| URL: | https://ci3.googleusercontent.com/mail-sig/AIorK4xXJQ9CRvZBAm45-j12gZ2jmkoKiNS0FAVBSWrTMRBfYvzqk_f17e9GKeMgI-ZcfqntDZEBKzA |
| Full analysis: | https://app.any.run/tasks/35e6835a-1a69-4901-a3a2-b565164eb3bd |
| Verdict: | Malicious activity |
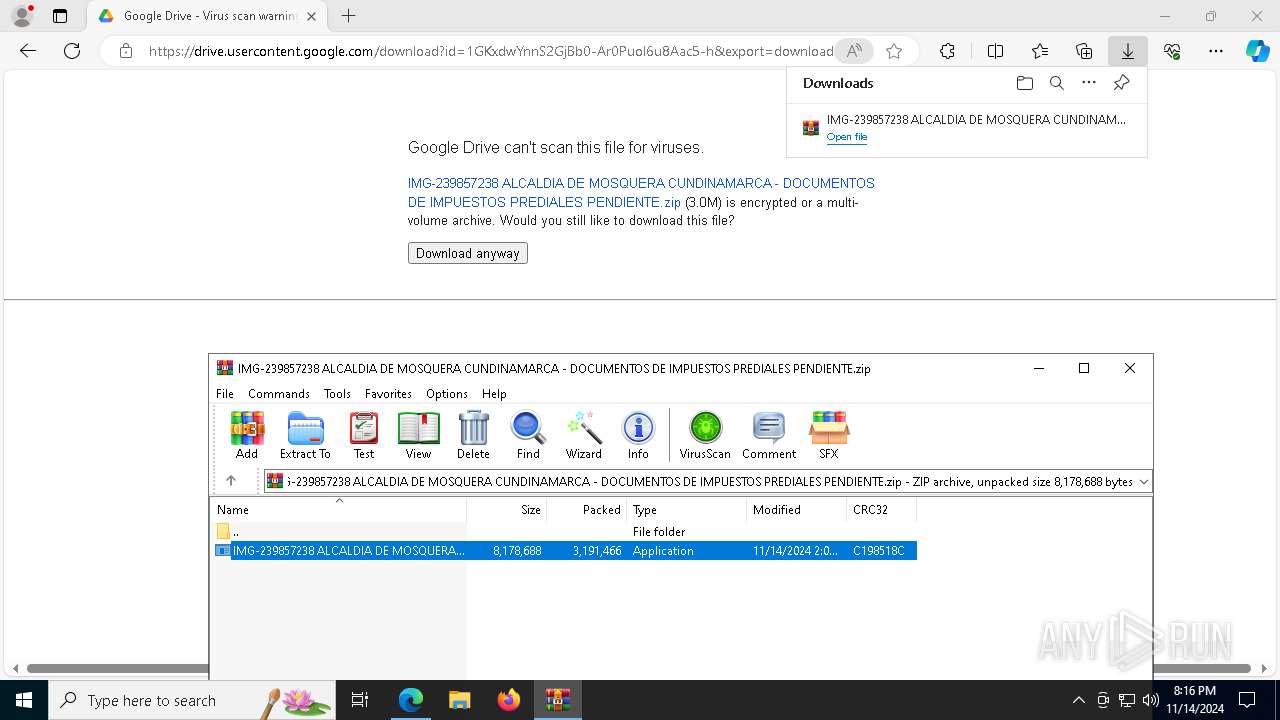
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | November 14, 2024, 20:15:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2933FC98FBFEACCBD53050ADDF8ED9BF |
| SHA1: | 17C4AD30D8D90C7CF0DB2D1F7BD80ABDE139223E |
| SHA256: | 38C8F193A7C1A5EED9D1E64D7C12C2711A8E96850D4FC9F27E66DABCC75725A9 |
| SSDEEP: | 3:N8RWLTPALtGT3Dudy3TGImuN7X5p0TQhC/2:2wLQG2dQGSNLAT2X |
MALICIOUS
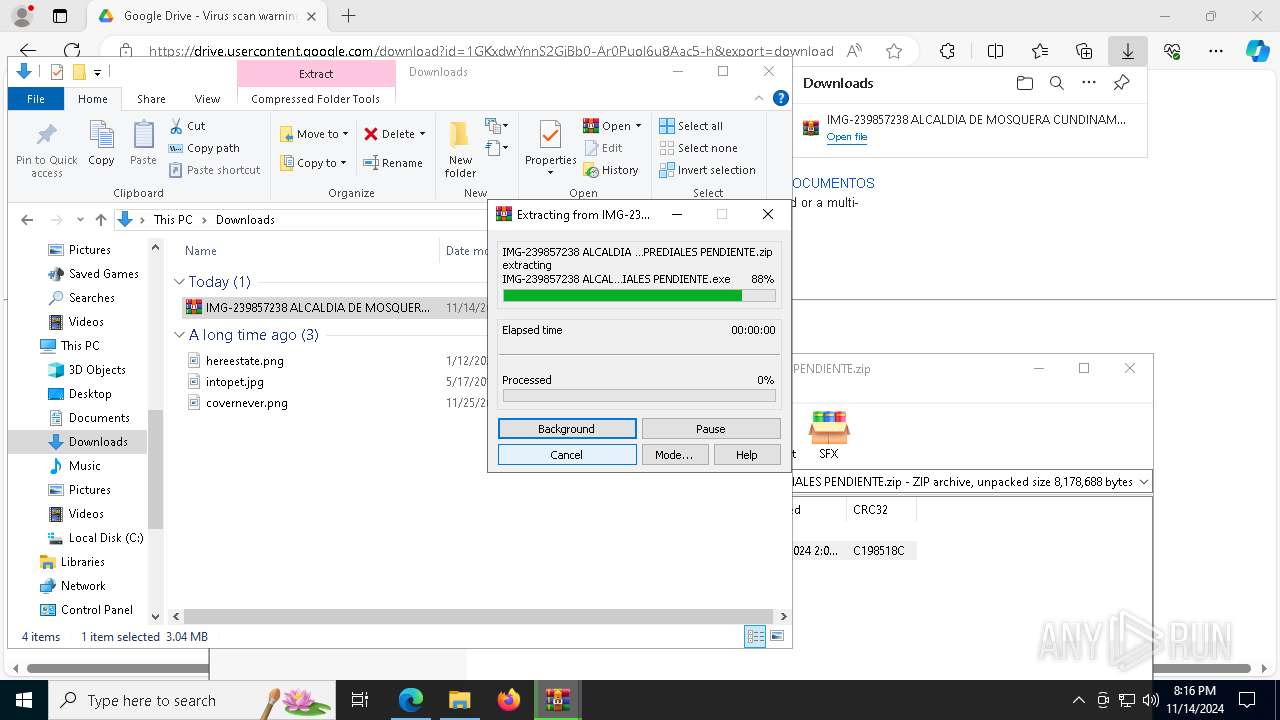
Starts Visual C# compiler
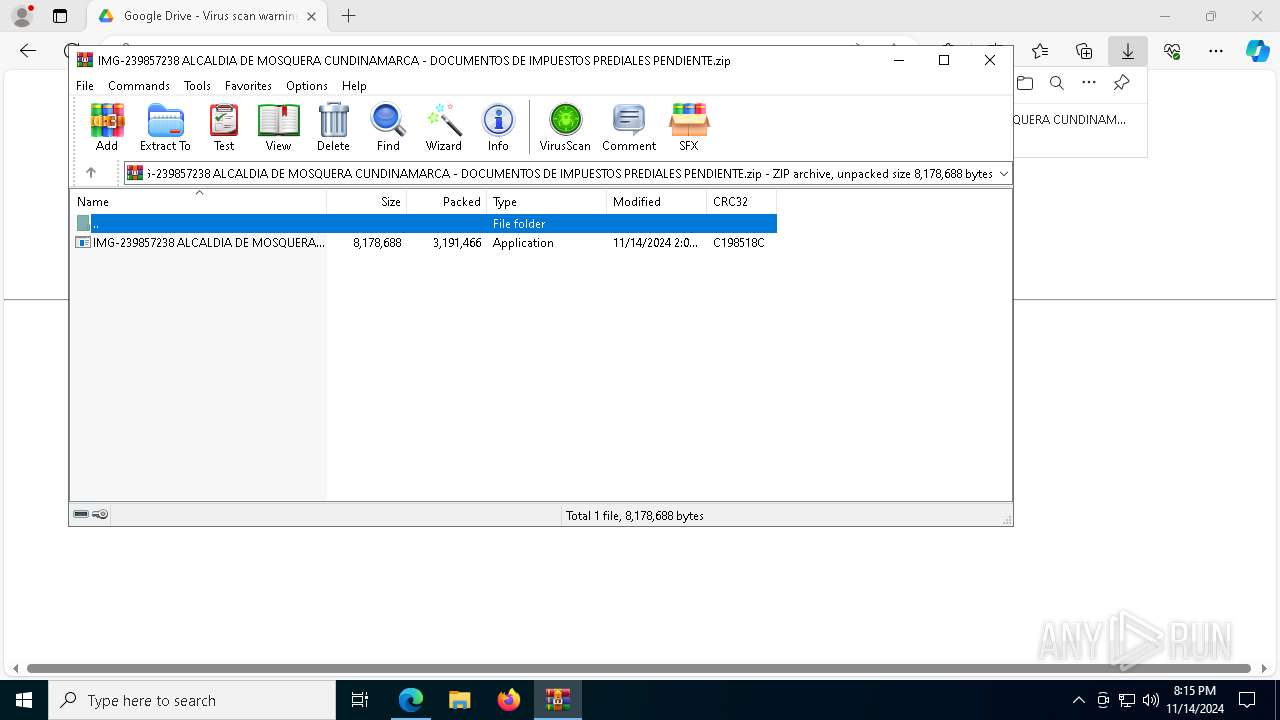
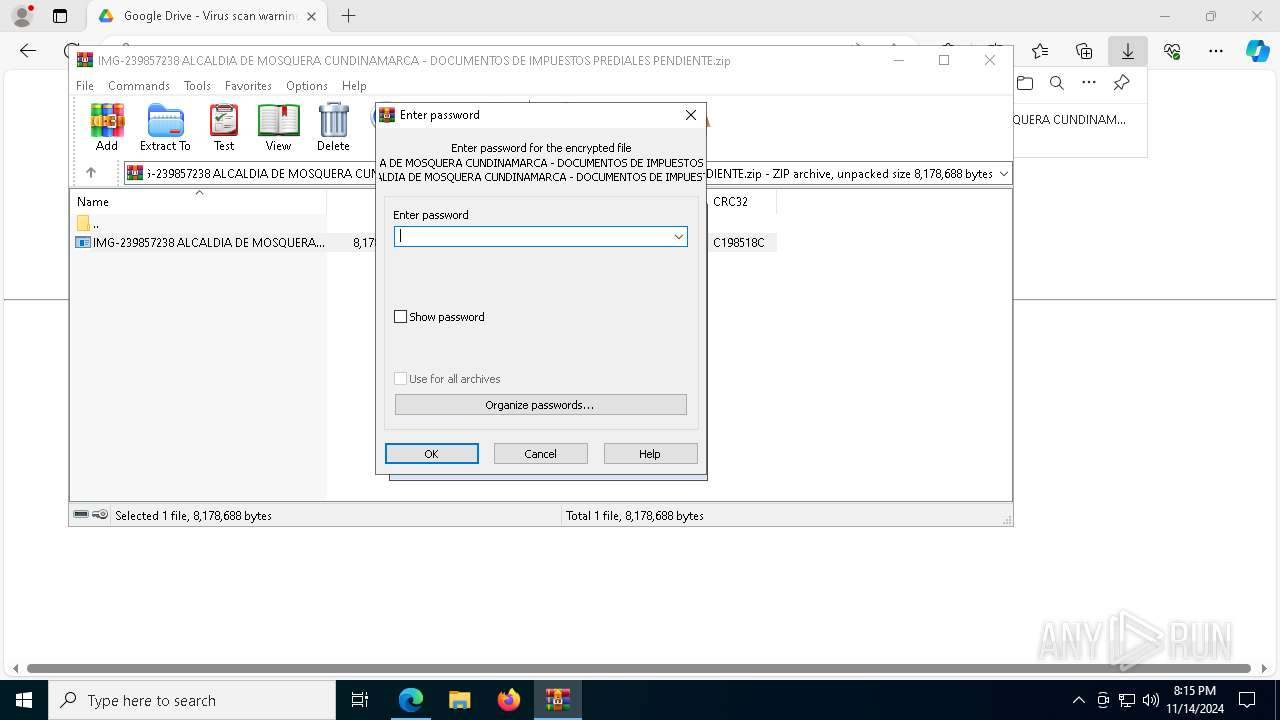
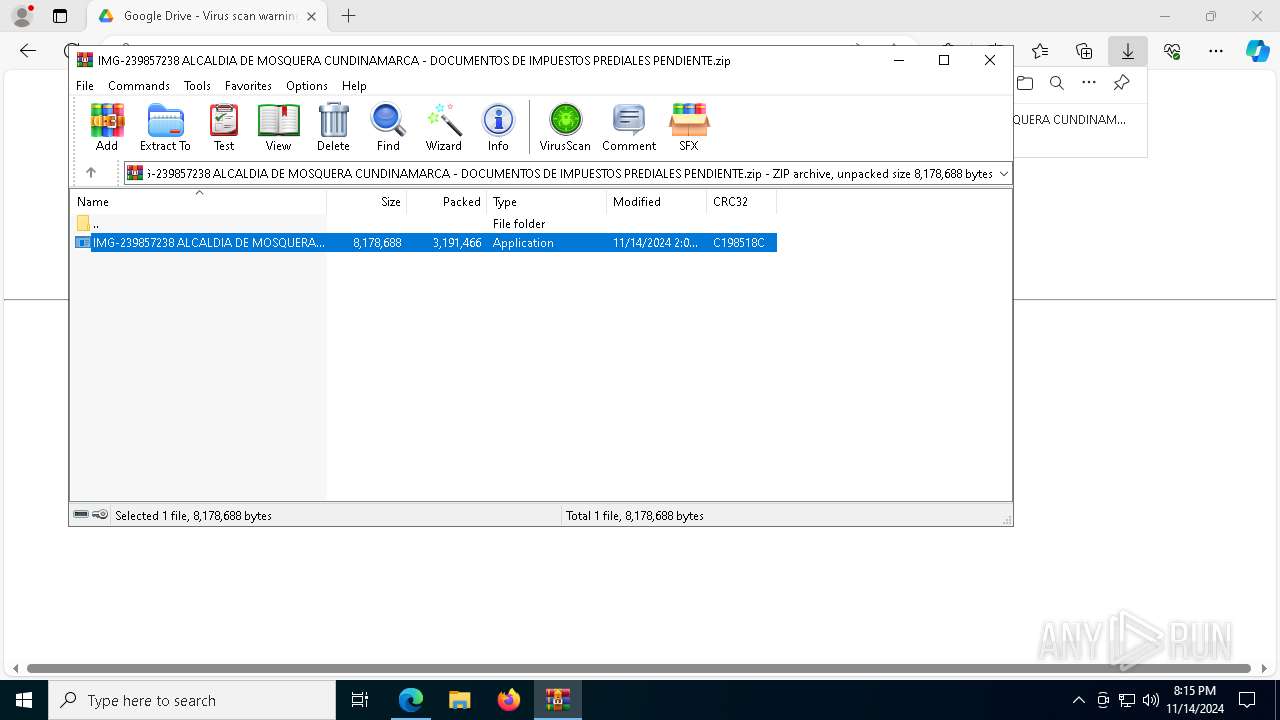
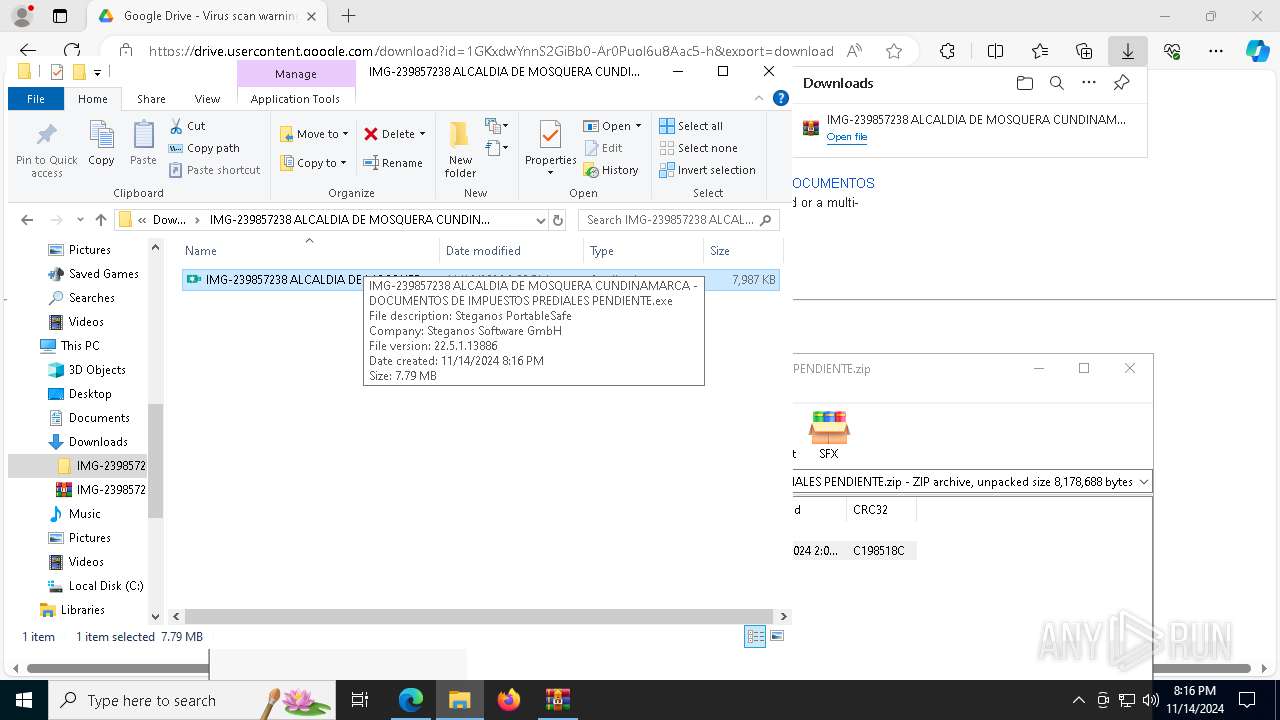
- IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe (PID: 6584)
- IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe (PID: 8072)
- IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe (PID: 7744)
- IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe (PID: 2364)
XWORM has been detected (YARA)
- csc.exe (PID: 8156)
XWORM has been detected (SURICATA)
- csc.exe (PID: 8156)
Connects to the CnC server
- csc.exe (PID: 8156)
SUSPICIOUS
Connects to unusual port
- csc.exe (PID: 8156)
Executable content was dropped or overwritten
- csc.exe (PID: 8156)
Contacting a server suspected of hosting an CnC
- csc.exe (PID: 8156)
Application launched itself
- fgmrrt.exe (PID: 7808)
INFO
Application launched itself
- msedge.exe (PID: 6216)
- msedge.exe (PID: 7112)
Manual execution by a user
- msedge.exe (PID: 6284)
- WinRAR.exe (PID: 1280)
- IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe (PID: 2364)
- IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe (PID: 8072)
- IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe (PID: 7744)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5744)
- WinRAR.exe (PID: 1280)
- msedge.exe (PID: 6972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(8156) csc.exe
C2domingogamarralora09.chickenkiller.com:1887
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.2
MutexNpW5g91wAGxns8rh
Total processes
242
Monitored processes
98
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --mojo-platform-channel-handle=6716 --field-trial-handle=2288,i,13963051318613255442,18039427821350537178,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1008 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5532 --field-trial-handle=2288,i,13963051318613255442,18039427821350537178,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 | |||||||||||||||
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7304 --field-trial-handle=2288,i,13963051318613255442,18039427821350537178,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1280 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1440 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2664 --field-trial-handle=2436,i,10525654458050505447,13901517579211322702,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7064 --field-trial-handle=2288,i,13963051318613255442,18039427821350537178,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | IMG-239857238 ALCALDIA DE MOSQUERA CUNDINAMARCA - DOCUMENTOS DE IMPUESTOS PREDIALES PENDIENTE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3608 --field-trial-handle=2436,i,10525654458050505447,13901517579211322702,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=4296 --field-trial-handle=2288,i,13963051318613255442,18039427821350537178,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
13 391
Read events
13 318
Write events
60
Delete events
13
Modification events
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8379A3637B852F00 | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 5D4AAB637B852F00 | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328256 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {34DE8529-FDBE-4F05-B1C6-F29F986C2205} | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328256 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {35029BEB-9355-4F3B-A4DE-90B6CB60EA13} | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 4341DC637B852F00 | |||
| (PID) Process: | (6216) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
12
Suspicious files
1 012
Text files
209
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF8b29f.TMP | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF8b29f.TMP | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF8b29f.TMP | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF8b29f.TMP | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF8b29f.TMP | — | |
MD5:— | SHA256:— | |||
| 6216 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
127
DNS requests
138
Threats
53
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2420 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8e66c1e5-210a-491f-9c6d-8c3fc4d9c3eb?P1=1731862761&P2=404&P3=2&P4=XgoI36eEtOgWrvrAFLBU7YMaCKGicvnneATjzQ%2fuYU7JlJ1o1RrJH4GfHeSGH9yQCdlFyIMkRLvUY8Ba33cR9w%3d%3d | unknown | — | — | whitelisted |
8156 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7304 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8156 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2420 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8e66c1e5-210a-491f-9c6d-8c3fc4d9c3eb?P1=1731862761&P2=404&P3=2&P4=XgoI36eEtOgWrvrAFLBU7YMaCKGicvnneATjzQ%2fuYU7JlJ1o1RrJH4GfHeSGH9yQCdlFyIMkRLvUY8Ba33cR9w%3d%3d | unknown | — | — | whitelisted |
2420 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/8e66c1e5-210a-491f-9c6d-8c3fc4d9c3eb?P1=1731862761&P2=404&P3=2&P4=XgoI36eEtOgWrvrAFLBU7YMaCKGicvnneATjzQ%2fuYU7JlJ1o1RrJH4GfHeSGH9yQCdlFyIMkRLvUY8Ba33cR9w%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.25:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6216 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6044 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6044 | msedge.exe | 172.217.18.1:443 | ci3.googleusercontent.com | — | — | whitelisted |
6044 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6044 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6044 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
ci3.googleusercontent.com |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.chickenkiller .com Domain |
8156 | csc.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm TCP Packet |
— | — | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.freeddns .org Domain |
— | — | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
— | — | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |
48 ETPRO signatures available at the full report