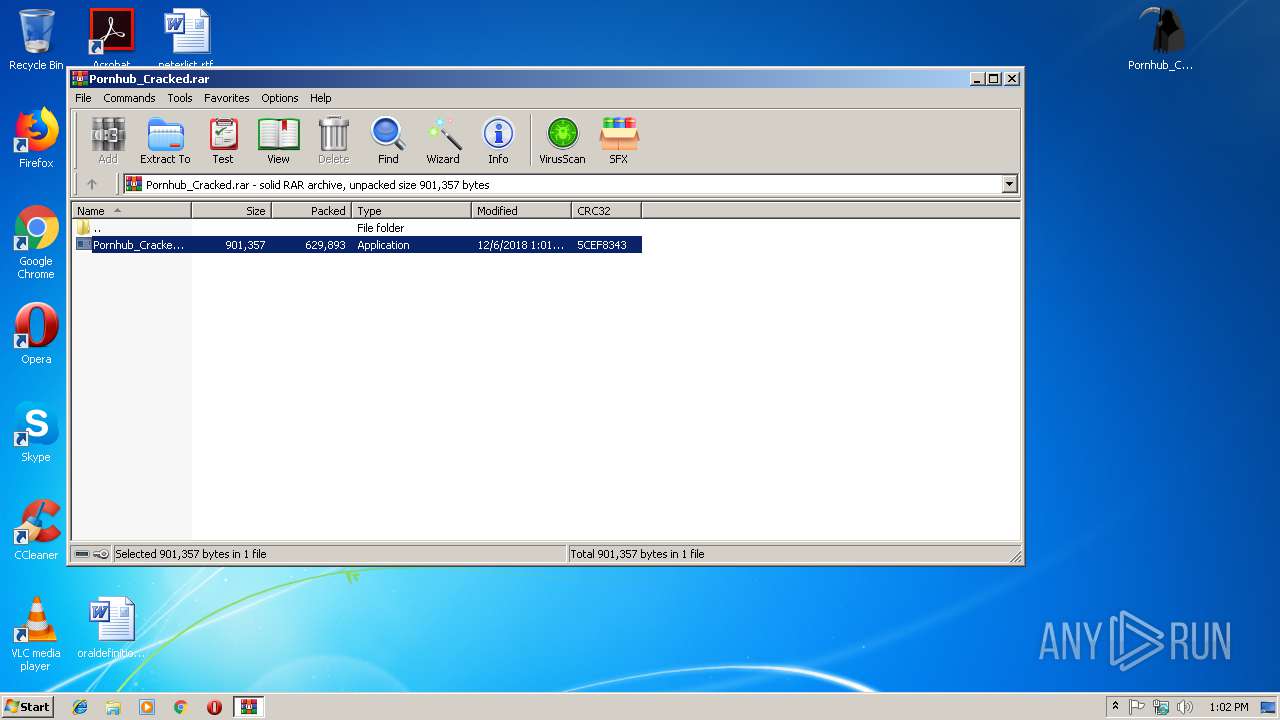
| File name: | Pornhub_Cracked.rar |
| Full analysis: | https://app.any.run/tasks/718014db-9613-4e3f-9441-74e7e28d3c7b |
| Verdict: | Malicious activity |
| Threats: | njRAT is a remote access trojan. It is one of the most widely accessible RATs on the market that features an abundance of educational information. Interested attackers can even find tutorials on YouTube. This allows it to become one of the most popular RATs in the world. |
| Analysis date: | December 06, 2018, 13:01:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F71335174583BBA04C2906283D919555 |
| SHA1: | 592DAD0475BC1ADE209DAA2A8D7BEE9DC8589D14 |
| SHA256: | 3824303D78C8154A2D3B2417C008F9F850A49D3BDB842BFF3C929B4983A246DF |
| SSDEEP: | 12288:fjYG8NcqSY4BQyCNtdodlLFTa3MjalPYVDool/9GH6uCYT3b1Uw9n:fkGdqSY4uyCRodZFTaLZc7x9OXCYL5b |
MALICIOUS
Application was dropped or rewritten from another process
- Pornhub Cracked.exe (PID: 3956)
- Pornhub_Cracked.exe (PID: 1376)
- crypted.exe (PID: 2136)
- svghost.exe (PID: 4080)
Writes to a start menu file
- svghost.exe (PID: 4080)
NJRAT was detected
- svghost.exe (PID: 4080)
SUSPICIOUS
Creates files in the user directory
- Pornhub_Cracked.exe (PID: 1376)
- svghost.exe (PID: 4080)
Executable content was dropped or overwritten
- Pornhub_Cracked.exe (PID: 1376)
- crypted.exe (PID: 2136)
- svghost.exe (PID: 4080)
Creates files in the program directory
- crypted.exe (PID: 2136)
Starts itself from another location
- crypted.exe (PID: 2136)
Connects to unusual port
- svghost.exe (PID: 4080)
INFO
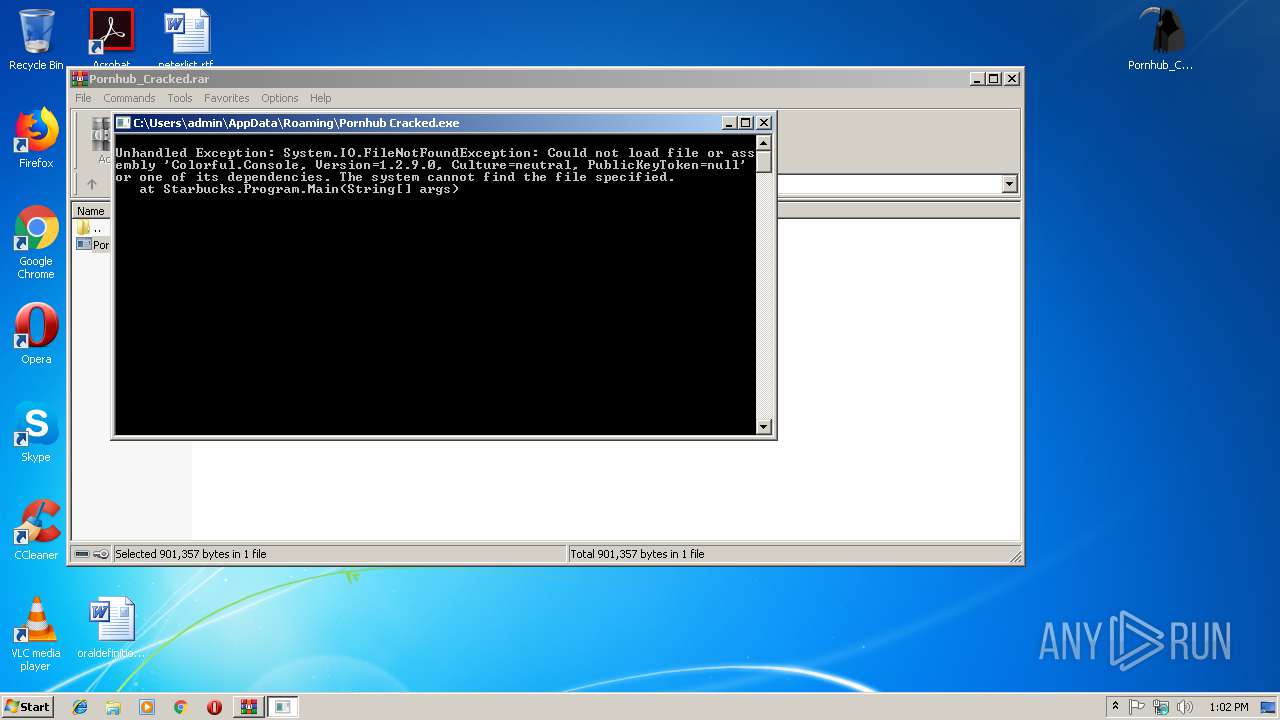
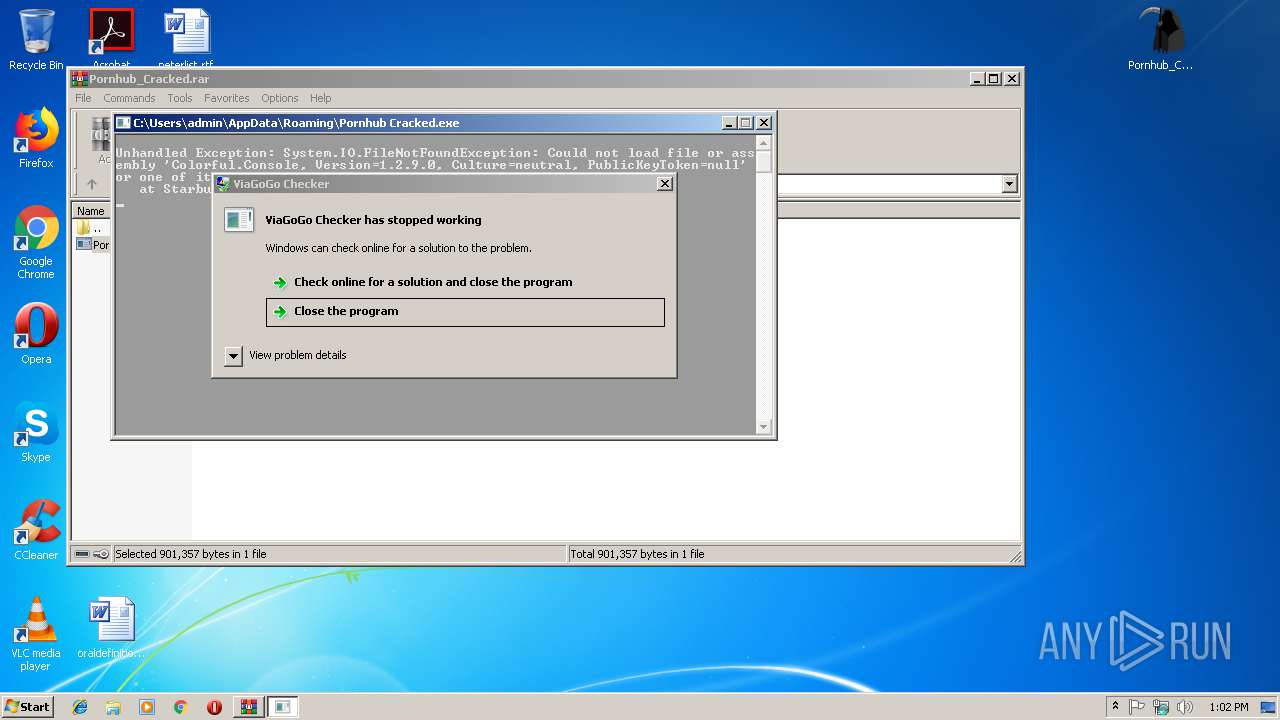
Application was crashed
- Pornhub Cracked.exe (PID: 3956)
Dropped object may contain Bitcoin addresses
- Pornhub_Cracked.exe (PID: 1376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
41
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1376 | "C:\Users\admin\Desktop\Pornhub_Cracked.exe" | C:\Users\admin\Desktop\Pornhub_Cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\AppData\Roaming\crypted.exe" | C:\Users\admin\AppData\Roaming\crypted.exe | Pornhub_Cracked.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: cat 70zx Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2948 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Pornhub_Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3956 | "C:\Users\admin\AppData\Roaming\Pornhub Cracked.exe" | C:\Users\admin\AppData\Roaming\Pornhub Cracked.exe | Pornhub_Cracked.exe | ||||||||||||
User: admin Company: Azetej Company Integrity Level: HIGH Description: ViaGoGo Checker Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4080 | "C:\ProgramData\svghost.exe" | C:\ProgramData\svghost.exe | crypted.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: cat 70zx Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 386
Read events
818
Write events
568
Delete events
0
Modification events
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Pornhub_Cracked.rar | |||
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2948) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1376) Pornhub_Cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1376) Pornhub_Cracked.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2948 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2948.33504\Pornhub_Cracked.exe | — | |
MD5:— | SHA256:— | |||
| 2136 | crypted.exe | C:\ProgramData\svghost.exe | executable | |
MD5:— | SHA256:— | |||
| 1376 | Pornhub_Cracked.exe | C:\Users\admin\AppData\Roaming\Pornhub Cracked.exe | executable | |
MD5:— | SHA256:— | |||
| 4080 | svghost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\be1b22e51a35057733504927de28e62a.exe | executable | |
MD5:— | SHA256:— | |||
| 1376 | Pornhub_Cracked.exe | C:\Users\admin\AppData\Roaming\crypted.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
11
DNS requests
6
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4080 | svghost.exe | 197.0.5.209:5552 | atacker007.ddns.net | TOPNET | TN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
atacker007.ddns.net |
| malicious |
dns.msftncsi.com |
| shared |