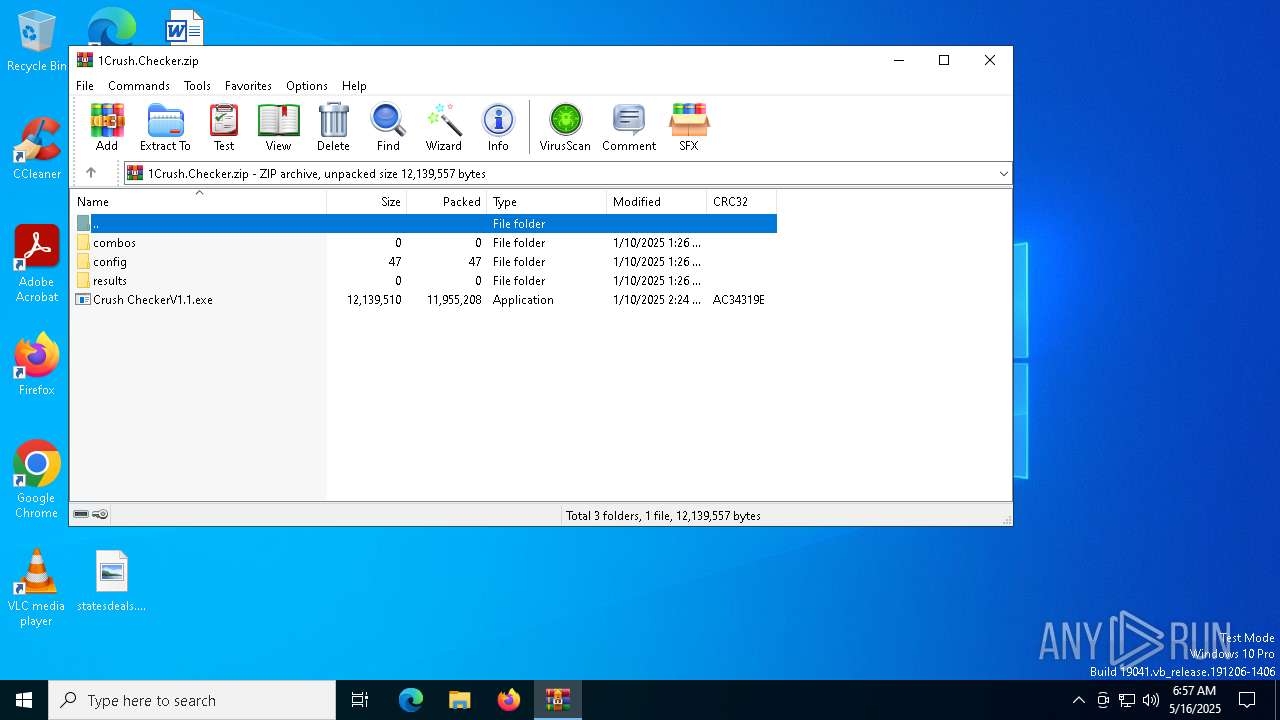
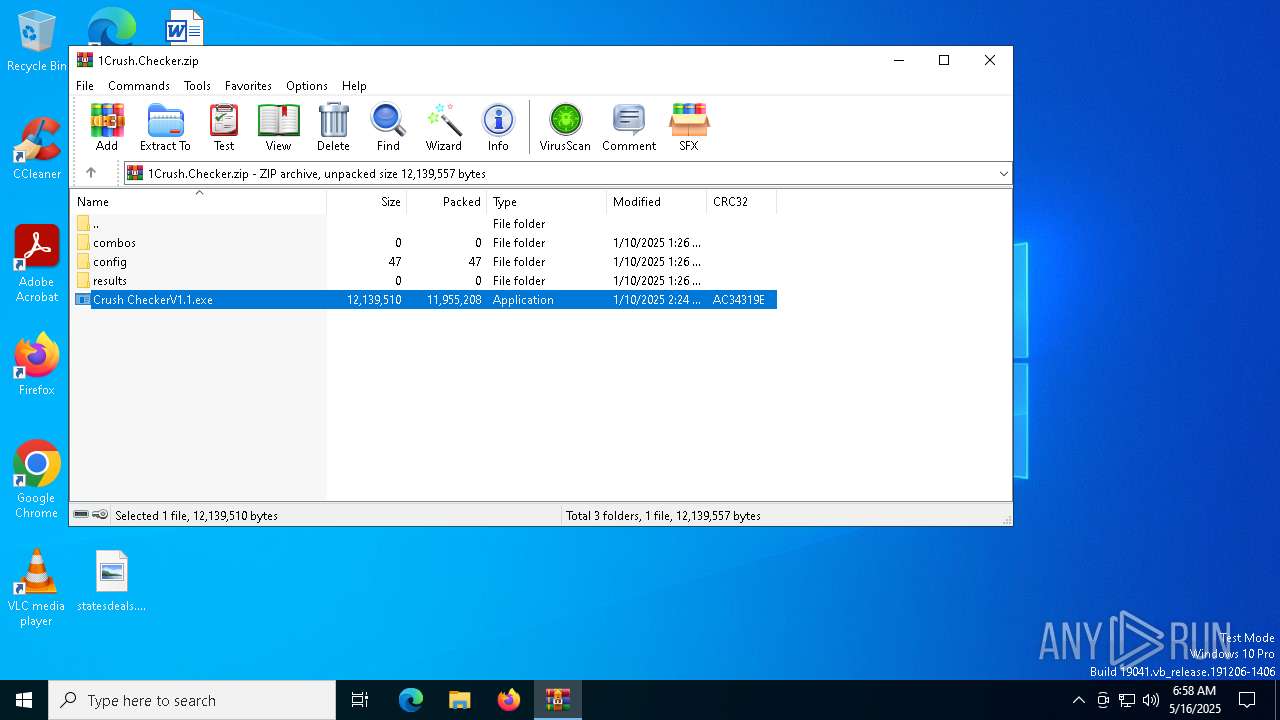
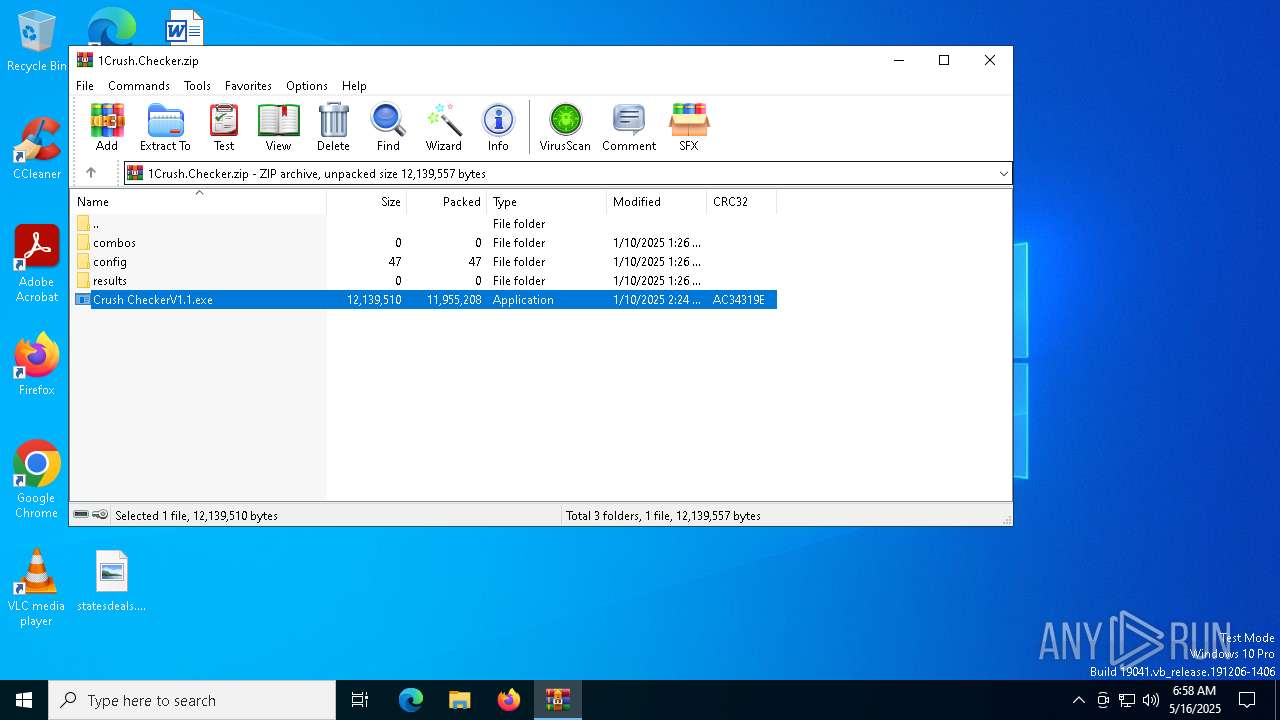
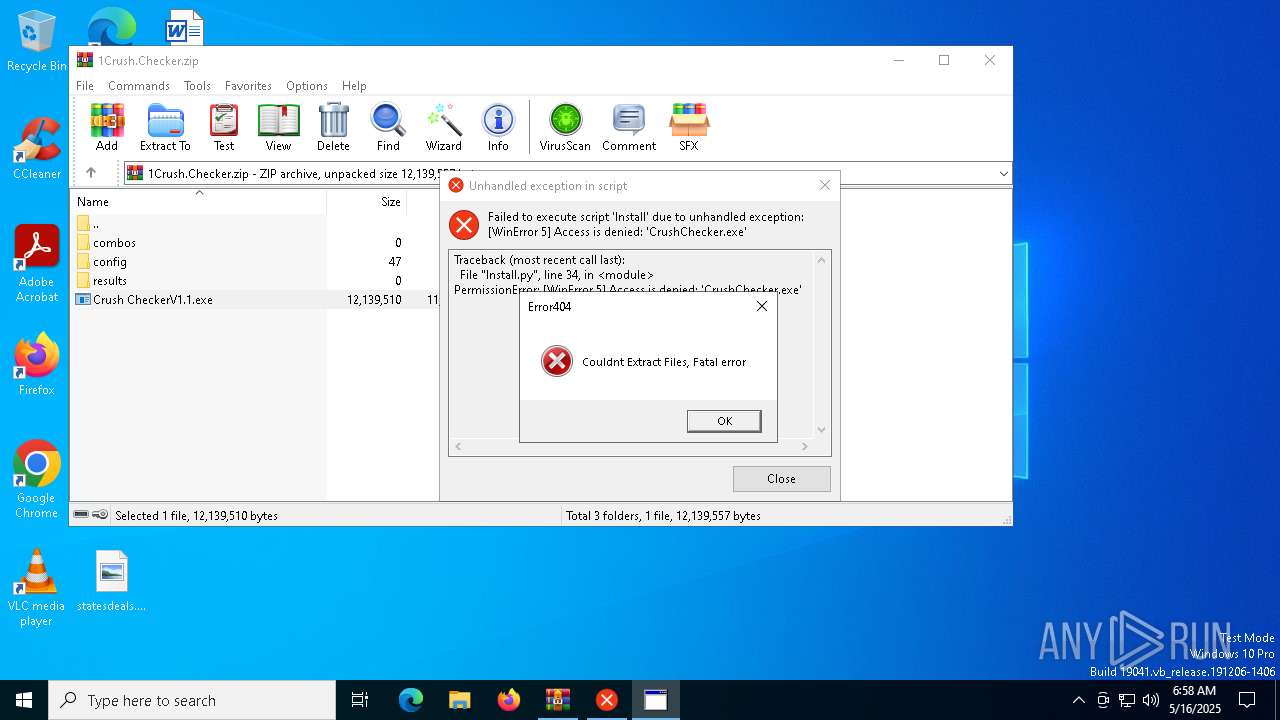
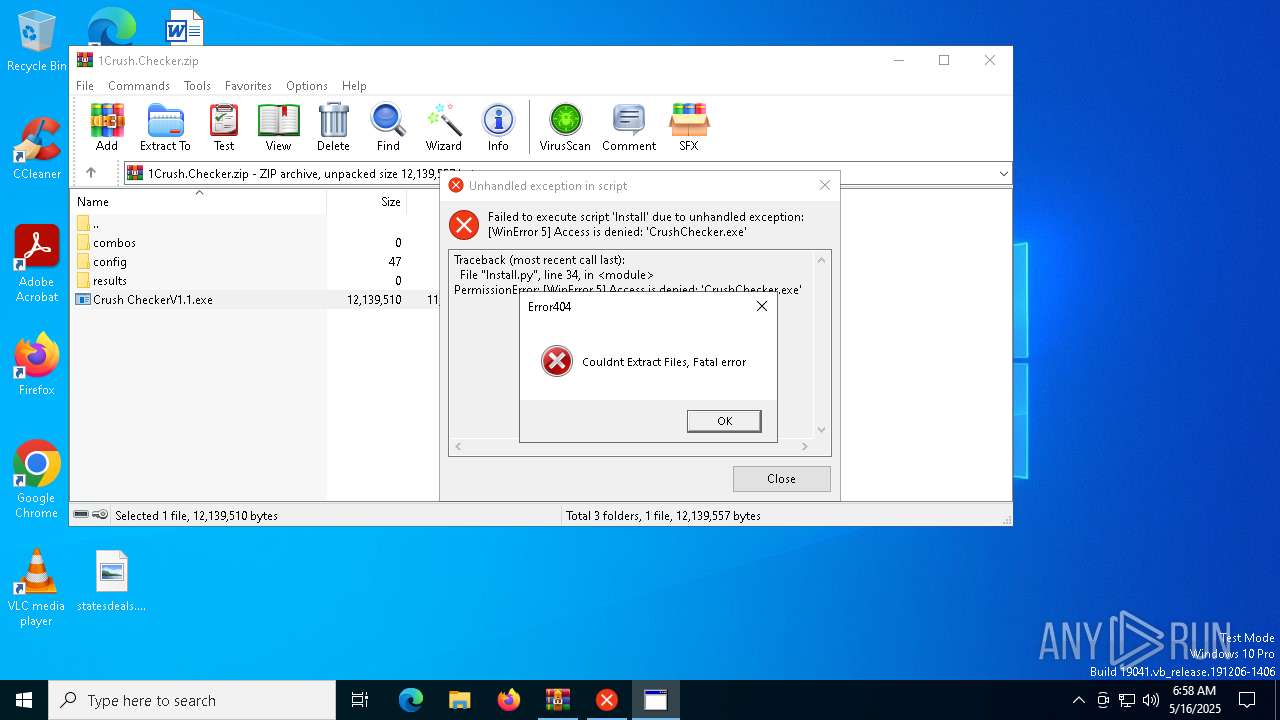
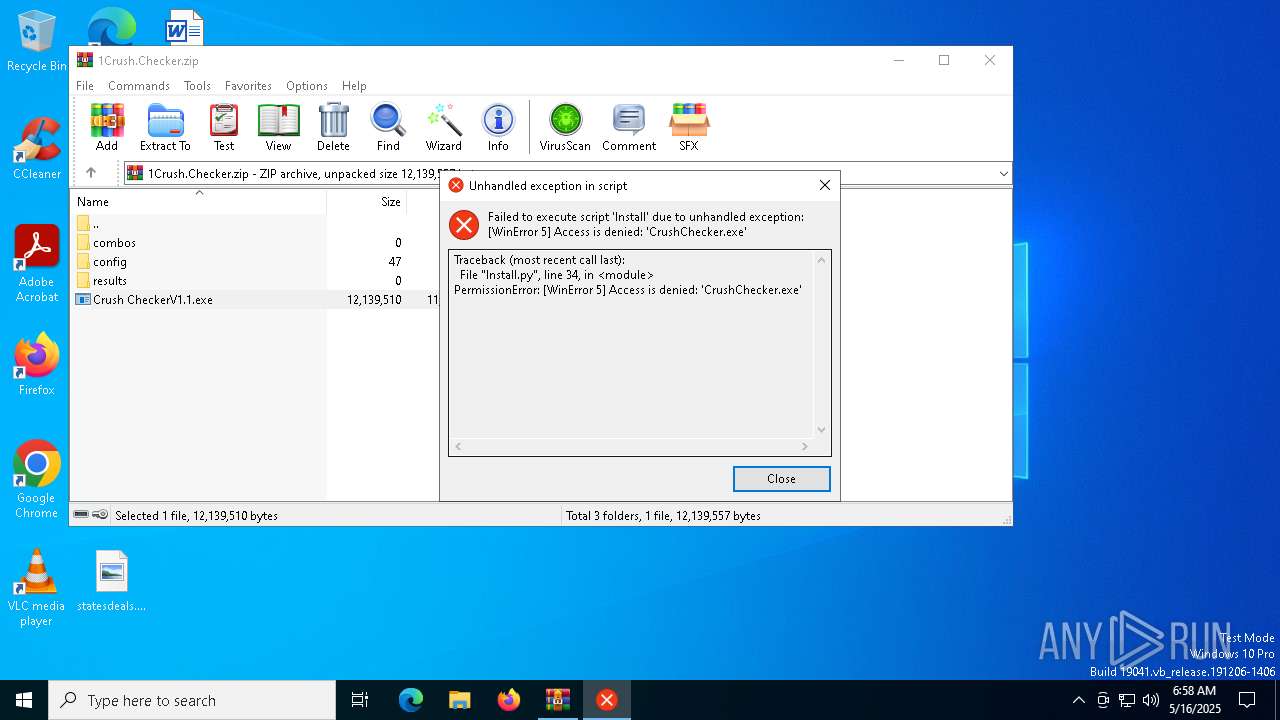
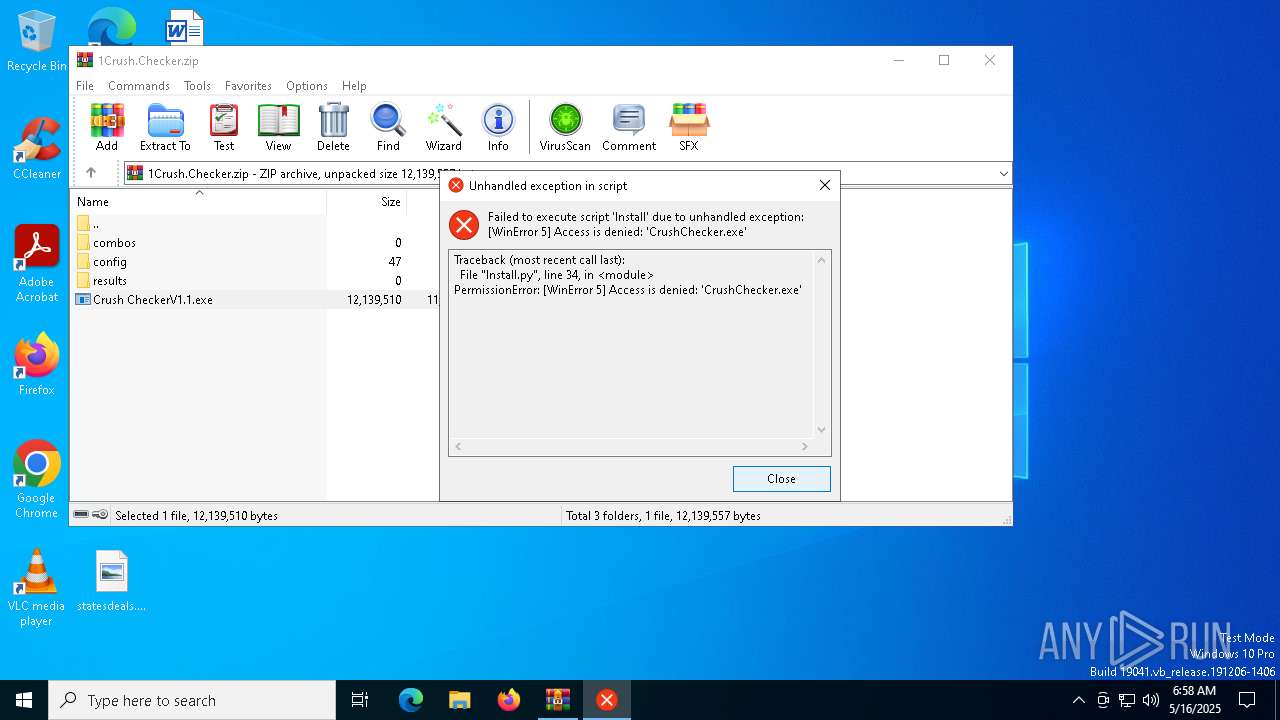
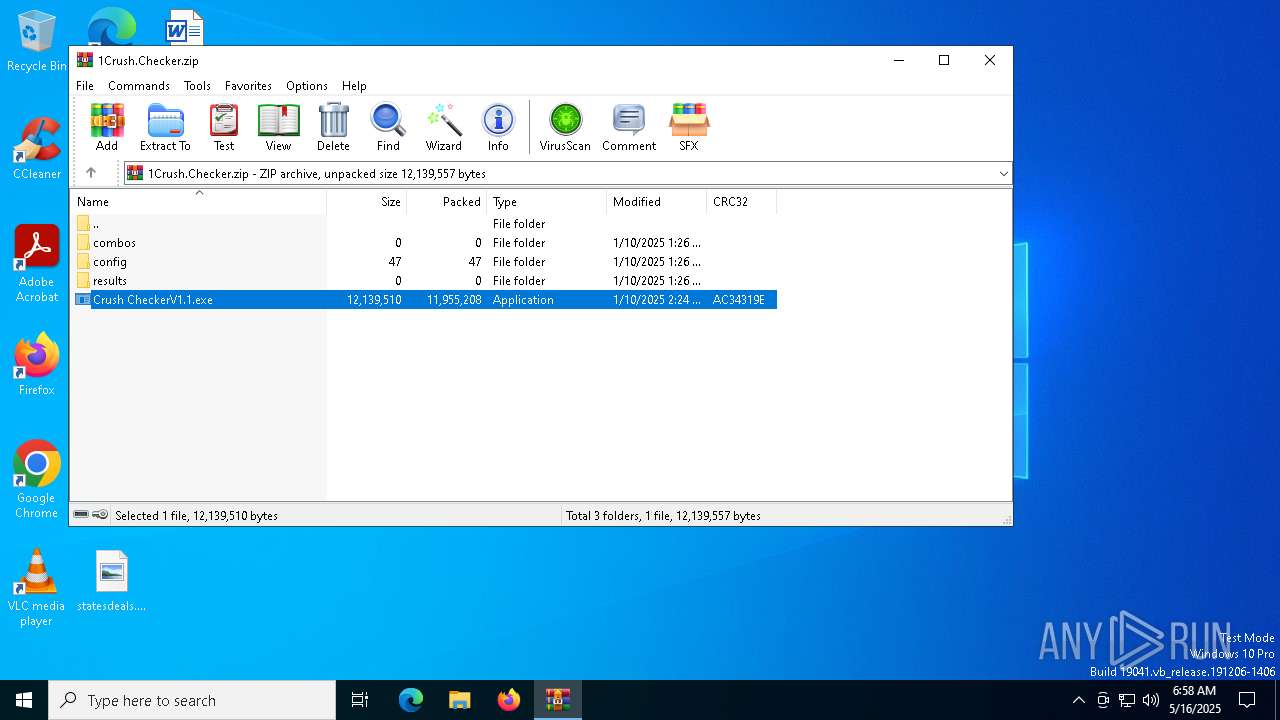
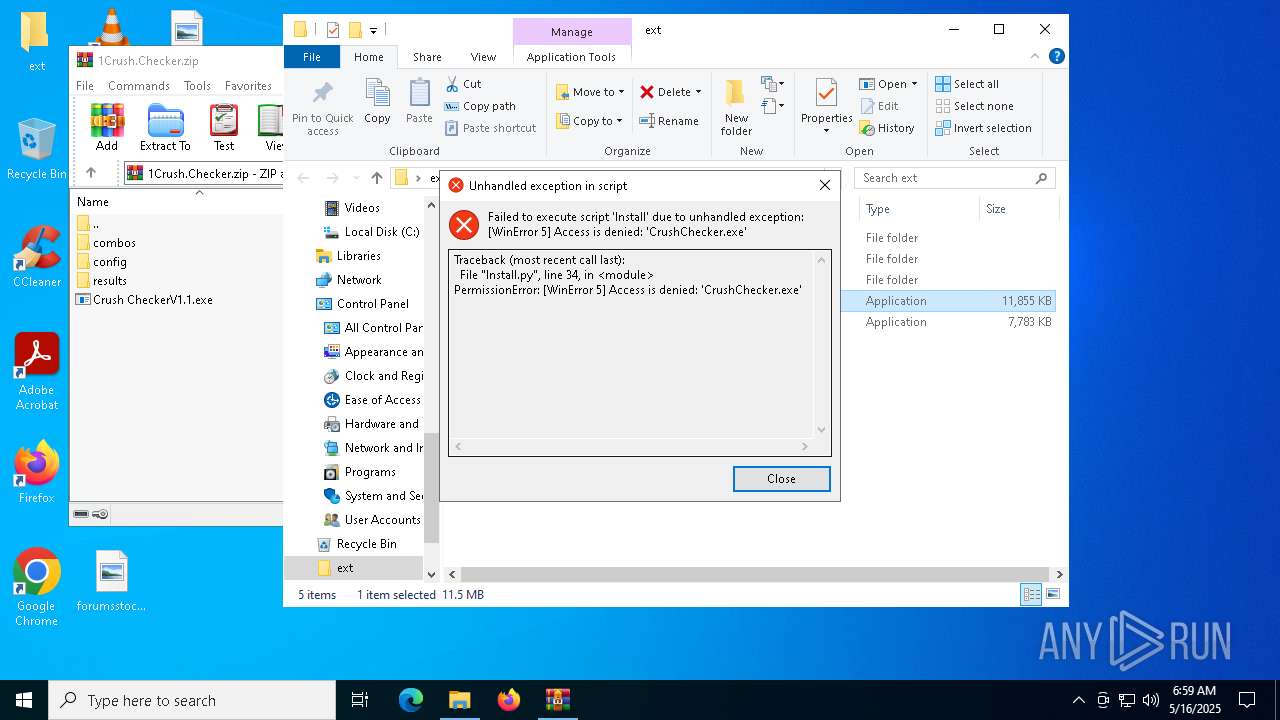
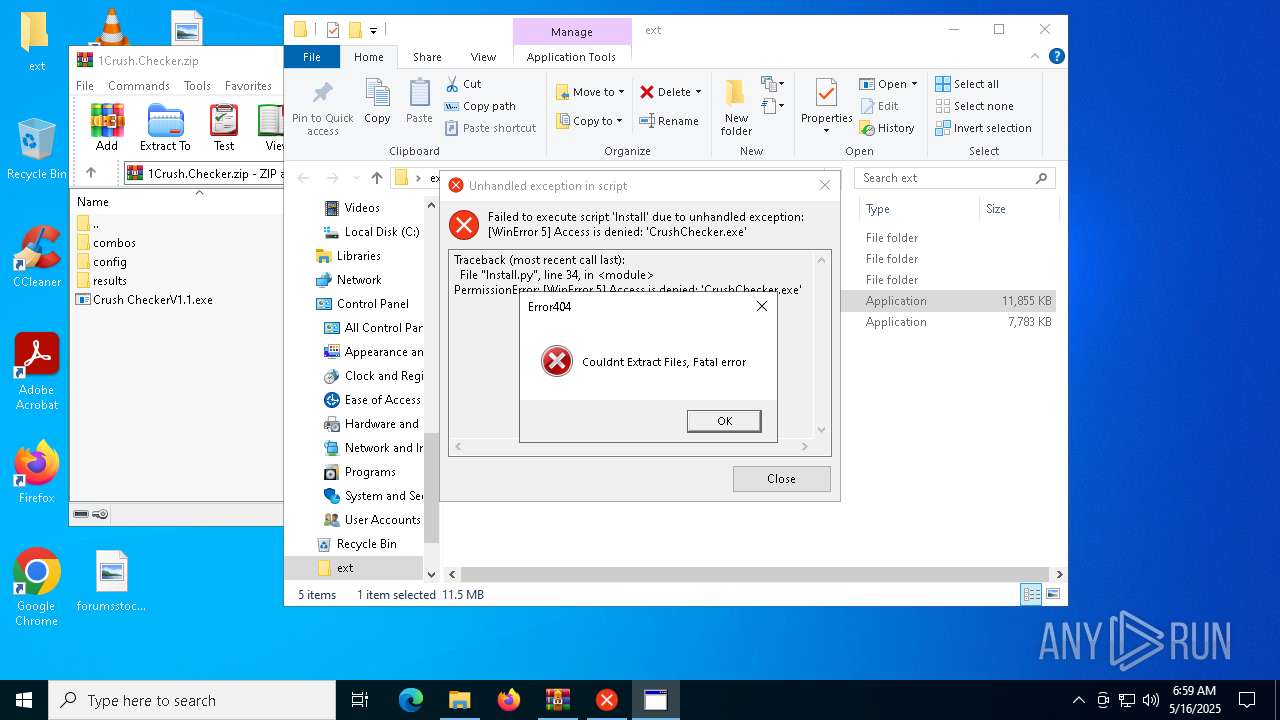
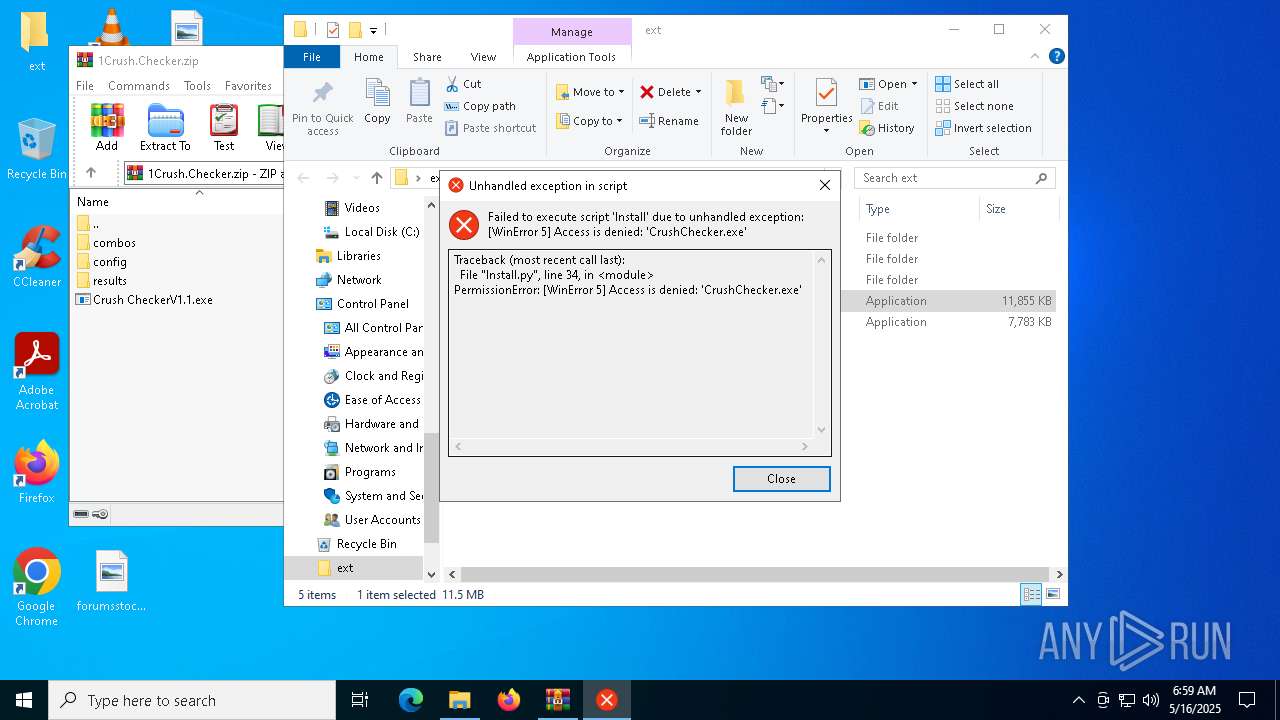
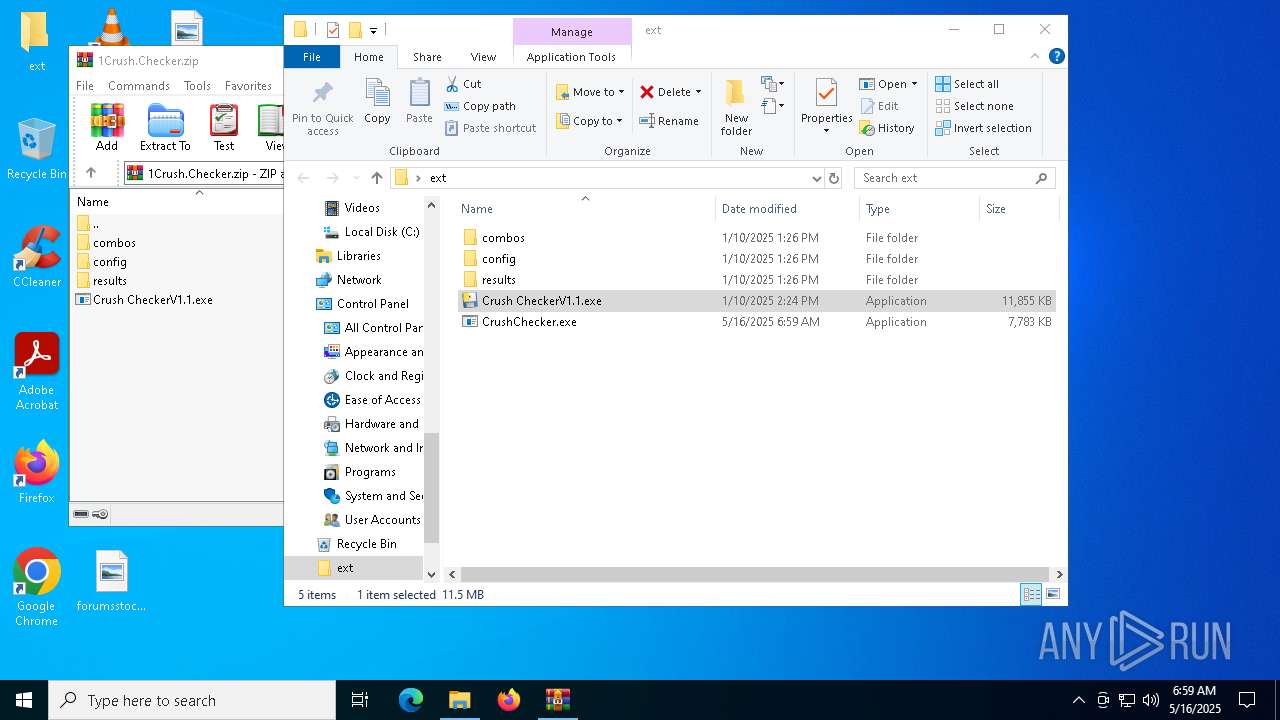
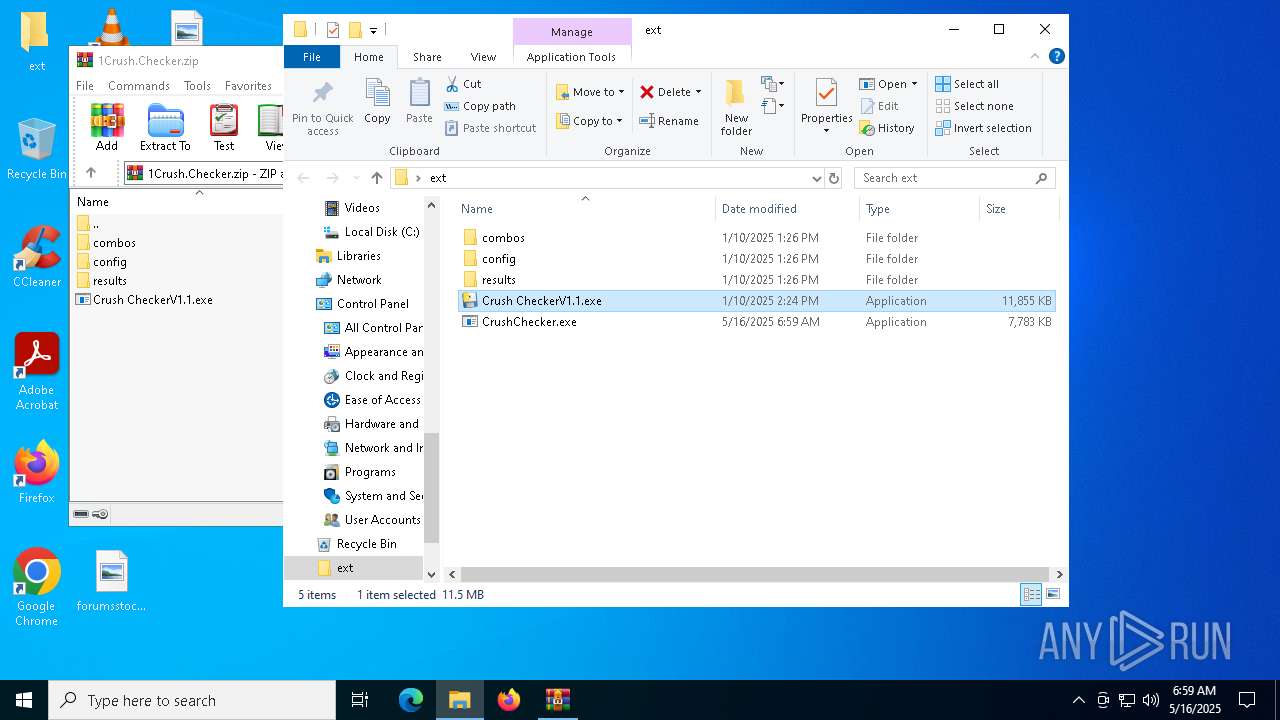
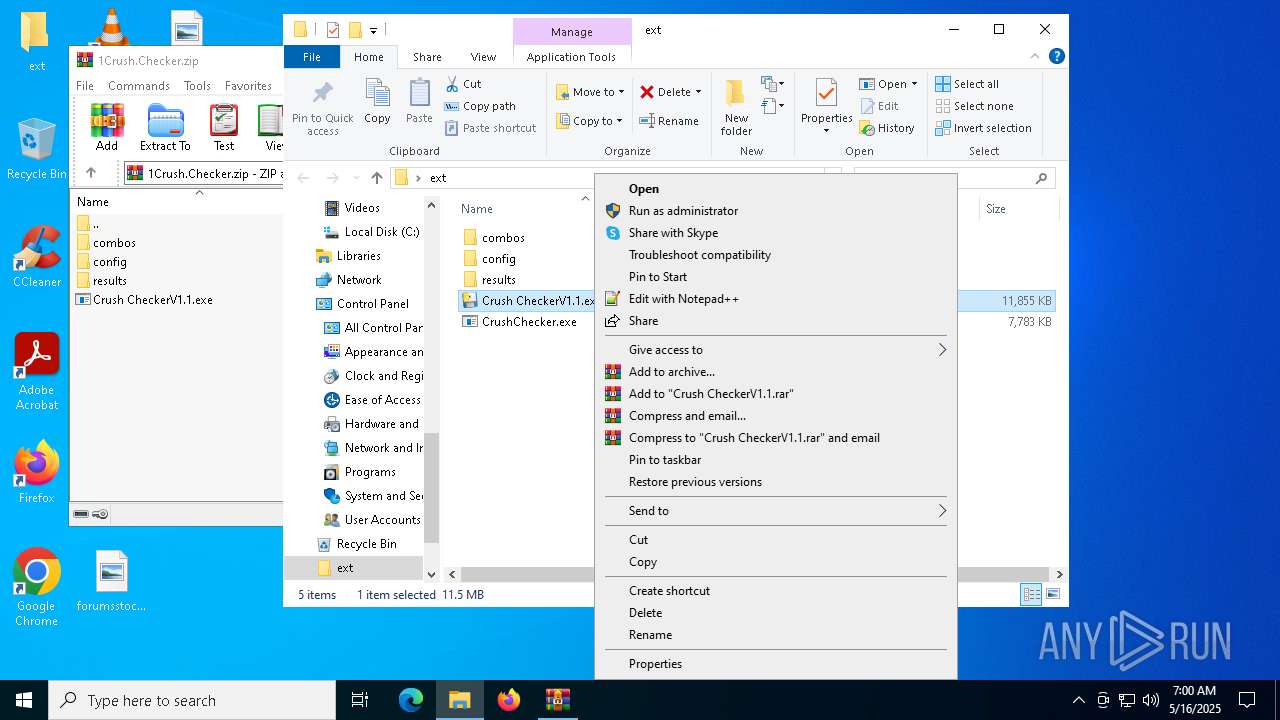
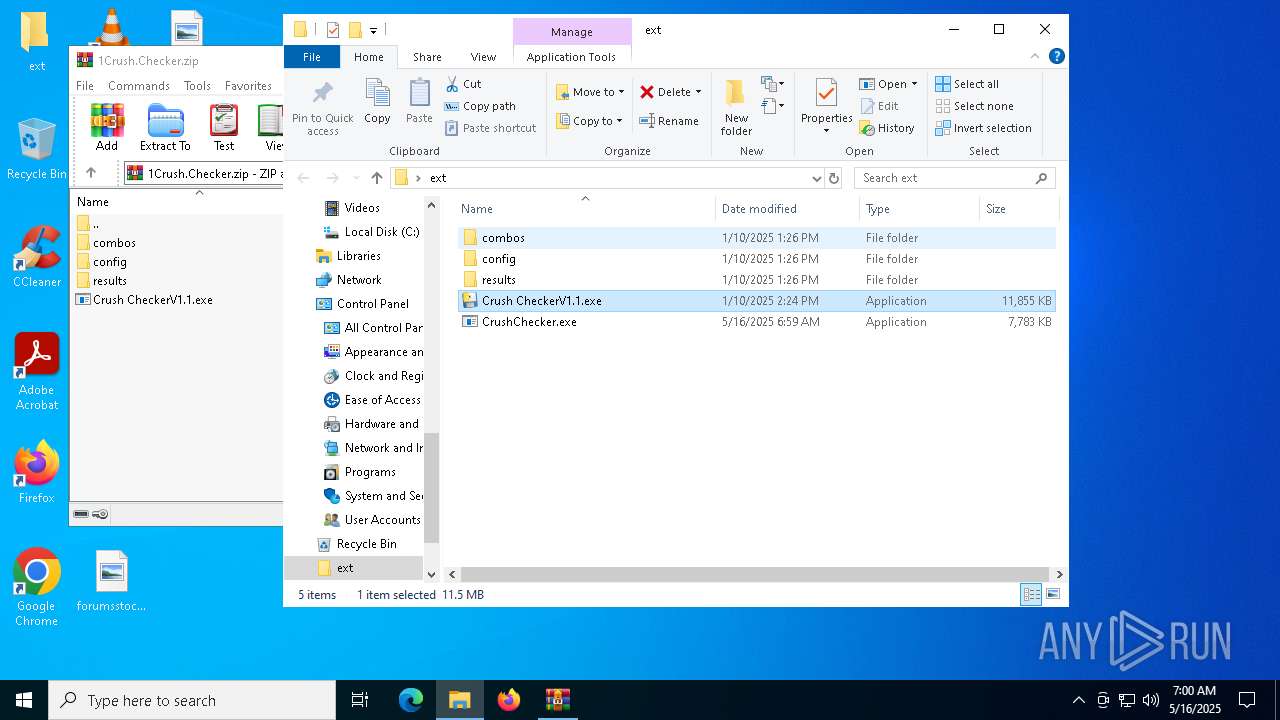
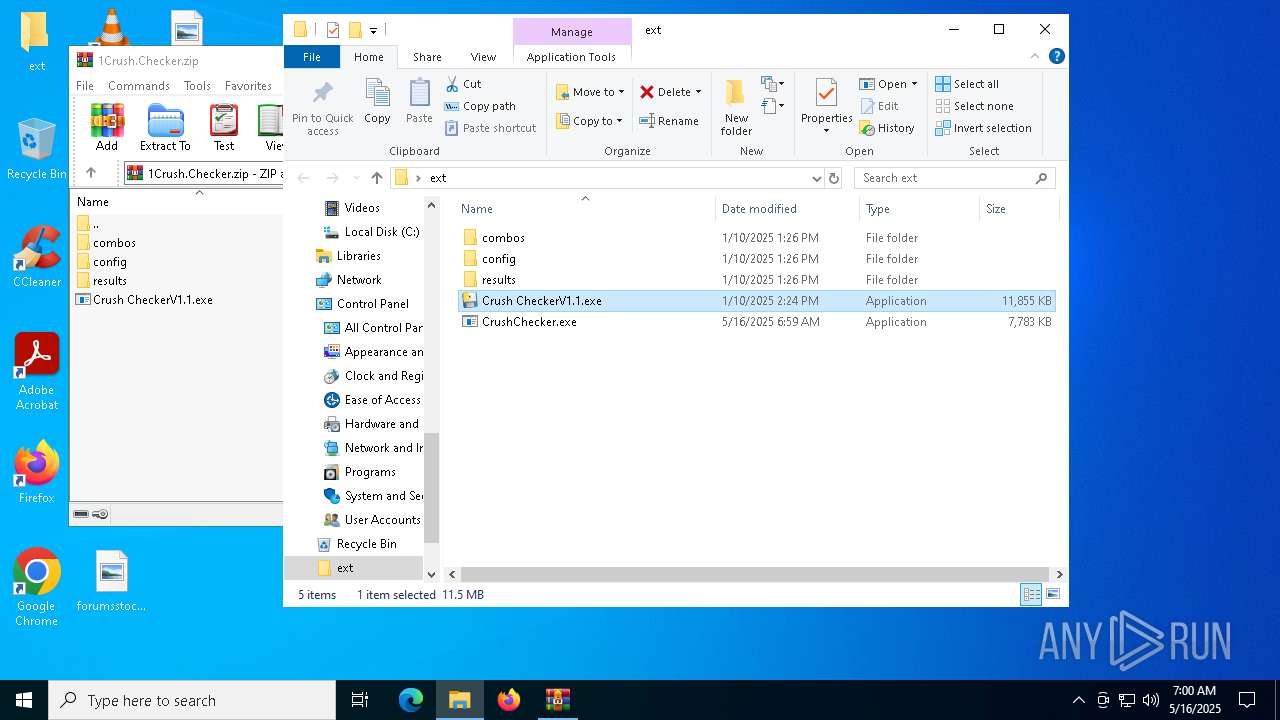
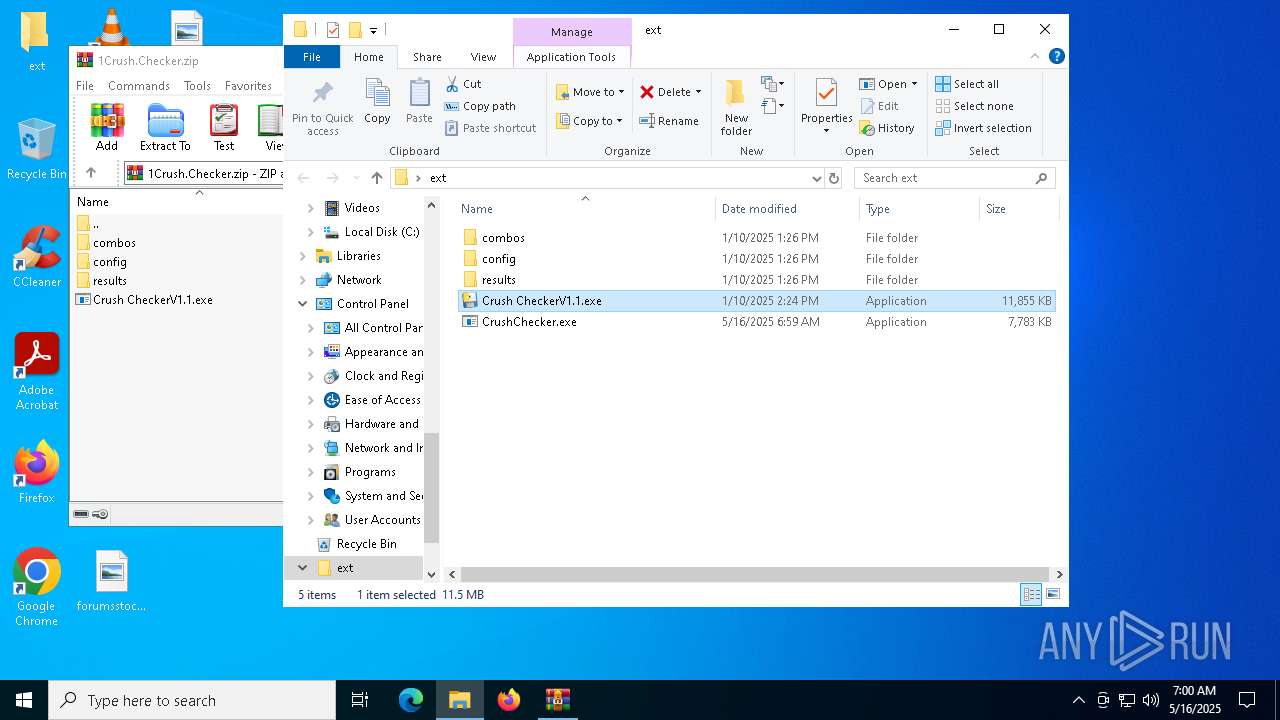
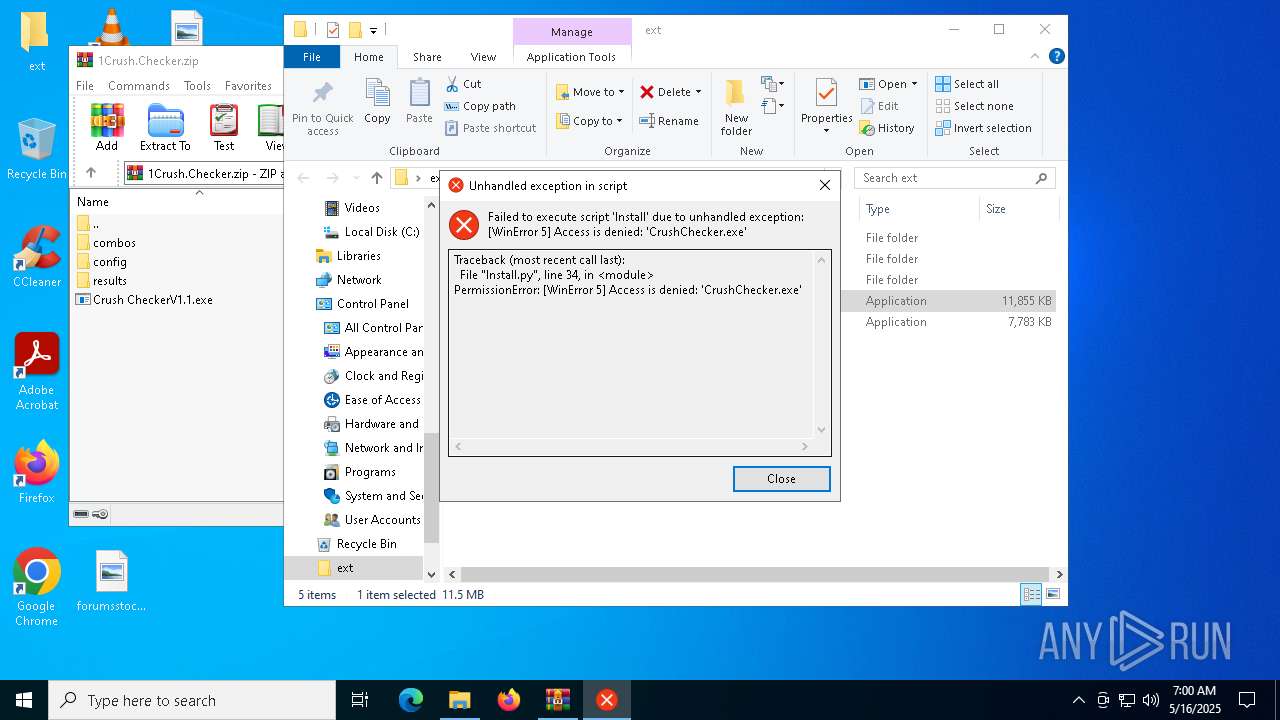
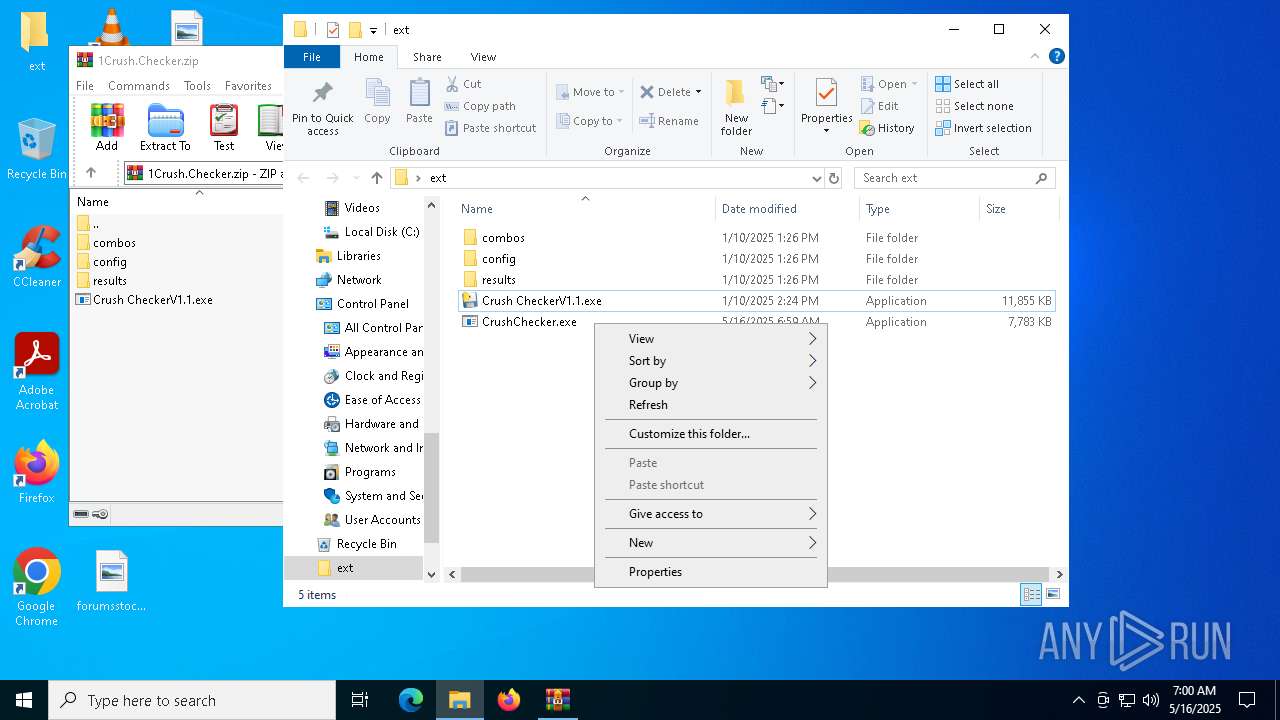
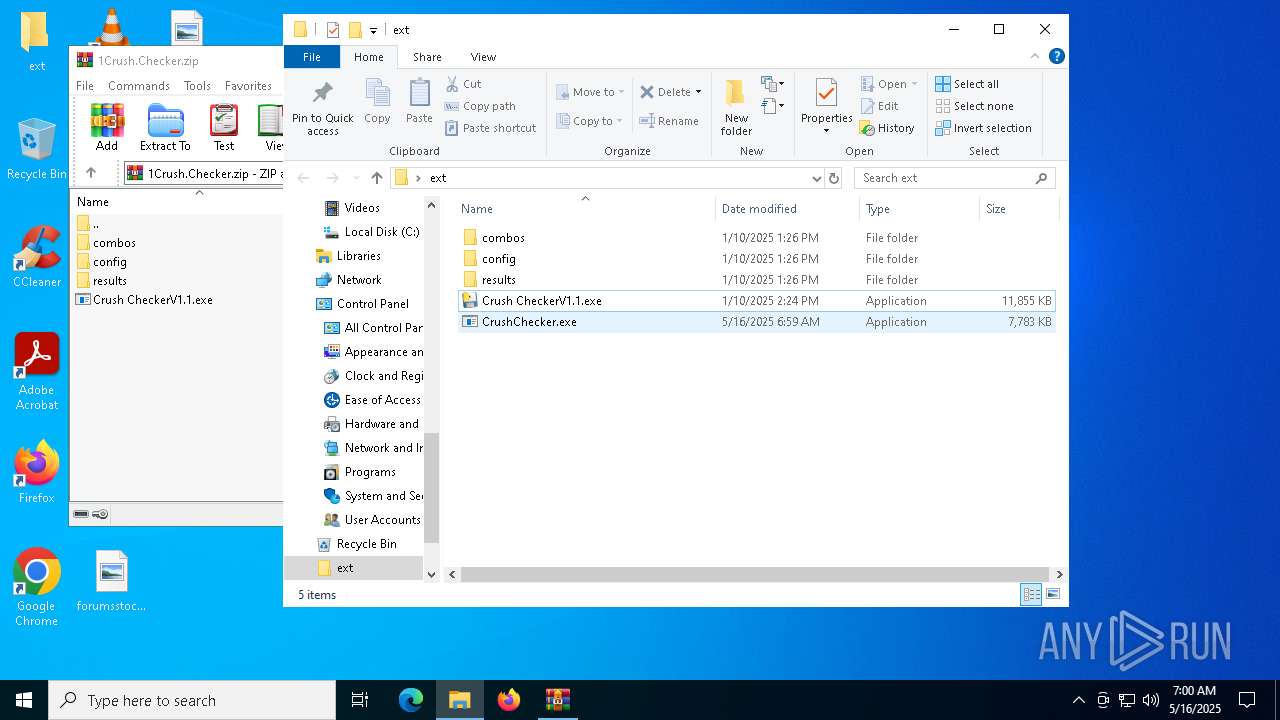
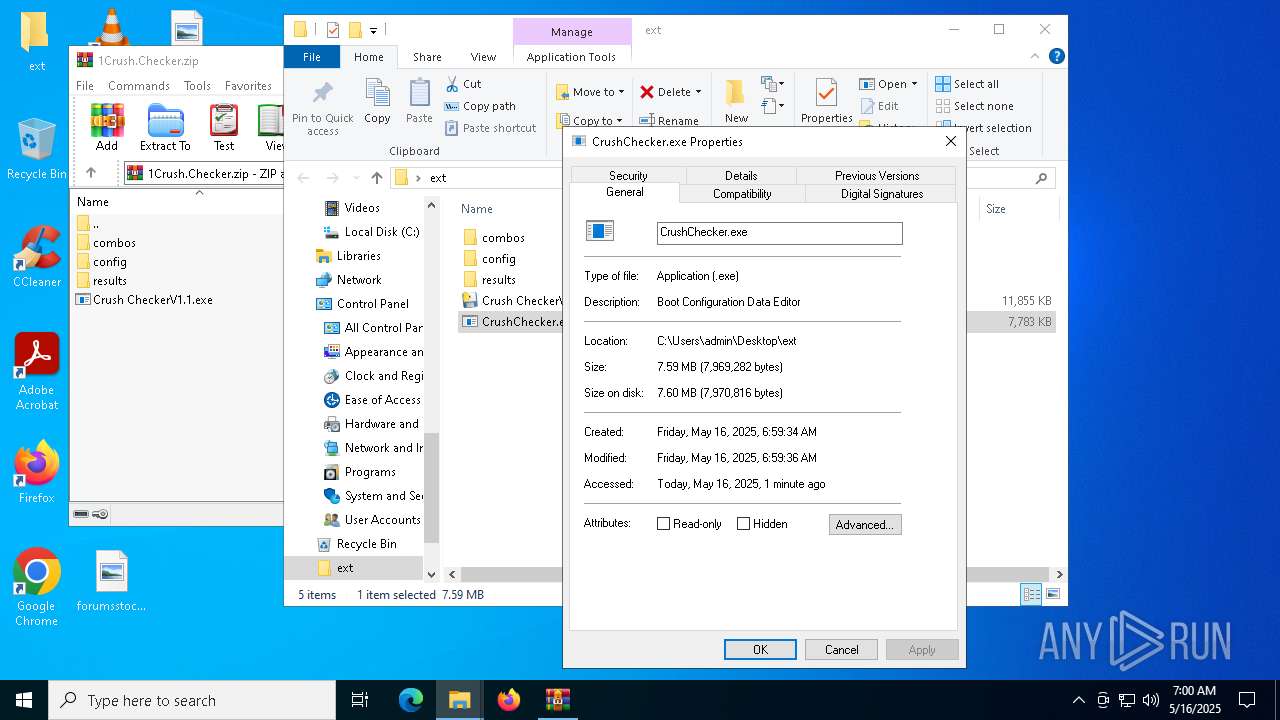
| File name: | 1Crush.Checker.zip |
| Full analysis: | https://app.any.run/tasks/bdd08e51-e017-4c56-8743-a3ff83612356 |
| Verdict: | Malicious activity |
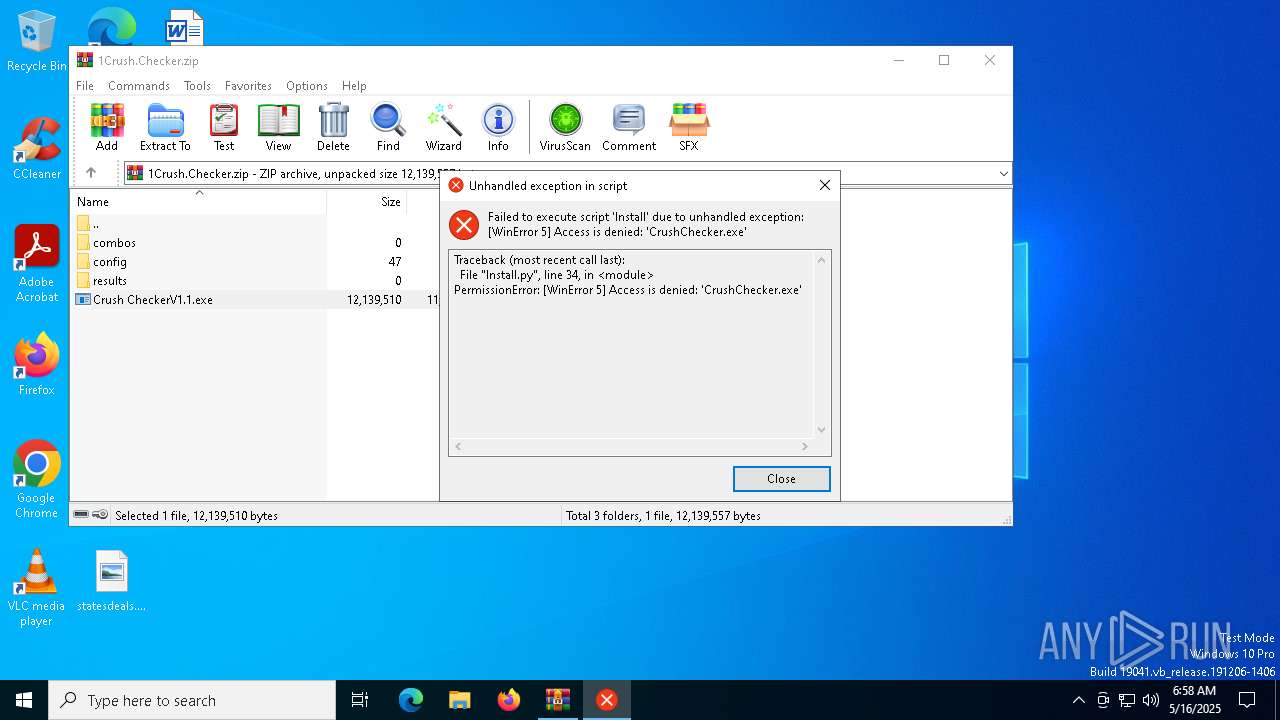
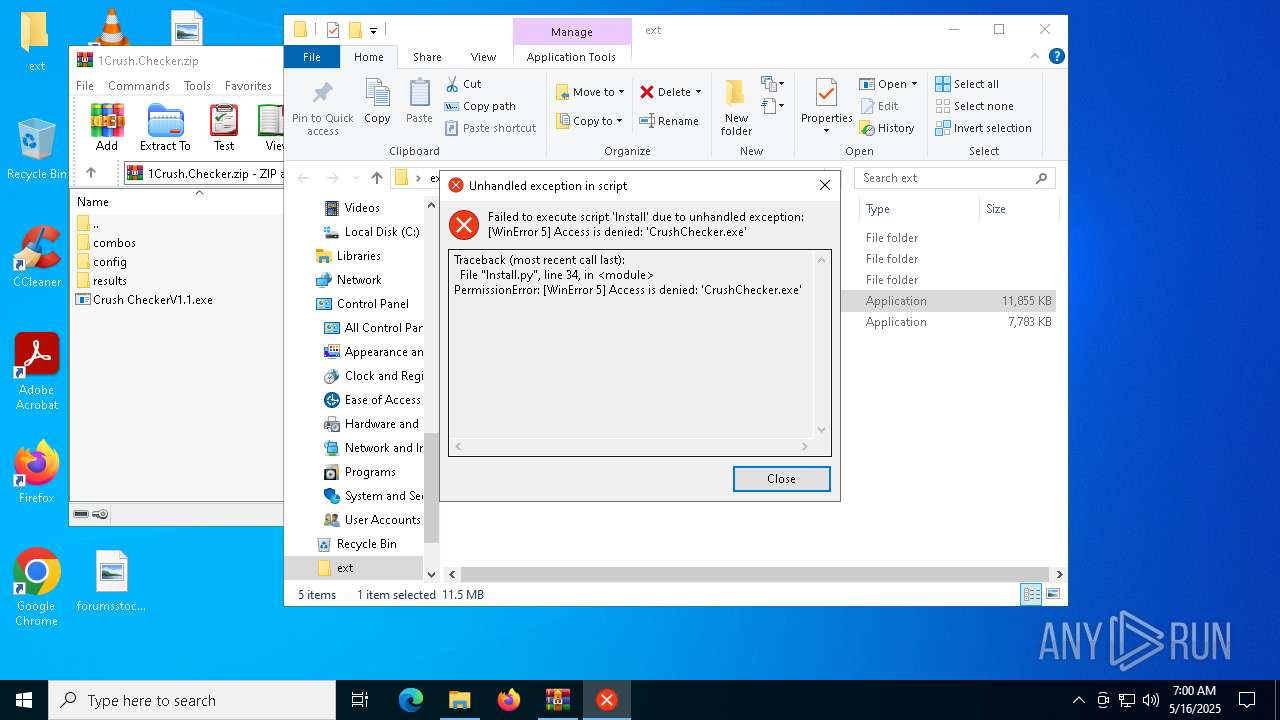
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | May 16, 2025, 06:57:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F5F4EA334C5973F333D9021BAEC2A0CE |
| SHA1: | 2D312B7902DA1DDFC2F682D5EB6A3B236DAE764F |
| SHA256: | 396E7FB50471BB2E7A9AD2BC60585757DB232AB08CF2869DCF86D9AE277BA050 |
| SSDEEP: | 98304:iucpZfY++fJ2nGzpBTeyZVkyJkzKJoq0I98WzeIe8oUmAEGt0odIlhcbTnynjRK2:ZFoa05VtTSKiieS/A+fJMS |
MALICIOUS
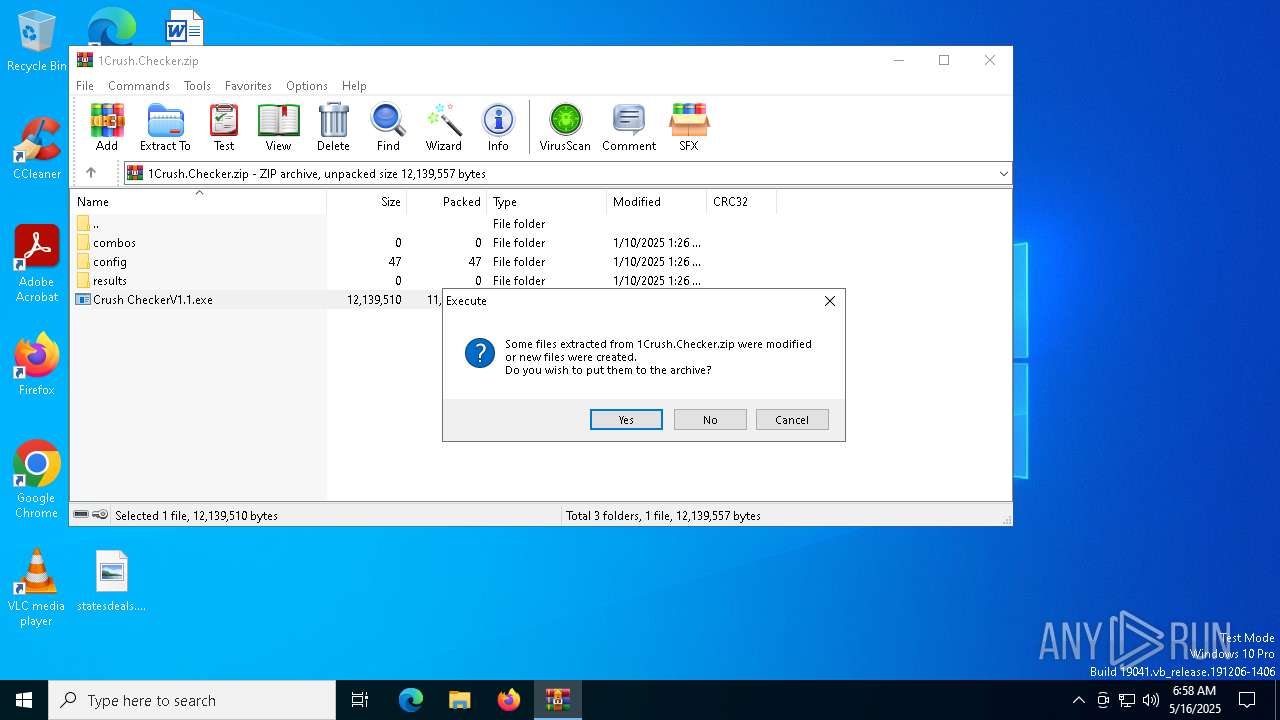
Executing a file with an untrusted certificate
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 6192)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 6252)
- CrushChecker.exe (PID: 208)
- CrushChecker.exe (PID: 7444)
BlankGrabber has been detected
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 6268)
- ComputerDefaults.exe (PID: 7552)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 632)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 7036)
- cmd.exe (PID: 2432)
Adds path to the Windows Defender exclusion list
- CrushChecker.exe (PID: 2284)
- cmd.exe (PID: 4336)
- cmd.exe (PID: 7688)
- CrushChecker.exe (PID: 7444)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 3992)
Changes Windows Defender settings
- cmd.exe (PID: 4336)
- cmd.exe (PID: 7036)
- cmd.exe (PID: 7688)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 2432)
- cmd.exe (PID: 3992)
Changes settings for protection against network attacks (IPS)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7752)
Changes antivirus protection settings for downloading files from the Internet (IOAVProtection)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7752)
Changes settings for real-time protection
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7752)
Changes settings for reporting to Microsoft Active Protection Service (MAPS)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7752)
Changes Controlled Folder Access settings
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7752)
Changes settings for checking scripts for malicious actions
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7752)
Changes settings for sending potential threat samples to Microsoft servers
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7752)
Create files in the Startup directory
- CrushChecker.exe (PID: 2284)
Actions looks like stealing of personal data
- CrushChecker.exe (PID: 2284)
Steals credentials from Web Browsers
- CrushChecker.exe (PID: 2284)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 2552)
Bypass execution policy to execute commands
- powershell.exe (PID: 7616)
- powershell.exe (PID: 5452)
Resets Windows Defender malware definitions to the base version
- MpCmdRun.exe (PID: 8160)
- MpCmdRun.exe (PID: 8072)
BLANKGRABBER has been detected (SURICATA)
- CrushChecker.exe (PID: 2284)
- CrushChecker.exe (PID: 7444)
Stealers network behavior
- CrushChecker.exe (PID: 2284)
SUSPICIOUS
Application launched itself
- Crush CheckerV1.1.exe (PID: 904)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- Crush CheckerV1.1.exe (PID: 7996)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 208)
- Crush CheckerV1.1.exe (PID: 7772)
The process drops C-runtime libraries
- Crush CheckerV1.1.exe (PID: 904)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- Crush CheckerV1.1.exe (PID: 7996)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 208)
- Crush CheckerV1.1.exe (PID: 7772)
Process drops python dynamic module
- Crush CheckerV1.1.exe (PID: 904)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- Crush CheckerV1.1.exe (PID: 7996)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 208)
- Crush CheckerV1.1.exe (PID: 7772)
Process drops legitimate windows executable
- Crush CheckerV1.1.exe (PID: 904)
- Crush CheckerV1.1.exe (PID: 5380)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- Crush CheckerV1.1.exe (PID: 7996)
- CrushChecker.exe (PID: 208)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 7444)
- Crush CheckerV1.1.exe (PID: 7772)
Executable content was dropped or overwritten
- Crush CheckerV1.1.exe (PID: 904)
- Crush CheckerV1.1.exe (PID: 5380)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- csc.exe (PID: 4152)
- Crush CheckerV1.1.exe (PID: 7996)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 208)
- CrushChecker.exe (PID: 7444)
- csc.exe (PID: 7324)
- Crush CheckerV1.1.exe (PID: 7772)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5988)
Loads Python modules
- Crush CheckerV1.1.exe (PID: 5380)
Starts a Microsoft application from unusual location
- CrushChecker.exe (PID: 6192)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 6252)
- CrushChecker.exe (PID: 208)
- CrushChecker.exe (PID: 7444)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 728)
- cmd.exe (PID: 896)
- cmd.exe (PID: 6032)
- cmd.exe (PID: 7288)
- cmd.exe (PID: 7264)
- cmd.exe (PID: 2084)
Found strings related to reading or modifying Windows Defender settings
- CrushChecker.exe (PID: 6192)
- CrushChecker.exe (PID: 2284)
- CrushChecker.exe (PID: 6252)
- CrushChecker.exe (PID: 7444)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 6516)
- cmd.exe (PID: 2268)
- cmd.exe (PID: 7560)
- cmd.exe (PID: 4920)
Changes default file association
- reg.exe (PID: 632)
Starts CMD.EXE for commands execution
- CrushChecker.exe (PID: 6192)
- CrushChecker.exe (PID: 2284)
- CrushChecker.exe (PID: 6252)
- CrushChecker.exe (PID: 7444)
Get information on the list of running processes
- CrushChecker.exe (PID: 2284)
- cmd.exe (PID: 5400)
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7880)
- cmd.exe (PID: 8104)
- CrushChecker.exe (PID: 7444)
- cmd.exe (PID: 5404)
- cmd.exe (PID: 5380)
- cmd.exe (PID: 5324)
- cmd.exe (PID: 6436)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 4336)
- cmd.exe (PID: 7688)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 3992)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 7036)
- cmd.exe (PID: 2432)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7036)
- cmd.exe (PID: 4336)
- cmd.exe (PID: 7688)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 7996)
- cmd.exe (PID: 5124)
- cmd.exe (PID: 4988)
- cmd.exe (PID: 6620)
- cmd.exe (PID: 7296)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 2432)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 5332)
- cmd.exe (PID: 2552)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 2152)
- cmd.exe (PID: 4056)
- cmd.exe (PID: 4844)
Script disables Windows Defender's IPS
- cmd.exe (PID: 7036)
- cmd.exe (PID: 2432)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 4212)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 7724)
- cmd.exe (PID: 7988)
- cmd.exe (PID: 7264)
- cmd.exe (PID: 1164)
Executes JavaScript directly as a command
- cmd.exe (PID: 6592)
- cmd.exe (PID: 5956)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 7416)
- cmd.exe (PID: 7580)
- cmd.exe (PID: 7492)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 7548)
Checks for external IP
- CrushChecker.exe (PID: 2284)
- svchost.exe (PID: 2196)
- CrushChecker.exe (PID: 7444)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 7484)
- WMIC.exe (PID: 7640)
There is functionality for taking screenshot (YARA)
- Crush CheckerV1.1.exe (PID: 904)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 720)
Base64-obfuscated command line is found
- cmd.exe (PID: 7308)
- cmd.exe (PID: 2552)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7308)
- cmd.exe (PID: 2552)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 7308)
- cmd.exe (PID: 2552)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 5360)
- cmd.exe (PID: 7644)
Starts application with an unusual extension
- cmd.exe (PID: 8128)
- cmd.exe (PID: 8116)
- cmd.exe (PID: 6136)
- cmd.exe (PID: 536)
- cmd.exe (PID: 5116)
- cmd.exe (PID: 7268)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 7944)
- cmd.exe (PID: 4572)
- cmd.exe (PID: 7448)
- cmd.exe (PID: 8124)
- cmd.exe (PID: 7688)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 8164)
- cmd.exe (PID: 7320)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7288)
CSC.EXE is used to compile C# code
- csc.exe (PID: 4152)
- csc.exe (PID: 7324)
Captures screenshot (POWERSHELL)
- powershell.exe (PID: 7616)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 7436)
- rar.exe (PID: 2344)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 8160)
- cmd.exe (PID: 7400)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7768)
- cmd.exe (PID: 3032)
INFO
Reads the computer name
- Crush CheckerV1.1.exe (PID: 5380)
- Crush CheckerV1.1.exe (PID: 904)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- MpCmdRun.exe (PID: 8160)
Checks supported languages
- Crush CheckerV1.1.exe (PID: 5380)
- Crush CheckerV1.1.exe (PID: 904)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 6192)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- tree.com (PID: 4488)
- tree.com (PID: 4920)
- tree.com (PID: 5544)
- tree.com (PID: 5960)
- tree.com (PID: 7644)
- MpCmdRun.exe (PID: 8160)
- tree.com (PID: 7876)
- csc.exe (PID: 4152)
- cvtres.exe (PID: 6712)
The sample compiled with english language support
- Crush CheckerV1.1.exe (PID: 904)
- Crush CheckerV1.1.exe (PID: 5380)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- Crush CheckerV1.1.exe (PID: 7996)
- CrushChecker.exe (PID: 7000)
- CrushChecker.exe (PID: 208)
- CrushChecker.exe (PID: 7444)
- Crush CheckerV1.1.exe (PID: 7772)
Create files in a temporary directory
- Crush CheckerV1.1.exe (PID: 904)
- Crush CheckerV1.1.exe (PID: 5380)
- CrushChecker.exe (PID: 6192)
- CrushChecker.exe (PID: 4040)
- CrushChecker.exe (PID: 7148)
- CrushChecker.exe (PID: 2284)
- MpCmdRun.exe (PID: 8160)
- cvtres.exe (PID: 6712)
- csc.exe (PID: 4152)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5988)
Checks proxy server information
- Crush CheckerV1.1.exe (PID: 5380)
Reads security settings of Internet Explorer
- ComputerDefaults.exe (PID: 6268)
- WMIC.exe (PID: 720)
- WMIC.exe (PID: 7484)
- WMIC.exe (PID: 7640)
- WMIC.exe (PID: 7288)
Reads Internet Explorer settings
- mshta.exe (PID: 5936)
Creates files in the program directory
- CrushChecker.exe (PID: 2284)
PyInstaller has been detected (YARA)
- Crush CheckerV1.1.exe (PID: 904)
- CrushChecker.exe (PID: 7148)
The Powershell gets current clipboard
- powershell.exe (PID: 5680)
- powershell.exe (PID: 7728)
Checks the directory tree
- tree.com (PID: 7644)
- tree.com (PID: 4488)
- tree.com (PID: 4920)
- tree.com (PID: 5544)
- tree.com (PID: 5960)
- tree.com (PID: 7876)
- tree.com (PID: 7796)
- tree.com (PID: 5392)
- tree.com (PID: 2104)
- tree.com (PID: 5084)
- tree.com (PID: 5508)
- tree.com (PID: 5548)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7740)
- powershell.exe (PID: 6652)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6652)
- powershell.exe (PID: 2040)
- powershell.exe (PID: 7740)
Reads the machine GUID from the registry
- csc.exe (PID: 4152)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 7280)
- getmac.exe (PID: 2064)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
Manual execution by a user
- Crush CheckerV1.1.exe (PID: 7996)
- Crush CheckerV1.1.exe (PID: 7772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:11 00:24:28 |
| ZipCRC: | 0xac34319e |
| ZipCompressedSize: | 11955208 |
| ZipUncompressedSize: | 12139510 |
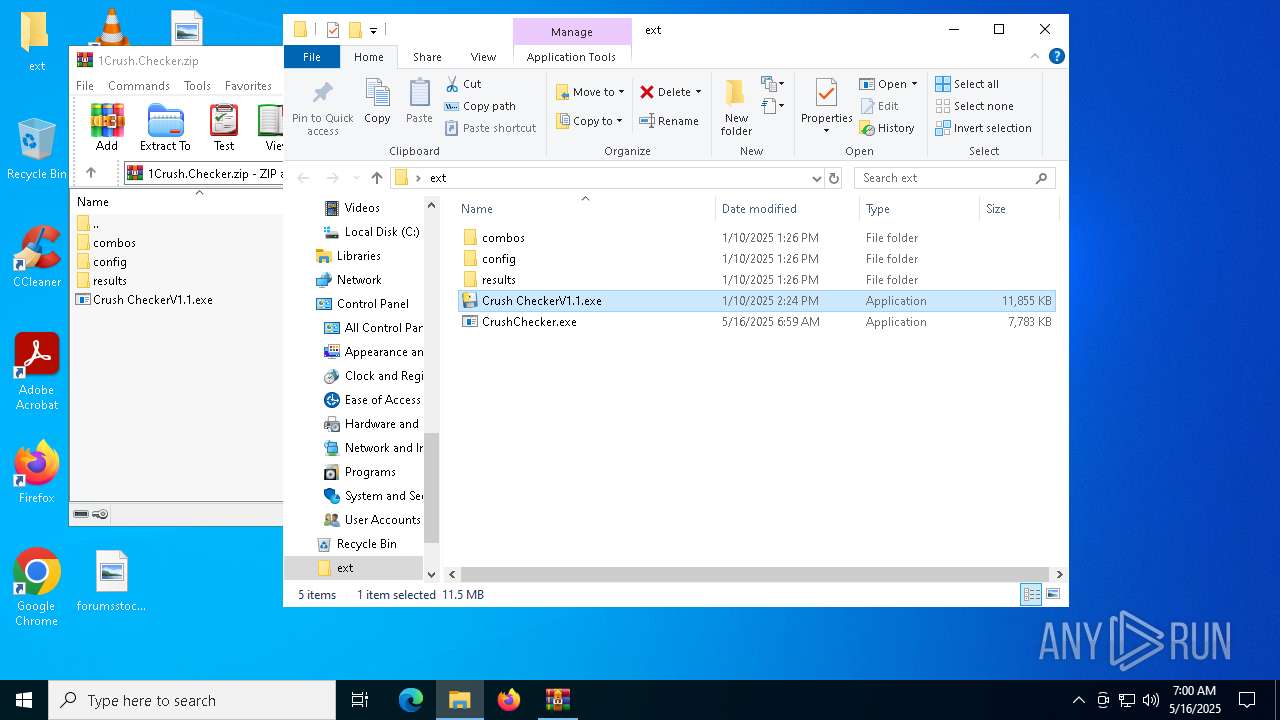
| ZipFileName: | Crush CheckerV1.1.exe |
Total processes
413
Monitored processes
277
Malicious processes
26
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Users\admin\Desktop\ext\CrushChecker.exe" | C:\Users\admin\Desktop\ext\CrushChecker.exe | ComputerDefaults.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 10.0.19041.5129 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | C:\WINDOWS\system32\cmd.exe /c "tree /A /F" | C:\Windows\System32\cmd.exe | — | CrushChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | reg add hkcu\Software\Classes\ms-settings\shell\open\command /v "DelegateExecute" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | powershell -Command Add-MpPreference -ExclusionPath 'C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp\ .scr' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\system32\cmd.exe /c "reg add hkcu\Software\Classes\ms-settings\shell\open\command /d "C:\Users\admin\AppData\Local\Temp\Rar$EXa5988.49023\CrushChecker.exe" /f" | C:\Windows\System32\cmd.exe | — | CrushChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | C:\WINDOWS\system32\cmd.exe /c "reg add hkcu\Software\Classes\ms-settings\shell\open\command /v "DelegateExecute" /f" | C:\Windows\System32\cmd.exe | — | CrushChecker.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5988.49023\Crush CheckerV1.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5988.49023\Crush CheckerV1.1.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
124 695
Read events
124 663
Write events
24
Delete events
8
Modification events
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1Crush.Checker.zip | |||
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5988) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (632) reg.exe | Key: | HKEY_CLASSES_ROOT\ms-settings\shell\open\command |
| Operation: | write | Name: | DelegateExecute |
Value: | |||
| (PID) Process: | (6268) ComputerDefaults.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
136
Suspicious files
50
Text files
116
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5988.49023\Crush CheckerV1.1.exe | executable | |
MD5:9A552271D7E3DDA42CF8714789D3FF89 | SHA256:035B66DC1550980B289C17B37F583BC41783006397380F151DF200833BFF49EE | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\_ssl.pyd | executable | |
MD5:CF541CC288AC0BEC9B682A2E0011D1FF | SHA256:E94F0195363C5C9BABFC4C17EC6FB1AA8BBABF59E377DB66CE6A79C4C58BBD07 | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\_hashlib.pyd | executable | |
MD5:422E214CA76421E794B99F99A374B077 | SHA256:78223AEF72777EFC93C739F5308A3FC5DE28B7D10E6975B8947552A62592772B | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\_lzma.pyd | executable | |
MD5:66A9028EFD1BB12047DAFCE391FD6198 | SHA256:E44DEA262A24DF69FD9B50B08D09AE6F8B051137CE0834640C977091A6F9FCA8 | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\_socket.pyd | executable | |
MD5:ABF998769F3CBA685E90FA06E0EC8326 | SHA256:62D0493CED6CA33E2FD8141649DD9889C23B2E9AFC5FDF56EDB4F888C88FB823 | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\_bz2.pyd | executable | |
MD5:C17DCB7FC227601471A641EC90E6237F | SHA256:55894B2B98D01F37B9A8CF4DAF926D0161FF23C2FB31C56F9DBBAC3A61932712 | |||
| 5988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5988.49023\config\config.yml | text | |
MD5:289B367A07DBF3553B96B73DD0E30E3B | SHA256:9C9BBFD364465694998803285D3E8935AA1967074FFB843AFB6D17D9F6E1A425 | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 904 | Crush CheckerV1.1.exe | C:\Users\admin\AppData\Local\Temp\_MEI9042\_queue.pyd | executable | |
MD5:955B197C38EA5BD537CE9C7CB2109802 | SHA256:73CADE82EE139459FE5841E5631274FC9CAF7F579418B613F278125435653539 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
27
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.38:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7524 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2284 | CrushChecker.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7524 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2284 | CrushChecker.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | whitelisted |
7444 | CrushChecker.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
7444 | CrushChecker.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.38:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4112 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
blank-f4sm4.in |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2284 | CrushChecker.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2284 | CrushChecker.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
2284 | CrushChecker.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
2284 | CrushChecker.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2284 | CrushChecker.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |