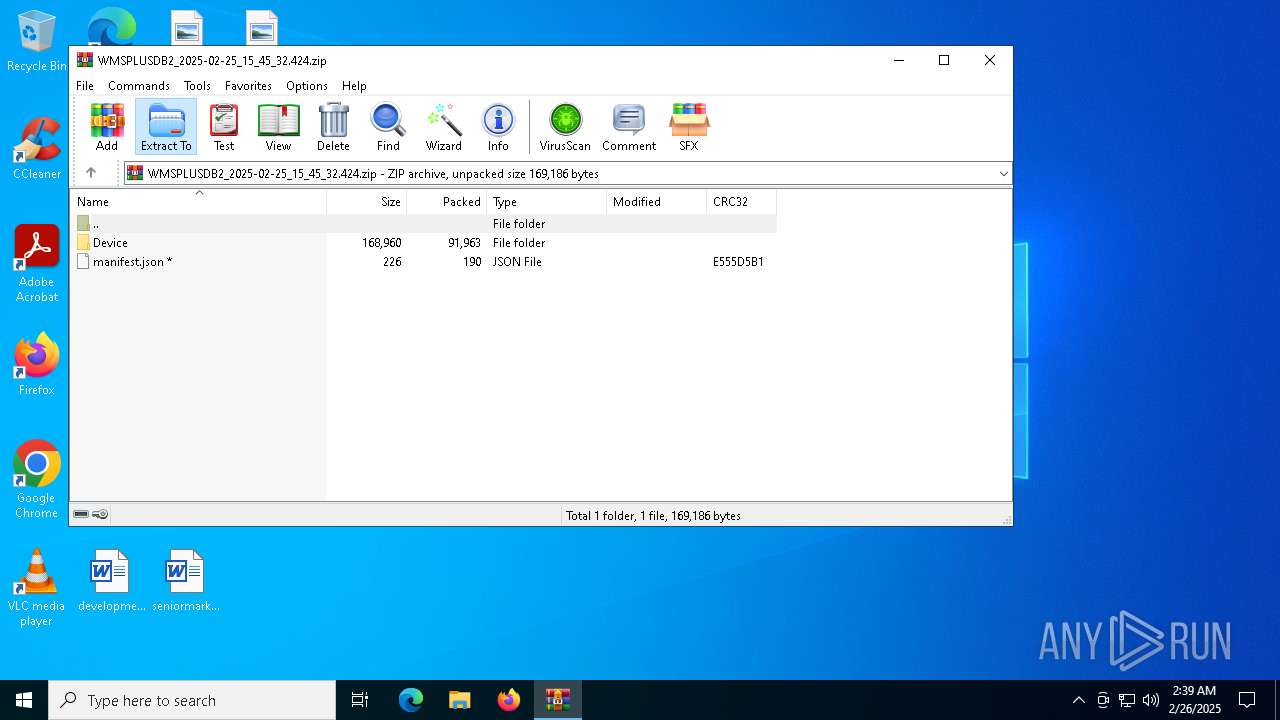
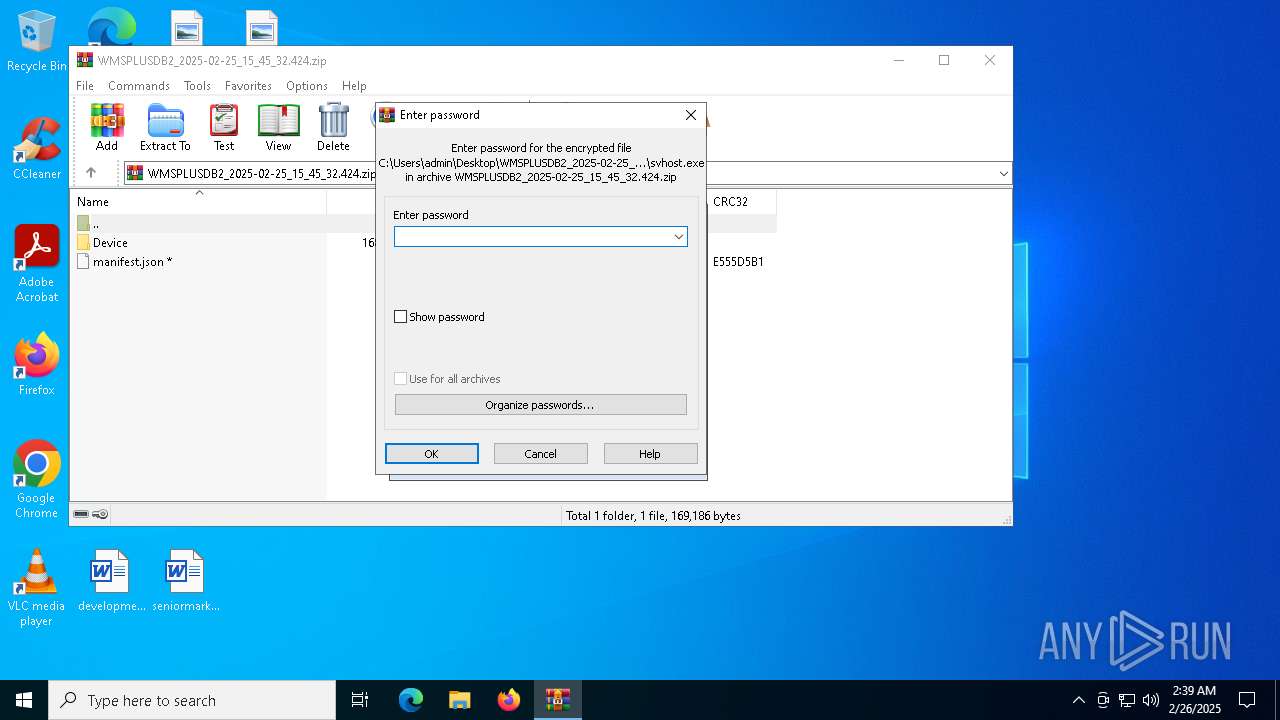
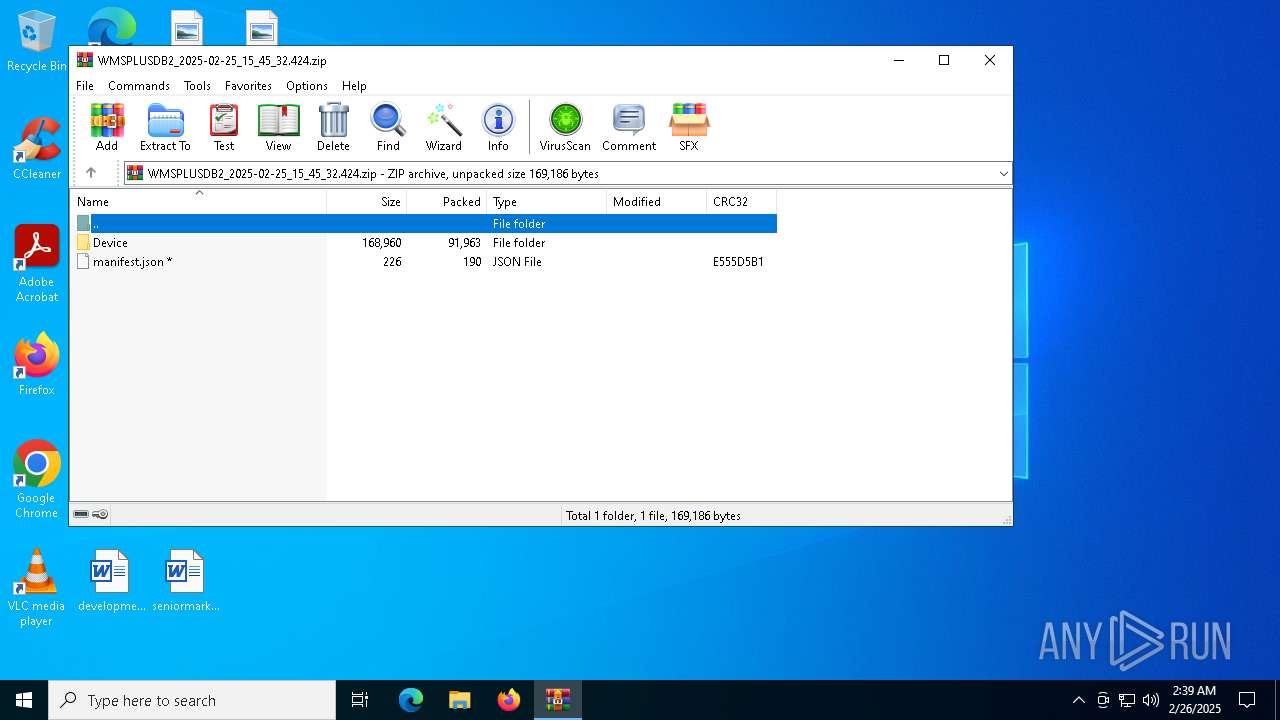
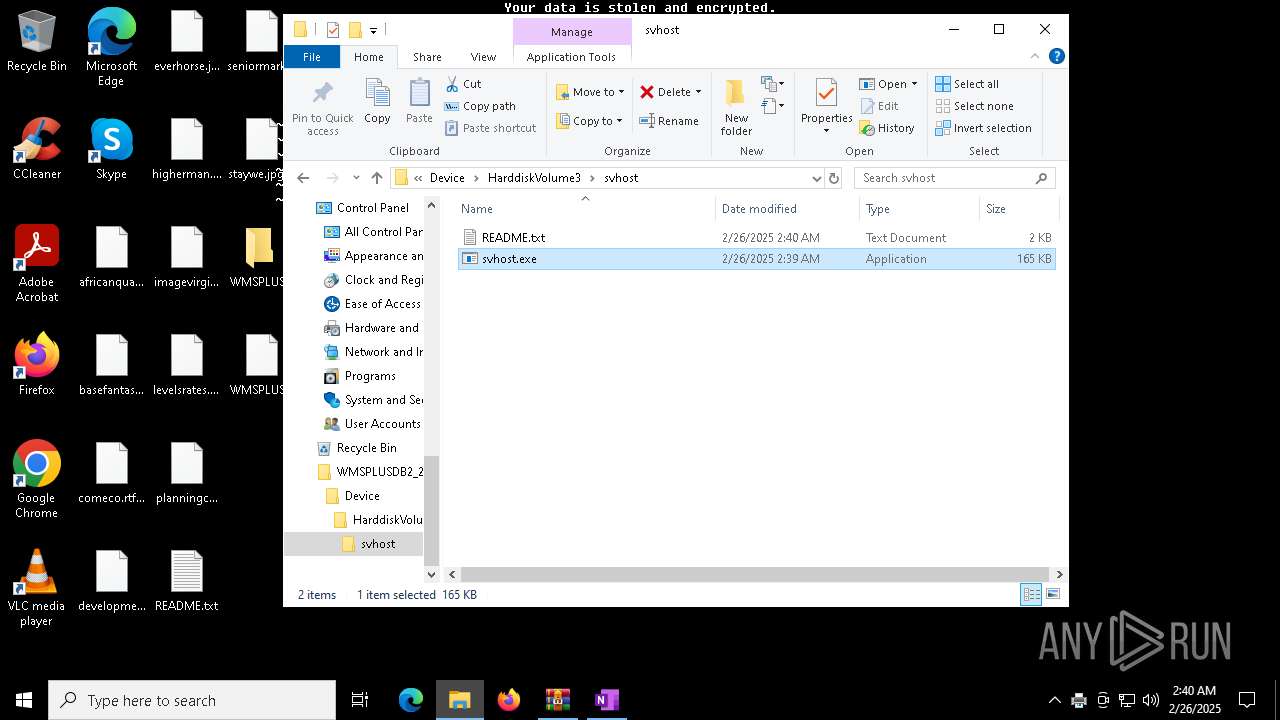
| File name: | WMSPLUSDB2_2025-02-25_15_45_32.424.zip |
| Full analysis: | https://app.any.run/tasks/56c28af4-b606-4330-9d08-f17f52e6422f |
| Verdict: | Malicious activity |
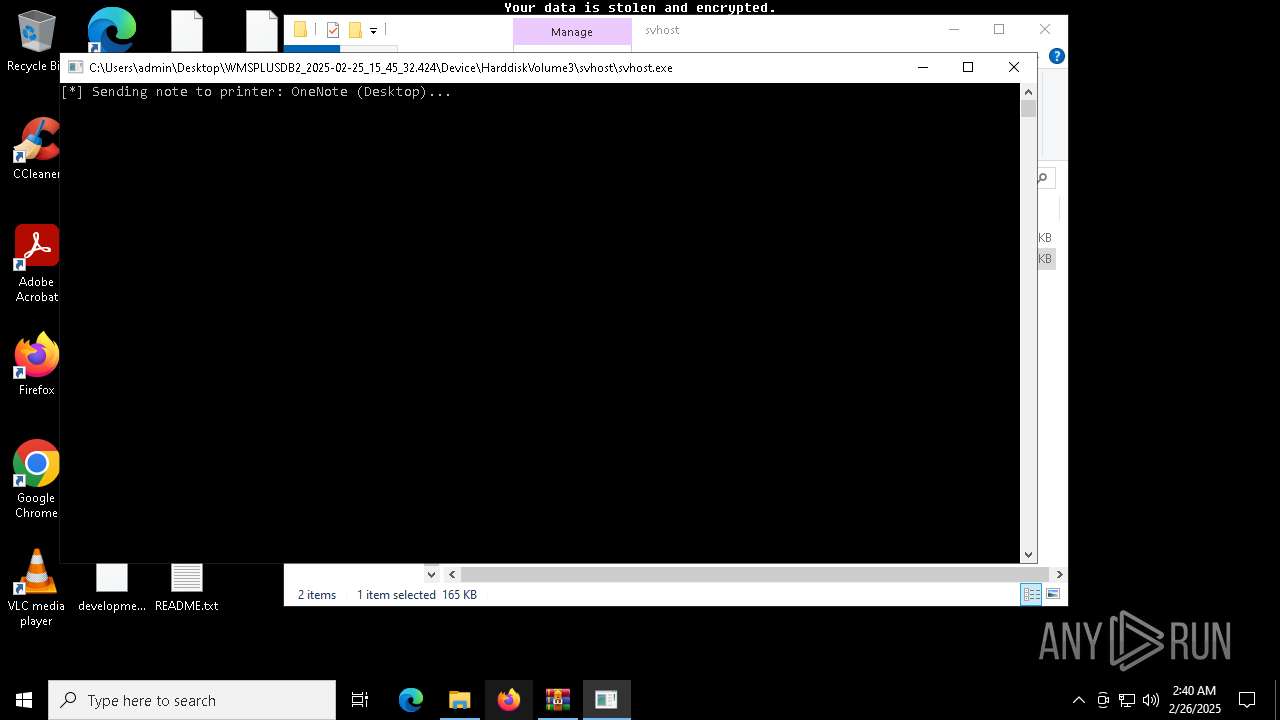
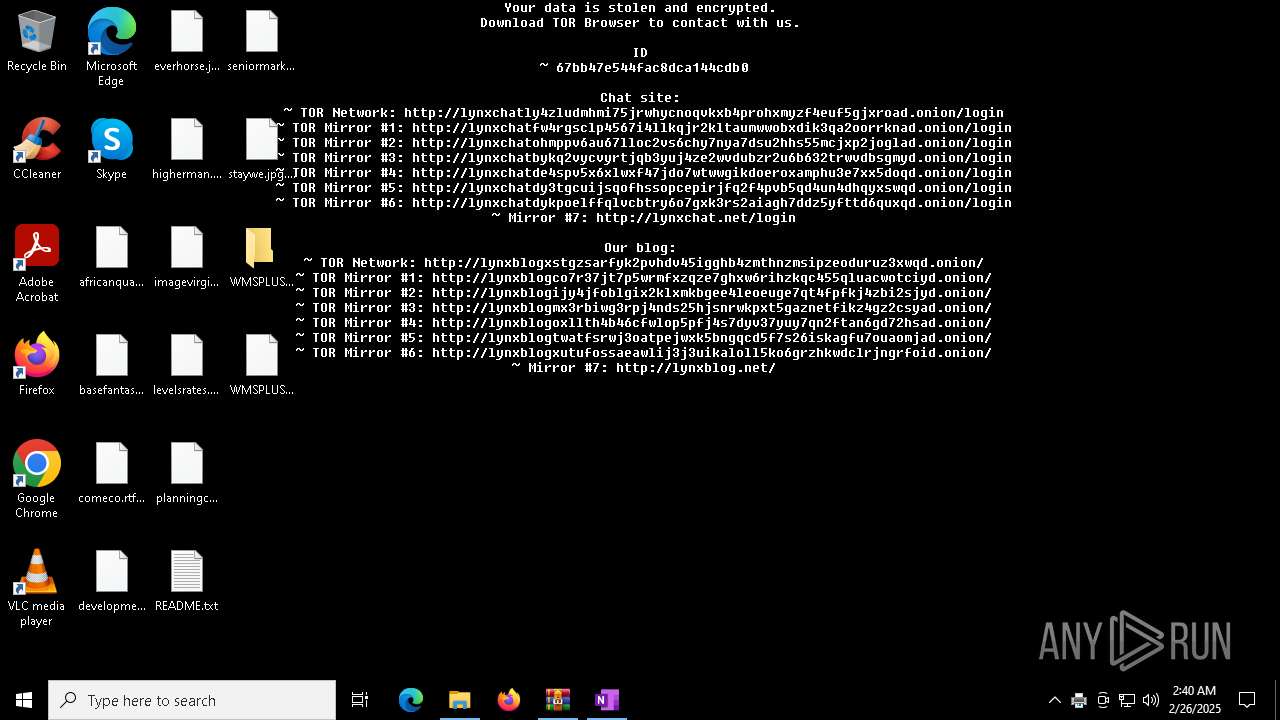
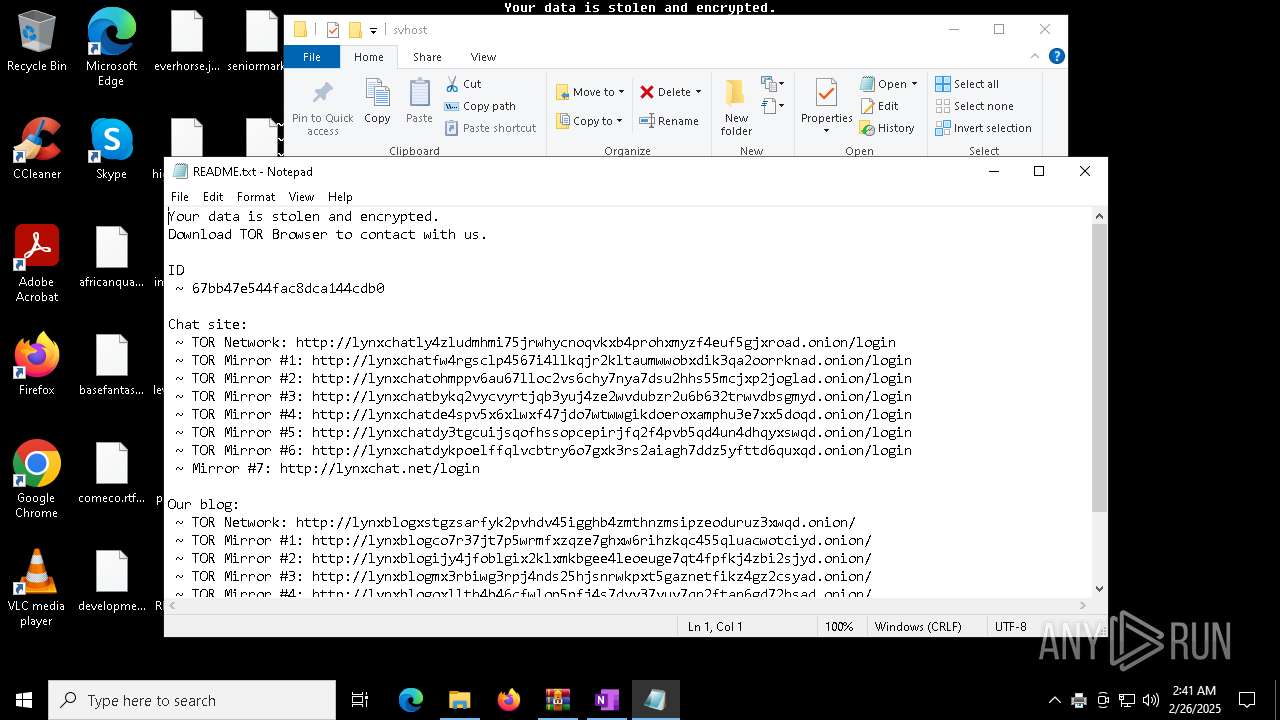
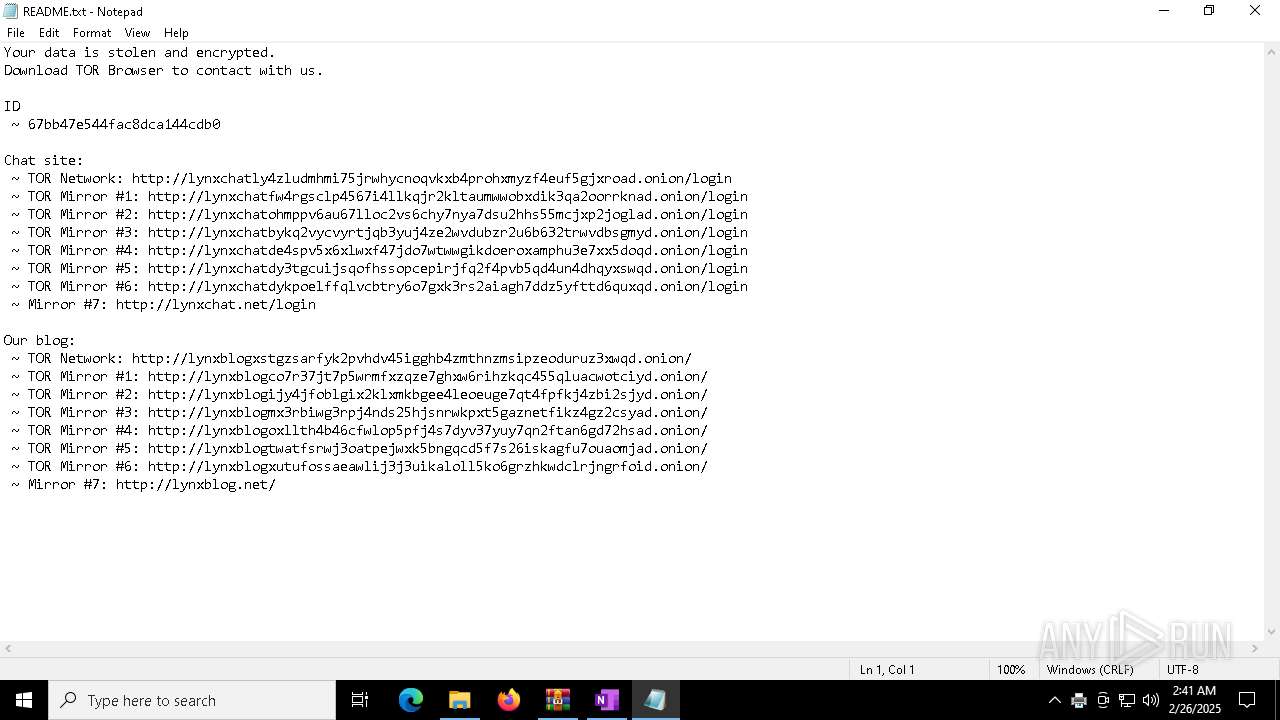
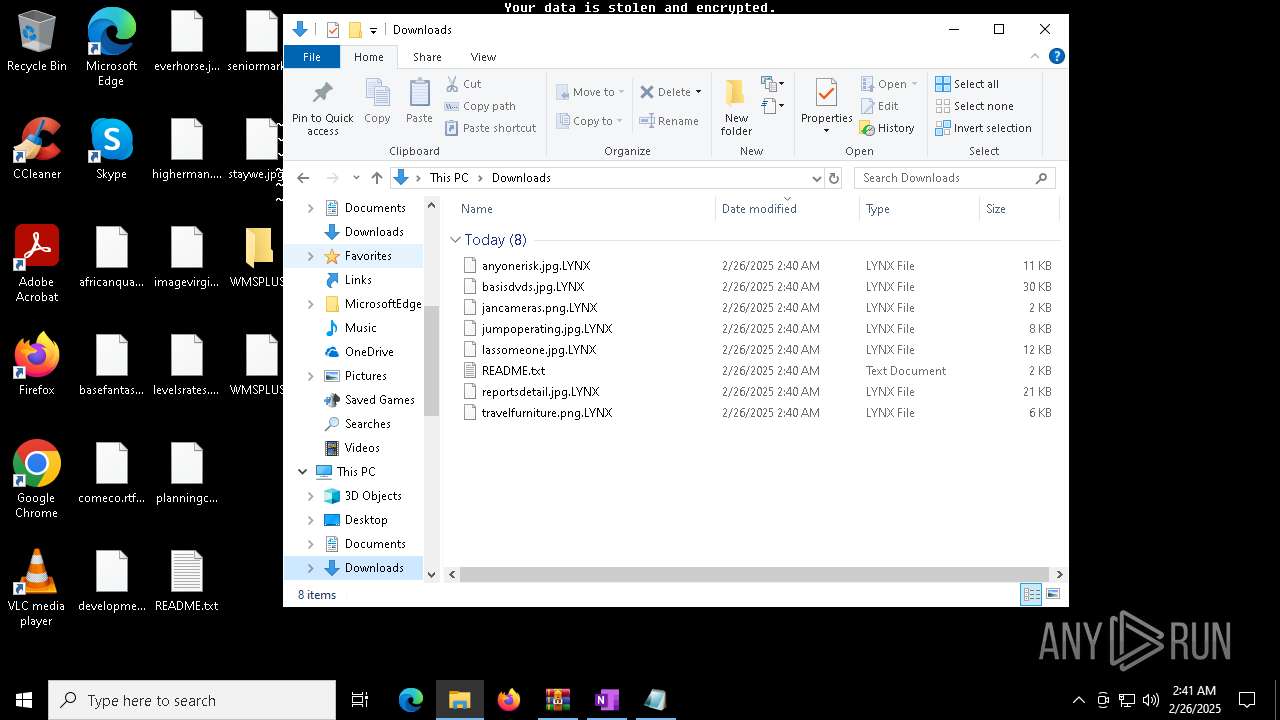
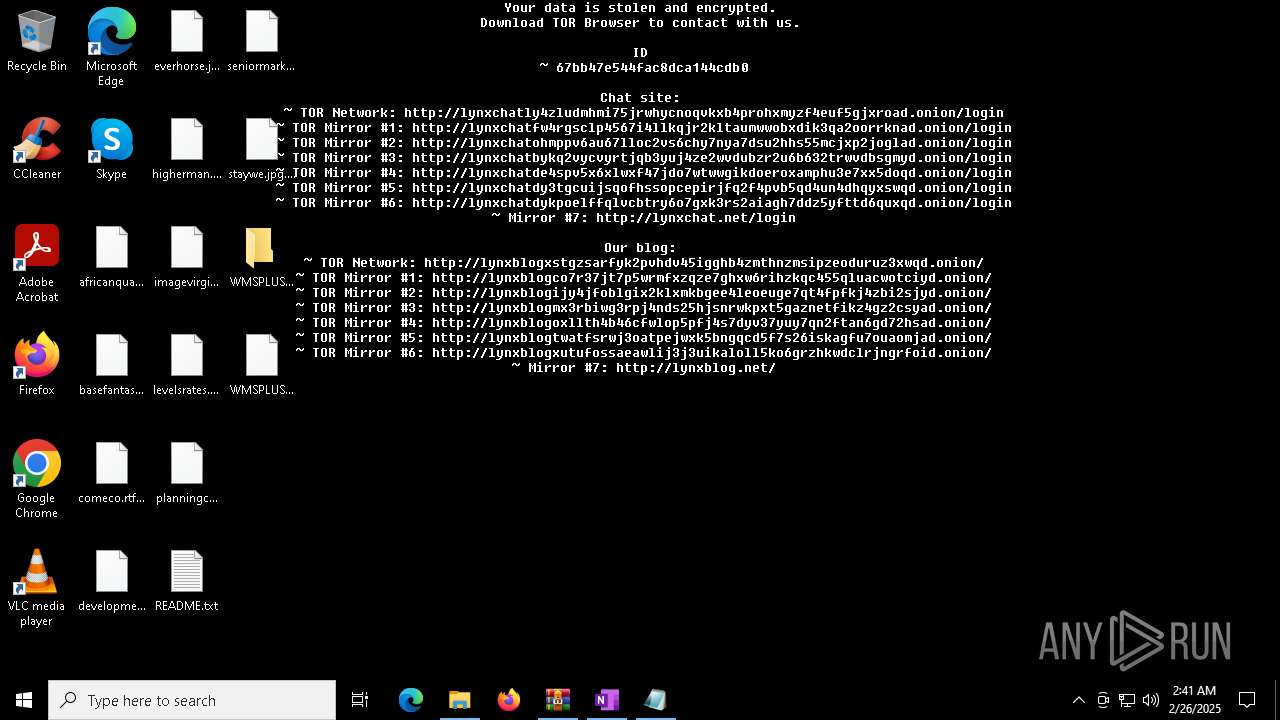
| Threats: | Lynx is a double extortion ransomware: attackers encrypt important and sensitive data and demand a ransom for decryption simultaneously threatening to publish or sell the data. Active since mid-2024. Among techniques are terminating processes and services, privilege escalation, deleting shadow copies. Distribution by phishing, malvertising, exploiting vulnerabilities. |
| Analysis date: | February 26, 2025, 02:38:55 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | F1B14D8C5ABC51B9F46FFBD018BEF76E |
| SHA1: | 5273FB89C74BBE1D107D62484A327A772CC4096B |
| SHA256: | 384EC4FDC26248FBDFFB078471501DC182D506A5563DBA92B9ECE2A64B5F958E |
| SSDEEP: | 1536:Nx3oo9KBlyxQY2vaio6XgYWNLEtQYYob3QNPnzwBgIYs+lWR+L/:33oo0BlyxQTvHH1QAugTCk1+cR+b |
MALICIOUS
LYNX has been detected
- svhost.exe (PID: 3060)
RANSOMWARE has been detected
- svhost.exe (PID: 3060)
Renames files like ransomware
- svhost.exe (PID: 3060)
LYNX has been detected (YARA)
- svhost.exe (PID: 3060)
Scans artifacts that could help determine the target
- ONENOTE.EXE (PID: 10012)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6296)
There is functionality for taking screenshot (YARA)
- svhost.exe (PID: 3060)
Changes the desktop background image
- svhost.exe (PID: 3060)
Executes as Windows Service
- FXSSVC.exe (PID: 9980)
Detected use of alternative data streams (AltDS)
- ONENOTE.EXE (PID: 10012)
Reads security settings of Internet Explorer
- ONENOTE.EXE (PID: 10012)
Creates file in the systems drive root
- ONENOTE.EXE (PID: 10012)
Reads the date of Windows installation
- ONENOTE.EXE (PID: 10012)
Checks Windows Trust Settings
- ONENOTE.EXE (PID: 10012)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6296)
Reads the machine GUID from the registry
- svhost.exe (PID: 3060)
- ONENOTE.EXE (PID: 10012)
Manual execution by a user
- svhost.exe (PID: 3060)
- notepad.exe (PID: 488)
Reads the computer name
- svhost.exe (PID: 3060)
- ONENOTE.EXE (PID: 10012)
- ONENOTEM.EXE (PID: 6904)
Creates files in the program directory
- svhost.exe (PID: 3060)
- FXSSVC.exe (PID: 9980)
Checks supported languages
- svhost.exe (PID: 3060)
- ONENOTE.EXE (PID: 10012)
- ONENOTEM.EXE (PID: 6904)
Creates files or folders in the user directory
- svhost.exe (PID: 3060)
- printfilterpipelinesvc.exe (PID: 9856)
- ONENOTE.EXE (PID: 10012)
Create files in a temporary directory
- svhost.exe (PID: 3060)
- ONENOTE.EXE (PID: 10012)
Reads security settings of Internet Explorer
- printfilterpipelinesvc.exe (PID: 9856)
- notepad.exe (PID: 488)
Disables trace logs
- FXSSVC.exe (PID: 9980)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 10012)
- ONENOTEM.EXE (PID: 6904)
Reads Environment values
- ONENOTE.EXE (PID: 10012)
Reads the software policy settings
- ONENOTE.EXE (PID: 10012)
Checks proxy server information
- ONENOTE.EXE (PID: 10012)
Process checks computer location settings
- ONENOTE.EXE (PID: 10012)
Reads product name
- ONENOTE.EXE (PID: 10012)
Reads CPU info
- ONENOTE.EXE (PID: 10012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x565025a6 |
| ZipCompressedSize: | 91963 |
| ZipUncompressedSize: | 168960 |
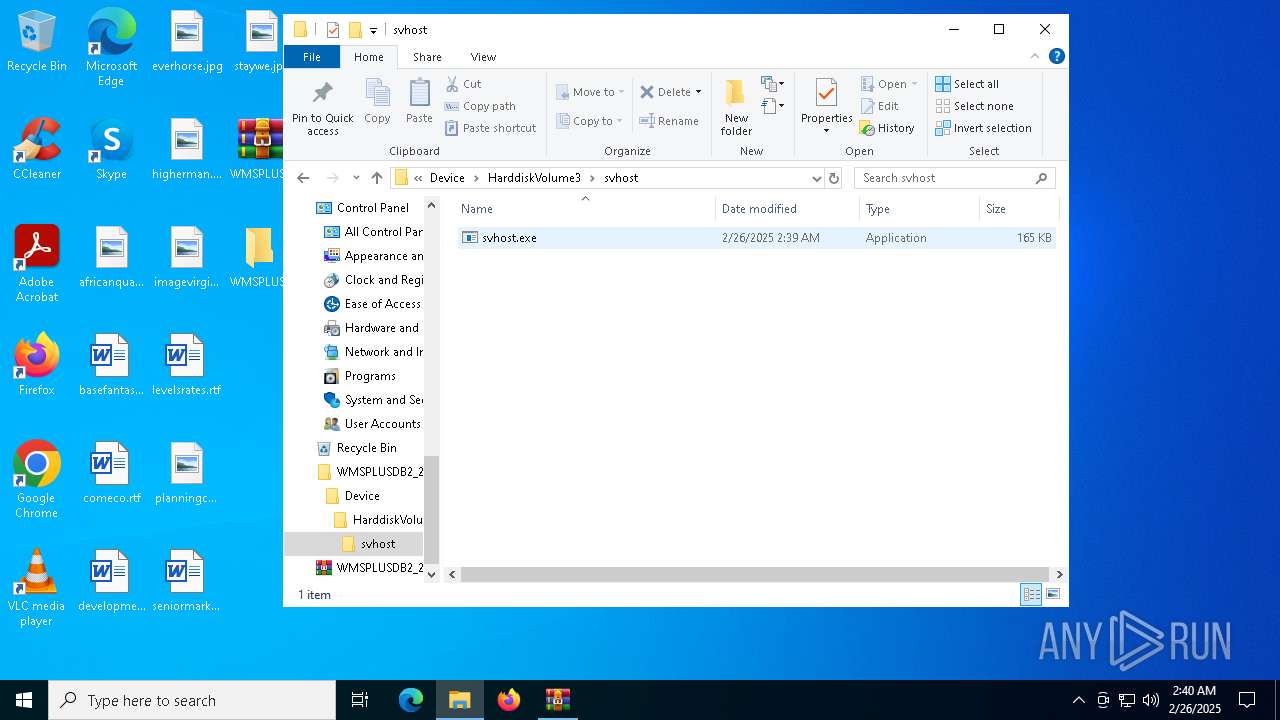
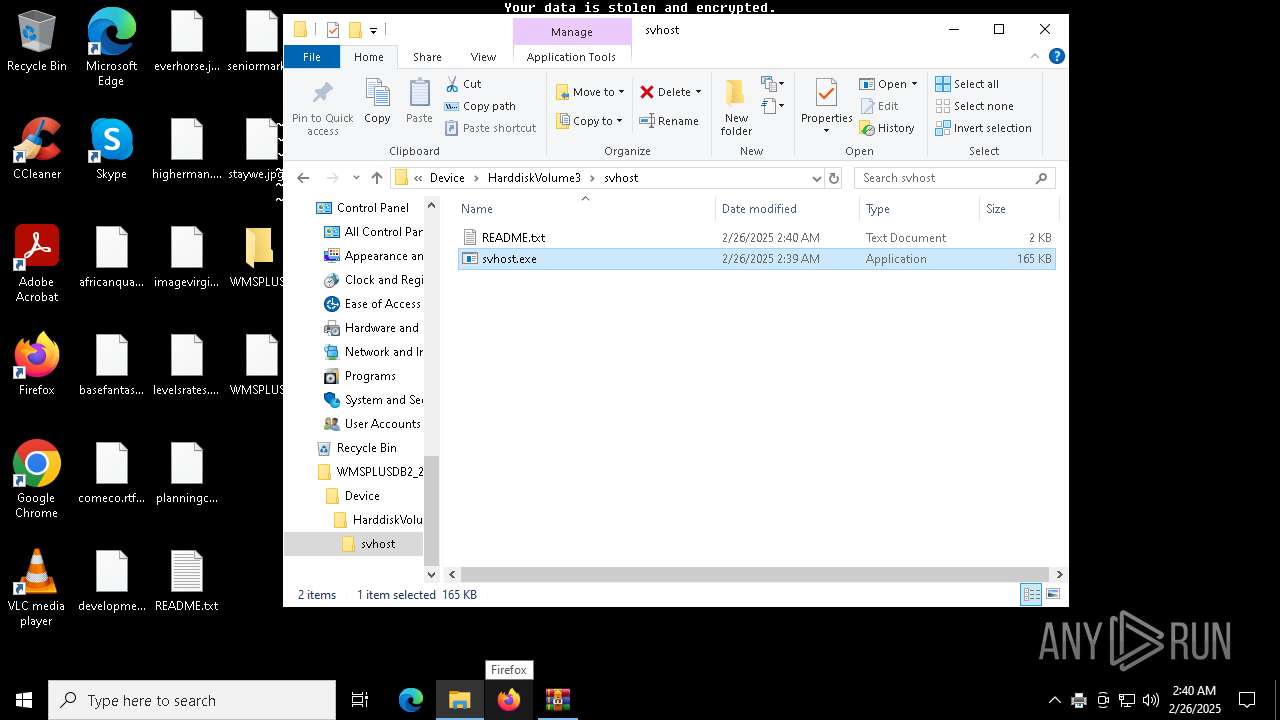
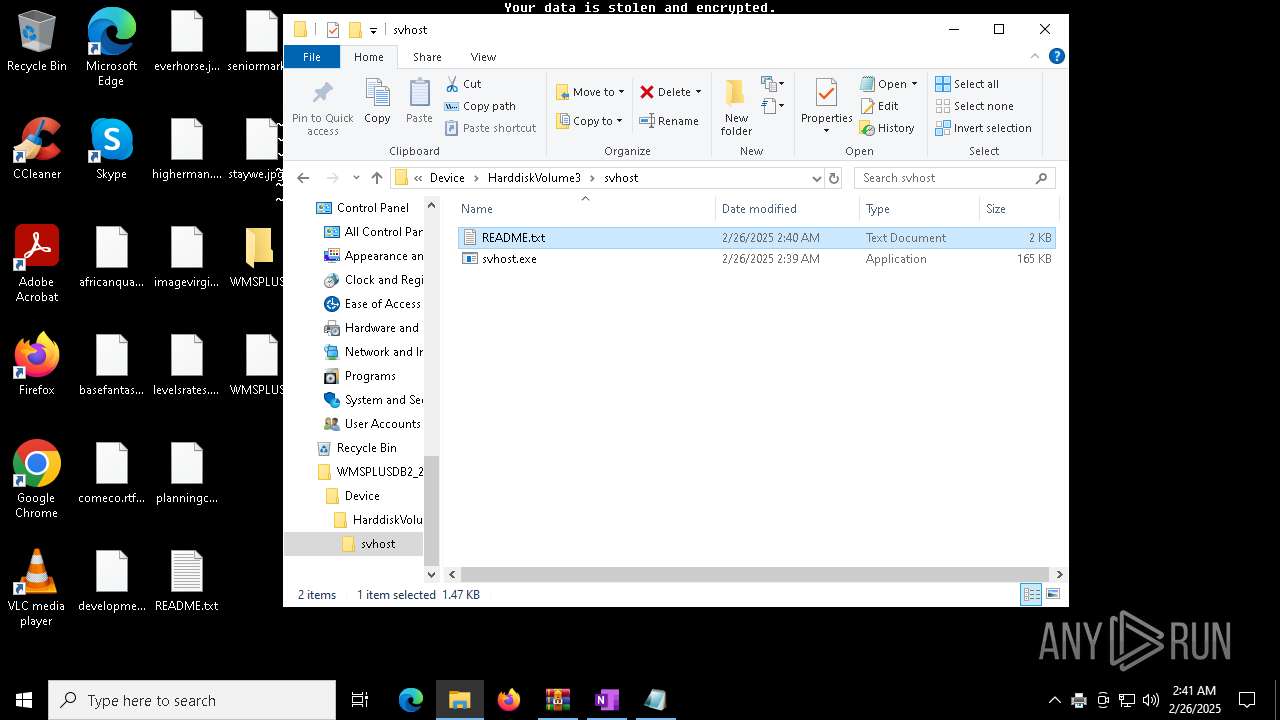
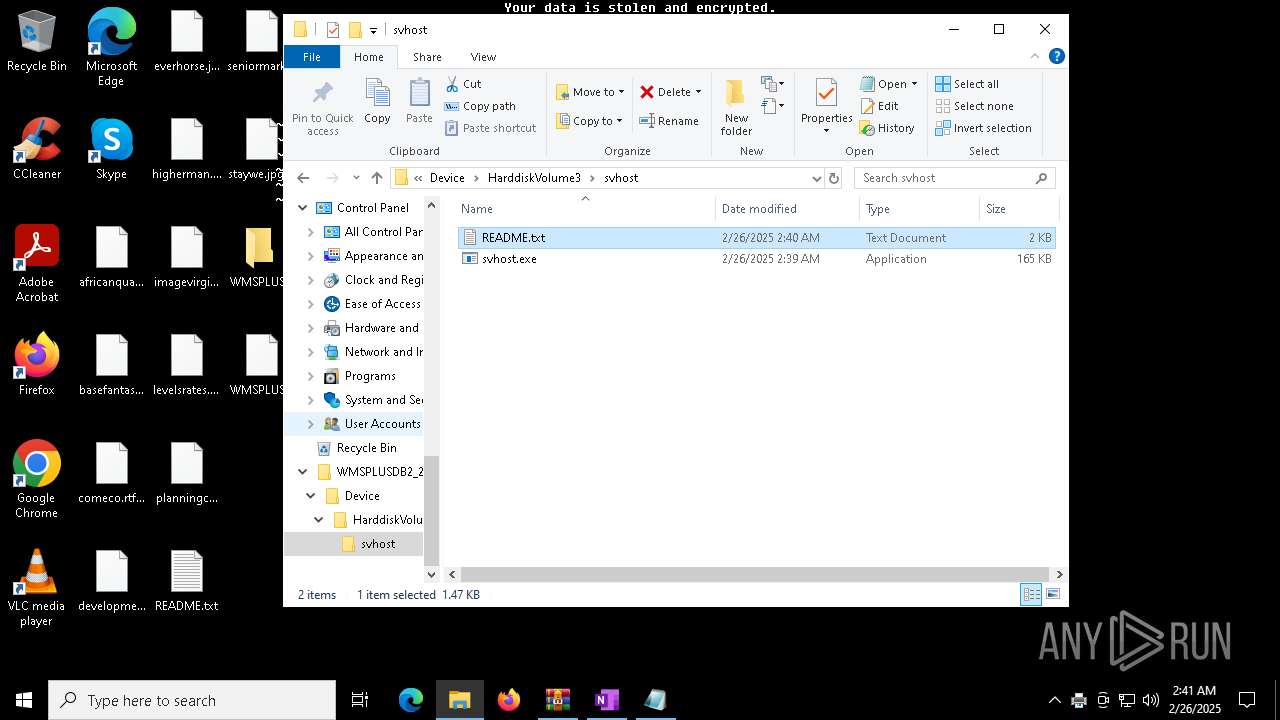
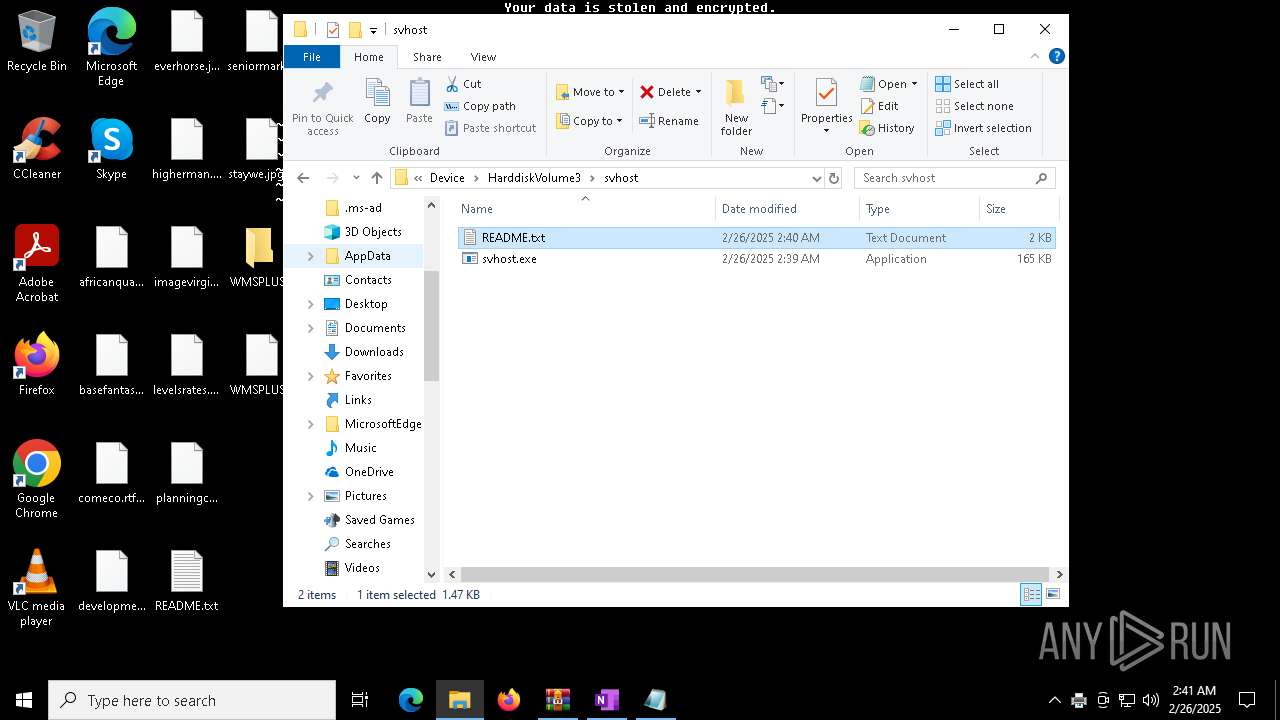
| ZipFileName: | Device/HarddiskVolume3/svhost/svhost.exe |
Total processes
147
Monitored processes
10
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\WMSPLUSDB2_2025-02-25_15_45_32.424\Device\HarddiskVolume3\svhost\README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3060 | "C:\Users\admin\Desktop\WMSPLUSDB2_2025-02-25_15_45_32.424\Device\HarddiskVolume3\svhost\svhost.exe" | C:\Users\admin\Desktop\WMSPLUSDB2_2025-02-25_15_45_32.424\Device\HarddiskVolume3\svhost\svhost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4624 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5200 | C:\WINDOWS\system32\DllHost.exe /Processid:{46B988E8-BEC2-401F-A1C5-16C694F26D3E} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6296 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\WMSPLUSDB2_2025-02-25_15_45_32.424.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | svhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6904 | /tsr | C:\Program Files\Microsoft Office\root\Office16\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Send to OneNote Tool Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 9856 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 9980 | C:\WINDOWS\system32\fxssvc.exe | C:\Windows\System32\FXSSVC.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Fax Service Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 10012 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\{9BEB86F4-D681-4F07-92AB-879C1319D3C7}.xps" 133850112356520000 | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | printfilterpipelinesvc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
13 597
Read events
13 336
Write events
232
Delete events
29
Modification events
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\WMSPLUSDB2_2025-02-25_15_45_32.424.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
4
Suspicious files
724
Text files
180
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3060 | svhost.exe | C:\ProgramData\Adobe\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\ProgramData\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\ProgramData\Comms\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\ProgramData\Adobe\ARM\S\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\ProgramData\Adobe\ARM\Acrobat_23.001.20093\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\ProgramData\Adobe\Temp\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\ProgramData\Adobe\ARM\S\388\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\ProgramData\Adobe\ARM\{291AA914-A987-4CE9-BD63-0C0A92D435E5}\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
| 3060 | svhost.exe | C:\Users\admin\AppData\Local\VirtualStore\ProgramData\Microsoft\ClickToRun\MachineData\README.txt | text | |
MD5:92E75ADD26C4946FA04774C71767D8B8 | SHA256:9F432A69FAC1581BF5A2ECB1EAFA7C8CCD0958D5DF2404B7026EFB39E51713E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
41
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
188 | svchost.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4704 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
188 | svchost.exe | GET | 200 | 23.216.77.30:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4704 | SIHClient.exe | GET | 200 | 104.85.1.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
10012 | ONENOTE.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6508 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6076 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
188 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.110.240.131:443 | www.bing.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|