| File name: | faf551a93829a709a7174f6ae283cbde.exe |
| Full analysis: | https://app.any.run/tasks/1fa2b2bc-cbfa-4916-bcfa-e862f42039fc |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | April 29, 2025, 07:18:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | FAF551A93829A709A7174F6AE283CBDE |
| SHA1: | E7A1FE71A67F25F3E37EA4B78D1B07710ADFAB66 |
| SHA256: | 35D825988B4411C29DBF9360578872C722C58D63C8AE1967153C9A28DFE45375 |
| SSDEEP: | 196608:z/9YujRAOEOFucWMvz5zUqvHKmXpH9+JaiRgSff7q:2kAxOFZdTtFYvySX7q |
MALICIOUS
Executing a file with an untrusted certificate
- core.exe (PID: 1228)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
LUMMA mutex has been found
- core.exe (PID: 1228)
Actions looks like stealing of personal data
- core.exe (PID: 1228)
SUSPICIOUS
Executable content was dropped or overwritten
- faf551a93829a709a7174f6ae283cbde.exe (PID: 5960)
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
Reads the Windows owner or organization settings
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
Reads security settings of Internet Explorer
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
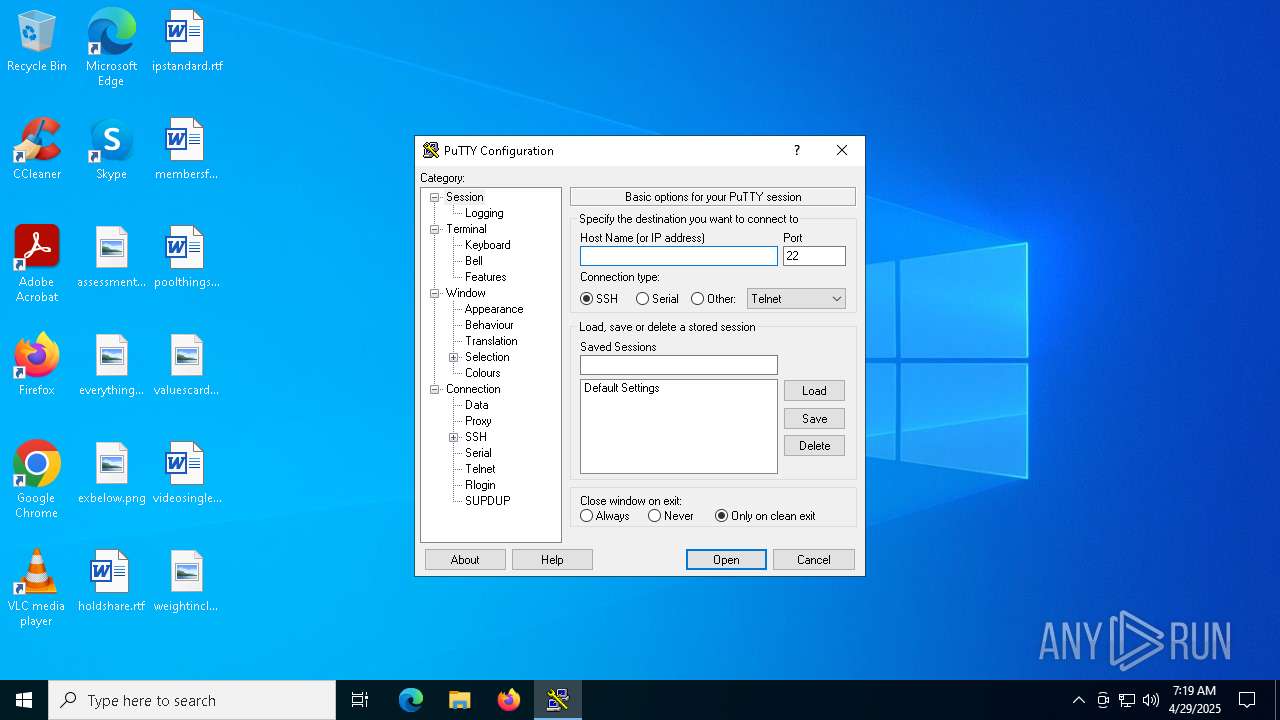
PUTTY has been detected
- putty.exe (PID: 1324)
Searches for installed software
- core.exe (PID: 1228)
INFO
Checks supported languages
- faf551a93829a709a7174f6ae283cbde.exe (PID: 5960)
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
- putty.exe (PID: 1324)
- info.exe (PID: 5800)
- core.exe (PID: 1228)
The sample compiled with english language support
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
Create files in a temporary directory
- faf551a93829a709a7174f6ae283cbde.exe (PID: 5960)
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
Reads the computer name
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
- putty.exe (PID: 1324)
- info.exe (PID: 5800)
- core.exe (PID: 1228)
Creates files or folders in the user directory
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
Creates a software uninstall entry
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
Process checks computer location settings
- faf551a93829a709a7174f6ae283cbde.tmp (PID: 4920)
Reads the software policy settings
- core.exe (PID: 1228)
- slui.exe (PID: 5344)
Checks proxy server information
- slui.exe (PID: 5344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:01:08 15:36:35+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 684032 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7f98 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | MyApp Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | MyApp |
| ProductVersion: | 1.0 |
Total processes
138
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1228 | "C:\Users\admin\AppData\Roaming\MyApp\core.exe" | C:\Users\admin\AppData\Roaming\MyApp\core.exe | faf551a93829a709a7174f6ae283cbde.tmp | ||||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Stremio Server JavaScript Runtime Version: 14.15.0 Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Roaming\MyApp\data\putty.exe" | C:\Users\admin\AppData\Roaming\MyApp\data\putty.exe | faf551a93829a709a7174f6ae283cbde.tmp | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Version: Release 0.83 (with embedded help) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4920 | "C:\Users\admin\AppData\Local\Temp\is-AHDBG.tmp\faf551a93829a709a7174f6ae283cbde.tmp" /SL5="$602E6,19201947,844800,C:\Users\admin\AppData\Local\Temp\faf551a93829a709a7174f6ae283cbde.exe" | C:\Users\admin\AppData\Local\Temp\is-AHDBG.tmp\faf551a93829a709a7174f6ae283cbde.tmp | faf551a93829a709a7174f6ae283cbde.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 5344 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5800 | "C:\Users\admin\AppData\Roaming\MyApp\info.exe" | C:\Users\admin\AppData\Roaming\MyApp\info.exe | faf551a93829a709a7174f6ae283cbde.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 5960 | "C:\Users\admin\AppData\Local\Temp\faf551a93829a709a7174f6ae283cbde.exe" | C:\Users\admin\AppData\Local\Temp\faf551a93829a709a7174f6ae283cbde.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: MyApp Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | info.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 827
Read events
1 807
Write events
20
Delete events
0
Modification events
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.4.0 | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Roaming\MyApp | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Roaming\MyApp\ | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: MyApp | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: default | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | DisplayName |
Value: MyApp version 1.0 | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Users\admin\AppData\Roaming\MyApp\unins000.exe | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Roaming\MyApp\unins000.exe" | |||
| (PID) Process: | (4920) faf551a93829a709a7174f6ae283cbde.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyApp_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Roaming\MyApp\unins000.exe" /SILENT | |||
Executable files
8
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-TKRU6.tmp | — | |
MD5:— | SHA256:— | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\core.exe | — | |
MD5:— | SHA256:— | |||
| 5960 | faf551a93829a709a7174f6ae283cbde.exe | C:\Users\admin\AppData\Local\Temp\is-AHDBG.tmp\faf551a93829a709a7174f6ae283cbde.tmp | executable | |
MD5:E4C43138CCB8240276872FD1AEC369BE | SHA256:46BE5E3F28A5E4ED63D66B901D927C25944B4DA36EFFEA9C97FB05994360EDF5 | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\unins000.exe | executable | |
MD5:4134EC81A9D645602B1FA265F98FBF35 | SHA256:69966257CE41717F2121EA1F03F8BFA1486423ACECFCC977DD9F1E157C911AD4 | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-LD9K1.tmp | executable | |
MD5:4134EC81A9D645602B1FA265F98FBF35 | SHA256:69966257CE41717F2121EA1F03F8BFA1486423ACECFCC977DD9F1E157C911AD4 | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\is-6B2S6.tmp | executable | |
MD5:EE0334F3083FED56762CE148E23EFAAA | SHA256:5E57CD5C98F41A350D15D833494DDCF6E58D0616753D8F80E5949BB6B53E2D45 | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\data\putty.exe | executable | |
MD5:36E31F610EEF3223154E6E8FD074190F | SHA256:16CBE40FB24CE2D422AFDDB5A90A5801CED32EF52C22C2FC77B25A90837F28AD | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\info.exe | executable | |
MD5:EE0334F3083FED56762CE148E23EFAAA | SHA256:5E57CD5C98F41A350D15D833494DDCF6E58D0616753D8F80E5949BB6B53E2D45 | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Roaming\MyApp\data\is-FVUDR.tmp | executable | |
MD5:36E31F610EEF3223154E6E8FD074190F | SHA256:16CBE40FB24CE2D422AFDDB5A90A5801CED32EF52C22C2FC77B25A90837F28AD | |||
| 4920 | faf551a93829a709a7174f6ae283cbde.tmp | C:\Users\admin\AppData\Local\Temp\is-VTP6H.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
30
DNS requests
18
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5800 | info.exe | GET | 200 | 82.115.223.212:80 | http://stats-1.crabdance.com/api/record?t=a6 | unknown | — | — | malicious |
6048 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6048 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5800 | info.exe | 82.115.223.212:80 | stats-1.crabdance.com | Partner LLC | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
stats-1.crabdance.com |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.crabdance .com Domain |
2196 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing Domain ( .crabdance .com) |
5800 | info.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS HTTP Request to a *.crabdance .com Domain |
5800 | info.exe | Misc activity | ET USER_AGENTS Go HTTP Client User-Agent |
5800 | info.exe | Misc activity | ET INFO Go-http-client User-Agent Observed Outbound |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |