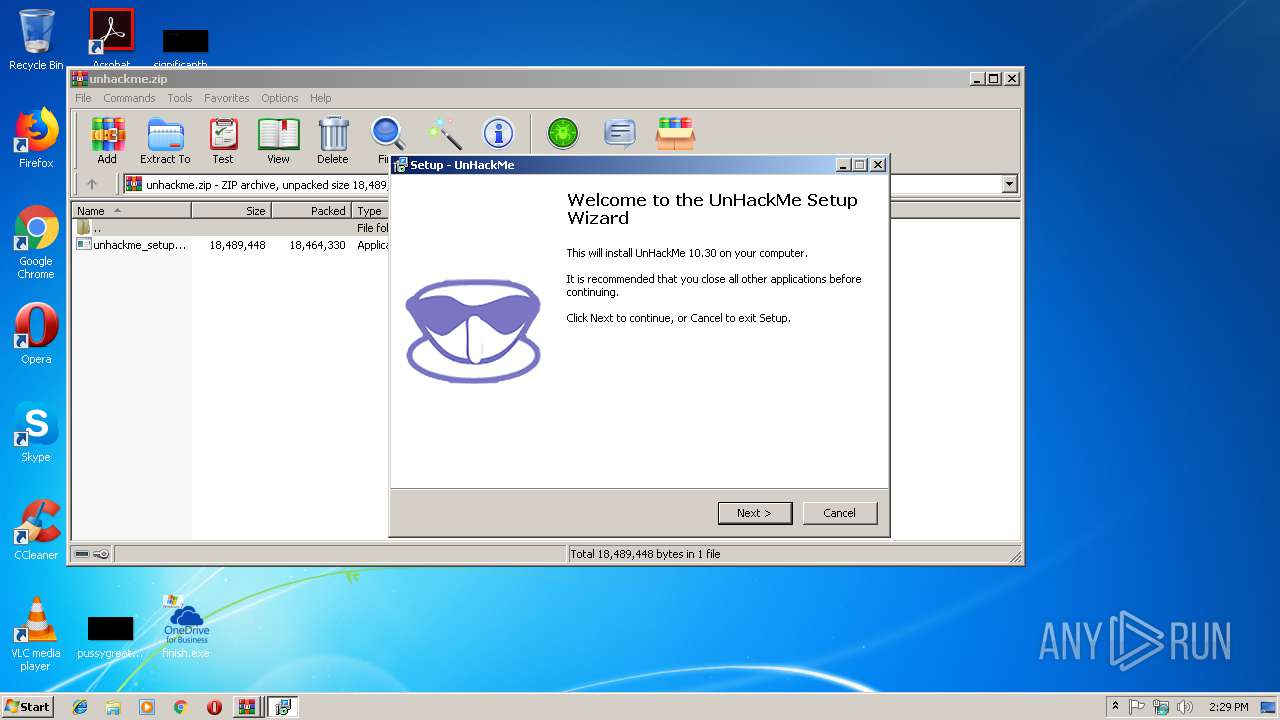
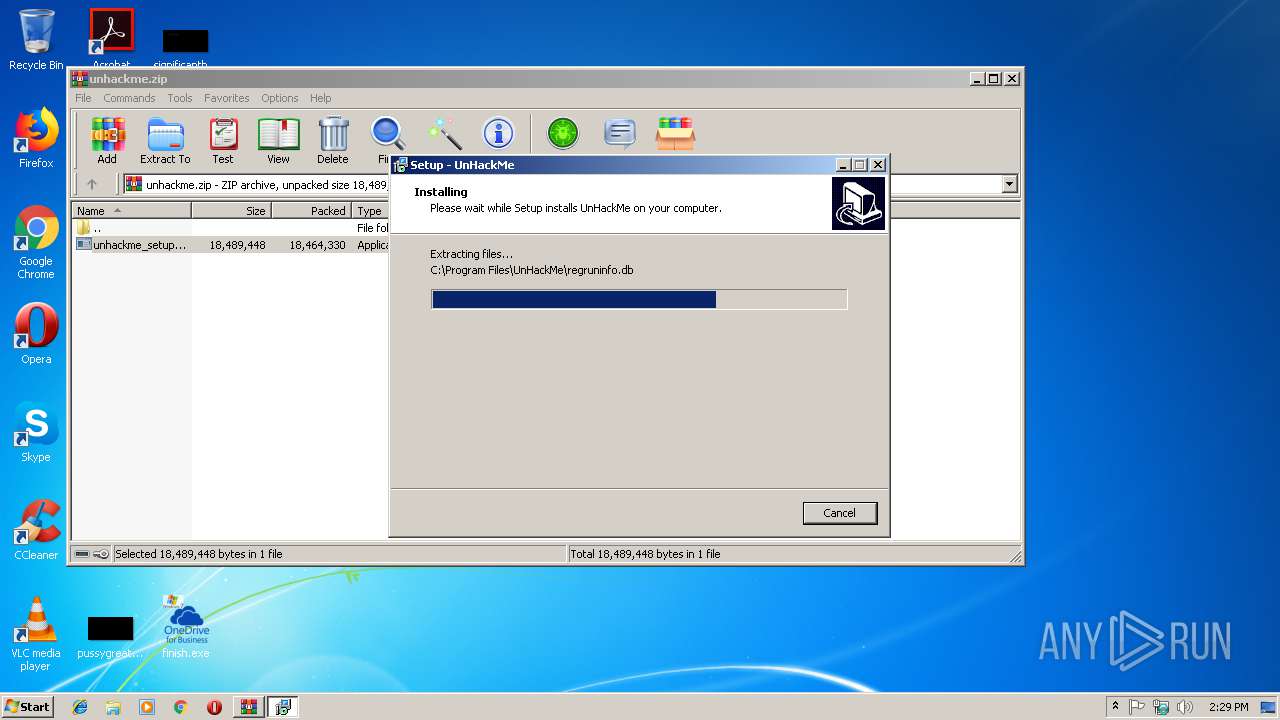
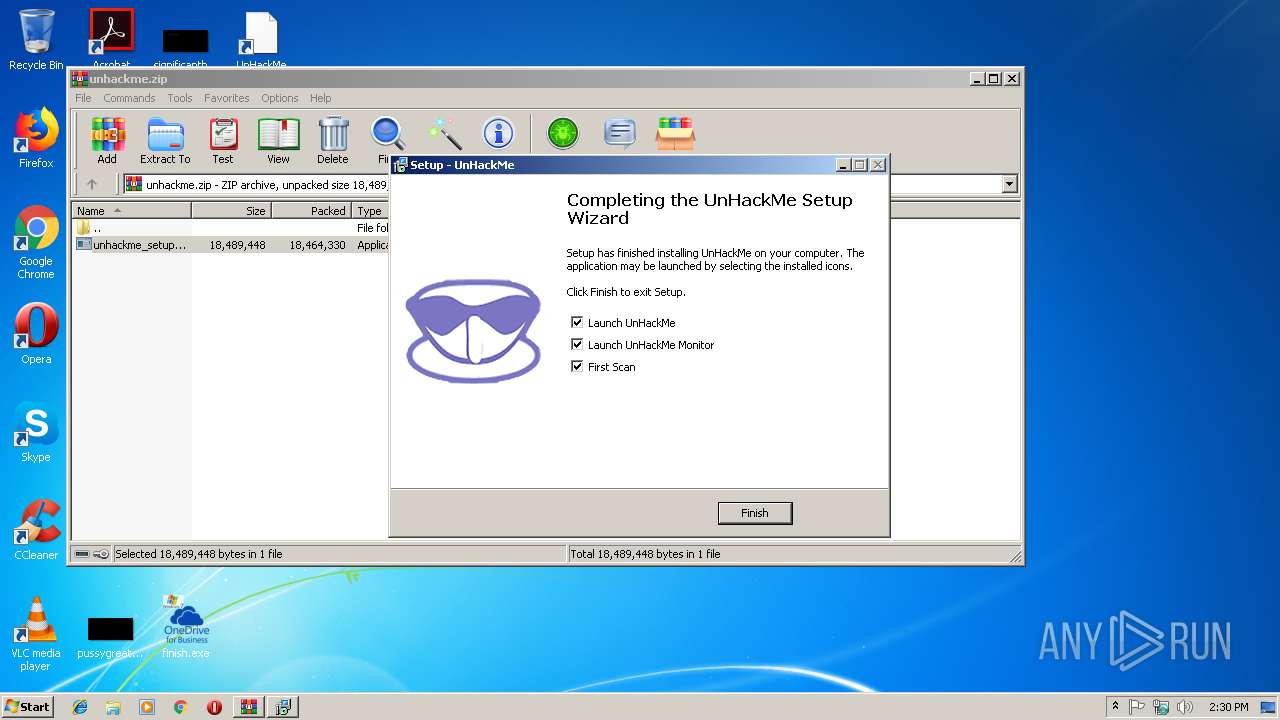
| File name: | finish.exe |
| Full analysis: | https://app.any.run/tasks/51c66f6b-8639-486e-abef-342e82400b81 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | February 21, 2019, 14:28:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F3785C36761BA6583A5F36D60C9D13E5 |
| SHA1: | 7CCD94137ED403656D711437187E8C085FF345B9 |
| SHA256: | 35DE0CE1AE8A131E40590823ABC8D597DF5620AC0C63BB3AA4FABEC50CA31932 |
| SSDEEP: | 49152:4h+ZkldoPK8Ya0Dh0H/9QiozzEXY75ka8R0gh2yNm7DM+DMdk9hC7KKALOonCvf:52cPK8UCQiel8R2HXMsMqy7KKALMX |
MALICIOUS
Uses SVCHOST.EXE for hidden code execution
- dllhost.exe (PID: 4028)
- dllhost.exe (PID: 2680)
DARKVNC was detected
- svchost.exe (PID: 2316)
- svchost.exe (PID: 2372)
Application was dropped or rewritten from another process
- unhackme_setup.exe (PID: 3652)
- build__Protected.exe (PID: 3592)
- build_startup_Protected.exe (PID: 1832)
- unhackme_setup.exe (PID: 3780)
- Unhackme.exe (PID: 2388)
- unhackmeschedule.exe (PID: 3984)
- wu.exe (PID: 2652)
- reanimator.exe (PID: 3124)
- reanimator.exe (PID: 2368)
- reanimator.exe (PID: 3308)
- mozlz4d.exe (PID: 2884)
- regruninfo.exe (PID: 3120)
- regruninfo.exe (PID: 2224)
- regruninfo.exe (PID: 1244)
- 7za.exe (PID: 3880)
Changes the autorun value in the registry
- dllhost.exe (PID: 4028)
Connects to CnC server
- svchost.exe (PID: 2316)
- svchost.exe (PID: 2372)
Loads the Task Scheduler COM API
- unhackmeschedule.exe (PID: 3984)
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
Loads dropped or rewritten executable
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
- reanimator.exe (PID: 2368)
Changes settings of System certificates
- regruninfo.exe (PID: 3120)
- reanimator.exe (PID: 3308)
- regruninfo.exe (PID: 1244)
Actions looks like stealing of personal data
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
Loads the Task Scheduler DLL interface
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
Dropped file may contain instructions of ransomware
- reanimator.exe (PID: 3124)
SUSPICIOUS
Executable content was dropped or overwritten
- finish.exe (PID: 3752)
- WinRAR.exe (PID: 3672)
- unhackme_setup.exe (PID: 3652)
- unhackme_setup.exe (PID: 3780)
- unhackme_setup.tmp (PID: 3084)
Creates files in the user directory
- finish.exe (PID: 3752)
- regruninfo.exe (PID: 2224)
Modifies the open verb of a shell class
- unhackme_setup.tmp (PID: 3084)
Creates files in the Windows directory
- unhackme_setup.tmp (PID: 3084)
- Unhackme.exe (PID: 2388)
Dropped object may contain URLs of mainers pools
- unhackme_setup.tmp (PID: 3084)
Creates files in the driver directory
- unhackme_setup.tmp (PID: 3084)
- Unhackme.exe (PID: 2388)
Uses NETSH.EXE for network configuration
- unhackme_setup.tmp (PID: 3084)
Creates files in the program directory
- reanimator.exe (PID: 2368)
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
Adds / modifies Windows certificates
- regruninfo.exe (PID: 3120)
- reanimator.exe (PID: 3308)
- regruninfo.exe (PID: 1244)
Creates COM task schedule object
- Unhackme.exe (PID: 2388)
Low-level read access rights to disk partition
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
Searches for installed software
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
INFO
Application launched itself
- chrome.exe (PID: 296)
Reads Internet Cache Settings
- chrome.exe (PID: 296)
Application was dropped or rewritten from another process
- unhackme_setup.tmp (PID: 2300)
- unhackme_setup.tmp (PID: 3084)
Dropped object may contain TOR URL's
- unhackme_setup.tmp (PID: 3084)
- Unhackme.exe (PID: 2388)
- reanimator.exe (PID: 3308)
- regruninfo.exe (PID: 1244)
- reanimator.exe (PID: 3124)
Loads dropped or rewritten executable
- unhackme_setup.tmp (PID: 3084)
Creates files in the program directory
- unhackme_setup.tmp (PID: 3084)
Dropped object may contain Bitcoin addresses
- unhackme_setup.tmp (PID: 3084)
- reanimator.exe (PID: 3124)
- reanimator.exe (PID: 3308)
- regruninfo.exe (PID: 2224)
- regruninfo.exe (PID: 1244)
Creates a software uninstall entry
- unhackme_setup.tmp (PID: 3084)
Reads settings of System Certificates
- reanimator.exe (PID: 3308)
- reanimator.exe (PID: 3124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:01:22 13:20:33+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 581632 |
| InitializedDataSize: | 2825216 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2800a |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 22-Jan-2019 12:20:33 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000110 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 22-Jan-2019 12:20:33 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0008DFDD | 0x0008E000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.67525 |
.rdata | 0x0008F000 | 0x0002FD8E | 0x0002FE00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.76324 |
.data | 0x000BF000 | 0x00008F74 | 0x00005200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.19638 |
.rsrc | 0x000C8000 | 0x002758E4 | 0x00275A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.96696 |
.reloc | 0x0033E000 | 0x00007134 | 0x00007200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.78396 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.40026 | 1007 | Latin 1 / Western European | English - United Kingdom | RT_MANIFEST |
2 | 7.92501 | 10215 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
3 | 4.31783 | 67624 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
4 | 4.47076 | 16936 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
5 | 4.77183 | 9640 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
6 | 4.74697 | 4264 | Latin 1 / Western European | English - United Kingdom | RT_ICON |
7 | 3.34702 | 1428 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
8 | 3.2817 | 1674 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
9 | 3.28849 | 1168 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
10 | 3.28373 | 1532 | Latin 1 / Western European | English - United Kingdom | RT_STRING |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
MPR.dll |
OLEAUT32.dll |
PSAPI.DLL |
SHELL32.dll |
Total processes
81
Monitored processes
39
Malicious processes
19
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1244 | "C:\Program Files\UnHackMe\regruninfo.exe" /sendlog "C:\Users\admin\Desktop\regrunlog.txt" | C:\Program Files\UnHackMe\regruninfo.exe | reanimator.exe | ||||||||||||
User: admin Company: Greatis Software Integrity Level: HIGH Description: Module for retrieving file info from Internet Exit code: 0 Version: 10.0.0.750 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\unhackme.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | chrome.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=996,15199732680498109763,2113684897000526393,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=C595AFC46A4D6145A0CF5B53FE26E08E --mojo-platform-channel-handle=1012 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1832 | "C:\Users\admin\AppData\Roaming\Z33775803\build_startup_Protected.exe" | C:\Users\admin\AppData\Roaming\Z33775803\build_startup_Protected.exe | — | finish.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1904 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2224 | "C:\Program Files\UnHackMe\regruninfo.exe" C:\Users\admin\DOCUME~1\RegRun2\regrunlog.txt /hid: "2019-02-21-14:30:17 On-line Multi-Antivirus Scanning...." /mal: C:\Users\admin\DOCUME~1\RegRun2\ | C:\Program Files\UnHackMe\regruninfo.exe | reanimator.exe | ||||||||||||
User: admin Company: Greatis Software Integrity Level: HIGH Description: Module for retrieving file info from Internet Exit code: 0 Version: 10.0.0.750 Modules
| |||||||||||||||
| 2260 | C:\ProgramData\RegRun\avgwdsvc.exe | C:\ProgramData\RegRun\avgwdsvc.exe | — | reanimator.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 5 Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=996,15199732680498109763,2113684897000526393,131072 --enable-features=PasswordImport --service-pipe-token=3B148C399A616BD96FE2AC533094C6DB --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3B148C399A616BD96FE2AC533094C6DB --renderer-client-id=5 --mojo-platform-channel-handle=1908 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2300 | "C:\Users\admin\AppData\Local\Temp\is-0GEG3.tmp\unhackme_setup.tmp" /SL5="$201BE,18224442,56832,C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.38763\unhackme_setup.exe" | C:\Users\admin\AppData\Local\Temp\is-0GEG3.tmp\unhackme_setup.tmp | — | unhackme_setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
5 372
Read events
3 196
Write events
2 091
Delete events
85
Modification events
| (PID) Process: | (3752) finish.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3752) finish.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4028) dllhost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | Load |
Value: C:\Windows\System32\dllhost.exe | |||
| (PID) Process: | (2200) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 296-13195232967156500 |
Value: 259 | |||
| (PID) Process: | (296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
Executable files
24
Suspicious files
113
Text files
282
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3752 | finish.exe | C:\Users\admin\AppData\Local\Temp\autE6C7.tmp | — | |
MD5:— | SHA256:— | |||
| 3752 | finish.exe | C:\Users\admin\AppData\Local\Temp\autEADF.tmp | — | |
MD5:— | SHA256:— | |||
| 296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b0764011-89b3-4c55-ba54-85b6255c087c.tmp | — | |
MD5:— | SHA256:— | |||
| 296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\85d28706-1083-4a21-a7fa-b2f70d894ae5.tmp | — | |
MD5:— | SHA256:— | |||
| 3752 | finish.exe | C:\Users\admin\AppData\Roaming\Z33775803\build_startup_Protected.exe | executable | |
MD5:— | SHA256:— | |||
| 3752 | finish.exe | C:\Users\admin\AppData\Roaming\Z33775803\build__Protected.exe | executable | |
MD5:— | SHA256:— | |||
| 296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\CacheStorage\e6622492fa163609ddd4212f54512baa07929ed3\caecb3bd-7969-4305-84d6-3a376453ec73\index-dir\temp-index | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
110
DNS requests
20
Threats
338
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2652 | wu.exe | GET | — | 208.76.245.34:80 | http://greatis.com/dbs.ini | US | — | — | whitelisted |
3120 | regruninfo.exe | GET | 200 | 93.184.221.240:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.2 Kb | whitelisted |
3120 | regruninfo.exe | GET | 200 | 52.85.188.197:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2372 | svchost.exe | 216.170.126.109:443 | — | ColoCrossing | US | malicious |
2316 | svchost.exe | 216.170.126.109:443 | — | ColoCrossing | US | malicious |
296 | chrome.exe | 216.58.208.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
296 | chrome.exe | 172.217.23.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
296 | chrome.exe | 172.217.16.163:443 | www.google.de | Google Inc. | US | whitelisted |
296 | chrome.exe | 172.217.21.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
296 | chrome.exe | 172.217.18.100:443 | www.google.com | Google Inc. | US | whitelisted |
296 | chrome.exe | 128.140.224.121:443 | softpedia-secure-download.com | T-Mobile Czech Republic a.s. | RO | unknown |
296 | chrome.exe | 216.58.205.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
296 | chrome.exe | 216.58.205.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
play.google.com |
| whitelisted |
softpedia-secure-download.com |
| unknown |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2316 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] BackDoor.DarkVNC.6 |
2372 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] BackDoor.DarkVNC.6 |
2372 | svchost.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] VNC connection |
2316 | svchost.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] VNC connection |
2316 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] BackDoor.DarkVNC.6 |
2316 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] BackDoor.DarkVNC.6 |
2372 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] BackDoor.DarkVNC.6 |
2316 | svchost.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] VNC connection |
2372 | svchost.exe | Potential Corporate Privacy Violation | SUSPICIOUS [PTsecurity] VNC connection |
2372 | svchost.exe | A Network Trojan was detected | MALWARE [PTsecurity] BackDoor.DarkVNC.6 |
131 ETPRO signatures available at the full report