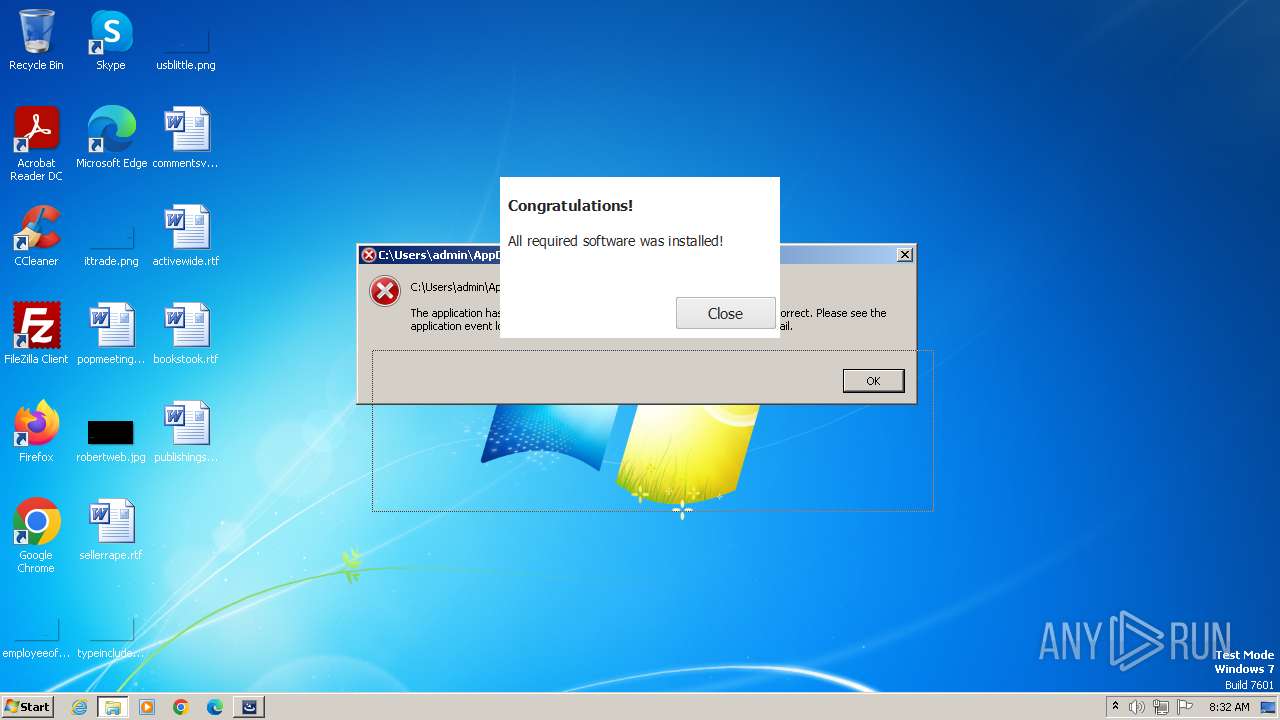
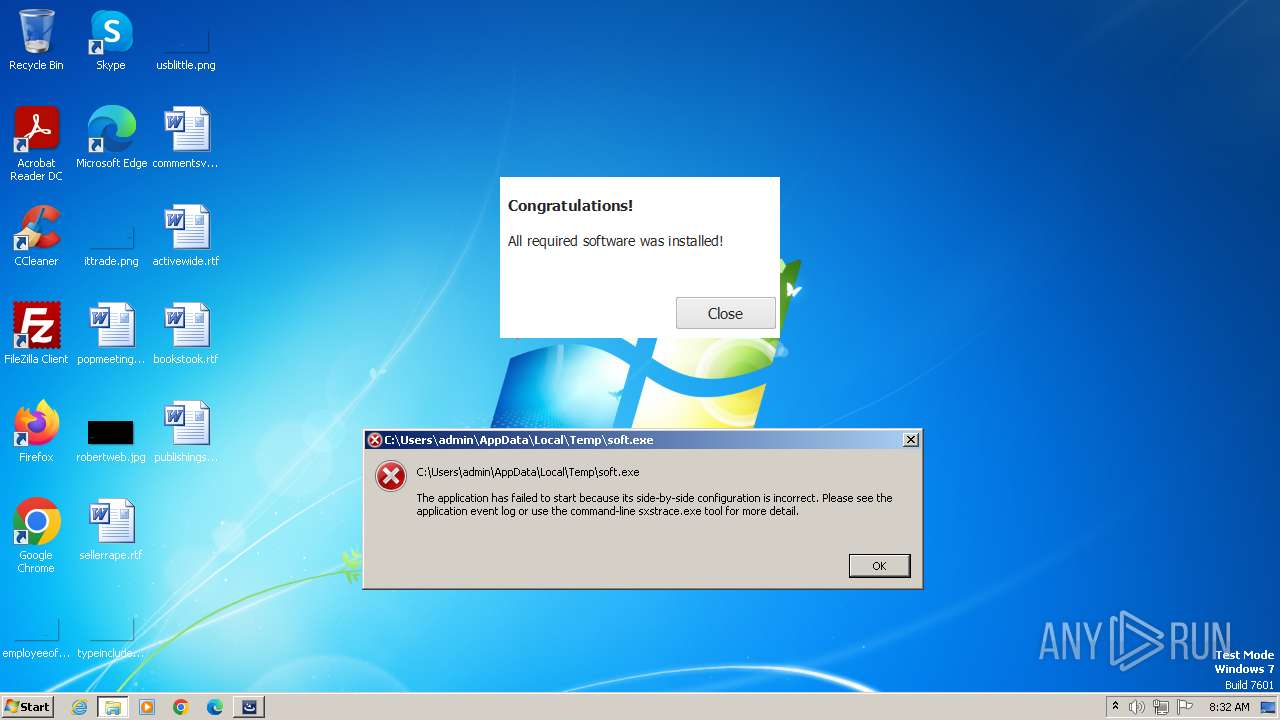
| File name: | Space.exe |
| Full analysis: | https://app.any.run/tasks/b548734d-555e-45d4-aaa5-8e698eb23d4c |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | November 08, 2023, 08:30:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 1BF373C53DE45AED1C626510FB8C3C74 |
| SHA1: | 5657E19B4FB86470E91AFC67D6F71D8668B61DC4 |
| SHA256: | 34A5D22F282DF6E3D88ADDA858DCDB20914EB18A94FD1F9BEF753FF7D9C90AD8 |
| SSDEEP: | 98304:gWxConLrrqOd/7aJU7RFWWPVGehLi38rrVSFlI9hI6jo1xM+S9OkTSa+0qNzXTpe:DoPQiCk6BcLht7fq |
MALICIOUS
Drops the executable file immediately after the start
- javaw.exe (PID: 3140)
REDLINE has been detected (YARA)
- Setup.exe (PID: 4048)
Steals credentials from Web Browsers
- Setup.exe (PID: 4048)
Actions looks like stealing of personal data
- Setup.exe (PID: 4048)
SUSPICIOUS
Checks for Java to be installed
- Space.exe (PID: 3484)
Reads the Internet Settings
- soft.exe (PID: 3936)
- Setup.exe (PID: 4048)
Searches for installed software
- Setup.exe (PID: 4048)
Reads browser cookies
- Setup.exe (PID: 4048)
Reads settings of System Certificates
- Setup.exe (PID: 4048)
INFO
Checks supported languages
- Space.exe (PID: 3484)
- javaw.exe (PID: 3140)
- soft.exe (PID: 3936)
- wmpnscfg.exe (PID: 3900)
- Setup.exe (PID: 4048)
Reads the computer name
- javaw.exe (PID: 3140)
- soft.exe (PID: 3936)
- wmpnscfg.exe (PID: 3900)
- Setup.exe (PID: 4048)
Reads the machine GUID from the registry
- javaw.exe (PID: 3140)
- wmpnscfg.exe (PID: 3900)
- Setup.exe (PID: 4048)
Creates files in the program directory
- javaw.exe (PID: 3140)
Create files in a temporary directory
- javaw.exe (PID: 3140)
- soft.exe (PID: 3936)
Reads the Internet Settings
- explorer.exe (PID: 3832)
- explorer.exe (PID: 1528)
- explorer.exe (PID: 1836)
Creates files or folders in the user directory
- javaw.exe (PID: 3140)
Manual execution by a user
- wmpnscfg.exe (PID: 3900)
Reads Environment values
- Setup.exe (PID: 4048)
Reads product name
- Setup.exe (PID: 4048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:01:06 20:50:04+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.22 |
| CodeSize: | 25088 |
| InitializedDataSize: | 14848 |
| UninitializedDataSize: | 36864 |
| EntryPoint: | 0x1290 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
56
Monitored processes
15
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 756 | explorer C:\Users\admin\AppData\Local\Temp\soft.exe | C:\Windows\explorer.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1528 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1644 | "C:\Users\admin\AppData\Local\Temp\soft.exe" | C:\Users\admin\AppData\Local\Temp\soft.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
| 1836 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | explorer C:\Users\admin\AppData\Local\Temp\soft.exe | C:\Windows\explorer.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2376 | "C:\Users\admin\AppData\Local\Temp\soft.exe" | C:\Users\admin\AppData\Local\Temp\soft.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
| 3140 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -Dfile.encoding=UTF-8 -classpath "C:\Users\admin\AppData\Local\Temp\Space.exe" org.develnext.jphp.ext.javafx.FXLauncher | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | Space.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3484 | "C:\Users\admin\AppData\Local\Temp\Space.exe" | C:\Users\admin\AppData\Local\Temp\Space.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3504 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3832 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
7 002
Read events
6 940
Write events
57
Delete events
5
Modification events
| (PID) Process: | (3140) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (3832) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3832) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3832) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3832) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3900) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{D772FDA6-B10B-4535-A09E-420BBE9CEFB4}\{2B146889-30B6-466B-9772-BB9B4BFFD365} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3900) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{D772FDA6-B10B-4535-A09E-420BBE9CEFB4} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3900) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{DA94A22A-B266-4A3A-955D-5E81D875FF41}\{2B146889-30B6-466B-9772-BB9B4BFFD365} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3900) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{DA94A22A-B266-4A3A-955D-5E81D875FF41} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3900) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{A68B6EB6-8A3D-429A-BF39-E4EC6654D972} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
4
Suspicious files
6
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | soft.exe | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | |
MD5:— | SHA256:— | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\467d5b05-9809-4bef-9ded-f821adf7f7e5\range-170537-341072.tmp | — | |
MD5:— | SHA256:— | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\467d5b05-9809-4bef-9ded-f821adf7f7e5\cookie.jurl | text | |
MD5:D751713988987E9331980363E24189CE | SHA256:4F53CDA18C2BAA0C0354BB5F9A3ECBE5ED12AB4D8E11BA873C2F11161202B945 | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\467d5b05-9809-4bef-9ded-f821adf7f7e5\range-464555-696831.tmp | binary | |
MD5:C0301A30E053D04AB24E01C4D239D6F3 | SHA256:FBFDE339D5CCEB8859881493D936172D90D4F3C06AE5F3438ECAF87B13130F47 | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\soft.exe | executable | |
MD5:96D20A834E22147464FE9E8B4F8CE469 | SHA256:30DDE6304870480AD6538489CD3ADFA053DF6EE1D1EC53E65E5C81B0FCA68C15 | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\467d5b05-9809-4bef-9ded-f821adf7f7e5\range-232278-464554.tmp | binary | |
MD5:C12E14E5B0DF6FC8D4FE919AF26E4D9B | SHA256:F9D5AD40257EFDE55811F4895E0234B13CF266939EC3CA16C140151033793D16 | |||
| 3140 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:1F3ABA5996A3C6BED6882B4FD6B9C142 | SHA256:AA5EE03DF07932170B8D0D66ADC67C5A845B91D6BE2DB34C9D61C556DEE3ACB5 | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\467d5b05-9809-4bef-9ded-f821adf7f7e5\range-0-232277.tmp | executable | |
MD5:3621839077AF3CDB7E0AC7159E4864C8 | SHA256:A3EC17D0573267CD68559FF26594FA09AEC845842550C2F67E03046C858D30F2 | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\467d5b05-9809-4bef-9ded-f821adf7f7e5\range-696832-929107.tmp | binary | |
MD5:44C831690773446AF772710FCA0723C6 | SHA256:24FCCA28E342D1B3CD5771B3EF55CA525D231E28C6EEDB8B96AAA9D1863D7A56 | |||
| 3140 | javaw.exe | C:\Users\admin\AppData\Local\Temp\467d5b05-9809-4bef-9ded-f821adf7f7e5\range-341073-511608.tmp | binary | |
MD5:78269529702549EB812846073F05B7D7 | SHA256:9689E2DE5926309DE224223F464B4BEA8B52AF141F141CE2C677A0353C8E714A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
26
DNS requests
3
Threats
19
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3140 | javaw.exe | 172.67.148.191:443 | download7z-soft.xyz | CLOUDFLARENET | US | unknown |
4048 | Setup.exe | 104.20.68.143:443 | pastebin.com | CLOUDFLARENET | — | unknown |
4048 | Setup.exe | 65.109.160.253:443 | up.xopolllo.today | Hetzner Online GmbH | FI | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download7z-soft.xyz |
| unknown |
pastebin.com |
| shared |
up.xopolllo.today |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
3140 | javaw.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |