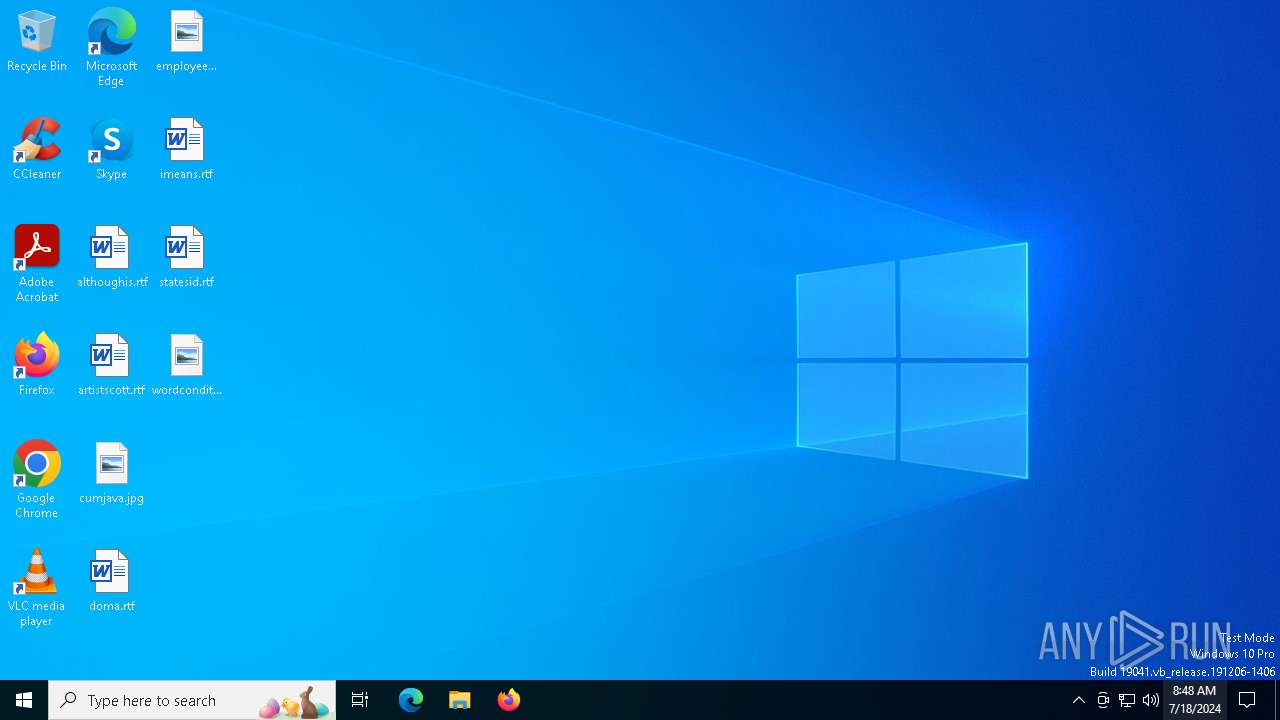
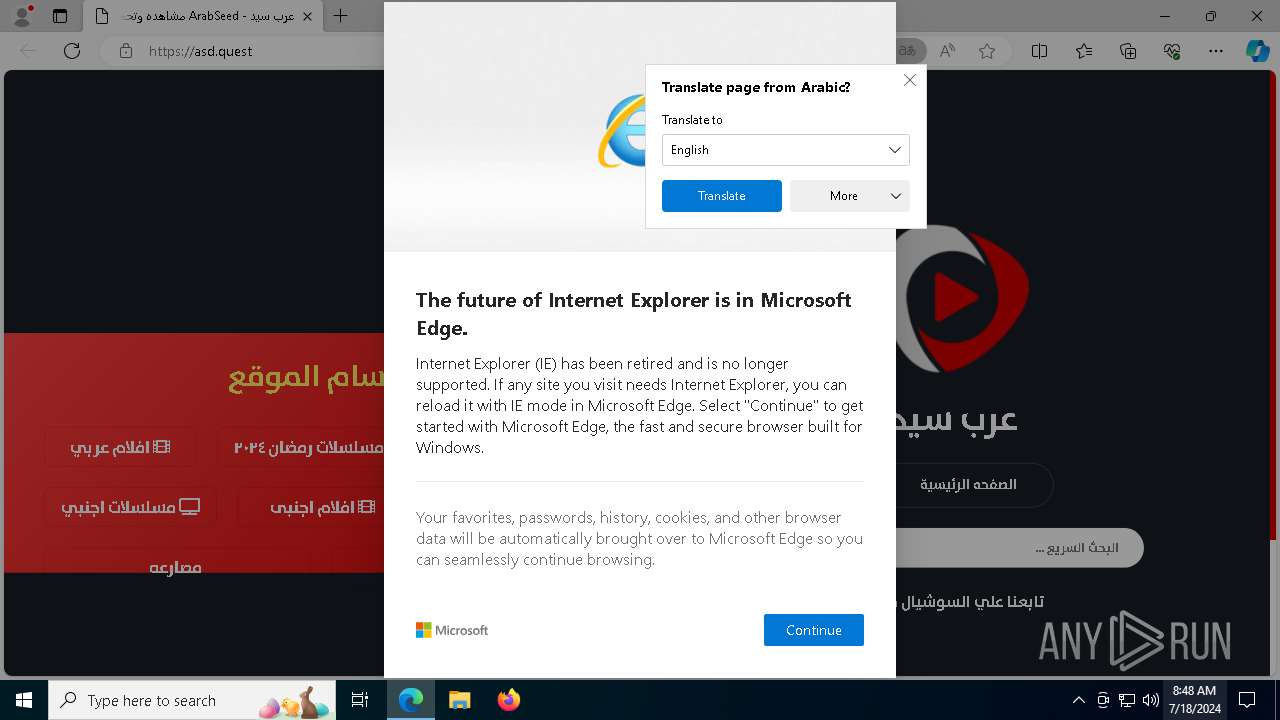
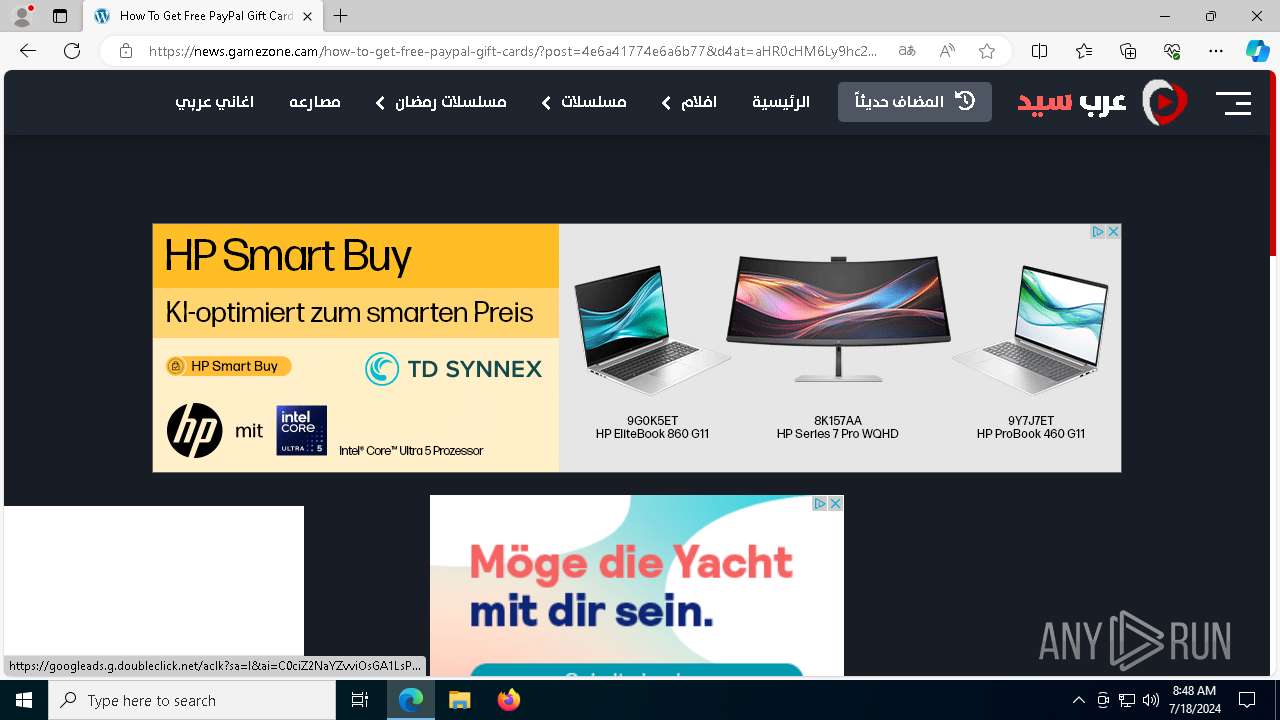
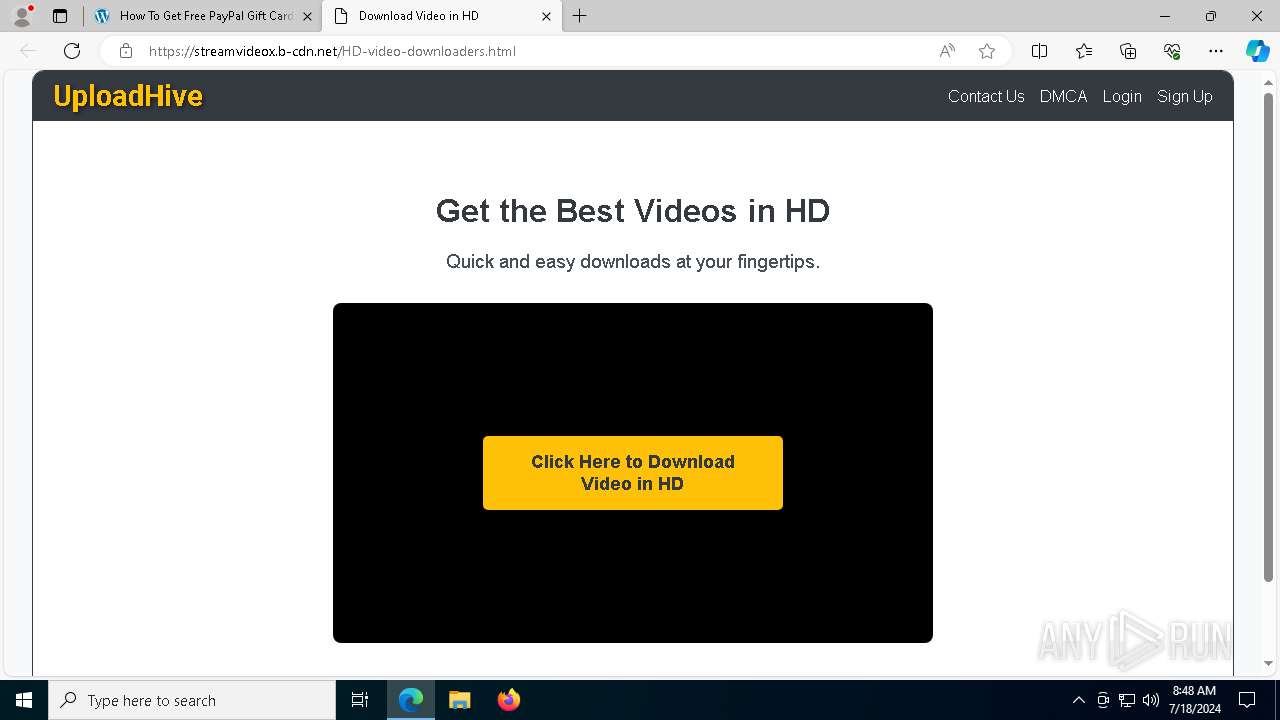
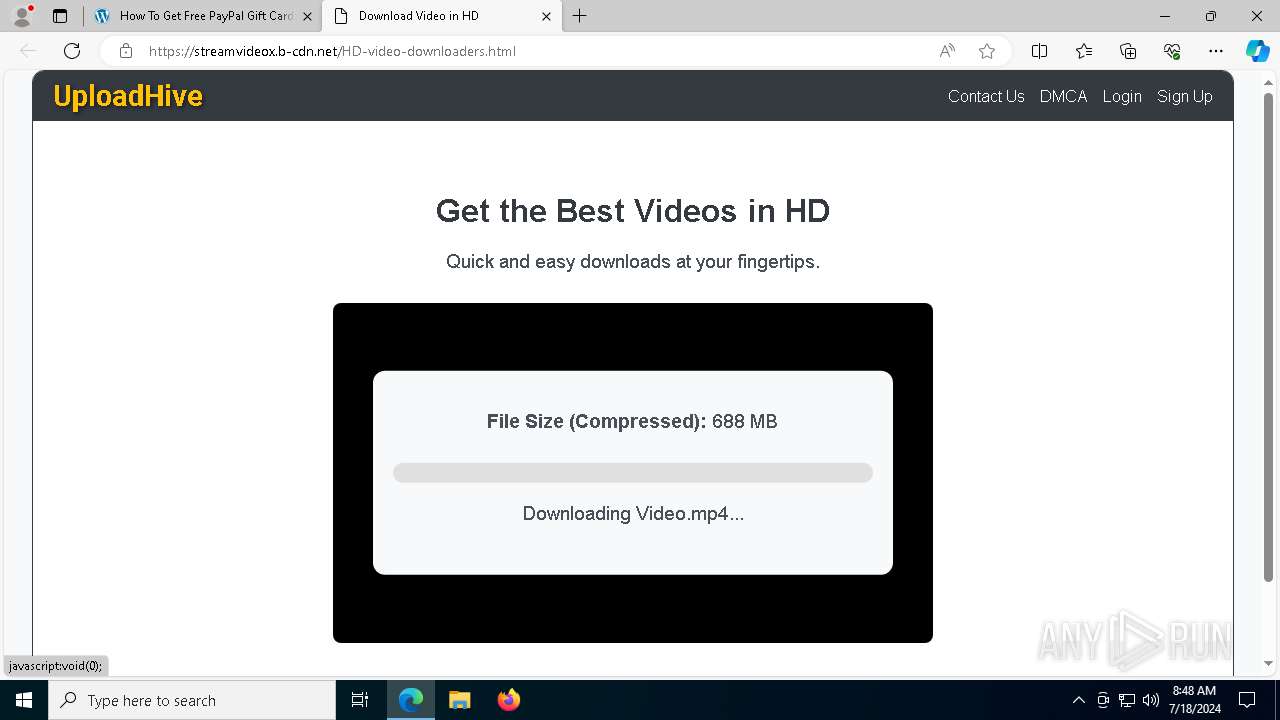
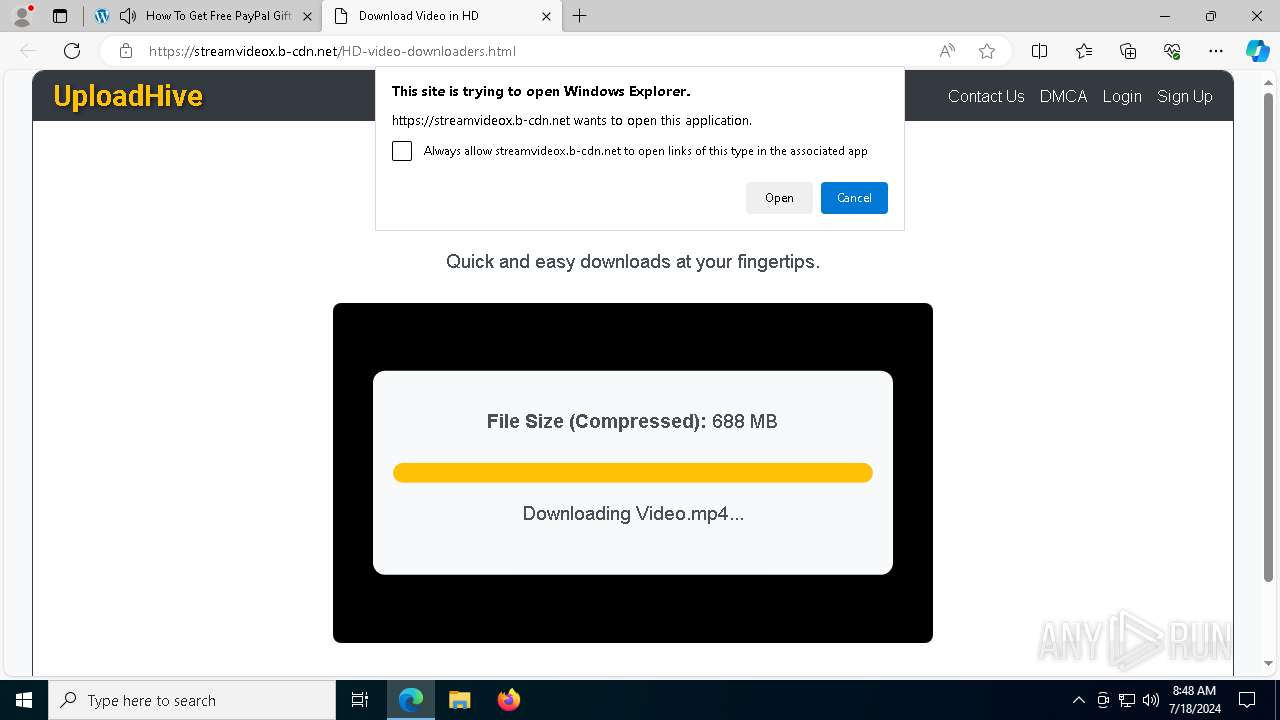
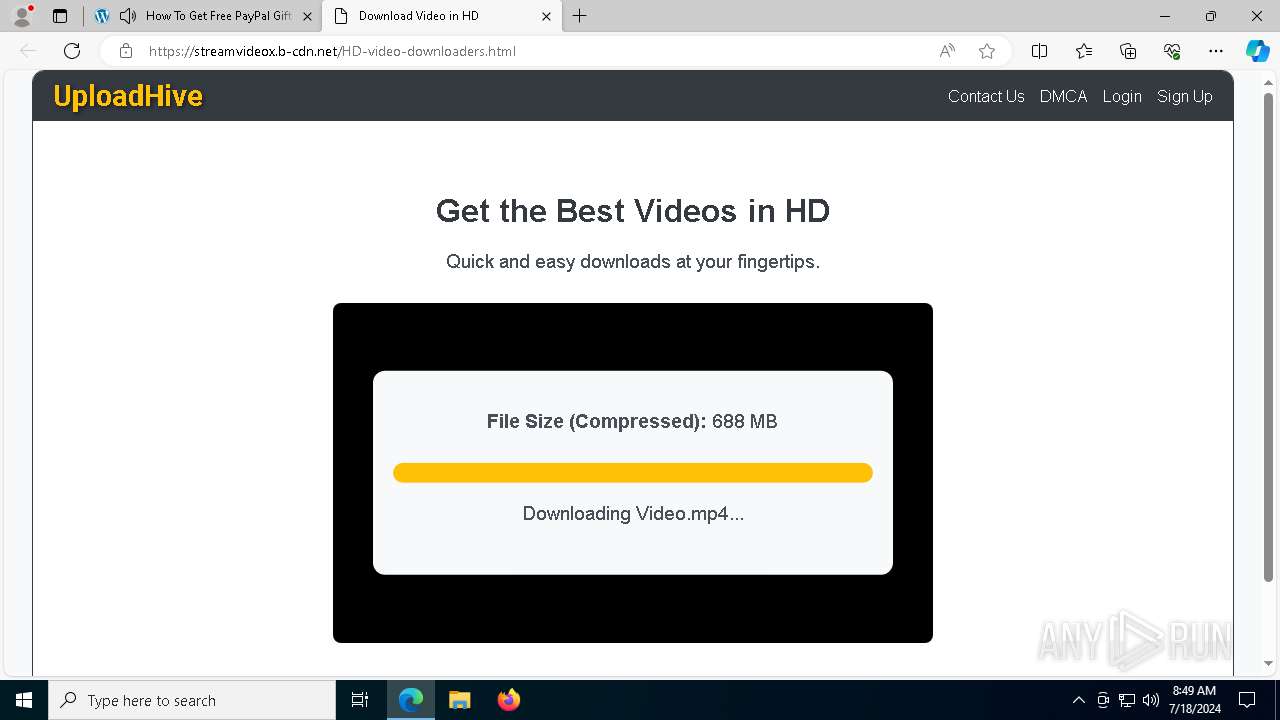
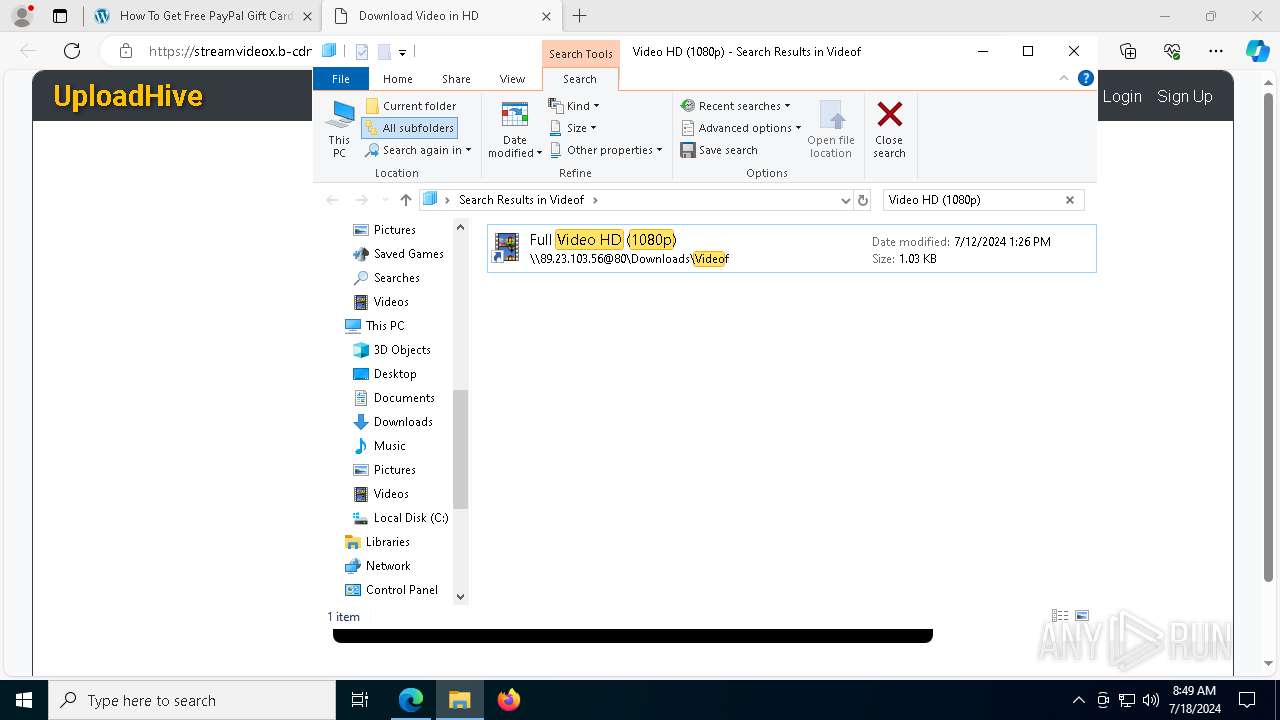
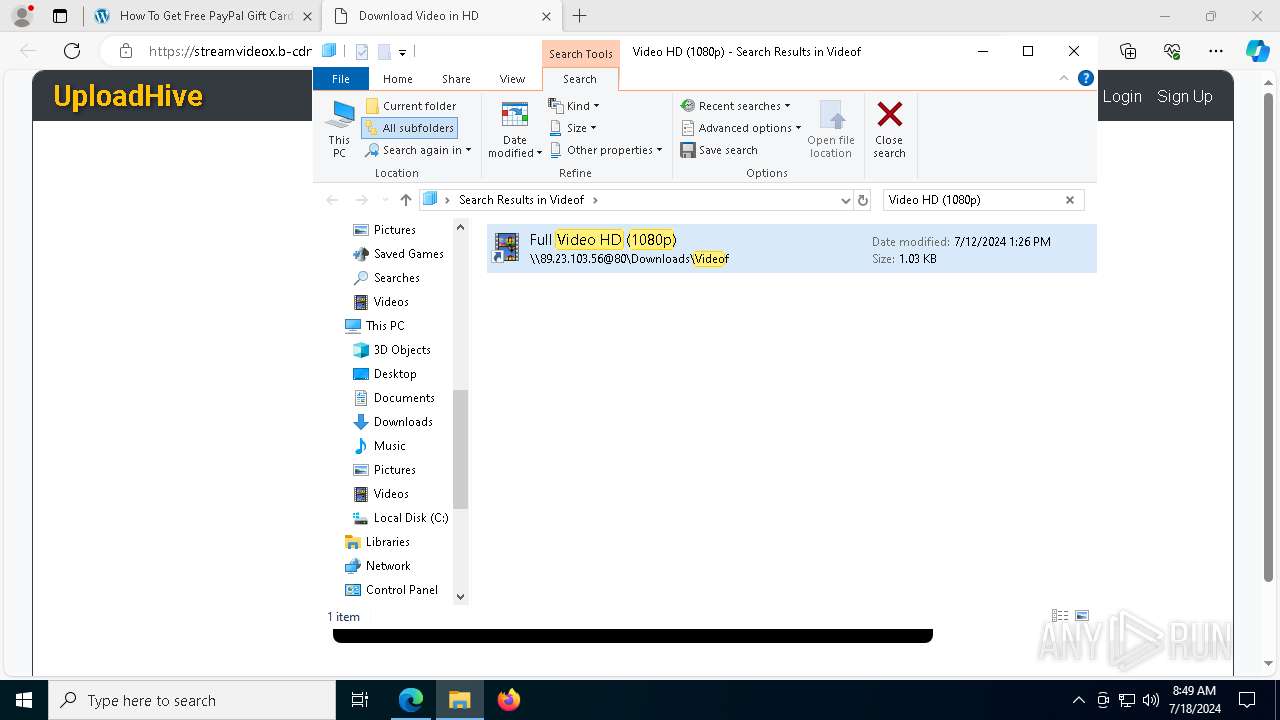
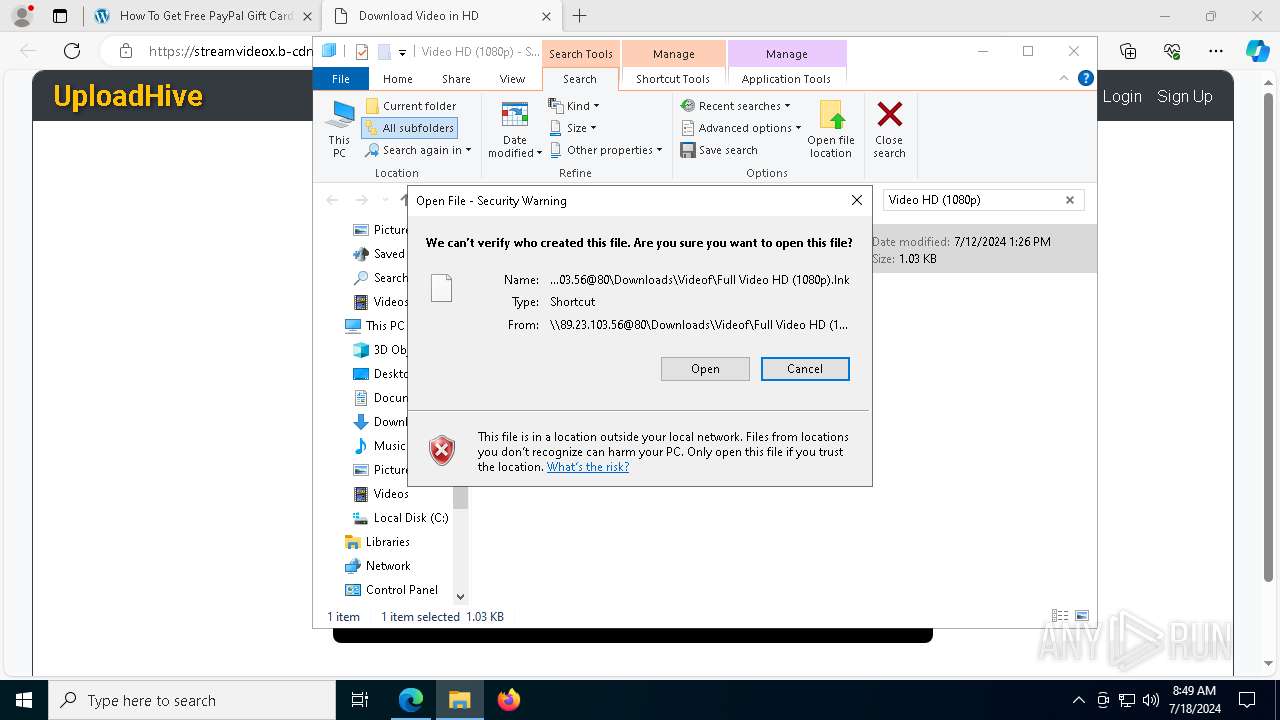
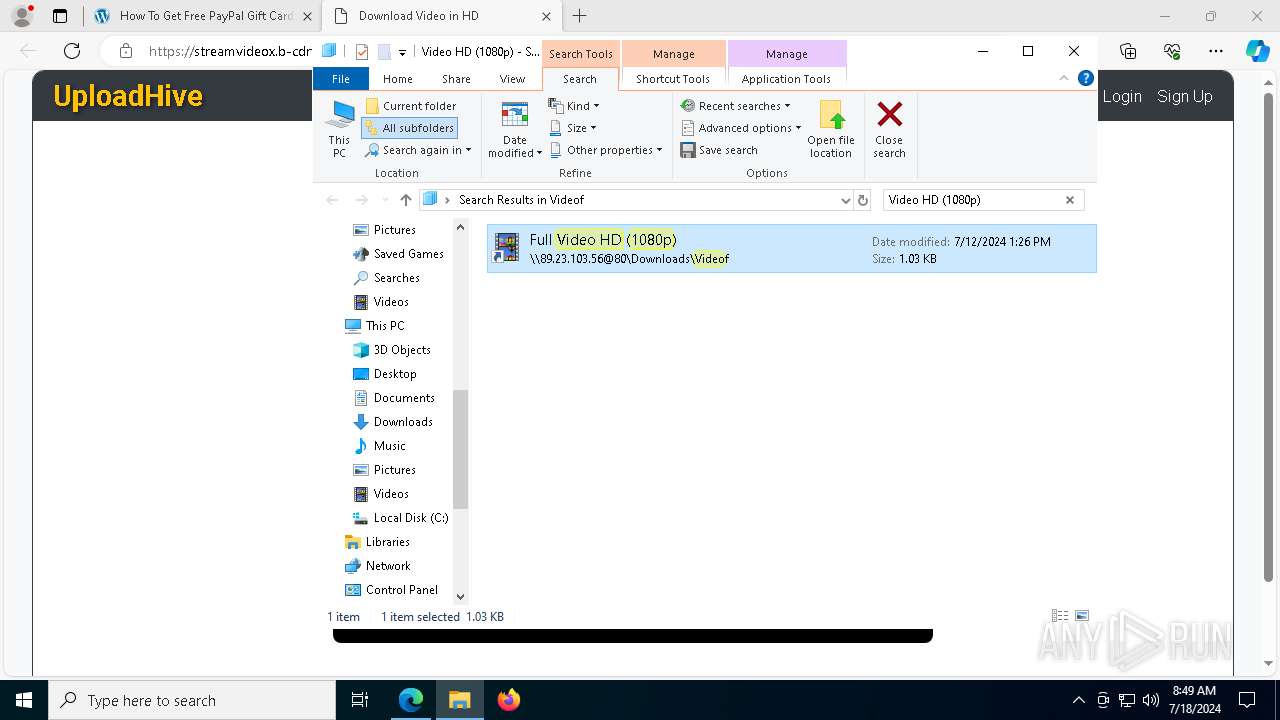
| URL: | arabseed.show |
| Full analysis: | https://app.any.run/tasks/12ee109c-b68b-45e7-864d-5888ae4a578f |
| Verdict: | Malicious activity |
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | July 18, 2024, 08:47:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 134B7DD726663DF91AF79DE514D7F6AD |
| SHA1: | B3FA36053C59CA3FF70D8C5CE4CB4DEDBD0D0941 |
| SHA256: | 3584D78156F6D0EAC646965B2A5DA913582E7C19F54973C2FFE878AB20A8CFA0 |
| SSDEEP: | 3:+/BuKS:+Jo |
MALICIOUS
Attempting to connect via WebDav
- svchost.exe (PID: 7804)
Run PowerShell with an invisible window
- powershell.exe (PID: 5764)
Scans artifacts that could help determine the target
- mshta.exe (PID: 4452)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 4452)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 5764)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 5764)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 5764)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 5764)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 5764)
Drops the executable file immediately after the start
- powershell.exe (PID: 5764)
- Setup.exe (PID: 5856)
HIJACKLOADER has been detected (YARA)
- SearchIndexer.exe (PID: 7528)
Connects to the CnC server
- SearchIndexer.exe (PID: 7528)
Actions looks like stealing of personal data
- SearchIndexer.exe (PID: 7528)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 7804)
Attempting to connect via WebDav
- msedge.exe (PID: 6252)
Abuses WebDav for code execution
- svchost.exe (PID: 7804)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 6520)
Uses pipe srvsvc via SMB (transferring data)
- conhost.exe (PID: 2204)
- powershell.exe (PID: 6520)
- msedge.exe (PID: 6252)
Potential Corporate Privacy Violation
- svchost.exe (PID: 7804)
Connects to the server without a host name
- svchost.exe (PID: 7804)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 4452)
Probably obfuscated PowerShell command line is found
- mshta.exe (PID: 4452)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 4452)
Base64-obfuscated command line is found
- mshta.exe (PID: 4452)
Cryptography encrypted command line is found
- powershell.exe (PID: 5764)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 5764)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 5764)
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 7608)
Executable content was dropped or overwritten
- powershell.exe (PID: 5764)
- Setup.exe (PID: 5856)
Process drops legitimate windows executable
- powershell.exe (PID: 5764)
- Setup.exe (PID: 5856)
The process drops C-runtime libraries
- powershell.exe (PID: 5764)
- Setup.exe (PID: 5856)
Loads Python modules
- Setup.exe (PID: 5856)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 5764)
Starts application with an unusual extension
- Setup.exe (PID: 5856)
Searches for installed software
- SearchIndexer.exe (PID: 7528)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 5764)
INFO
Application launched itself
- msedge.exe (PID: 6252)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6252)
Checks supported languages
- identity_helper.exe (PID: 7408)
- cookie_exporter.exe (PID: 7608)
- Setup.exe (PID: 5856)
- more.com (PID: 5872)
Connects to unusual port
- msedge.exe (PID: 6504)
Checks proxy server information
- conhost.exe (PID: 2204)
- powershell.exe (PID: 6520)
- mshta.exe (PID: 4452)
- cookie_exporter.exe (PID: 7608)
- slui.exe (PID: 5100)
- powershell.exe (PID: 5764)
Manual execution by a user
- powershell.exe (PID: 6520)
Reads security settings of Internet Explorer
- conhost.exe (PID: 2204)
Reads Internet Explorer settings
- mshta.exe (PID: 4452)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 5764)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5764)
Reads the computer name
- cookie_exporter.exe (PID: 7608)
- identity_helper.exe (PID: 7408)
- Setup.exe (PID: 5856)
- more.com (PID: 5872)
Disables trace logs
- powershell.exe (PID: 5764)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5764)
The executable file from the user directory is run by the Powershell process
- Setup.exe (PID: 5856)
Creates files or folders in the user directory
- Setup.exe (PID: 5856)
Reads the software policy settings
- slui.exe (PID: 7016)
- slui.exe (PID: 5100)
Create files in a temporary directory
- Setup.exe (PID: 5856)
- more.com (PID: 5872)
Drops the executable file immediately after the start
- msedge.exe (PID: 916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
228
Monitored processes
80
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8584 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1192 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --mojo-platform-channel-handle=6308 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8664 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1512 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=40 --mojo-platform-channel-handle=7672 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5456 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1708 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1828 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=39 --mojo-platform-channel-handle=1540 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8676 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=41 --mojo-platform-channel-handle=5512 --field-trial-handle=2132,i,14498156763205182976,7993307829200494991,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
37 955
Read events
37 705
Write events
239
Delete events
11
Modification events
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31119599 | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
35
Suspicious files
422
Text files
186
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1ceab5.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1ceab5.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1ceab5.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1ceab5.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1ceac5.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
127
TCP/UDP connections
349
DNS requests
254
Threats
97
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1832 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1832 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3760 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5112 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3656 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6252 | msedge.exe | OPTIONS | 200 | 89.23.103.56:80 | http://89.23.103.56/ | unknown | — | — | unknown |
7804 | svchost.exe | OPTIONS | 200 | 89.23.103.56:80 | http://89.23.103.56/Downloads | unknown | — | — | unknown |
7804 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads | unknown | — | — | unknown |
7804 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads | unknown | — | — | unknown |
7804 | svchost.exe | PROPFIND | 207 | 89.23.103.56:80 | http://89.23.103.56/Downloads | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3868 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
900 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1832 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1832 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6504 | msedge.exe | 188.114.97.3:443 | asd.quest | — | — | unknown |
6504 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
arabseed.show |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
asd.quest |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6504 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |
6504 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
6504 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
7804 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Retrieves Properties of a Lnk file via WebDAV |
7804 | svchost.exe | Misc activity | ET INFO LNK File Downloaded via HTTP |
7804 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7804 | svchost.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] A suspicious Lnk file was downloaded causing the exe file to be executed |
7804 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7804 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
7804 | svchost.exe | Misc activity | ET HUNTING Successful PROPFIND Response for Application Media Type |
5 ETPRO signatures available at the full report