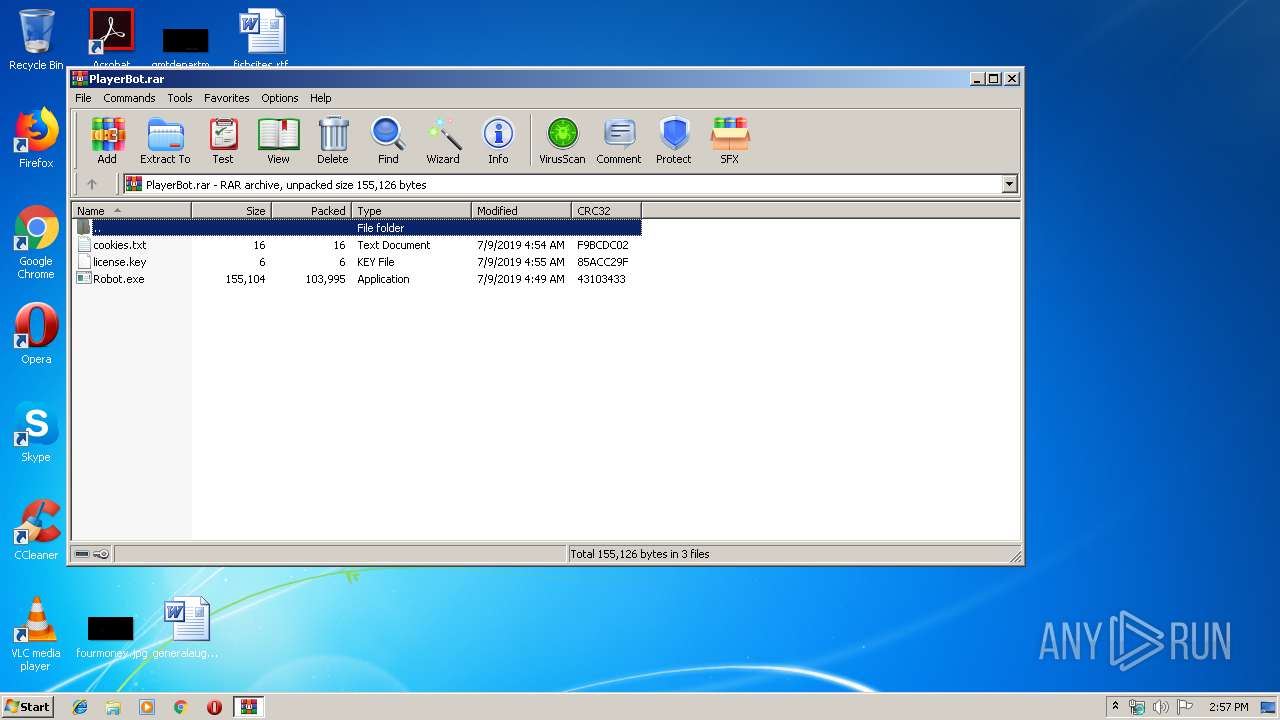
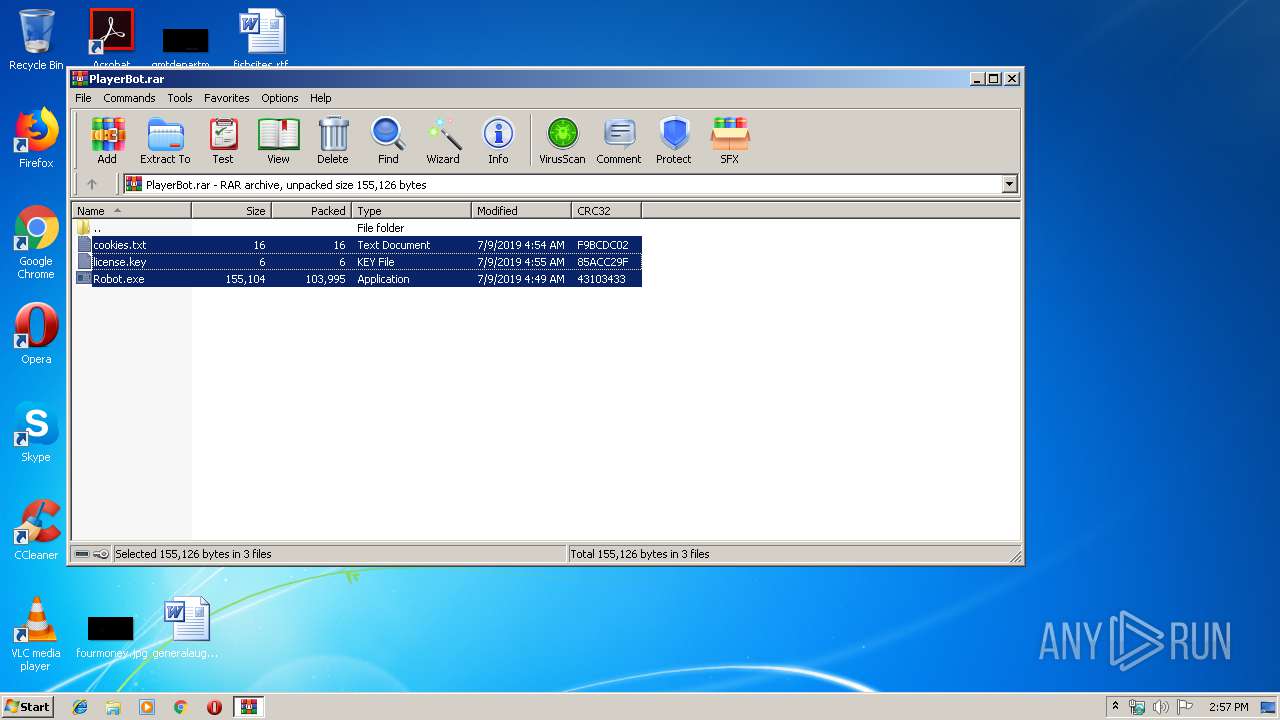
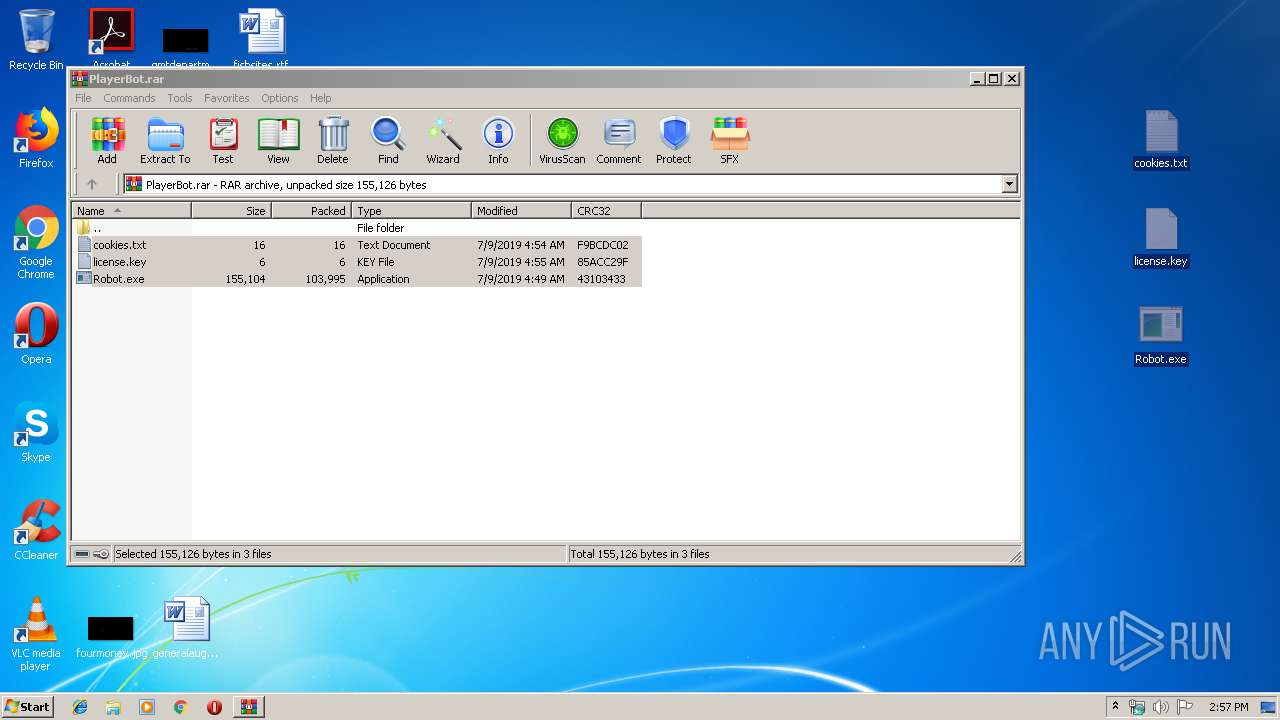
| File name: | PlayerBot.rar |
| Full analysis: | https://app.any.run/tasks/6efdd665-09ac-436c-bd05-5db1cc27e22e |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | July 11, 2019, 13:56:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7EAB6FA8846346FC2854602BAFE6DD68 |
| SHA1: | 98AD7A16BA11E8EE92D51895E8AB68C906C80B05 |
| SHA256: | 34606B57832BF6CD94DE8F1B2A9A7DD59A3F371A0B014A2E12FD8518DD47CC29 |
| SSDEEP: | 3072:EonKQjPF8gzYp5FCK3NA2JVTwamuYRZ8+D5/ulz:EonbPhz2Ff6O2tZ38+dy |
MALICIOUS
Application was dropped or rewritten from another process
- Robot.exe (PID: 2332)
Actions looks like stealing of personal data
- Robot.exe (PID: 2332)
QUASAR was detected
- Robot.exe (PID: 2332)
Connects to CnC server
- Robot.exe (PID: 2332)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2984)
Creates files in the user directory
- notepad++.exe (PID: 2584)
Reads the cookies of Google Chrome
- Robot.exe (PID: 2332)
Reads Environment values
- Robot.exe (PID: 2332)
INFO
Manual execution by user
- notepad++.exe (PID: 2584)
- Robot.exe (PID: 2332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
37
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2332 | "C:\Users\admin\Desktop\Robot.exe" | C:\Users\admin\Desktop\Robot.exe | explorer.exe | ||||||||||||
User: admin Company: Aris Integrity Level: MEDIUM Description: Robot Exit code: 0 Version: 5.2.2.2 Modules
| |||||||||||||||
| 2584 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\license.key" "C:\Users\admin\Desktop\Robot.exe" "C:\Users\admin\Desktop\cookies.txt" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PlayerBot.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3804 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
Total events
554
Read events
498
Write events
56
Delete events
0
Modification events
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PlayerBot.rar | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
1
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2984.43791\cookies.txt | — | |
MD5:— | SHA256:— | |||
| 2984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2984.43791\license.key | — | |
MD5:— | SHA256:— | |||
| 2984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2984.43791\Robot.exe | executable | |
MD5:— | SHA256:— | |||
| 2584 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:— | SHA256:— | |||
| 2332 | Robot.exe | C:\Users\admin\AppData\Local\Temp\93b65675-46b1-45a0-96c5-e2a6d9161f2c_chrome.txt | text | |
MD5:— | SHA256:— | |||
| 2584 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:E792264BEC29005B9044A435FBA185AB | SHA256:5298FD2F119C43D04F6CF831F379EC25B4156192278E40E458EC356F9B49D624 | |||
| 2584 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\Config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
| 2584 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:44982E1D48434C0AB3E8277E322DD1E4 | SHA256:3E661D3F1FF3977B022A0ACC26B840B5E57D600BC03DCFC6BEFDB408C665904C | |||
| 2584 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:EA9FE896B4305C2A9629FEB279084544 | SHA256:EF99FB4EFE424FABB1F3CD0076CC532EF5767D6CD1D09611C4F69F1BE03702B6 | |||
| 2584 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:AD21A64014891793DD9B21D835278F36 | SHA256:C24699C9D00ABDD510140FE1B2ACE97BFC70D8B21BF3462DED85AFC4F73FE52F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
4
DNS requests
4
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.21.242.187:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | NL | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3804 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
2332 | Robot.exe | 104.31.77.103:443 | rokey.xyz | Cloudflare Inc | US | shared |
2332 | Robot.exe | 104.31.76.103:443 | rokey.xyz | Cloudflare Inc | US | shared |
— | — | 2.21.242.187:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
rokey.xyz |
| malicious |
browserloot.rokey.xyz |
| malicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2332 | Robot.exe | A Network Trojan was detected | MALWARE [PTsecurity] BrowserLoot Stealer |
2332 | Robot.exe | A Network Trojan was detected | MALWARE [PTsecurity] BrowserLoot Stealer |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|