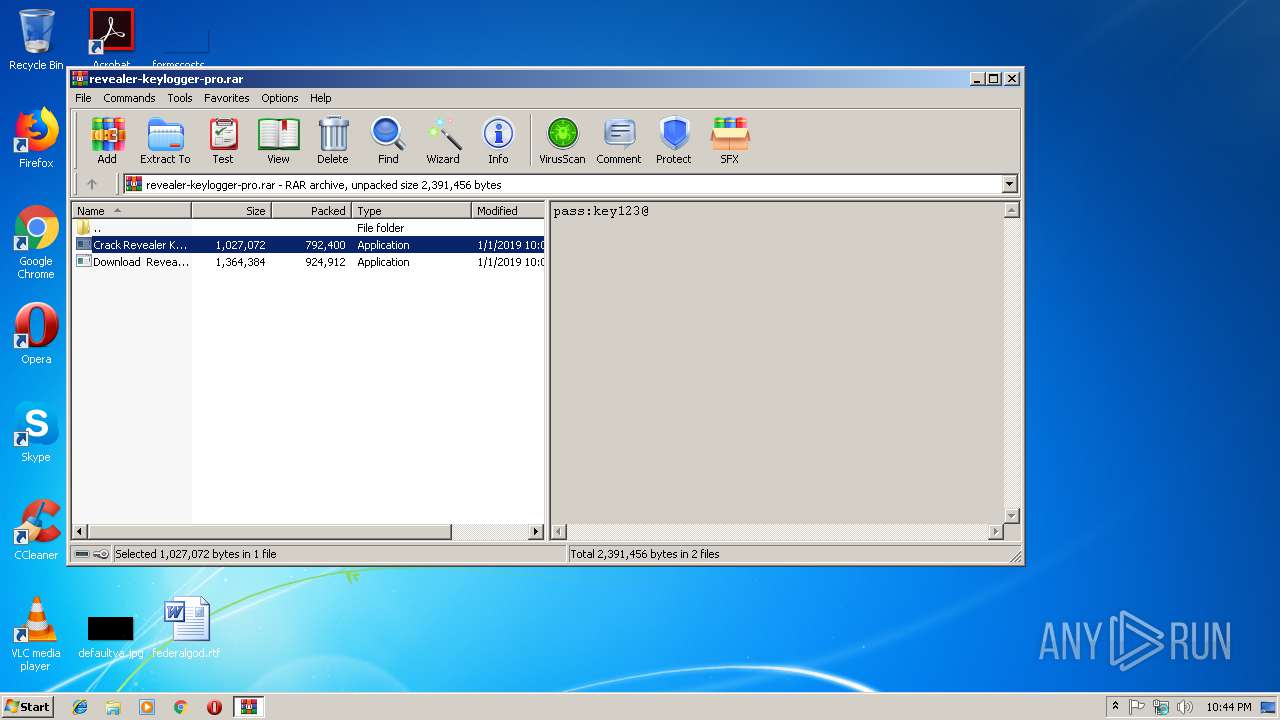
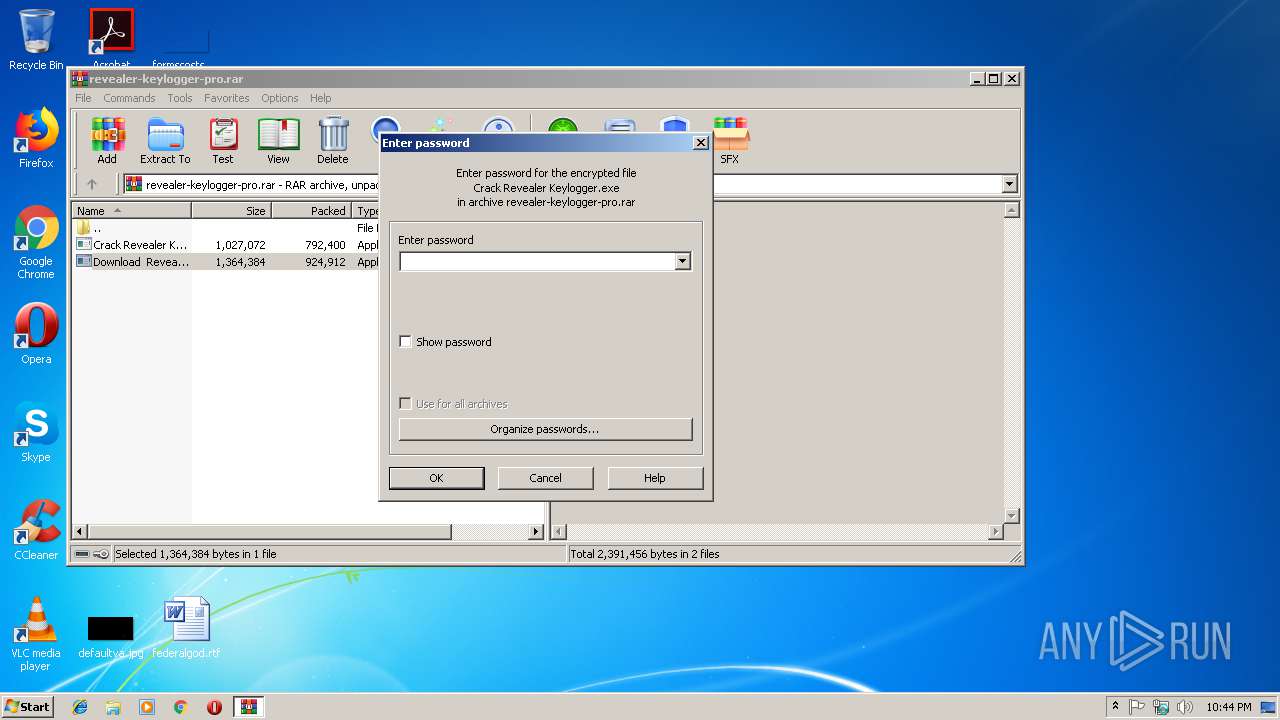
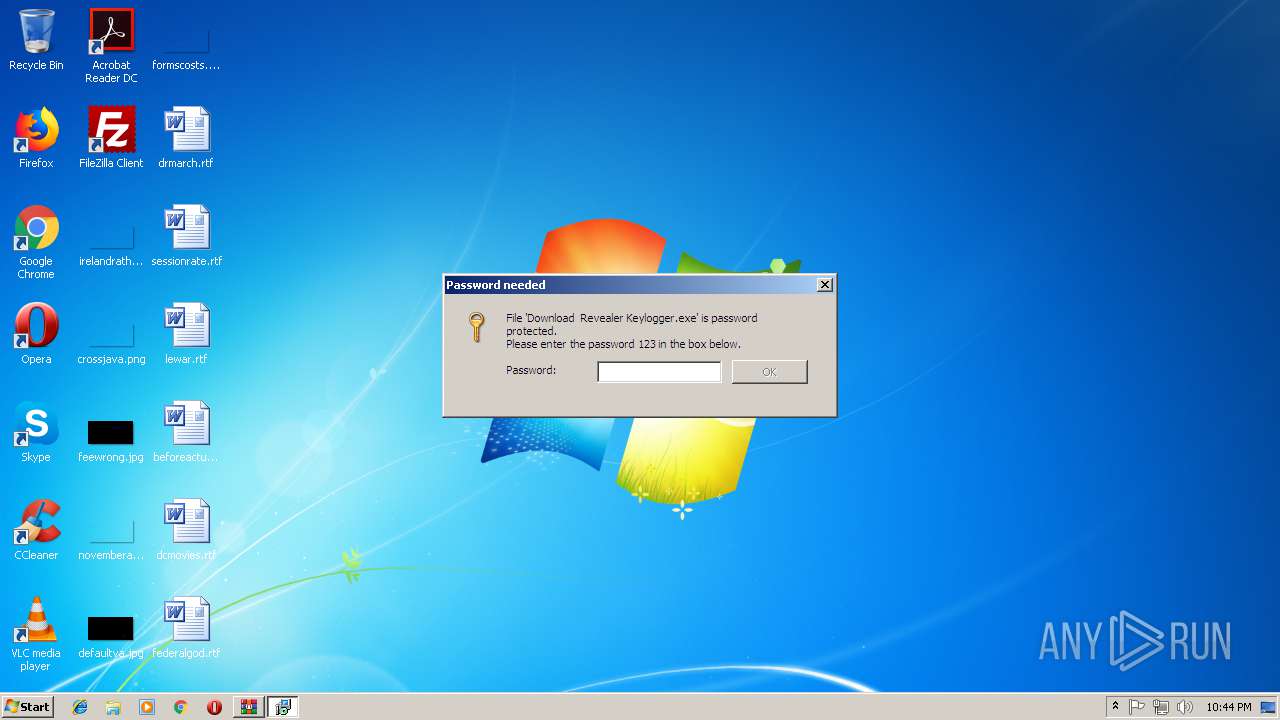
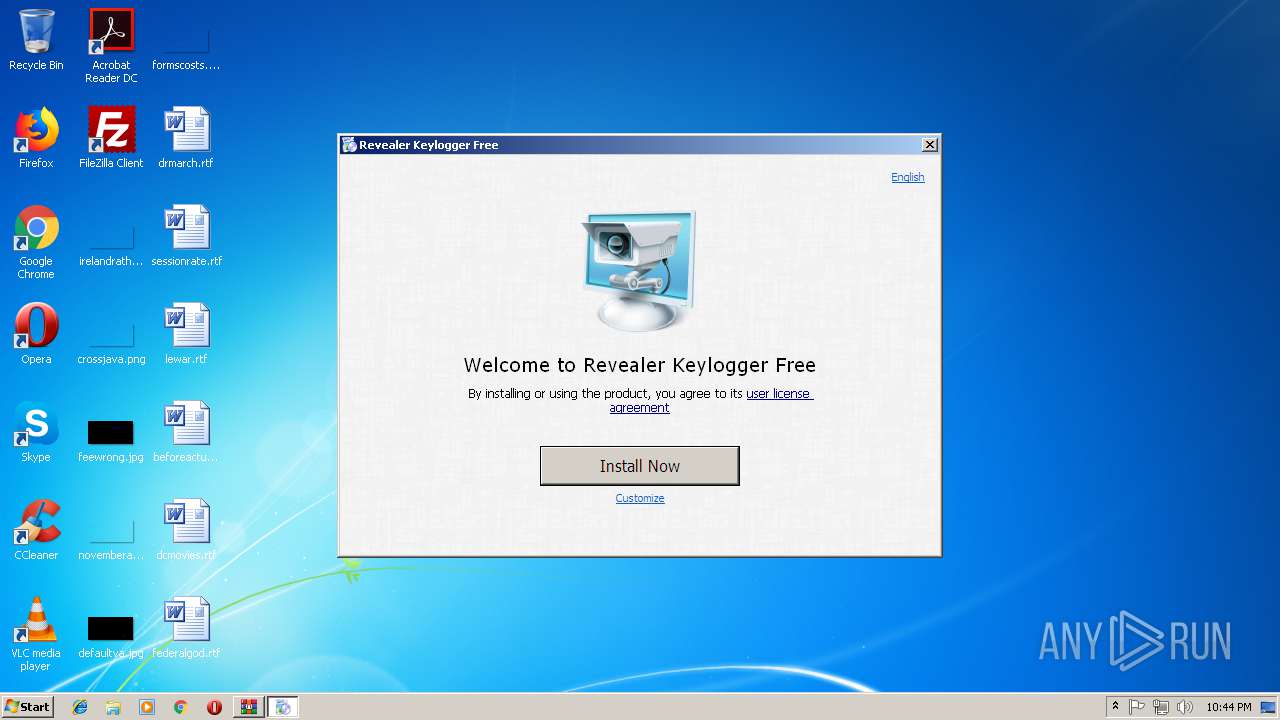
| File name: | revealer-keylogger-pro.rar |
| Full analysis: | https://app.any.run/tasks/93ff9595-aa96-4c3d-a4ac-e74507600399 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | January 01, 2019, 22:43:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BC869B75245E63C204E5CD6F77EF3A82 |
| SHA1: | C470030399715311DBFFD155208A49AA793499BB |
| SHA256: | 344A65172488BE82553DE21E3147B1AC1228F97501BBECC446FC8D301C5134C4 |
| SSDEEP: | 24576:3wff9ca7IQrSftSzRm2LJdQcXB25Xc2umDZM3QbzxT5RBBN0DmVQvBySM1Ohp:gfEfvcxAMrmtZbzxTTNSmVQpySwOhp |
MALICIOUS
Uses SVCHOST.EXE for hidden code execution
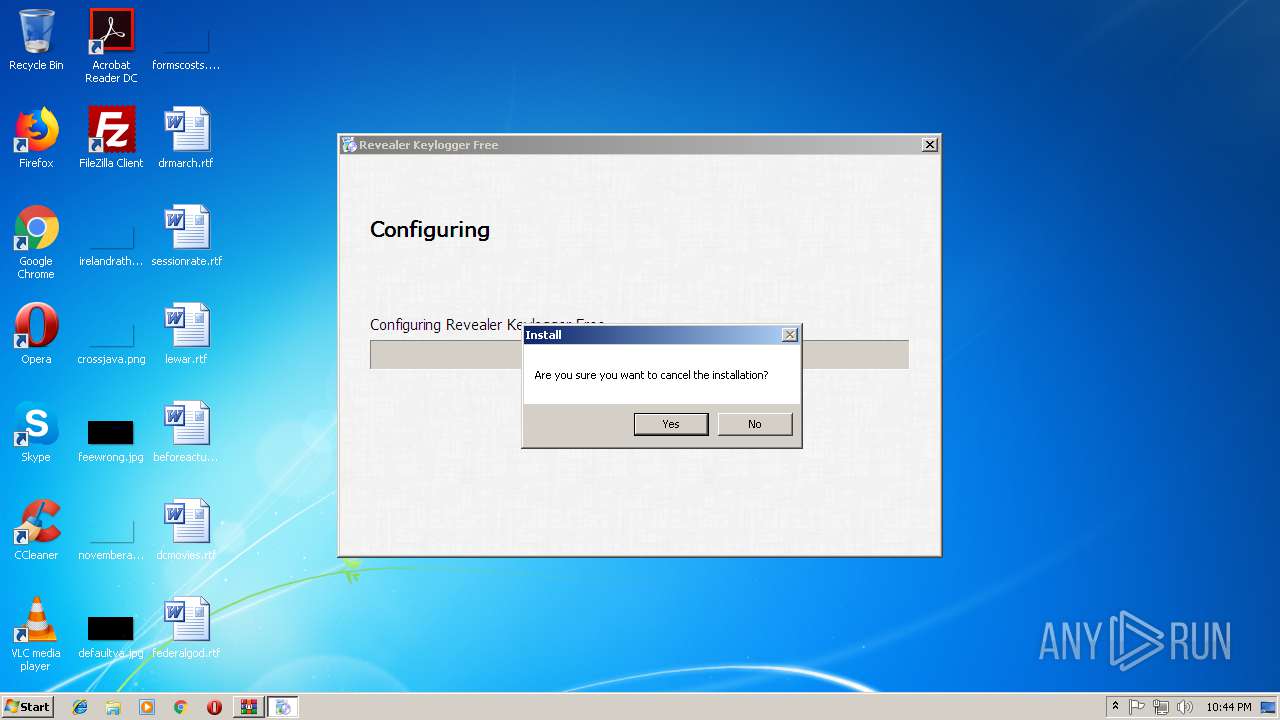
- Crack Revealer Keylogger.exe (PID: 3340)
- loader.exe (PID: 3592)
Application was dropped or rewritten from another process
- loader.exe (PID: 3592)
- Crack Revealer Keylogger.exe (PID: 2908)
- Crack Revealer Keylogger.exe (PID: 3340)
- 7za.exe (PID: 2908)
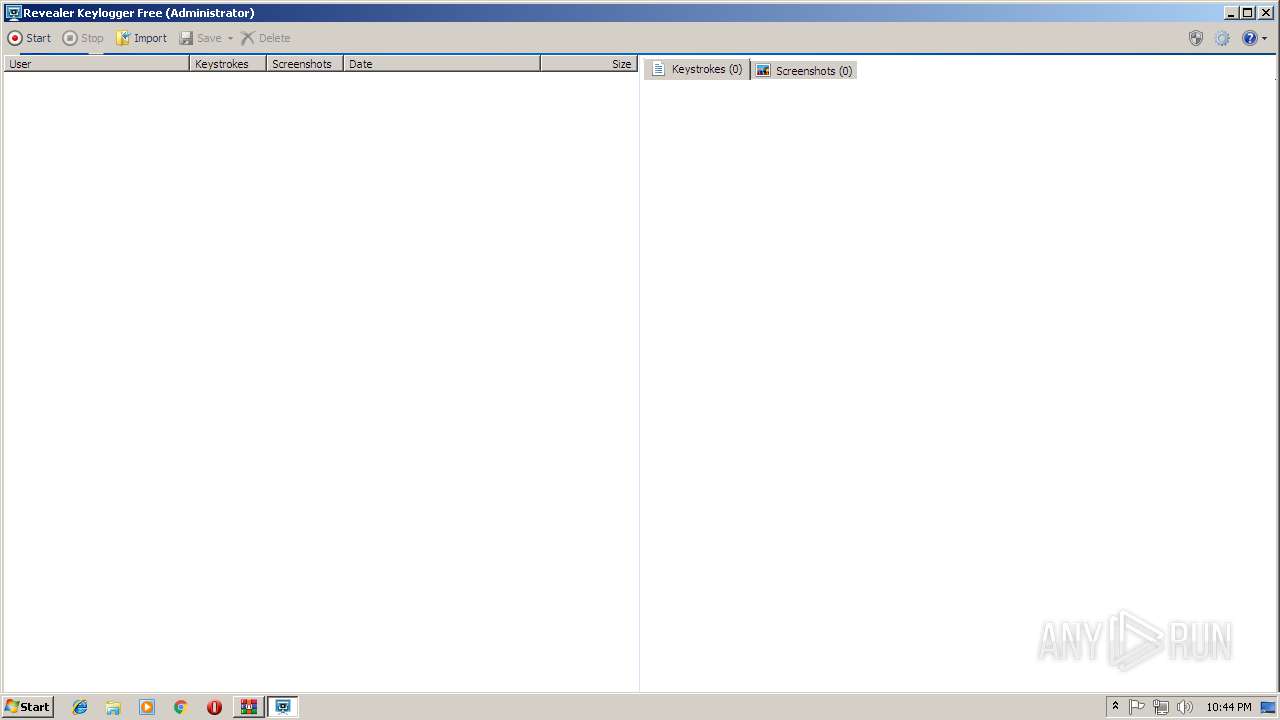
- rvlkl.exe (PID: 2324)
- setup.exe (PID: 2360)
- rvlkl.exe (PID: 3764)
- Download Revealer Keylogger.exe (PID: 3696)
- Download Revealer Keylogger.exe (PID: 3720)
Writes to a start menu file
- setup.exe (PID: 2360)
MINER was detected
- svchost.exe (PID: 2216)
Connects to CnC server
- svchost.exe (PID: 2216)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2132)
SUSPICIOUS
Creates or modifies windows services
- Crack Revealer Keylogger.exe (PID: 2908)
- loader.exe (PID: 3592)
Creates a software uninstall entry
- Crack Revealer Keylogger.exe (PID: 3340)
Starts CMD.EXE for commands execution
- Crack Revealer Keylogger.exe (PID: 2908)
Creates files in the program directory
- Crack Revealer Keylogger.exe (PID: 2908)
- setup.exe (PID: 2360)
- rvlkl.exe (PID: 3764)
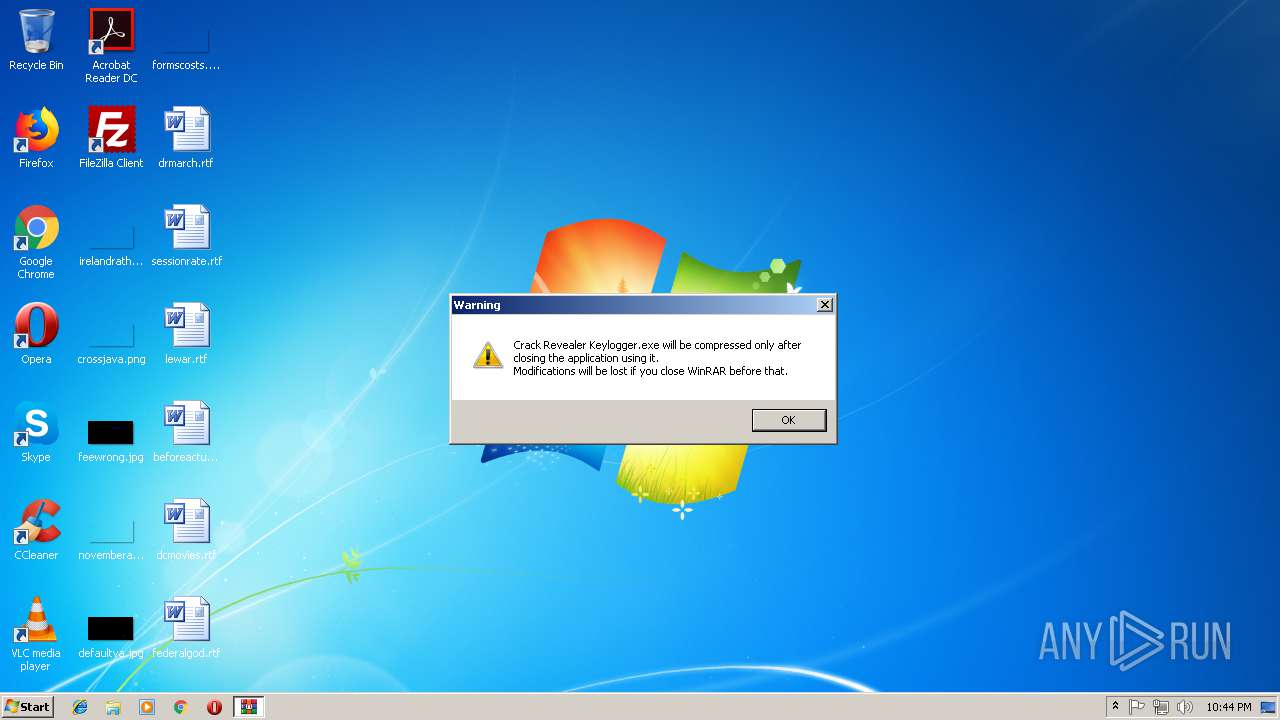
Executable content was dropped or overwritten
- Crack Revealer Keylogger.exe (PID: 2908)
- WinRAR.exe (PID: 2844)
- Download Revealer Keylogger.exe (PID: 3696)
- 7za.exe (PID: 2908)
- setup.exe (PID: 2360)
Creates files in the Windows directory
- setup.exe (PID: 2360)
Reads internet explorer settings
- rvlkl.exe (PID: 3764)
Connects to unusual port
- svchost.exe (PID: 2216)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
56
Monitored processes
18
Malicious processes
7
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1248 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1868 | C:\Windows\system32\DllHost.exe /Processid:{FCC74B77-EC3E-4DD8-A80B-008A702075A9} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2132 | C:\Windows\system32\cmd.exe /c @ping -n 15 127.0.0.1&del C:\Users\admin\AppData\Local\Temp\RAR$EX~1.136\CRACKR~1.EXE > nul | C:\Windows\system32\cmd.exe | — | Crack Revealer Keylogger.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2216 | "C:\Windows\system32\svchost.exe" | C:\Windows\system32\svchost.exe | loader.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2324 | "C:\Windows\system32\rvlkl.exe" | C:\Windows\system32\rvlkl.exe | — | setup.exe | |||||||||||
User: admin Company: Logixoft Integrity Level: HIGH Description: Revealer Keylogger Free Exit code: 3221226540 Version: 2.2.9.0 Modules
| |||||||||||||||
| 2360 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | Download Revealer Keylogger.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2844 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\revealer-keylogger-pro.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2908 | "C:\Users\admin\AppData\Local\Temp\7za.exe" x setup.7z setup.exe -p123 | C:\Users\admin\AppData\Local\Temp\7za.exe | Download Revealer Keylogger.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Exit code: 0 Version: 18.05 Modules
| |||||||||||||||
| 2908 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2844.13693\Crack Revealer Keylogger.exe" BypassUac | C:\Users\admin\AppData\Local\Temp\Rar$EXb2844.13693\Crack Revealer Keylogger.exe | DllHost.exe | ||||||||||||
User: admin Company: U5GTWUY18XA1 Integrity Level: HIGH Description: R58W7 Exit code: 0 Version: 3.2.4.6 Modules
| |||||||||||||||
| 3072 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\New Text Document.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 112
Read events
1 075
Write events
35
Delete events
2
Modification events
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\revealer-keylogger-pro.rar | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3340) Crack Revealer Keylogger.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\{A16390FC-9D81-43B1-8A3C-82802F608193} |
| Operation: | write | Name: | UninstallString |
Value: C:\Users\admin\AppData\Local\Temp\Rar$EXb2844.13693\Crack Revealer Keylogger.exe BypassUac | |||
| (PID) Process: | (2844) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
8
Suspicious files
5
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2360 | setup.exe | C:\ProgramData\rvlkl\conf_ | — | |
MD5:— | SHA256:— | |||
| 3764 | rvlkl.exe | C:\ProgramData\rvlkl\conf_ | — | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2844.13693\Download Revealer Keylogger.exe | executable | |
MD5:— | SHA256:— | |||
| 2844 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2844.13693\Crack Revealer Keylogger.exe | executable | |
MD5:— | SHA256:— | |||
| 2908 | 7za.exe | C:\Users\admin\AppData\Local\Temp\setup.exe | executable | |
MD5:— | SHA256:— | |||
| 2360 | setup.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\rvlkl.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2360 | setup.exe | C:\Windows\system32\rvlkl.exe | executable | |
MD5:— | SHA256:— | |||
| 3764 | rvlkl.exe | C:\ProgramData\rvlkl\conf | binary | |
MD5:— | SHA256:— | |||
| 2360 | setup.exe | C:\ProgramData\rvlkl\conf | binary | |
MD5:— | SHA256:— | |||
| 2908 | Crack Revealer Keylogger.exe | C:\ProgramData\WinTcpAutoProxySvc\loader.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
7
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2216 | svchost.exe | 136.243.102.157:45700 | xmr.pool.minergate.com | Hetzner Online GmbH | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xmr.pool.minergate.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | A Network Trojan was detected | ET POLICY Monero Mining Pool DNS Lookup |
2216 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2216 | svchost.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
2216 | svchost.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
2216 | svchost.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |
2216 | svchost.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
2216 | svchost.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |
Process | Message |
|---|---|
loader.exe | My Sample Service: ServiceMain: Entry
|
loader.exe | My Sample Service: ServiceMain: Performing Service Start Operations
|
loader.exe | My Sample Service: ServiceMain: Waiting for Worker Thread to complete
|
loader.exe | host_data.m_CheckTaskmgr = 1
|
loader.exe | thread= 2452, SuspendThread Count = 0 succeeds !
|
loader.exe | thread= 3812, SuspendThread Count = 0 succeeds !
|
loader.exe | thread= 3824, SuspendThread Count = 0 succeeds !
|
loader.exe | thread= 3900, SuspendThread Count = 0 succeeds !
|
loader.exe | thread= 3904, SuspendThread Count = 0 succeeds !
|
loader.exe | thread= 3932, SuspendThread Count = 0 succeeds !
|