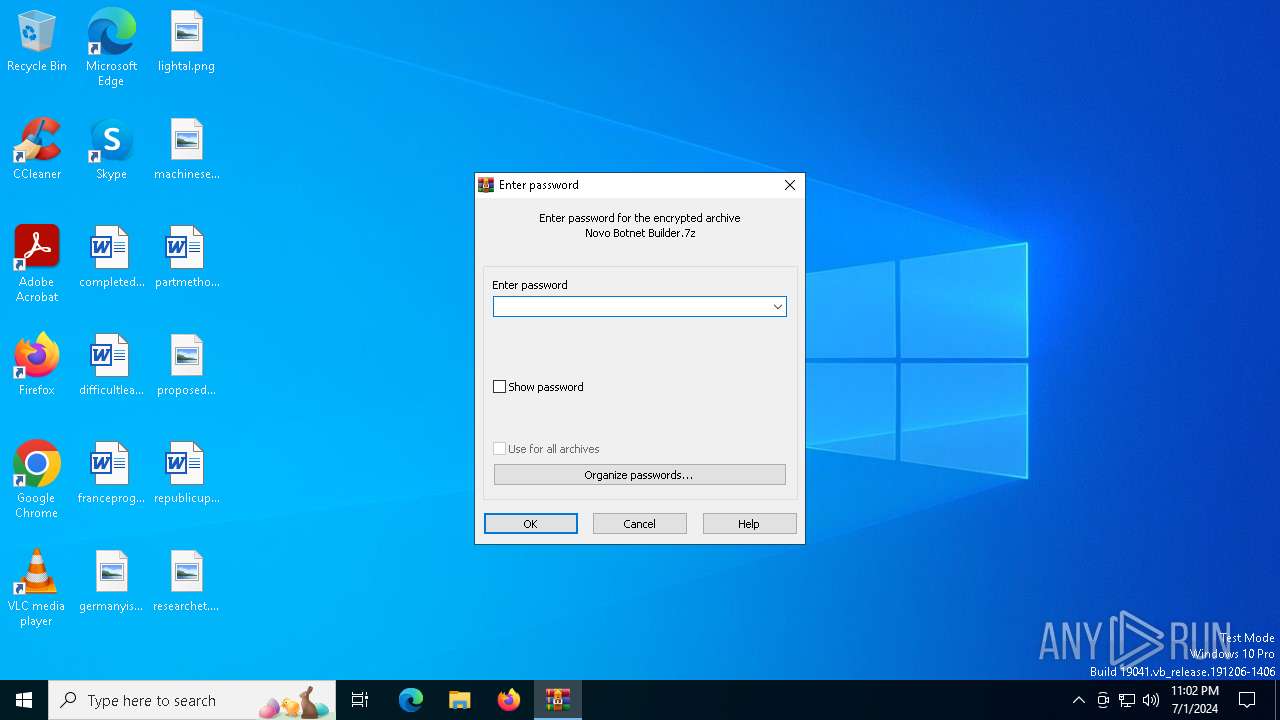
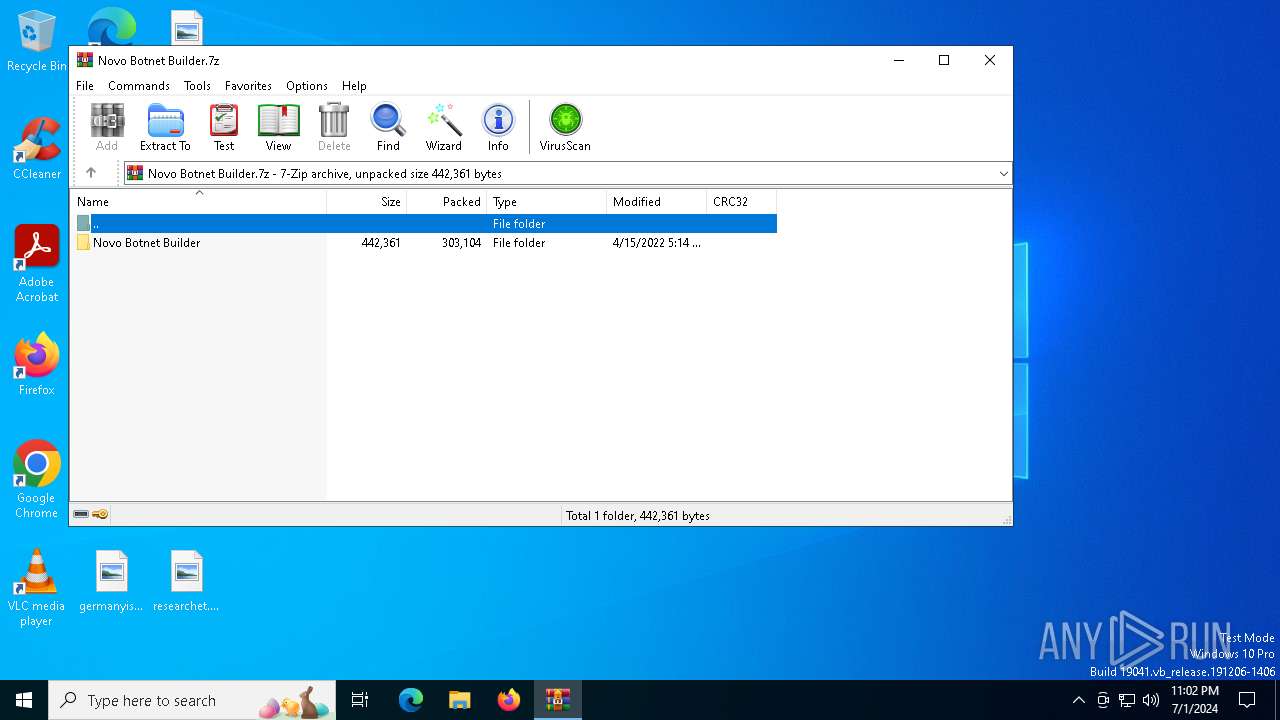
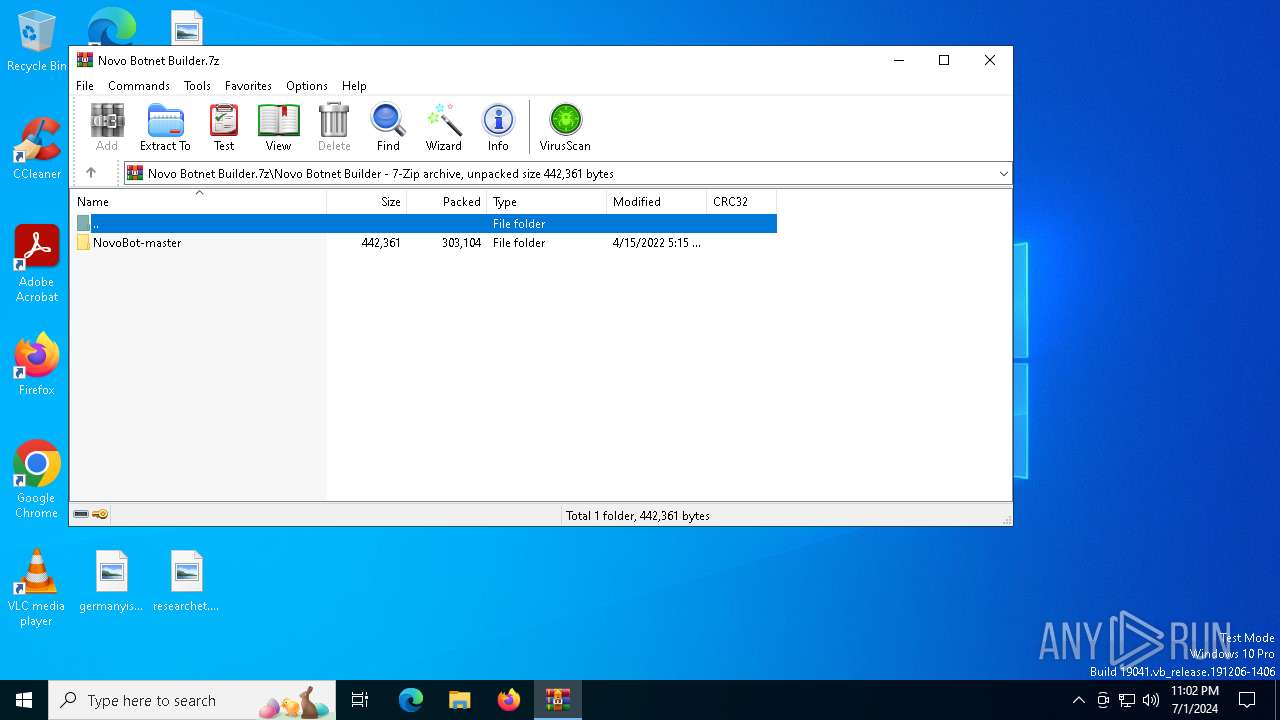
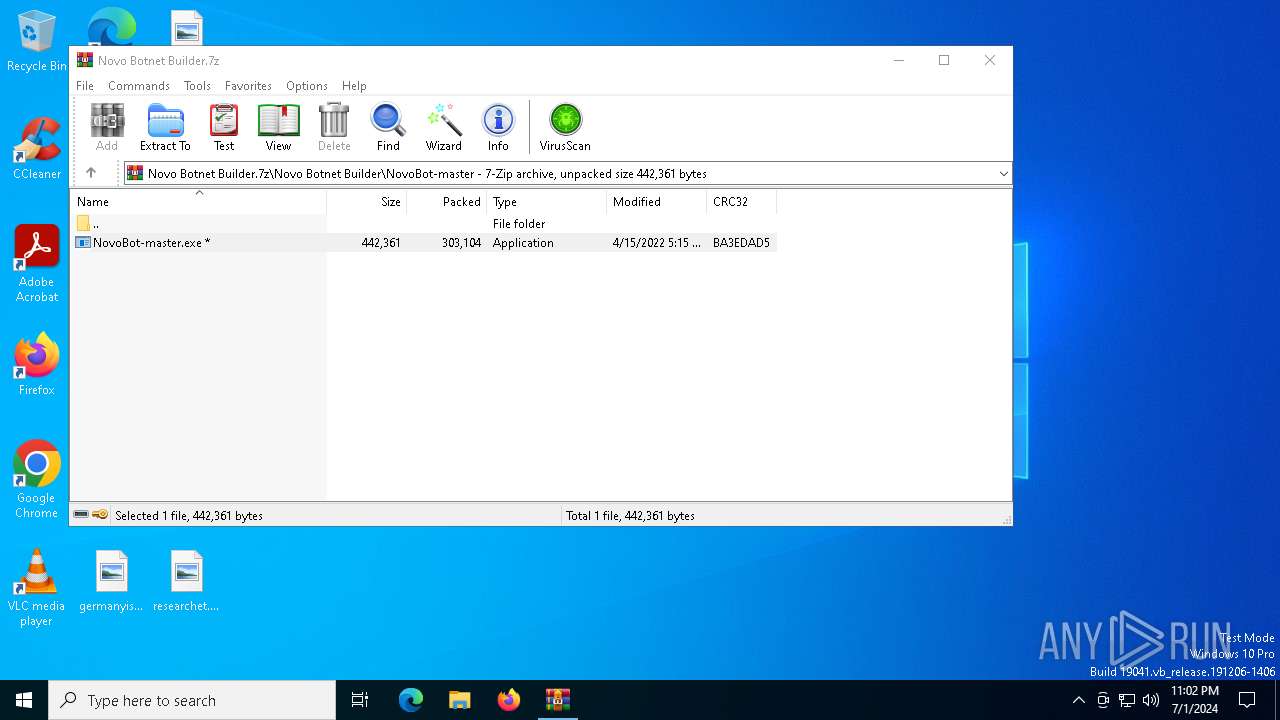
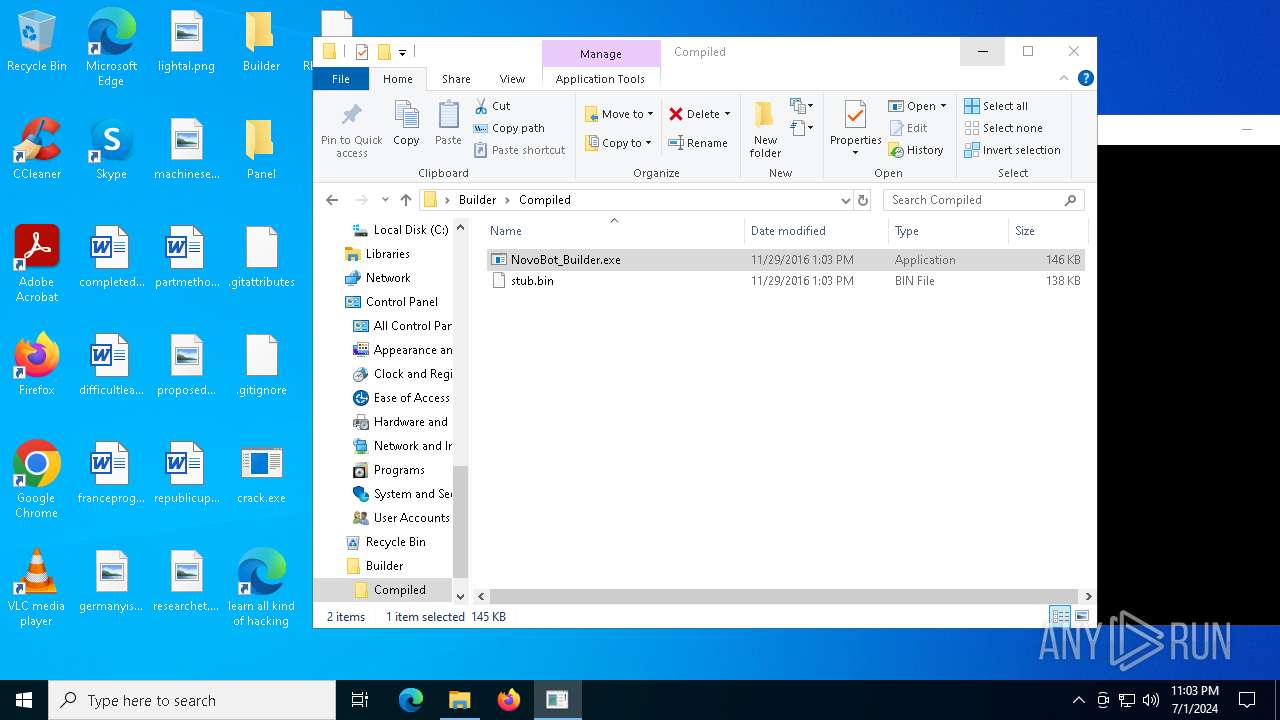
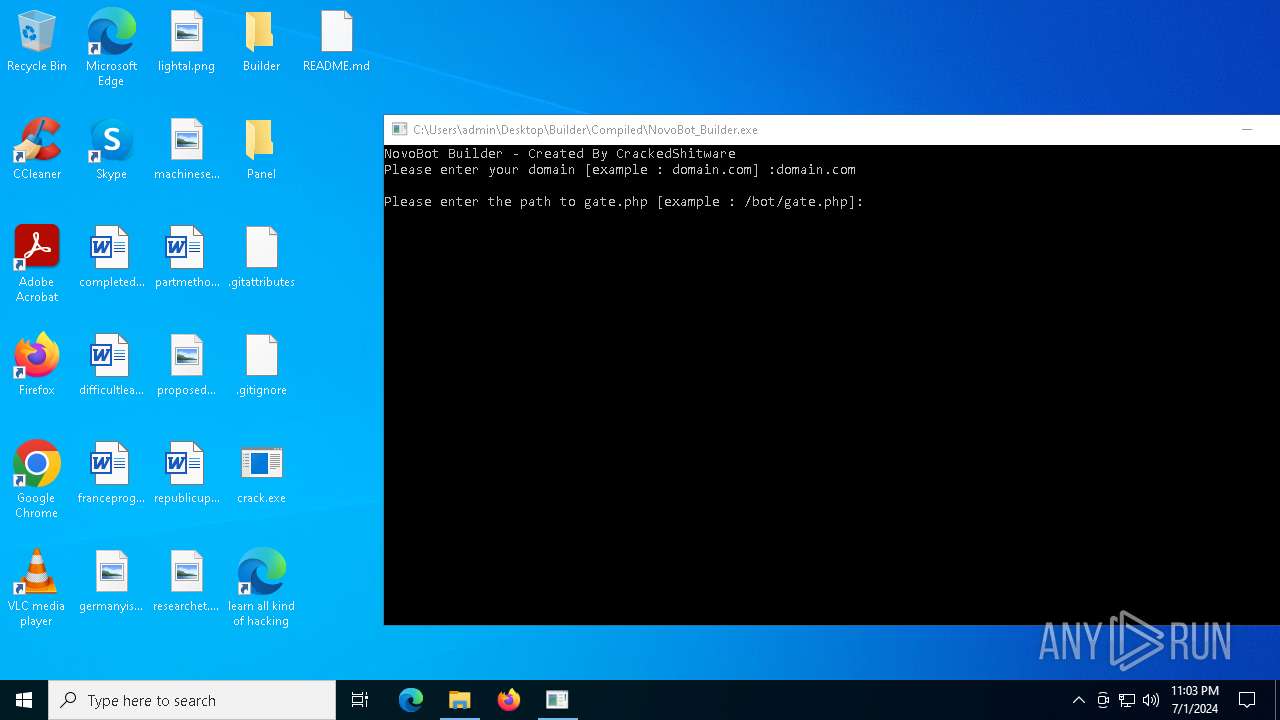
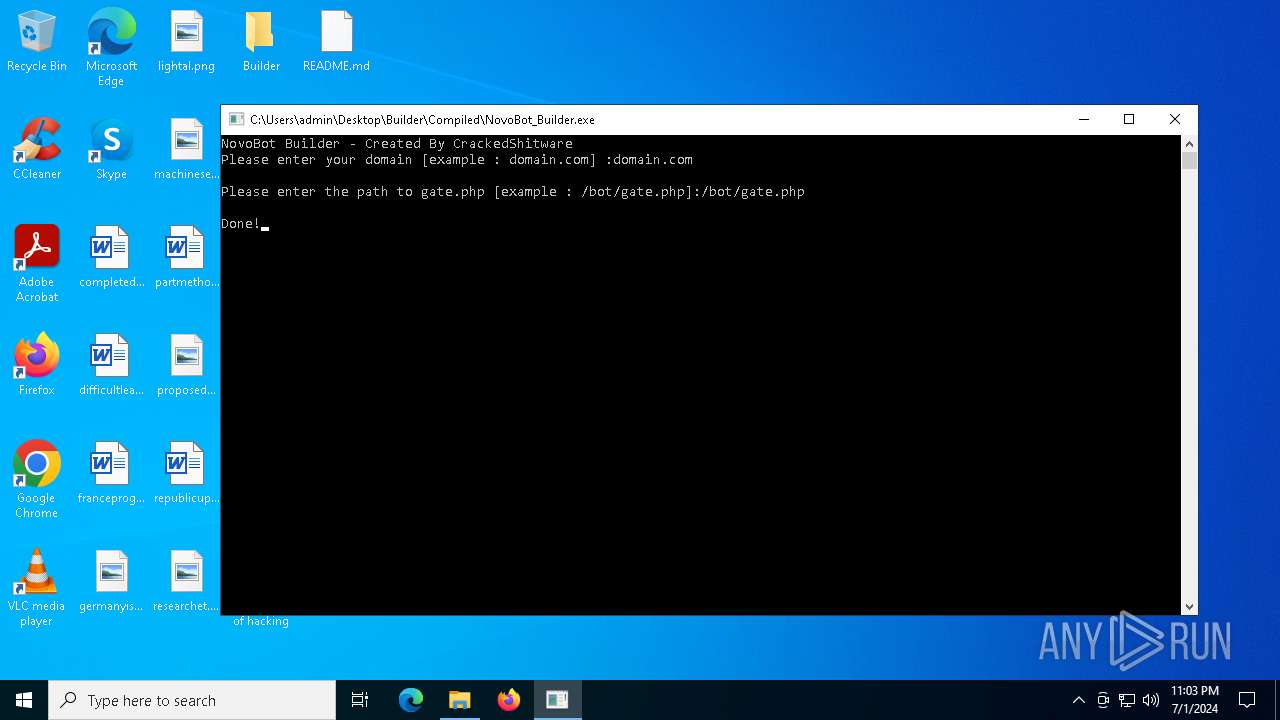
| File name: | Novo Botnet Builder.7z |
| Full analysis: | https://app.any.run/tasks/c611441e-d770-4640-8465-ec10115b24ca |
| Verdict: | Malicious activity |
| Threats: | WarZone RAT is a remote access trojan, which is written in C++ and offered as a malware-as-a-service. It packs a wide range of capabilities, from stealing victims’ files and passwords to capturing desktop activities. WarZone RAT is primarily distributed via phishing emails and receives regular updates from its C2. |
| Analysis date: | July 01, 2024, 23:02:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | B3D56739AC1259A1138B2B249A3ACF7D |
| SHA1: | 7AEBEB7480F884F0B51CBF8D63B1BBBA54C1EAB6 |
| SHA256: | 3483475A1A14498E47A315002AD894C357322DF76747BD4143D219BD97443192 |
| SSDEEP: | 12288:pqySJXgL7T6QjzMCEe4+tfQ3fFE7lAaZl3M/pALF2z0:gyAXe7uozMPe4+tfQ3fi7lAaZl3M/6Lx |
MALICIOUS
Drops the executable file immediately after the start
- NovoBot-master.exe (PID: 2276)
- crack.exe (PID: 3720)
- NovoBot_Builder.exe (PID: 2784)
- bot.exe (PID: 2208)
- bot.exe (PID: 732)
- load.exe (PID: 4448)
Create files in the Startup directory
- crack.exe (PID: 3720)
- crack.exe (PID: 6156)
Changes the autorun value in the registry
- crack.exe (PID: 3720)
- crack.exe (PID: 1792)
- bot.exe (PID: 732)
- crack.exe (PID: 6248)
- crack.exe (PID: 6156)
Avemaria is detected
- bot.exe (PID: 3808)
- bot.exe (PID: 732)
- bot.exe (PID: 1164)
Creates a writable file in the system directory
- bot.exe (PID: 732)
- load.exe (PID: 4448)
SUSPICIOUS
Reads the date of Windows installation
- NovoBot-master.exe (PID: 2276)
- bot.exe (PID: 2208)
- bot.exe (PID: 732)
Executable content was dropped or overwritten
- NovoBot-master.exe (PID: 2276)
- crack.exe (PID: 3720)
- NovoBot_Builder.exe (PID: 2784)
- bot.exe (PID: 2208)
- dllhost.exe (PID: 3884)
- bot.exe (PID: 732)
- load.exe (PID: 4448)
Reads Internet Explorer settings
- NovoBot-master.exe (PID: 2276)
Application launched itself
- bot.exe (PID: 3808)
- bot.exe (PID: 1164)
Reads security settings of Internet Explorer
- crack.exe (PID: 3720)
- crack.exe (PID: 1792)
- bot.exe (PID: 2208)
- bot.exe (PID: 732)
- crack.exe (PID: 6156)
- crack.exe (PID: 6248)
- NovoBot-master.exe (PID: 2276)
Drops a system driver (possible attempt to evade defenses)
- bot.exe (PID: 732)
- load.exe (PID: 4448)
Creates files in the driver directory
- load.exe (PID: 4448)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4196)
Reads Microsoft Outlook installation path
- NovoBot-master.exe (PID: 2276)
INFO
Manual execution by a user
- NovoBot-master.exe (PID: 2276)
- NovoBot_Builder.exe (PID: 2784)
- crack.exe (PID: 1792)
- bot.exe (PID: 3808)
- bot.exe (PID: 1164)
- crack.exe (PID: 6156)
- crack.exe (PID: 6248)
Checks supported languages
- NovoBot-master.exe (PID: 2276)
- crack.exe (PID: 3720)
- NovoBot_Builder.exe (PID: 2784)
- crack.exe (PID: 1792)
- bot.exe (PID: 3808)
- bot.exe (PID: 2208)
- bot.exe (PID: 732)
- load.exe (PID: 4448)
- PLUGScheduler.exe (PID: 4196)
- bot.exe (PID: 1164)
- crack.exe (PID: 6156)
- crack.exe (PID: 6248)
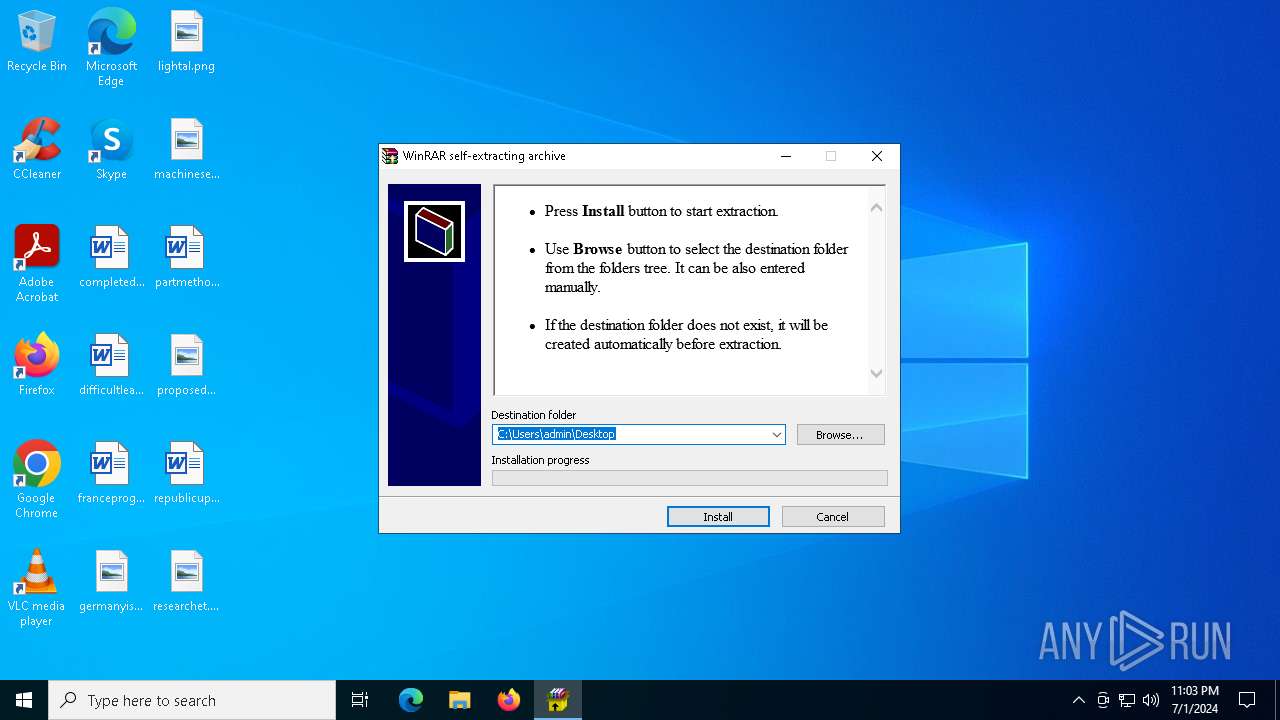
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2720)
- dllhost.exe (PID: 3884)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2720)
Process checks Internet Explorer phishing filters
- NovoBot-master.exe (PID: 2276)
Reads the computer name
- crack.exe (PID: 3720)
- crack.exe (PID: 1792)
- bot.exe (PID: 2208)
- load.exe (PID: 4448)
- bot.exe (PID: 732)
- PLUGScheduler.exe (PID: 4196)
- crack.exe (PID: 6248)
- NovoBot-master.exe (PID: 2276)
- crack.exe (PID: 6156)
Create files in a temporary directory
- crack.exe (PID: 3720)
- bot.exe (PID: 2208)
- bot.exe (PID: 732)
Process checks computer location settings
- NovoBot-master.exe (PID: 2276)
- bot.exe (PID: 2208)
- bot.exe (PID: 732)
Reads the machine GUID from the registry
- crack.exe (PID: 3720)
- crack.exe (PID: 1792)
- bot.exe (PID: 2208)
- crack.exe (PID: 6248)
- crack.exe (PID: 6156)
Creates files or folders in the user directory
- crack.exe (PID: 3720)
- crack.exe (PID: 1792)
- crack.exe (PID: 6156)
- crack.exe (PID: 6248)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 3884)
Checks proxy server information
- bot.exe (PID: 732)
- NovoBot-master.exe (PID: 2276)
Reads Environment values
- bot.exe (PID: 732)
Creates files in the program directory
- PLUGScheduler.exe (PID: 4196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
297
Monitored processes
22
Malicious processes
6
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | "C:\Users\admin\Desktop\Builder\Compiled\bot.exe" | C:\Users\admin\Desktop\Builder\Compiled\bot.exe | Dism.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 936 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\Desktop\Builder\Compiled\bot.exe" | C:\Users\admin\Desktop\Builder\Compiled\bot.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\Desktop\crack.exe" | C:\Users\admin\Desktop\crack.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Get Cliboard Address Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\Desktop\Builder\Compiled\bot.exe" | C:\Users\admin\Desktop\Builder\Compiled\bot.exe | bot.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\Desktop\NovoBot-master.exe" | C:\Users\admin\Desktop\NovoBot-master.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2488 | "C:\WINDOWS\system32\pkgmgr.exe" /n:%temp%\ellocnak.xml | C:\Windows\SysWOW64\PkgMgr.exe | — | bot.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Package Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2720 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Novo Botnet Builder.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
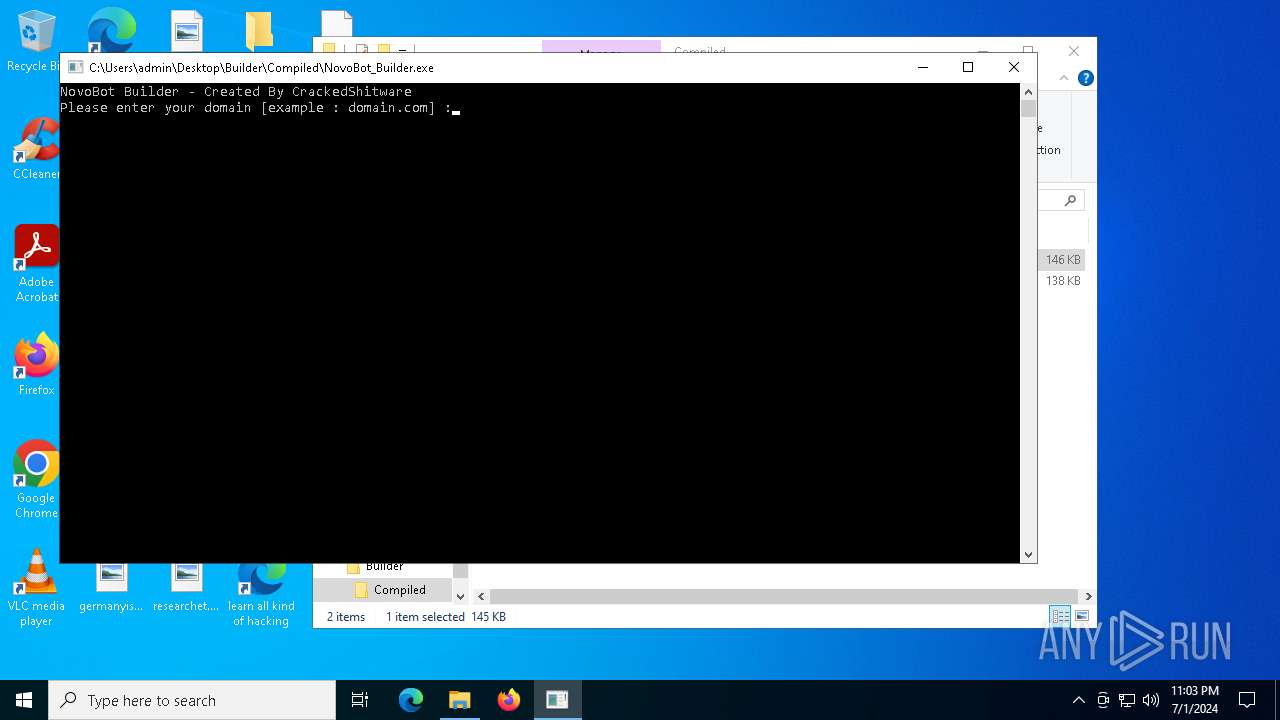
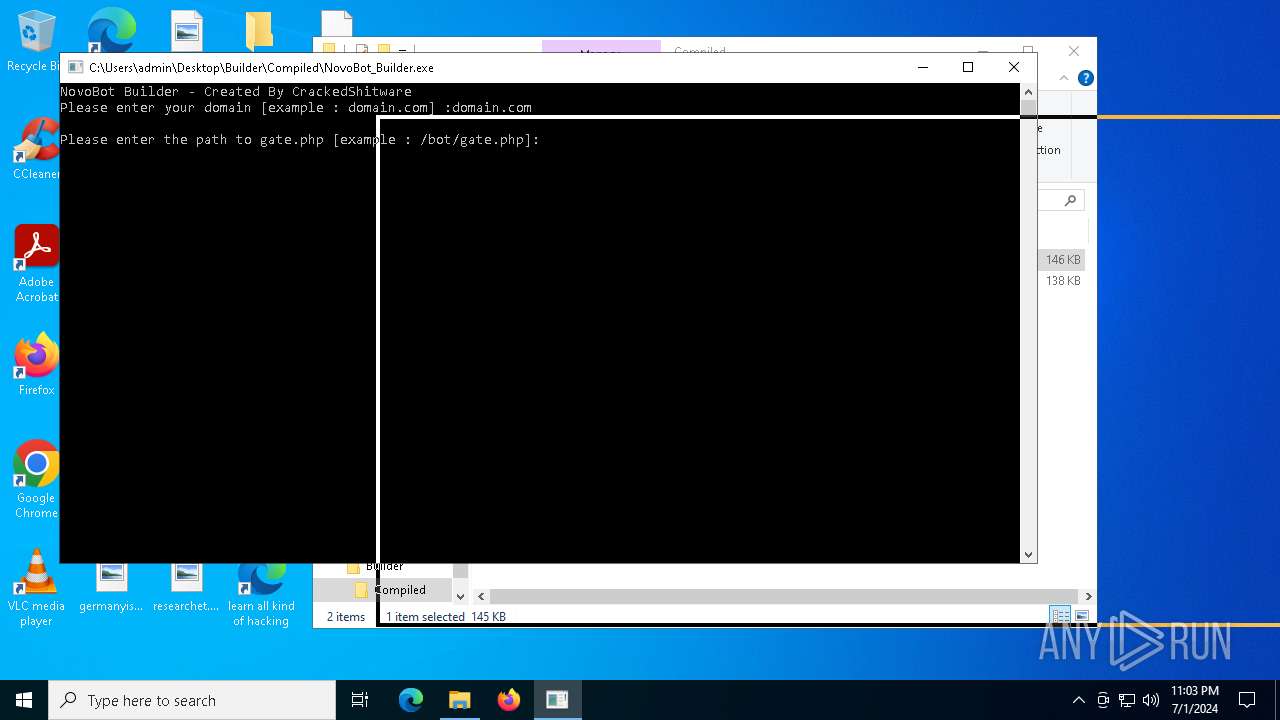
| 2784 | "C:\Users\admin\Desktop\Builder\Compiled\NovoBot_Builder.exe" | C:\Users\admin\Desktop\Builder\Compiled\NovoBot_Builder.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3720 | "C:\Users\admin\Desktop\crack.exe" | C:\Users\admin\Desktop\crack.exe | NovoBot-master.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Get Cliboard Address Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
27 706
Read events
27 606
Write events
98
Delete events
2
Modification events
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Novo Botnet Builder.7z | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2720) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
15
Suspicious files
9
Text files
23
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2720.28826\Novo Botnet Builder\NovoBot-master\NovoBot-master.exe | executable | |
MD5:D0D11673FA64ADDFA89DACA4CB4F8320 | SHA256:3B4D16ED8A13DDAAE638EAABC66CE0863FC8489DBFEA2480E3A66E83FCBC1475 | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\Panel\panel.php | text | |
MD5:4AFA19EC2F9A778F9028E2A2A33D11E5 | SHA256:198AE1ABC40F11344AEC520A331EF2C38029540873876A002E74C1E167DE38D0 | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\Panel\css\bootstrap.min.css | text | |
MD5:7D6D6A0C0F4D21A996D61ADED638E567 | SHA256:32A73773133B21BF09494EC997876C78AC7E62E7FE17830F3D57A8F74F224B01 | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\Panel\js\bootstrap.min.js | text | |
MD5:C5B5B2FA19BD66FF23211D9F844E0131 | SHA256:2979F9A6E32FC42C3E7406339EE9FE76B31D1B52059776A02B4A7FA6A4FD280A | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\crack.exe | executable | |
MD5:B5086EEBE0A0A878807A677AEB4FC4F6 | SHA256:69029912F948D6BD6C3084CA34885CDEEF97190865F6838C9A928FAD56B3F958 | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\Panel\bot.sql | text | |
MD5:E36A78AF188E0F00731F42F750D80C29 | SHA256:83350ED3F3444FF73E98E4FB31C07B6A3F2D2C7057DC863CDD73EB118618BC0E | |||
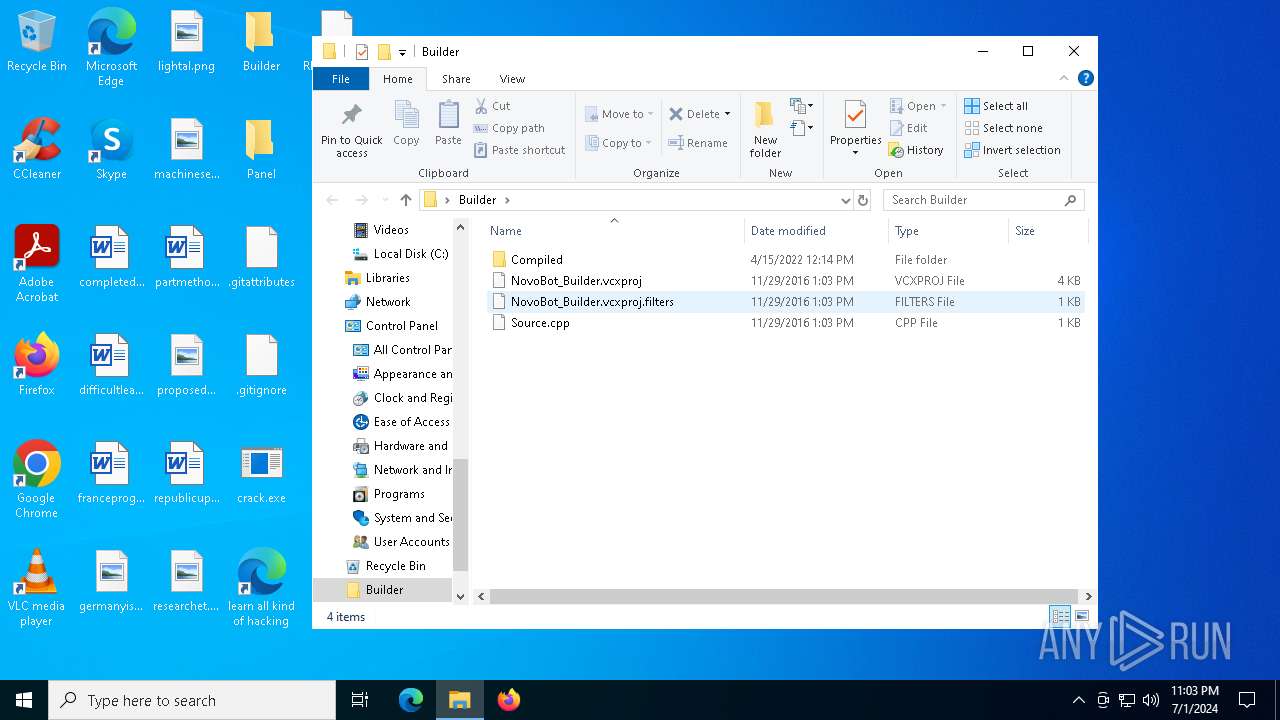
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\Builder\Compiled\NovoBot_Builder.exe | executable | |
MD5:D9A2312364E96967C4070AA1A0D40E69 | SHA256:3287564B9E7372621D5FC240425C75DAAA95C3AEBAEC227F415E5D2048C66A49 | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\Builder\Compiled\stub.bin | executable | |
MD5:06AB9A87BCD4B95FBAF8C959602970DF | SHA256:1659CEE0621F61ED712131115451F5E86EA3773EB1304E7201AF3A7274921B45 | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\Builder\NovoBot_Builder.vcxproj | xml | |
MD5:D76EAB3C706758451F286EB5F2D0B66F | SHA256:AAFDCBBF4A6AC7DCE5946698F8943370399ADD09C448036E6529151B6B830DAE | |||
| 2276 | NovoBot-master.exe | C:\Users\admin\Desktop\.gitattributes | text | |
MD5:01C2BA45B8CE4CB9D870B39204AAE551 | SHA256:BDBD68B106767972511720C3034130C2FFC1862C5ABC29BFE110BF82C5137383 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
111
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2672 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2672 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1912 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
1912 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6116 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
5960 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4088 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3560 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2672 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5968 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2672 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2672 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 52.178.17.3:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3040 | OfficeClickToRun.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4656 | SearchApp.exe | 104.126.37.155:443 | r.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
r.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |