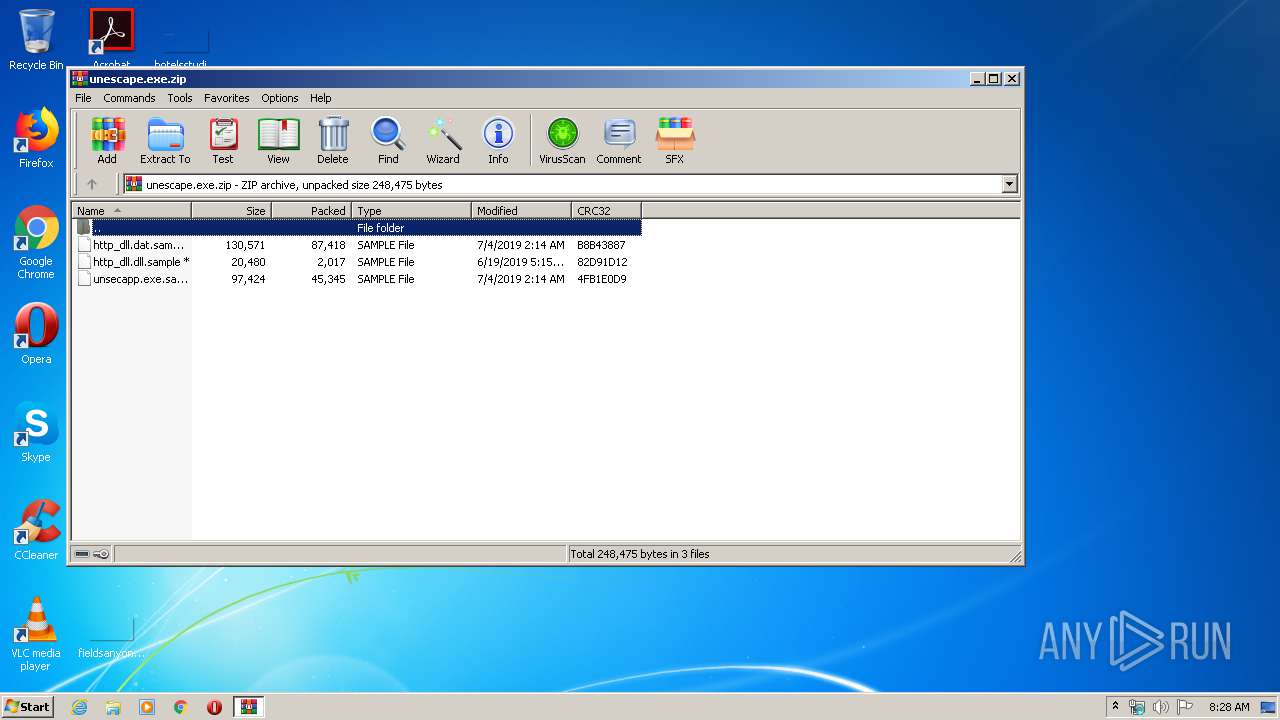
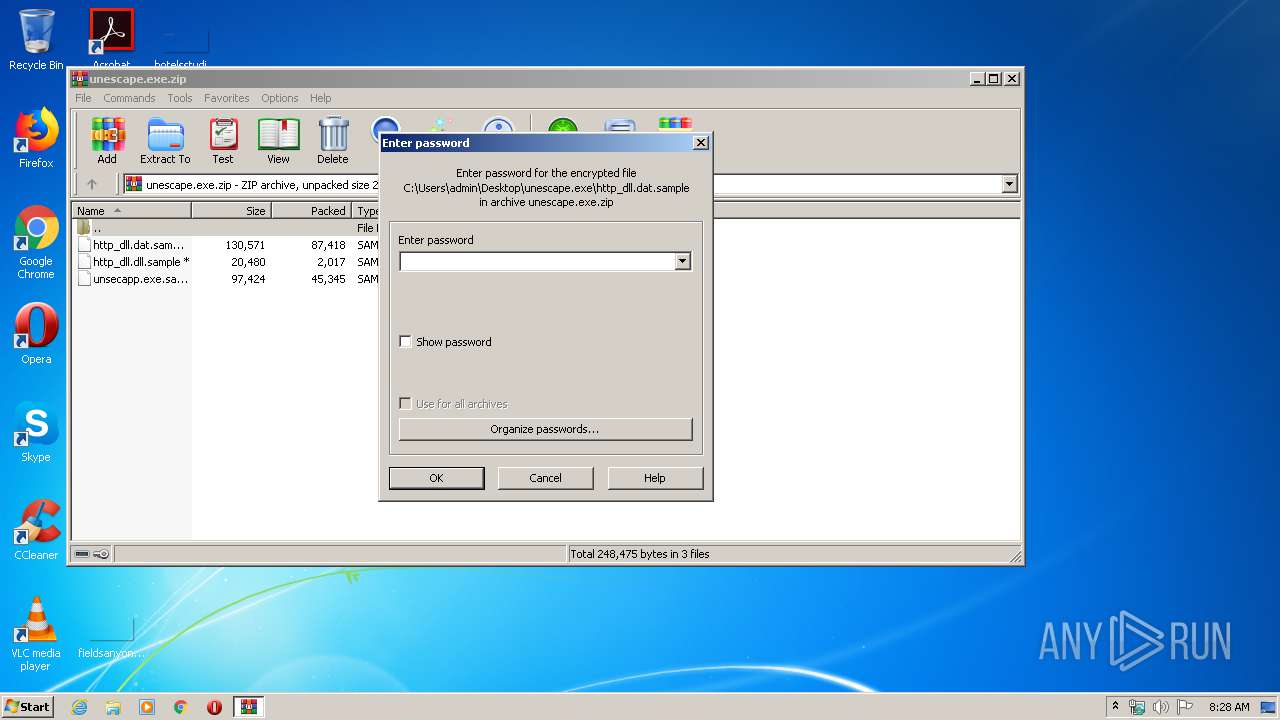
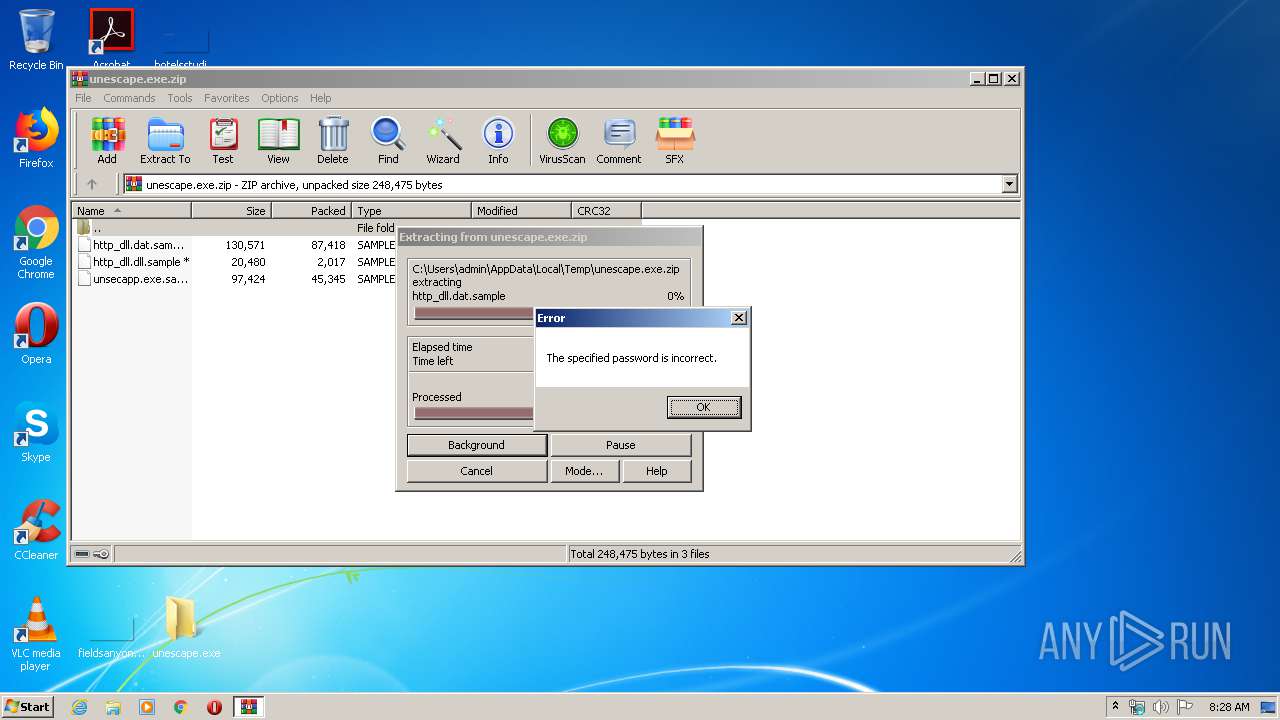
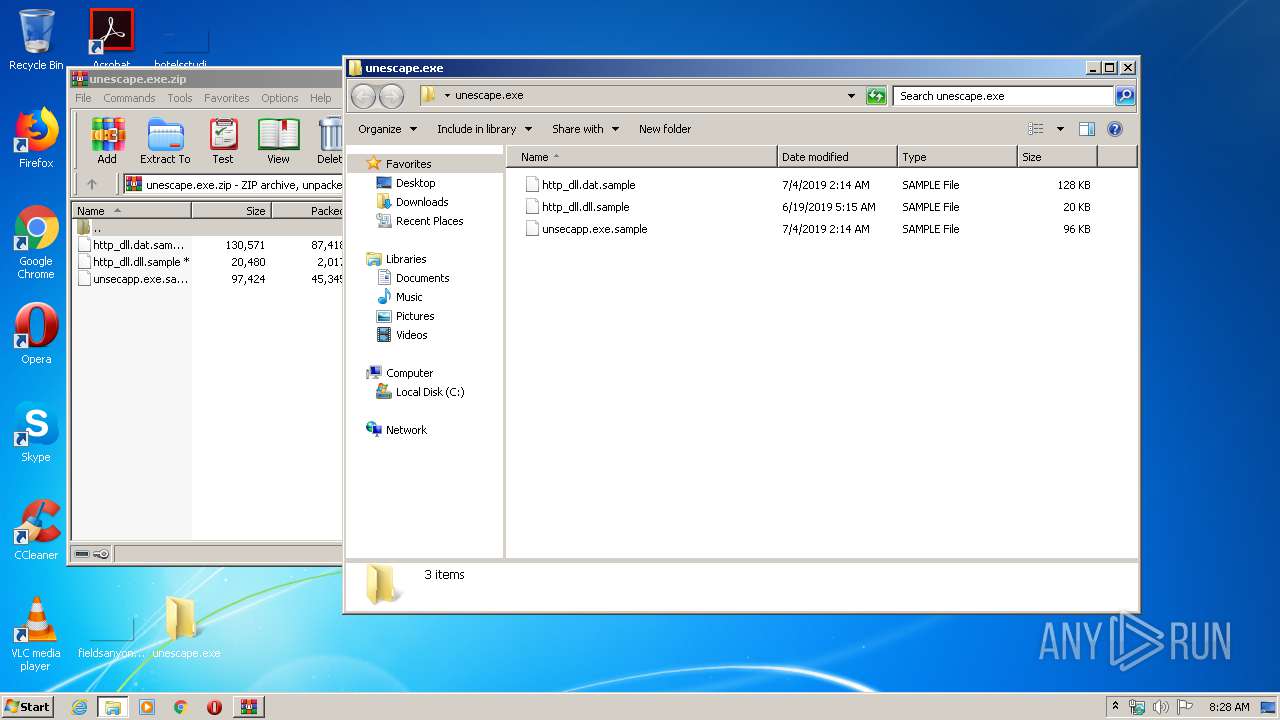
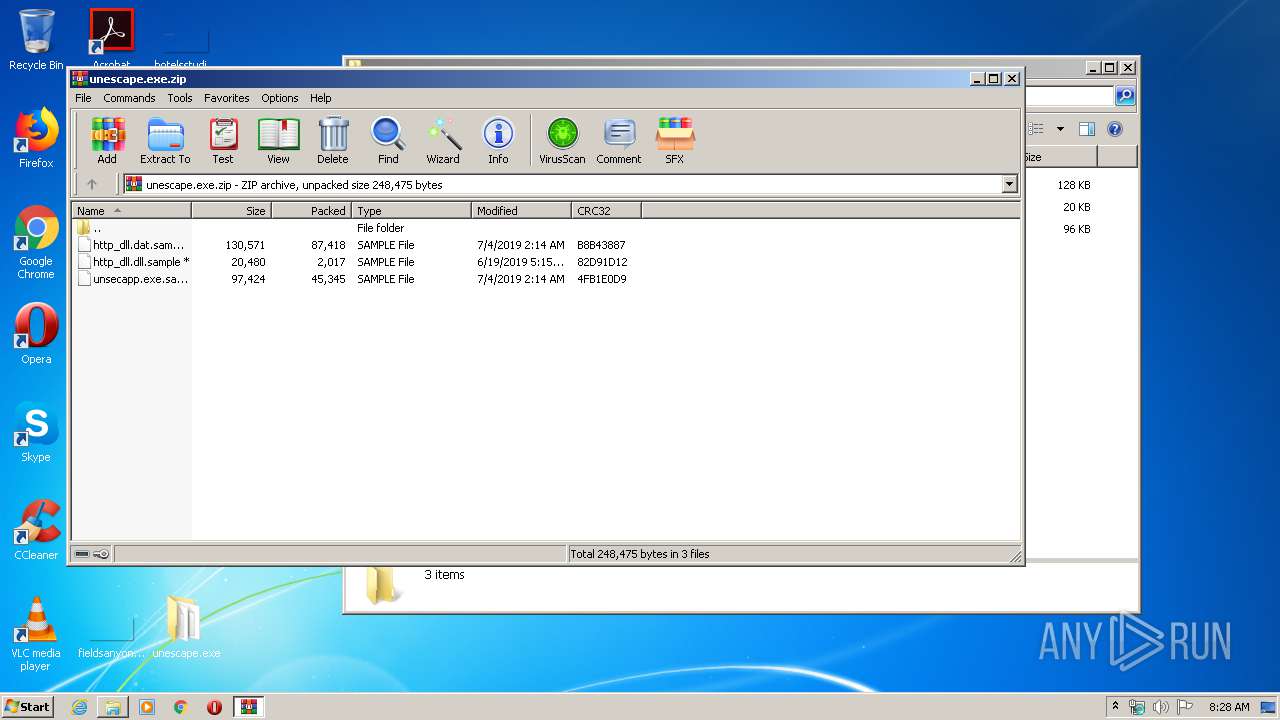
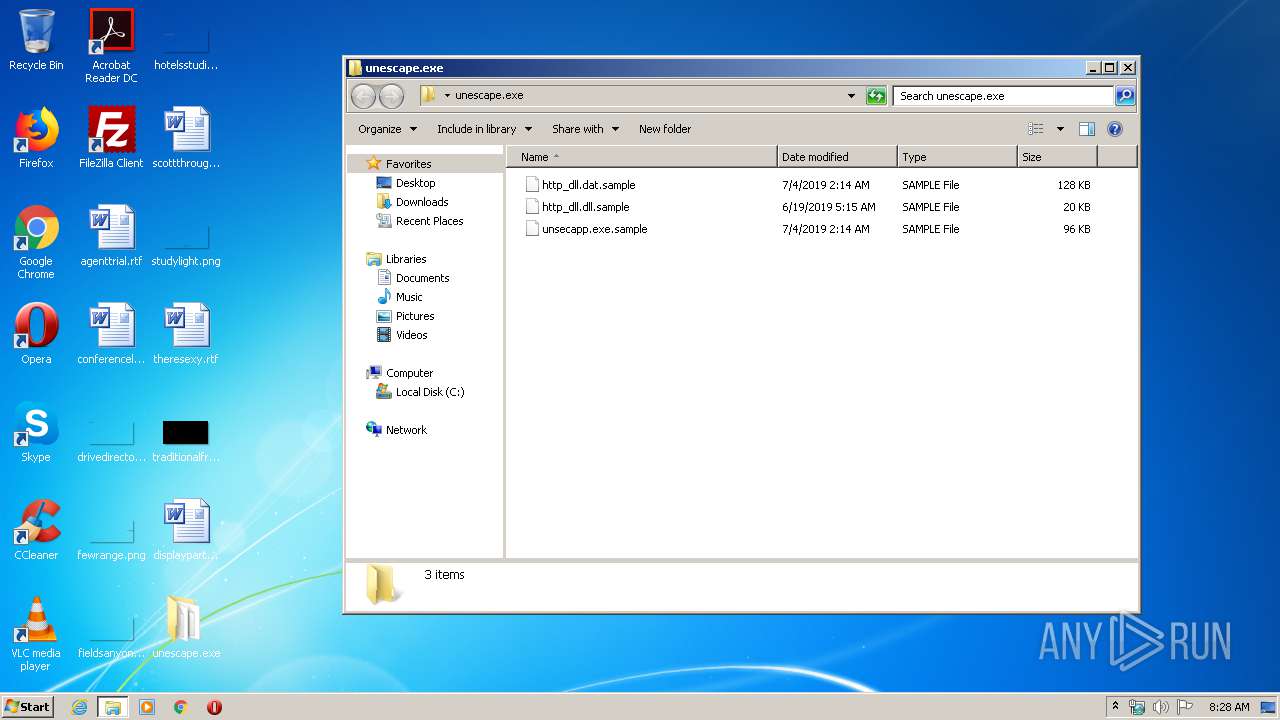
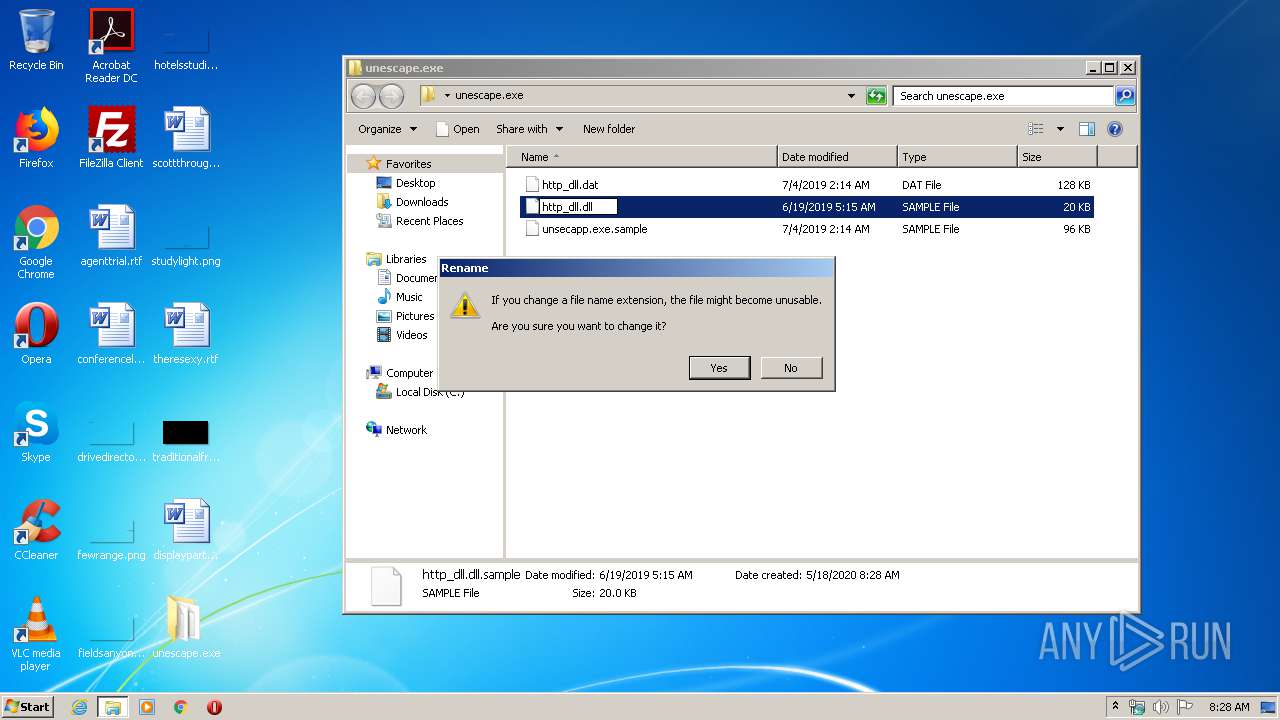
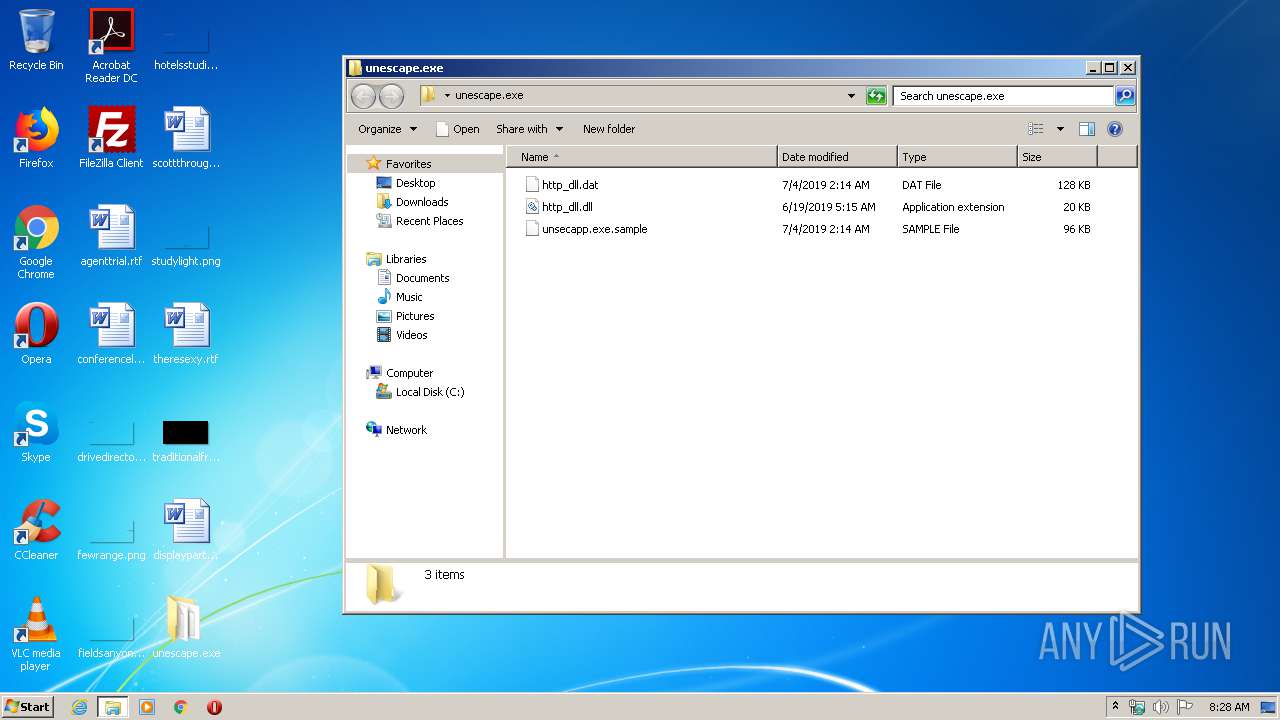
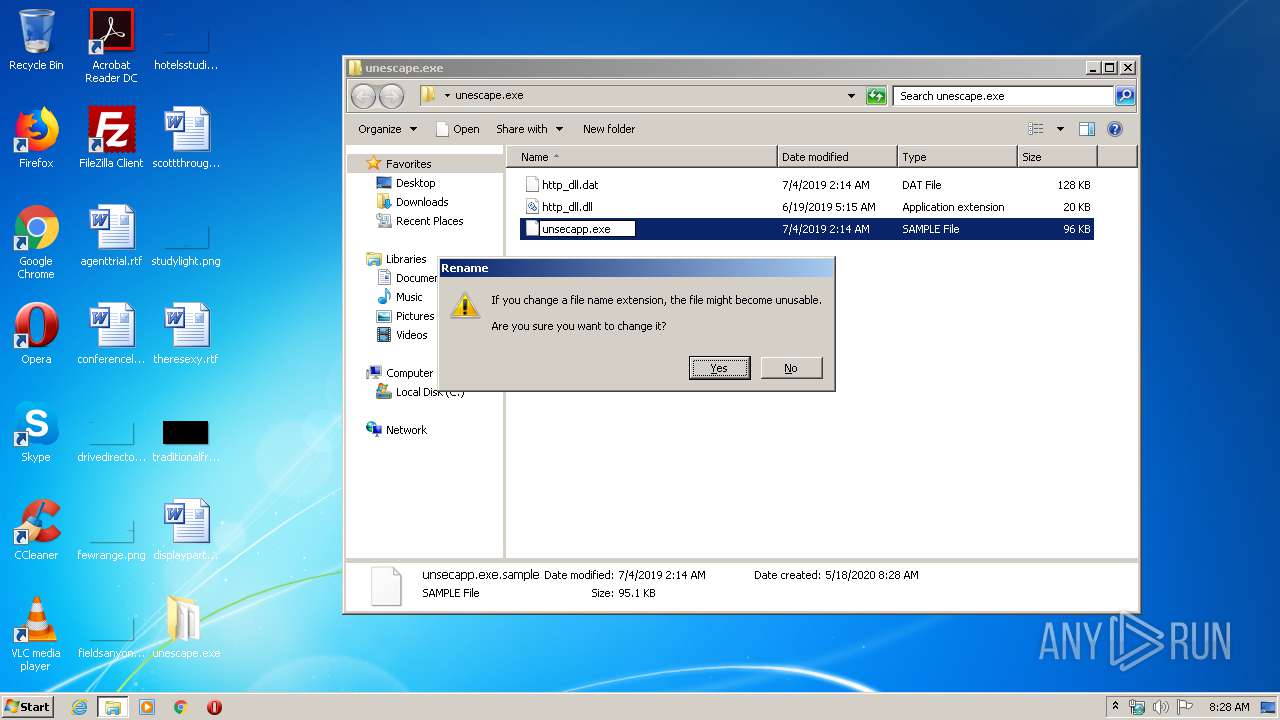
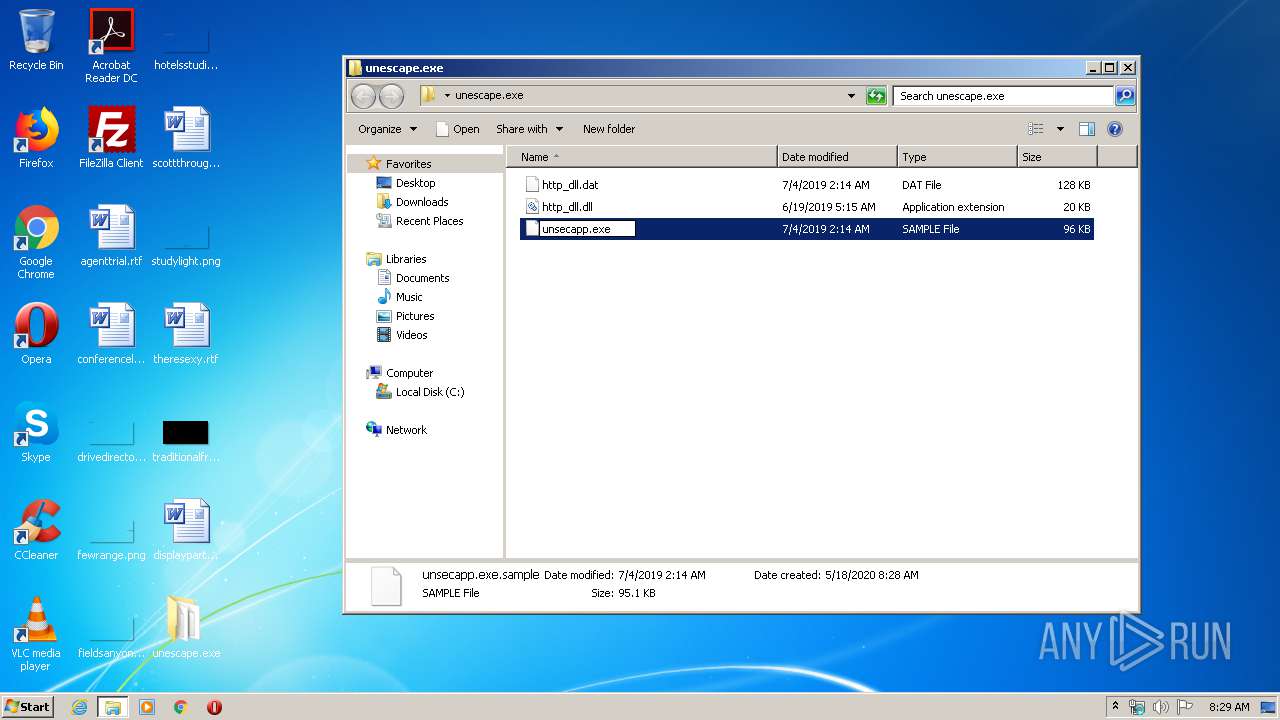
| File name: | unescape.exe.zip |
| Full analysis: | https://app.any.run/tasks/7b38bab5-c4c9-43dd-8380-b3bca0cfaaf1 |
| Verdict: | Malicious activity |
| Threats: | PlugX is a remote access trojan that is used extensively by Chinese APTs. The malware is primarily employed for spying on victims and can perform a variety of malicious activities, such as logging users’ keystrokes and exfiltrating information from browsers. |
| Analysis date: | May 18, 2020, 07:28:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | C00DB0270D1B433D4006BA09000FE8D9 |
| SHA1: | 0BD650F3C3753434B8C30DCC50551B7F500BB95E |
| SHA256: | 38629FB94F89D2504E1582679F82960BF343143C624A148B923D9CF4AA4DB0B7 |
| SSDEEP: | 1536:w4krgUXKa8KlwFZAdU2vdvdBJGcPJqM8oWV/ArZHJx+VCz6glmmo5cvIGh/FWxKV:/QAKlwobtBGPhVIBCkJ/FWxZyEkmHDcl |
MALICIOUS
Application was dropped or rewritten from another process
- unsecapp.exe (PID: 2564)
- unsecapp.exe (PID: 3896)
Changes the autorun value in the registry
- unsecapp.exe (PID: 3896)
Loads dropped or rewritten executable
- unsecapp.exe (PID: 3896)
- unsecapp.exe (PID: 2564)
- SearchProtocolHost.exe (PID: 2648)
PLUGX was detected
- unsecapp.exe (PID: 2564)
Connects to CnC server
- unsecapp.exe (PID: 2564)
SUSPICIOUS
Creates files in the program directory
- unsecapp.exe (PID: 3896)
Reads Internet Cache Settings
- unsecapp.exe (PID: 2564)
Executable content was dropped or overwritten
- unsecapp.exe (PID: 3896)
- WinRAR.exe (PID: 3448)
INFO
Manual execution by user
- unsecapp.exe (PID: 3896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:07:04 08:14:03 |
| ZipCRC: | 0xb8b43887 |
| ZipCompressedSize: | 87418 |
| ZipUncompressedSize: | 130571 |
| ZipFileName: | http_dll.dat.sample |
Total processes
46
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2564 | "C:\ProgramData\Microsoft Malware ProtectionbOr\unsecapp.exe" 6 | C:\ProgramData\Microsoft Malware ProtectionbOr\unsecapp.exe | unsecapp.exe | ||||||||||||
User: admin Company: ESET Integrity Level: MEDIUM Description: ESET HTTP Server Service Exit code: 0 Version: 5.0.511.0 Modules
| |||||||||||||||
| 2648 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\unescape.exe.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3896 | "C:\Users\admin\Desktop\unescape.exe\unsecapp.exe" | C:\Users\admin\Desktop\unescape.exe\unsecapp.exe | explorer.exe | ||||||||||||
User: admin Company: ESET Integrity Level: MEDIUM Description: ESET HTTP Server Service Exit code: 0 Version: 5.0.511.0 Modules
| |||||||||||||||
Total events
875
Read events
842
Write events
33
Delete events
0
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\unescape.exe.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\unescape.exe | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
4
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\unescape.exe\http_dll.dll.sample | executable | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\unescape.exe\http_dll.dat.sample | binary | |
MD5:— | SHA256:— | |||
| 3896 | unsecapp.exe | C:\ProgramData\Microsoft Malware ProtectionbOr\http_dll.dll | executable | |
MD5:— | SHA256:— | |||
| 3896 | unsecapp.exe | C:\ProgramData\Microsoft Malware ProtectionbOr\http_dll.dat | binary | |
MD5:— | SHA256:— | |||
| 3896 | unsecapp.exe | C:\ProgramData\Microsoft Malware ProtectionbOr\unsecapp.exe | executable | |
MD5:28C6F235946FD694D2634C7A2F24C1BA | SHA256:C3159D4F85CEB84C4A0F7EA9208928E729A30DDDA4FEAD7EC6257C7DD1984763 | |||
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\unescape.exe\unsecapp.exe.sample | executable | |
MD5:28C6F235946FD694D2634C7A2F24C1BA | SHA256:C3159D4F85CEB84C4A0F7EA9208928E729A30DDDA4FEAD7EC6257C7DD1984763 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
21
DNS requests
3
Threats
46
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2564 | unsecapp.exe | POST | 200 | 27.133.148.196:80 | http://www.apple-net.com/update?wd=3f097bcb | JP | — | — | malicious |
2564 | unsecapp.exe | POST | 200 | 27.133.148.196:80 | http://www.apple-net.com/update?wd=51912192 | JP | — | — | malicious |
2564 | unsecapp.exe | POST | 200 | 27.133.148.196:80 | http://www.apple-net.com/update?wd=eea354c0 | JP | — | — | malicious |
2564 | unsecapp.exe | POST | — | 27.133.148.196:443 | http://www.apple-net.com:443/update?wd=95968efc | JP | — | — | malicious |
2564 | unsecapp.exe | POST | — | 27.133.148.196:53 | http://www.apple-net.com:53/update?wd=64a421d6 | JP | — | — | malicious |
2564 | unsecapp.exe | POST | — | 27.133.148.196:53 | http://www.apple-net.com:53/update?wd=cdcccf02 | JP | — | — | malicious |
2564 | unsecapp.exe | POST | — | 27.133.148.196:53 | http://www.apple-net.com:53/update?wd=b01e06f5 | JP | — | — | malicious |
2564 | unsecapp.exe | POST | — | 27.133.148.196:8080 | http://www.apple-net.com:8080/update?wd=5818a5b8 | JP | — | — | malicious |
2564 | unsecapp.exe | POST | — | 27.133.148.196:8080 | http://www.apple-net.com:8080/update?wd=f9d38d1b | JP | — | — | malicious |
2564 | unsecapp.exe | POST | — | 27.133.148.196:8080 | http://www.apple-net.com:8080/update?wd=27b95a7e | JP | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2564 | unsecapp.exe | 27.133.148.196:80 | www.apple-net.com | SAKURA Internet Inc. | JP | malicious |
2564 | unsecapp.exe | 27.133.148.196:443 | www.apple-net.com | SAKURA Internet Inc. | JP | malicious |
2564 | unsecapp.exe | 27.133.148.196:53 | www.apple-net.com | SAKURA Internet Inc. | JP | malicious |
2564 | unsecapp.exe | 27.133.148.196:8080 | www.apple-net.com | SAKURA Internet Inc. | JP | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.apple-net.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2564 | unsecapp.exe | Generic Protocol Command Decode | SURICATA HTTP METHOD terminated by non-compliant character |
2564 | unsecapp.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN Possible PlugX Common Header Struct |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN APT Mustang Panda Payload - CnC Checkin |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN Possible PlugX Common Header Struct |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN APT Mustang Panda Payload - CnC Checkin |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN Possible PlugX Common Header Struct |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN APT Mustang Panda Payload - CnC Checkin |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN Possible PlugX Common Header Struct |
2564 | unsecapp.exe | A Network Trojan was detected | ET TROJAN APT Mustang Panda Payload - CnC Checkin |
6 ETPRO signatures available at the full report