWfG3X2UfcshlDvMGAnJmP7DurO1GljnVBIlbwq7kvt5fr0vxhkjRqf3v7vQ/yFEoec50URlUcrxGhe2D0mBuHtq7p/hVazL7ZgQy115iH4S7XU0xKF7ma1mH/ClIqqfqs7CMNt+GWuCpTOCxHw2et3mDMEKfL4jg2BRvsrjAhMbBsUpgCJFHdVi2fp6O3D7N3qzyybqu66Tz6Tacmk3YhyMsEBs9LziKqfPIktuW5LBdNls/KkH6W+/2kNC6rliYQkV8f3jQdhT7jcmLBIFB2fYK/... Keys AES3ba19f5745707765622685da09069cc136aa4bab50332d61ed039d571eac5931 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 1196 | "C:\Windows\System32\WScript.exe" "C:\Users\Public\app.js" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1544 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3424 --field-trial-handle=1352,i,14259957167152711850,793287415789943488,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2352 --field-trial-handle=1352,i,14259957167152711850,793287415789943488,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1656 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1328 --field-trial-handle=1352,i,14259957167152711850,793287415789943488,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
31 805
Read events
31 617
Write events
176
Delete events
12
Modification events
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Bill_2755134646.html (1).zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
27
Text files
71
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF186bb5.TMP | — | |
MD5:— | SHA256:— | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF186bd4.TMP | — | |
MD5:— | SHA256:— | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF186be4.TMP | — | |
MD5:— | SHA256:— | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF186c22.TMP | — | |
MD5:— | SHA256:— | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3960 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\CrashpadMetrics.pma | binary | |
MD5:886E82F2CA62ECCCE64601B30592078A | SHA256:E5E13D53601100FF3D6BB71514CBCCC4C73FE9B7EF5E930100E644187B42948E | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
| 3276 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:72265FBF816F9AAE473C0CEB421DE724 | SHA256:C549BD4A176A3744A5D91391D311E28F0503BB69213E38835A1CB213038D938C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
17
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3020 | wscript.exe | GET | 200 | 37.1.211.139:80 | http://transfers.ath.cx/2222/g4.txt | unknown | text | 665 b | unknown |
856 | svchost.exe | HEAD | 200 | 37.1.211.139:80 | http://transfers.ath.cx/2222/kkk.jpg | unknown | — | — | unknown |
856 | svchost.exe | GET | 200 | 37.1.211.139:80 | http://transfers.ath.cx/2222/kkk.jpg | unknown | compressed | 111 Kb | unknown |
1092 | aspnet_compiler.exe | GET | 200 | 2.19.198.57:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?04114ebd06f1fcc9 | unknown | compressed | 67.5 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2372 | msedge.exe | 13.107.22.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3276 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
2372 | msedge.exe | 52.123.243.221:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3276 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
2372 | msedge.exe | 131.253.33.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2372 | msedge.exe | 152.199.21.175:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | EDGECAST | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
transfers.ath.cx |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
hassan.webhop.net |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to ath .cx Domain |
3020 | wscript.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.ath .cx Domain |
— | — | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.ath .cx Domain |
856 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS HTTP Request to a *.ath .cx Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.webhop .net Domain |
1092 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
1092 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
1092 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
1092 | aspnet_compiler.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |