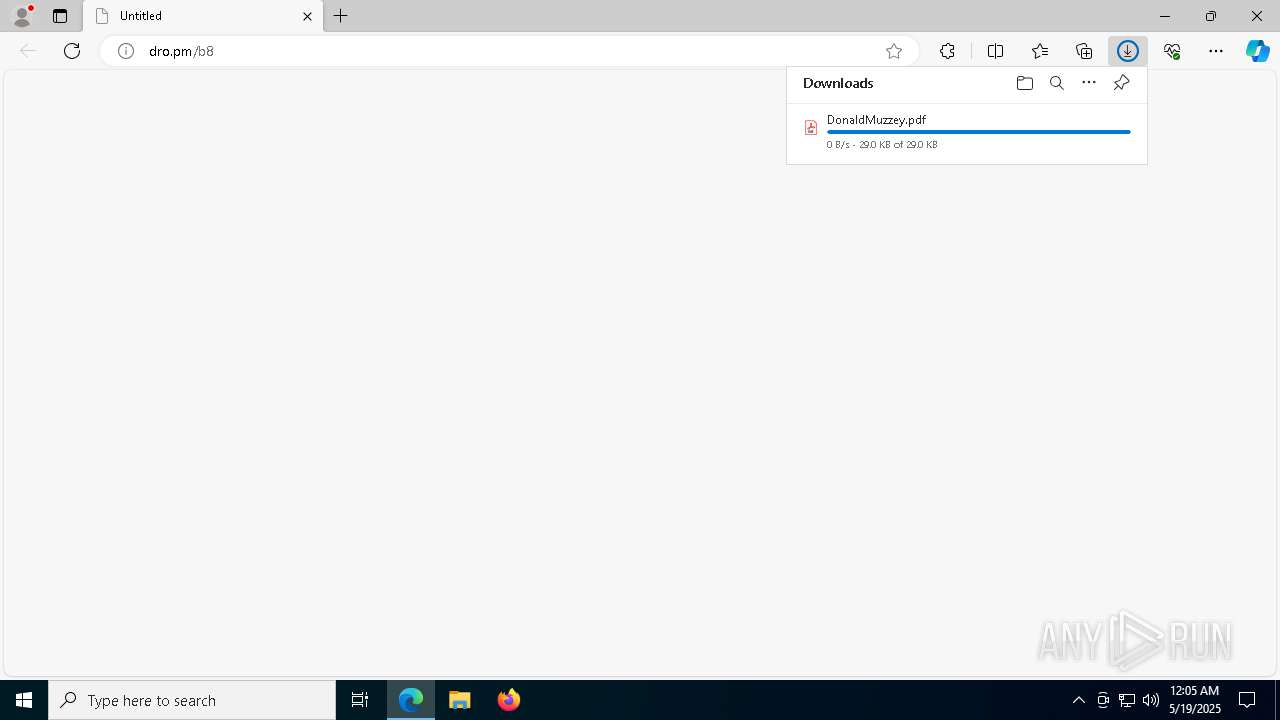
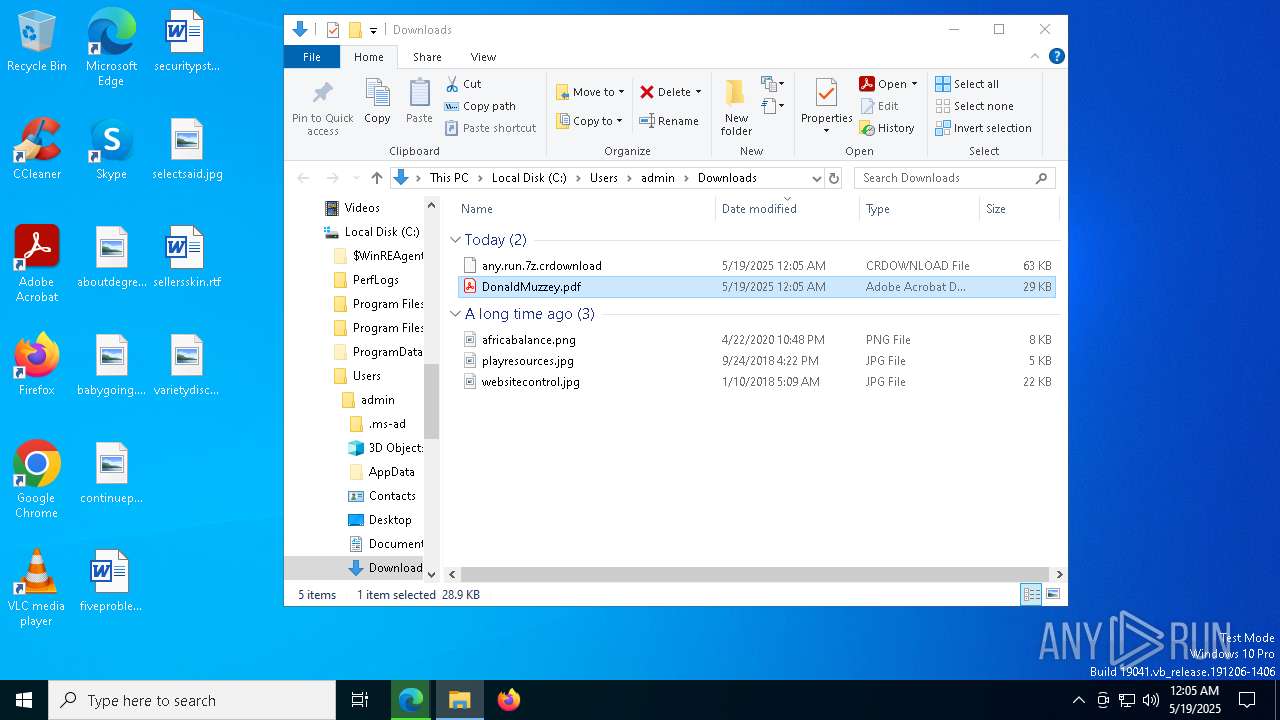
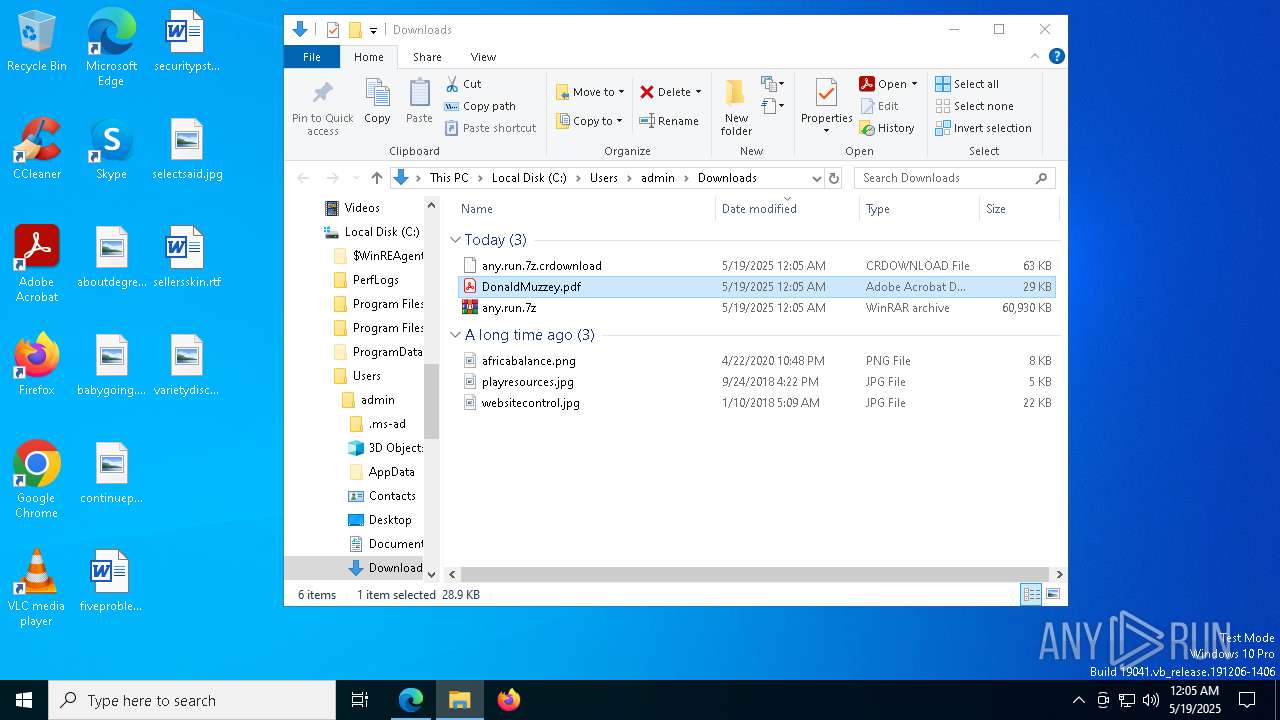
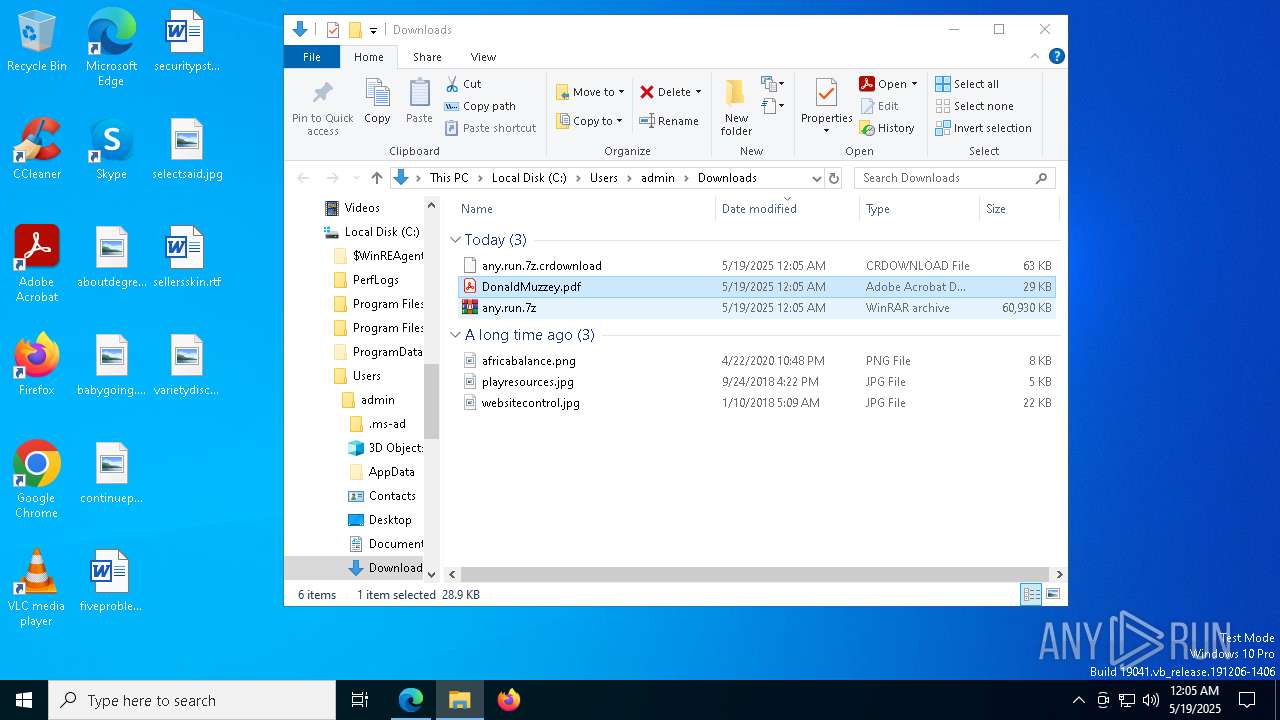
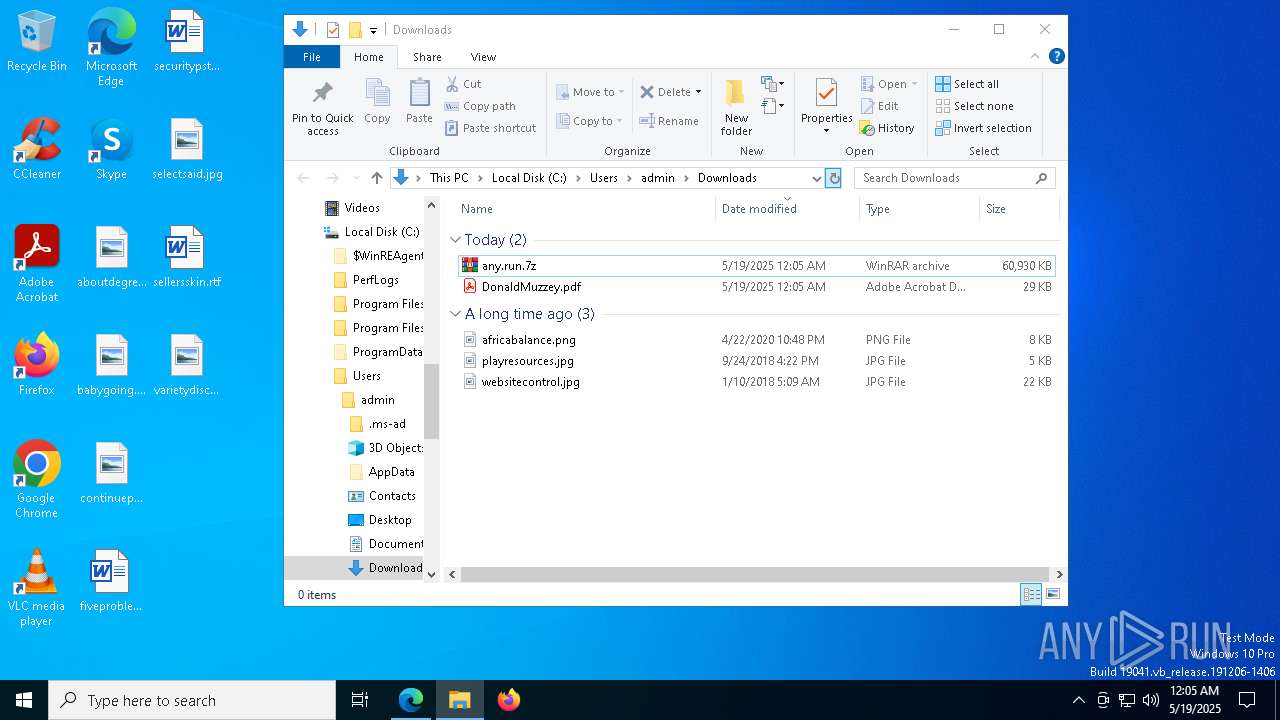
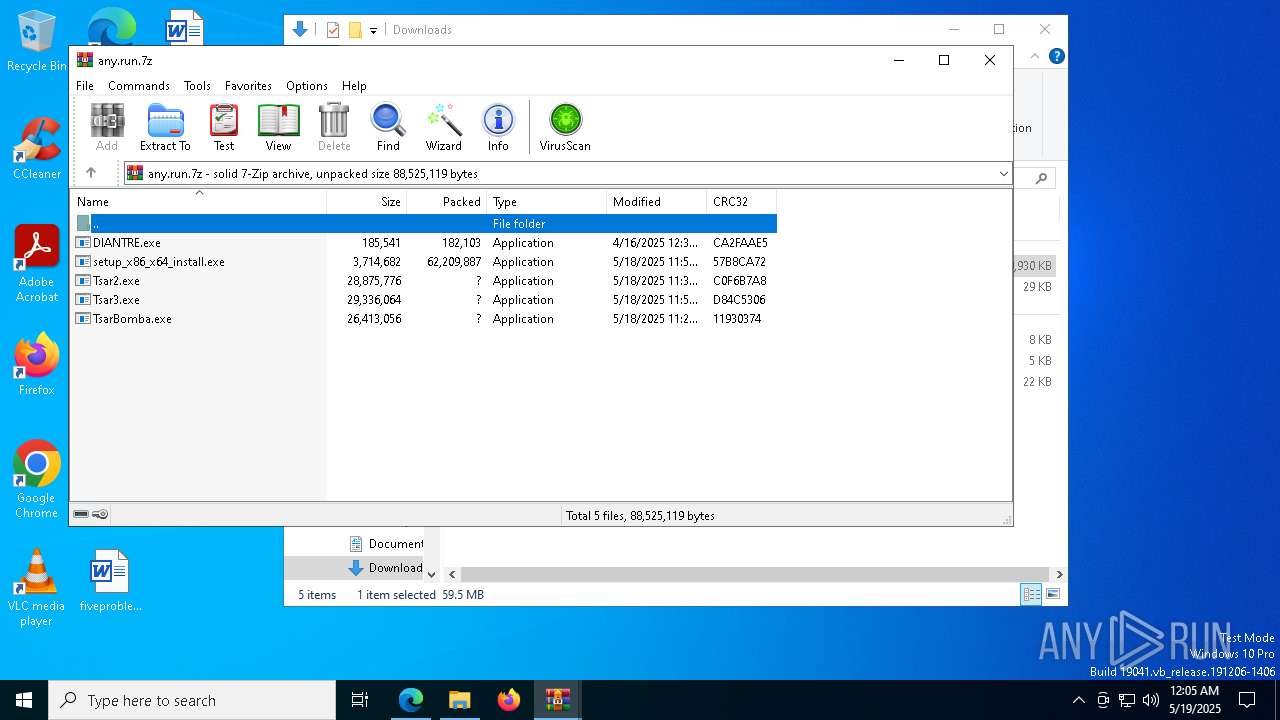
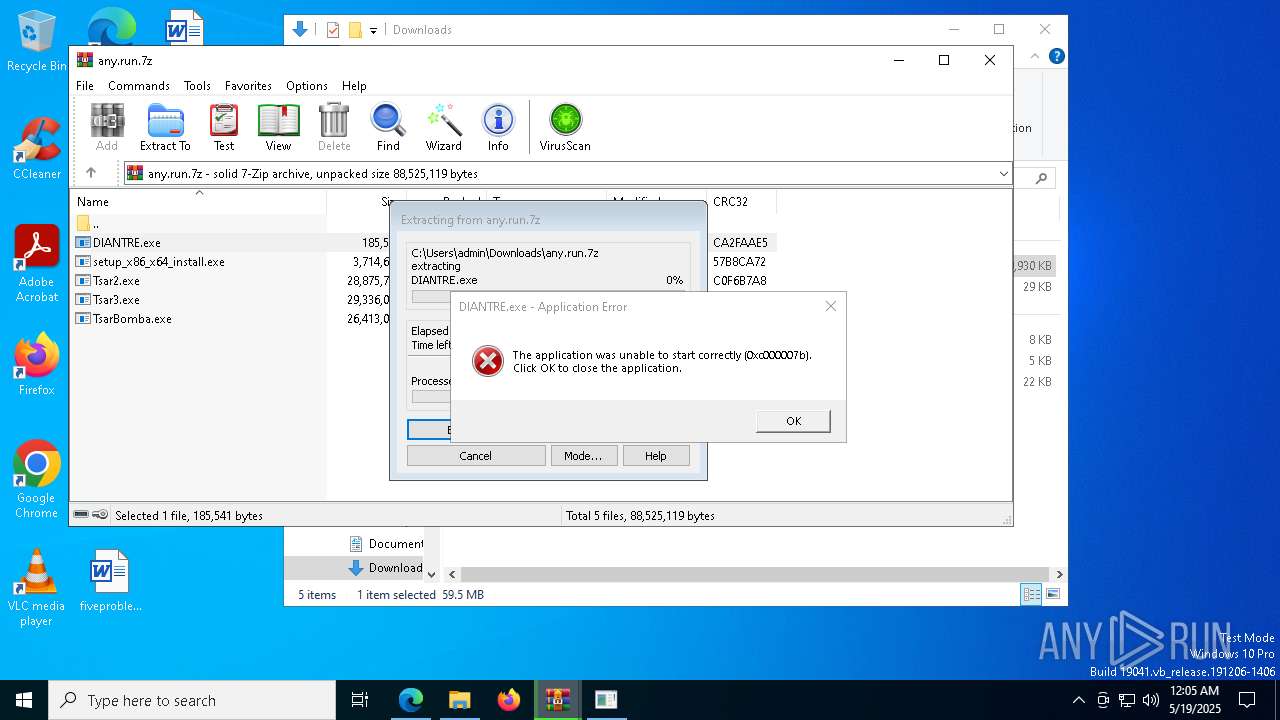
| URL: | dro.pm/b8 |
| Full analysis: | https://app.any.run/tasks/97303f94-7a45-4867-9846-b075d26e2592 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | May 19, 2025, 00:04:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 22808E0E88D6F318CABFCC27EDA11697 |
| SHA1: | AF1E451EA042339C00AF270F52DF56C1083FDE10 |
| SHA256: | 37DF30BD62180E8A7CE71493D86490687F790D3841A097768E5159B425DF26B1 |
| SSDEEP: | 3:cLVtn:cLzn |
MALICIOUS
BACKDOOR has been found (auto)
- Tsar2.exe (PID: 9064)
FLOXIF has been found (auto)
- Tsar2.exe (PID: 9064)
- Tsar2.exe (PID: 8688)
SALITY mutex has been found
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
- Tsar2.exe (PID: 9064)
Changes firewall settings
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
SAINBOX has been detected
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
Changes Security Center notification settings
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
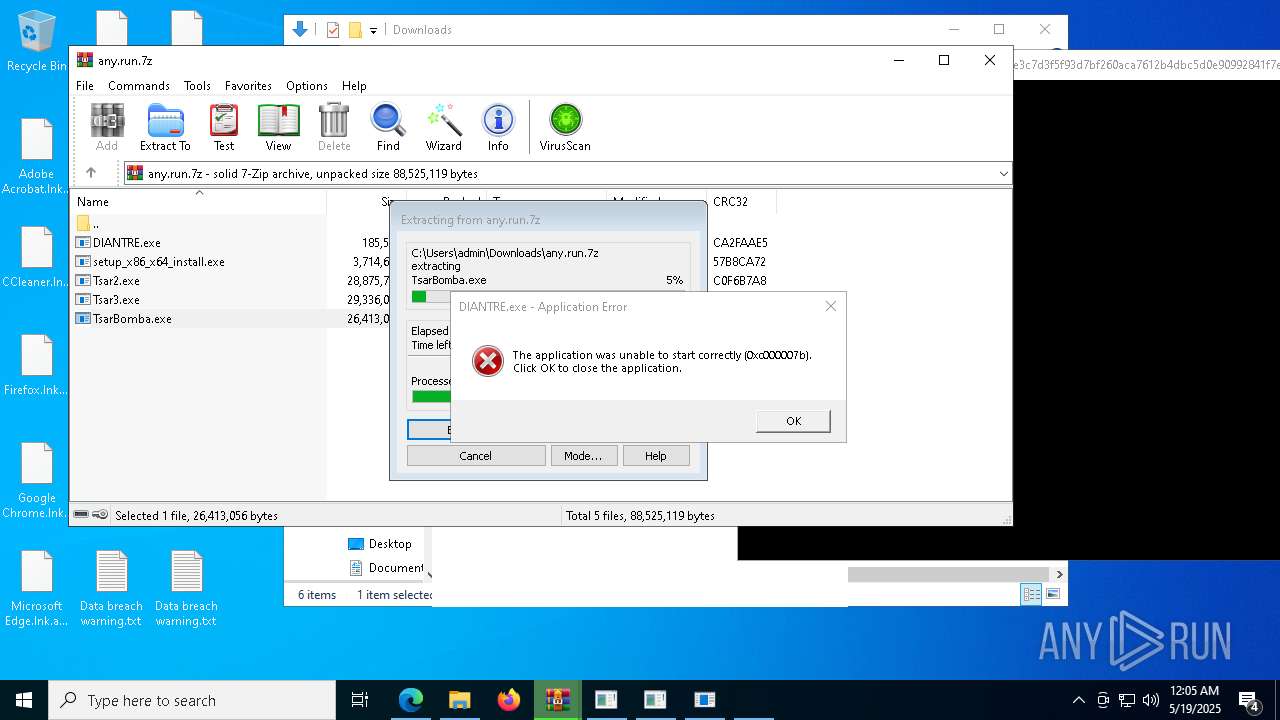
RANSOMWARE has been found (auto)
- TsarBomba.exe (PID: 6048)
FRAMEWORK has been found (auto)
- TsarBomba.exe (PID: 6048)
Executing a file with an untrusted certificate
- 7a8c864ed8b7ca908d3f317d7e63a30a85fb3e8c94070f23f2cf0bfa01c5e0b5.exe (PID: 8620)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8220)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 13332)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
GENERIC has been found (auto)
- TsarBomba.exe (PID: 6048)
- TsarBomba.exe (PID: 6048)
Deletes shadow copies
- cmd.exe (PID: 8940)
- cmd.exe (PID: 9936)
KILLMBR has been found (auto)
- Tsar3.exe (PID: 8156)
Connects to the CnC server
- 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe (PID: 8892)
SILVERFOX has been detected (SURICATA)
- 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe (PID: 8892)
METERPRETER has been detected (SURICATA)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7228)
STEALER has been found (auto)
- TsarBomba.exe (PID: 6048)
ADWARE has been found (auto)
- TsarBomba.exe (PID: 6048)
RAT has been found (auto)
- TsarBomba.exe (PID: 6048)
ADESSTEALER has been found (auto)
- TsarBomba.exe (PID: 6048)
JLOCKER has been found (auto)
- TsarBomba.exe (PID: 6048)
DISCORDTOKEN has been found (auto)
- TsarBomba.exe (PID: 6048)
HIDDENTEAR has been found (auto)
- TsarBomba.exe (PID: 6048)
Adds path to the Windows Defender exclusion list
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4428)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 9084)
- cmd.exe (PID: 13140)
Changes Windows Defender settings
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4428)
- cmd.exe (PID: 13140)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 10896)
- cmd.exe (PID: 10312)
Starts CMD.EXE for self-deleting
- f74ea81bcd59a58e2784f74cd28c63744de51639ccc974507eff5619764b0f4d.exe (PID: 8232)
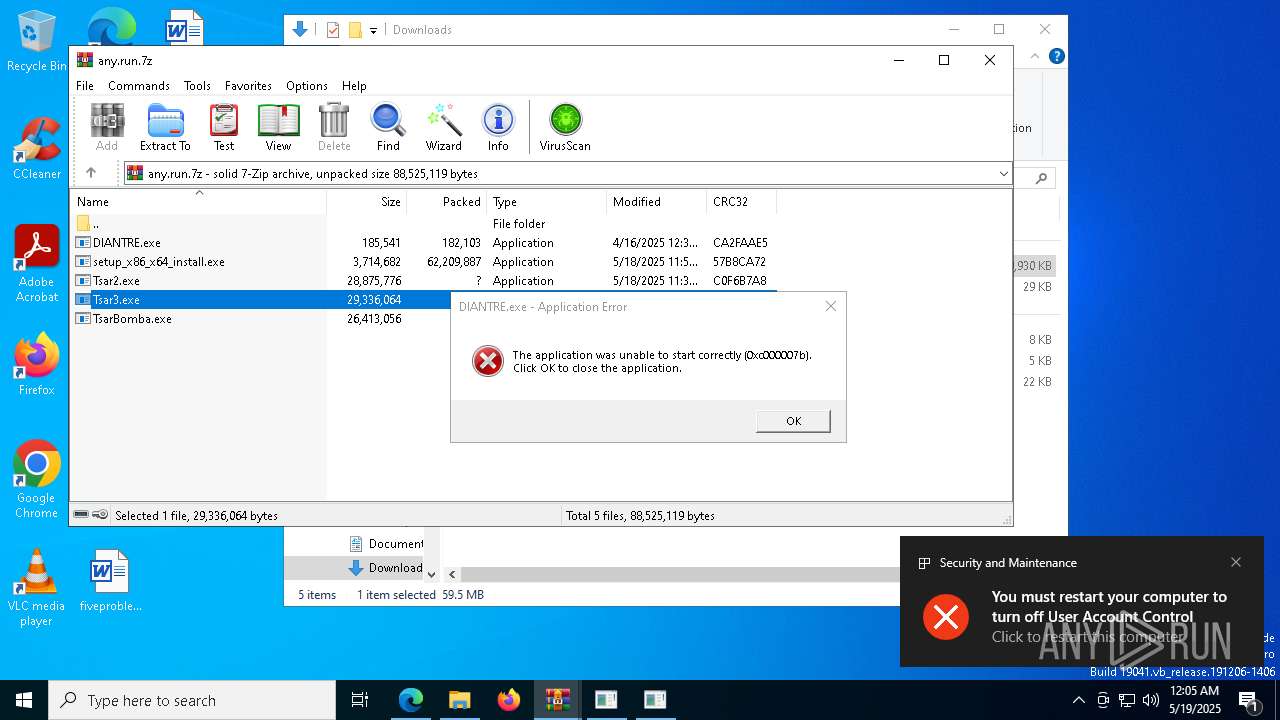
UAC/LUA settings modification
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
Disables Windows firewall
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
SUSPICIOUS
Executable content was dropped or overwritten
- Tsar2.exe (PID: 9064)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
- TsarBomba.exe (PID: 6048)
- Tsar3.exe (PID: 8156)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4428)
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
- e98182d44dc7ec4a154021757da3132769db318cf9d78f15fc06c92682f8a253.exe (PID: 9944)
- ffcc4cc79785d4b96b26d0db89383627e084c3483b1e787ac1150d8e6917f506.exe (PID: 10552)
- f497e0f58f93c129f70a89f01aa20b3a5372e4e9f83580ad9a1d8e613ab389a9.exe (PID: 10440)
- Tsar2.exe (PID: 8688)
- TsarBomba.exe (PID: 10184)
- setup_x86_x64_install.exe (PID: 11724)
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 9960)
- InstallUtil.exe (PID: 11048)
- ResonateII.exe (PID: 6268)
Process drops legitimate windows executable
- Tsar2.exe (PID: 9064)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
- TsarBomba.exe (PID: 6048)
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
- InstallUtil.exe (PID: 11048)
Starts a Microsoft application from unusual location
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 1088)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 9084)
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 13184)
Reads security settings of Internet Explorer
- Tsar2.exe (PID: 9064)
- WinRAR.exe (PID: 9088)
- ShellExperienceHost.exe (PID: 8148)
- TsarBomba.exe (PID: 6048)
Reads the history of recent RDP connections
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
Starts POWERSHELL.EXE for commands execution
- 1bad2b6e8ab16c5a692b2d05f68f7924a73a5818ddf3a9678ca8caab3568a78e.exe (PID: 5772)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4428)
- f258f660f30a7f9669b025d9c2d5663f16c576a03f48e6fc169af692d43336c3.exe (PID: 10292)
- cmd.exe (PID: 13140)
Starts CMD.EXE for commands execution
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 8200)
- 188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe (PID: 8608)
- ab0acdb0c45ccafcc0ec594d30dc8153936574dde9ebe4e0b22504770361c666.exe (PID: 9916)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4428)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 9084)
- f74ea81bcd59a58e2784f74cd28c63744de51639ccc974507eff5619764b0f4d.exe (PID: 8232)
Uses WMIC.EXE to obtain Windows Installer data
- 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe (PID: 660)
Contacting a server suspected of hosting an CnC
- 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe (PID: 8892)
Connects to unusual port
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7228)
- 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe (PID: 8892)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 668)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 8968)
Checks for external IP
- svchost.exe (PID: 2196)
- 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe (PID: 660)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 8968)
- e962736250ea5b158e2b690f6154ef8d3309c9e63aadb575583ebaded94b049e.exe (PID: 9016)
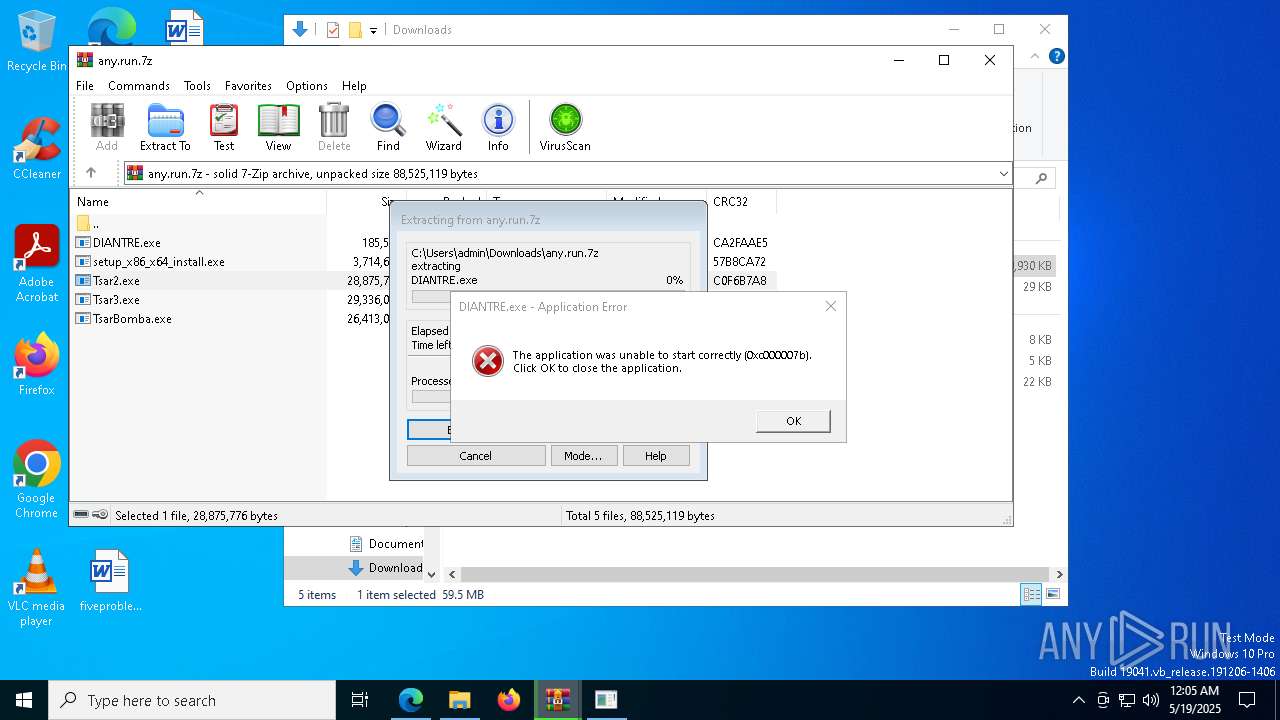
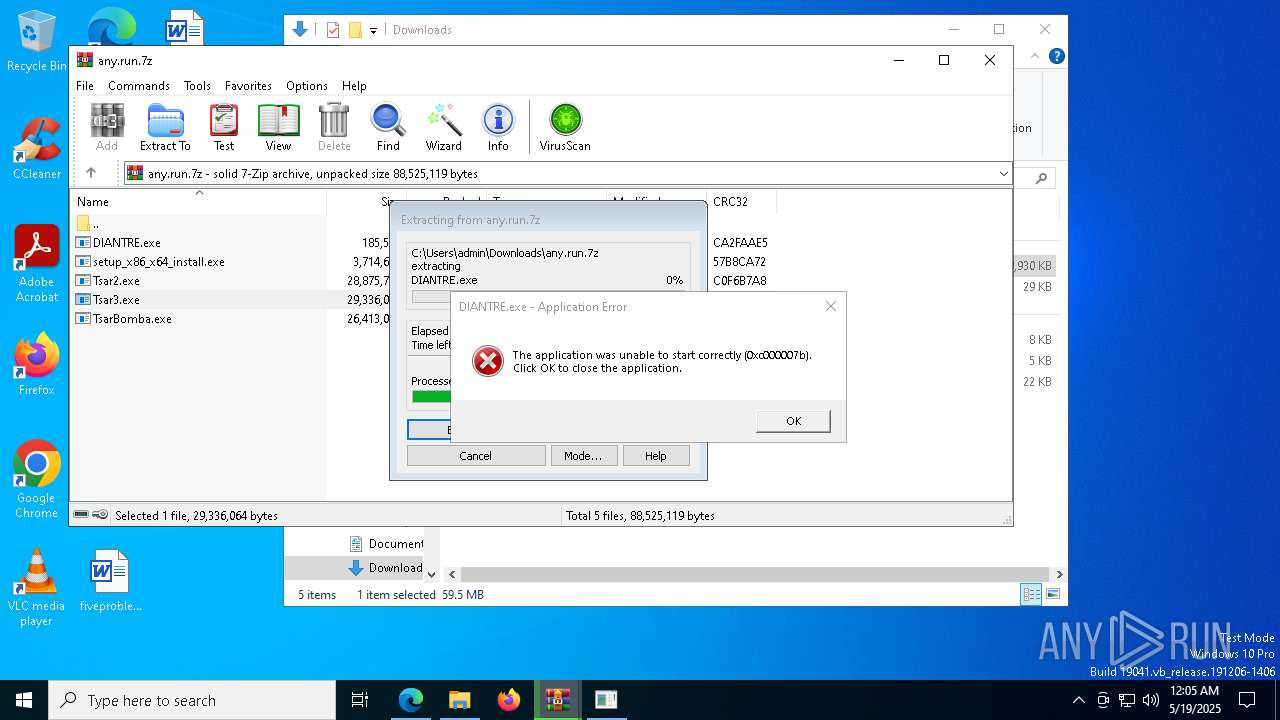
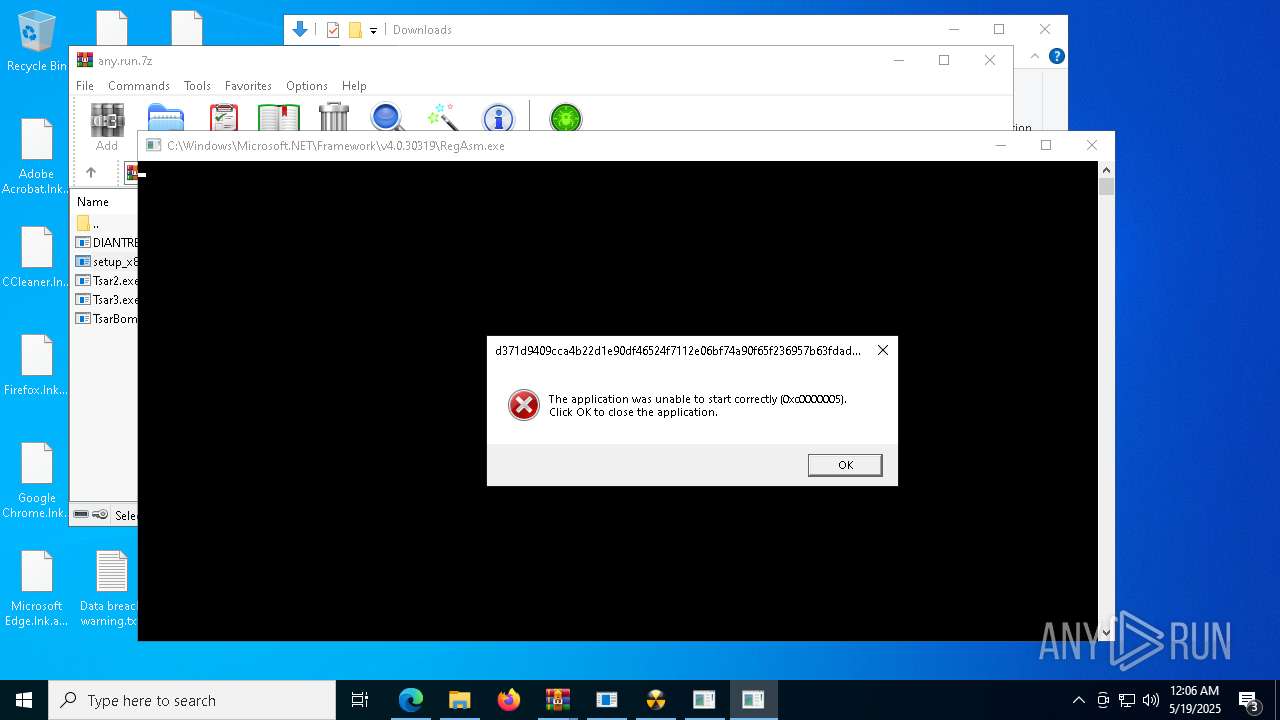
Executes application which crashes
- 954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe (PID: 664)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 13352)
- 0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe (PID: 9132)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 13404)
Executed via WMI
- schtasks.exe (PID: 10328)
- schtasks.exe (PID: 10528)
- schtasks.exe (PID: 10376)
- schtasks.exe (PID: 10448)
- schtasks.exe (PID: 10580)
- schtasks.exe (PID: 10660)
- schtasks.exe (PID: 10620)
- schtasks.exe (PID: 11096)
- schtasks.exe (PID: 11024)
- schtasks.exe (PID: 11180)
- schtasks.exe (PID: 11148)
- schtasks.exe (PID: 10492)
- schtasks.exe (PID: 10356)
- schtasks.exe (PID: 4200)
- schtasks.exe (PID: 10532)
- schtasks.exe (PID: 8328)
- schtasks.exe (PID: 10512)
- schtasks.exe (PID: 10596)
Script adds exclusion path to Windows Defender
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4428)
- cmd.exe (PID: 13140)
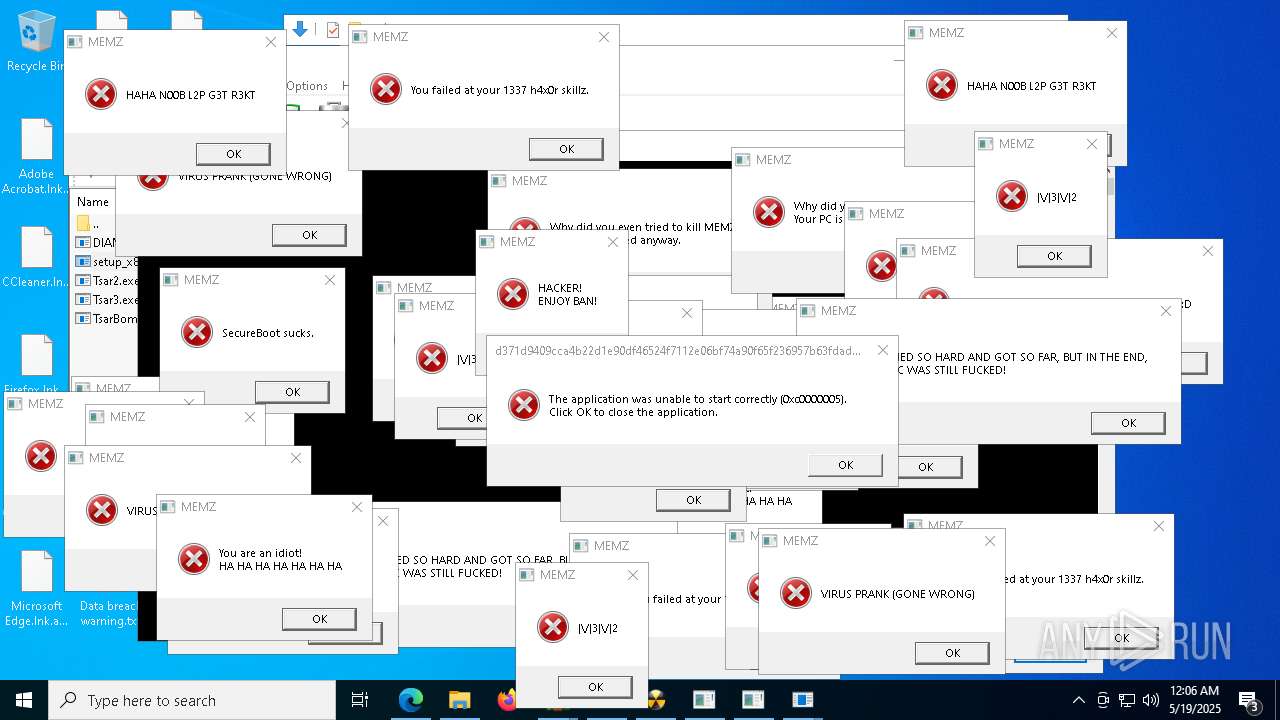
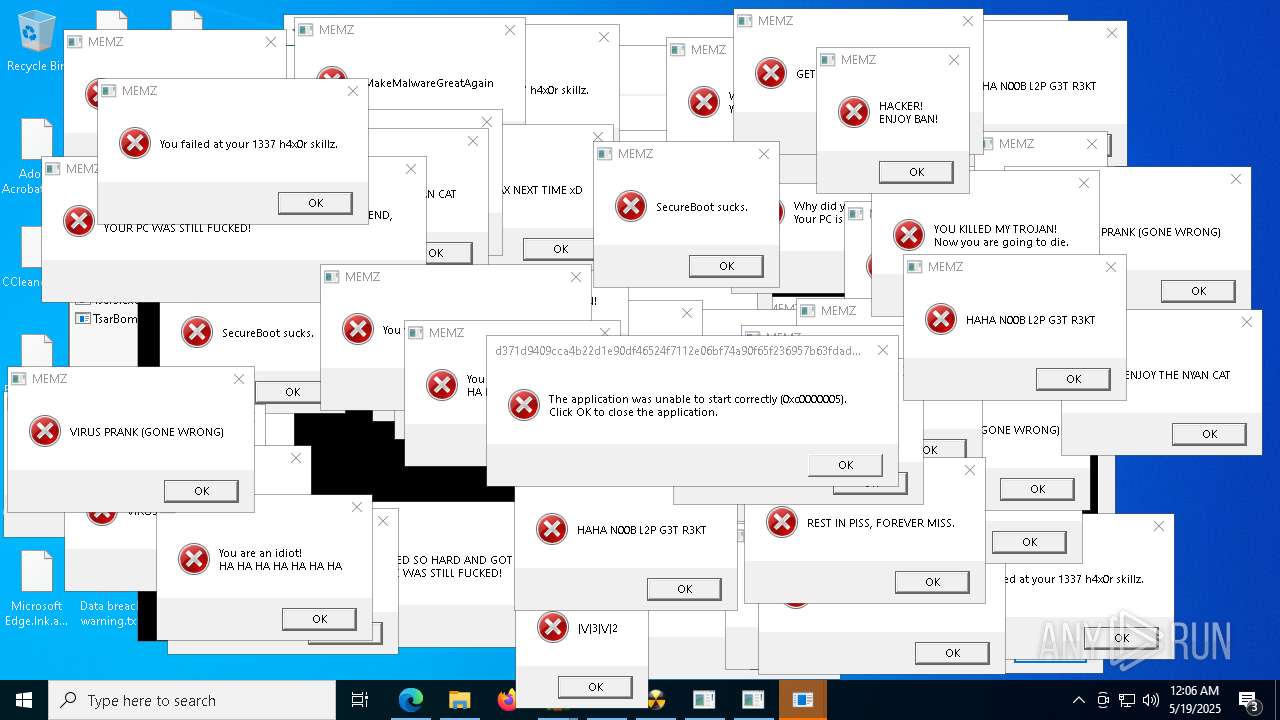
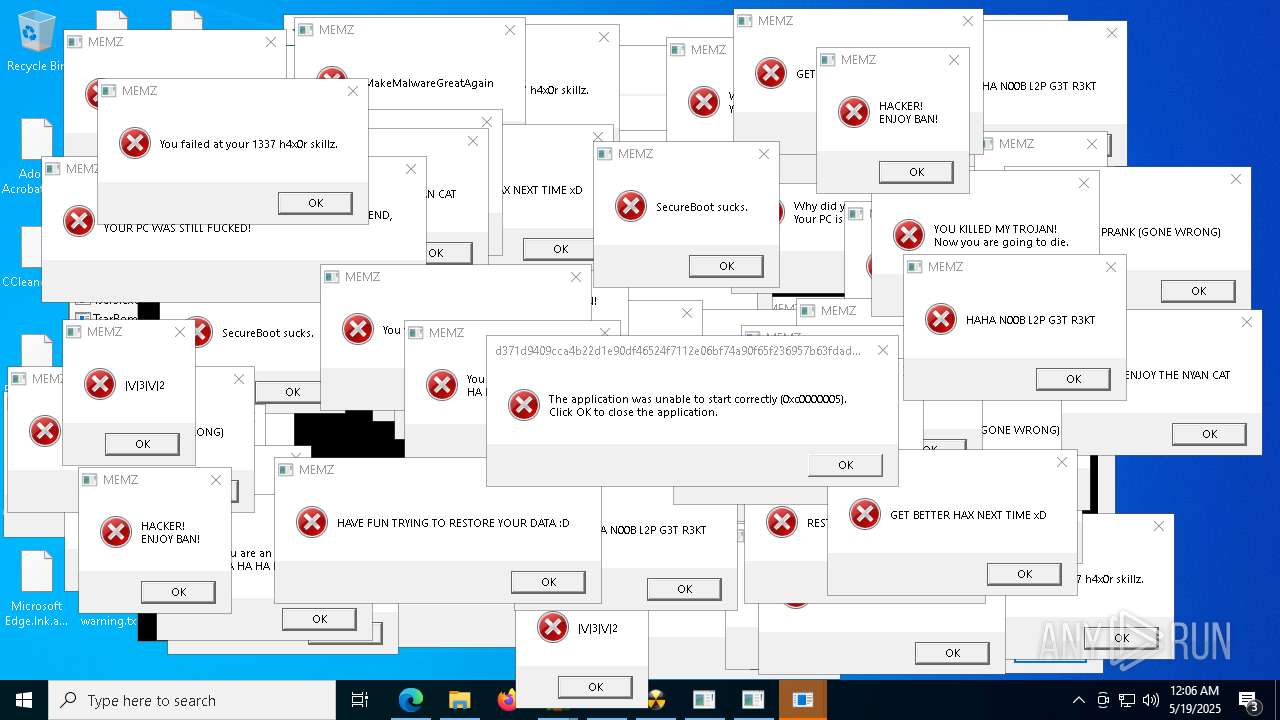
Application launched itself
- MEMZ.exe (PID: 7352)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8088)
Executing commands from a ".bat" file
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4428)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 10272)
- MSBuild.exe (PID: 8680)
BASE64 encoded PowerShell command has been detected
- f258f660f30a7f9669b025d9c2d5663f16c576a03f48e6fc169af692d43336c3.exe (PID: 10292)
Drops 7-zip archiver for unpacking
- setup_x86_x64_install.exe (PID: 11724)
Base64-obfuscated command line is found
- f258f660f30a7f9669b025d9c2d5663f16c576a03f48e6fc169af692d43336c3.exe (PID: 10292)
Starts application with an unusual extension
- cmd.exe (PID: 12968)
The process executes via Task Scheduler
- mshta.exe (PID: 14332)
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 13928)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1116)
Executes as Windows Service
- VSSVC.exe (PID: 6264)
INFO
Manual execution by a user
- WinRAR.exe (PID: 8764)
- WinRAR.exe (PID: 9088)
Application launched itself
- msedge.exe (PID: 7180)
Reads the computer name
- identity_helper.exe (PID: 8532)
- Tsar2.exe (PID: 9064)
- ResonateII.exe (PID: 6268)
- TsarBomba.exe (PID: 6048)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
- ShellExperienceHost.exe (PID: 8148)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 1088)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 668)
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
Reads Environment values
- identity_helper.exe (PID: 8532)
Checks supported languages
- identity_helper.exe (PID: 8532)
- Tsar2.exe (PID: 9064)
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
- 0fd46aca09c54c256d22420d2ac3e947ff204a42a24158dfcb562de18a77f3f1.exe (PID: 4628)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 668)
- ResonateII.exe (PID: 6268)
- ShellExperienceHost.exe (PID: 8148)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 1088)
- TsarBomba.exe (PID: 6048)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 9088)
The sample compiled with english language support
- WinRAR.exe (PID: 9088)
- TsarBomba.exe (PID: 6048)
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
- setup_x86_x64_install.exe (PID: 11724)
- InstallUtil.exe (PID: 11048)
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
Create files in a temporary directory
- Tsar2.exe (PID: 9064)
- TsarBomba.exe (PID: 6048)
The sample compiled with chinese language support
- Tsar2.exe (PID: 9064)
Process checks computer location settings
- Tsar2.exe (PID: 9064)
- TsarBomba.exe (PID: 6048)
Creates files in the program directory
- e934e286e2ec0985f44cc3109c6db434a65aeb731a8979e931164881ba2d4729.exe (PID: 9056)
The sample compiled with russian language support
- TsarBomba.exe (PID: 6048)
FSG packer has been detected
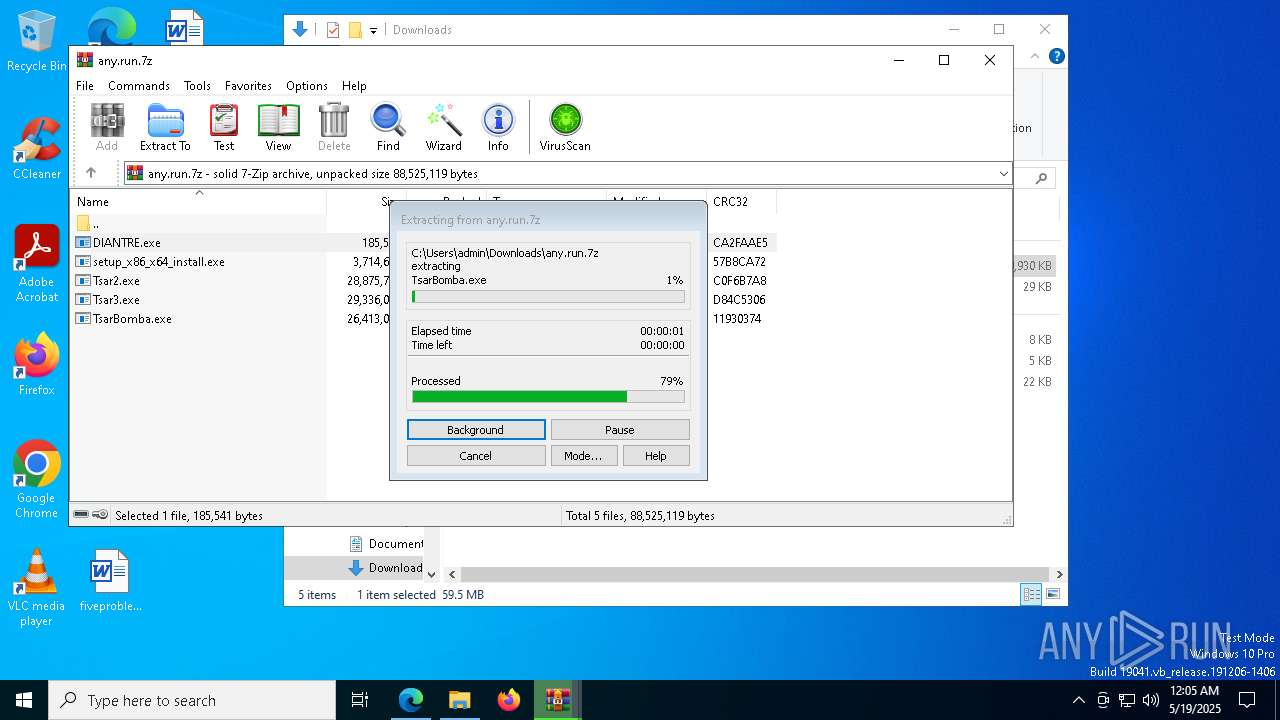
- DIANTRE.exe (PID: 7816)
Attempting to use instant messaging service
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 10272)
Compiled with Borland Delphi (YARA)
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
UPX packer has been detected
- aae8a9852809300d5ee4f5a8031f42f660dff3e427aef081d9aeabb2dca84058.exe (PID: 9044)
Application based on Java
- javaw.exe (PID: 10964)
Changes the display of characters in the console
- cmd.exe (PID: 12968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
380
Monitored processes
236
Malicious processes
15
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Users\admin\AppData\Local\Temp\876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe" | C:\Users\admin\AppData\Local\Temp\876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe | TsarBomba.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Local\Temp\954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe" | C:\Users\admin\AppData\Local\Temp\954d8fcd6b74d76999f9ec033ca855ffdab6595be23039f03bc4c6017fa3932c.exe | TsarBomba.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 3762504530 Version: 0.0.0.0 Modules
| |||||||||||||||
| 668 | "C:\Users\admin\AppData\Local\Temp\0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe" | C:\Users\admin\AppData\Local\Temp\0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe | TsarBomba.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\Temp\60e76eda46185d1d2e9463d15e31d4c87eb03535d368cc3471c55992bc99ad5f.exe" | C:\Users\admin\AppData\Local\Temp\60e76eda46185d1d2e9463d15e31d4c87eb03535d368cc3471c55992bc99ad5f.exe | — | TsarBomba.exe | |||||||||||
User: admin Company: VAN32 Integrity Level: HIGH Description: WinLocker Builder Version: 0.4.0.0 Modules
| |||||||||||||||
| 968 | powershell -Command "& { }" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | 1bad2b6e8ab16c5a692b2d05f68f7924a73a5818ddf3a9678ca8caab3568a78e.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=6864 --field-trial-handle=2164,i,14310189153868690160,1868098558587580948,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1056 | "C:\Users\admin\AppData\Local\Temp\4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe" | C:\Users\admin\AppData\Local\Temp\4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe | — | TsarBomba.exe | |||||||||||
User: admin Company: 博典创新科技 Integrity Level: HIGH Description: 亚历山大学者版 Version: 3.5.2240.18 Modules
| |||||||||||||||
| 1088 | "C:\Users\admin\AppData\Local\Temp\01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe" | C:\Users\admin\AppData\Local\Temp\01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe | — | TsarBomba.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Shell Extension Version: 1.0.0.0 Modules
| |||||||||||||||
| 1116 | "cmd.exe" /C timeout 1 && del "C:\Users\admin\AppData\Local\Temp\f74ea81bcd59a58e2784f74cd28c63744de51639ccc974507eff5619764b0f4d.exe" | C:\Windows\SysWOW64\cmd.exe | — | f74ea81bcd59a58e2784f74cd28c63744de51639ccc974507eff5619764b0f4d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=7312 --field-trial-handle=2164,i,14310189153868690160,1868098558587580948,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
92 161
Read events
90 759
Write events
1 393
Delete events
9
Modification events
| (PID) Process: | (4112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (4112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (7180) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7180) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7180) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7180) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
142
Suspicious files
669
Text files
369
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b0c4.TMP | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b0d3.TMP | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b0d3.TMP | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b0e3.TMP | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b0f3.TMP | — | |
MD5:— | SHA256:— | |||
| 7180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
99
DNS requests
95
Threats
23
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8620 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8968 | 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
660 | 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
1852 | svchost.exe | HEAD | 200 | 2.19.126.157:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1747698237&P2=404&P3=2&P4=JWjeqkFDxuz2FSSaz%2bHpMrunvxl4wDEGRnFpv4%2fUhq9DCXQYRuYcPrW3z0zilEgoeF9i1TJ28RM2v2pAx6pjSw%3d%3d | unknown | — | — | whitelisted |
9016 | e962736250ea5b158e2b690f6154ef8d3309c9e63aadb575583ebaded94b049e.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/84.17.48.85 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7180 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7420 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7420 | msedge.exe | 86.80.32.182:80 | dro.pm | KPN B.V. | NL | unknown |
7420 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7420 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
dro.pm |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (gateway .discord .gg) |
8856 | 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Misc activity | ET INFO Observed Discord Service Domain (gateway .discord .gg) in TLS SNI |
7228 | 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe | Targeted Malicious Activity was Detected | ET HUNTING Suspicious Empty SSL Certificate - Observed in Cobalt Strike |
7228 | 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe | A Network Trojan was detected | ET MALWARE Meterpreter or Other Reverse Shell SSL Cert |
8892 | 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe | Malware Command and Control Activity Detected | ET MALWARE Winos4.0 Framework CnC Login Message |
8892 | 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe | Malware Command and Control Activity Detected | BACKDOOR [ANY.RUN] SilverFox Keep-Alive Client Packet |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
660 | 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
660 | 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |