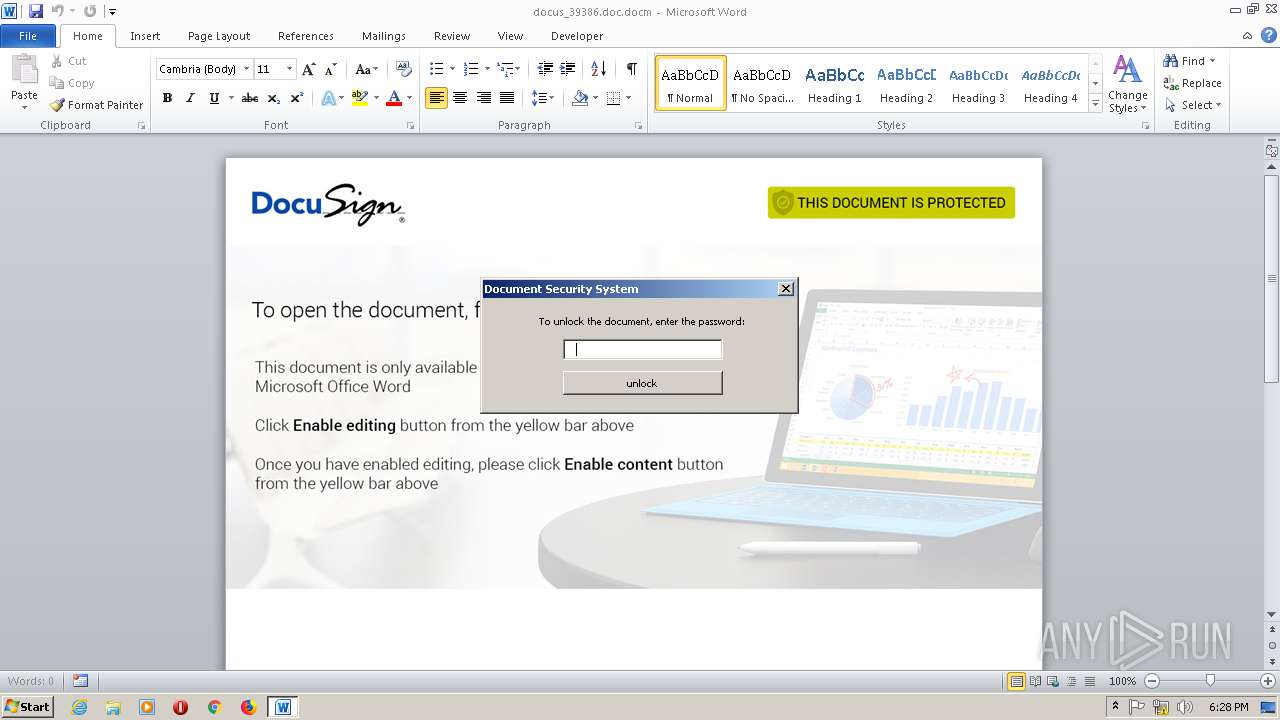
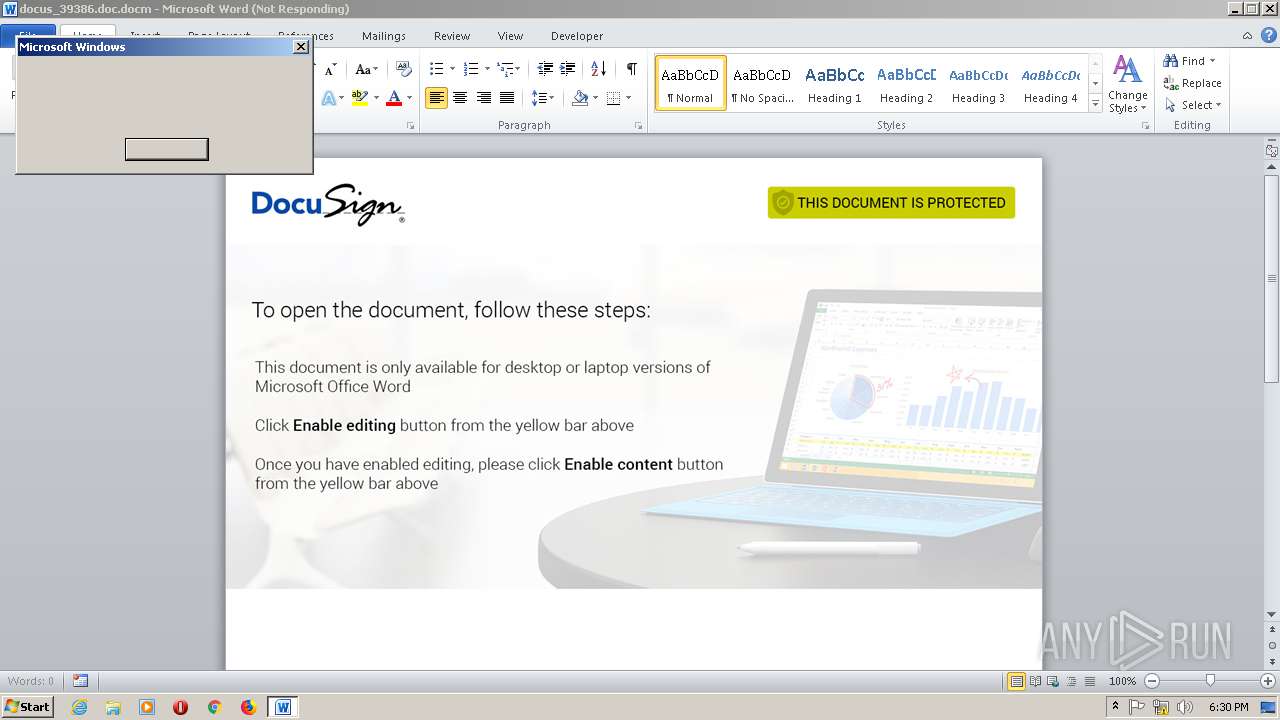
| File name: | docus_39386.doc |
| Full analysis: | https://app.any.run/tasks/1846edad-f6eb-4a29-b83a-8393dbf65075 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | October 09, 2019, 18:27:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
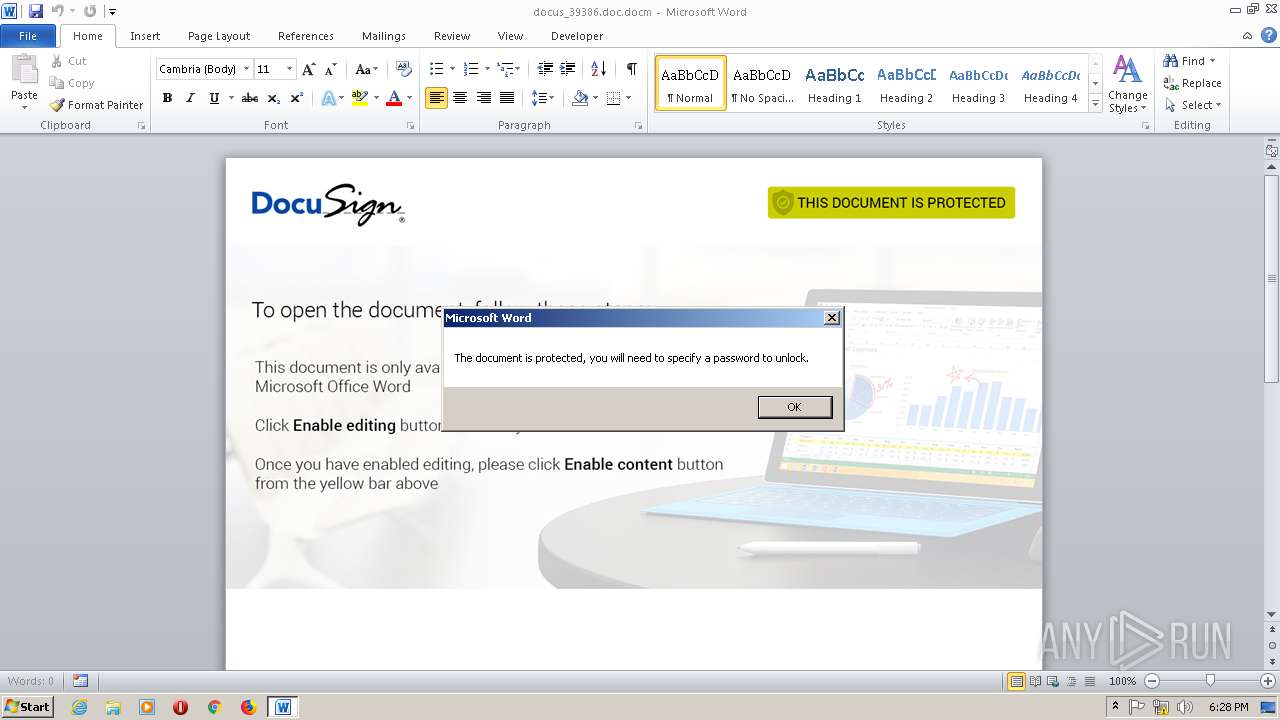
| File info: | Microsoft Word 2007+ |
| MD5: | 34D0636684F0577CB9C2C3F701C0E8F8 |
| SHA1: | B584590C206CD4F67C5CA054C1B3EC02E6699867 |
| SHA256: | 36448DE9A48210F85E5FD61329BBCE4D86173BA705FCA75D0DFECDF2002D1684 |
| SSDEEP: | 3072:5vvvvvvvvvvvvvvvvvvvvvv/ZRynrChbtCY8QOjnX3Npkv4wTh6ivbiFuzRmDPrE:5vvvvvvvvvvvvvvvvvvvvvv/KnrChbs8 |
MALICIOUS
Writes file to Word startup folder
- WINWORD.EXE (PID: 2428)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2428)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 1172)
Uses SVCHOST.EXE for hidden code execution
- svchost.exe (PID: 2072)
- regsvr32.exe (PID: 1172)
Application was dropped or rewritten from another process
- BNF883.tmp (PID: 1980)
- BNFA78.tmp (PID: 280)
COBALTSTRIKE was detected
- BNF883.tmp (PID: 1980)
HANCITOR was detected
- svchost.exe (PID: 2072)
Detected Pony/Fareit Trojan
- svchost.exe (PID: 2072)
Actions looks like stealing of personal data
- svchost.exe (PID: 2072)
- svchost.exe (PID: 2564)
Connects to CnC server
- svchost.exe (PID: 2072)
- IEXPLORE.EXE (PID: 1616)
- svchost.exe (PID: 2564)
- IEXPLORE.EXE (PID: 2256)
URSNIF was detected
- IEXPLORE.EXE (PID: 1616)
- IEXPLORE.EXE (PID: 2256)
PONY was detected
- svchost.exe (PID: 2564)
SUSPICIOUS
Executed via COM
- iexplore.exe (PID: 1260)
Executed via WMI
- regsvr32.exe (PID: 2224)
Executable content was dropped or overwritten
- svchost.exe (PID: 2072)
Checks for external IP
- svchost.exe (PID: 2072)
Starts CMD.EXE for commands execution
- svchost.exe (PID: 2072)
Application launched itself
- svchost.exe (PID: 2072)
Starts application with an unusual extension
- svchost.exe (PID: 2072)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2428)
Reads Internet Cache Settings
- iexplore.exe (PID: 1260)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2428)
- iexplore.exe (PID: 1260)
Creates files in the user directory
- WINWORD.EXE (PID: 2428)
- iexplore.exe (PID: 1260)
Changes internet zones settings
- iexplore.exe (PID: 1260)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 1952)
- IEXPLORE.EXE (PID: 1616)
- IEXPLORE.EXE (PID: 2256)
Reads the hosts file
- BNFA78.tmp (PID: 280)
Reads settings of System Certificates
- iexplore.exe (PID: 1260)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x0eab7932 |
| ZipCompressedSize: | 440 |
| ZipUncompressedSize: | 1769 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | python-docx |
| Description: | generated by python-docx |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | onx |
| RevisionNumber: | 2 |
| CreateDate: | 2019:10:09 14:41:00Z |
| ModifyDate: | 2019:10:09 14:41:00Z |
| Category: | - |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | - |
| Manager: | - |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinkBase: | - |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
52
Monitored processes
14
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | C:\Users\admin\AppData\Local\Temp\BNFA78.tmp | C:\Users\admin\AppData\Local\Temp\BNFA78.tmp | svchost.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1172 | -s C:\Users\admin\AppData\Roaming\Microsoft\Word\Startup\55F.wll | C:\Windows\SysWOW64\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1616 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:1260 CREDAT:1709325 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1704 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:1260 CREDAT:2692362 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1952 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:1260 CREDAT:267521 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1956 | cmd /K | C:\Windows\SysWOW64\cmd.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1980 | C:\Users\admin\AppData\Local\Temp\BNF883.tmp | C:\Users\admin\AppData\Local\Temp\BNF883.tmp | svchost.exe | ||||||||||||
User: admin Company: THQ Canada Inc. Integrity Level: MEDIUM Exit code: 0 Version: 1, 4, 0, 0 Modules
| |||||||||||||||
| 2072 | C:\Windows\System32\svchost.exe | C:\Windows\SysWOW64\svchost.exe | regsvr32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2224 | regsvr32.exe -s C:\Users\admin\AppData\Roaming\Microsoft\Word\Startup\55F.wll | C:\Windows\system32\regsvr32.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 4 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 064
Read events
3 455
Write events
591
Delete events
18
Modification events
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 0%8 |
Value: 302538007C090000010000000000000000000000 | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330184234 | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184318 | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1330184319 | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 7C090000E6FADF50CF7ED50100000000 | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | :(8 |
Value: 3A2838007C09000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | :(8 |
Value: 3A2838007C09000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2428) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
46
Text files
63
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2428 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8130.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2428 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso8670.tmp | — | |
MD5:— | SHA256:— | |||
| 1260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BDW1XBVN\favicon[2].ico | — | |
MD5:— | SHA256:— | |||
| 1260 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2428 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF9723338A48D58E12.TMP | — | |
MD5:— | SHA256:— | |||
| 2428 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF91F09CE257B2ACD2.TMP | — | |
MD5:— | SHA256:— | |||
| 2428 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFE5D56EFC56402A75.TMP | — | |
MD5:— | SHA256:— | |||
| 1260 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4E324E3FAFB9DDBC.TMP | — | |
MD5:— | SHA256:— | |||
| 1952 | IEXPLORE.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\UJFUX3OG\download[1].htm | html | |
MD5:— | SHA256:— | |||
| 1260 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\85IIS8OXDYZ0CZFOBVJN.temp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
104
DNS requests
58
Threats
105
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1980 | BNF883.tmp | GET | 200 | 31.44.184.123:80 | http://31.44.184.123/pixel.gif | RU | — | — | malicious |
1980 | BNF883.tmp | GET | 200 | 31.44.184.123:80 | http://31.44.184.123/pixel.gif | RU | — | — | malicious |
1980 | BNF883.tmp | GET | 200 | 31.44.184.123:80 | http://31.44.184.123/pixel.gif | RU | — | — | malicious |
1980 | BNF883.tmp | GET | — | 31.44.184.123:80 | http://31.44.184.123/CjnA | RU | — | — | malicious |
1980 | BNF883.tmp | GET | 200 | 31.44.184.123:80 | http://31.44.184.123/pixel.gif | RU | — | — | malicious |
2072 | svchost.exe | POST | 200 | 95.169.181.133:80 | http://avantusthea.com/4/forum.php | DE | text | 12 b | malicious |
1952 | IEXPLORE.EXE | GET | 200 | 47.74.181.177:80 | http://elitefireandsafety.com/download.html | US | html | 45.0 Kb | whitelisted |
2072 | svchost.exe | GET | 200 | 173.201.96.128:80 | http://kylemarketing.com/wp-includes/widgets/1 | US | binary | 45.2 Kb | malicious |
2072 | svchost.exe | POST | — | 95.169.181.133:80 | http://avantusthea.com/mlu/forum.php | DE | — | — | malicious |
2072 | svchost.exe | POST | 200 | 95.169.181.133:80 | http://avantusthea.com/4/forum.php | DE | text | 992 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1952 | IEXPLORE.EXE | 47.74.181.177:80 | elitefireandsafety.com | Alibaba (China) Technology Co., Ltd. | US | malicious |
1260 | iexplore.exe | 47.74.181.177:80 | elitefireandsafety.com | Alibaba (China) Technology Co., Ltd. | US | malicious |
1260 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2072 | svchost.exe | 23.23.229.94:80 | api.ipify.org | Amazon.com, Inc. | US | malicious |
2072 | svchost.exe | 95.169.181.133:80 | avantusthea.com | Keyweb AG | DE | malicious |
2072 | svchost.exe | 173.201.96.128:80 | kylemarketing.com | GoDaddy.com, LLC | US | malicious |
2564 | svchost.exe | 95.169.181.133:80 | avantusthea.com | Keyweb AG | DE | malicious |
2072 | svchost.exe | 192.254.233.200:80 | domainnamesexpert.info | Unified Layer | US | malicious |
1980 | BNF883.tmp | 31.44.184.123:80 | — | Petersburg Internet Network ltd. | RU | malicious |
280 | BNFA78.tmp | 8.8.8.8:53 | — | Google Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
elitefireandsafety.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
api.ipify.org |
| shared |
avantusthea.com |
| malicious |
kylemarketing.com |
| malicious |
domainnamesexpert.info |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
has.votaritar.at |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1952 | IEXPLORE.EXE | A Network Trojan was detected | MALWARE [PTsecurity] Hex Encoded PE EXE or DLL Windows file download |
2072 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup api.ipify.org |
2072 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Hancitor POST Data send |
2072 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Fareit/Pony/Hancitor Payload (Zeus) |
2072 | svchost.exe | A Network Trojan was detected | ET TROJAN Fareit/Pony Downloader Checkin 2 |
2072 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Fareit/Pony/Hancitor Payload (Zeus) |
2072 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Fareit/Pony/Hancitor Payload (Zeus) |
1980 | BNF883.tmp | A Network Trojan was detected | MALWARE [PTsecurity] Backdoor.Cobalt |
1980 | BNF883.tmp | A Network Trojan was detected | MALWARE [PTsecurity] Cobalt Strike Beacon Observed |
2072 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] Fareit/Pony/Hancitor Payload (Zeus) |
73 ETPRO signatures available at the full report
Process | Message |
|---|---|
BNF883.tmp | yfpT4m |