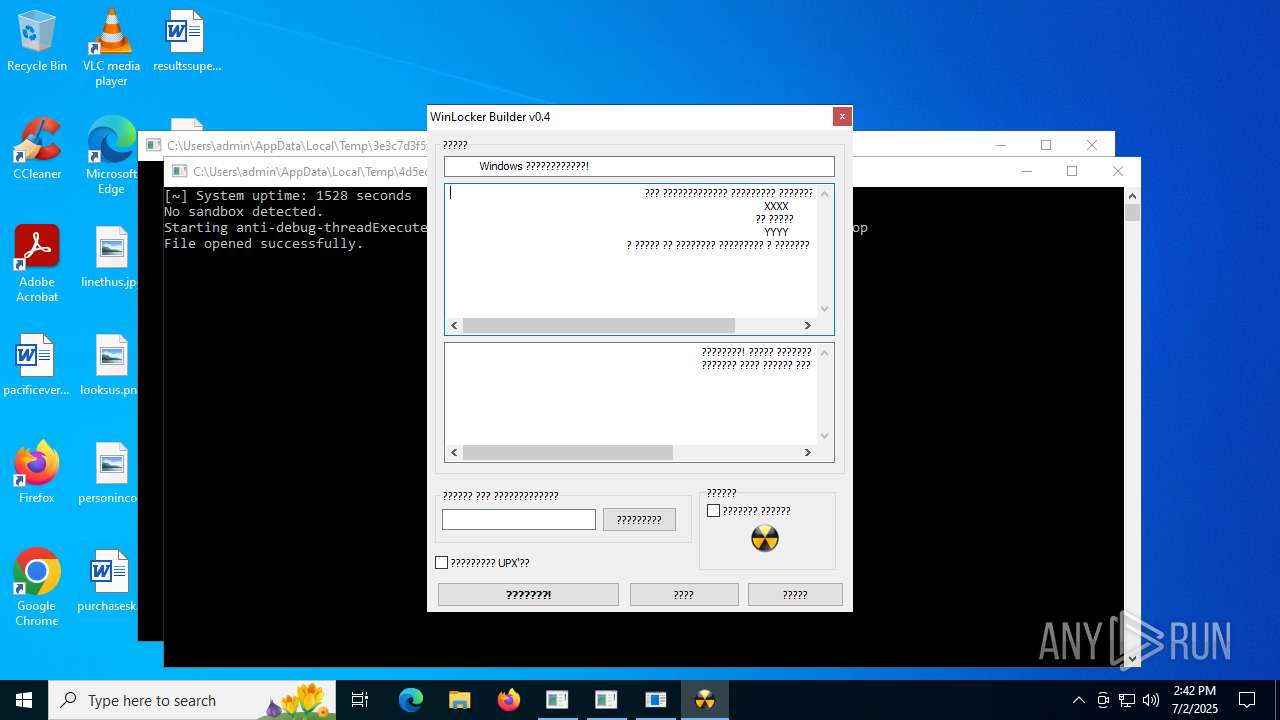
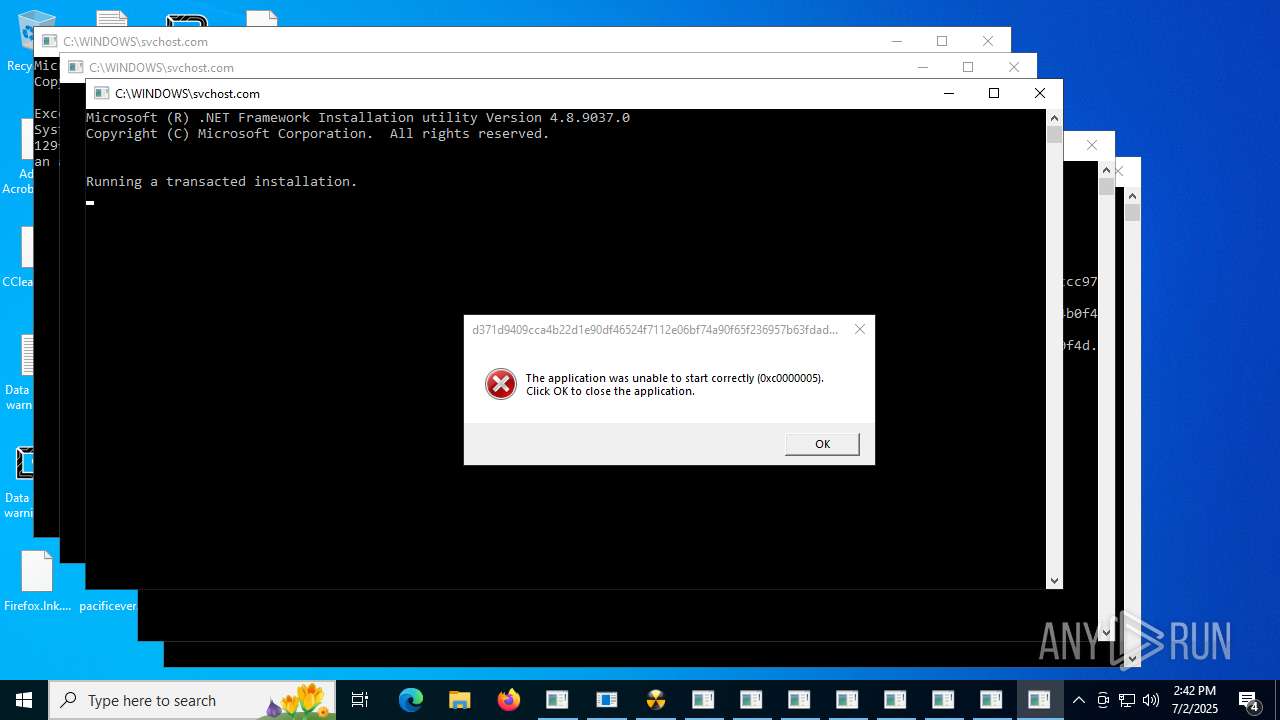
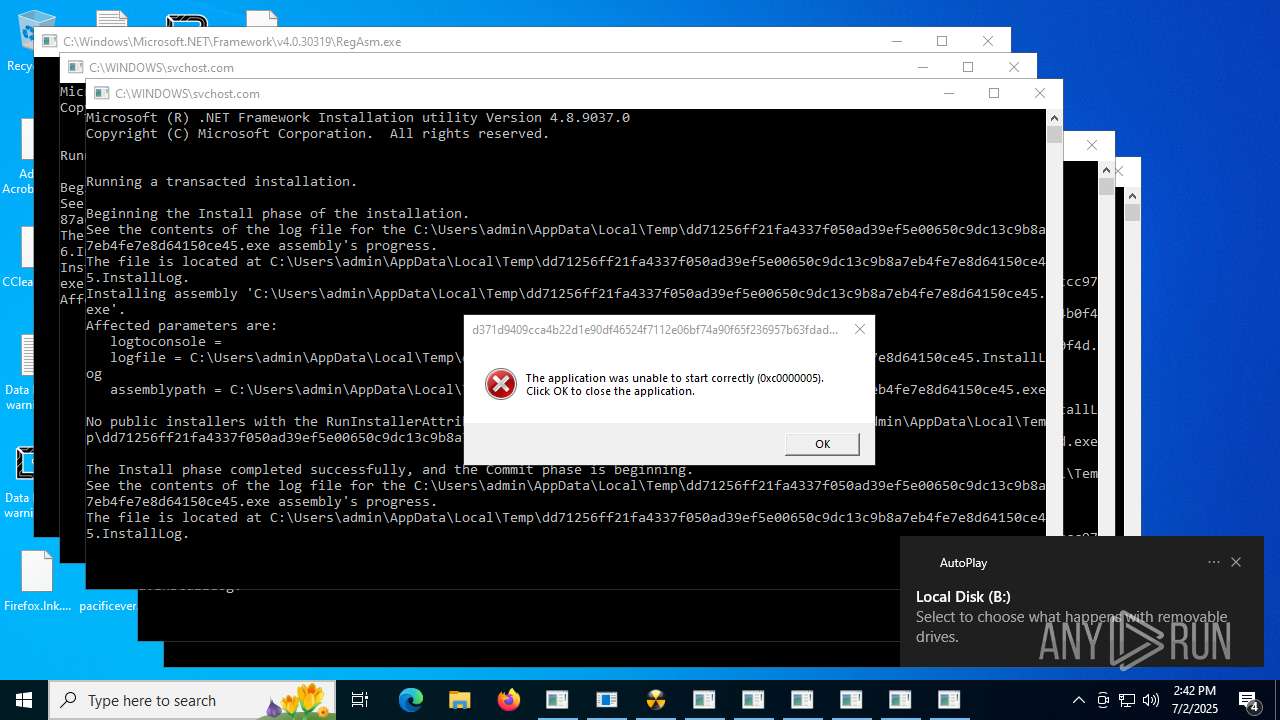
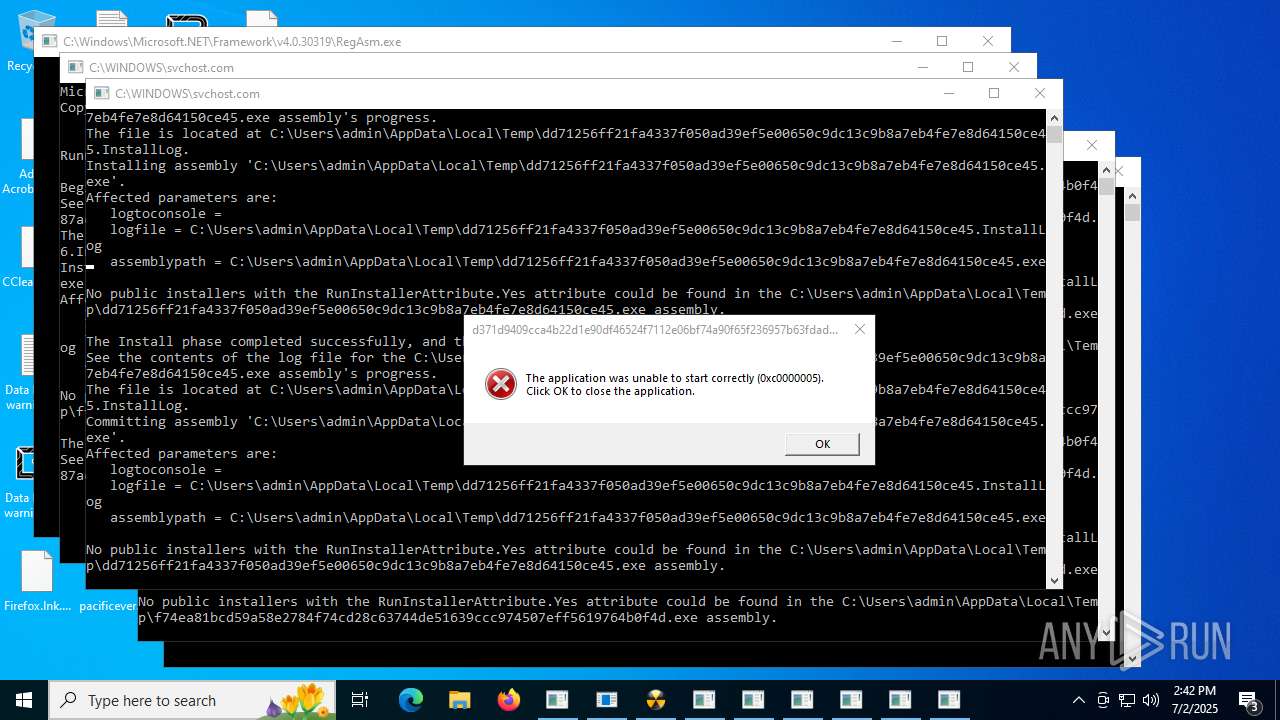
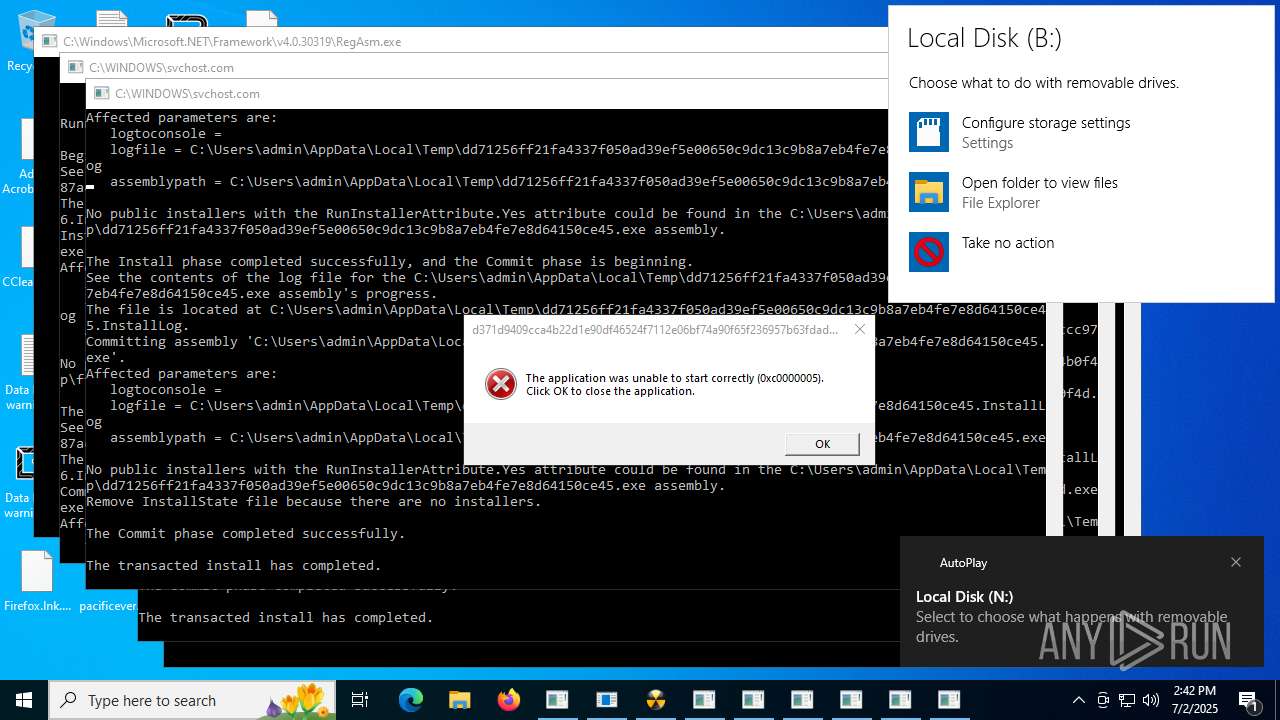
| File name: | TsarBomba.exe |
| Full analysis: | https://app.any.run/tasks/56d1a9a6-7bfe-4130-92ed-d7e62f59d9e6 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | July 02, 2025, 14:41:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 4 sections |
| MD5: | 91025D6F02E542F2E37FFCE7D0CE8B51 |
| SHA1: | E2D80EF6075556CD23CE0445473C061F200B5DD4 |
| SHA256: | 3755718DB9D33F4ABA2563DE454D4530A308B41B1096C904102D08E2101F2020 |
| SSDEEP: | 196608:OhuvCqhWk4mEsw8VKcgdiyXXLO7Lz30zVKHfXk7ra62OIkwYTQUR2NA:gg4t8VrgTioVcfXka62Bk7TQUR2NA |
MALICIOUS
VALLEY has been found (auto)
- TsarBomba.exe (PID: 6860)
- TsarBomba.exe (PID: 6860)
REDLINE has been found (auto)
- TsarBomba.exe (PID: 6860)
RANSOMWARE has been found (auto)
- TsarBomba.exe (PID: 6860)
FRAMEWORK has been found (auto)
- TsarBomba.exe (PID: 6860)
DCRAT has been found (auto)
- TsarBomba.exe (PID: 6860)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
GENERIC has been found (auto)
- TsarBomba.exe (PID: 6860)
- TsarBomba.exe (PID: 6860)
Executing a file with an untrusted certificate
- 7a8c864ed8b7ca908d3f317d7e63a30a85fb3e8c94070f23f2cf0bfa01c5e0b5.exe (PID: 4084)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- remoteadmin.exe (PID: 4080)
- mshta.exe (PID: 12880)
DBATLOADER has been found (auto)
- TsarBomba.exe (PID: 6860)
CONTI mutex has been found
- 80e3a04fa68be799b3c91737e1918f8394b250603a231a251524244e4d7f77d9.exe (PID: 7008)
RAWORLD mutex has been found
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
COBALTSTRIKE has been found (auto)
- TsarBomba.exe (PID: 6860)
Steals credentials from Web Browsers
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
Run PowerShell with an invisible window
- powershell.exe (PID: 7548)
- powershell.exe (PID: 9156)
Actions looks like stealing of personal data
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
STEALER has been found (auto)
- TsarBomba.exe (PID: 6860)
Adds path to the Windows Defender exclusion list
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 8428)
- cmd.exe (PID: 8984)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 7960)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
Changes Windows Defender settings
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- cmd.exe (PID: 8984)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
Deletes shadow copies
- cmd.exe (PID: 7100)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 9472)
- cmd.exe (PID: 10164)
- cmd.exe (PID: 11788)
- cmd.exe (PID: 9956)
- cmd.exe (PID: 12460)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 5724)
- cmd.exe (PID: 8268)
- cmd.exe (PID: 8604)
- cmd.exe (PID: 9320)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
Renames files like ransomware
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
RANSOMWARE has been detected
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
ADWARE has been found (auto)
- TsarBomba.exe (PID: 6860)
VIDAR mutex has been found
- MSBuild.exe (PID: 7352)
RAT has been found (auto)
- TsarBomba.exe (PID: 6860)
- TsarBomba.exe (PID: 6860)
AVEMARIA has been found (auto)
- TsarBomba.exe (PID: 6860)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8568)
Create files in the Startup directory
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 7688)
NANOCORE has been found (auto)
- TsarBomba.exe (PID: 6860)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
NESHTA mutex has been found
- InstallUtil.exe (PID: 8900)
REDLINE has been detected (YARA)
- TsarBomba.exe (PID: 6860)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
XORed URL has been found (YARA)
- TsarBomba.exe (PID: 6860)
DISCORDGRABBER has been detected (YARA)
- TsarBomba.exe (PID: 6860)
[YARA] LockBit is detected
- TsarBomba.exe (PID: 6860)
UMBRALSTEALER has been detected (YARA)
- TsarBomba.exe (PID: 6860)
Changes the autorun value in the registry
- svchost.exe (PID: 9084)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8568)
- MSBuild.exe (PID: 1828)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
METERPRETER has been detected (SURICATA)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
JLOCKER has been found (auto)
- TsarBomba.exe (PID: 6860)
DISCORDTOKEN has been found (auto)
- TsarBomba.exe (PID: 6860)
HIDDENTEAR has been found (auto)
- TsarBomba.exe (PID: 6860)
Connects to the CnC server
- svchost.exe (PID: 2200)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
Disables Windows Defender
- RegAsm.exe (PID: 8648)
Changes the login/logoff helper path in the registry
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
Changes the AppInit_DLLs value (autorun option)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
SNAKEKEYLOGGER has been detected (SURICATA)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
Starts NET.EXE for service management
- 1bad2b6e8ab16c5a692b2d05f68f7924a73a5818ddf3a9678ca8caab3568a78e.exe (PID: 4932)
- net.exe (PID: 9048)
- net.exe (PID: 9144)
- net.exe (PID: 9128)
- net.exe (PID: 11648)
- net.exe (PID: 2588)
- net.exe (PID: 8212)
- net.exe (PID: 7932)
- net.exe (PID: 12372)
- net.exe (PID: 12636)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 4104)
Deletes a file (SCRIPT)
- wscript.exe (PID: 4104)
AGENTTESLA has been found (auto)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 9156)
SUSPICIOUS
Process drops legitimate windows executable
- TsarBomba.exe (PID: 6860)
- InstallUtil.exe (PID: 8900)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- MSBuild.exe (PID: 1828)
Starts a Microsoft application from unusual location
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 8428)
Reads security settings of Internet Explorer
- TsarBomba.exe (PID: 6860)
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
- MSBuild.exe (PID: 7352)
- ShellExperienceHost.exe (PID: 8920)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- svchost.com (PID: 9792)
- svchost.com (PID: 9672)
- svchost.com (PID: 10220)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 7960)
- svchost.com (PID: 10088)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- MSBuild.exe (PID: 1828)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe (PID: 1356)
- RegAsm.exe (PID: 8648)
Reads the date of Windows installation
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
Executable content was dropped or overwritten
- TsarBomba.exe (PID: 6860)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 7688)
- InstallUtil.exe (PID: 8900)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8568)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- MSBuild.exe (PID: 1828)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
Starts CMD.EXE for commands execution
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe (PID: 1480)
- 80e3a04fa68be799b3c91737e1918f8394b250603a231a251524244e4d7f77d9.exe (PID: 7008)
- ab0acdb0c45ccafcc0ec594d30dc8153936574dde9ebe4e0b22504770361c666.exe (PID: 5724)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 8428)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- images.exe (PID: 7628)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
Start notepad (likely ransomware note)
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
The process creates files with name similar to system file names
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
Creates or modifies Windows services
- 539b377d4a33d1e884f18ecf0e0b0330e5dc26023b7ae051843cac8014142d98.exe (PID: 3672)
Creates file in the systems drive root
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
Found IP address in command line
- powershell.exe (PID: 7548)
- powershell.exe (PID: 9156)
Probably download files using WebClient
- mshta.exe (PID: 7116)
- mshta.exe (PID: 8276)
Manipulates environment variables
- powershell.exe (PID: 7548)
- powershell.exe (PID: 9156)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 7116)
- 1bad2b6e8ab16c5a692b2d05f68f7924a73a5818ddf3a9678ca8caab3568a78e.exe (PID: 4932)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- mshta.exe (PID: 8276)
- cmd.exe (PID: 8984)
- RegAsm.exe (PID: 8648)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
Starts process via Powershell
- powershell.exe (PID: 7548)
- powershell.exe (PID: 9156)
Script adds exclusion path to Windows Defender
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- cmd.exe (PID: 8984)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
Write to the desktop.ini file (may be used to cloak folders)
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
- c348c7e4d9028bdf84aba828bbb81ce46ae55c0246a94351edbfb9c63e41a8ee.exe (PID: 8456)
Executes as Windows Service
- VSSVC.exe (PID: 7836)
Uses WMIC.EXE to obtain Windows Installer data
- 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe (PID: 7656)
Executed via WMI
- schtasks.exe (PID: 6420)
- schtasks.exe (PID: 7692)
- schtasks.exe (PID: 8808)
- schtasks.exe (PID: 8228)
- schtasks.exe (PID: 9320)
- schtasks.exe (PID: 9580)
- schtasks.exe (PID: 9832)
- schtasks.exe (PID: 8544)
- schtasks.exe (PID: 8288)
- schtasks.exe (PID: 10212)
- schtasks.exe (PID: 5372)
- schtasks.exe (PID: 9416)
- schtasks.exe (PID: 9760)
- schtasks.exe (PID: 8836)
- schtasks.exe (PID: 9936)
- schtasks.exe (PID: 8824)
- schtasks.exe (PID: 8108)
- schtasks.exe (PID: 7948)
Reads the BIOS version
- aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe (PID: 1736)
Checks for Java to be installed
- b066d97c63093902c0debe32ed5a001cc150eae3fb841d87a58408762d32466e.exe (PID: 8196)
Mutex name with non-standard characters
- InstallUtil.exe (PID: 8900)
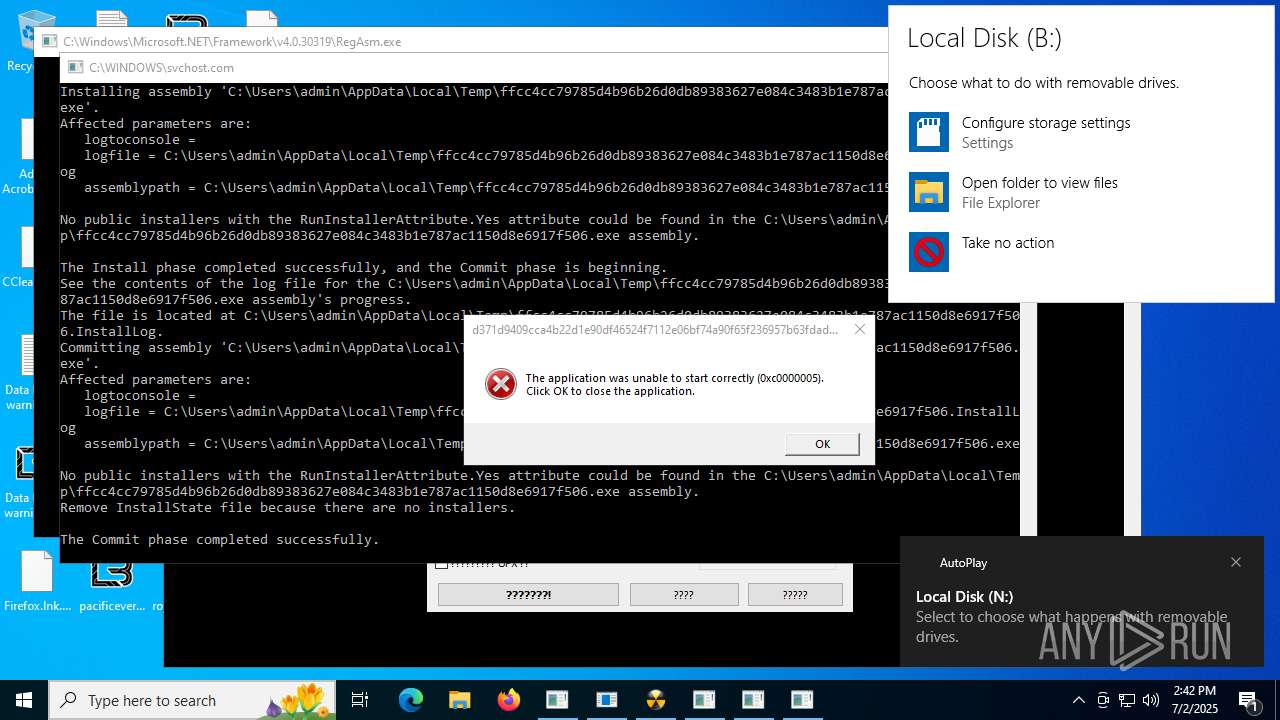
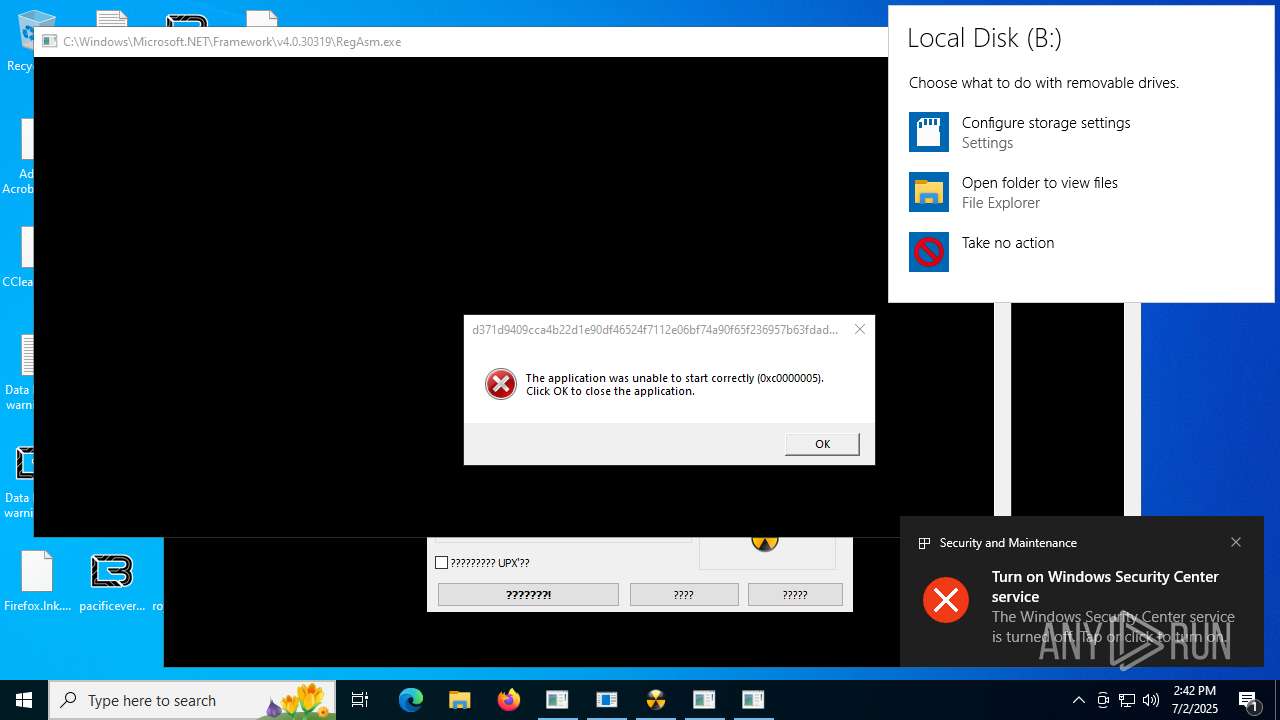
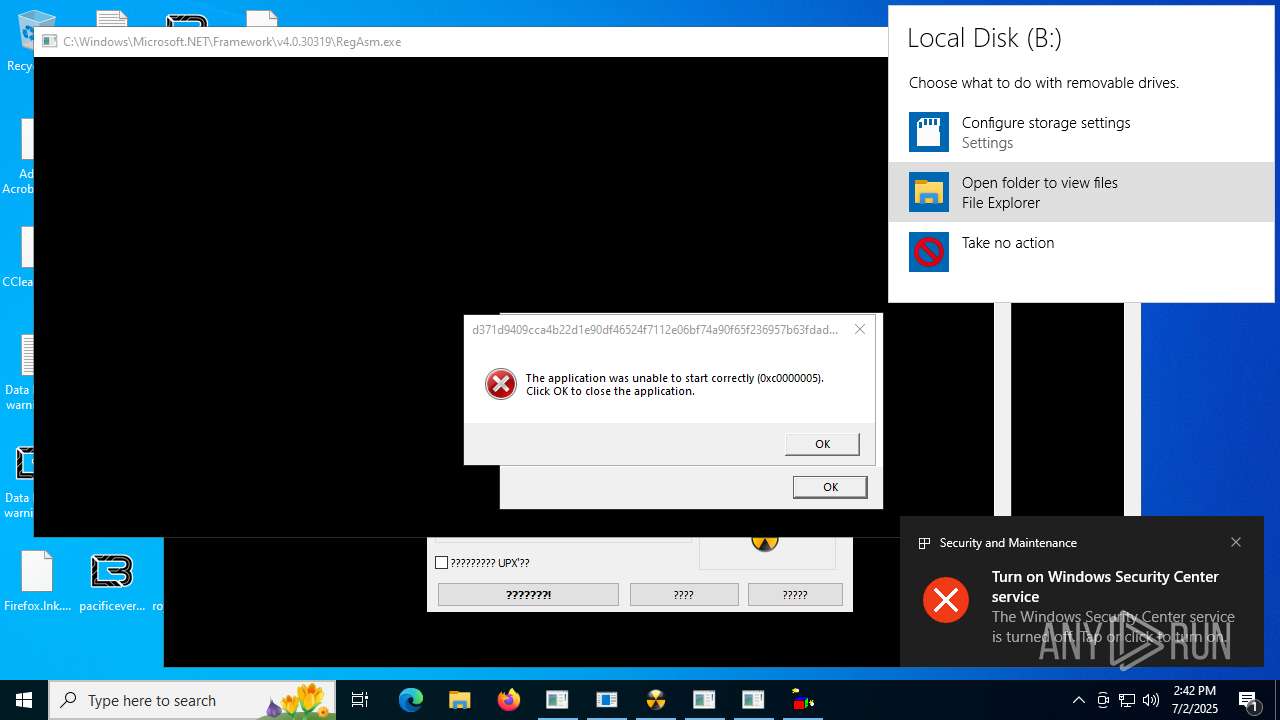
Executes application which crashes
- 0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe (PID: 1356)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8676)
- images.exe (PID: 3704)
- a10fe565f9891cb66e24299122c236e1e641451564a930b60ae91a24e09e6d62.exe (PID: 3620)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7996)
Multiple wallet extension IDs have been found
- TsarBomba.exe (PID: 6860)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
Found regular expressions for crypto-addresses (YARA)
- TsarBomba.exe (PID: 6860)
Application launched itself
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8836)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 9032)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7912)
- images.exe (PID: 10184)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 7960)
Starts application with an unusual extension
- TsarBomba.exe (PID: 6860)
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 7960)
- cmd.exe (PID: 10588)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
Connects to unusual port
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
- 145289accb8c684e583ca3d99532d64d0a6a40142062e648c65ffd8da070c4c9.exe (PID: 6284)
- 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe (PID: 1984)
- images.exe (PID: 7628)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- remoteadmin.exe (PID: 4080)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
Checks for external IP
- svchost.exe (PID: 2200)
- 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe (PID: 7656)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
Starts itself from another location
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8568)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 7352)
- MSBuild.exe (PID: 5456)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2200)
Query Microsoft Defender preferences
- RegAsm.exe (PID: 8648)
The process executes VB scripts
- MSBuild.exe (PID: 1828)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 4104)
Deletes system .NET executable
- wscript.exe (PID: 4104)
Executing commands from a ".bat" file
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 10588)
INFO
The sample compiled with english language support
- TsarBomba.exe (PID: 6860)
- InstallUtil.exe (PID: 8900)
- MSBuild.exe (PID: 1828)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
Checks supported languages
- TsarBomba.exe (PID: 6860)
- 0fd46aca09c54c256d22420d2ac3e947ff204a42a24158dfcb562de18a77f3f1.exe (PID: 1484)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- 1bad2b6e8ab16c5a692b2d05f68f7924a73a5818ddf3a9678ca8caab3568a78e.exe (PID: 4932)
- 7a8c864ed8b7ca908d3f317d7e63a30a85fb3e8c94070f23f2cf0bfa01c5e0b5.exe (PID: 4084)
- 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe (PID: 1984)
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 60e76eda46185d1d2e9463d15e31d4c87eb03535d368cc3471c55992bc99ad5f.exe (PID: 5116)
- 65fd5041c1a1c4115b0c59995221023486f02e5e5d8e313c3e48f3a42ef9a623.exe (PID: 5184)
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
- 182fb9756b66963f458ebbe0f20ff2715a758825ac6655fc56ec85579df61330.exe (PID: 6384)
- 188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe (PID: 1480)
- 80e3a04fa68be799b3c91737e1918f8394b250603a231a251524244e4d7f77d9.exe (PID: 7008)
- 0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe (PID: 1356)
- 539b377d4a33d1e884f18ecf0e0b0330e5dc26023b7ae051843cac8014142d98.exe (PID: 3672)
- 577b3a152ddc9d6558ad1b38ef6da89257229adf06d298ea025048a6d5d2fcea.exe (PID: 7260)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7912)
- MSBuild.exe (PID: 7352)
- 145289accb8c684e583ca3d99532d64d0a6a40142062e648c65ffd8da070c4c9.exe (PID: 6284)
- a0da672fdaf8943fc0453424197c5ae5539ed1cc86a47e955ea706a3e8365fe7.exe (PID: 3396)
- ab0acdb0c45ccafcc0ec594d30dc8153936574dde9ebe4e0b22504770361c666.exe (PID: 5724)
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 7688)
- b066d97c63093902c0debe32ed5a001cc150eae3fb841d87a58408762d32466e.exe (PID: 8196)
- javaw.exe (PID: 8248)
- aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe (PID: 1736)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 8428)
- c348c7e4d9028bdf84aba828bbb81ce46ae55c0246a94351edbfb9c63e41a8ee.exe (PID: 8456)
- b975f3981291f86d4a8f023b2cd5473abf6b8f4f33bb6f6cbb19bab0fa01d2ad.exe (PID: 8232)
- Chrome_boostrap.exe (PID: 8648)
- c558e126c64a89887115a45276d5a8751f90c399eb32ca103f6e50901abc7abd.exe (PID: 8568)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8836)
- InstallUtil.exe (PID: 8900)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 9032)
- RegAsm.exe (PID: 8648)
- svchost.com (PID: 6348)
- MSBuild.exe (PID: 5456)
- svchost.com (PID: 8468)
- ShellExperienceHost.exe (PID: 8920)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8568)
- svchost.com (PID: 9732)
- svchost.com (PID: 9672)
- svchost.com (PID: 9792)
- images.exe (PID: 10184)
- svchost.com (PID: 9848)
- svchost.com (PID: 9992)
- svchost.com (PID: 9976)
- svchost.com (PID: 10220)
- svchost.com (PID: 10088)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- images.exe (PID: 7628)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 7960)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- svchost.com (PID: 10000)
- MSBuild.exe (PID: 1828)
- svchost.com (PID: 9128)
- svchost.com (PID: 8232)
- remoteadmin.exe (PID: 4080)
- chcp.com (PID: 12128)
- svchost.com (PID: 12120)
Create files in a temporary directory
- TsarBomba.exe (PID: 6860)
- 188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe (PID: 1480)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- ab0acdb0c45ccafcc0ec594d30dc8153936574dde9ebe4e0b22504770361c666.exe (PID: 5724)
- javaw.exe (PID: 8248)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 9032)
- svchost.com (PID: 9792)
- svchost.com (PID: 10220)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- svchost.com (PID: 9672)
- svchost.com (PID: 10088)
- MSBuild.exe (PID: 1828)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
Reads the computer name
- TsarBomba.exe (PID: 6860)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- 7a8c864ed8b7ca908d3f317d7e63a30a85fb3e8c94070f23f2cf0bfa01c5e0b5.exe (PID: 4084)
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe (PID: 1984)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
- 65fd5041c1a1c4115b0c59995221023486f02e5e5d8e313c3e48f3a42ef9a623.exe (PID: 5184)
- 60e76eda46185d1d2e9463d15e31d4c87eb03535d368cc3471c55992bc99ad5f.exe (PID: 5116)
- 80e3a04fa68be799b3c91737e1918f8394b250603a231a251524244e4d7f77d9.exe (PID: 7008)
- 188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe (PID: 1480)
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
- 577b3a152ddc9d6558ad1b38ef6da89257229adf06d298ea025048a6d5d2fcea.exe (PID: 7260)
- 539b377d4a33d1e884f18ecf0e0b0330e5dc26023b7ae051843cac8014142d98.exe (PID: 3672)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7912)
- 145289accb8c684e583ca3d99532d64d0a6a40142062e648c65ffd8da070c4c9.exe (PID: 6284)
- MSBuild.exe (PID: 7352)
- aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe (PID: 1736)
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 7688)
- ab0acdb0c45ccafcc0ec594d30dc8153936574dde9ebe4e0b22504770361c666.exe (PID: 5724)
- 0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe (PID: 1356)
- Chrome_boostrap.exe (PID: 8648)
- javaw.exe (PID: 8248)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8836)
- c348c7e4d9028bdf84aba828bbb81ce46ae55c0246a94351edbfb9c63e41a8ee.exe (PID: 8456)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 8428)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 9032)
- ShellExperienceHost.exe (PID: 8920)
- RegAsm.exe (PID: 8648)
- svchost.com (PID: 6348)
- MSBuild.exe (PID: 5456)
- svchost.com (PID: 8468)
- images.exe (PID: 10184)
- svchost.com (PID: 9792)
- svchost.com (PID: 9672)
- svchost.com (PID: 9732)
- svchost.com (PID: 9992)
- svchost.com (PID: 9976)
- svchost.com (PID: 10088)
- svchost.com (PID: 10220)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- svchost.com (PID: 10000)
- svchost.com (PID: 9128)
- MSBuild.exe (PID: 1828)
- svchost.com (PID: 8232)
- remoteadmin.exe (PID: 4080)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- images.exe (PID: 7628)
- svchost.com (PID: 12120)
Process checks computer location settings
- TsarBomba.exe (PID: 6860)
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 7960)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- MSBuild.exe (PID: 1828)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
Reads the machine GUID from the registry
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- 80e3a04fa68be799b3c91737e1918f8394b250603a231a251524244e4d7f77d9.exe (PID: 7008)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 577b3a152ddc9d6558ad1b38ef6da89257229adf06d298ea025048a6d5d2fcea.exe (PID: 7260)
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 7960)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
- 4895f3e5549c1333698e23707fb39c0d24c33c31d1bc089b7970911fba3dc0f7.exe (PID: 7364)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7912)
- 145289accb8c684e583ca3d99532d64d0a6a40142062e648c65ffd8da070c4c9.exe (PID: 6284)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe (PID: 1736)
- MSBuild.exe (PID: 7352)
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 7688)
- c348c7e4d9028bdf84aba828bbb81ce46ae55c0246a94351edbfb9c63e41a8ee.exe (PID: 8456)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8836)
- javaw.exe (PID: 8248)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- RegAsm.exe (PID: 8648)
- svchost.com (PID: 9792)
- svchost.com (PID: 9672)
- svchost.com (PID: 10220)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- images.exe (PID: 10184)
- svchost.com (PID: 10088)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- remoteadmin.exe (PID: 4080)
Reads Environment values
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- 5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe (PID: 4708)
- 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe (PID: 7656)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
Checks proxy server information
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
- MSBuild.exe (PID: 7352)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- powershell.exe (PID: 9156)
- powershell.exe (PID: 7548)
- 0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe (PID: 1356)
- WerFault.exe (PID: 4324)
Disables trace logs
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 9156)
Reads mouse settings
- 188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe (PID: 1480)
- ab0acdb0c45ccafcc0ec594d30dc8153936574dde9ebe4e0b22504770361c666.exe (PID: 5724)
Reads Microsoft Office registry keys
- 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe (PID: 6748)
Creates files in the program directory
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
- MSBuild.exe (PID: 7352)
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
- javaw.exe (PID: 8248)
- c81ece0b60ed50db7d3769388f34ba051a05c95bd026e78dabb6ce08ff91bbba.exe (PID: 8428)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8568)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
Reads Internet Explorer settings
- mshta.exe (PID: 7116)
- mshta.exe (PID: 8276)
The sample compiled with russian language support
- TsarBomba.exe (PID: 6860)
Reads the software policy settings
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe (PID: 7656)
- 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe (PID: 7484)
- MSBuild.exe (PID: 7352)
- aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe (PID: 1736)
- MSBuild.exe (PID: 5456)
- 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe (PID: 7016)
- 4797cb80b22ba0da0ede6593bfc16399a5ffc289400155115c8de7786ea0db49.exe (PID: 10172)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- WerFault.exe (PID: 4324)
Launching a file from Task Scheduler
- cmd.exe (PID: 5724)
- cmd.exe (PID: 8268)
- cmd.exe (PID: 9320)
Creates files or folders in the user directory
- 3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe (PID: 5432)
- 77ebb550f38da3f28a65940a4c665ae3a679249ad906aa39387568a1f7ddd3fa.exe (PID: 5352)
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 7688)
- 771a06e3a1bdb42a7249d1c888e740c2bc46ba30b54490188c17f6c84ca96e26.exe (PID: 7536)
- MSBuild.exe (PID: 7352)
- javaw.exe (PID: 8248)
- WerFault.exe (PID: 8956)
- 01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe (PID: 3652)
- WerFault.exe (PID: 10200)
- cf75a4bb6793649841a5c9c4a7dcd93e3bea2924333d13bb855b8996b2cb8955.exe (PID: 8664)
- WerFault.exe (PID: 9140)
- WerFault.exe (PID: 10168)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- WerFault.exe (PID: 9756)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
- WerFault.exe (PID: 8840)
- WerFault.exe (PID: 12076)
- WerFault.exe (PID: 12176)
- WerFault.exe (PID: 2136)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7996)
- WMIC.exe (PID: 8296)
- WMIC.exe (PID: 1204)
- WMIC.exe (PID: 8896)
- WMIC.exe (PID: 12124)
- WMIC.exe (PID: 5288)
Application based on Java
- javaw.exe (PID: 8248)
Launching a file from the Startup directory
- aead1f538ae65044f17554b188d4d1f88d7c4840bb554f3d70a2fe3ab86f6abf.exe (PID: 7688)
Attempting to use instant messaging service
- 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe (PID: 1740)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 7352)
- MSBuild.exe (PID: 5456)
Compiled with Borland Delphi (YARA)
- TsarBomba.exe (PID: 6860)
- 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe (PID: 2696)
- conhost.exe (PID: 2680)
Launching a file from a Registry key
- svchost.exe (PID: 9084)
- d371d9409cca4b22d1e90df46524f7112e06bf74a90f65f236957b63fdad2c1b.exe (PID: 8568)
- MSBuild.exe (PID: 1828)
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
- 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe (PID: 6364)
Process checks whether UAC notifications are on
- def98259bba7c128a22dbb9100a3e9512911d9775ec82175f8a8a3c26b993dbf.exe (PID: 8968)
Reads CPU info
- 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe (PID: 3948)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7664)
- powershell.exe (PID: 9508)
- powershell.exe (PID: 8748)
- powershell.exe (PID: 9304)
- powershell.exe (PID: 10104)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 9768)
- powershell.exe (PID: 2128)
- powershell.exe (PID: 10084)
- powershell.exe (PID: 8888)
- powershell.exe (PID: 7392)
- powershell.exe (PID: 9908)
- powershell.exe (PID: 3556)
- powershell.exe (PID: 9816)
- powershell.exe (PID: 8344)
- powershell.exe (PID: 9280)
- powershell.exe (PID: 7732)
- powershell.exe (PID: 10020)
- powershell.exe (PID: 9436)
- powershell.exe (PID: 8996)
- powershell.exe (PID: 6348)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7664)
- powershell.exe (PID: 9508)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 10104)
- powershell.exe (PID: 6940)
- powershell.exe (PID: 9304)
- powershell.exe (PID: 2128)
- powershell.exe (PID: 9768)
- powershell.exe (PID: 3836)
- powershell.exe (PID: 9156)
Changes the display of characters in the console
- cmd.exe (PID: 10588)
Failed to connect to remote server (POWERSHELL)
- powershell.exe (PID: 7548)
- powershell.exe (PID: 9156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6860) TsarBomba.exe
Decrypted-URLs (4)http://medusakxxtp3uo7vusntvubnytaph4d3amxivbggl3hnhpk2nmus34yd.onion/227098164ef1fdb119ef537986bbdf24
http://medusaxko7jxtrojdkxo66j7ck4q5tgktf7uqsqyfry4ebnxlcbkccyd.onion/
https://utox.org/uTox_win64.exe)
https://www.torproject.org/download/):
RedLine
(PID) Process(2696) 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe
C2 (1)154.91.34.165:64951
Botnetcheat
Keys
Xor
Options
ErrorMessage
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 5632 |
| InitializedDataSize: | 26406400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2321 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.6.6.6 |
| ProductVersionNumber: | 6.6.6.6 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | HELL |
| FileTitle: | RAT Pack |
| FileDescription: | Tsar Bomba RAT PACK |
| FileVersion: | 6,6,6,6 |
| LegalCopyright: | 2025 |
| LegalTrademark: | HELL |
| ProductName: | Tsar Bomba |
| ProductVersion: | 6,6,6,6 |
Total processes
411
Monitored processes
264
Malicious processes
43
Suspicious processes
13
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{910B9DE3-4626-4A21-BE4D-C3C7AAE48CE1}'" delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | C:\WINDOWS\system32\net1 stop "Sophos Clean Service" /y | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1356 | "C:\Users\admin\AppData\Local\Temp\0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe" | C:\Users\admin\AppData\Local\Temp\0379d402a94f960380d7d91e3bfa106eeac01cd39ae7b0ba5010ba737088a215.exe | TsarBomba.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\AppData\Local\Temp\188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe" | C:\Users\admin\AppData\Local\Temp\188c3798b6d41bdfa3981bb61a40b81f4fe123c64b9bed2d4c40951de2064f19.exe | — | TsarBomba.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1484 | "C:\Users\admin\AppData\Local\Temp\0fd46aca09c54c256d22420d2ac3e947ff204a42a24158dfcb562de18a77f3f1.exe" | C:\Users\admin\AppData\Local\Temp\0fd46aca09c54c256d22420d2ac3e947ff204a42a24158dfcb562de18a77f3f1.exe | — | TsarBomba.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1736 | "C:\Users\admin\AppData\Local\Temp\aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe" | C:\Users\admin\AppData\Local\Temp\aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe | TsarBomba.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\AppData\Local\Temp\6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe" | C:\Users\admin\AppData\Local\Temp\6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | TsarBomba.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Discord rat Version: 1.0.0.0 Modules
| |||||||||||||||
| 1812 | cmd.exe /c C:\Windows\System32\wbem\WMIC.exe shadowcopy where "ID='{ED9ADACA-EA44-4B28-B8A6-2FC0FAA519D5}'" delete | C:\Windows\System32\cmd.exe | — | 80e3a04fa68be799b3c91737e1918f8394b250603a231a251524244e4d7f77d9.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
213 082
Read events
212 861
Write events
191
Delete events
30
Modification events
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (1740) 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
114
Suspicious files
800
Text files
1 468
Unknown types
133
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\0fd46aca09c54c256d22420d2ac3e947ff204a42a24158dfcb562de18a77f3f1.exe | executable | |
MD5:3167685FFBDAE55B00485896310FE2F4 | SHA256:1B67F07F970CE46FC189DBD787AE2200D42B86A331141F6FBF900F1F78A008DD | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\01ec7b1066df7c55e262dc375bff5fd13a1fc9706c3db4b3522ac8b9d2453b52.exe | executable | |
MD5:9C7B97EB3958D4309E6BA38BB1A99471 | SHA256:01EC7B1066DF7C55E262DC375BFF5FD13A1FC9706C3DB4B3522AC8B9D2453B52 | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe | executable | |
MD5:A85DED286361BD125CDFCEB0B6C93108 | SHA256:0F78A658B60F0879ACCCF0933D9AE8A5D2C188E9F16B8E6F7B01BD0CC9B5C4E1 | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe | executable | |
MD5:8B157AD42FA665D263904052F56A009B | SHA256:4D5ECF3D1955458195771630F03F6EF42F5F62E66ED8E0681F8311D25AECC2BB | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | executable | |
MD5:692726995AD5CF7D9DABAF873FEF7106 | SHA256:6CA05DA8350D9F5E5D3A7547C0D4693EBC1190E3B76F58F4196021D0C080C722 | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\3e3c7d3f5f93d7bf260aca7612b4dbc5d0e90992841f7e6826d7fb7fa3abe044.exe | executable | |
MD5:5887E7ED9DCEC96AC39CBDA2B19D8CC0 | SHA256:3E3C7D3F5F93D7BF260ACA7612B4DBC5D0E90992841F7E6826D7FB7FA3ABE044 | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\1bad2b6e8ab16c5a692b2d05f68f7924a73a5818ddf3a9678ca8caab3568a78e.exe | executable | |
MD5:BD29231BC4F2C6D2F22FA026E2EACA40 | SHA256:1BAD2B6E8AB16C5A692B2D05F68F7924A73A5818DDF3A9678CA8CAAB3568A78E | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\5f7dbb2374af6314df4cd22c830ffaced38bc2ea8ec16775e502d7422ca74f35.exe | executable | |
MD5:0C14B5BB56A334CF17EF9B247EA1134E | SHA256:5F7DBB2374AF6314DF4CD22C830FFACED38BC2EA8EC16775E502D7422CA74F35 | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\7a8c864ed8b7ca908d3f317d7e63a30a85fb3e8c94070f23f2cf0bfa01c5e0b5.exe | executable | |
MD5:0C03D5237E53FACD034B810687726E41 | SHA256:7A8C864ED8B7CA908D3F317D7E63A30A85FB3E8C94070F23F2CF0BFA01C5E0B5 | |||
| 6860 | TsarBomba.exe | C:\Users\admin\AppData\Local\Temp\9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe | executable | |
MD5:EAF71E0105C5C4380D1B50A31AB8CD55 | SHA256:9C65D850589E6AB34C6C8E65B8A3B4AA26FA913CA850472023A3B708F95C226B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
190
DNS requests
61
Threats
77
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6364 | 06922dd72ff4f3e3cffcfe8a6f2070672c341588f3a8ea1f847a0cdf601854d5.exe | GET | 200 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
7656 | 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3948 | 59ab63c99285e35679153e299e411aa32a94d25482566428a6fd7d908f04d4ad.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
2552 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7016 | 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe | GET | 200 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
7016 | 53055b6d2651d5c6b4a0bf9ee2f50c73918e65c9d36acfd10eb2eefb0d3e957f.exe | GET | 200 | 193.122.6.168:80 | http://checkip.dyndns.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1740 | 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | 162.159.133.234:443 | gateway.discord.gg | CLOUDFLARENET | — | whitelisted |
6748 | 4d5ecf3d1955458195771630f03f6ef42f5f62e66ed8e0681f8311d25aecc2bb.exe | 98.177.107.142:60446 | — | ASN-CXA-ALL-CCI-22773-RDC | US | unknown |
2696 | 0f78a658b60f0879acccf0933d9ae8a5d2c188e9f16b8e6f7b01bd0cc9b5c4e1.exe | 154.91.34.165:64951 | — | Shanghai Anchang Network Security Technology Co.,Ltd. | US | unknown |
— | — | 192.168.100.4:49718 | — | — | — | unknown |
7656 | 876ba1145745c2e088c0df36f8241a20916a092211d05646eae5c7004dd4d429.exe | 216.58.206.35:443 | gstatic.com | GOOGLE | US | whitelisted |
7484 | 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe | 103.171.35.26:9443 | — | VH Global Limited | HK | malicious |
1984 | 9c65d850589e6ab34c6c8e65b8a3b4aa26fa913ca850472023a3b708f95c226b.exe | 154.23.184.57:4433 | — | Hong Kong Communications International Co., Limited | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
gateway.discord.gg |
| whitelisted |
gstatic.com |
| whitelisted |
t.me |
| whitelisted |
17.aa.4t.com |
| unknown |
steamcommunity.com |
| whitelisted |
api.pcloud.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ip-api.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (gateway .discord .gg) |
1740 | 6ca05da8350d9f5e5d3a7547c0d4693ebc1190e3b76f58f4196021d0c080c722.exe | Misc activity | ET INFO Observed Discord Service Domain (gateway .discord .gg) in TLS SNI |
7484 | 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe | Targeted Malicious Activity was Detected | ET HUNTING Suspicious Empty SSL Certificate - Observed in Cobalt Strike |
7484 | 755b9e89416a664f52a0dfee6de54687f15ae900a7317763b0a4144996724f6a.exe | A Network Trojan was detected | ET MALWARE Meterpreter or Other Reverse Shell SSL Cert |
7352 | MSBuild.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO Cloud Storage API Related Domain in DNS Lookup (api .pcloud .com) |
2200 | svchost.exe | Misc activity | ET INFO Commonly Abused File Sharing Site Domain Observed in DNS Lookup (pcloud .com) |
7352 | MSBuild.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
1736 | aa76b4db29cf929b4b22457ccb8cd77308191f091cde2f69e578ade9708d7949.exe | Misc activity | ET INFO Observed Commonly Abused File Sharing Site Domain (pcloud .com) in TLS SNI |
2200 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |