| URL: | togotribune.com |
| Full analysis: | https://app.any.run/tasks/c06b7237-18ac-45e6-b7f3-402f324cc191 |
| Verdict: | Malicious activity |
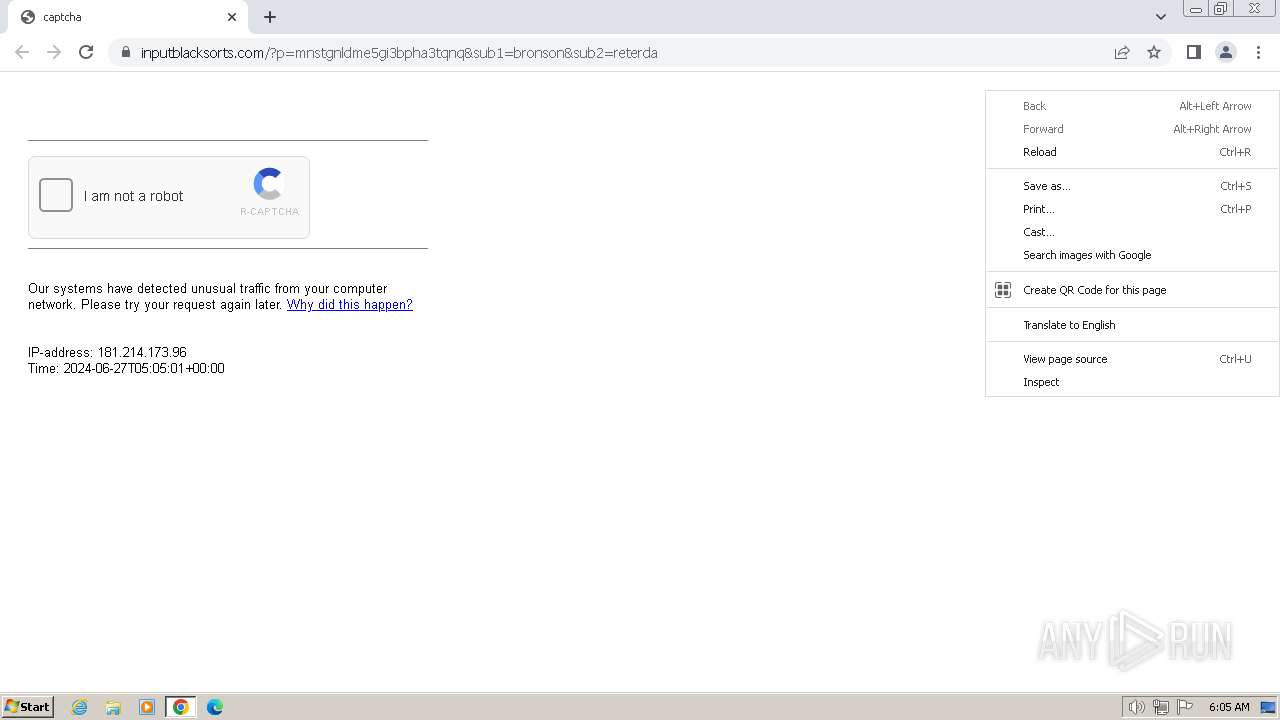
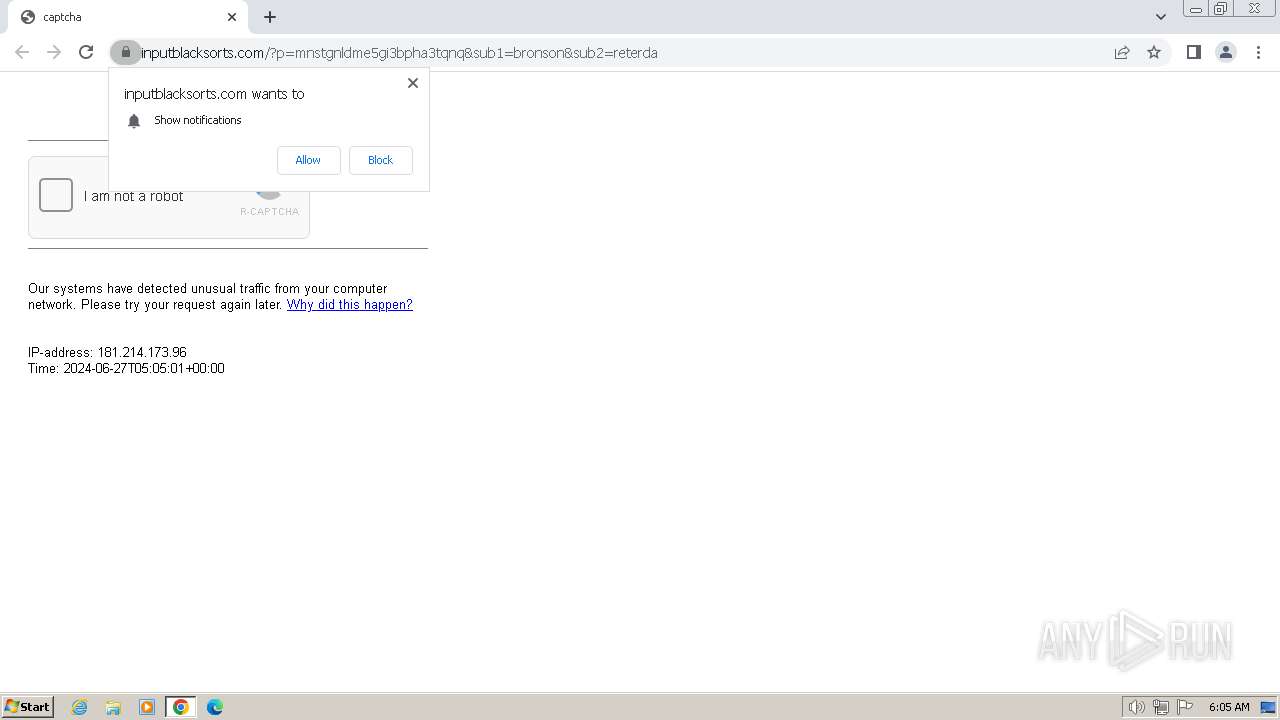
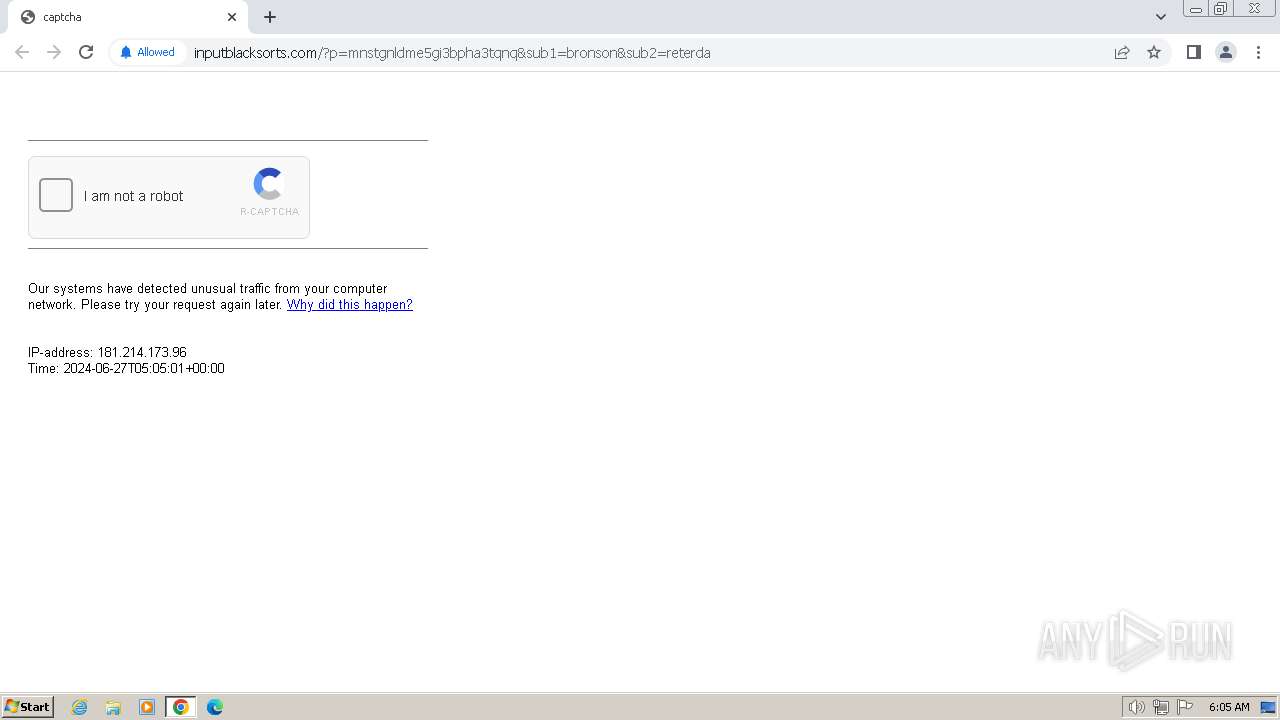
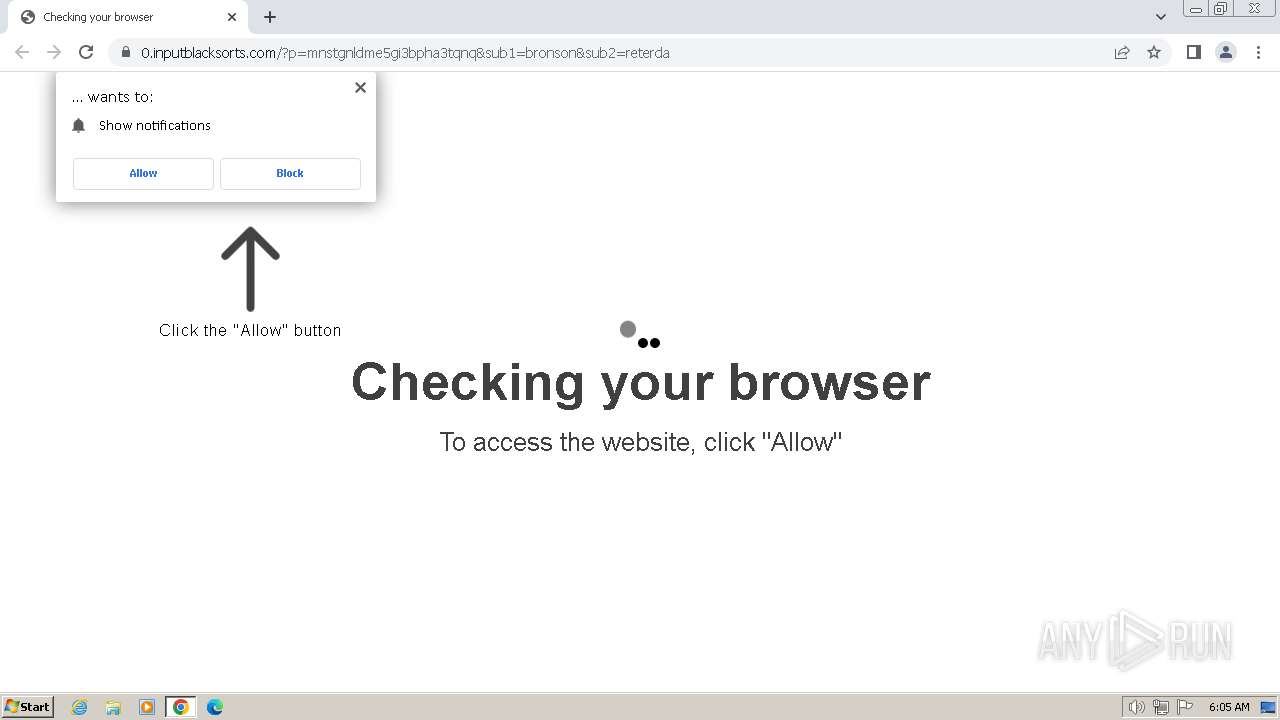
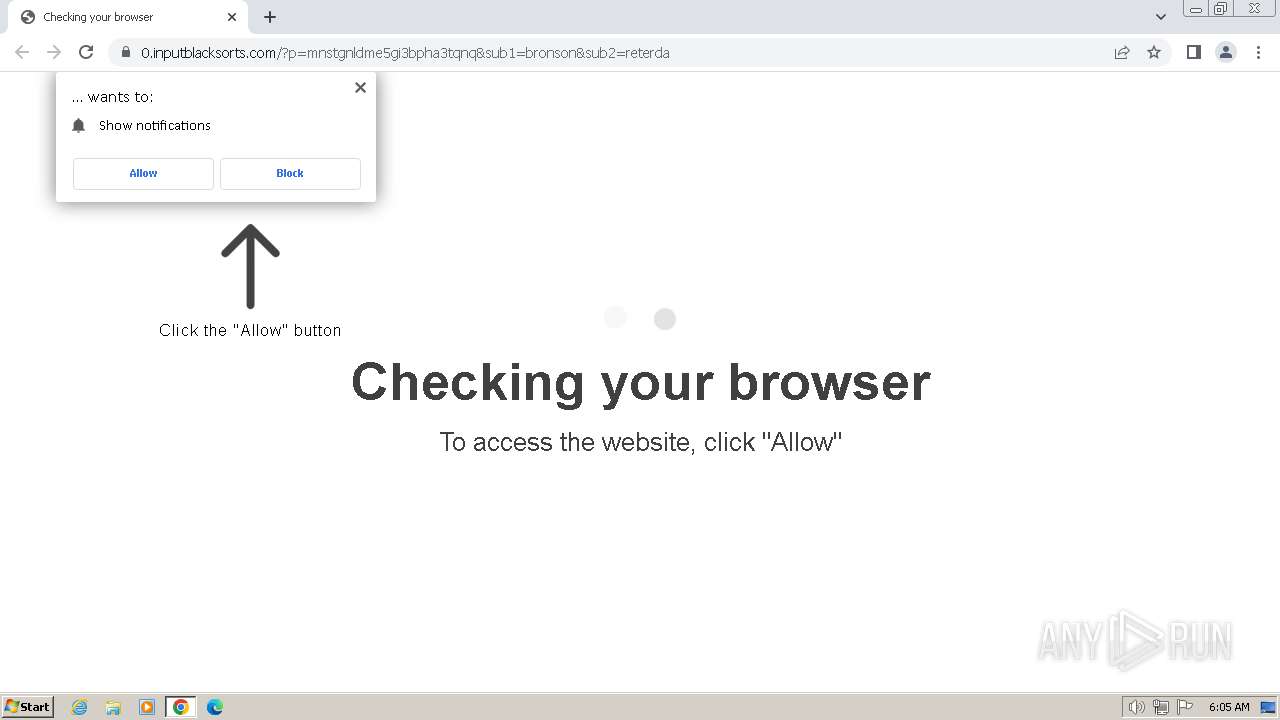
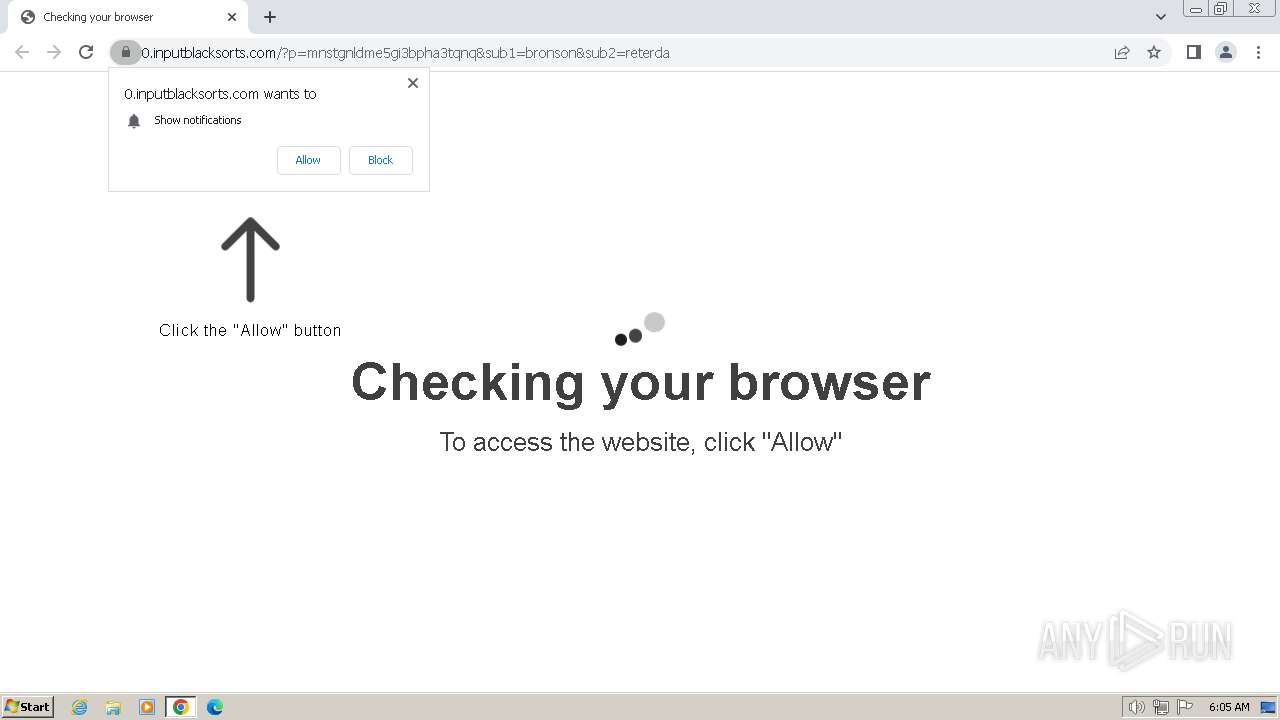
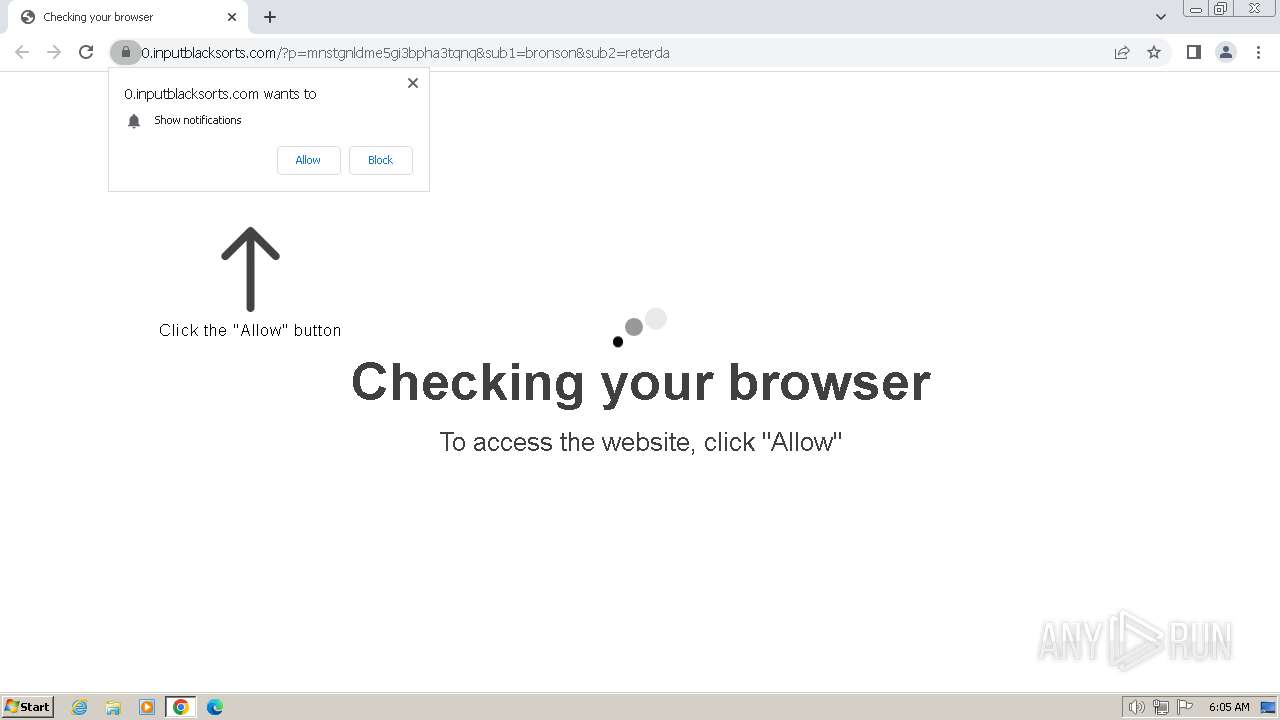
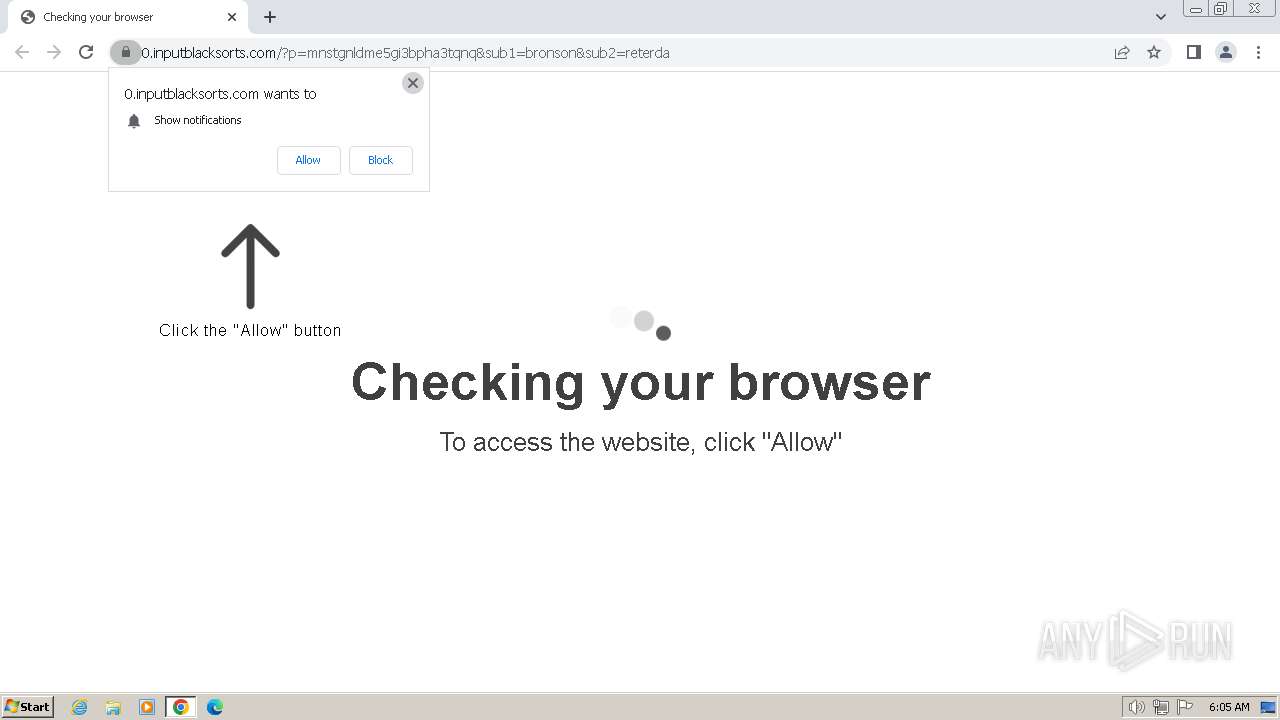
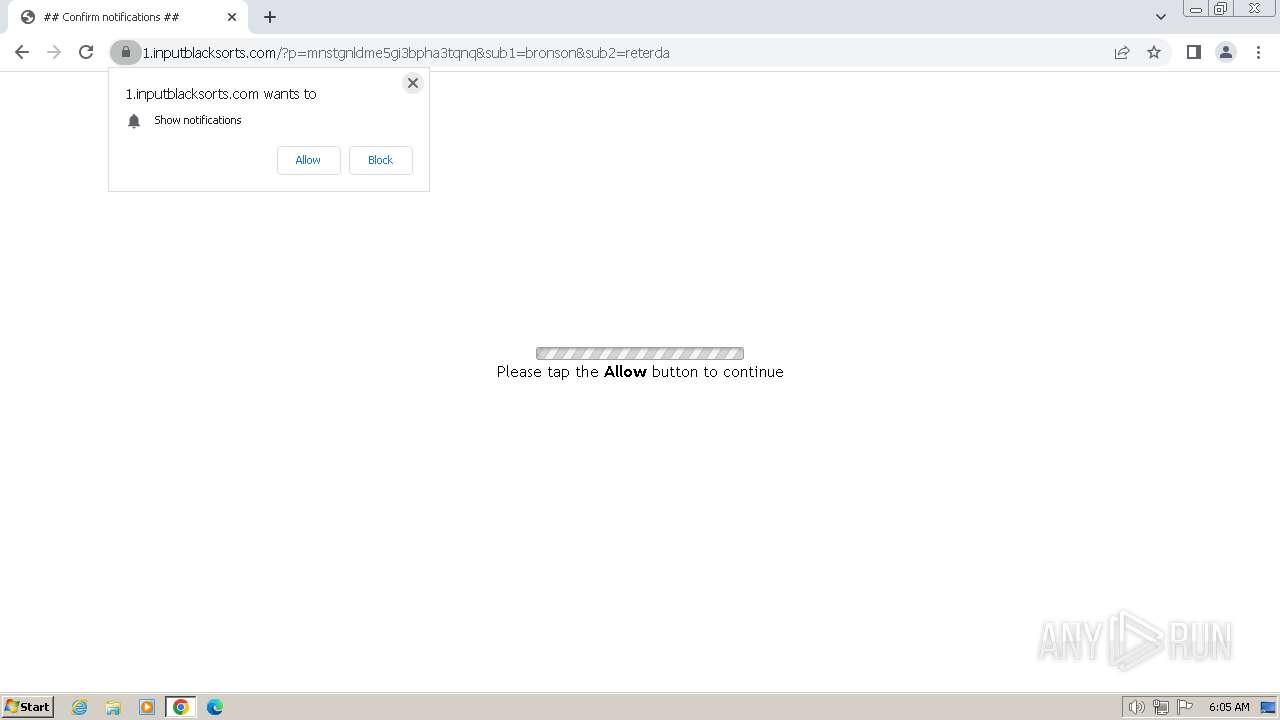
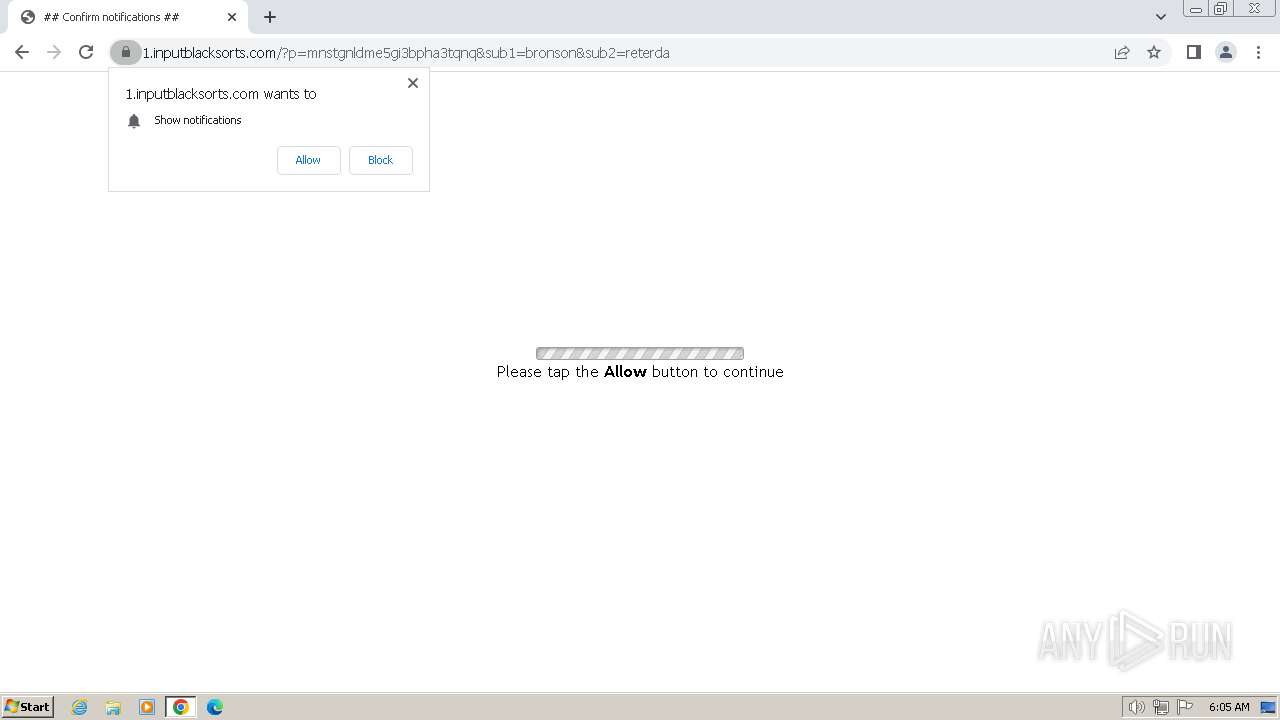
| Threats: | Balada Injector is a long-running malware campaign that targets WordPress websites by exploiting vulnerabilities in plugins and themes. The attackers inject malicious code into compromised sites, leading to unauthorized redirects, data theft, and the creation of [backdoors](https://any.run/malware-trends/backdoor) for persistent access. The campaign operates in waves, with spikes in activity observed every few weeks, continually adapting to exploit newly discovered vulnerabilities. |
| Analysis date: | June 27, 2024, 05:04:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 139A4416E8354C50FB2CCAE1CB94041E |
| SHA1: | AF269A0678EBC5EAF361FE72B61CE7CB2BD335AD |
| SHA256: | 36B590C553A8FA84007DA5DBC1EE1B347C5E164B595A3792BF711007EB0D3A56 |
| SSDEEP: | 3:jKRXGeALdIn:wULK |
MALICIOUS
BALADA has been detected (SURICATA)
- chrome.exe (PID: 2936)
SUSPICIOUS
Contacting a server suspected of hosting an Exploit Kit
- chrome.exe (PID: 2936)
INFO
Connects to unusual port
- chrome.exe (PID: 2936)
Application launched itself
- chrome.exe (PID: 3368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
14
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=3388 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3424 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2028 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2996 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2752 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1092 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=3248 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1356 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1524 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1332 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3324 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=2064 --field-trial-handle=1168,i,13048394123454966409,17280537768277843965,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
3 249
Read events
3 214
Write events
35
Delete events
0
Modification events
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3368) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
0
Suspicious files
60
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF4fd67.TMP | — | |
MD5:— | SHA256:— | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF4fdf4.TMP | text | |
MD5:ECD3386BCC950E73B86EB128A5F57622 | SHA256:C9A068EAFBC587EDFC89392F64DDD350EEB96C5CF195CDB030BAB8F6DD33833B | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\e86dcb90-0ae5-40bd-839e-c8361a48fa30.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:FA25AF7098FC1571F24F200A9D105D58 | SHA256:4F40C87070B7A151FB241CCF36E7027AA703C15CA0ACB0A1759DA07B2C318574 | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF51228.TMP | — | |
MD5:— | SHA256:— | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 3368 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:825B582C78EC88D54C215EFDF1EAD639 | SHA256:367995D01A8F13E5C30C79499F86B034775BFD009D83DC97635DE438D47DFA37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
59
DNS requests
100
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
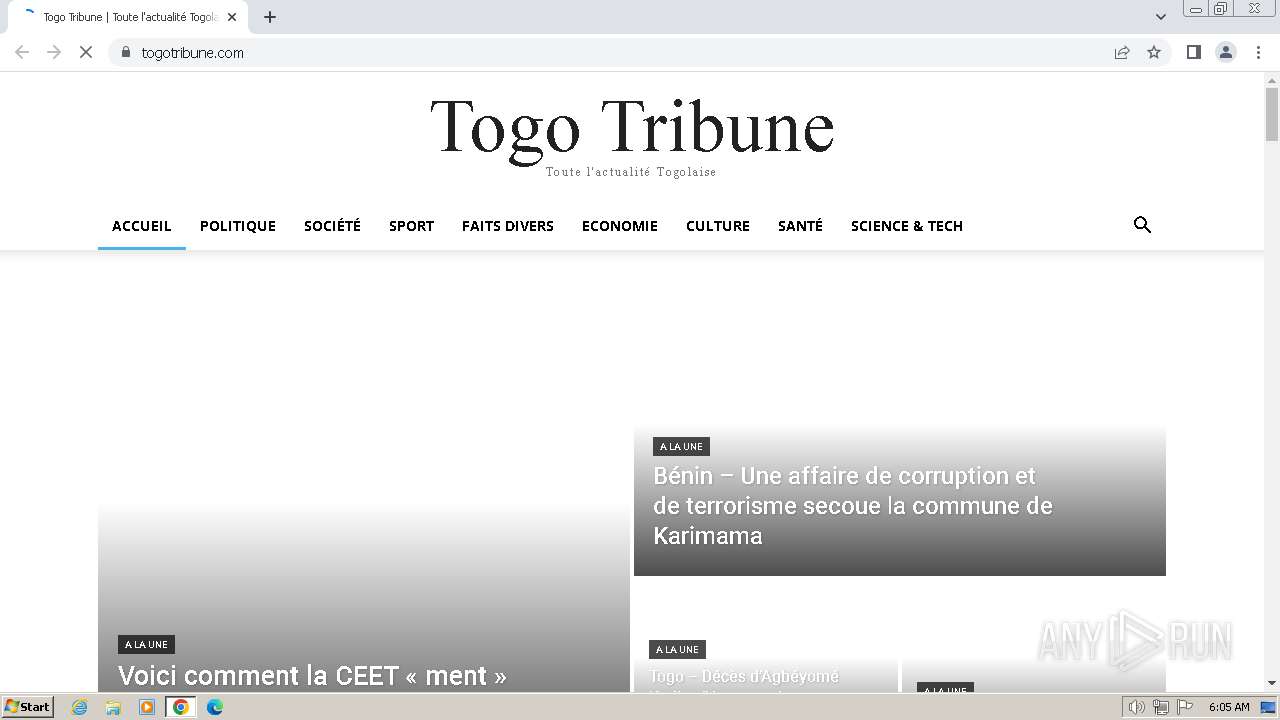
2936 | chrome.exe | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | unknown |
2936 | chrome.exe | 172.67.161.8:443 | togotribune.com | CLOUDFLARENET | US | unknown |
3368 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2936 | chrome.exe | 142.250.186.100:443 | www.google.com | GOOGLE | US | whitelisted |
2936 | chrome.exe | 192.0.77.37:443 | c0.wp.com | AUTOMATTIC | US | unknown |
2936 | chrome.exe | 172.217.18.10:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
togotribune.com |
| unknown |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
c0.wp.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
synd.edgecdnc.com |
| malicious |
secure.gravatar.com |
| whitelisted |
v0.wordpress.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
a.nel.cloudflare.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2936 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in DNS Lookup (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in DNS Lookup (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in DNS Lookup (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in DNS Lookup (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in TLS SNI (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in TLS SNI (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in DNS Lookup (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in DNS Lookup (rdntocdns .com) |
2936 | chrome.exe | Exploit Kit Activity Detected | ET EXPLOIT_KIT Balada Domain in TLS SNI (rdntocdns .com) |