| File name: | Nero 2020 - Crack+Patch+Serial.exe |
| Full analysis: | https://app.any.run/tasks/dd18e09b-26a1-4a70-8ebe-64fd41f790d5 |
| Verdict: | Malicious activity |
| Threats: | Netwire is an advanced RAT — it is a malware that takes control of infected PCs and allows its operators to perform various actions. Unlike many RATs, this one can target every major operating system, including Windows, Linux, and MacOS. |
| Analysis date: | November 25, 2023, 10:12:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3EA116F1650DA9AA00A77435CBA8C42F |
| SHA1: | 0B215AAA66A3C3A84120EC3B11AF4A2B37D94AF6 |
| SHA256: | 383590E5289A5908899CD612222F6677C4675691715BFAFF65B599EDE17DC16A |
| SSDEEP: | 98304:Mat/0SdpmYs/Nf4HhSjrckztFmG5Zmy+XerxuU3uvm3A2c8DwRosU/jxKa359bhn:GqNUlcMDQV/jBvqsNgo8LY3 |
MALICIOUS
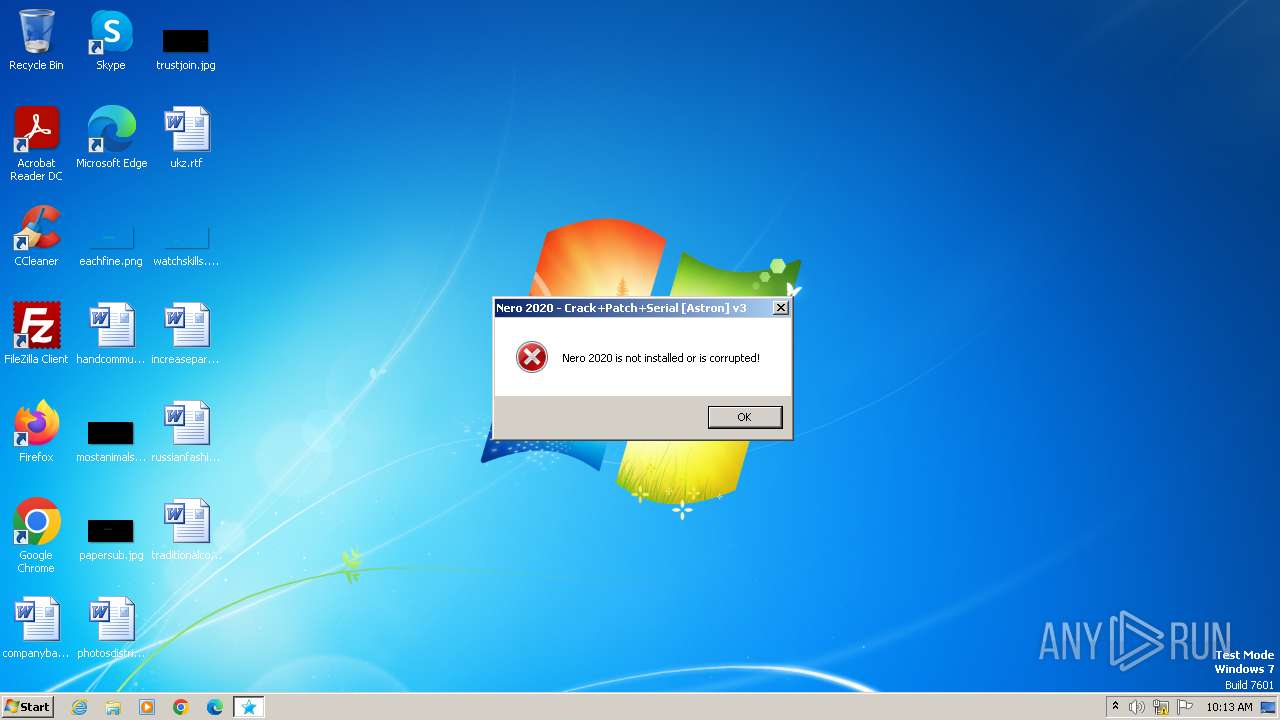
Drops the executable file immediately after the start
- Nero 2020 - Crack+Patch+Serial.exe (PID: 2708)
NETWIRE has been detected (YARA)
- Chrome.exe (PID: 2504)
SUSPICIOUS
Reads the Internet Settings
- Nero 2020 - Crack+Patch+Serial.exe (PID: 2708)
INFO
Reads mouse settings
- Nero 2020 - Crack+Patch+Serial.exe (PID: 2708)
Create files in a temporary directory
- Nero 2020 - Crack+Patch+Serial.exe (PID: 2708)
Reads the computer name
- Nero 2020 - Crack+Patch+Serial.exe (PID: 2708)
- Chrome.exe (PID: 2504)
- vv.exe (PID: 1736)
Checks supported languages
- Nero 2020 - Crack+Patch+Serial.exe (PID: 2708)
- vv.exe (PID: 1736)
- Chrome.exe (PID: 2504)
Reads the machine GUID from the registry
- Chrome.exe (PID: 2504)
Creates files in the program directory
- vv.exe (PID: 1736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:01:11 06:55:53+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 581120 |
| InitializedDataSize: | 11473408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27f4a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Total processes
45
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1736 | "C:\Users\admin\AppData\Local\Temp\vv.exe" | C:\Users\admin\AppData\Local\Temp\vv.exe | Nero 2020 - Crack+Patch+Serial.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Nero-Astron Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\AppData\Local\Temp\vv.exe" | C:\Users\admin\AppData\Local\Temp\vv.exe | — | Nero 2020 - Crack+Patch+Serial.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Nero-Astron Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2504 | "C:\Users\admin\AppData\Local\Temp\Chrome.exe" | C:\Users\admin\AppData\Local\Temp\Chrome.exe | Nero 2020 - Crack+Patch+Serial.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: WindowsForm_練習用 Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\AppData\Local\Temp\Nero 2020 - Crack+Patch+Serial.exe" | C:\Users\admin\AppData\Local\Temp\Nero 2020 - Crack+Patch+Serial.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
918
Read events
910
Write events
8
Delete events
0
Modification events
| (PID) Process: | (2708) Nero 2020 - Crack+Patch+Serial.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2708) Nero 2020 - Crack+Patch+Serial.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2708) Nero 2020 - Crack+Patch+Serial.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2708) Nero 2020 - Crack+Patch+Serial.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2708 | Nero 2020 - Crack+Patch+Serial.exe | C:\Users\admin\AppData\Local\Temp\vv.exe | executable | |
MD5:AA6BBC51A664D5133F913AB68B4BB8E9 | SHA256:4804B970614A35ACD7DF64302E647DF791519128A4467D1E919F928A3B9B7708 | |||
| 1736 | vv.exe | C:\ProgramData\SomInicial.wav | binary | |
MD5:7CB1BC93F0D168C6D4CBC94C86CB625E | SHA256:4EF0102A0D07D686E0177EDCC6C3EB3CEDF52243104DE4A41ECE28094B39C7E4 | |||
| 2708 | Nero 2020 - Crack+Patch+Serial.exe | C:\Users\admin\AppData\Local\Temp\Chrome.exe | executable | |
MD5:925000463BDE0E7FA22560416497D50D | SHA256:7FD679473CA28EFDBD89C6540CEC28EDEE1A6175AF634761F44A2BD555440F5A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |