| File name: | SubSeven S.A.T 1.0.7.rar |
| Full analysis: | https://app.any.run/tasks/9185cc1b-e527-4a0b-9964-6a089e8d236c |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | March 10, 2019, 19:03:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B85AEA526843A6CCB23D8A25E2859095 |
| SHA1: | 656F8A2D9F95D199EBBD6EC7C695590816A05069 |
| SHA256: | 39CF91175D8AB9B6DB693FBDDD845ADE6AD14EF5BFC5432DBE92CC5971CEFCEE |
| SSDEEP: | 6144:oMNm6dAruZW6m4uo1WYBkCk9hrHcKjEtZSLKTE8Lr/4JwjNpLrQlqcS5OmP:o4m6OHSkCk3vjEtcOThLb4ANpLTBOmP |
MALICIOUS
Application was dropped or rewritten from another process
- SubSeven S.A.T 1.0.7.exe (PID: 3016)
QUASAR was detected
- SubSeven S.A.T 1.0.7.exe (PID: 3016)
Stealing of credential data
- SubSeven S.A.T 1.0.7.exe (PID: 3016)
Connects to CnC server
- SubSeven S.A.T 1.0.7.exe (PID: 3016)
Actions looks like stealing of personal data
- SubSeven S.A.T 1.0.7.exe (PID: 3016)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2696)
Reads Environment values
- SubSeven S.A.T 1.0.7.exe (PID: 3016)
Reads the cookies of Google Chrome
- SubSeven S.A.T 1.0.7.exe (PID: 3016)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3796)
Creates files in the user directory
- WINWORD.EXE (PID: 3796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
32
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2696 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SubSeven S.A.T 1.0.7.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2696.12905\SubSeven S.A.T 1.0.7\SubSeven S.A.T 1.0.7.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2696.12905\SubSeven S.A.T 1.0.7\SubSeven S.A.T 1.0.7.exe | WinRAR.exe | ||||||||||||
User: admin Company: SubSeven Inc. Integrity Level: MEDIUM Description: SubSeven S.A.T 1.0.7 Exit code: 0 Version: 1.0.7 Modules
| |||||||||||||||
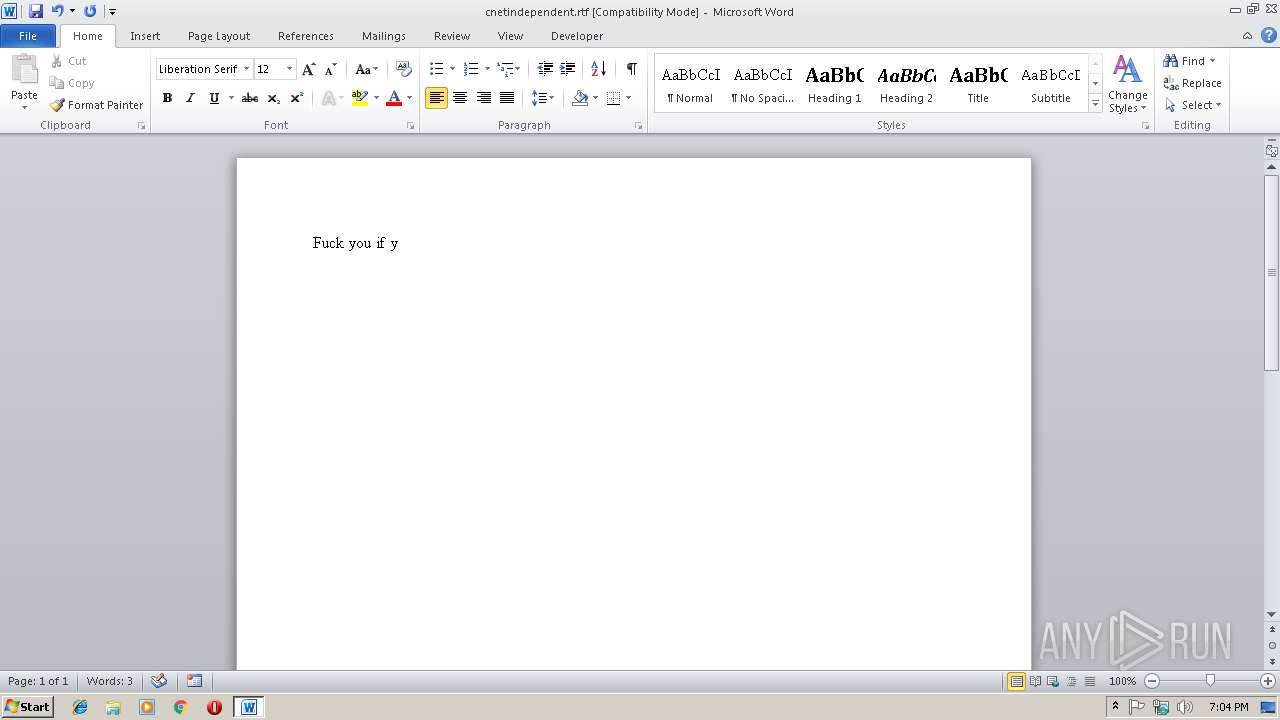
| 3796 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\cnetindependent.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 077
Read events
988
Write events
83
Delete events
6
Modification events
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SubSeven S.A.T 1.0.7.rar | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2696) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
1
Text files
14
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3796 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR31A0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2696.12905\SubSeven S.A.T 1.0.7\Configuration\FileSearcher.ini | text | |
MD5:075AE3D2FC31640504F814F60E5EF713 | SHA256:17EB3C0168D0D7B21EDE5481150F17233427D89833EC121B4DBC4FB96CFAB71E | |||
| 3796 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\cnetindependent.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3796 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3796 | WINWORD.EXE | C:\Users\admin\Desktop\~$etindependent.rtf | pgc | |
MD5:— | SHA256:— | |||
| 2696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2696.12905\SubSeven S.A.T 1.0.7\Configuration\LoginRememberMe.ini | text | |
MD5:68934A3E9455FA72420237EB05902327 | SHA256:FCBCF165908DD18A9E49F7FF27810176DB8E9F63B4352213741664245224F8AA | |||
| 2696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2696.12905\SubSeven S.A.T 1.0.7\Configuration\networkcontrol.ini | text | |
MD5:7E9F5A0E02F7B2B8654CABA1364A01B3 | SHA256:2A4B016BB7792CDB46BDC0075BCC0EE846046204BC1A87455B7BA9266B9CCC58 | |||
| 3796 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 2696 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2696.12905\SubSeven S.A.T 1.0.7\Data\GeoIP.dat | binary | |
MD5:1F897B5825CF91799831862620911AFF | SHA256:5F85518CF71E7B53544E0BD0C1874D1F89A0D6DE7A6AD50683517575AAA56301 | |||
| 3796 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3016 | SubSeven S.A.T 1.0.7.exe | GET | 301 | 104.31.76.103:80 | http://browserloot.rokey.xyz/api/get-ip.php | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3016 | SubSeven S.A.T 1.0.7.exe | 104.31.76.103:80 | browserloot.rokey.xyz | Cloudflare Inc | US | shared |
3016 | SubSeven S.A.T 1.0.7.exe | 104.31.76.103:443 | browserloot.rokey.xyz | Cloudflare Inc | US | shared |
3016 | SubSeven S.A.T 1.0.7.exe | 104.31.77.103:443 | browserloot.rokey.xyz | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
browserloot.rokey.xyz |
| malicious |
rokey.xyz |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3016 | SubSeven S.A.T 1.0.7.exe | A Network Trojan was detected | MALWARE [PTsecurity] BrowserLoot Stealer |
3016 | SubSeven S.A.T 1.0.7.exe | A Network Trojan was detected | MALWARE [PTsecurity] BrowserLoot Stealer Connection |
2 ETPRO signatures available at the full report