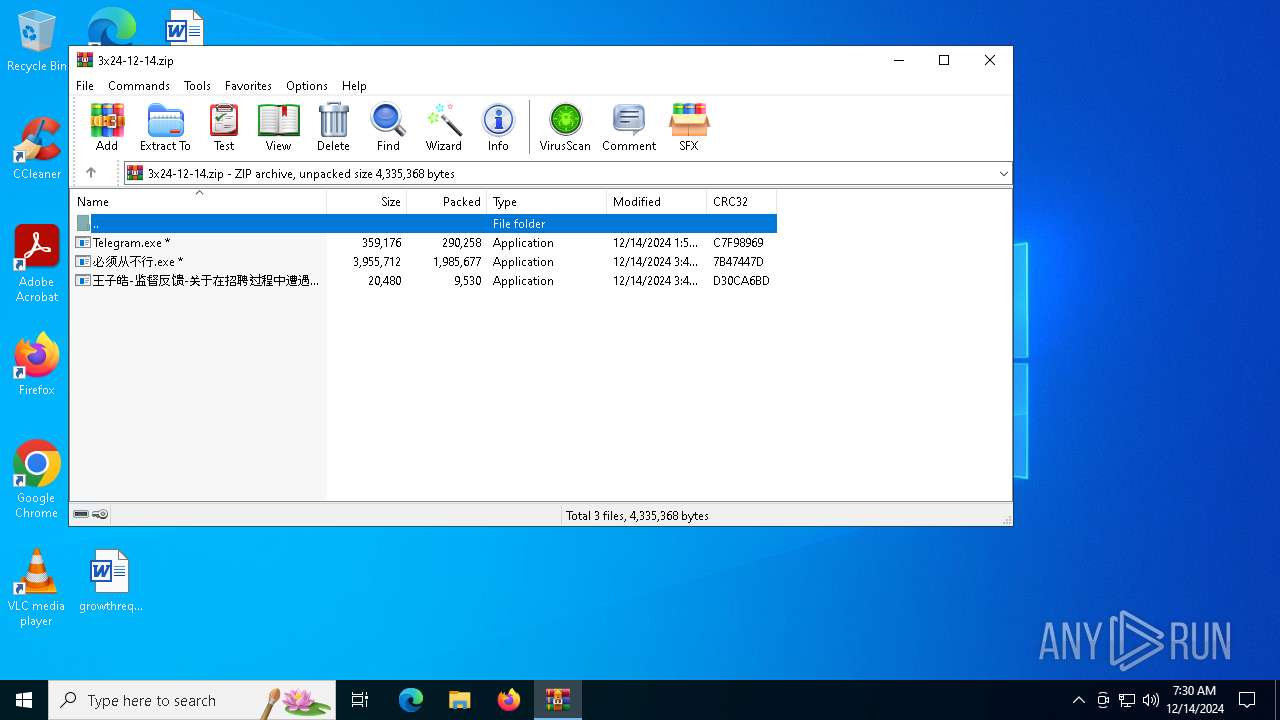
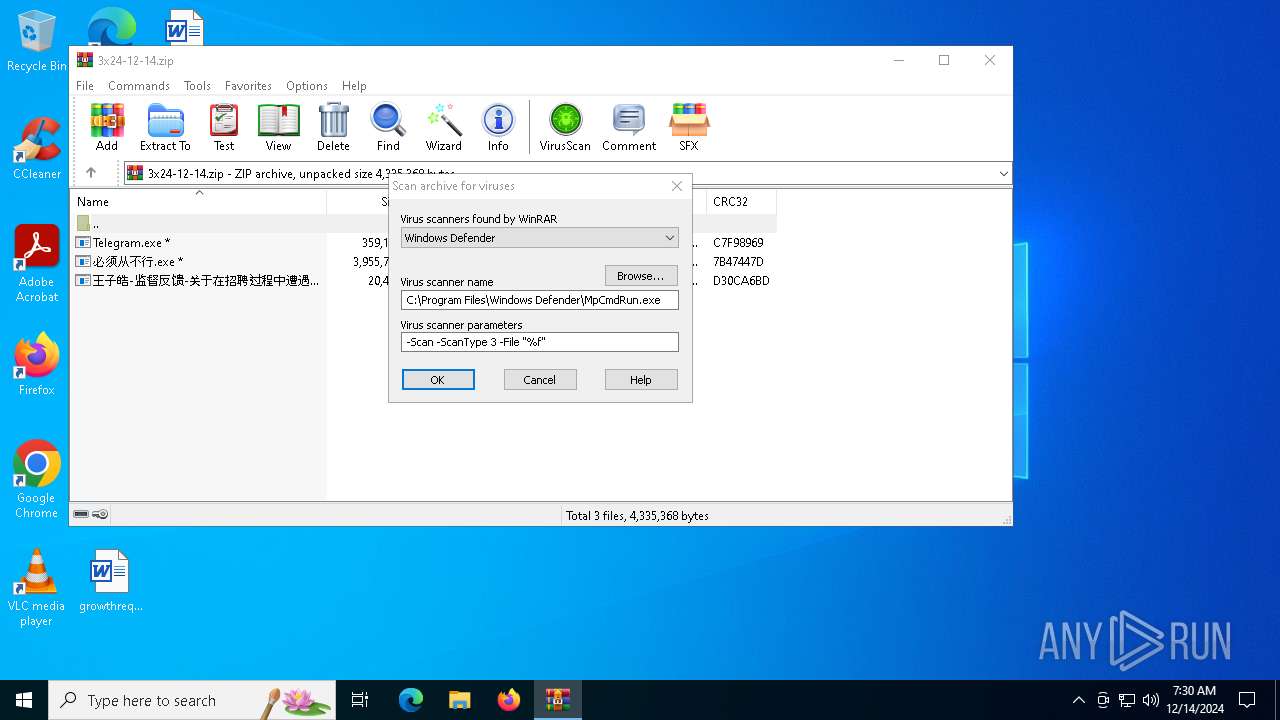
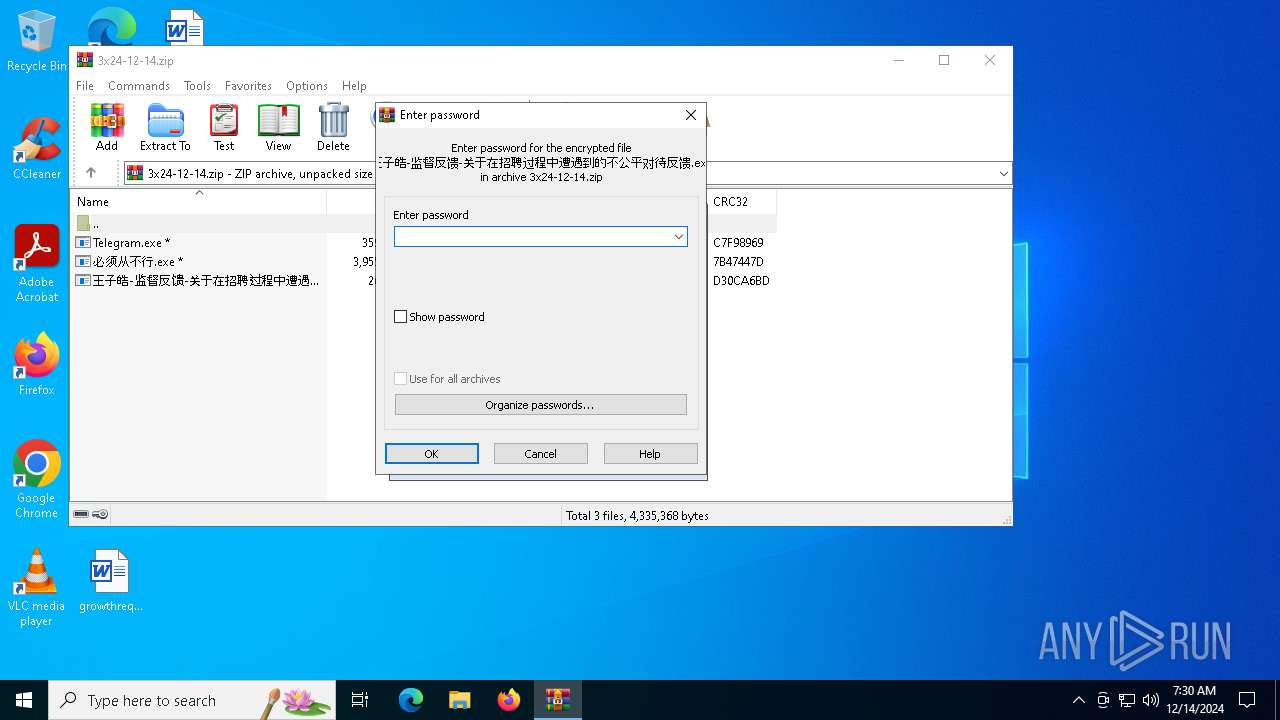
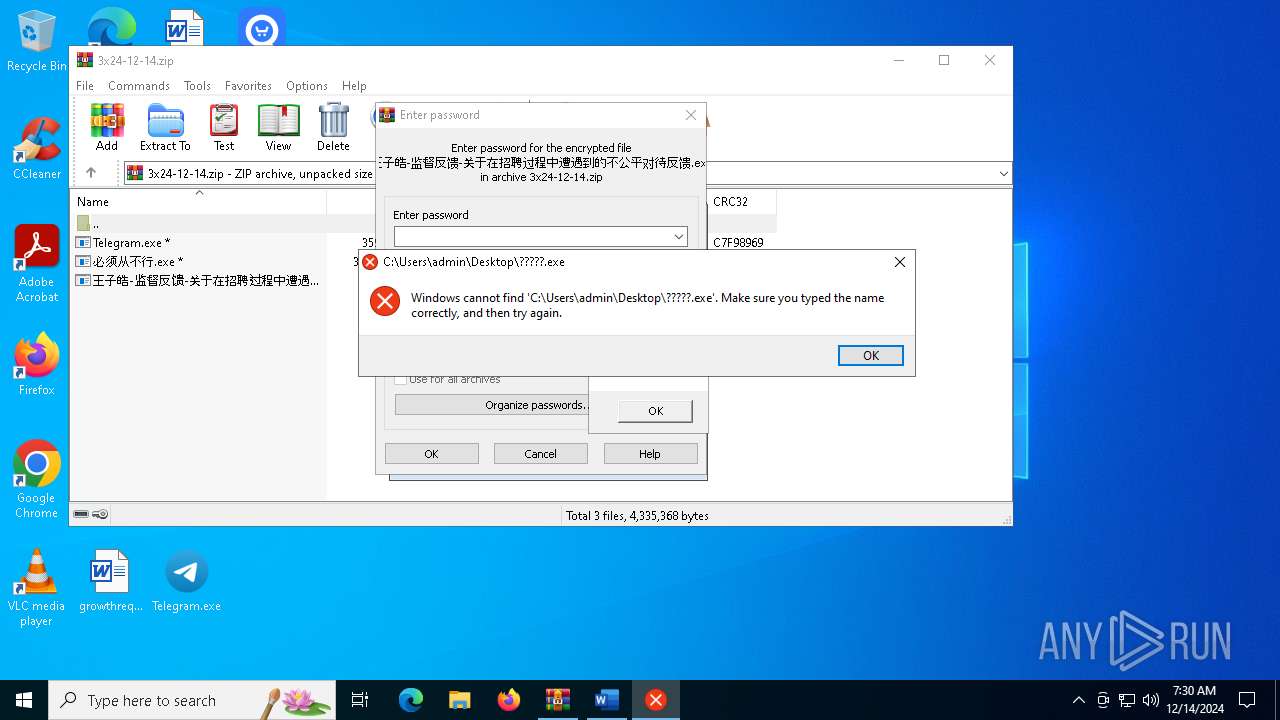
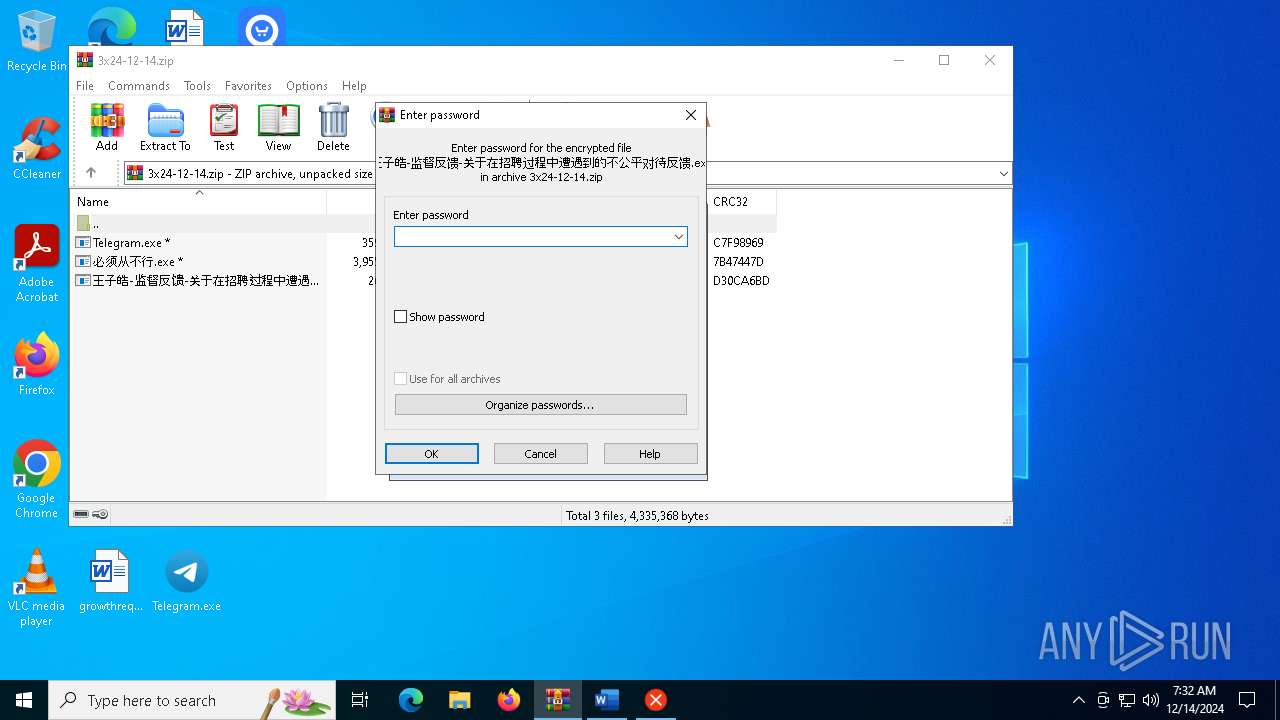
| File name: | 3x24-12-14.zip |
| Full analysis: | https://app.any.run/tasks/e23ce71d-e8f5-4841-9d1f-4642c8c8a8cd |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | December 14, 2024, 07:30:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
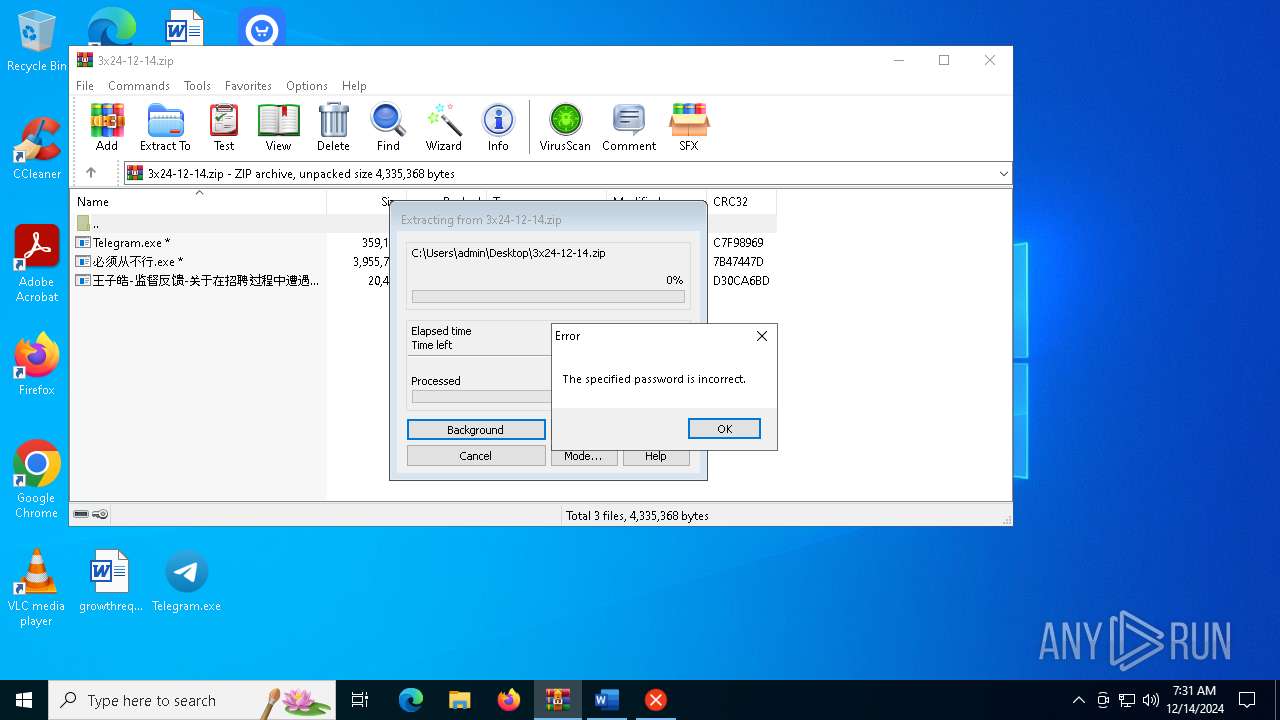
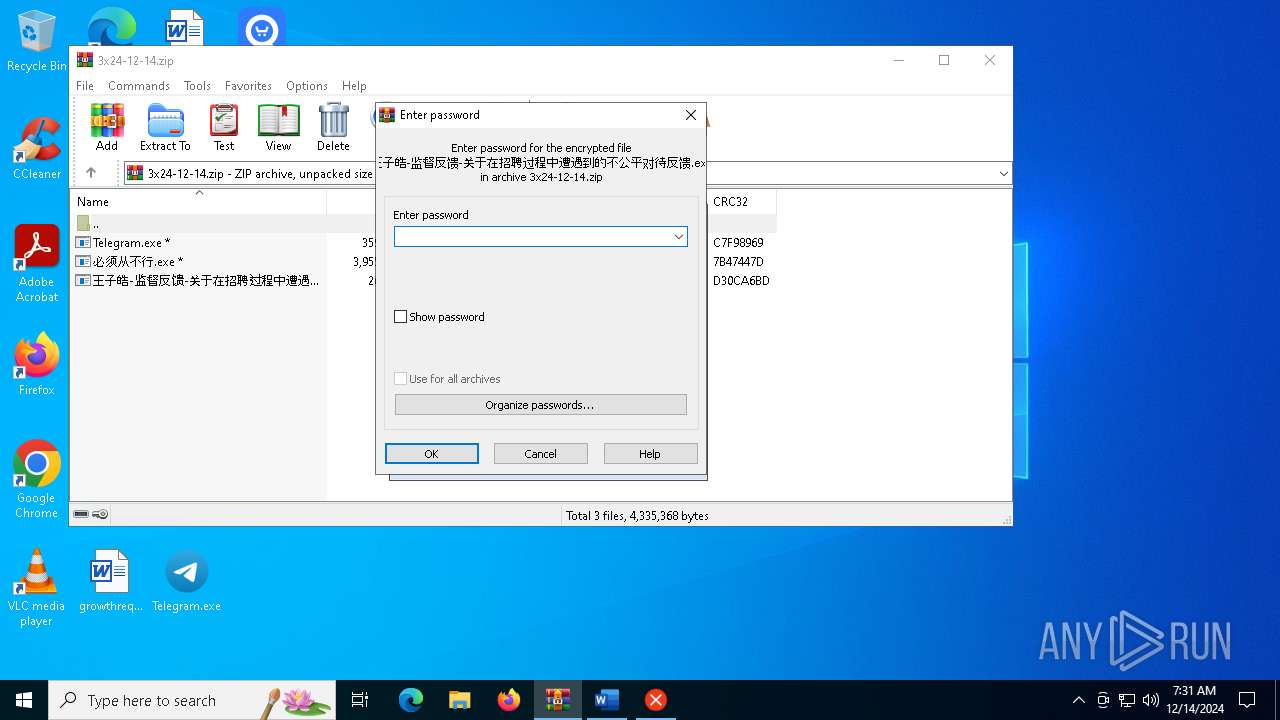
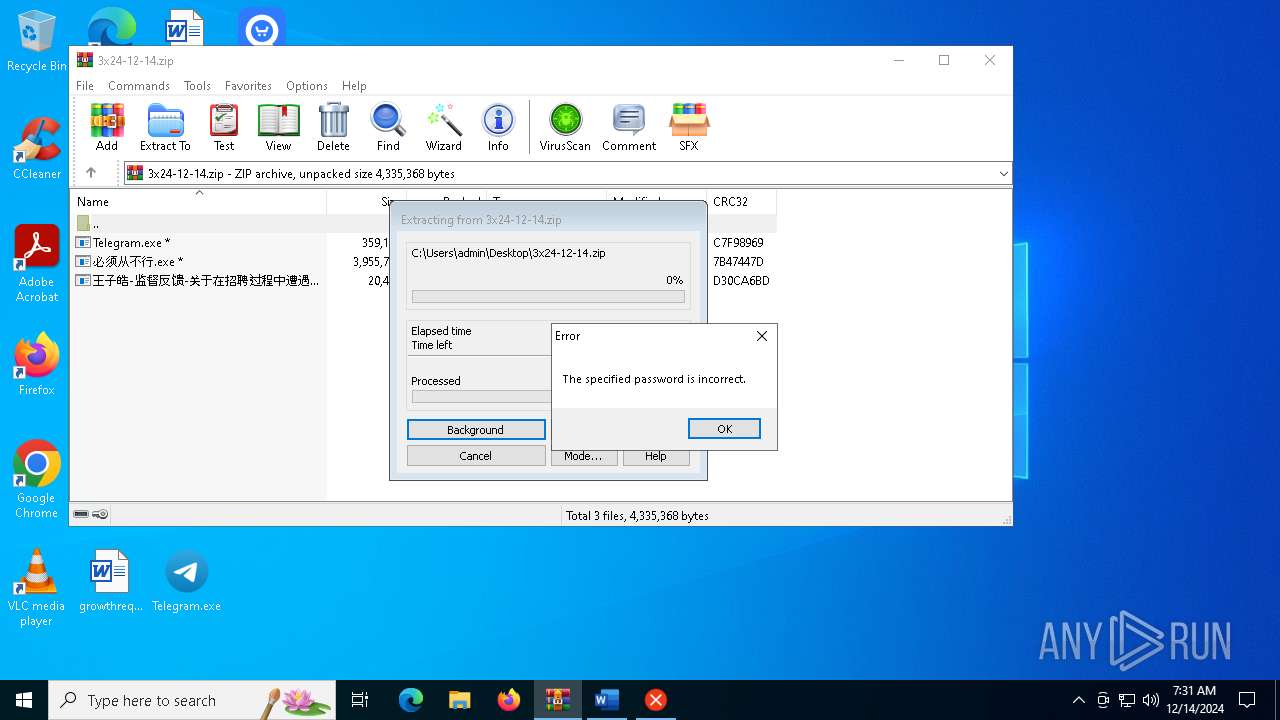
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 822AAF1D2944A55EC5601C8A123CD7BD |
| SHA1: | 9BCE8204060F4C6146BBABF4509B75D8BD6A87D2 |
| SHA256: | 38C68D9BF561E61B7AC46E5CFA6BF5F92C866340898A71D5530ED995C4A4DA2F |
| SSDEEP: | 98304:s5PP/NnQ92oWveMHLqq6qx1iIpA/bN7KDkfCxgWIWVQp0Oq6FMIeQ7pHFhIx7P2m:CbGO |
MALICIOUS
Executing a file with an untrusted certificate
- Telegram.exe (PID: 4628)
COBALTSTRIKE has been detected (YARA)
- Telegram.exe (PID: 4628)
SUSPICIOUS
Reads security settings of Internet Explorer
- Telegram.exe (PID: 4628)
Checks Windows Trust Settings
- Telegram.exe (PID: 4628)
INFO
Reads the computer name
- 王子皓-监督反馈-关于在招聘过程中遭遇到的不公平对待反馈.exe (PID: 4876)
- Telegram.exe (PID: 4628)
- 必须从不行.exe (PID: 5972)
The sample compiled with english language support
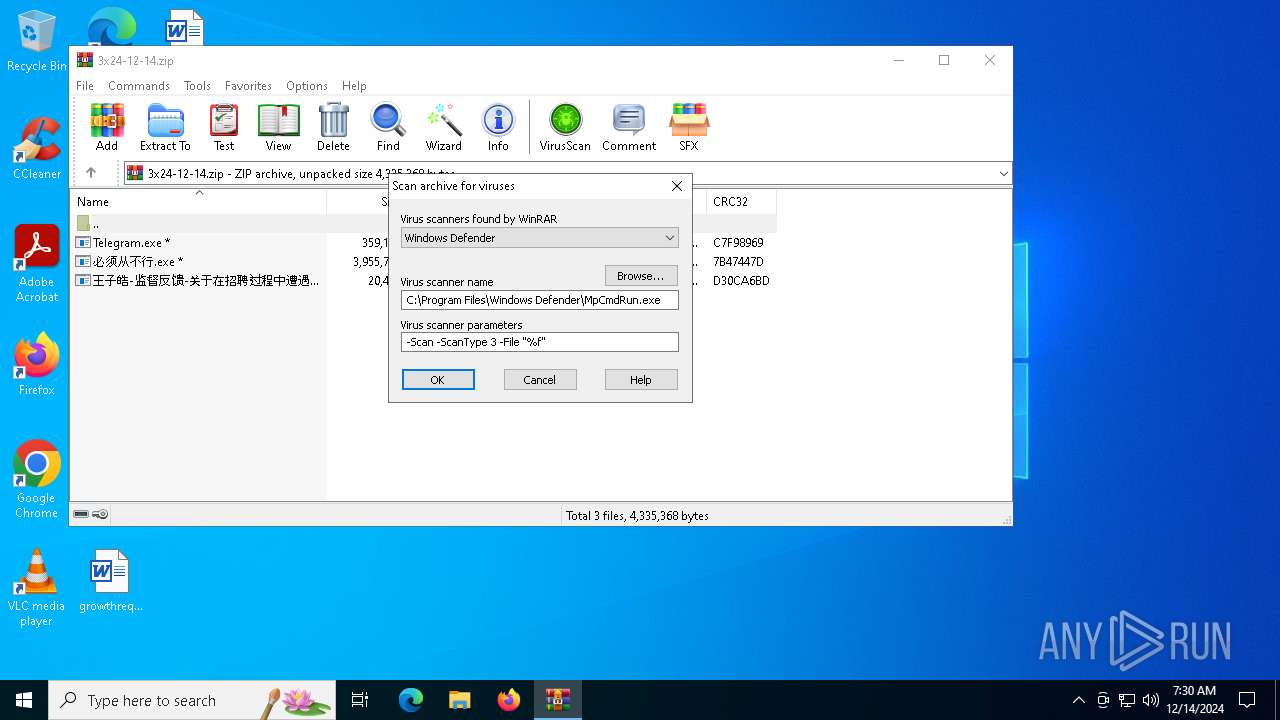
- WinRAR.exe (PID: 6096)
Manual execution by a user
- 王子皓-监督反馈-关于在招聘过程中遭遇到的不公平对待反馈.exe (PID: 4876)
- Telegram.exe (PID: 4628)
- 必须从不行.exe (PID: 5972)
Checks supported languages
- 王子皓-监督反馈-关于在招聘过程中遭遇到的不公平对待反馈.exe (PID: 4876)
- Telegram.exe (PID: 4628)
- 必须从不行.exe (PID: 5972)
The process uses the downloaded file
- WinRAR.exe (PID: 6096)
Reads the machine GUID from the registry
- Telegram.exe (PID: 4628)
Checks proxy server information
- Telegram.exe (PID: 4628)
Reads the software policy settings
- Telegram.exe (PID: 4628)
Create files in a temporary directory
- 必须从不行.exe (PID: 5972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:12:14 11:46:32 |
| ZipCRC: | 0xd30ca6bd |
| ZipCompressedSize: | 9530 |
| ZipUncompressedSize: | 20480 |
| ZipFileName: | ??????-?ල????-????????Ƹ?????????????IJ???ƽ?Դ?????.exe |
Total processes
123
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4628 | "C:\Users\admin\Desktop\Telegram.exe" | C:\Users\admin\Desktop\Telegram.exe | explorer.exe | ||||||||||||
User: admin Company: Telegram FZ-LLC Integrity Level: MEDIUM Description: Telegram Desktop Version: 5.8.3.0 Modules
| |||||||||||||||
| 4876 | "C:\Users\admin\Desktop\王子皓-监督反馈-关于在招聘过程中遭遇到的不公平对待反馈.exe" | C:\Users\admin\Desktop\王子皓-监督反馈-关于在招聘过程中遭遇到的不公平对待反馈.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5972 | "C:\Users\admin\Desktop\必须从不行.exe" | C:\Users\admin\Desktop\必须从不行.exe | — | explorer.exe | |||||||||||
User: admin Company: TODO: <Company name> Integrity Level: MEDIUM Description: SunloginClient Version: 1.0.0.1 Modules
| |||||||||||||||
| 6096 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\3x24-12-14.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
5 159
Read events
5 143
Write events
16
Delete events
0
Modification events
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\3x24-12-14.zip | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (6096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Notifications |
| Operation: | write | Name: | NotifyPswMan |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
18
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 74.48.129.165:443 | https://74.48.129.165/jquery-3.3.1.min.js | unknown | binary | 5.52 Kb | unknown |
— | — | GET | 200 | 74.48.129.165:443 | https://74.48.129.165/jquery-3.3.1.min.js | unknown | binary | 5.52 Kb | unknown |
— | — | GET | 200 | 74.48.129.165:443 | https://74.48.129.165/jquery-3.3.1.min.js | unknown | binary | 5.48 Kb | unknown |
— | — | GET | 200 | 74.48.129.165:443 | https://74.48.129.165/jquery-3.3.1.min.js | unknown | binary | 5.58 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
3000 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6032 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3000 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4628 | Telegram.exe | 74.48.129.165:443 | — | — | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |