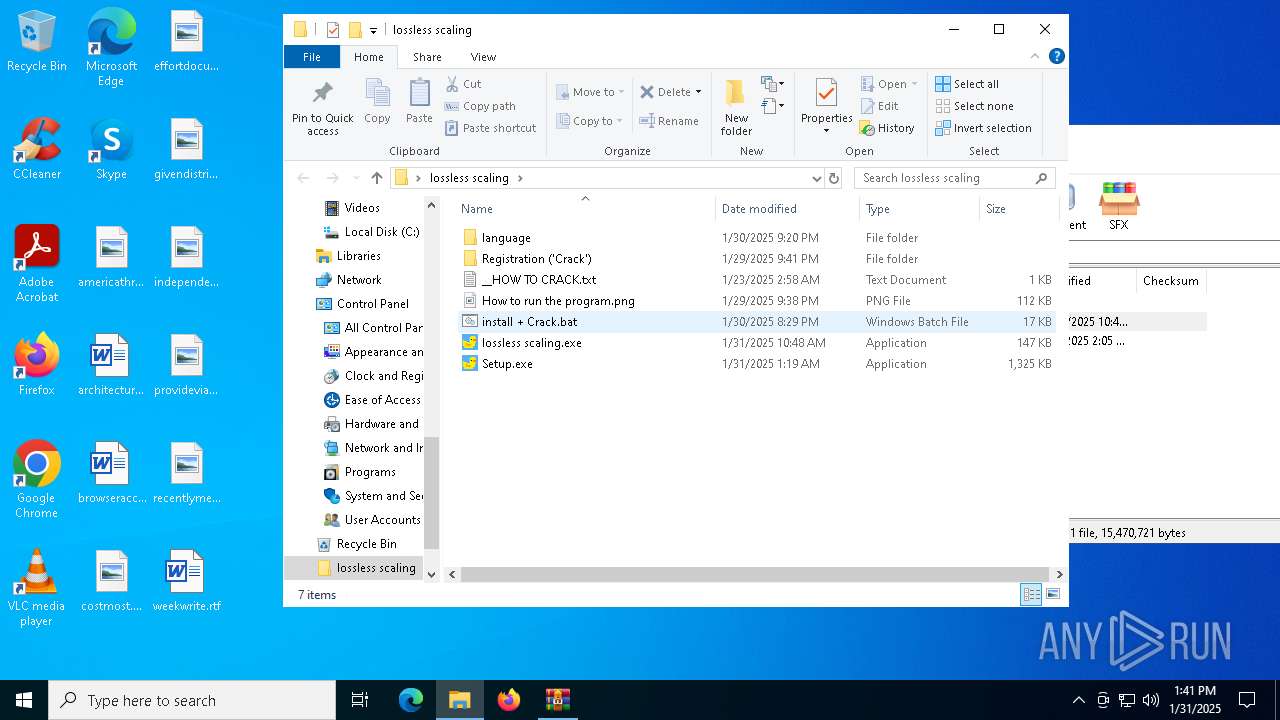
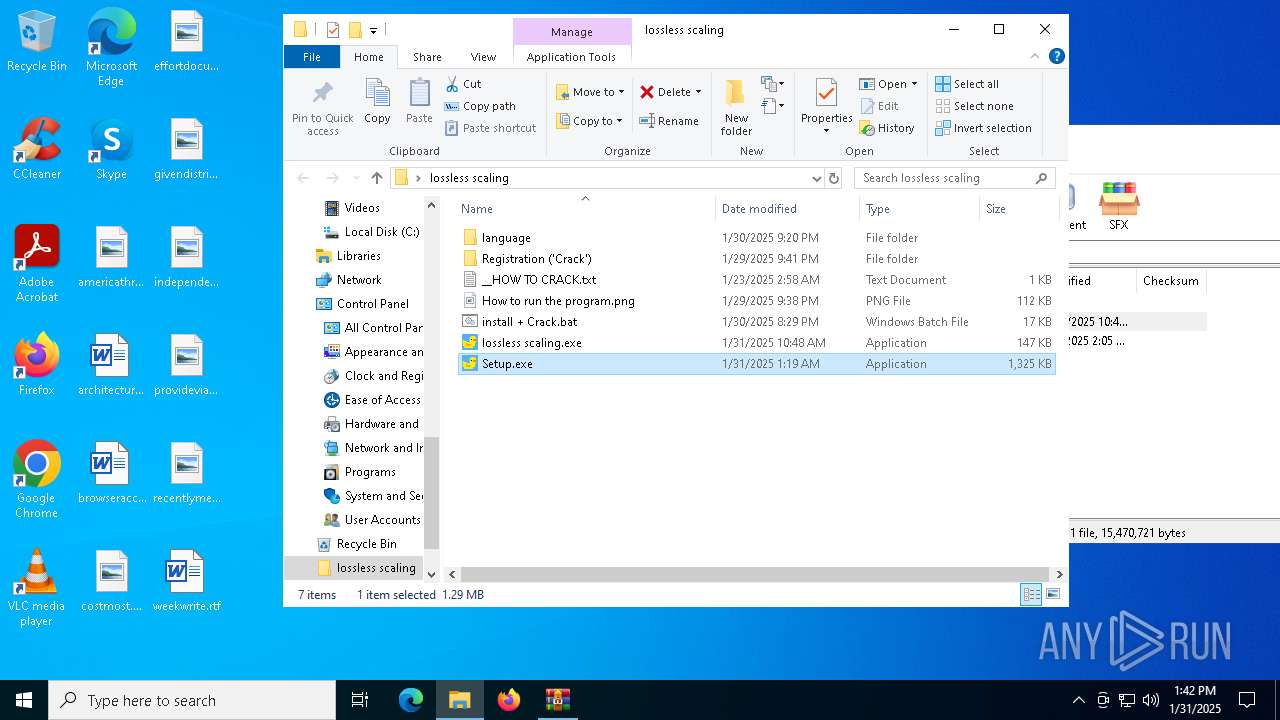
| File name: | lossless scaling.zip |
| Full analysis: | https://app.any.run/tasks/a4a46617-34d9-467d-b97a-3c5347a3cf0b |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | January 31, 2025, 13:41:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 11BF2E6ABB5FA3717ED2CC967F5FEA42 |
| SHA1: | 160186A702ECE19956AF6FBADDB5C7F16FC46039 |
| SHA256: | 3600628371F327A224A65A521AACE3A86AAADBC7B8A993840B097C593D090D66 |
| SSDEEP: | 98304:i6QSRXFI4umk5aJ/x+uggqN6y2mgniNZFW81ecxSDQHQT0HOwKkUp5pgpU95BZXK:2XkU+RMNlqTOuTo |
MALICIOUS
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 4596)
- cmd.exe (PID: 244)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 7100)
- wscript.exe (PID: 7056)
- wscript.exe (PID: 6316)
Run PowerShell with an invisible window
- powershell.exe (PID: 5392)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 4444)
Bypass execution policy to execute commands
- powershell.exe (PID: 5392)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 4504)
- powershell.exe (PID: 3692)
- powershell.exe (PID: 4444)
- powershell.exe (PID: 2624)
- powershell.exe (PID: 6952)
Uses Task Scheduler to run other applications
- powershell.exe (PID: 5392)
Actions looks like stealing of personal data
- aspnet_compiler.exe (PID: 1808)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 4504)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 2624)
- powershell.exe (PID: 6952)
ASYNCRAT has been detected (SURICATA)
- aspnet_compiler.exe (PID: 1808)
ASYNCRAT has been detected (YARA)
- aspnet_compiler.exe (PID: 1808)
PURECRYPTER has been detected (SURICATA)
- MSBuild.exe (PID: 5872)
SUSPICIOUS
Executing commands from a ".bat" file
- powershell.exe (PID: 5604)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 4328)
- net.exe (PID: 1904)
- cmd.exe (PID: 4596)
- net.exe (PID: 4556)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 5604)
- Setup.exe (PID: 6892)
- aspnet_compiler.exe (PID: 1808)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4328)
- cmd.exe (PID: 4596)
- cmd.exe (PID: 244)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 7100)
- cmd.exe (PID: 5320)
- wscript.exe (PID: 7056)
- wscript.exe (PID: 6316)
Likely accesses (executes) a file from the Public directory
- xcopy.exe (PID: 6288)
- powershell.exe (PID: 5392)
- schtasks.exe (PID: 1684)
- RAR.exe (PID: 5592)
- RAR.exe (PID: 4932)
- wscript.exe (PID: 7020)
- powershell.exe (PID: 4536)
- wscript.exe (PID: 7100)
- powershell.exe (PID: 4504)
- wscript.exe (PID: 7056)
- powershell.exe (PID: 2624)
- wscript.exe (PID: 6316)
- powershell.exe (PID: 6952)
Starts process via Powershell
- powershell.exe (PID: 5604)
- powershell.exe (PID: 3692)
Executable content was dropped or overwritten
- xcopy.exe (PID: 6288)
- powershell.exe (PID: 1200)
- aspnet_compiler.exe (PID: 1808)
- hjfnql.exe (PID: 3744)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4596)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4596)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 7100)
- wscript.exe (PID: 7056)
- wscript.exe (PID: 6316)
Reads the date of Windows installation
- Setup.exe (PID: 6912)
Reads security settings of Internet Explorer
- Setup.exe (PID: 6912)
- aspnet_compiler.exe (PID: 1808)
Application launched itself
- Setup.exe (PID: 6912)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 4596)
- cmd.exe (PID: 244)
Reads binary file using Get-Content
- powershell.exe (PID: 5392)
The process hide an interactive prompt from the user
- cmd.exe (PID: 244)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 5392)
Executes script without checking the security policy
- powershell.exe (PID: 1200)
Lists all scheduled tasks
- schtasks.exe (PID: 1792)
- schtasks.exe (PID: 5548)
- schtasks.exe (PID: 6800)
- schtasks.exe (PID: 7108)
The process verifies whether the antivirus software is installed
- powershell.exe (PID: 5392)
- powershell.exe (PID: 1200)
Executes application which crashes
- LosslessScaling.exe (PID: 3060)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 7100)
- wscript.exe (PID: 7056)
- wscript.exe (PID: 6316)
The process executes VB scripts
- powershell.exe (PID: 5392)
- powershell.exe (PID: 1200)
- aspnet_compiler.exe (PID: 1808)
The process executes Powershell scripts
- wscript.exe (PID: 7020)
- wscript.exe (PID: 7100)
- wscript.exe (PID: 7056)
- wscript.exe (PID: 6316)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7100)
- wscript.exe (PID: 7020)
- wscript.exe (PID: 6316)
- wscript.exe (PID: 7056)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 4504)
- powershell.exe (PID: 2624)
- powershell.exe (PID: 6952)
Contacting a server suspected of hosting an CnC
- aspnet_compiler.exe (PID: 1808)
- MSBuild.exe (PID: 5872)
Connects to unusual port
- aspnet_compiler.exe (PID: 1808)
- MSBuild.exe (PID: 5872)
The process executes via Task Scheduler
- powershell.exe (PID: 4444)
- Certificate.exe (PID: 7032)
- wscript.exe (PID: 7056)
- wscript.exe (PID: 6316)
There is functionality for taking screenshot (YARA)
- LosslessScaling.exe (PID: 4244)
Found regular expressions for crypto-addresses (YARA)
- aspnet_compiler.exe (PID: 1808)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6612)
The sample compiled with english language support
- WinRAR.exe (PID: 6612)
- xcopy.exe (PID: 6288)
- powershell.exe (PID: 1200)
Manual execution by a user
- cmd.exe (PID: 4328)
- Setup.exe (PID: 6912)
Checks supported languages
- Setup.exe (PID: 6912)
- Setup.exe (PID: 6892)
- LosslessScaling.exe (PID: 4244)
- LosslessScaling.exe (PID: 3060)
- RAR.exe (PID: 5592)
- RAR.exe (PID: 4932)
- mode.com (PID: 6816)
- aspnet_compiler.exe (PID: 6416)
- hjfnql.exe (PID: 3744)
- aspnet_compiler.exe (PID: 1808)
- Certificate.exe (PID: 7032)
- MSBuild.exe (PID: 5872)
- aspnet_compiler.exe (PID: 5888)
Reads the computer name
- Setup.exe (PID: 6912)
- LosslessScaling.exe (PID: 4244)
- Setup.exe (PID: 6892)
- LosslessScaling.exe (PID: 3060)
- aspnet_compiler.exe (PID: 6416)
- aspnet_compiler.exe (PID: 1808)
- hjfnql.exe (PID: 3744)
- Certificate.exe (PID: 7032)
- MSBuild.exe (PID: 5872)
- aspnet_compiler.exe (PID: 2324)
Process checks computer location settings
- Setup.exe (PID: 6912)
- aspnet_compiler.exe (PID: 1808)
Creates files in the program directory
- powershell.exe (PID: 1200)
Checks current location (POWERSHELL)
- powershell.exe (PID: 1200)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5392)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 4504)
- powershell.exe (PID: 4444)
- powershell.exe (PID: 2624)
- powershell.exe (PID: 6952)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5392)
- powershell.exe (PID: 1200)
- powershell.exe (PID: 4536)
- powershell.exe (PID: 4504)
- powershell.exe (PID: 4444)
- powershell.exe (PID: 2624)
- powershell.exe (PID: 6952)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 5392)
- powershell.exe (PID: 1200)
Creates files or folders in the user directory
- LosslessScaling.exe (PID: 4244)
- WerFault.exe (PID: 6700)
- hjfnql.exe (PID: 3744)
Reads the machine GUID from the registry
- LosslessScaling.exe (PID: 3060)
- LosslessScaling.exe (PID: 4244)
- RAR.exe (PID: 4932)
- aspnet_compiler.exe (PID: 6416)
- aspnet_compiler.exe (PID: 1808)
- hjfnql.exe (PID: 3744)
- Certificate.exe (PID: 7032)
- MSBuild.exe (PID: 5872)
- aspnet_compiler.exe (PID: 2324)
- aspnet_compiler.exe (PID: 5888)
Detects Fody packer (YARA)
- powershell.exe (PID: 5392)
- LosslessScaling.exe (PID: 4244)
Checks proxy server information
- WerFault.exe (PID: 6700)
Starts MODE.COM to configure console settings
- mode.com (PID: 6816)
The executable file from the user directory is run by the Powershell process
- hjfnql.exe (PID: 3744)
Reads the software policy settings
- aspnet_compiler.exe (PID: 1808)
Create files in a temporary directory
- aspnet_compiler.exe (PID: 1808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(1808) aspnet_compiler.exe
C2 (1)eg4x4.casacam.net
Ports (1)304
VersionA 14
Options
AutoRunfalse
MutexMaterxMutex_Egypt2
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignatureHFvuaaLQpoqpAubV8+PWzUt8djQZXJcvXPr4Kbq/U4RRbitA8ULztUj+UP+a51KrxbuLM3xiWkBqoF/W++thUctmw3e4y213f6brMcFhd8wzYKizkxlG+BiX9OJlZe2CqAoS7gFg8G9nhG51jJk4RTs7UYsWAGBh1RCNxDJwGGNByT9mP/7r00AzHMfq3fhHYjEpC+vuY6ADpYrQcsbqxYLauGOuKr0fGlmaUd0x2dzWuitD2h3TLCXxXKIp30EavfHJy/rLbD45JsHeDWHBwB+27l/0SAyLb8DMCuf90zs9...
Keys
AES8a741d0df21cf3b4fbc5bf4f34a9d6730c390a895088e0f7791e766f32693358
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:01:31 02:48:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | lossless scaling/ |
Total processes
194
Monitored processes
64
Malicious processes
13
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | Cmd.exe /c POWeRSHeLL.eXe -NOP -WIND HIDDeN -eXeC BYPASS -NONI < language\Win.Lan | C:\Windows\System32\cmd.exe | — | Setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | POWeRSHeLL.eXe -NOP -WIND HIDDeN -eXeC BYPASS -NONI | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1572 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | "C:\WINDOWS\system32\schtasks.exe" /create /tn administrator /sc minute /mo 2 /tr C:\Users\Public\IObitUnlocker\Loader.vbs /rl HIGHEST | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1792 | "C:\WINDOWS\system32\schtasks.exe" /query /tn administrator | C:\Windows\System32\schtasks.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1808 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_compiler.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: aspnet_compiler.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
AsyncRat(PID) Process(1808) aspnet_compiler.exe C2 (1)eg4x4.casacam.net Ports (1)304 VersionA 14 Options AutoRunfalse MutexMaterxMutex_Egypt2 InstallFolder%AppData% Certificates Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva... Server_SignatureHFvuaaLQpoqpAubV8+PWzUt8djQZXJcvXPr4Kbq/U4RRbitA8ULztUj+UP+a51KrxbuLM3xiWkBqoF/W++thUctmw3e4y213f6brMcFhd8wzYKizkxlG+BiX9OJlZe2CqAoS7gFg8G9nhG51jJk4RTs7UYsWAGBh1RCNxDJwGGNByT9mP/7r00AzHMfq3fhHYjEpC+vuY6ADpYrQcsbqxYLauGOuKr0fGlmaUd0x2dzWuitD2h3TLCXxXKIp30EavfHJy/rLbD45JsHeDWHBwB+27l/0SAyLb8DMCuf90zs9... Keys AES8a741d0df21cf3b4fbc5bf4f34a9d6730c390a895088e0f7791e766f32693358 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 1904 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
68 096
Read events
68 050
Write events
43
Delete events
3
Modification events
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\lossless scaling.zip | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4624) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Valve\Steam\Apps\993090 |
| Operation: | write | Name: | Installed |
Value: 1 | |||
Executable files
87
Suspicious files
18
Text files
58
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\How to run the program.png | binary | |
MD5:5C932F935AE20FE79D779A8F03D58A09 | SHA256:7CF3B5FE89C1DB2732AF19730AB1A1E91C9FBA9A1117E268578D4DC604152807 | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\en-US\Lan.vbs | text | |
MD5:49AF07D132592C9A62EAAEF421E3E589 | SHA256:487985D63734CD4828EAF03284E0D1D2FA684AFC2D46DA489C99D498F31A83AB | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\diagerr.xml | csv | |
MD5:44317C4008BFB84314D098A68944A0D6 | SHA256:DD43C2C0A8F53036AA4B346DE52DA6C0254C4747D129FE4130ECE4E078BB0A10 | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\uk-UA\cs\LosslessScaling.resources.dll | executable | |
MD5:0009B54449D6EE8D723BE5266CB96C32 | SHA256:6F4CD5D91EDEE8DBC547A6F914F1441C5A55D559B784893A98B9AB3A1C96EE62 | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\en-US\UK.dll | text | |
MD5:B573EB820A0233ACBA7B6E33D1D8ED28 | SHA256:919C8006BCF5C03AC8B4D83DFC824E4F918A6D3D2FCABD6BD905494EC79513AE | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\en-US\EN.dll | compressed | |
MD5:83663DB5670D46990660D5BC77D8234D | SHA256:5A56446709D211D66336E49FB0E56D4D2A66521F77E3A60B8CEC5E8FC57BF04B | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\install + Crack.bat | binary | |
MD5:741BBEAE98E31E4AF6D4E07C63DFDF81 | SHA256:66FBD40FF1411E3B4FEA4107E90C690AAD47BFCA38D70705BF2231552906A8E7 | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\en-US\RAR.exe | executable | |
MD5:D3E9F98155C0FAAB869CCC74FB5E8A1E | SHA256:3E0FDB5C40336482DACEF3496116053D7772A51720900141B3C6F35C6E9B351B | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\en-US\diagerr.xml | csv | |
MD5:7A5A52B35E4171BE17B53923B483E166 | SHA256:C496A24679E835C842D28C3BCE4408D99EF2207F4F83E7A5B2F06108C9A9ADBA | |||
| 6612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6612.21244\lossless scaling\language\en-US\RU.dll | text | |
MD5:83BF9BA8BECAC139CB05C1AB68468E62 | SHA256:7BFD69BDD83904D39A4E09C55FE6E380F027A2F13593C167ACF92160BB9CF125 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
34
DNS requests
21
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
436 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
436 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6400 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6700 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6700 | WerFault.exe | GET | 200 | 23.48.23.145:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
900 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
436 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
436 | SIHClient.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.casacam .net Domain |
1808 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
1808 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
1808 | aspnet_compiler.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
1808 | aspnet_compiler.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
2192 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.ddnsgeek .com Domain |
5872 | MSBuild.exe | Malware Command and Control Activity Detected | LOADER [ANY.RUN] PureLoader Reset Connection (RST) |